GRE Tunnel with VRF Configuration Example
Available Languages
Contents
Introduction
This document provides a sample configuration for a VPN routing and forwarding (VRF) instance under a generic routing encapsulation (GRE) tunnel interface.
Prerequisites
Requirements
Before you attempt this configuration, ensure that you meet these requirements:
Readers of this document should have knowledge of these topics:
Components Used
The information in this document is based on Cisco IOS® Software Release 12.3(4)T1 on 3725 Series routers.
Use Cisco Feature Navigator II (registered customers only) and search for the GRE Tunnel IP Source and Destination VRF Membership feature, to obtain additional software and hardware requirements that you need.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
For more information on document conventions, refer to the Cisco Technical Tips Conventions.
Configure
In this section, you are presented with the information to configure the features described in this document.
The configuration is set up in this way:
-
R1-CE and R2-CE are located in VRF BLUE.
-
R1-CE is also located in VRF GREEN through the use of a GRE tunnel to R3-PE.
R1-CE uses a static host route to get to R3-PE (tunnel destination), which ensures that recursive routing does not occur for the GRE tunnel (learning the tunnel destination address through the tunnel).
VRF BLUE and VRF GREEN are owned by two different companies, and no route leaks occur between them. In addition, the access control list (ACL) on the interface between R1-CE and R2-CE can be used to only permit GRE traffic between them.
Note: To find additional information on the commands used in this document, use the Command Lookup Tool (registered customers only) .
Network Diagram
This document uses this network setup:
Figure 1 – Physical Topology 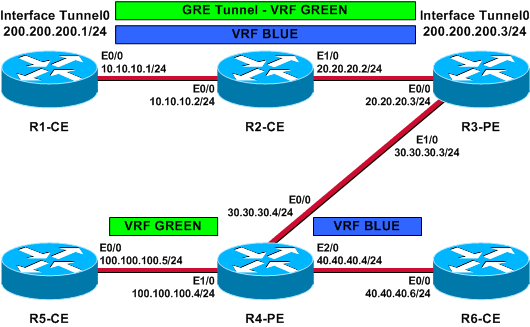
Configurations
This document uses these configurations:
| R3-PE (Tunnel Endpoint) |
|---|
R3-PE# show running-config Building configuration... . ! no ip domain lookup ! ip vrf blue rd 1:1 route-target export 311:311 route-target import 411:411 ! ip vrf green rd 2:2 route-target export 322:322 route-target import 422:422 ! ip cef ! interface Tunnel0 ip vrf forwarding green ip address 200.200.200.3 255.255.255.0 tunnel source Ethernet0/0 tunnel destination 10.10.10.1 tunnel vrf blue !--- Tunnel 0 is part of VRF GREEN; but it uses the tunnel !--- destination and source addresses from the routing !--- table of VRF BLUE, because of this tunnel vrf blue !--- command. ! interface Ethernet0/0 ip vrf forwarding blue ip address 20.20.20.3 255.255.255.0 !--- Connection to the VRF BLUE network and the VRF GREEN !--- network using the GRE tunnel. ! interface Ethernet1/0 ip address 30.30.30.3 255.255.255.0 tag-switching ip ! router bgp 1 no bgp default ipv4-unicast bgp log-neighbor-changes neighbor 30.30.30.4 remote-as 1 ! address-family vpnv4 neighbor 30.30.30.4 activate neighbor 30.30.30.4 send-community extended exit-address-family ! address-family ipv4 vrf green redistribute connected no auto-summary no synchronization exit-address-family ! address-family ipv4 vrf blue redistribute connected no auto-summary no synchronization exit-address-family ! ip classless ip route vrf blue 10.10.10.1 255.255.255.255 20.20.20.2 !--- Static Host route to ensure that recursive routing !--- does not occur. no ip http server ! . end |
| R4-PE |
|---|
R4-PE# show running-config Building configuration... . . . no ip domain lookup ! ip vrf blue rd 1:1 route-target export 411:411 route-target import 311:311 ! ip vrf green rd 2:2 route-target export 422:422 route-target import 322:322 ! ip cef ! interface Ethernet0/0 ip address 30.30.30.4 255.255.255.0 tag-switching ip ! interface Ethernet1/0 ip vrf forwarding green ip address 100.100.100.4 255.255.255.0 ! interface Ethernet2/0 ip vrf forwarding blue ip address 40.40.40.4 255.255.255.0 ! router bgp 1 no bgp default ipv4-unicast bgp log-neighbor-changes neighbor 30.30.30.3 remote-as 1 ! address-family vpnv4 neighbor 30.30.30.3 activate neighbor 30.30.30.3 send-community extended exit-address-family ! address-family ipv4 vrf green redistribute connected no auto-summary no synchronization exit-address-family ! address-family ipv4 vrf blue redistribute connected no auto-summary no synchronization exit-address-family ! ip classless . . end |
| R1-CE (Tunnel Endpoint) |
|---|
R1-CE# show running-config Building configuration... . . no ip domain lookup ! ip cef ! interface Tunnel0 ip address 200.200.200.1 255.255.255.0 tunnel source Ethernet0/0 tunnel destination 20.20.20.3 !--- Both the tunnel source and destination address are in !--- the VRF BLUE, to provide transport for the VRF GREEN !--- network. ! interface Ethernet0/0 description Connection to R2-CE router ip address 10.10.10.1 255.255.255.0 ip access-group 100 in ip access-group 100 out !--- Access-group to allow only GRE packets through the !--- R2-CE network. However, R1-CE networks data is in the !--- GRE packet. ! ! ip classless ip route 0.0.0.0 0.0.0.0 Tunnel0 ip route 20.20.20.3 255.255.255.255 10.10.10.2 !--- Static Host route to ensure that recursive routing !--- does not occur. no ip http server ! access-list 100 permit gre host 10.10.10.1 host 20.20.20.3 access-list 100 permit gre host 20.20.20.3 host 10.10.10.1 !--- Permits only GRE packets between the endpoints. ! . . end |
