-
Cisco NAC Appliance - Clean Access Server Installation and Configuration Guide, Release 4.6(1)
-
About This Guide
-
Introduction
-
Planning Your Deployment
-
Configuring Layer 3 Out-of-Band
-
Installing the Clean Access Server NAC Appliance
-
Configuring the CAS Managed Network
-
Configuring DHCP
-
Integrating with Cisco VPN Concentrators
-
Local Traffic Control Policies
-
Configuring Active Directory Single Sign-On
-
Local Authentication Settings
-
Local Certified and Floating Devices
-
Administering the CAS
-
Configuring High Availability
-
Open Source License Acknowledgements
-
Index
-
Table Of Contents
Installing the Clean Access Server
Cisco NAC Appliance Hardware Platforms
Virtual Gateway Mode Connection Requirements
Switch Support for CAS Virtual Gateway/VLAN Mapping (IB and OOB)
Determining VLANs For Virtual Gateway
Summary of Steps For New Installation
Connect the Clean Access Server
Configuring Boot Settings on NAC-3310 Based Appliances
Install the Clean Access Server Software from CD-ROM
Perform the Initial Configuration
Important Notes for SSL Certificates
CAS CLI Commands for Cisco NAC Appliance
CAS CLI Commands for Cisco NAC Profiler
CAM/CAS Connectivity Across a Firewall
Configuring the CAS Behind a NAT Firewall
Configuring Additional NIC Cards
Troubleshooting the Installation
Network Interface Card (NIC) Driver Not Supported
Resetting the Clean Access Server Configuration
Installing the Clean Access Server
Note
The installation example and references in this chapter focus on Cisco NAC 3300 Series appliances. For Cisco NAC network module installation information, refer to Getting Started with Cisco NAC Network Modules in Cisco Access Routers and Installing Cisco Network Modules in Cisco Access Routers.
This chapter describes how to install and initially configure the Clean Access Server (CAS). Topics include:
•
Virtual Gateway Mode Connection Requirements
•
Summary of Steps For New Installation
•
Connect the Clean Access Server
•
Install the Clean Access Server Software from CD-ROM
•
Perform the Initial Configuration
•
CAM/CAS Connectivity Across a Firewall
•
Configuring the CAS Behind a NAT Firewall
•
Configuring Additional NIC Cards
•
Troubleshooting the Installation
Overview
When you receive a new Cisco NAC Appliance, you will need to connect to the appliance and perform initial configuration. If you want to install a different version of the software than what is shipped on the appliance, you can perform software installation via CD first. Refer to Supported Hardware and System Requirements for Cisco NAC Appliance (Cisco Clean Access) for details on the software versions supported on Cisco NAC Appliance 3300 Series platforms.
This chapter contains information for performing CD software installation and initial configuration of a Clean Access Server. With Cisco NAC Appliance software installation via CD, you must select whether to install the Clean Access Manager or Clean Access Server application. Once the CAM or CAS is installed on the appliance (application, OS, and relevant components), the installation of any other packages or applications on the CAM or CAS is not supported.
Note
Static IP addresses must be configured for the CAM/CAS interfaces. DHCP mode is not supported for configuration of these interfaces.
Cisco NAC Appliance Hardware Platforms
The Cisco NAC Appliance 3300 Series hardware platforms are Linux-based network hardware appliances which are pre-installed with either the CAM (MANAGER) or CAS (SERVER) application, the operating system, and all relevant components on a dedicated CAS machine. The operating system comprises a hardened Linux kernel based on a Fedora core. Cisco NAC Appliance does not support the installation of any other packages or applications onto a CAM or CAS dedicated machine.
Starting from Cisco NAC Appliance Release 4.5, Cisco NAC Appliance software only supports and can only be installed on the following Cisco NAC Appliance platforms:
•
Cisco CCA-3140
•
Cisco NAC-3310
•
Cisco NAC-3350
•
Cisco NAC-3390
•
Cisco NAC Network Module (NME-NAC-K9)
Note
Refer to the Release Notes for Cisco NAC Appliance, Version 4.6(1) for additional hardware compatibility information in Release 4.6(1).
The Cisco NAC Appliance 3300 Series provides Linux-based network hardware appliances which are pre-installed with either the CAM (MANAGER) or CAS (SERVER) application, the operating system and all relevant components on a dedicated server machine.
The Cisco NAC network module is a CAS you can install in a Cisco 2800 and 3800 Series ISR chassis that features all of the same features and functionality as a stand-alone CAS appliance with one exception; the Cisco NAC network module does not support high availability.
Note
For installation details on the Cisco NAC Network Module (CAS on a network module), refer to Getting Started with Cisco NAC Network Modules in Cisco Access Routers and Installing Cisco Network Modules in Cisco Access Routers.
The Cisco NAC Appliance operating system is comprised of a hardened Linux kernel based on a Fedora core. Cisco NAC Appliance does not support the installation of any other packages or applications onto a CAM or CAS dedicated machine.
Note
The Cisco NAC Appliance 3100 Series includes the Cisco CCA-3140 (CCA-3140-H1) NAC Appliance (EOL). The CCA-3140-H1 requires CD installation of either the Clean Access Server or Clean Access Manager software.
Refer the Cisco NAC Appliance Hardware Installation Quick Start Guide, Release 4.5 for further details on the Cisco NAC Appliance 3300 Series appliances.
Switch/Router Configuration
The Clean Access Server does not advertise routes. Instead, static routes must be added to the next hop router indicating that traffic to the managed subnets must be relayed to the Clean Access Server's trusted interface.
When the Clean Access Server is in Real-IP Gateway mode, it can act as a DHCP Server or DHCP Relay. With DHCP functionality enabled, the CAS provides the appropriate gateway information (that is, the CAS's untrusted interface IP address) to the clients. If the CAS is working as a DHCP Relay, then the DHCP server in your network must be configured to provide the managed clients with the appropriate gateway information (that is, the Clean Access Server's untrusted interface IP address).
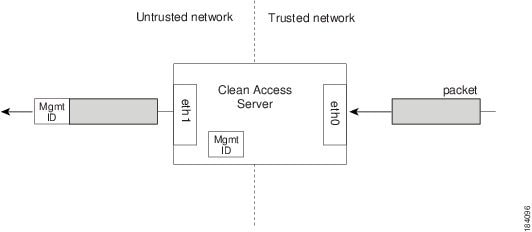
Virtual Gateway Mode Connection Requirements
For all deployments, if planning to configure the Clean Access Server in Virtual Gateway mode (IB or OOB), do not connect the untrusted interface (eth1) of the standalone CAS or HA-Primary CAS until after you have added the CAS to the CAM from the web admin console. For Virtual Gateway HA-CAS pairs, also do not connect the eth1 interface of the HA-Secondary CAS until after HA configuration is fully complete. Keeping the eth1 interface connected while performing initial installation and configuration of the CAS for Virtual Gateway mode can result in network connectivity issues.
When setting up a CAS in Virtual Gateway mode, you specify the same IP address for the trusted (eth0) and untrusted (eth1) network interfaces during the initial installation of the CAS via CLI. At this point in the installation, the CAS does not recognize that it is a Virtual Gateway. It will attempt to connect to the network using both interfaces, causing collisions and possible port disabling by the switch. Disconnecting the untrusted interface until after adding the CAS to the CAM in Virtual Gateway mode prevents these connectivity issues. Once the CAS has been added to the CAM in Virtual Gateway mode, you can reconnect the untrusted interface.
Administrators must use the following procedure for correct configuration of a Virtual Gateway Central Deployment. To prevent looping on any central/core switch as you plug both interfaces of the Clean Access Server into the switch, perform the following steps:
Step 1
Before you connect both interfaces of the CAS to the switch, physically disconnect the eth1 interface.
Step 2
Physically connect the eth0 interface of the CAS to the network.
Step 3
Add the CAS to the CAM in the CAM web console under Device Management > CCA Servers > New Server, as described in Add the CAS to the CAM, page 5-2.
Step 4
Manage the CAS by accessing the CAS management pages, via Device Management > CCA Servers > Manage [CAS_IP] as described in Navigating the CAS Management Pages, page 5-11.
Step 5
Configure VLAN mapping. This is a mandatory step for a Central Deployment where both interfaces of the CAS connect to the same switch. (Note that you can configure VLAN mapping in Edge Deployments with no adverse affect, but you are not required to do so.)
a.
Make sure you check the "Enable VLAN Mapping" checkbox and click Update.
b.
Make sure to set the Untrusted VLAN-to-Trusted VLAN mapping under Device Management > CCA Servers > Manage [CAS_IP] > Advanced > VLAN Mapping. See VLAN Mapping in Virtual Gateway Modes, page 5-35.
Note
Enable VLAN Pruning is checked by default on the Virtual Gateway CAS (starting from release 4.1(1) and later) under Device Management > CCA Servers > Manage [CAS_IP] > Advanced > VLAN Mapping.
Step 6
Once the preceding steps are completed, physically connect the eth1 interface of the CAS to the switch.
Note
If the CAM is down and the CAS is performing VLAN mapping in "fail open" state, do not reboot the CAS because the VLAN mapping capability will be lost until the CAM comes back online.
Step 7
For the 802.1q ports configuration on the switch, make sure to prune all other VLANs for switches trunking to eth0 and eth1 of the CAS except those used for the CAS Management VLAN and the User VLANs.
Step 8
Prune VLAN 1 on the switch ports connecting to the CAS eth0 and eth1 interfaces. For details, see: /en/US/docs/switches/lan/catalyst2950/software/release/12.1_22ea/SCG/swvlan.html#wp1150302.
Switch Support for CAS Virtual Gateway/VLAN Mapping (IB and OOB)
For details on Cisco Catalyst switch model/NME support for the Virtual Gateway VLAN Mapping feature of the Clean Access Server for either in-band (IB) or out-of-band (OOB) deployments, refer to Switch Support for Cisco NAC Appliance.
Determining VLANs For Virtual Gateway
Before you start the initial installation for a Clean Access Server Virtual Gateway deployment, ensure that following is in place for your deployment:
•
The CAS and CAM must be on different subnets (and VLANs).
•
The CAS management VLAN must be on a different VLAN than the user authentication and access VLANs.
•
Configure the native VLAN to be different than the CAS management VLAN. Setting native VLANs helps prevent inadvertent switching loops. The native VLAN must not be the same on the eth0 and eth1 interfaces of the CAS.
–
CAS native VLAN (eth0) (e.g. unused "dummy" vlan 999)
–
CAS native VLAN (eth1) (e.g. unused "dummy" vlan 998)
•
Configure different user authentication and access VLANs on the switches, and configure untrusted subnets on the CAS as Managed Subnets (refer to Configuring Managed Subnets).
•
Ensure there are no common VLANs being forwarded on the switch ports connecting the trusted (eth0) and untrusted (eth1) ports of the CAS. For every VLAN that is allowed on the trunk links going to the Virtual Gateway CAS, there must be a corresponding VLAN Mapping entry (except for the CAS management VLAN).
•
Make sure the eth1 untrusted interface of the CAS is not connected to the network until after VLAN Mapping is configured.
•
Switch(es) must not have SVI (Layer 3) interfaces for the user authentication VLANs anywhere on the network.
•
User authentication VLANs should be on the CAS untrusted interface only and must be pruned from all other trunk links.
See Understanding VLAN Settings, page 5-33 and VLAN Mapping in Virtual Gateway Modes, page 5-35 for additional details.
Summary of Steps For New Installation
Note
Refer to the Cisco NAC Appliance - Clean Access Manager Installation and Configuration Guide, Release 4.6(1) for general deployment information for new installations.
Step 1
Follow the instructions on your welcome letter to obtain a valid license file for your installation. Refer to the instructions in Cisco NAC Appliance Service Contract/Licensing Support for details. (If you are evaluating Cisco NAC Appliance, visit http://www.cisco.com/go/license/public to obtain an evaluation license.)
Note
CAS licenses are generated based on the eth0 address of the CAM. Both CAM and CAS licenses are installed via the CAM web admin console.
Step 2
Obtain a bootable CD of the latest version of the software. You can log in to Cisco Secure Software and download the latest 4.6(1) .ISO image from http://www.cisco.com/pcgi-bin/apps/tblbld/tablebuild.pl?topic=279515766, or click the "Download Software" link from the Cisco NAC Appliance support page here and burn it as a bootable disk to a CD-R.
Note
Cisco recommends burning the .ISO image to a CD-R using speeds 10x or lower. Higher speeds can result in corrupted/unbootable installation CDs.
Note
Refer to the Release Notes for Cisco NAC Appliance, Version 4.6(1) for additional and late-breaking information on 4.6(1) software releases.
