Table Of Contents
Bidirectional Forwarding Detection
Prerequisites for Bidirectional Forwarding Detection
Restrictions for Bidirectional Forwarding Detection
Information About Bidirectional Forwarding Detection
BFD Support on Cisco 12000 Routers
Benefits of Using BFD for Failure Detection
How to Configure Bidirectional Forwarding Detection
Configuring BFD Session Parameters on the Interface
Configuring BFD Support for Routing Protocols
Configuring BFD Support for BGP
Configuring BFD Support for EIGRP
Configuring BFD Support for IS-IS
Configuring BFD Support for OSPF
Configuring BFD Support for HSRP
Configuring the BFD Slow Timer
Disabling BFD Echo Mode Without Asymmetry
Monitoring and Troubleshooting BFD
Monitoring and Troubleshooting BFD for Cisco 7600 Series Routers
Monitoring and Troubleshooting BFD for Cisco 12000 Series Routers
Monitoring and Troubleshooting BFD for Cisco 10720 Internet Routers
Configuration Examples for Bidirectional Forwarding Detection
Configuring BFD in an EIGRP Network with Echo Mode Enabled by Default: Example
Configuring BFD in an OSPF Network: Example
Configuring BFD in a BGP Network: Example
Configuring BFD in an IS-IS Network: Example
Configuring BFD in an HSRP Network: Example
Feature Information for Bidirectional Forwarding Detection
Bidirectional Forwarding Detection
This document describes how to enable the Bidirectional Forwarding Detection (BFD) protocol. BFD is a detection protocol designed to provide fast forwarding path failure detection times for all media types, encapsulations, topologies, and routing protocols. In addition to fast forwarding path failure detection, BFD provides a consistent failure detection method for network administrators. Because the network administrator can use BFD to detect forwarding path failures at a uniform rate, rather than the variable rates for different routing protocol hello mechanisms, network profiling and planning will be easier, and reconvergence time will be consistent and predictable.
Finding Feature Information in This Module
Your Cisco IOS software release may not support all of the features documented in this module. To reach links to specific feature documentation in this module and to see a list of the releases in which each feature is supported, use the "Feature Information for Bidirectional Forwarding Detection" section.
Finding Support Information for Platforms and Cisco IOS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS and Catalyst OS software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Contents
•
Prerequisites for Bidirectional Forwarding Detection
•
Restrictions for Bidirectional Forwarding Detection
•
Information About Bidirectional Forwarding Detection
•
How to Configure Bidirectional Forwarding Detection
•
Configuration Examples for Bidirectional Forwarding Detection
•
Feature Information for Bidirectional Forwarding Detection
Prerequisites for Bidirectional Forwarding Detection
•
Cisco Express Forwarding (CEF) and IP routing must be enabled on all participating routers.
•
You must enable Cisco Parallel eXpress Forwarding (PXF) on the Cisco 10720 Internet router in order for BFD to operate properly. PXF is enabled by default and is generally not turned off.
•
One of the IP routing protocols supported by BFD must be configured on the routers before BFD is deployed. You should implement fast convergence for the routing protocol that you are using. See the IP routing documentation for your version of Cisco IOS software for information on configuring fast convergence. See the "Restrictions for Bidirectional Forwarding Detection" section for more information on BFD routing protocol support in Cisco IOS software.
Restrictions for Bidirectional Forwarding Detection
•
For the current Cisco implementation of BFD for Cisco IOS Releases 12.2(18)SXE, 12.0(31)S, 12.4(4)T, 12.0(32)S, , 12.2(33)SRA, and 12.2(33)SRB, only asynchronous mode is supported. In asynchronous mode, either BFD peer can initiate a BFD session.
•
For the current Cisco implementation of BFD for Cisco IOS Releases 12.2(18)SXE, 12.0(31)S, 12.4(4)T, 12.0(32)S, 12.2(33)SRA, and 12.2(33)SRB, BFD is supported only for IPv4 networks.
•
For Cisco IOS Release 12.2(33)SRB, the Cisco implementation of BFD supports only the following routing protocols: BGP, EIGRP, IS-IS, and OSPF.
•
For Cisco IOS Release 12.2(33)SRA, the Cisco implementation of BFD supports only the following routing protocols: BGP, IS-IS, and OSPF.
•
For Cisco IOS Release 12.4(4)T, the Cisco implementation of BFD supports only the following routing protocols: Border Gateway Protocol (BGP), Enhanced Interior Gateway Routing Protocol (EIGRP), Intermediate System-to-Intermediate System (IS-IS), and Open Shortest Path First (OSPF).
•
For Cisco IOS Release 12.4(11)T, the Cisco implementation of BFD introduced support for the Hot Standby Router Protocol (HSRP). BFD support is not available for all platforms and interfaces. In Cisco IOS Release 12.4(11)T, this feature was introduced on Cisco 7200 series, Cisco 7600 series, and Cisco 12000 series routers.
•
For Cisco IOS Releases 12.0(31)S and 12.0(32)S, the Cisco implementation of BFD supports only the following routing protocols: BGP, IS-IS, and OSPF.
•
For Cisco IOS Release 12.2(18)SXE, the Cisco implementation of BFD supports only the following routing protocols: EIGRP, IS-IS, and OSPF.
•
BFD works only for directly connected neighbors. BFD neighbors must be no more than one IP hop away. Multihop configurations are not supported.
•
BFD support is not available for all platforms and interfaces. To confirm BFD support for a specific platform or interface and obtain the most accurate platform and hardware restrictions, see the Cisco IOS software release notes for your software version.
•
On the Cisco 10720 Internet router, BFD is supported only on Fast Ethernet, Gigabit Ethernet, and RPR-IEEE interfaces. BFD is not supported on Spatial Reuse Protocol (SRP) and Packet-over-SONET (POS) interfaces.
•
When you configure the BFD session parameters on a Cisco 10720 interface using the bfd command (in interface configuration mode), the minimum configurable time period supported for the milliseconds argument in both the interval milliseconds and min_rx milliseconds parameters is 50 milliseconds.
•
A maximum of 100 BFD sessions are supported on the Cisco 10720 Internet router. When BFD tries to set up a connection between routing protocols and establish a 101th session between a Cisco 10720 Internet router and adjacent routers, the following error message is displayed:
00:01:24: %OSPF-5-ADJCHG: Process 100, Nbr 10.0.0.0 on RPR-IEEE1/1 from LOADING to FULL, Loading Done 00:01:24: %BFD-5-SESSIONLIMIT: Attempt to exceed session limit of 100 neighbors.•
The Cisco 10720 Internet router does not support the following BFD features:
–
Demand mode
–
Echo packets
–
BFD over IP Version 6
•
On the Cisco 12000 series router, asymmetrical routing between peer devices may cause a BFD control packet to be received on a line card other than the line card that initiated the session. In this special case, the BFD session between the routing peers will not be established.
•
A maximum 100 sessions per line card are supported for the distributed Cisco 12000 series Internet router. The minimum hello interval is 50 ms with up to three Max retries for a BFD control packet to be received from a remote system before a session with a neighbor is declared down.
Note
For the most accurate platform and hardware restrictions, see the Cisco IOS software release notes for your software version.
Information About Bidirectional Forwarding Detection
Before you configure BFD, you should become familiar with the information in the following sections:
•
Benefits of Using BFD for Failure Detection
BFD Operation
BFD provides a low-overhead, short-duration method of detecting failures in the forwarding path between two adjacent routers, including the interfaces, data links, and forwarding planes. BFD is a detection protocol that you enable at the interface and routing protocol levels. Cisco supports the BFD asynchronous mode, which depends on the sending of BFD control packets between two systems to activate and maintain BFD neighbor sessions between routers. Therefore, in order for a BFD session to be created, you must configure BFD on both systems (or BFD peers). Once BFD has been enabled on the interfaces and at the router level for the appropriate routing protocols, a BFD session is created, BFD timers are negotiated, and the BFD peers will begin to send BFD control packets to each other at the negotiated interval.
