- Preface
- New and Changed Information
- Overview
- Managing User Accounts
- Configuring VSD
- Configuring AAA
- Configuring RADIUS
- Configuring TACACS+
- Configuring SSH
- Configuring Telnet
- Configuring IP ACLs
- Configuring MAC ACLs
- Configuring Port Security
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring IP Source Guard
- Disabling the HTTP Server
- Blocking Unknown Unicast Flooding
- Configuring Cisco TrustSec
- Index
Cisco Nexus 1000V Security Configuration Guide, Release 4.2(1)SV2(2.1)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- March 4, 2015
Chapter: Configuring RADIUS
Contents
- Configuring RADIUS
- Information About RADIUS
- RADIUS Network Environments
- RADIUS Operation
- RADIUS Server Monitoring
- Vendor-Specific Attributes
- Prerequisites for RADIUS
- Guidelines and Limitations
- Default Settings
- Configuring RADIUS Servers
- Configuring RADIUS Server Hosts
- Configuring the Global RADIUS Key
- Configuring a RADIUS Server Key
- Configuring RADIUS Server Groups
- Enabling RADIUS Server-Directed Requests
- Setting a Global Timeout for All RADIUS Servers
- Configuring a Global Retry Count for All RADIUS Servers
- Setting a Timeout Interval for a Single RADIUS Server
- Configuring Retries for a Single RADIUS Server
- Configuring a RADIUS Accounting Server
- Configuring a RADIUS Authentication Server
- Configuring Periodic RADIUS Server Monitoring
- Configuring the Global Dead-Time Interval
- Manually Monitoring RADIUS Servers or Groups
- Verifying the RADIUS Configuration
- Displaying RADIUS Server Statistics
- Configuration Example for RADIUS
- Feature History for RADIUS
Configuring RADIUS
This chapter contains the following sections:
- Information About RADIUS
- Prerequisites for RADIUS
- Guidelines and Limitations
- Default Settings
- Configuring RADIUS Servers
- Verifying the RADIUS Configuration
- Displaying RADIUS Server Statistics
- Configuration Example for RADIUS
- Feature History for RADIUS
Information About RADIUS
The RADIUS distributed client/server system allows you to secure networks against unauthorized access. In the Cisco implementation, RADIUS clients run on Cisco NX-OS devices and send authentication and accounting requests to a central RADIUS server that contains all user authentication and network service access information.
RADIUS Network Environments
RADIUS can be implemented in a variety of network environments that require high levels of security while maintaining network access for remote users.
You can use RADIUS in the following network environments that require access security:
Networks with multiple-vendor network devices, each supporting RADIUS. For example, network devices from several vendors can use a single RADIUS server-based security database.
Networks already using RADIUS. You can add a Cisco NX-OS device with RADIUS to the network. This action might be the first step when you make a transition to a AAA server.
Networks that require resource accounting. You can use RADIUS accounting independent of RADIUS authentication or authorization. The RADIUS accounting functions allow data to be sent at the start and end of services, indicating the amount of resources (such as time, packets, bytes, and so on) used during the session. An Internet service provider (ISP) might use a freeware-based version of the RADIUS access control and accounting software to meet special security and billing needs.
Networks that support authentication profiles. Using the RADIUS server in your network, you can configure AAA authentication and set up per-user profiles. Per-user profiles enable the Cisco NX-OS device to better manage ports using their existing RADIUS solutions and to efficiently manage shared resources to offer different service-level agreements.
RADIUS Operation
When a user attempts to log in and authenticate to a Cisco NX-OS device using RADIUS, the following occurs:
The user is prompted for and enters a username and password.
The username and encrypted password are sent over the network to the RADIUS server.
The user receives one of the following responses from the RADIUS server:
ACCEPT—The user is authenticated.
REJECT—The user is not authenticated and is prompted to reenter the username and password, or access is denied.
CHALLENGE—A challenge is issued by the RADIUS server. The challenge collects additional data from the user.
CHANGE PASSWORD—A request is issued by the RADIUS server, asking the user to select a new password.
