Table Of Contents
Accessing the Administration Console
Creating Resource-based Policies
Reviewing Policies with Audit Entitlement
Quick Start Guide
Introduction
This guide takes you step-by-step through the following operations:
•
Accessing the Administration Console
•
Creating an Application Group
•
Creating Resource-based Policies
•
Reviewing Policies with Audit Entitlement
Prerequisites
The Policy Administration Point (PAP) and Policy Decision Point (PDP) must be installed successfully and must be operational. If either or both of the components are not operational, follow the instructions given in the Cisco Enterprise Policy Manager Installation and Configuration Guide.
Starting the PAP and PDP
First you must start the PAP and PDP. If you are using the embedded Tomcat engine that ships with CEPM installer, then run startsecurentgui.bat (for Windows) or startsecurentgui.sh (for UNIX or Linux). If you are using a Cisco-supported application server, start the application server hosting the securent.war and pdp.war applications and make sure that the applications are started and operational.
Accessing the Administration Console
The PAP administration console is a GUI for policy administration, review, and reporting. You can access the administration console using a web browser.
To start the administration console, follow these steps:
Step 1
Open your browser and enter the following URL: http://host:port/cepm
In the URL string, replace host and port with the values corresponding to those of your application server where the PAP is installed.
The login page is displayed, which prompts you to log in. If no screen is displayed, or if you get an error, see CEPM Installation and Configuration Guide [especially its troubleshooting section] to address the issue before proceeding.
During the setup process for the entitlements repository (database), a default administrator account is created that can be used to access the administration console initially. The default administrator credentials are:
•
User ID: superuser
•
Password: admin
Step 2
Log in to the administration console using these credentials with Default Domain. If you do not have a Default Domain choose a valid domain.
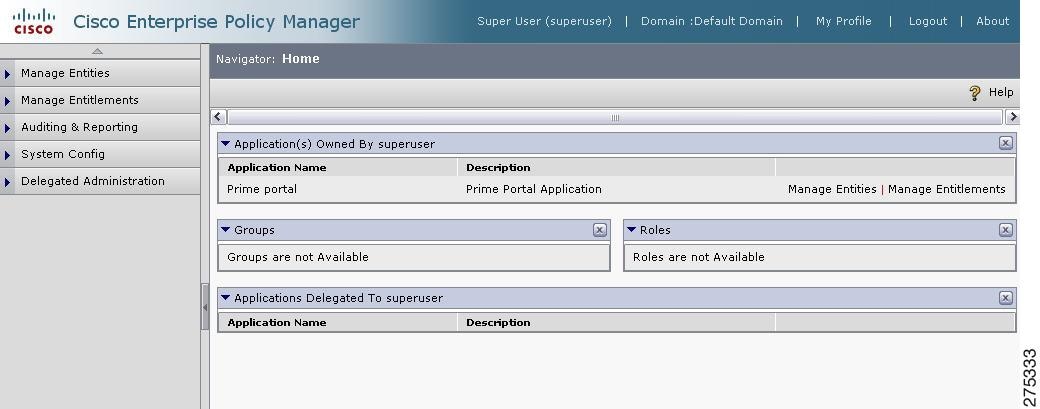
After you successfully login, the PAP home page is displayed showing all the application groups and applications that are you currently own. Initially, this page contains only default information created at the time of CEPM installation. (These default items are the Prime Portal application and Prime Group application group, which are displayed on the administration console home page.)
Figure 1-1 Home Page
Step 3
To change the superuser password, click the Edit Profile button at the upper right of the administration console.
Creating an Application Group
An application group is a group of applications that you intend to secure within CEPM. Groupings are used for various reasons, but applications are mainly grouped for administration and segregation purpose. You should create an application group first before creating an application.
To create a new application group, follow these s teps:
Step 1
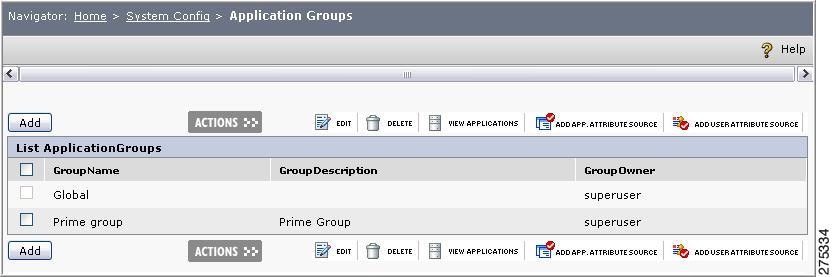
Choose System Config > Application Groups.
Figure 1-2 Application Group
Step 2
Click Add.
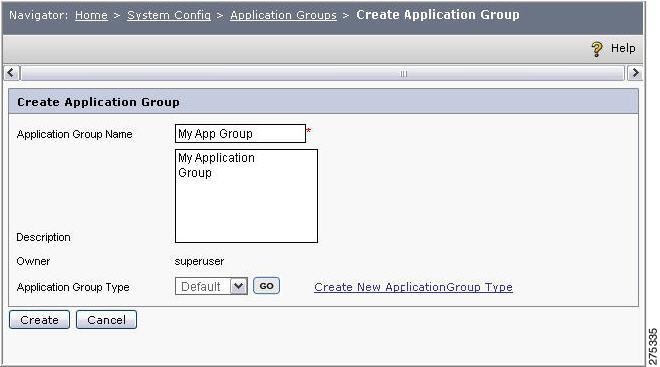
Figure 1-3 Create Application Group
Step 3
Enter a new Application Group Name (for example, MyApplicationGroup) and a Description of the group in the respective fields.
Step 4
Select the Application Group Type from the drop-down menu. By default it is set to Default. If you choose Default as the application group type, there is no need to click Go because it is meant for showing the attributes created under the selected attribute type.
Step 5
Click Create.
The new application group (MyApplicationGroup) is now created in the PAP application.
Creating a PDP
Using the PAP console, you can create the PDPs, that is, PDPs that contain the entitlement decisions. The PDP component is shipped as a Java .war file, pdp.war, which should be deployed on your application server.
Note
This example uses a PDP that is deployed on the embedded Tomcat Server, which comes bundled with CEPM. In this example, the PDP is deployed on a server with IP address 131.107.0.52, and the pdp.war application is running on port 8080. The correct configuration of the PDP for this example is shown in the next figure. The credentials being used are admin:password. The remainder of the configuration is as it appears in the next figure.
To create a PDP, follow these steps:
Step 1
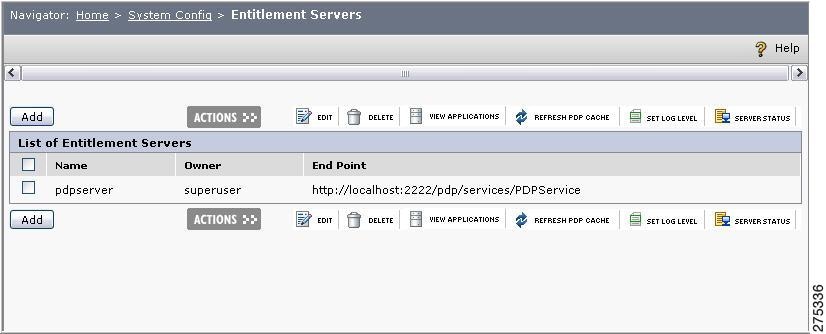
Choose System Config > PDPs.
The List of PDPs page is displayed.
Figure 1-4 Entitlement Server
Step 2
Click Add.
The Create PDP page is displayed.
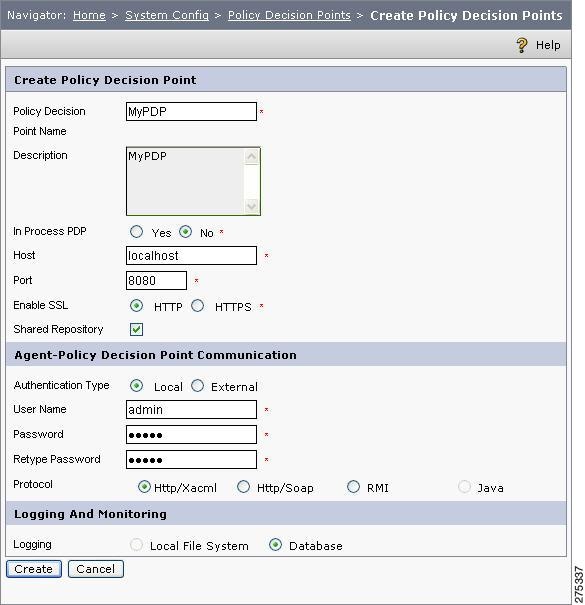
Figure 1-5 Create Policy Decision Point
Step 3
Enter the PDP details:
•
Enter the name of the PDP in the Policy Decsion field (for example, MyPDP) and a brief Description about it.
•
If you want to create an in-process PDP, click Yes. The Host and Port fields are disabled. Click No to define an external PDP. (For additional details about in-process PDPs, see the Cisco Enterprise Policy Manager In-Process PDP Deployment Guide.)
•
Enter values for host name or IP address and port number in the Host and Port fields. These values must refer to the host and port used by a PDP application deployed in your environment.
•
Click HTTP or HTTPS to specify the transport protocol for the PDP. If you select HTTPS, the HTTPS Details section is included above the Logging And Monitoring section.
Refer to CEPM User Guide for more information on SSL configuration.
•
By default, Shared Repository is checked, which means that the PDP and PAP will share the same database instance. Uncheck the Shared Repository if you want to have separate database instances for the PDP and PAP.
•
Enter the values for Agent-Policy Decision Point Communication:
–
Click the required authentication type. Click Local to use the entitlement repository (CEPM database) to store the credentials of the application users for authentication purpose. Click External if you want to use the LDAP server to store the credentials of the users.
–
Enter the username and password and reenter the password.
–
Choose the Agent-PDP Communication protocol as Http/Xacml, Http/Soap, or RMI.
•
Enter the Logging And Monitoring parameters:
–
Click the Local File System if you want to store the audit information in a local file system.
–
Click the Database to store the audit information in the entitlement repository.
Step 4
Click Create.
The PDP with the name MyPDP is created.
Creating an Application
An application in CEPM is the object used to represent the application or other entity you are providing entitlement services to. An application has a name, is created within an application group, and uses one or more PDPs for policy decisions, review, and auditing. Within CEPM, all resources and policies are created within an application.
To create a new application, follow these steps:
Step 1
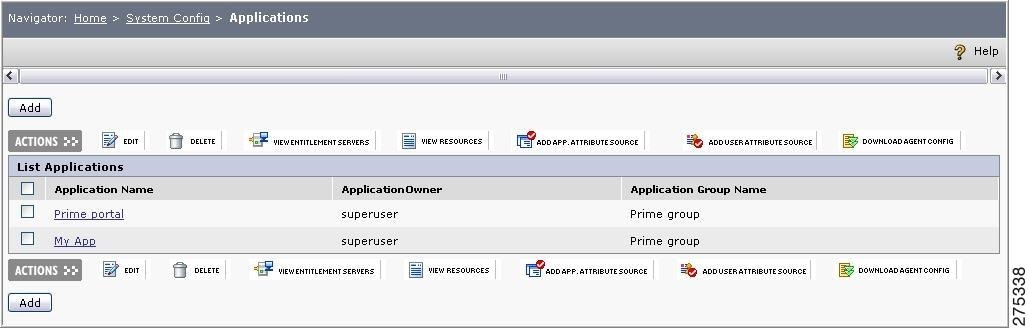
Choose System Config > Applications.
The List of Applications page is displayed.
Figure 1-6 Applications
Step 2
Click Add New Application.