Step 3
Connect the CAS to the network, as described in Connect the Clean Access Server.
Step 4
Connect a monitor and keyboard to the CAS, or connect your workstation to the CAS via serial cable, as described in Connect the Clean Access Server.
Step 5
Install the software as described in Install the Clean Access Server Software from CD-ROM.
Note
If your NAC-3310 appliance does not read the software on the CD ROM drive and instead attempts to boot from the hard disk, before proceeding you will need to change the appliance settings to boot from CD ROM as described in Configuring Boot Settings on NAC-3310 Based Appliances.
Step 6
Perform the initial configuration of the CAS, as described in Perform the Initial Configuration.
Note
For High Availability mode, install and initially configure each CAS first before configuring HA. Refer to Chapter 13, "Configuring High Availability (HA)" for details.
You must use identical appliances (e.g. NAC-3350 and NAC-3350) in order to configure High Availability (HA) pairs of Clean Access Managers (CAMs) or Clean Access Servers (CASs).Step 7
Make sure your Clean Access Manager is installed and initially configured as described in the Cisco NAC Appliance - Clean Access Manager Installation and Configuration Guide, Release 4.6(1). Valid FlexLM license file(s) for your Clean Access Server (s) must be installed via the Clean Access Manager web console to complete configuration of the CAS.
Step 8
Add your Clean Access Server(s) to the Clean Access Manager, as described in Add the CAS to the CAM, page 5-2. From this point, you can configure your Clean Access Servers via the CAM web console, or via the CAS direct access web console for certain specific settings.
Connect the Clean Access Server
To install the Clean Access Server software from CD-ROM or to perform its initial configuration, you will need to connect the target machine and access the CAS command line interface.
Step 1
The Clean Access Server requires two 10/100/1000BASE-TX interface connectors on the back panel of the CAS for its eth0 (trusted) and eth1 (untrusted) network interface. Connect the NIC1 (eth0) network interface on the target machine to your local area network (LAN) using a CAT5 Ethernet cable.
Warning
Do not physically connect the eth1 (NIC2) untrusted network interface on a Virtual Gateway CAS until the proper configuration has been performed. Refer to Install the Clean Access Server Software from CD-ROM for details.
If needed, refer to "Cisco NAC Appliance Hardware Summary" in the Cisco NAC Appliance Hardware Installation Quick Start Guide, or the documentation that came with your CAS to find the serial and Ethernet connectors.
Step 2
Connect the power by plugging one end of the AC power cord into the back of the machine and the other end into an electrical outlet.
Step 3
Power on the machine by pressing the power button on the front of the appliance. The diagnostic LEDs will flash a few times as part of an LED diagnostic test. Status messages are displayed on the console as the CAS boots up.
Step 4
Access the command line or the CAS by either:
a.
Connecting a monitor and keyboard directly to the CAS via the keyboard connector and video monitor/console connector on the back panel.
b.
Or, connecting a serial cable from an external workstation (PC/laptop) to the CAS and open a serial connection using terminal emulation software (such as HyperTerminal or SecureCRT) on the external workstation, as described in Install the Clean Access Server Software from CD-ROM.
Note
Static IP addresses must be configured for the CAM/CAS interfaces. DHCP mode is not supported for configuration of these interfaces.
Serial Connection to the CAS
This section details how to access the CAS command line via serial connection.
Step 1
Connect the serial port of your admin computer to an available serial port on the CAS with a serial cable.
Note
If the CAS is already configured for High-Availability (failover), one of its serial connections may be in use for the peer heartbeat connection. In this case, the CAS must have at least two serial ports to be able to manage the CAS over a serial connection. If it does not, you have the option of freeing the serial port by using an Ethernet connection for the peer connection. For more information, see Chapter 13, "Configuring High Availability (HA)."
Step 2
After physically connecting the workstation to the CAS, access the serial connection interface using any terminal emulation software. The following steps describe how to connect using Microsoft® HyperTerminal. If you are using different software, the steps may vary.
Setting Up the HyperTerminal Connection
Step 3
Open the HyperTerminal window by clicking Start > Programs > Accessories > Communications > HyperTerminal.
Step 4
Give any name to the session and click OK.
Step 5
In the Connect using list, choose the COM port on the workstation to which the serial cable is connected (usually either COM1 or COM2) and click OK.
Step 6
Configure the Port Settings as follows:
•
Bits per second - 9600
•
Data bits - 8
•
Parity - None
•
Stop bits - 1
•
Flow control - None
Step 7
Go to File > Properties to open the Properties dialog for the session and change the Emulation setting to VT100.
Step 8
You should now be able to access the command interface for the CAS. You can now:
•
Install the Clean Access Server Software from CD-ROM
•
Perform the Initial Configuration
Note
If you already performed the initial installation, but need to modify the original settings, you can log in as user root and run the service perfigo config command.
Configuring Boot Settings on NAC-3310 Based Appliances
If your NAC-3310 appliance does not read the software on the CD ROM drive, and instead attempts to boot from the hard disk, use the following steps to configure the appliance to boot from CD ROM before attempting to re-image or upgrade the appliance from CD.
Step 1
Press the F10 key while the system is booting.
Step 2
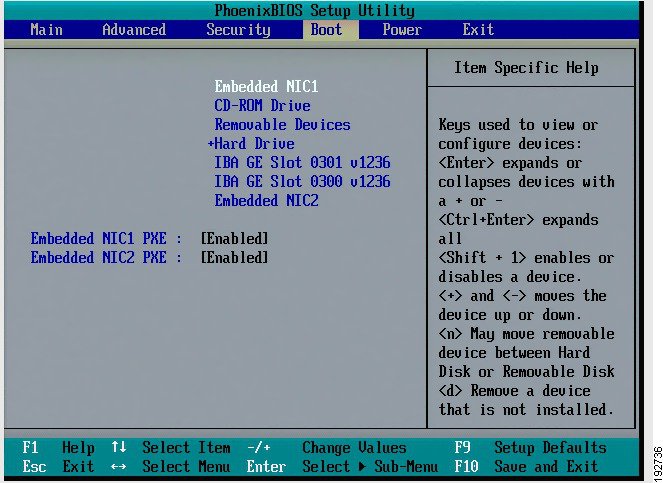
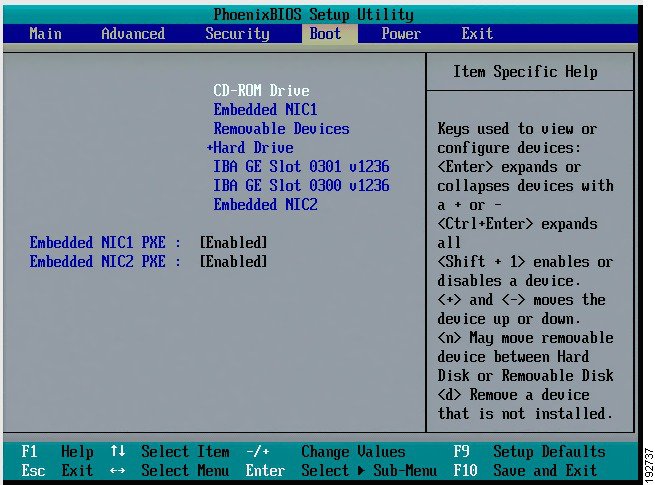
Go to the Boot menu (Figure 4-1).
Figure 4-1 Boot Menu
Step 3
Change the setting to boot from CD ROM by selecting "CD-ROM Drive" from the menu and pressing the plus ("+") key (Figure 4-2).
Figure 4-2 Boot from CD-ROM Drive
Step 4
Press the F10 key to Save and Exit.
Install the Clean Access Server Software from CD-ROM
Once you are connected to the command line of the CAS (as described in Connect the Clean Access Server) use the following steps to install the Clean Access Server software from CD-ROM.
CautionCisco NAC Appliance software is not intended to coexist with other software or data on the target machine. The installation process formats and partitions the target hard drive, destroying any data or software on the drive. Before starting the installation, make sure that the target machine does not contain any data or applications that you need to keep.
CD Installation Steps
The entire installation process, including the configuration steps described in Perform the Initial Configuration should take about 15 minutes.
Step 1
Insert the distribution CD-ROM that contains the Clean Access Server .ISO file into the CD-ROM drive of the target CAS machine.
Step 2
Reboot the machine. The welcome screen appears after the machine restarts:
Cisco Clean Access 4.6-1 Installer (C) 2009 Cisco Systems, Inc.Welcome to the Cisco Clean Access 4.6-1 Installer!- To install a Cisco Clean Access device, press the <ENTER> key.- To install a Cisco Clean Access device over a serial console, enter serial at the boot prompt and press the <ENTER> key.boot:
Note
If your NAC-3310 appliance does not read the software on the CD ROM drive and instead attempts to boot from the hard disk, before proceeding you will need to change the appliance settings to boot from CD ROM as described in Configuring Boot Settings on NAC-3310 Based Appliances.
Step 3
At the "boot:" prompt, type one of the following options depending on the type of connection:
•
Press the Enter key if your monitor and keyboard are directly connected to the CAS.
•
Type serial and press enter in the terminal emulation console if you are accessing the appliance over a serial connection.
Step 4
The Install selection option appears next, prompting you to perform a brand new installation of Cisco NAC Appliance or exit/cancel the install process. At the following prompt, enter 1 to install a new version of Cisco NAC Appliance.
Checking for existing installations.Clean Access Server 4.1.2.1 installation detected.Please choose one of the following actions:1) Install.2) Exit.Step 5
Next, the Cisco NAC Appliance software installer asks you to specify whether you are installing a Clean Access Manager or Clean Access Server. At the following prompt, enter 2 to perform the installation for a Clean Access Server.
Please choose one of the following configurations:1) CCA Manager.2) CCA Server.
CautionOnly one CD is used for installation of the Clean Access Manager or Clean Access Server software and the installation script does not automatically detect CAM or CAS installation for the target machine. You must select the appropriate type, either CAM or CAS, for the target machine on which you are performing installation.
Step 6
The Clean Access Server Package Installation then executes. The installation takes several minutes. When finished, the installation script presents the following message, prompting you to press Enter to reboot the CAS and launch the Clean Access Server quick configuration utility.
Installation complete. Press <ENTER> to continueWhen finished, the welcome screen for the Clean Access Server quick configuration utility appears, and a series of questions prompt you for the initial CAS configuration, as described in the next section, Configuration Utility Script.
Note
If after installation you need to reset the CAS configuration settings (such as the eth0 IP address), connect to the CAS machine serially or via SSH and run the service perfigo config command. See CAS CLI Commands for details. Most other settings can also be modified later from the web console.
Perform the Initial Configuration
When installing the Clean Access Server from CD-ROM, the Configuration Utility Script automatically appears after software package installation to prompt you for the initial CAS configuration.
Note
If necessary, you can always manually start the Configuration Utility Script as follows:
1.
Over a serial connection or working directly on the CAS, log onto the CAS as user root with the root user password.
2.
Run the initial configuration script by entering the following command:
service perfigo configYou can run the service perfigo config command to modify the configuration of the CAS if it cannot be reached through the web admin console. For further details on CLI commands, see CAS CLI Commands.
Configuration Utility Script
Step 1
The configuration utility script suggests default values for particular parameters. To configure the installation, either accept the default value or provide a new one, as described below.
Step 2
After the software is installed from the CD and package installation is complete, the welcome script for the configuration utility appears:
Welcome to the Cisco Clean Access Server quick configuration utility.Note that you need to be root to execute this utility.The utility will now ask you a series of configuration questions.Please answer them carefully.Cisco Clean Access Server, (C) 2009 Cisco Systems, Inc.Step 3
The script first asks for settings for the trusted interface (eth0). The trusted interface is the interface to the protected, backend network.
Configuring the network interfaces:Please enter the IP address for the interface eth0 []: 10.201.1.20You entered 10.201.1.20 Is this correct? (y/n)? [y]At the prompt, type the eth0 IP address of the CAS and press Enter. Note that the eth0 IP address of the CAS is the same as the Management IP address. At the confirmation prompt, type y to accept the entry or type n to change it and enter another address for the trusted eth0 network interface. When prompted, press Enter to confirm the value.
Step 4
Type the subnet mask of the eth0 interface or press Enter to accept the default of 255.255.255.0. Confirm the value at when prompted.
Please enter the netmask for the interface eth0 []: 255.255.255.0You entered 255.255.255.0, is this correct? (y/n)? [y]Step 5
Specify the default gateway address for the trusted interface and press Enter. Confirm the value at when prompted.