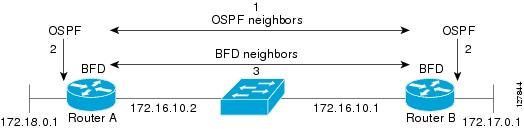
BFD provides fast BFD peer failure detection times independently of all media types, encapsulations, topologies, and routing protocols BGP, EIGRP, IS-IS, and OSPF. By sending rapid failure detection notices to the routing protocols in the local router to initiate the routing table recalculation process, BFD contributes to greatly reduced overall network convergence time. Figure 1 shows a simple network with two routers running OSPF and BFD. When OSPF discovers a neighbor (1) it sends a request to the local BFD process to initiate a BFD neighbor session with the OSPF neighbor router (2). The BFD neighbor session with the OSPF neighbor router is established (3).
Figure 1 Establishing a BFD Neighbor Relationship
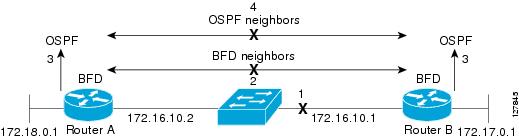
Figure 2 shows what happens when a failure occurs in the network (1). The BFD neighbor session with the OSPF neighbor router is torn down (2). BFD notifies the local OSPF process that the BFD neighbor is no longer reachable (3). The local OSPF process tears down the OSPF neighbor relationship (4). If an alternative path is available the routers will immediately start converging on it.
Figure 2 Tearing Down an OSPF Neighbor Relationship
BFD Detection of Failures
Once a BFD session has been established and timer negations are complete, BFD peers send BFD control packets that act in the same manner as an IGP hello protocol to detect liveliness, except at a more accelerated rate. The following information should be noted:
•
BFD is a forwarding path failure detection protocol. BFD detects a failure, but the routing protocol must take action to bypass a failed peer.
•
Typically, BFD can be used at any protocol layer. However, the Cisco implementation of BFD for Cisco IOS Releases 12.2(18)SXE, 12.0(31)S, and 12.4(4)T supports only Layer 3 clients, in particular, the BGP, EIGRP, IS-IS, and OSPF routing protocols.
•
Cisco devices will use one BFD session for multiple client protocols in the Cisco implementation of BFD for Cisco IOS Releases 12.2(18)SXE, 12.0(31)S, and 12.4(4)T. For example, if a network is running OSPF and EIGRP across the same link to the same peer, only one BFD session will be established, and BFD will share session information with both routing protocols.
BFD Version Interoperability
Cisco IOS Release 12.4(9)T supports BFD Version 1 as well as BFD Version 0. All BFD sessions come up as Version 1 by default and will be interoperable with Version 0. The system automatically performs BFD version detection, and BFD sessions between neighbors will run in the highest common BFD version between neighbors. For example, of one BFD neighbor is running BFD Version 0 and the other BFD neighbor is running Version 1, the session will run BFD Version 0. The output from the show bfd neighbors [details] command will verify which BFD version a BFD neighbor is running.
See the "Configuring BFD in an EIGRP Network with Echo Mode Enabled by Default: Example" section for an example of BFD version detection.
BFD Support on Cisco 12000 Routers
The Cisco 12000 series routers support distributed BFD to take advantage of its distributed Route Processor (RP) and line card (LC) architecture. The BFD tasks will be divided and assigned to the BFD process on RP and LC as described in the following sections:
BFD Process on the RP
Client Interaction
The BFD process on the RP will handle the interaction with clients, which create and delete BFD sessions.
Session Management for BFD Process on the RP
The BFD RP process will primarily own all BFD sessions on the router. It will pass the session creation and deletion requests to the BFD processes on all LCs. BFD LC sessions will have no knowledge of sessions being added or deleted by the clients. Only the BFD RP process will send session addition and deletion commands to the BFD LC process.
Session Database Management
The BFD RP process will maintain a database of all the BFD sessions on the router. This database will contain only the minimum required information.
Process EXEC Commands
The BFD RP process services the BFD show commands.
BFD Process on the LC
Session Management for BFD Process on the LC
The BFD LC process manages sessions, adds and deletes commands from the BFD RP process, and creates and deletes new sessions based on the commands. In the event of transmit failure, receive failure, or session down detection, the LC BFD instance will immediately notify the BFD RP process. It will also update transmit and receive counters. The BFD session is maintained completely on the LC. BFD control packets are received and processed, as well as sent, from the LC itself.
Database Management
The BFD LC process maintains a database of all the BFD sessions hosted on the LC.
Receive and Transmit
The BFD LC process is responsible for transmitting and receiving BFD packets for the sessions on the LC.
Benefits of Using BFD for Failure Detection
When you deploy any feature, it is important to consider all the alternatives and be aware of any trade-offs being made.
The closest alternative to BFD in conventional EIGRP, IS-IS, and OSPF deployments is the use of modified failure detection mechanisms for EIGRP, IS-IS, and OSPF routing protocols.
If you set EIGRP hello and hold timers to their absolute minimums, the failure detection rate for EIGRP falls to within a one- to two-second range.
If you use fast hellos for either IS-IS or OSPF, these Interior Gateway Protocol (IGP) protocols reduce their failure detection mechanisms to a minimum of one second.
There are several advantages to implementing BFD over reduced timer mechanisms for routing protocols:
•
Although reducing the EIGRP, IS-IS, and OSPF timers can result in minimum detection timer of one to two seconds, BFD can provide failure detection in less than one second.
•
Because BFD is not tied to any particular routing protocol, it can be used as a generic and consistent failure detection mechanism for EIGRP, IS-IS, and OSPF.
•
Because some parts of BFD can be distributed to the data plane, it can be less CPU-intensive than the reduced EIGRP, IS-IS, and OSPF timers, which exist wholly at the control plane.
How to Configure Bidirectional Forwarding Detection
You start a BFD process by configuring BFD on the interface. When the BFD process is started, no entries are created in the adjacency database, in other words, no BFD control packets are sent or received. BFD echo mode, which is supported in BFD Version 1 for Cisco IOS 12.4(9)T, is enabled by default. BFD echo packets are sent and received in addition to BFD control packets. The adjacency creation takes places once you have configured BFD support for the applicable routing protocols. This section contains the following procedures:
•
Configuring BFD Session Parameters on the Interface (required)
•
Configuring BFD Support for Routing Protocols (required)
•
Configuring BFD Echo Mode (optional)
•
Monitoring and Troubleshooting BFD (optional)
Configuring BFD Session Parameters on the Interface
The steps in this procedure show how to configure BFD on the interface by setting the baseline BFD session parameters on an interface. Repeat the steps in this procedure for each interface over which you want to run BFD sessions to BFD neighbors.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface type number
4.
bfd interval milliseconds min_rx milliseconds multiplier interval-multiplier
5.
end
DETAILED STEPS
Configuring BFD Support for Routing Protocols
You can enable BFD support for routing protocols at the router level to enable BFD support globally for all interfaces or you can configure BFD on a per-interface basis at the interface level.
For Cisco IOS Release 12.2(18)SXE, you must configure BFD support for one or more of the following routing protocols: EIGRP, IS-IS, and OSPF.
For Cisco IOS Releases 12.2(33)SRA, you must configure BFD support for one or more of the following routing protocols: EIGRP, IS-IS, and OSPF.
For Cisco IOS Releases 12.2(33)SRB, you must configure BFD support for one or more of the following routing protocols: BGP, EIGRP, IS-IS, and OSPF.
For Cisco IOS Releases 12.0(31)S and 12.4(4)T, you must configure BFD support for one or more of the following routing protocols: BGP, IS-IS, and OSPF.
For Cisco IOS Release 12.0(32)S, for the Cisco 10720 platform, you must configure BFD for one or more of the following routing protocols: BGP, IS-IS, and OSPF.
For Cisco IOS Release 12.4(11)T, BFD support for HSRP was introduced.
This section describes the following procedures:
•
Configuring BFD Support for BGP (optional)
•
Configuring BFD Support for EIGRP (optional)
•
Configuring BFD Support for IS-IS (optional)
•
Configuring BFD Support for OSPF (optional)
•
Configuring BFD Support for HSRP (optional)
Configuring BFD Support for BGP
This section describes the procedure for configuring BFD support for BGP, so that BGP is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD.
Prerequisites
BGP must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the "Configuring BFD Session Parameters on the Interface" section for more information.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
router bgp as-tag
4.
neighbor ip-address fall-over bfd
5.
end
6.
show bfd neighbors [details]
7.
show ip bgp neighbor
DETAILED STEPS
What to Do Next
See the "Monitoring and Troubleshooting BFD" section for more information on monitoring and troubleshooting BFD. If you want to configure BFD support for another routing protocol, see the following sections:
•
Configuring BFD Support for EIGRP
•
Configuring BFD Support for IS-IS
•
Configuring BFD Support for OSPF
•
Configuring BFD Support for HSRP
Configuring BFD Support for EIGRP
This section describes the procedure for configuring BFD support for EIGRP, so that EIGRP is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD. There are two methods for enabling BFD support for EIGRP:
•
You can enable BFD for all of the interfaces for which EIGRP is routing by using the bfd all-interfaces command in router configuration mode.
•
You can enable BFD for a subset of the interfaces for which EIGRP is routing by using the bfd interface type number command in router configuration mode.
Prerequisites
EIGRP must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the "Configuring BFD Session Parameters on the Interface" section for more information.
Restrictions
BFD for EIGRP is not supported on the Cisco 12000 series routers for Cisco IOS Releases 12.0(31)S, 12.0(32)S, 12.4(4)T, and 12.2(33)SRA.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
router eigrp as-number
4.
log-adjacency-changes [detail]
5.
bfd all-interfaces
or
bfd interface type number6.
end
7.
show bfd neighbors [details]
8.
show ip eigrp interfaces [type number] [as-number] [detail]
DETAILED STEPS
What to Do Next
See the "Monitoring and Troubleshooting BFD" section for more information on monitoring and troubleshooting BFD. If you want to configure BFD support for another routing protocol, see the following sections:
•
Configuring BFD Support for BGP
•
Configuring BFD Support for IS-IS
•
Configuring BFD Support for OSPF
•
Configuring BFD Support for HSRP
Configuring BFD Support for IS-IS
This section describes the procedures for configuring BFD support for IS-IS, so that IS-IS is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD. There are two methods for enabling BFD support for IS-IS:
•
You can enable BFD for all of the interfaces for which IS-IS is routing by using the bfd all-interfaces command in router configuration mode. You can then disable BFD for one or more of those interfaces using the isis bfd disable command in interface configuration mode.
•
You can enable BFD for a subset of the interfaces for which IS-IS is routing by using the isis bfd command in interface configuration mode.
To configure BFD support for IS-IS, perform the steps in one of the following sections:
•
Configuring BFD Support for IS-IS for All Interfaces
•
Configuring BFD Support for IS-IS for One or More Interfaces
Prerequisites
IS-IS must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces that you want to run BFD sessions to BFD neighbors over must be configured. See the "Configuring BFD Session Parameters on the Interface" section for more information.
Configuring BFD Support for IS-IS for All Interfaces
To configure BFD on all IS-IS interfaces, perform the steps in this section.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
router isis area-tag
4.
bfd all-interfaces
5.
exit
6.
interface type number
7.
isis bfd [disable]
8.
end
9.
show bfd neighbors [details]
10.
show clns interface
DETAILED STEPS
What to Do Next
See the "Monitoring and Troubleshooting BFD" section for more information on monitoring and troubleshooting BFD. If you want to configure only for a specific subset of interfaces, perform the tasks in the "Configuring BFD Support for IS-IS for One or More Interfaces" section.
Configuring BFD Support for IS-IS for One or More Interfaces
To configure BFD for only one or more IS-IS interfaces, perform the steps in this section.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface type number
4.
isis bfd [disable]
5.
end
6.
show bfd neighbors [details]
7.
show clns interface
DETAILED STEPS
What to Do Next
See the "Monitoring and Troubleshooting BFD" section for more information on monitoring and maintaining BFD. If you want to configure BFD support for another routing protocol, see one of the following sections:
•
Configuring BFD Support for BGP
•
Configuring BFD Support for EIGRP
•
Configuring BFD Support for OSPF
•
Configuring BFD Support for HSRP
Configuring BFD Support for OSPF
This section describes the procedures for configuring BFD support for OSPF, so that OSPF is a registered protocol with BFD and will receive forwarding path detection failure messages from BFD. You can either configure BFD support for OSPF globally on all interfaces or configure it selectively on one or more interfaces.
There are two methods for enabling BFD support for OSPF:
•
You can enable BFD for all of the interfaces for which OSPF is routing by using the bfd all-interfaces command in router configuration mode. You can disable BFD support on individual interfaces using the ip ospf bfd [disable] command in interface configuration mode.
•
You can enable BFD for a subset of the interfaces for which OSPF is routing by using the ip ospf bfd command in interface configuration mode.
See the following sections for tasks for configuring BFD support for OSPF:
•
Configuring BFD Support for OSPF for All Interfaces (optional)
•
Configuring BFD Support for OSPF for One or More Interfaces (optional)
Configuring BFD Support for OSPF for All Interfaces
To configure BFD for all OSPF interfaces, perform the steps in this section.
If you do not want to configure BFD on all OSPF interfaces and would rather configure BFD support specifically for one or more interfaces, see the "Configuring BFD Support for OSPF for One or More Interfaces" section.
Prerequisites
OSPF must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the "Configuring BFD Session Parameters on the Interface" section for more information.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
router ospf process-id
4.
bfd all-interfaces
5.
exit
6.
interface name number
7.
ip ospf bfd [disable]
8.
end
9.
show bfd neighbors [details]
10.
show ip ospf
DETAILED STEPS
What to Do Next
See the "Monitoring and Troubleshooting BFD" section for more information on monitoring and troubleshooting BFD. If you want to configure BFD support for another routing protocol, see the following sections:
•
Configuring BFD Support for BGP
•
Configuring BFD Support for EIGRP
•
Configuring BFD Support for IS-IS
•
Configuring BFD Support for HSRP
Configuring BFD Support for OSPF for One or More Interfaces
To configure BFD on one or more OSPF interfaces, perform the steps in this section.
Prerequisites
OSPF must be running on all participating routers.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the "Configuring BFD Session Parameters on the Interface" section for more information.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface type number
4.
ip ospf bfd [disable]
5.
end
6.
show bfd neighbors [details]
7.
show ip ospf
DETAILED STEPS
What to Do Next
See the "Monitoring and Troubleshooting BFD" section for more information on monitoring and troubleshooting BFD. If you want to configure BFD support for another routing protocol, see the following sections:
•
Configuring BFD Support for BGP
•
Configuring BFD Support for EIGRP
•
Configuring BFD Support for IS-IS
•
Configuring BFD Support for HSRP
Configuring BFD Support for HSRP
Perform this task to enable BFD support for Hot Standby Router Protocol (HSRP.) Repeat the steps in this procedure for each interface over which you want to run BFD sessions to HSRP peers.
HSRP supports BFD by default. If HSRP support for BFD has been manually disabled, you can reenable it at the router level to enable BFD support globally for all interfaces or on a per-interface basis at the interface level.
Prerequisites
•
HSRP must be running on all participating routers.
•
Cisco Express Forwarding (CEF) must be enabled.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ip cef [distributed]
4.
interface type number
5.
ip address ip-address mask
6.
standby [group-number] ip [ip-address [secondary]]
7.
standby bfd
8.
exit
9.
standby bfd all-interfaces
10.
exit
11.
show standby [neighbors]
DETAILED STEPS
What to Do Next
See the "Monitoring and Troubleshooting BFD" section for more information on monitoring and troubleshooting BFD. If you want to configure BFD support for another routing protocol, see the following sections:
•
Configuring BFD Support for BGP
•
Configuring BFD Support for EIGRP
•
Configuring BFD Support for IS-IS
•
Configuring BFD Support for OSPF
Configuring BFD Echo Mode
BFD echo mode is enabled by default, but you can disable it such that it can run independently in each direction. Before you configure echo mode you should be familiar with the following concepts:
BFD Echo Mode
Benefits of Running BFD Echo Mode
BFD echo mode works with asynchronous BFD. Echo packets are sent by the forwarding engine and forwarded back along the same path in order to perform detection—the BFD session at the other end does not participate in the actual forwarding of the echo packets. The echo function and the forwarding engine are responsible for the detection process, therefore the number of BFD control packets that are sent out between two BFD neighbors is reduced. And since the forwarding engine is testing the forwarding path on the remote (neighbor) system without involving the remote system, there is an opportunity to improve the interpacket delay variance, thereby achieving quicker failure detection times than when using BFD Version 0 with BFD control packets for the BFD session.
Echo Mode Without Asymmetry
Echo mode is described as without asymmetry when it is running on both sides (both BFD neighbors are running echo mode).
Prerequisites
BFD must be running on all participating routers.
Before using BFD echo mode, you must disable the sending of Internet Control Message Protocol (ICMP) redirect messages by entering the no ip redirects command, in order to avoid high CPU utilization.
The baseline parameters for BFD sessions on the interfaces over which you want to run BFD sessions to BFD neighbors must be configured. See the "Configuring BFD Session Parameters on the Interface" section for more information.
Restrictions
BFD echo mode which is supported in BFD Version 1, is available only in Cisco IOS Releases 12.4(9)T and 12.2(33)SRA.
This section contains the following configuration tasks for BFD echo mode:
•
Configuring the BFD Slow Timer
•
Disabling BFD Echo Mode Without Asymmetry
Configuring the BFD Slow Timer
The steps in this procedure show how to change the value of the BFD slow timer. Repeat the steps in this procedure for each BFD router.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
bfd slow-timer milliseconds
4.
end
DETAILED STEPS
Disabling BFD Echo Mode Without Asymmetry
The steps in this procedure show how to disable BFD echo mode without asymmetry —no echo packets will be sent by the router, and the router will not forward BFD echo packets that are received from any neighbor routers.
Repeat the steps in this procedure for each BFD router.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
[no] bfd echo
4.
bfd echo
5.
end
DETAILED STEPS
Monitoring and Troubleshooting BFD
This section describes how to retrieve BFD information for maintenance and troubleshooting. The commands in these tasks can be entered as needed, in any order desired.
For more information about BFD session initiation and failure, refer to the "BFD Operation" section.
This section contains information for monitoring and troubleshooting BFD for the following Cisco platforms:
•
Monitoring and Troubleshooting BFD for Cisco 7600 Series Routers
•
Monitoring and Troubleshooting BFD for Cisco 12000 Series Routers
•
Monitoring and Troubleshooting BFD for Cisco 10720 Internet Routers
Monitoring and Troubleshooting BFD for Cisco 7600 Series Routers
To monitor or troubleshoot BFD on Cisco 7600 series routers, perform one or more of the steps in this section.
SUMMARY STEPS
1.
enable
2.
show bfd neighbors [details]
3.
debug bfd [packet | event]
DETAILED STEPS
Monitoring and Troubleshooting BFD for Cisco 12000 Series Routers
To monitor or troubleshoot BFD on Cisco 12000 series routers, perform one or more of the steps in this section.
SUMMARY STEPS
1.
enable
2.
attach slot-number
3.
show bfd neighbors [details]
4.
show monitor event-trace bfd [all]
5.
debug bfd event
6.
debug bfd packet
7.
debug bfd ipc-error
8.
debug bfd ipc-event
9.
debug bfd oir-error
10.
debug bfd oir-event
DETAILED STEPS
Monitoring and Troubleshooting BFD for Cisco 10720 Internet Routers
To monitor or troubleshoot BFD on Cisco 10720 Internet routers, perform one or more of the steps in this section.
SUMMARY STEPS
1.
enable
2.
show bfd neighbors [details]
3.
debug bfd event
4.
debug bfd packet
DETAILED STEPS
Configuration Examples for Bidirectional Forwarding Detection
This section provides the following configuration examples:
•
Configuring BFD in an EIGRP Network with Echo Mode Enabled by Default: Example
•
Configuring BFD in an OSPF Network: Example
•
Configuring BFD in a BGP Network: Example
•
Configuring BFD in an IS-IS Network: Example
•
Configuring BFD in an HSRP Network: Example
Configuring BFD in an EIGRP Network with Echo Mode Enabled by Default: Example
12.4(9)T Example
In the following example, the EIGRP network contains RouterA, RouterB, and RouterC. Fast Ethernet interface 0/1 on RouterA is connected to the same network as FastEthernet interface 0/1 on Router B. Fast Ethernet interface 0/1 on RouterB is connected to the same network as Fast Ethernet interface 0/1 on RouterC.
RouterA and RouterB are running BFD Version 1 which supports echo mode, and RouterC is running BFD Version 0, which does not support echo mode. The BFD sessions between RouterC and its BFD neighbors are said to be running echo mode with asymmetry because echo mode will run on the forwarding path for RouteA and RouterB, and their echo packets will return along the same path to for BFD sessions and failure detections, while their BFD neighbor RouterC runs BFD Version 0 and uses BFD controls packets for BFD sessions and failure detections.