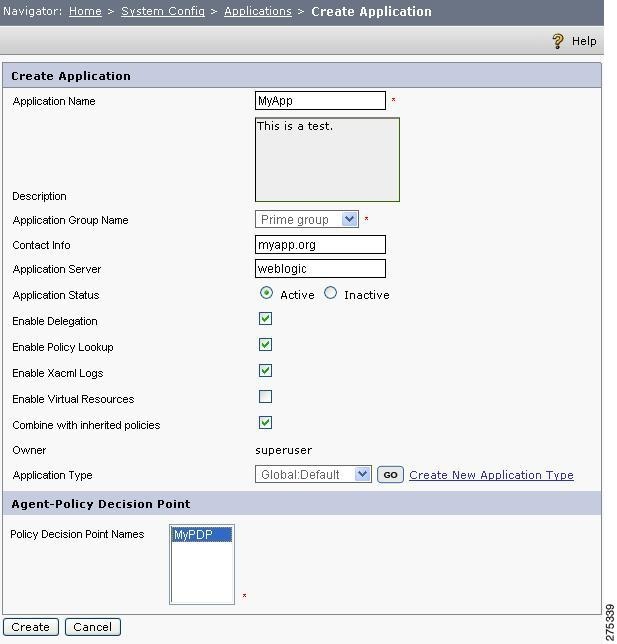
The Create Application page is displayed.
Figure 1-7 Create Application
Step 3
Enter the following information in the Application Name, Description, Contact Info, and Application Server fields:
a.
Enter the name of the application, for example, MyApplication.
b.
Enter a brief description of the application.
c.
Enter contact information, for example, the email address of the application owner.
d.
Enter the application server related information, for example, an IP address, host name, or platform of the server machine.
e.
Application Server: Enter the application server in which the new application is running.
f.
Enable Delegation: If you check this check box while creating or updating an application, the selected application will be available for Copy Entitlement, which allows you to entitle all the policies of a PEP user created on this application and its resources to other PEP users. For more information, refer to Copy Entitlement.
g.
Enable Xacml Logs: Check the Enable Xacml logs check box to enable runtime log generation for the new application. If you uncheck this check box, you cannot view the runtime application logs in the server side and in the PAP console as well.
h.
Enable Virtual Resources: Enabling partial fully qualified name (FQN) means giving a decision for the resource FQN passed in the request on the basis of the parent level in the absence of the requested resource.
For example, when a request for Prime Group:Prime Portal:View reports: Report10 is sent to the PDP, though no resource called Report10 exists, the PDP will give the decision on the parent level of Report10. That is, view reports only if the Enable Partial FQN field is checked for the application Prime Portal.
i.
Combine with inherited policies: Check the Combine with inherited policies check box for the requested resource to inherit its policies, all its parent policies and the application policies.
For example, consider a resource called Res2 under resource Prime group:Prime portal:Res1. Resource Res1 is having Allow:Internal Dev policy and resource Res2 is having Allow: Internal Dev Tokyo policy and the application Prime Portal is having Allow:Internal Dev London policy.
If the Combine with inherited policies check box is checked for the application and the request for Prime group:Prime portal:Res1:Res2 is sent, it will get all the three policies, such as Internal Dev Tokyo (itself), Internal Dev (its parent), and Internal Dev London (application policy). Then PDP will give the decision after applying the policy-combining algorithm.
j.
Application Type: Choose the Application Type from the drop-down list. If Default is considered as the application type. For more details about application type, refer chapter.
k.
PDP: Choose the application server to be associated with the new application. In the runtime process, when the PEP sends a request, it will hit the selected PDP and the PDP will respond the request by querying the concerned database and gives the appropriate decision. You can select multiple PDPs for a single application. This helps the PDP decision making proceed uninterrupted even if one of the PDPs is shutdown.
In the Agent-PDP section, the PDP box contains all existing PDPs registered under the application. While creating a new application, you need to select PDP(s) to be associated with it. The main purpose of selecting multiple PDPs is to make it possible for the remaining PDPs to respond the request if the first PDP fails.
l.
Check the appropriate mode of Data Transportation. By default, CEPM supports HTTP, SOAP, and RMI.
m.
Click Create to add the new application to the existing list of applications.
Creating Resources
Resources model the objects that are accessed (or which you want to secure) within your physical application. See the Cisco Enterprise Policy Manager Concepts Guide V 3.3.0.0 and the Cisco Enterprise Policy Manager Resource and Subject Modeling Best Practices Guide for further details on resources and modeling them within CEPM. These are the static resources. If you want to define dynamic resources or resources stored in a database, you do this using rules in a policy. An example of this would be patient claim data stored in a database. In this case, you would create a static resource, claims, for example, and then create an allow policy with rules to define the access to the claims or claim data. In this case, the rules would use dynamic database queries or procedures (called application attribute sources) to evaluate, and based on these rules, access would either be allowed or denied. For further information on dynamic rules and application attribute sources, see the Cisco Enterprise Policy Manager User Guide and Cisco Enterprise Policy Manager Concepts Guide.
To add new resources to an application, follow these steps:
Step 1
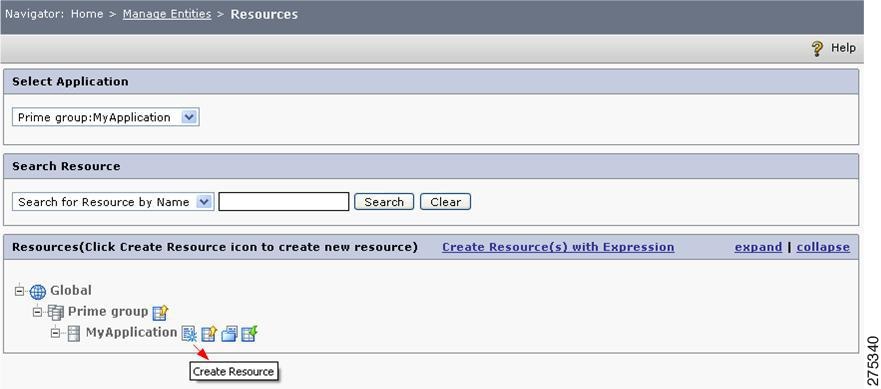
Choose Manage Entities > Resources.
The Resources page is displayed, which contains the list of application groups, applications, and resources under the Global context.
Figure 1-8 Resource Page
Step 2
To create a new resource under the application MyApplication, click the Create Resource icon next to the application MyApplication.
The Create Resource page is displayed.
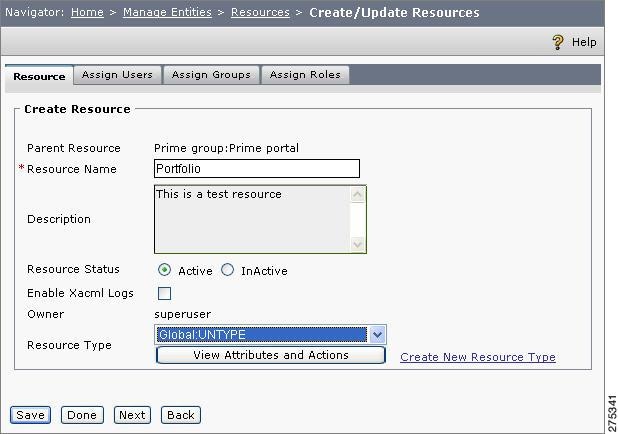
Figure 1-9 Create or Update Resources
Step 3
Enter a name for the resource (for example, MyResource) and a brief description about the resource.
Step 4
Click Active from the Resource Status radio button.
Step 5
Enable Xacml Logs: Check the Enable Xacml logs checkbox enables the log tracking of this resource.
Step 6
Owner: This displays the owner name (Superuser or any other the PAP User name).
Step 7
Resource Type: Choose appropriate resource type for the drop-down list.To create a resource select Global:UNTYPE from the drop-down list.
Click View Attributes and Action displays the attributes associated with the resource type. You can create a new resource type by clicking the Create New Resource Type link. For details on how to create and use resource types, refer to the Cisco Enterprise Policy Manager User Guide.
Step 8
Click Save.
This creates the new resource in the PAP under the selected application, MyApplication.
You can also assign users, groups, and roles to this resource by clicking Next or by clicking the appropriate tab (Assign Users, Assign Groups, or Assign Roles) directly. Click Done after you have assigned appropriate users, groups, and roles to this resource.
You can add a new child resource under this newly created resource by clicking the Create Resource icon next to the newly created resource. You can also create additional resources for the application by repeating this entire process.
Creating Roles
CEPM supports the creation of roles, which are then used in creating policies. This mechanism is called Roles-based Access Control (RBAC). It is not mandatory to create RBAC policies in CEPM (which also supports group-based, user-based, and rule-based policies), but RBAC is an industry best practice and is the typical way to cretate policies.
Roles are created in CEPM under an application, application group, or role. The creation of a role under an application is referred to as an application or application-specific role. The following example creates an application role.
To create an application role, follow these steps:
Step 1
Choose Manage Entities > Roles.
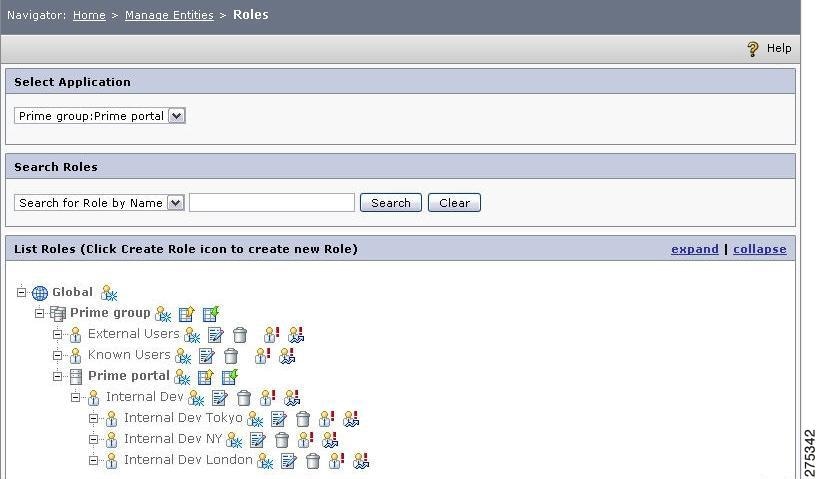
The List of Roles page is displayed.
Figure 1-10 Roles Page
Step 2
Click the Create Role icon next to the application under which you want to create the new role (in this case, the MyApplication application).
The Create Role page is displayed. (To create a role under an application group, application, or role, click the Create Role icon next to the application group, application, or role under which you want to create the role.)
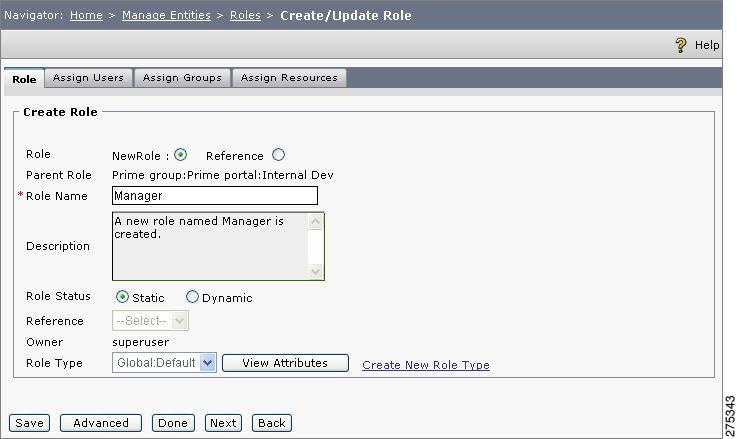
Figure 1-11 Create or Update Role
Step 3
Click the NewRole radio button. (A reference is a way to reference an existing role for the application or application group and is discussed in detail in the Cisco Enterprise Policy Manager User Guide.)
Step 4
Enter the Role Name, for example, Manager.
Step 5
Enter a brief Description of the new role.
Step 6
For Role Status, click the Static radio button. (Dynamic Roles include Rule(s), which determine membership at the runtime and are discussed in detail in the Cisco Enterprise Policy Manager User Guide.)
Step 7
Choose the Reference Role from the Refrence drop-down list. This is enabled only if you create the role as a Reference Role. Select the appropriate Reference Role from this list.
Step 8
Choose the Role Type. (For our example, select Global:Default. Just like resources, roles can be of a particular type in CEPM. For more information about creating role types, refer to the Cisco Enterprise Policy Manager User Guide.)
Step 9
Click Save. The new role in is created in the PAP.
You can also assign users, groups, and resources to this role by clicking Next or by clicking the appropriate tab directly. Click Done after you have assigned appropriate users, groups, and resources to this role.
Repeat this same procedure to create any additional roles that you may need.
Creating Users
CEPM supports users in multiple ways. The users described in this section are application users and not users of the administration console (although most of the same concepts apply to both sets of users within CEPM). These users are also referred to as a subject in the application or Policy Enforcement Point (PEP). It is important to note that a subject is not the same as a user. A user is actually stored somewhere (in CEPM, in a directory or database, or elsewhere), whereas a subject is just an identifier (typically in the form of a string) of the user (or entity) performing a transaction.
CEPM supports users in the following three ways:
•
Users can be created in CEPM database (or entitlement repository).
•
Users can be imported (and synchronized) into CEPM database from LDAP directory by creating user attribute sources.
•
Users can be referenced externally if they exist in a supported database or LDAP directory. This is done by using an application attribute source to reference the users and by using the external users role or a dynamic role.
CEPM also supports users stored in various other systems (such as, provisioning systems, legacy databases, flat files, and meta directories) by using Java Application Attribute Source.
Some use cases require all of the mechanisms identified here for creating and accessing application users. However, for a basic use case, you need an easy way to create users and therefore only users created in CEPM entitlement repository (internal users) are discussed in this guide. Another reason to use internal users is that there is no other available way to manage users within the application environment. A reason for importing the users (and not referencing them externally) could be the need to create additional attributes that an external repository does not or will not support (CEPM supports type-casting internal users).
You might want to reference users externally (using external users) for the following reasons:
•
You do not want to synchronize or duplicate the external user records.
•
Users are already being managed in an external source with all of the required attributes for authorization.
For details on working with users using various mechanisms, refer to the Cisco Enterprise Policy Manager User Guide, v3.0.
To create a new user in the entitlement repository, follow these steps:
Step 1
Choose Manage Entities > Users.
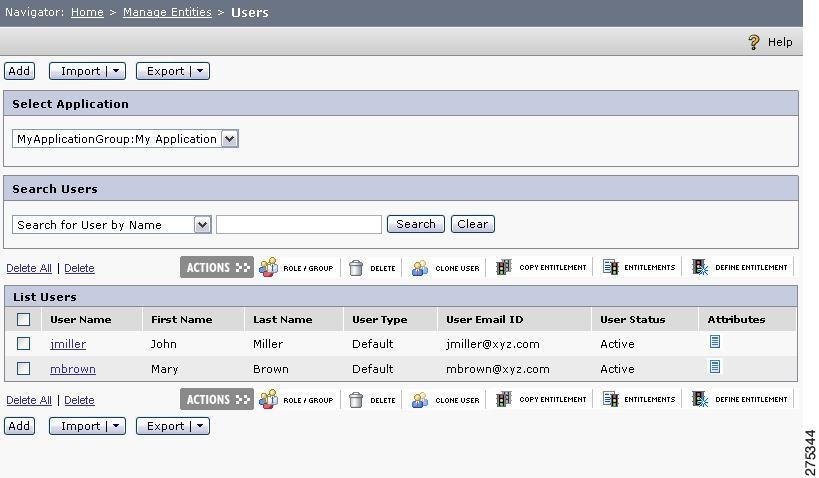
The Users List page is displayed, which provides the functionality of managing users for the selected application or application group.
Step 2
Choose the application or application group from the Select Application drop-down list (for this example, select the MyApplicationGroup:MyApplication application).
Figure 1-12 Users Page
Step 3
Click Add.
The Create User page is displayed.
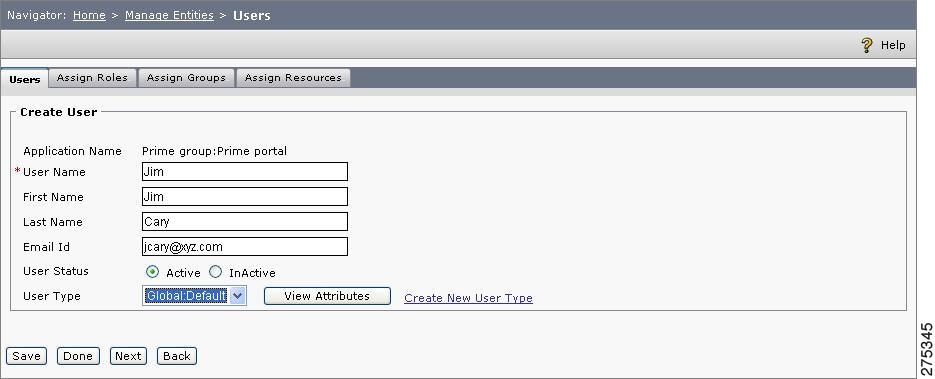
Figure 1-13 Create Users
Step 4
Enter the values for User Name, First Name, Last Name, and User Email ID.
Step 5
Choose the User Type. (In this example, choose Global:Default.) Just like with resources and roles, users can also be of a particular type in CEPM. A particular user type can include specific attributes that can be used for users of that type. For additional details on creating user types, refer to the Cisco Enterprise Policy Manager User Guide.
Step 6
Click Save.
You can also assign roles, groups and resources to this user by clicking Next or by clicking the appropriate tab directly. Click Done after you have assigned appropriate roles, groups, and resources to this user.
Mapping Users to Roles
After roles and users are created, you can map the users to the roles. One of the ways of mapping users to roles is explained here.
To map a user to a role, follow these steps:
Step 1
Choose Manage Entities > Entity Assignments > Add Users To Roles.
The User Role Map page is displayed.
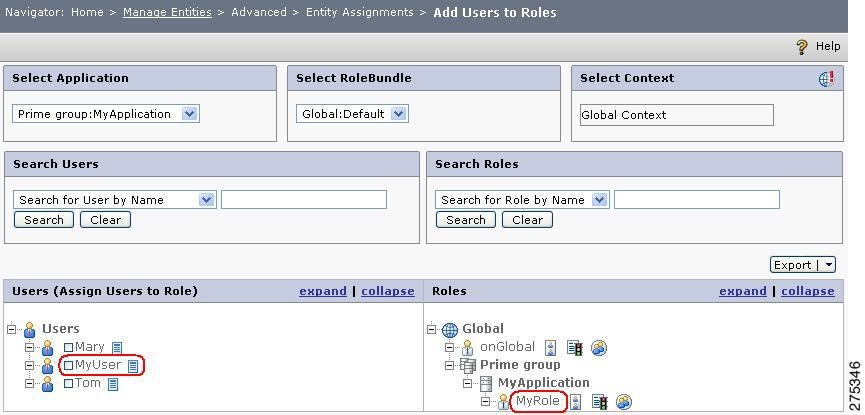
Figure 1-14 Add Users to Role
The User Role Map page has four areas.
•
The first area is where you select the application or application group for which you want to map users to roles. In this example, this is the MyApplicationGroup:MyApplication application.
•
The second area of the page contains two search options, Search for User by name and Search for Role by name, which you can use to search for the user, role or both without traversing through the user or role hierarchy.
•
The third area contains the Role Bundle list and Context button, which should set to Global:Default and Global Context, respectively. Role Bundles and Contexts are covered in detail in the Cisco Enterprise Policy Manager User Guide.
•
The fourth area displays two tree structures that list the users and roles for the application group or application. This is where the mapping of users to roles is done.
Step 2
Check the check box to the left of the requisite user name to choose the user (MyUser) that you want to map to a role (MyRole).
Step 3
Click the Map Users icon that is to the right of the role (MyRole) to which you want to map the selected user (MyUser).
Thus, in this example, the user MyUser is mapped to the role MyRole.
Creating Resource-based Policies
A policy decides whether a subject (generally, the application user) has access permissions for a particular resource. This guide provides procedures to create a resource-based policy. CEPM also supports role-, group-, and user-based policies. For further details on these types of policies, refer to the Cisco Enterprise Policy Manager User Guide.
A policy can also contain one or more rules. Rules can be either Dynamic or Static, and they typically use additional data beyond just the subject and the static resource name to evaluate. The policy evaluation (true or false) translates into the policy returning either an allow (access granted) or deny (access restricted) for the subject. Rules are covered in more detail in the Cisco Enterprise Policy Manager User Guide.
A resource-based policy is a policy that you create by assigning a role to a resource. You can create either an allow or a deny policy. The following example creates an allow policy on a resource.
To create a resource-based policy, follow these steps:
Step 1
Choose Manage Entitlements > By Resources.
Step 2
In the Select Application field, choose MyApplicationGroup:MyApplication application.
The Policy Management page shows the collapsed Roles and Resources lists. Click the expand link in the upper right of the Roles and Resources list sections to expand the lists.
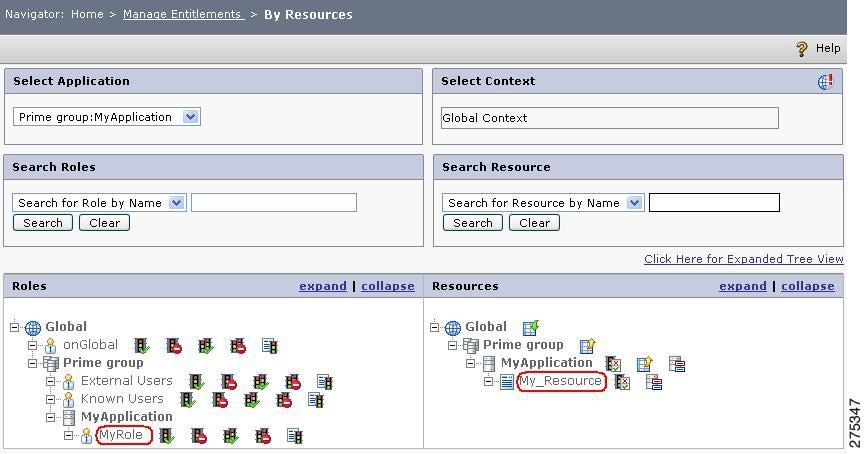
Figure 1-15 By Resources
Step 3
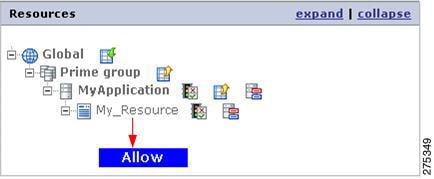
Double-click the Allow icon to the right of the MyRole role. A blue box with the selected policy will hover next to the mouse pointer.
Figure 1-16 Roles
Step 4
Move the mouse to the Resource tree and click the MyResource resource.
Figure 1-17 Resources
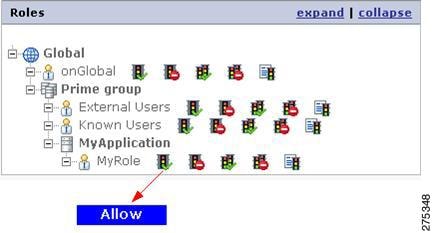
This creates an allow policy for the MyRole role on the MyResource resource and an allow policy for the selected role is displayed under the resource.
Figure 1-18 Allow Resource
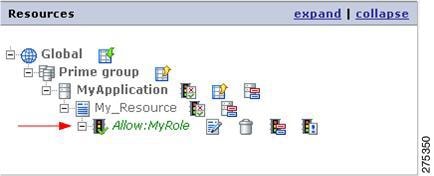
You may also double-click the Deny icon present near the role name to map the Deny policy for the selected role for the selected resource.
This completes the setup for policies in the administration console.
Next, you can test the policies you have created using the Review Entitlement function in the administration console, and then you will use these policies in a PEP.
Reviewing Policies with Audit Entitlement
CEPM provides monitoring capabilities in the administration console. Part of this functionality includes the ability to review entitlements. Entitlements can be reviewed based on user, group, role, or resource. In this example, you will review the entitlements based on user.
To access the Audit Entitlement function, follow these steps:
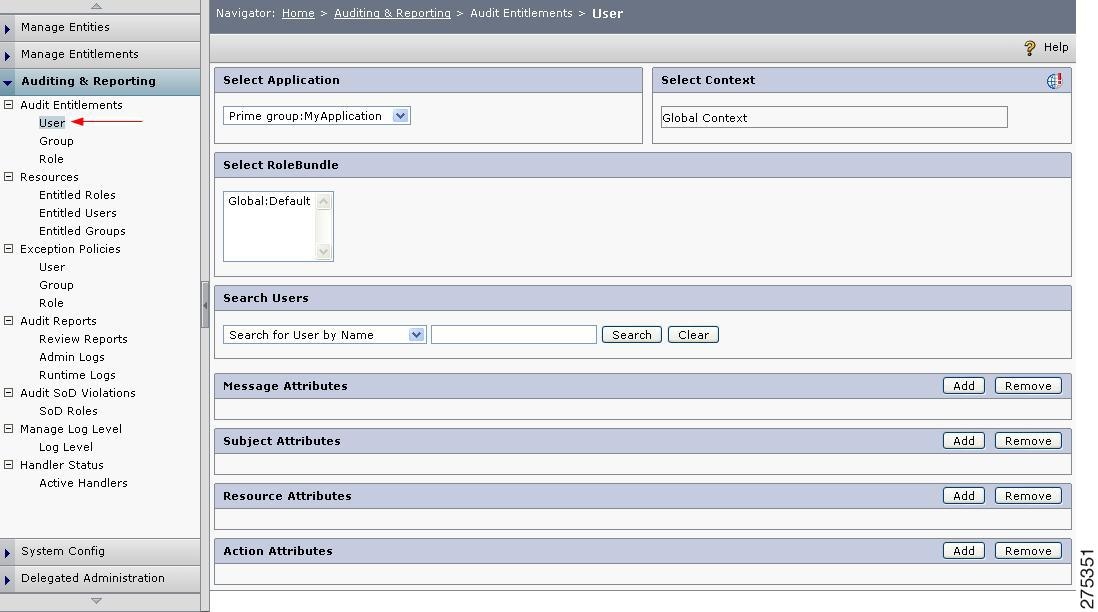
Step 1
Choose Auditing & Reporting > Audit Entitlements > User.
The Audit Entitlements By User page is displayed.
Figure 1-19 Audit Entitlement by Users
Step 2
From the Application list, choose MyApplicationGroup: MyApplication.
Step 3
In the Search Users field, enter MyUser.
Step 4
Click Search.
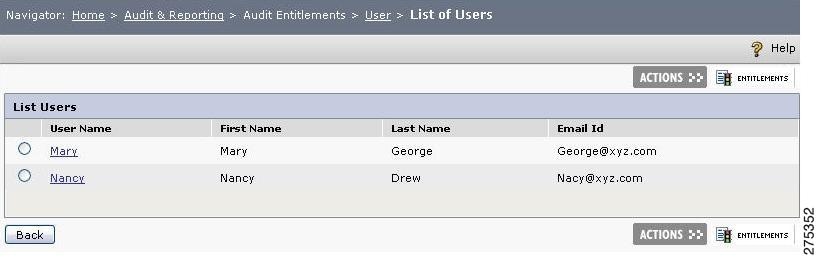
The List of Users page is displayed, with MyUser as one of the rows.
Figure 1-20 List of Users
Step 5
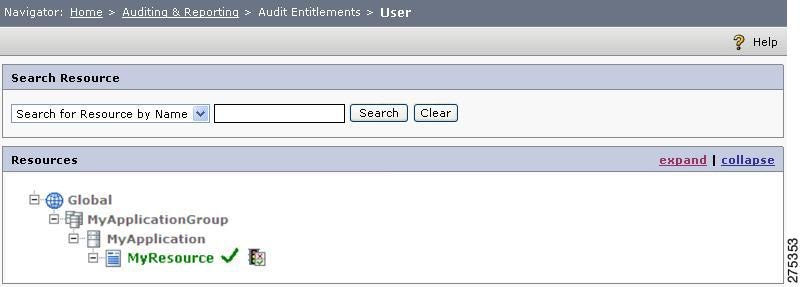
Select the MyUser check box and click the ENTITLEMENTS icon.
The List Entitlements page is displayed. Click the plus (+) sign next to the resources until MyResource is displayed. (You may also click the expand link so as to display the complete hierarchy.)
Figure 1-21 Audit Entitlement
Note
It may take a few seconds for the MyResource resource to appear after clicking the MyApplication application. This is because the PEP embedded in the administration console is making a request to the PDP defined for the MyApplication application to get all of the decisions for the defined resources for MyUser.
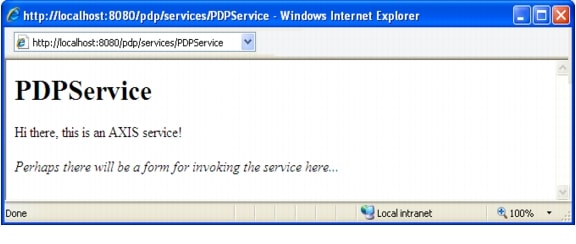
If everything is working fine and has been configured correctly, you will see the MyResource resource appear in Green with tick mark near it. This indicates that MyUser is allowed to access the MyResource resource. If the resource does not appear or if MyResource appears in Red with a cross mark, then something is configured incorrectly or the PDP is not working. If this is the case, revalidate that you have configured everything correctly, and that your PDP is accessible on the Host and Port specified in the PDP configuration. You can do this by accessing http://Host:Port/pdp/services/PDPService in your web browser. You should see the following message
Figure 1-22 PDP message window
If you do not see this message, refer to the Cisco Enterprise Policy Manager Installation and Configuration Guide to correct this issue before proceeding further.
Using Policies with a PEP
In this section we will test our policies with a PEP. The PEP is the decision enforcement API provided by CEPM. The PEP comes in two main types: Java-based and C-based. The Java-based API is used in this section for giving examples. CEPM includes a Java program with the PEP installation called the PEP Simulator. The PEP Simulator is a PEP simulator Java console program that includes all of the appropriate Java classes for the PEP for making a request to the PDP. Also included are the necessary configuration files for the PEP.
To configure the PEP Simulator, follow these steps:
Step 1
Install the Java Development Kit (JDK) on the machine on which you will be running the PEP Simulator program. You can run the PEP Simulator from the server where you configured the PAP and PDP, in which case a JDK will be already be available.
Step 2
Install the PEP Simulator by unzipping it into the C:\PEPSimulator directory on Windows or /PEPSimulator directory on Linux or UNIX. Note: You that you can use any directory name. This example assumes you have chosen the directory name as PEPSimulator.
Step 3
Start a command line window or shell.
•
For Windows, choose Start > run, and type cmd, and press Enter key.
•
For Linux or UNIX, telnet to the machine or start a new shell.
In either case, this will be referred to as the shell for the remainder of this guide.
Step 4
Enter the PEPSimulator directory.
•
For Windows: cd\PEPSimulator
•
For Linux or UNIX: cd/PEPSimulator
Step 5
Set the classpath in your shell.
Ensure that:
•
pep-v3.3.0.0_[YYYYMMDD].jar matches the PEP jar that is included with your version of the PEP Simulator.
Note
Here [YYYYMMDD] is a variable name and is the timestamp of the particular PEP release, where: YYYY=Year, MM=Month and DD=Day. Example, PEP JAR having version 3.0 and released on 30th April 2007 will have the file name of pep-v3.3_20070430.jar.
•
pep-v3.0_[YYYYMMDD].jar is set in your classpath.
Example for Windows:
set classpath=.;./pep-v3.3_[YYYYMMDD].jarExample for Linux or Unix:
export CLASSPATH=.;./pep-v3.3_[YYYYMMDD].jarStep 6
Edit the pep_config.xml file as follows:
a.
Set the value of <applicationgroup> to MyApplicationGroup.
b.
Set the value of <application> to MyApplication.
In the <pdps> section, make the following changes:
c.
Set the value of <username> to admin.
d.
Set the value of <password> to ieryRDe9fQtEq6iEZjvEnQ==. This value is obtained by running the encryptor.bat file included with CEPM installer and passing the string password to it.
e.
Set the value of <url> to http://Host:Port/pdp/services/PDPService, where:
Host is the host machine name or IP address of the machine where the pdp.war application is running and Port is the port at which the pdp.war application is running on.
In the <http-proxy> section, make the following changes:
f.
If you do not have a forward proxy between the machine running the PEP Simulator and the PDP, then delete the values of <host> and <port>.
g.
If you have a forward proxy between the machine running the PEP Simulator and the PDP, then set the value of <host> to the forward proxy host or IP address, and set the value of <port> to the forward proxy port.
In the <apis> section, make the following changes:
h.
Set the value of <username> to superuser.
i.
Set the value of <password> to h1BYu+lcwcM=. This value is obtained by running the encryptor.bat file included with CEPM installer and passing the string admin to it.
j.
Set the value of <url> to http://Host:Port/securent, where:
Host is the host machine name or IP address of the machine where pap.war application is running and Port is the port at which the pap.war application is running.
k.
Save the pep_config.xml file.
The final pep_config.xml file should look like the one in Appendix A, "PEP Configuration File."
Step 7
Edit the PEPSimulator.java file as shown below:
import net.securent.util.pep.*;import net.securent.pdp.user.UserContext;import java.util.*;public class PEPSimulator{public static void main(String x[]) throws Exception{String subject = "MyUser";String resource = "MyApplicationGroup:MyApplication:MyResource";String action = "any";IAuthorizationManager mgr =AuthorizationManagerFactory.getInstance().getAuthorizationManager();System.out.println(mgr.isUserAccessAllowed(subject, resource, action));System.exit(1);}}Step 8
Compile the PEPSimulator.java file by running the following command:
javac PEPSimulator.java
Note
Ensure that javac is in your PATH. javac is located in the <JDK_HOME>/bin/ directory.
Step 9
Now run the PEPSimulator.class file by running the following command:
java -Dlog4j.configuration=./logging.xml -Dsecurent.agentconfig=./pep_config.xml;./oscache.properties -cp ;.;./pep-v3.0_[YYYYMMDD].jar;./jbosscache.xml;./servlet-api.jar;./commons-httpclient-2.0.j ar PEPSimulator
Note
The command must be on one line and java must be in your PATH. java is located in <JDK_HOME>/bin.
When you execute the PEPSimulator.class, the PEP connects to the PDP and calls the isUserAccessAllowed() method. The PDP returns a response indicating whether or not you are allowed to access the given resource with the given action. In string form, this is either true or false. The IAuthorizationManager object is capable of containing additional information about the response from the PDP, including such things as the XACML response and any obligations. For further information on the PEP APIs, including the IAuthorizationManager object, see the Cisco Enterprise Policy Manager Developers Guide.
What's Next?
For additional information on the administration console and the features available that are not covered here, refer to the Cisco Enterprise Policy Manager User Guide.
For additional information on the PEP and PAP APIs, refer to the Cisco Enterprise Policy Manager Developers Guide.
For general information on entitlement management and CEPM, refer to the Cisco Enterprise Policy Manager Concepts Guide.
Cisco has also published several whitepapers on entitlements management that are not specific to CEPM, but provide very good overview of the potential capabilities of a solution like CEPM. One example is the Security in a Service-Oriented Architecture whitepapers.

 Feedback
Feedback