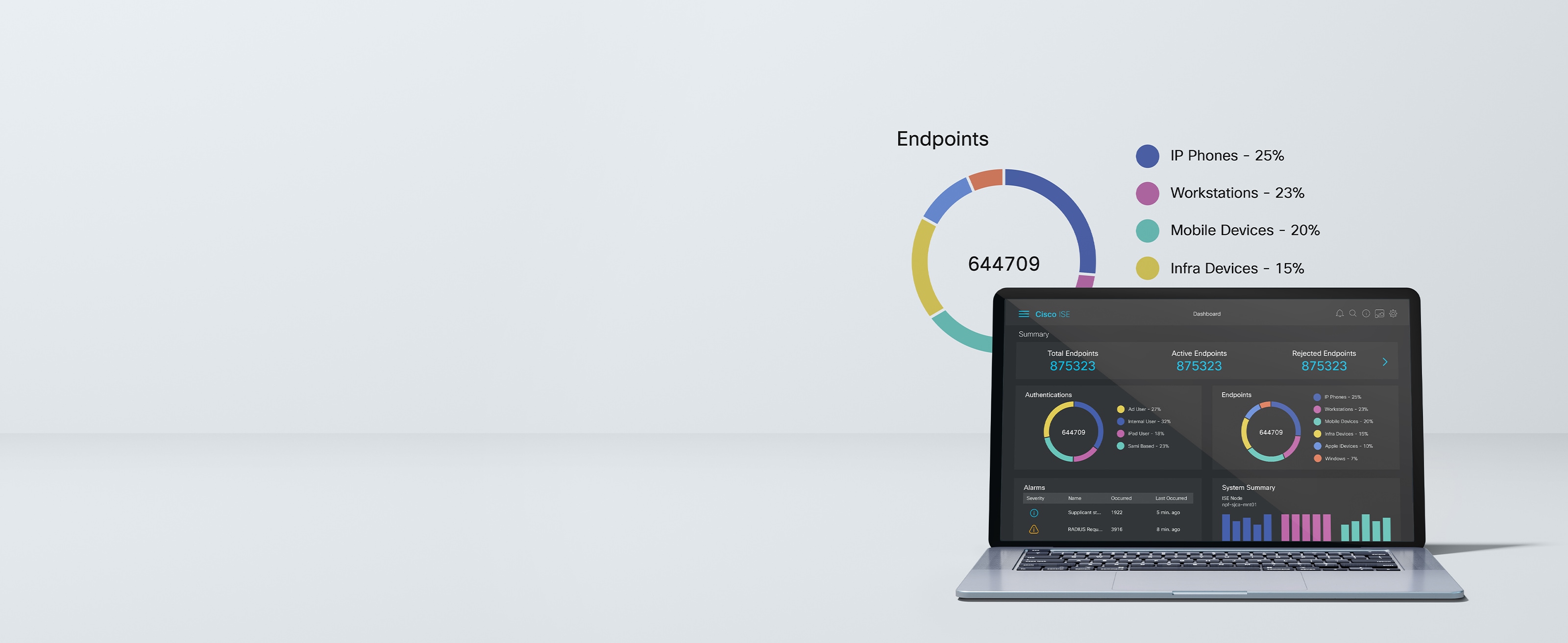
In zero-trust architecture, Cisco Identity Services Engine (ISE) is the policy decision point. It gathers intel from the stack to authenticate users and endpoints, automatically containing threats.
Cisco ISE 3.4 is ready for your network
Cisco ISE 3.4, our latest version, provides your network with operational flexibility, increased security, and cohesiveness with intelligent insights.
Harness the power of resilience
Resilience begins with secure connections. Cisco ISE allows only trusted users and devices access to resources on your network. It also uses intel to automatically identify, classify and profile devices.
Cisco ISE is the Common Policy hub
Common Policy provides users with the ability to send each domain the same user, endpoint and app context so that they have the flexibility to enforce policies on the domain of their choice.
Make a stand
Verify your device posture with Cisco ISE 3.x and see how easily it complies with your security policy. Cisco ISE works to protect your network, data, and resources from hostile attacks.
Unlock more value with solution integrations
Cisco Catalyst Center
Automate network management and secure access with Cisco Catalyst Center.
Cisco Software-Defined Access
Define and enforce device and access policies through effective segmentation to mitigate risks from unknown IoT devices.
Cisco Duo
Secure applications and enable frictionless access with strong multi-factor authentication (MFA) and more. Establish user and device trust, gain visibility into devices, and enable secure access to all apps.
Add value to security solutions
Cisco Security Enterprise Agreement
Instant savings
Experience security software buying flexibility with one easy-to-manage agreement.
Services for security
Let the experts secure your business
Get more from your investments and enable constant vigilance to protect your organization.