Please enter the IP address for the default gateway []: 10.201.1.1You entered 10.201.1.1 Is this correct? (y/n)? [y]Step 6
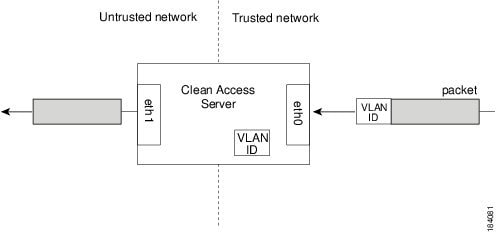
Specify VLAN ID passthrough behavior for the trusted interface. At the prompt, type n and press Enter (or just press Enter) to accept the default behavior where VLAN passthrough is disabled and VLAN IDs are stripped from traffic passing through the interface. Or, enter y to enable VLAN ID passthrough for traffic passing from the trusted network to the untrusted network.
[Vlan Id Passthrough] for packets from eth0 to eth1 is disabled.Would you like to enable it? (y/n)? [n]
Note
•
In most cases, enabling VLAN ID passthrough is not needed. Only enable VLAN ID passthrough if you are sure you need it. If you choose not to enable it at this time, you can always change this option later from the CAS Network > IP page of the web console or using the service perfigo config utility. Note that either method requires a reboot of the CAS.
•
Faulty VLAN settings can render the Clean Access Server unreachable from the Clean Access Manager, so use caution when configuring VLAN settings.
By default, the VLAN ID is not passed through, that is, the VLAN ID is stripped from packets passed through the CAS, as illustrated in Figure 4-3. The IDs are retained by the Clean Access Server and attached to response messages passed from the untrusted network back to the trusted network.
Figure 4-3 VLAN ID Termination
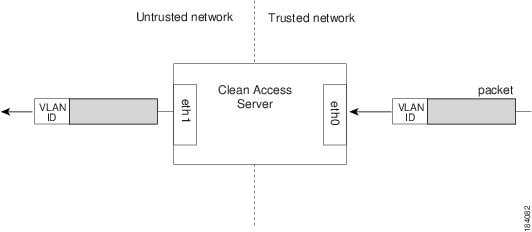
In VLAN ID passthrough, the identifier is retained on traffic that passes through the interface.
Figure 4-4 VLAN ID Passthrough
Step 7
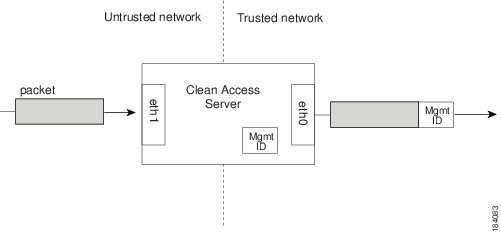
Specify Management VLAN Tagging for the trusted interface at the next prompt. Type N and press Enter (or just press Enter) to keep Management VLAN tagging disabled (default). Or, type Y and press Enter to enable Management VLAN tagging and specify the Management VLAN ID to use for the CAS trusted interface.
[Management Vlan Tagging] for egress packets of eth0 is disabled.Would you like to enable it? (y/n)? [n]
Note
You can change the Management VLAN ID later from the CAS Network > IP web console page; however, changing settings on the CAS IP page requires a reboot of the CAS.
A Management VLAN identifier is a default VLAN identifier that is added to a packet if it does not have its own VLAN identifier or if the identifier was originally stripped by the adjacent interface. The setting at the prompt applies to traffic passing from the untrusted network to the trusted network.
Figure 4-5 Eth0 Egress Packets with Management VLAN ID Tagging
Note
•
In most cases, enabling Management VLAN tagging is not needed. You should only enable it if you are sure it is necessary. If you choose not to enable it at this time, you can change the option later in the web console or using service perfigo config utility.
•
Also note that faulty VLAN settings can render the Clean Access Server unreachable from the Clean Access Manager, so be sure to use care when configuring VLAN settings.
Step 8
Next configure the untrusted interface. This is the interface to the untrusted (managed) network. At the prompt type the address you want to use for the untrusted interface (eth1) and press Enter. Unless deploying the Clean Access Server in a bridge (Virtual Gateway) configuration, the trusted and untrusted interfaces must be on separate subnets. Confirm the value when prompted.
Please enter the IP address for the untrusted interface eth1 []: 192.168.10.10You entered 192.168.10.10 Is this correct? (y/n)? [y]Step 9
Type the subnet mask of the eth1 interface or press Enter to accept the default of 255.255.255.0. Confirm the value at when prompted.
Please enter the netmask for the interface eth1 []: 255.255.255.0You entered 255.255.255.0, is this correct? (y/n)? [y]Step 10
Enter the default gateway address for the untrusted interface:
•
If the Clean Access Server will act as a Real-IP gateway or NAT gateway, this should be the IP address of the CAS's untrusted interface eth1.
•
If the Clean Access Server will act as a Virtual gateway (i.e., a bridge), this can be the same default gateway address used for the trusted side.
Please enter the IP address for the default gateway []: 192.168.10.1You entered 192.168.10.1 Is this correct? (y/n)? [y]Step 11
Specify VLAN passthrough behavior for traffic passing from the untrusted to the trusted network. At the prompt, type n and press Enter (or just press Enter) to accept the default behavior (disabled) or enter y to enable VLAN ID passthrough for traffic from the untrusted network.
[Vlan Id Passthrough] for packets from eth1 to eth0 is disabled.Would you like to enable it? (y/n)? [n]Figure 4-6 VLAN ID Passthrough
Step 12
Specify Management VLAN Tagging for the untrusted interface at the next prompt. Type N and press Enter (or just press Enter) to keep Management VLAN tagging disabled (default). Or, type Y and press Enter to enable Management VLAN tagging and specify the Management VLAN ID to use for the CAS untrusted interface.
[Management Vlan Tagging] for egress packets of eth1 is disabled.Would you like to enable it? (y/n)? [n]
Note
You can change the Management VLAN ID later from the CAS Network > IP web console page; however, changing settings on the CAS IP page requires a reboot of the CAS.