The ACCEPT or REJECT response is bundled with additional data that is used for EXEC or network authorization. You must first complete RADIUS authentication before using RADIUS authorization. The additional data included with the ACCEPT or REJECT packets consists of the following:
RADIUS Server Monitoring
An unresponsive RADIUS server can cause a delay in processing AAA requests. You can periodically monitor a RADIUS server to check whether it is responding (or alive) to save time in processing AAA requests. Unresponsive RADIUS servers are marked as dead and are not sent AAA requests. Dead RADIUS servers are periodically monitored and returned to the alive state once they respond. This monitoring process verifies that a RADIUS server is in a working state before real AAA requests are sent its way. Whenever a RADIUS server changes to the dead or alive state, a Simple Network Management Protocol (SNMP) trap is generated and an error message is displayed indicating that a failure is taking place.
 Note | The monitoring interval for alive servers and dead servers are different and can be configured by the user. The RADIUS server monitoring is performed by sending a test authentication request to the RADIUS server. |
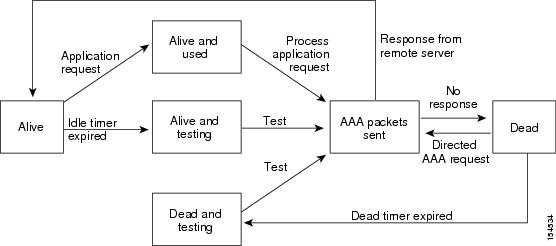
Vendor-Specific Attributes
The Internet Engineering Task Force (IETF) draft standard specifies a method for communicating vendor-specific attributes (VSAs) between the network access server and the RADIUS server. The IETF uses attribute 26. VSAs allow vendors to support their own extended attributes that are not suitable for general use. The Cisco RADIUS implementation supports one vendor-specific option using the format recommended in the specification. The Cisco vendor ID is 9, and the supported option is vendor type 1, which is named cisco-av-pair. The value is a string with the following format:
protocol : attribute separator value *
The protocol is a Cisco attribute for a particular type of authorization. The separator is = (equal sign) for mandatory attributes and * (asterisk) indicates optional attributes.
When you use RADIUS servers for authentication, the RADIUS protocol directs the RADIUS server to return user attributes, such as authorization information, with authentication results. This authorization information is specified through VSAs.
The following VSA protocol options are supported:
Shell—Protocol used in access-accept packets to provide user profile information.
Accounting—Protocol used in accounting-request packets. If a value contains any white spaces, you should enclose the value within double quotation marks.
The following attributes are supported:
roles—Lists all the roles to which the user belongs. The value field is a string that lists the role names delimited by white space. For example, if the user belongs to roles network-operator and vdc-admin, the value field would be “network-operator vdc-admin.” This attribute, which the RADIUS server sends in the VSA portion of the Access-Accept frames, can be only used with the shell protocol value. The following examples show the roles attribute as supported by Cisco Access Control System (ACS):
shell:roles=“network-operator vdc-admin” shell:roles*“network-operator vdc-admin”
The following examples show the roles attribute as supported by FreeRADIUS:
Cisco-AVPair = ”shell:roles=\“network-operator vdc-admin\”” Cisco-AVPair = “shell:roles*\“network-operator vdc-admin\””
If you are using Cisco ACS and intend to use the same ACS group for both Cisco Nexus 1000V and Cisco UCS authentication, use the following roles attribute:
cisco-av-pair*shell:roles="network-admin admin"

NoteWhen you specify a VSA as shell:roles*"network-operator vdc-admin" or "shell:roles*\"network-operator vdc-admin\"", this VSA is flagged as an optional attribute and other Cisco devices ignore this attribute.
accountinginfo—Stores accounting information in addition to the attributes covered by a standard RADIUS accounting protocol. This attribute is sent only in the VSA portion of the Account-Request frames from the RADIUS client on the switch. It can be used only with the accounting protocol data units (PDUs).
Prerequisites for RADIUS
Guidelines and Limitations
You can configure a maximum of 64 RADIUS servers.
Default Settings
Parameters |
Default |
|---|---|
Server roles |
Authentication and accounting |
Dead timer interval |
0 minutes |
Retransmission count |
1 |
Retransmission timer interval |
5 seconds |
Idle timer interval |
0 minutes |
Periodic server monitoring username |
test |
Periodic server monitoring password |
test |
Configuring RADIUS Servers
Configuring RADIUS Server Hosts
You can configure the IP address or the hostname for each RADIUS server to be used for authentication. You should know the following information:
Log in to the CLI in EXEC mode.
This example shows how to configure a RADIUS server host:
switch# configure terminal switch(config)# radius-server host 10.10.1.1 switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring the Global RADIUS Key
You can configure the key that is used by all RADIUS servers to authenticate with the Cisco Nexus 1000V.
This example shows how to configure a global RADIUS key:
switch# configure terminal switch(config)# radius-server key 0 QsEfThUkO switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring a RADIUS Server Key
You can configure a key for a single RADIUS server host.
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. | ||
| Step 2 | switch(config)# radius-server host {ipv4-address | host-name} key [0 | 7] key-value | Specifies a preshared key for a specific RADIUS server. You can specify a clear text (0) or encrypted (7) preshared key. The default format is clear text. The maximum length is 63 characters. | ||
| Step 3 | switch(config)# exit | Returns you to EXEC mode. | ||
| Step 4 | switch# show radius-server | (Optional) Displays the RADIUS server configuration.
| ||
| Step 5 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure a RADIUS server key:
switch# configure terminal switch(config)# radius-server host 10.10.1.1 key 0 PlIjUhYg switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring RADIUS Server Groups
You can configure a RADIUS server group whose member servers share authentication functions.
The servers in the group are tried in the same order in which you configure them
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. | ||
| Step 2 | switch(config)# aaa group server radius group-name | Creates a RADIUS server group and enters the RADIUS server group configuration mode for that group. The group-name argument is a case-sensitive alphanumeric string with a maximum length of 127 characters. | ||
| Step 3 | switch(config-radius)# server {ipv4-address | server-name} | Configures the RADIUS server as a member of the RADIUS server group.
| ||
| Step 4 | switch(config-radius)# deadtime minutes | (Optional) Configures the monitoring dead time. The default is 0 minutes. The range is from 1 through 1440.
| ||
| Step 5 | switch(config-radius)# use-vrf vrf-name | (Optional) Specifies the VRF to use to contact the servers in the server group | ||
| Step 6 | switch(config-radius)# source-interface {interface-type} {interface-number} | (Optional) Specifies a source interface to be used to reach the RADIUS server. The interface types and interface numbers are defines as follows: | ||
| Step 7 | switch(config-radius)# show radius-server groups [group-name] | (Optional) Displays the RADIUS server group configuration. | ||
| Step 8 | switch(config-radius)# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration |
This example shows how to configure a RADIUS server group:
switch# configure terminal
switch(config)# aaa group server radius RadServer
switch(config-radius)# server 10.10.1.1
switch(config-radius)# deadtime 30
switch(config-radius)# use-vrf vrf1
switch(config-radius)# source-interface mgmt0
switch(config-radius)# show radius-server group
total number of groups:2
following RADIUS server groups are configured:
group Radserver:
server: 10.10.1.1
deadtime is 30
group test:
deadtime is 30
switch(config-radius)# copy running-config startup-config
Enabling RADIUS Server-Directed Requests
You can allow users to designate the RADIUS server to send their authentication request to. This process is called a directed request.
If you enable this option, a user can log in as username@vrfname:hostname, where vrfname is the virtual routing and forwarding (VRF) to use and hostname is the name of a configured RADIUS server.
Directed requests are disabled by default.
 Note | User-specified logins are supported only for Telnet sessions. |
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# radius-server directed-request | Enables directed requests. The default is disabled. |
| Step 3 | switch(config)# exit | Returns to EXEC mode. |
| Step 4 | switch(config)# show radius-server directed-request | (Optional) Displays the directed request configuration. |
| Step 5 | switch(config)# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to enable a RADIUS server-directed request:
switch# configure terminal switch(config)# radius-server directed-request switch(config)# exit switch# show radius-server directed-request switch# copy running-config startup-config
Setting a Global Timeout for All RADIUS Servers
You can configure the global timeout interval that specifies how long to wait for a response from a RADIUS server before declaring a timeout failure.
The timeout specified in the “Setting the Timeout Interval for a Single RADIUS Server” section overrides the global RADIUS timeout.
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# radius-server timeout seconds |
Specifies the transmission timeout interval for RADIUS servers. The default timeout interval is 5 seconds and the allowable range is from 1 to 60 seconds. |
| Step 3 | switch(config-radius)# exit | Returns you to EXEC mode. |
| Step 4 | switch(config-radius)# show radius-server | (Optional) Displays the RADIUS server configuration. |
| Step 5 | switch(config-radius)# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
switch# configure terminal switch(config)# radius-server timeout 101 switch(config-radius)# exit switch(config-radius)# show radius-server switch(config-radius)# copy running-config startup-config
Configuring a Global Retry Count for All RADIUS Servers
You can configure the maximum number of times to retry transmitting to a RADIUS server before reverting to local authentication.This setting is applied to all RADIUS servers.