| R2-CE |
|---|
R2-CE# show running-config Building configuration... . . no ip domain lookup ! ip cef ! interface Ethernet0/0 description Connection to R1-CE router ip address 10.10.10.2 255.255.255.0 ip access-group 100 in ip access-group 100 out ! interface Ethernet1/0 ip address 20.20.20.2 255.255.255.0 ! ip classless ip route 0.0.0.0 0.0.0.0 20.20.20.3 no ip http server ! access-list 100 permit gre host 10.10.10.1 host 20.20.20.3 access-list 100 permit gre host 20.20.20.3 host 10.10.10.1 !--- Permits only GRE packets between the endpoints. . ! end |
| R5-CE |
|---|
R5-CE# show running-config Building configuration... . . no ip domain lookup ! interface Ethernet0/0 ip address 100.100.100.5 255.255.255.0 ! ! ip classless ip route 0.0.0.0 0.0.0.0 100.100.100.4 no ip http server ! . end |
| R6-CE |
|---|
R6-CE# show running-config Building configuration... . . no ip domain lookup ! interface Ethernet0/0 ip address 40.40.40.6 255.255.255.0 ! ! ip classless ip route 0.0.0.0 0.0.0.0 40.40.40.4 no ip http server ! . end |
Verify
This section provides information you can use to confirm your configuration is working properly.
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
-
show ip route , show ip route vrf —Issue these commands on the tunnel end points to ensure that the tunnel destination is reachable. This ensures that the tunnel interface will come up.
-
ping —Issue this command from the other end of the CE to ensure that the tunnels are reachable from the CE.
-
show ip bgp vpnv4 all labels —Issue this command on the PE devices to view the VPN labels distributed for each prefix via Border Gateway Protocol (BGP) to other PE devices.
R3-PE# show ip route vrf blue 10.10.10.1
Routing entry for 10.10.10.1/32
Known via "static", distance 1, metric 0
Routing Descriptor Blocks:
* 20.20.20.2
Route metric is 0, traffic share count is 1
R3-PE# show ip route vrf green
Routing Table: green
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 200.200.200.0/24 is directly connected, Tunnel0
100.0.0.0/24 is subnetted, 1 subnets
B 100.100.100.0 [200/0] via 30.30.30.4, 01:11:45
R3-PE# show interfaces tunnel 0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 200.200.200.3/24
MTU 1514 bytes, BW 9 Kbit, DLY 500000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 20.20.20.3 (Ethernet0/0), destination 10.10.10.1
Tunnel protocol/transport GRE/IP, key disabled, sequencing disabled
Tunnel TTL 255
Checksumming of packets disabled, fast tunneling enabled
Last input 00:44:05, output 00:26:16, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
105 packets input, 11964 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
83 packets output, 10292 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 output buffer failures, 0 output buffers swapped out
R3-PE# show ip bgp vpnv4 all labels
Network Next Hop In label/Out label
Route Distinguisher: 1:1 (blue)
20.20.20.0/24 0.0.0.0 16/aggregate(blue)
Route Distinguisher: 2:2 (green)
100.100.100.0/24 30.30.30.4 nolabel/16
200.200.200.0 0.0.0.0 17/aggregate(green)
R4-PE# show ip route vrf blue
Routing Table: blue
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
20.0.0.0/24 is subnetted, 1 subnets
B 20.20.20.0 [200/0] via 30.30.30.3, 01:14:05
R4-PE# show ip route vrf green
Routing Table: green
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
B 200.200.200.0/24 [200/0] via 30.30.30.3, 01:14:10
100.0.0.0/24 is subnetted, 1 subnets
C 100.100.100.0 is directly connected, Ethernet1/0
R1-CE# show ip route 20.20.20.3
Routing entry for 20.20.20.3/32
Known via "static", distance 1, metric 0
Routing Descriptor Blocks:
* 10.10.10.2
Route metric is 0, traffic share count is 1
R1-CE# show interfaces tunnel 0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 200.200.200.1/24
MTU 1514 bytes, BW 9 Kbit, DLY 500000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 10.10.10.1 (Ethernet0/0), destination 20.20.20.3
Tunnel protocol/transport GRE/IP, key disabled, sequencing disabled
Tunnel TTL 255
Checksumming of packets disabled, fast tunneling enabled
Last input 00:26:57, output 00:26:57, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
83 packets input, 10292 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
106 packets output, 12088 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 output buffer failures, 0 output buffers swapped out
R5-CE# ping 200.200.200.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.200.200.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/54/80 ms
R5-CE# ping 200.200.200.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.200.200.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/36/72 ms
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Caveats
These known caveats are identified for the configuration of this feature. You can use the Bug Toolkit (registered customers only) to search for bugs.
-
CSCea81266 (registered customers only) —Resolved (R) GRE: Traffic stops flowing after clear ip route *.
-
CSCdx74855 (registered customers only) —Resolved (R) Can not ping IP address of local GRE tunnel interface.
-
CSCdx57718 (registered customers only) —Resolved (R) IP packet loss in GRE tunnel when Cisco Express Forwarding (CEF) disabled on outgoing interface.
Related Information
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback