- Preface
- New and Changed Information
- Overview
- Managing User Accounts
- Configuring VSD
- Configuring AAA
- Configuring RADIUS
- Configuring TACACS+
- Configuring SSH
- Configuring Telnet
- Configuring IP ACLs
- Configuring MAC ACLs
- Configuring Port Security
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring IP Source Guard
- Disabling the HTTP Server
- Blocking Unknown Unicast Flooding
- Configuring Cisco TrustSec
- Index
Cisco Nexus 1000V Security Configuration Guide, Release 4.2(1)SV2(2.1)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- March 4, 2015
Chapter: Configuring Port Security
Contents
- Configuring Port Security
- Information About Port Security
- Secure MAC Address Learning
- Static Method
- Dynamic Method
- Sticky Method
- Dynamic Address Aging
- Secure MAC Address Maximums
- Interface Secure MAC Addresses
- Security Violations and Actions
- Port Security and Port Types
- Result of Changing an Access Port to a Trunk Port
- Result of Changing a Trunk Port to an Access Port
- Guidelines and Limitations for Port Security
- Default Settings for Port Security
- Configuring Port Security
- Enabling or Disabling Port Security on a Layer 2 Interface
- Enabling or Disabling Sticky MAC Address Learning
- Adding a Static Secure MAC Address on an Interface
- Removing a Static or a Sticky Secure MAC Address from an Interface
- Removing a Dynamic Secure MAC Address
- Configuring a Maximum Number of MAC Addresses
- Configuring an Address Aging Type and Time
- Configuring a Security Violation Action
- Recovering Ports Disabled for Port Security Violations
- Verifying the Port Security Configuration
- Displaying Secure MAC Addresses
- Configuration Example for Port Security
- Feature History for Port Security
Configuring Port Security
This chapter contains the following sections:
- Information About Port Security
- Guidelines and Limitations for Port Security
- Default Settings for Port Security
- Configuring Port Security
- Verifying the Port Security Configuration
- Displaying Secure MAC Addresses
- Configuration Example for Port Security
- Feature History for Port Security
Information About Port Security
Port security allows you to configure Layer 2 interfaces that permit inbound traffic from a restricted, secured set of MAC addresses. Traffic from secured MAC addresses is not allowed on another interface within the same VLAN. The number of MAC addresses that can be secured is configured per interface.
- Secure MAC Address Learning
- Dynamic Address Aging
- Secure MAC Address Maximums
- Security Violations and Actions
- Port Security and Port Types
Secure MAC Address Learning
Static Method
The static learning method allows you to manually add or remove secure MAC addresses to the running configuration of an interface. If you copy the running configuration to the startup configuration, static secure MAC addresses are persistent if the device restarts.
A static secure MAC address entry remains in the configuration of an interface until you explicitly remove the address from the configuration.
Adding secure addresses by the static method is not affected by whether dynamic or sticky address learning is enabled.
Dynamic Method
By default, when you enable port security on an interface, you enable the dynamic learning method. With this method, the device secures MAC addresses as ingress traffic passes through the interface. If the address is not yet secured and the device has not reached any applicable maximum, it secures the address and allows the traffic.
The device stores dynamic secure MAC addresses in memory. A dynamic secure MAC address entry remains in the configuration of an interface until one of the following events occurs:
Sticky Method
If you enable the sticky method, the device secures MAC addresses in the same manner as dynamic address learning. These addresses can be made persistent through a reboot by using the copy run start command to copy the running configuration to the startup configuration.
Dynamic and sticky address learning are mutually exclusive. When you enable sticky learning on an interface, dynamic learning is stopped and sticky learning is used instead. If you disable sticky learning, dynamic learning is resumed.
Sticky secure MAC addresses are not aged.
A sticky secure MAC address entry remains in the configuration of an interface until you explicitly remove the address.
Dynamic Address Aging
MAC addresses that are learned by the dynamic method are aged and dropped when reaching the age limit. You can configure the age limit on each interface. The range is from 0 to 1440 minutes, where 0 disables aging.
There are two methods of determining the address age:
Secure MAC Address Maximums
The secure MAC addresses on a secure port are inserted in the same MAC address table as other regular MAC addresses. If a MAC table has reached its limit, it does not learn any new secure MAC addresses for that VLAN.
The following figure shows that each VLAN in a VEM has a forwarding table that can store a maximum number of secure MAC addresses.
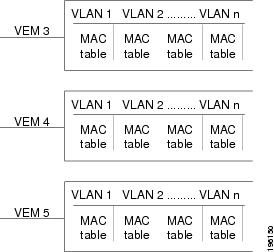
Interface Secure MAC Addresses
By default, an interface can have only one secure MAC address. You can configure the maximum number of MAC addresses permitted per interface or per VLAN on an interface. Maximums apply to secure MAC addresses learned by any method: dynamic, sticky, or static.
The following limits can determine how many secure MAC address are permitted on an interface:
Device maximum—The device has a nonconfigurable limit of 8192 secure MAC addresses. If learning a new address would violate the device maximum, the device does not permit the new address to be learned, even if the interface or VLAN maximum has not been reached.
Interface maximum—You can configure a maximum number of secure MAC addresses for each interface protected by port security. The default interface maximum is one address for both access and trunk vethernet ports. Interface maximums cannot exceed the device maximum.
VLAN maximum—You can configure the maximum number of secure MAC addresses per VLAN for each interface protected by port security. A VLAN maximum cannot exceed the interface maximum. VLAN maximums are useful only for trunk ports. There are no default VLAN maximums.
You can configure a VLAN and interface maximums per interface, as needed; however, when the new limit is less than the applicable number of secure addresses, you must reduce the number of secure MAC addresses first.
Security Violations and Actions
Port security triggers a security violation when either of the following occurs:
Ingress traffic arrives at an interface from a nonsecure MAC address and learning the address would exceed the applicable maximum number of secure MAC addresses.
When an interface has both a VLAN maximum and an interface maximum configured, a violation occurs when either maximum is exceeded. For example, consider the following on a single interface configured with port security:
A violation is detected when either of the following occurs:
Ingress traffic from a secure MAC address arrives at a different interface in the same VLAN as the interface on which the address is secured. 
NoteAfter a secure MAC address is configured or learned on one secure port, the sequence of events that occurs when port security detects that secure MAC address on a different port in the same VLAN is known as a MAC move violation.
Shutdown—Shuts down the interface that received the packet triggering the violation. The interface is error disabled. This action is the default. After you reenable the interface, it retains its port security configuration, including its secure MAC addresses.
You can use the errdisable global configuration command to configure the device to reenable the interface automatically if a shutdown occurs, or you can manually reenable the interface by entering the shutdown and no shut down interface configuration commands.
switch(config)# errdisable recovery cause psecure-violation switch(config)# copy running-config startup-config
Protect—Prevents violations from occurring. Address learning continues until the maximum number of MAC addresses on the interface is reached, after which the device disables learning on the interface and drops all ingress traffic from nonsecure MAC addresses.
Restrict—Prevents violations from occurring. Address learning continues until the maximum number of MAC addresses on the interface is reached, after which the device disables learning on the interface and drops all ingress traffic from nonsecure MAC addresses and causes the security violation counter to increment.
A MAC Move Violation is triggered on the port that sees the MAC address that is already secured on another interface. If MAC A is secured on interface A, and then if ingress traffic arrives on interface B with the same source MAC as that of secured MAC A, then the action is applied to interface B that received the traffic. Interface B will be error disabled.
Port Security and Port Types
You can configure port security only on Layer 2 interfaces. Details about port security and different types of interfaces or ports are as follows:
Access ports—You can configure port security on interfaces that you have configured as Layer 2 access ports. On an access port, port security applies only to the access VLAN.
Trunk ports—You can configure port security on interfaces that you have configured as Layer 2 trunk veth ports. VLAN maximums are not useful for access ports. The device allows VLAN maximums only for VLANs associated with the trunk port.
SPAN ports—You can configure port security on SPAN source ports but not on SPAN destination ports.
Ethernet Ports—Port security is not supported on Ethernet ports.
Ethernet Port Channels—Port security is not supported on Ethernet port channels.
Result of Changing an Access Port to a Trunk Port
When you change a Layer 2 interface from an access port to a trunk port, the device drops all secure addresses learned by the dynamic method. The device moves the addresses learned by the static or sticky method to the native trunk VLAN.
Result of Changing a Trunk Port to an Access Port
When you change a Layer 2 interface from a trunk port to an access port, the device drops all secure addresses learned by the dynamic method. It also moves all addresses learned by the sticky method on the native trunk VLAN to the access VLAN. The device drops secure addresses learned by the sticky method if they are not on the native trunk VLAN.
Guidelines and Limitations for Port Security
Default Settings for Port Security
Parameters |
Default |
|---|---|
Interface |
Disabled |
MAC address learning method |
Dynamic |
Interface maximum number of secure MAC addresses |
1 |
Security violation action |
Shutdown |
Configuring Port Security
Enabling or Disabling Port Security on a Layer 2 Interface
By default, port security is disabled on all interfaces.
Enabling port security on an interface also enables dynamic MAC address learning.
This example shows how to enable port security on a Layer 2 interface:
switch# configure terminal switch(config)# interface vethernet 36 switch(config-if)# switchport port-security switch(config-if)# show running-config port-security interface Vethernet36 switchport port-security switch(config-if)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2303 0050.5687.3C68 DYNAMIC Vethernet36 0 ---------------------------------------------------------------------- switch(config-if)# show port-security interface vethernet 36 Port Security : Enabled Port Status : Secure UP Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Security violation count : 0 switch(config-if)# copy running-config startup-config
Enabling or Disabling Sticky MAC Address Learning
You can enable or disable sticky MAC address learning.
Dynamic MAC address learning is the default on an interface.
By default, sticky MAC address learning is disabled.
This example shows how to enable sticky MAC address learning:
switch(config)# interface Vethernet36 switch(config-if)# switchport port-security switch(config-if)# switchport port-security mac-address sticky switch(config-if)# switchport port-security mac-address 0050.5687.3C4B switch(config)# show running-config port-security interface Vethernet36 switchport port-security switchport port-security mac-address sticky switchport port-security mac-address 0050.5687.3C4B switch(config)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2304 0050.5687.3C4B STICKY Vethernet36 0 ----------------------------------------------------------------------
Adding a Static Secure MAC Address on an Interface
You can add a static secure MAC address on an interface.
By default, no static secure MAC addresses are configured on an interface.
This example shows how to add a static secure MAC address on an interface:
switch# configure terminal switch(config)# interface vethernet 36 switch(config-if)# switchport port-security mac-address 0019.D2D0.00AE switch(config)# show running-config port-security interface Vethernet36 switchport port-security switchport port-security maximum 5 switchport port-security mac-address 0019.D2D0.00AE switch(config)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2304 0019.D2D0.00AE STATIC Vethernet36 0 2304 0050.5687.3C4B DYNAMIC Vethernet36 0 ---------------------------------------------------------------------- VLAN MAC Address Type Age Port Mod switch(config-if)# copy running-config startup-config
Removing a Static or a Sticky Secure MAC Address from an Interface
You can remove a static or a sticky secure MAC address from a Layer 2 interface.
This example shows how to remove the MAC address from port security on the current interface:
switch(config-if)# interface Vethernet36 switch(config-if)# switchport port-security switch(config-if)# switchport port-security maximum 5 switch(config-if)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2303 0050.5687.1111 STATIC Vethernet36 0 2303 0050.5687.3C4B DYNAMIC Vethernet36 0 ---------------------------------------------------------------------- switch(config-if)# no switchport port-security mac-address 0050.5687.1111 switch(config-if)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2303 0050.5687.3C4B DYNAMIC Vethernet36 0 ----------------------------------------------------------------------
Removing a Dynamic Secure MAC Address
You can remove a specific address learned by the dynamic method or remove all addresses learned by the dynamic method on a specific interface.
Log in to the CLI in EXEC mode.
This example shows how to remove a dynamically learned, secure MAC address:
switch(config)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2303 0000.1111.2224 STATIC Vethernet36 0 2303 0050.5687.3C4B DYNAMIC Vethernet36 0 ---------------------------------------------------------------------- switch(config)# clear port-security dynamic interface vethernet 36 switch(config)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2303 0000.1111.2224 STATIC Vethernet36 0 ----------------------------------------------------------------------
Configuring a Maximum Number of MAC Addresses
You can configure the maximum number of MAC addresses that can be learned or statically configured on a Layer 2 interface. You can also configure a maximum number of MAC addresses per VLAN on a Layer 2 interface. The largest maximum number of addresses that you can configure is 4096 addresses.
The secure MAC addresses share the Layer 2 Forwarding Table (L2FT). The forwarding table for each VLAN can hold up to 1024 entries.
By default, an interface has a maximum of one secure MAC address.
VLANs have no default maximum number of secure MAC addresses.
To remove all addresses learned by the dynamic method, use the shutdown and no shutdown commands to restart the interface.
 Note | When you specify a maximum number of addresses that is less than the number of addresses already learned or statically configured on the interface, the command is rejected. |
This example shows how to configure a maximum number of MAC addresses:
switch(config-if)# interface Vethernet36 switch(config-if)# switchport port-security switch(config-if)# switchport port-security maximum 425 switch(config-if)# show port-security interface vethernet 36 Port Security : Enabled Port Status : Secure UP Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute Maximum MAC Addresses : 425 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Security violation count : 0 switch(config-if)# show running-config port-security interface Vethernet36 switchport port-security switchport port-security maximum 425
Configuring an Address Aging Type and Time
You can configure the MAC address aging type and the length of time used to determine when MAC addresses learned by the dynamic method have reached their age limit.
There are two methods for determining address aging:
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# interface type number | Places you into interface configuration mode for the specified interface. |
| Step 3 | switch(config-if)# [no] switchport port-security aging type {absolute | inactivity} |
Configures the type of aging that the device applies to dynamically learned MAC addresses. The no option resets the aging type to the default, which is absolute aging. |
| Step 4 | switch(config-if)# [no] switchport port-security aging time minutes | Configures the number of minutes that a dynamically learned MAC address must age before the address is dropped. The maximum valid minutes is 1440. The no option resets the aging time to the default, which is 0 minutes (no aging). |
| Step 5 | switch(config-if)# show port-security address interface vethernet number | (Optional) Displays the secure MAC address learnt on the interface. |
| Step 6 | switch(config-if)# show port-security interface vethernet number | (Optional) Displays the port security configuration on the interface. |
| Step 7 | switch(config-if)# show running-config port-security | (Optional) Displays the port security configuration. |
| Step 8 | switch(config-if)# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure an address aging type and time:
switch(config-if)# show running-config port-security interface Vethernet36 switchport port-security switchport port-security aging type inactivity switchport port-security aging time 120 switch(config-if)# interface Vethernet36 switch(config-if)# switchport port-security switch(config-if)# switchport port-security aging type inactivity switch(config-if)# switchport port-security aging time 120 switch(config-if)# show port-security address interface vethernet 36 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2304 0050.5687.3C4B DYNAMIC Vethernet36 120 ---------------------------------------------------------------------- switch(config-if)# show port-security interface vethernet 36 Port Security : Enabled Port Status : Secure UP Violation Mode : Shutdown Aging Time : 120 mins Aging Type : Inactivity Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Security violation count : 0
Configuring a Security Violation Action
protect—Drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value.
restrict—Drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value and causes the SecurityViolation counter to increment.
shutdown (the default)—Puts the interface into the error-disabled state immediately and sends an SNMP trap notification.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# interface type number | Places you into interface configuration mode for the specified interface. |
| Step 3 | switch(config-if)# [no] switchport port-security violation {protect | restrict | shutdown} |
Configures the security violation action for port security on the current interface. The no option resets the violation action to the default, which is to shut down the interface. The keywords are as follows:
|
| Step 4 | switch(config-if)# show port-security address interface vethernet number | Displays the secure MAC address learnt on the interface. |
| Step 5 | switch(config-if)# show port-security interface vethernet number | Displays the port security configuration on the interface. |
| Step 6 | switch(config-if)# show running-config port-security | (Optional) Displays the port security configuration. |
| Step 7 | switch(config-if)# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure a security violation action:
switch(config-if)# show running-config port-security interface Vethernet36 switchport port-security switchport port-security violation protect switch(config-if)# interface Vethernet36 switch(config-if)# switchport port-security switch(config-if)# switchport port-security violation protect switch(config-if)# show port-security interface vethernet 36 Port Security : Enabled Port Status : Secure UP Violation Mode : Protect Aging Time : 0 mins Aging Type : Absolute Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Security violation count : 0
Recovering Ports Disabled for Port Security Violations
You can automatically recover an interface disabled for port security violations. To recover an interface manually from the error-disabled state, you must enter the shutdown command and then the no shutdown command.
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# interface type number | Places you into interface configuration mode for the specified interface. |
| Step 3 | switch(config-if)# errdisable recovery cause psecure-violation |
Enables a timed automatic recovery of the specified port that is disabled for a port security violation. |
| Step 4 | switch(config-if)# errdisable recovery interval seconds | Configures a timer recovery interval in seconds from 30 to 65535 seconds. |
This example shows how to recover ports that are disabled for port security violations:
switch# configure terminal switch(config)# interface vethernet 36 switch(config-if)# errdisable recovery cause psecure-violation switch(config-if)# errdisable recovery interval 30 switch(config-if)# copy running-config startup-config switch(config-if)# show errdisable recovery ErrDisable Reason Timer Status ----------------- ------------ link-flap disabled dhcp-rate-limit disabled arp-inspection disabled security-violation disabled psecure-violation enabled failed-port-state enabled ip-addr-conflict disabled Timer interval: 30
Verifying the Port Security Configuration
Use the following commands to verify the configuration:
Command |
Purpose |
|---|---|
show running-config port-security |
Displays the port security configuration. |
show port-security |
Displays the port security status. |
show port-security address interface vethernet number |
Displays the secure MAC address learnt on the interface. |
show port-security interface vethernet number |
Displays the port security configuration on the interface. |
Displaying Secure MAC Addresses
Use the show port-security address command to display secure MAC addresses.
Use the show port-security address interface vethernet id command to display all secured MAC addresses on that interface.
Configuration Example for Port Security
This example shows a port security configuration for the vEthernet 36 interface with a VLAN and interface maximums for secure addresses. In this example, the interface is a trunk port. Additionally, the violation action is set to Protect.
switch# config terminal switch(config)# interface vethernet 36 switch(config-if)# switchport port-security switch(config-if))# switchport port-security maximum 10 switch(config-if))# switchport port-security maximum 7 vlan 10 switch(config-if))# switchport port-security maximum 3 vlan 20 switch(config-if))# switchport port-security violation protect switch(config-if))# switchport mode trunk switch(config-if)# show running-config interface vethernet 36 switchport port-security switchport port-security maximum 10 switchport port-security maximum 7 vlan 10 switchport port-security maximum 3 vlan 20 switchport port-security violation protect switchport mode trunk
The following example shows a port securtiy configuration for the vEthernet 40 interface as an access port with an interface maximum set to 20, a violation set to restrict, an absolute timeout of 1 minute and a port security static MAC address of 0000.1111.5555:
switch# config terminal switch(config)# interface vethernet 40 switch(config-if)# switchport port-security aging time 1 switch(config-if)# switchport port-security aging type absolute switch(config-if)# switchport port-security switch(config-if)# switchport port-security maximum 20 switch(config-if)# switchport port-security mac-address 0000.1111.5555 switch(config-if)# switchport port-security violation restrict switch(config-if)# show running-config interface vethernet 40 switchport port-security aging time 1 switchport port-security aging type absolute switchport port-security switchport port-security maximum 20 switchport port-security mac-address 0000.1111.5555 switchport port-security violation restrict switch(config-if)# show port-security interface vethernet 40 Port Security : Enabled Port Status : Secure UP Violation Mode : Restrict Aging Time : 1 mins Aging Type : Absolute Maximum MAC Addresses : 20 Total MAC Addresses : 2 Configured MAC Addresses : 1 Sticky MAC Addresses : 0 Security violation count : 0
This example shows a port security configuration for the vEthernet 42 interface as an access port with a violation set to shutdown and MAC address learning set to sticky:
switch# config terminal switch(config)# interface vethernet 42 switch(config-if)# switchport port-security switch(config-if)# switchport port-security mac-address sticky switch(config-if)# switchport port-security violation shutdown switch(config-if)# show running-config interface vethernet 42 switchport port-security switchport port-security mac-address sticky switchport port-security violation shutdown switch(config-if)# show port-security interface vethernet 42 Port Security : Enabled Port Status : Secure UP Violation Mode : Shutdown Aging Time : 0 mins Aging Type : Absolute Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 1 Security violation count : 0 switch(config-if)# show port-security address interface vethernet 42 Secure Mac Address Table ---------------------------------------------------------------------- Vlan Mac Address Type Ports Configured Age (mins) ---- ----------- ------ ----- --------------- 2303 0050.5687.3C68 STICKY Vethernet42 0 ----------------------------------------------------------------------
Feature History for Port Security
This table only includes updates for those releases that have resulted in additions to the feature.
Feature Name |
Releases |
Feature Information |
|---|---|---|
Port Security |
4.0(4)SV1(1) |
This feature was introduced. |