By default, retransmission to a RADIUS server is only tried once before reverting to local authentication.
You can increase the number of retries up to a maximum of five.
The retry count specified for a single RADIUS server in the “Configuring Retries for a Single RADIUS Server” section, overrides this global setting.
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# radius-server retransmitcount |
Defines the number of retransmits allowed before reverting to local authentication. This global setting applies to all RADIUS servers. The default number of retransmits is 1 and the range is from 0 to 5. |
| Step 3 | switch(config)# exit | Returns you to EXEC mode. |
| Step 4 | switch# show radius-server | (Optional) Displays the RADIUS server configuration |
| Step 5 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure a global retry count for all RADIUS servers:
switch# configure terminal switch(config)# radius-server retransmit 31 switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Setting a Timeout Interval for a Single RADIUS Server
You can configure how long to wait for a response from a RADIUS server before declaring a timeout failure.
The timeout specified for a single RADIUS server overrides the timeout defined in the “Setting the Global Timeout for All RADIUS Servers” section.
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. | ||
| Step 2 | switch(config)# radius-server host {ipv4-address |host-name}timeout seconds |
Specifies the timeout interval for the specified server. The default timeout interval is 5 seconds and the allowable range is from 1 to 60 seconds.
| ||
| Step 3 | switch(config)# exit | Returns you to EXEC mode. | ||
| Step 4 | switch# show radius-server | (Optional) Displays the RADIUS server configuration. | ||
| Step 5 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to set a timeout interval for a single RADIUS server:
switch# configure terminal switch(config)# radius-server host server1 timeout 10 switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring Retries for a Single RADIUS Server
You can configure the maximum number of times to retry transmitting to a RADIUS server before reverting to local authentication.This setting applies to a single RADIUS server and takes precedence over the global retry count.
Log in to the CLI in EXEC mode.
You should know the following:
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. | ||
| Step 2 | switch(config)# radius-server host {ipv4-address | host-name} retransmit count |
Specifies the retransmission count for a specific server. The default is the global value.
| ||
| Step 3 | switch(config)# exit | Returns you to EXEC mode. | ||
| Step 4 | switch# show radius-server | (Optional) Displays the RADIUS server configuration | ||
| Step 5 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure retries for a single RADIUS server:
switch# configure terminal switch(config)# radius-server host server1 retransmit 3 switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring a RADIUS Accounting Server
You can configure a server to perform accounting functions.
By default, RADIUS servers are used for both accounting and authentication.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# radius-server host {ipv4-address | host-name} acct-port udp-port | (Optional)
Associates a specific host with the UDP port that receives RADIUS accounting messages. The default UDP port is 1812. The range is from 0 to 65535. |
| Step 3 | switch(config)# radius-server host {ipv4-address | host-name} accounting | (Optional) Designates the specific RADIUS host as an accounting server. The default is both accounting and authentication. |
| Step 4 | switch(config)# exit | Returns you to EXEC mode. |
| Step 5 | switch# show radius-server | (Optional) Displays the RADIUS server configuration. |
| Step 6 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure a RADIUS accounting server:
switch# configure terminal switch(config)# radius-server host 10.10.1.1 acct-port 2004 switch(config)# radius-server host 10.10.1.1 accounting switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring a RADIUS Authentication Server
You can configure a server to perform authentication functions.
By default, RADIUS servers are used for both accounting and authentication.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# radius-server host {ipv4-address | hostname} auth-port udp-port | (Optional)
Associates a specific host with the UDP port that receives RADIUS authentication messages. The default UDP port is 1812. The range is from 0 to 65535. |
| Step 3 | switch(config)# radius-server host {ipv4-address | host-name} authentication | (Optional) Designates the specific RADIUS host as an authentication server. The default is both accounting and authentication. |
| Step 4 | switch(config)# exit | Returns you to EXEC mode. |
| Step 5 | switch# show radius-server | (Optional) Displays the RADIUS server configuration. |
| Step 6 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure a RADIUS authentication server:
switch# configure terminal switch(config)# radius-server host 10.10.2.2 auth-port 2005 switch(config)# radius-server host 10.10.2.2 authentication switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring Periodic RADIUS Server Monitoring
You can configure the monitoring of RADIUS servers.