Figure 4-7 Eth1 Egress Packets with Management VLAN ID Tagging
Step 13
Specify the host name for the Clean Access Server (nacserver is the default). Type and confirm the address when prompted:
Please enter the hostname [nacserver]: cas1You entered cas1 Is this correct? (y/n)? [y]Step 14
Specify the IP address of the Domain Name System (DNS) server in your environment. Type and confirm the address when prompted:
Please enter the IP address for the name server: []: 172.10.16.16You entered 172.10.16.16 Is this correct? (y/n)? [y]Step 15
The Clean Access Manager and Clean Access Servers in a deployment authenticate each other through a shared secret. The shared secret serves as an internal password for the deployment. Type and confirm the shared secret when prompted:
The shared secret used between Clean Access Manager and Clean Access Server is the default string: cisco123This is highly insecure. It is recommended that you choose a string that is unique to your installation.Please remember to configure all Clean Access Devices with the same string.Only the first 8 characters supplied will be used.Please enter the shared secret between Clean Access Server and Clean Access Manager:
CautionThe shared secret must be the same for the Clean Access Manager and all Clean Access Servers in the deployment. If they have different shared secrets, they cannot communicate.
Step 16
Specify time settings for the Clean Access Server.
a.
Choose the timezone location from the continents and oceans list. Type the number next to your location on the list, such as 2 for the Americas, and press enter. Enter 11 to enter the time zone in Posix TZ format, such as GST-10.
>>> Configuring date and time:The timezone is currently not set on this system.Please identify a location so that time zone rules can be set correctly.Please select a continent or ocean.1) Africa2) Americas3) Antarctica4) Arctic Ocean5) Asia6) Atlantic Ocean7) Australia8) Europe9) Indian Ocean10) Pacific Ocean11) none - I want to specify the time zone using the Posix TZ format.#? 2b.
Choose a country for the chosen timezone. Select your country from the country list, such as 45 for the United States, and press Enter.
Please select a country.1) Anguilla 18) Ecuador 35) Paraguay2) Antigua & Barbuda 19) El Salvador 36) Peru3) Argentina 20) French Guiana 37) Puerto Rico4) Aruba 21) Greenland 38) St Kitts & Nevis5) Bahamas 22) Grenada 39) St Lucia6) Barbados 23) Guadeloupe 40) St Pierre & Miquelon7) Belize 24) Guatemala 41) St Vincent8) Bolivia 25) Guyana 42) Suriname9) Brazil 26) Haiti 43) Trinidad & Tobago10) Canada 27) Honduras 44) Turks & Caicos Is11) Cayman Islands 28) Jamaica 45) United States12) Chile 29) Martinique 46) Uruguay13) Colombia 30) Mexico 47) Venezuela14) Costa Rica 31) Montserrat 48) Virgin Islands (UK)15) Cuba 32) Netherlands Antilles 49) Virgin Islands (US)16) Dominica 33) Nicaragua17) Dominican Republic 34) Panamac.
If the country contains more than one time zone, time zone regions for the country appear. Choose the appropriate time zone region from the list and press enter (for example, 19 for Pacific Time).
Please select one of the following time zone regions.1) Eastern Time2) Eastern Time - Michigan - most locations3) Eastern Time - Kentucky - Louisville area4) Eastern Time - Kentucky - Wayne County5) Eastern Time - Indiana - most locations6) Eastern Time - Indiana - Crawford County7) Eastern Time - Indiana - Starke County8) Eastern Time - Indiana - Switzerland County9) Central Time10) Central Time - Indiana - Daviess, Dubois, Knox, Martin, Perry & Pulaski Counties11) Central Time - Indiana - Pike County12) Central Time - Michigan - Dickinson, Gogebic, Iron & Menominee Counties13) Central Time - North Dakota - Oliver County14) Central Time - North Dakota - Morton County (except Mandan area)15) Mountain Time16) Mountain Time - south Idaho & east Oregon17) Mountain Time - Navajo18) Mountain Standard Time - Arizona19) Pacific Time20) Alaska Time21) Alaska Time - Alaska panhandle22) Alaska Time - Alaska panhandle neck23) Alaska Time - west Alaska24) Aleutian Islands25) Hawaiid.
Confirm your choices or cancel your choices and start over, by entering 1 to confirm or 2 to start over.
The following information has been given:United StatesPacific TimeIs the above information OK?1) Yes2) NoStep 17
Confirm the current date and time at the next prompt by pressing enter, or provide the correct date and time in the format shown. Confirm the values when prompted.
Current date and time hh:mm:ss mm/dd/yy [11:23:33 08/22/08]: 11:23:33 08/22/08You entered 11:23:33 08/22/08 Is this correct? (y/n)? [y]Step 18
Press Enter to configure the temporary SSL certificate. The certificate secures the login exchange between the Clean Access Server and untrusted (managed) clients. Configure the certificate as follows:
a.
Type the IP address or domain name for which you want the certificate to be issued.
Note
This is also the IP address or domain name to which the web server responds. If DNS is not already set up for a domain name, the CAS web console will not load. Make sure to create a DNS entry in your servers, or else use an IP address for the CAS.
b.
For the organization unit name, enter the group within your organization that is responsible for the certificate (for example, test or engineering).
c.
For the organization name, type the name of your organization or company for which you would like to receive the certificate (for example, access), and press enter.
d.
Type the name of the city or county in which your organization is legally located, and press enter.
e.
Enter the two-character state code in which the organization is located, such as CA or NY, and press enter.
f.
Type the two-letter country code, such as US, and press enter.
g.
A summary of the values you entered appears. Press enter to accept the values or N to start over.
You entered the following:Domain: mydomain.comOrganization unit: testOrganization name: accessCity name: My TownState code: CACountry code: USIs this correct? (y/n)? [y]When you confirm your values, the certificate is generated and the Clean Access Server database is initialized.
Step 19
Specify whether or not you want the CAS to feature Pre-login Banner Support at the following prompt.
Enable Prelogin Banner Support? (y/n)? [n]For more information and an example of the Pre-login Banner feature, see Figure 12-2 on page 12-3.
Step 20
Configure the root user password for the installed Linux operating system of the Clean Access Server. The root user account is used to access the system over a serial connection or through SSH.
Cisco NAC Appliance supports using Strong Passwords for root user login. Passwords must be at least 8 characters long and feature a combination of upper- and lower-case letters, digits, and other characters. For example, the password 10-9=One would not satisfy the requirements because it does not feature two characters from each category, but 1o-9=OnE is a valid password. For more details, see the "Manage System Passwords" section in the "Administer the CAM" chapter in the Cisco NAC Appliance - Clean Access Manager Installation and Configuration Guide, Release 4.6(1).
For security reasons, it is highly recommended that you change the password for the root user.** Please enter a valid password for root user as per the requirements below! **Changing password for user root.You can now choose the new password.A valid password should be a mix of upper and lower case letters,digits, and other characters. Minimum of 8 characters and maximumof 16 characters with characters from all of these classes. Minimumof 2 characters from each of the four character classes is mandatory.An upper case letter that begins the password and a digit that endsit do not count towards the number of character classes used.Enter new password:Re-type new password:passwd: all authentication tokens updated successfully.Step 21
Next type the password for the admin user for the CAS direct access web console.
Please enter an appropriately secure password for the web console admin user.New password for web console admin:Confirm new password for web console admin:Step 22
If installing from the CD-ROM, press the Enter key to reboot the CAS when configuration is complete:
Configuration is complete.Changes require a REBOOT of Clean Access Server.Step 23
Enter the following command to reboot the CAS:
# rebootStep 24
The initial configuration is now complete. Once the Clean Access Manager is also installed and initially configured, use the CAM web administration console to add the CAS to the CAM as described in Chapter 5, "Configuring the CAS Managed Network."
Important Notes for SSL Certificates
•
You must generate the temporary SSL certificate during CAS installation or you will not be able to access your CAS.
•
After CAM and CAS installation, make sure to synchronize the time on the CAM and CAS via the web console interface before regenerating a temporary certificate on which a Certificate Signing Request (CSR) will be based. For further details on the CAS, see:
–
Manage CAS SSL Certificates, page 12-7
–
Synchronize System Time, page 12-36
For details on CAM certificates, see the Cisco NAC Appliance - Clean Access Manager Installation and Configuration Guide, Release 4.6(1).
•
Before deploying the CAS in a production environment, Cisco Strongly recommends acquiring a trusted certificate from a third-party Certificate Authority to replace the temporary certificate (in order to avoid the security warning that is displayed to end users during user login).
Note
If present on the CAS, you will see messages on the CAS web console (Figure 4-8) warning that the "EMAILADDRESS=info@perfigo.com, CN=www.perfigo.com, OU=Product, O="Perfigo, Inc.", L=San Francisco, ST=California, C=US" certificate authority can render your CAS and associated client machines vulnerable to security attacks. To locate and remove this certificate authority from the CAS database, use the instructions in Manage Trusted Certificate Authorities, page 12-19.
Figure 4-8 Administrator Web Console Messages Warning to Obtain Trusted Certificate Authority and Remove Existing "www.perfigo.com" Certificate
CAS CLI Commands
The CAM web admin console allows you to perform most of the tasks required for administering Cisco NAC Appliance deployment. However, there are two cases where the command line interface of the CAS can be or must be used:
•
Use the CAS CLI Commands for Cisco NAC Appliance to access the CAS configuration directly for initial configuration of the CAS or if the web admin console is unavailable due to incorrect network or VLAN settings.
•
If you have purchased the Cisco NAC Profiler solution, use the CAS CLI Commands for Cisco NAC Profiler to enable the Cisco NAC Profiler Collector application on the Clean Access Server.
To run the CLI commands, access the CAS using SSH and log in as user root and enter the root user password. If already serially connected to the CAS, you can run CLI commands from the terminal emulation console after logging in as root (see Install the Clean Access Server Software from CD-ROM).
CAS CLI Commands for Cisco NAC Appliance
The format service perfigo <command> is used to enter a command from the command line. Table 4-1 lists the commonly used Cisco NAC Appliance CLI commands.
Table 4-1 Cisco NAC Appliance CLI Commands for CAS
service perfigo startStarts up the CAS. If the CAS is already running, a warning message appears. The CAS must be stopped for this command to be used.
service perfigo stopShuts down the Cisco NAC Appliance service.
Note
When the management VLAN is set, this command will cause the CAS to lose network connectivity when issued. You can use service perfigo maintenance instead.
service perfigo maintenanceThis command brings the CAS to maintenance mode, in which only the basic CAS router runs and continues to handle VLAN-tagged packets. The command allows communication through the management VLAN and is intended for environments where the CAS is in trunk mode and the native VLAN is different than the management VLAN.
Note
You can use service perfigo maintenance to stop the service when testing high availability (failover) for Virtual Gateway CASs over an SSH connection.
service perfigo platformThis command allows you to determine whether the CAS is a standard Clean Access Server appliance or a Cisco NAC network module installed in a Cisco ISR router chassis. The output displays either "APPLIANCE" or "NME-NAC" as the platform setting.
For detailed installation and configuration information, see Getting Started with Cisco NAC Network Modules in Cisco Access Routers and Installing Cisco Network Modules in Cisco Access Routers.
service perfigo restartShuts down the Cisco NAC Appliance service and starts it up again. This is used when the service is already running and you want to restart it.
Note
service perfigo restart should not be used to test high availability (failover). Instead, Cisco recommends "shutdown" or "reboot" on the machine to test failover, or, if a CLI command is preferred, service perfigo stop or service perfigo maintenance followed by service perfigo start
service perfigo rebootShuts down and reboots the machine. You can also use the Linux reboot command.
service perfigo configStarts the configuration script to modify the CAS configuration. After completing service perfigo config, you must reboot the CAS. For instructions on using the script, see Perform the Initial Configuration
service perfigo timeUse to modify the time zone settings.
CAS CLI Commands for Cisco NAC Profiler
The Clean Access Server is shipped with a default version of the Cisco NAC Profiler Collector component, which needs to be enabled and configured separately when integrating with the Cisco NAC Profiler solution. Table 4-2 lists CLI commands issued on the CAS for the Cisco NAC Profiler Collector service. For complete details on the Cisco NAC Profiler solution, refer to the Cisco NAC Profiler Installation and Configuration Guide and Release Notes for Cisco NAC Profiler.
Note
To display the version of the Collector on the CAS, SSH to the CAS machine running the Collector service and type rpm -q Collector.
Table 4-2 Cisco NAC Profiler Collector CLI Commands for CAS
service collector start
Starts the Collector service on the CAS.
service collector stop
Shuts down the Collector service on the CAS.
service collector verify
Displays the configured Collector Services running on the CAS
Collector Network ConfigurationCollector Name = bcas1-fwConnection Type = serverListen on IP = 10.40.1.10Network IP ACL127.0.0.110.10.0.21110.10.0.21010.10.0.212Port Number = 31416Encryption type = AESShared secret = profilerservice collector status
Displays the running status of the individual Collector modules on the CAS, for example:
Profiler Statuso Server Not Installedo Forwarder Runningo NetMap Runningo NetTrap Runningo NetWatch Runningo NetInquiry Runningo NetRelay Runningservice collector restart
Stops and then restarts the Collector service on the CAS. This is used when the service is already running and you want to restart it.
service collector config
Starts the Collector service configuration script to allow communication with the Cisco NAC Profiler Server. For example:
[root@caserver12 /]# service collector configEnable the NAC Collector (y/n) [y]:Configure NAC Collector (y/n) [y]:Network configuration to connect to a NAC Profiler ServerConnection type (server/client) [client]:Connect to IP [127.0.0.1]: 192.168.96.20Port number [31416]:Encryption type (AES, blowfish, none) [AES]: noneShared secret []: cisco1232-- Configured caserver12-fw-- Configured caserver12-nm-- Configured caserver12-nt-- Configured caserver12-nw-- Configured caserver12-ni-- Configured caserver12-nrNAC Collector has been configuredFor detailed installation and configuration information, see the Cisco NAC Profiler Installation and Configuration Guide.
CAM/CAS Connectivity Across a Firewall
See the Cisco NAC Appliance - Clean Access Manager Installation and Configuration Guide, Release 4.6(1) for details on which ports to open in a firewall to allow communication between the Clean Access Manager and Clean Access Server(s).
Configuring the CAS Behind a NAT Firewall
CautionIf deploying a NAT firewall between the CAS and the CAM, the CAS must be in Standalone mode. Cisco NAC Appliance does not support High Availability CAS pairs when a NAT firewall is deployed on the trusted side of the CAS HA pair.
If deploying the Clean Access Server behind a firewall (there is a NAT router between CAS and CAM), you will need to perform the following steps to make the CAS accessible:
Step 1
Connect to the CAS by SSH or use a serial console. Log in as root user.
Step 2
Change directories to /perfigo/access/bin/.
Step 3
You will need to edit two files: restartweb and starttomcat.
Step 4
Locate the CATALINA_OPTS variable definition in each file.
Step 5
Add -Djava.rmi.server.hostname=<caserver1_hostname> to the variable, replacing caserver1_hostname with the host name of the server you are modifying. For example:
CATALINA_OPTS="-server -Xms64m -Xmx${MAX}m -Xincgc -Djava.util.logging.config.file=${CATALINA_HOME}/conf/redirect-log.properties -Dperfigo.jmx.context=${PERFIGO_SECRET} -Djava.security.auth.login.config=${CATALINA_HOME}/conf/sso-login.conf -Dsun.net.inetaddr.ttl=60 -Dsun.net.inetaddr.negative.ttl=10 -Djava.security.egd=file:/dev/urandom"-Djava.rmi.server.hostname=caserver1"Step 6
Restart the CAS by entering the service perfigo restart command.
Step 7
Repeat the preceding steps for each Clean Access Server in your deployment.
Step 8
Connect to the Clean Access Manager by SSH or using a serial console. Login as root.
Step 9
Change directories to /etc/.
Step 10
Edit the hosts file by appending the following line:
<public_IP_address> <caserver1_hostname> <caserver2_hostname>where:
•
<public_IP_address> - The address that is accessible outside the firewall.
•
<caservern_hostname> - The host name of each Clean Access Server behind the firewall.
The Clean Access Server(s) should now be addressable behind the firewall.
Configuring Additional NIC Cards
The Configuration Utility script assumes that the CAM and CAS machines come with eth0 (NIC1) and eth1 (NIC2) interfaces by default and allows you to configure these during initial installation. If your system has additional network interface cards (e.g. NIC3, NIC4), you can use the following instructions to configure the additional interfaces (e.g. eth2, eth3) on those cards. Typically, eth2 needs to be configured when setting up Clean Access Server systems for High Availability. For HA, once the eth2 (NIC3) interface is configured with the proper addressing, it can then be configured as the dedicated UDP heartbeat interface for the HA-CAS.
Note
•
For Cisco NAC Appliance hardware, the following instructions assume that the NIC is plugged in and "working" (i.e. recognized by BIOS and by Linux).
•
If the NIC card is not recognized by BIOS (for example, for a non-appliance server machine), you may need to adjust IRQ/memory settings as per the manufacturer's recommendations.
•
Once the NIC is recognized by BIOS, it should be automatically recognized by the software (Linux). If for some reason, the NIC is recognized by BIOS, but not by Linux, then login to the system and run "kudzu". This will bring up a utility that helps you configure the NIC.
To Configure an Additional NIC
Step 1
To verify that the NIC has been recognized by Linux, type ifconfig eth<n> (where <n> is the interface number). For example, <n> will be 2 if adding a NIC to a system that already has two built-in Ethernet interfaces; therefore, you would type:
ifconfig eth2
Step 2
You should see information about the interface including MAC address, transmit and receive counters. This means the interface has been recognized by Linux and can be used.
Step 3
Change to the following directory:
cd /etc/sysconfig/network-scripts
Step 4
Use vi to edit the ifcfg file for the interface, for example:
vi ifcfg-eth2Step 5
Add the following lines into the file—replacing IPADDR, NETMASK, BROADCAST and NETWORK values with the actual values suitable for your network:
DEVICE=eth2IPADDR=192.168.0.253NETMASK=255.255.255.252BROADCAST=192.168.0.255NETWORK=192.168.0.252BOOTPROTO=staticONBOOT=yesTYPE=EthernetStep 6
Save the file and reboot the system.
Step 7
The network interface is now ready to be used for HA.
Note
See CAS High Availability Requirements, page 13-5 for additional details.
Troubleshooting the Installation
Note
For further troubleshooting information, see the latest version of the Release Notes.
Network Interface Card (NIC) Driver Not Supported
For complete details, refer to the "Troubleshooting Network Card Driver Support Issues" section of the Supported Hardware and System Requirements for Cisco NAC Appliance (Cisco Clean Access).
Resetting the Clean Access Server Configuration
If incorrect network, shared secret, or VLAN settings have rendered the Clean Access Server unreachable from the Clean Access Manager, you can reset the Clean Access Server's configuration. Note that resetting the configuration restores the Clean Access Server configuration to its install state. Any configuration settings made since installation will be lost.
To reset the configuration:
Step 1
Connect to the Clean Access Server by SSH.
Step 2
Delete the env file:
# rm /perfigo/access/bin/env
Step 3
Then reboot using:
# service perfigo reboot
You can now add the CAS to the CAM. See Chapter 5, "Configuring the CAS Managed Network."