The test idle timer specifies the interval of time that elapses before a test packet is sent to a nonresponsive RADIUS server.
The default idle timer value is 0 minutes. When the idle time interval is 0 minutes, the Cisco NX-OS device does not perform periodic RADIUS server monitoring.
 Note | For security reasons, do not configure a username that is in the RADIUS database as a test username. |
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. | ||
| Step 2 | switch(config)# radius-server host {ipv4-address | host-name} test {idle-time minutes | password password [idle-time minutes ] | username name [password password [idle-timeminutes]]} |
Specifies parameters for server monitoring. The default username is test and the default password is test. The default value for the idle timer is 0 minutes. The valid range is from 0 to 1440 minutes.
| ||
| Step 3 | switch(config)# radius-server dead-time minutes | Specifies the number of minutes to wait before sending a test packet to a RADIUS server that was declared dead. The default value is 0 minutes. The valid range is 1 to 1440 minutes. | ||
| Step 4 | switch(config)# exit | Returns you to EXEC mode. | ||
| Step 5 | switch# show radius-server | (Optional) Displays the RADIUS server configuration. | ||
| Step 6 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure periodic RADIUS server monitoring:
switch# configure terminal switch(config)# radius-server host 10.10.1.1 test username user1 password Ur2Gd2BH idle-time 3 switch(config)# radius-server dead-time 5 switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Configuring the Global Dead-Time Interval
You can configure the dead-time interval for all RADIUS servers. The dead-time interval specifies the time to wait after declaring a RADIUS server dead, before sending out a test packet to determine if the server is now alive. The default value is 0 minutes
 Note | When the dead-time interval is 0 minutes, RADIUS servers are not marked as dead even if they are not responding. You can configure the dead-time interval for a RADIUS server group. |
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch(config)# radius-server deadtime minutes |
Configures the dead-time interval. The default value is 0 minutes. The range is from 1 to 1440 minutes. |
| Step 3 | switch(config)# exit | Returns you to EXEC mode. |
| Step 4 | switch# show radius-server | (Optional) Displays the RADIUS server configuration. |
| Step 5 | switch# copy running-config startup-config | (Optional) Copies the running configuration to the startup configuration. |
This example shows how to configure the global dead-time interval:
switch# configure terminal switch(config)# radius-server deadtime 5 switch(config)# exit switch# show radius-server switch# copy running-config startup-config
Manually Monitoring RADIUS Servers or Groups
You can manually send a test message to a RADIUS server or to a server group.
Log in to the CLI in EXEC mode.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal | Enters global configuration mode. |
| Step 2 | switch# test aaa server radius {ipv4-address | server-name} [vrf vrf-name] username password |
Sends a test message to a RADIUS server to confirm availability. |
| Step 3 | switch(config)# test aaa group group-name username password | Sends a test message to a RADIUS server group to confirm availability. |
This example shows how to manually monitor a RADIUS server or group:
switch# configure terminal switch# test aaa server radius 10.10.1.1 user1 Ur2Gd2BH switch# test aaa group RadGroup user2 As3He3CI
Verifying the RADIUS Configuration
Use the following commands to verify the configuration.
Command |
Purpose |
|---|---|
show running-config radius [all] |
Displays the RADIUS configuration in the running configuration. |
show startup-config radius |
Displays the RADIUS configuration in the startup configuration. |
show radius-server [server-name | ipv4-address] [directed-request | groups | sorted | statistics] |
Displays all configured RADIUS server parameters. |
Displaying RADIUS Server Statistics
Use the following command to display statistics for RADIUS server activity:
show radius-server statistics { hostname | ipv4-address }Configuration Example for RADIUS
This example shows how to configure a global RADIUS key and a RADIUS server host key:
switch# configure terminal
switch(config)# radius-server key 7 "ToIkLhPpG"
switch(config)# radius-server host 10.10.1.1 key 7 "ShMoMhTl" authentication accounting
switch(config)# aaa group server radius RadServer
server 10.10.1.1
Feature History for RADIUS
This table only includes updates for those release that have resulted in additions to the feature.
Feature Name |
Releases |
Feature Information |
|---|---|---|
RADIUS |
4.0(4)SV1(1) |
This feature was introduced. |