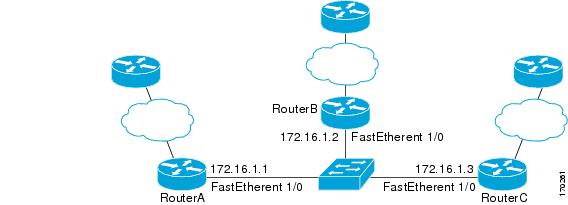
Figure 3 EIGRP Network with Three BFD Neighbors Running V1 or V0
Figure 3 shows a large EIGRP network with several routers, three of which are BFD neighbors that are running EIGRP as their routing protocol.
The example, starting in global configuration mode, shows the configuration of BFD.
Configuration for RouterA
interface FastEthernet0/0no shutdownip address 10.4.9.14 255.255.255.0duplex autospeed auto!interface FastEthernet0/1ip address 172.16.1.1 255.255.255.0bfd interval 50 min_rx 50 multiplier 3no shutdownduplex autospeed auto!router eigrp 11network 172.16.0.0bfd all-interfacesauto-summary!ip default-gateway 10.4.9.1ip default-network 0.0.0.0ip route 0.0.0.0 0.0.0.0 10.4.9.1ip route 171.16.1.129 255.255.255.255 10.4.9.1!no ip http server!logging alarm informational!control-plane!line con 0exec-timeout 30 0stopbits 1line aux 0stopbits 1line vty 0 4login!!endConfiguration for RouterB
!interface FastEthernet0/0no shutdownip address 10.4.9.34 255.255.255.0duplex autospeed auto!interface FastEthernet0/1ip address 172.16.1.2 255.255.255.0bfd interval 50 min_rx 50 multiplier 3no shtdownduplex autospeed auto!router eigrp 11network 172.16.0.0bfd all-interfacesauto-summary!ip default-gateway 10.4.9.1ip default-network 0.0.0.0ip route 0.0.0.0 0.0.0.0 10.4.9.1ip route 171.16.1.129 255.255.255.255 10.4.9.1!no ip http server!logging alarm informational!control-plane!line con 0exec-timeout 30 0stopbits 1line aux 0stopbits 1line vty 0 4login!!endConfiguration for RouterC
!!interface FastEthernet0/0no shutdownip address 10.4.9.34 255.255.255.0duplex autospeed auto!interface FastEthernet0/1ip address 172.16.1.2 255.255.255.0bfd interval 50 min_rx 50 multiplier 3no shutdownduplex autospeed auto!router eigrp 11network 172.16.0.0bfd all-interfacesauto-summary!ip default-gateway 10.4.9.1ip default-network 0.0.0.0ip route 0.0.0.0 0.0.0.0 10.4.9.1ip route 171.16.1.129 255.255.255.255 10.4.9.1!no ip http server!logging alarm informational!control-plane!line con 0exec-timeout 30 0stopbits 1line aux 0stopbits 1line vty 0 4login!!endThe output from the show bfd neighbors details command from RouterA verifies that BFD sessions have been created among all three routers and that EIGRP is registered for BFD support. The first group of output shows that RouterC with the IP address 172.16.1.3 runs BFD Version 0 and therefore does not use the echo mode. The second group of output shows that RouterB with the IP address 172.16.1.2 does run BFD Version 1, and the 50 millisecond BFD interval parameter had been adopted. The relevant command output is shown in bold in the output.
RouterARouterA# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int172.16.1.1 172.16.1.3 5/3 1(RH) 150 (3 ) Up Fa0/1Session state is UP and not using echo function.Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 50000, MinRxInt: 50000, Multiplier: 3Received MinRxInt: 50000, Received Multiplier: 3Holdown (hits): 150(0), Hello (hits): 50(1364284)Rx Count: 1351813, Rx Interval (ms) min/max/avg: 28/64/49 last: 4 ms agoTx Count: 1364289, Tx Interval (ms) min/max/avg: 40/68/49 last: 32 ms agoRegistered protocols: EIGRPUptime: 18:42:45Last packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 3 - Your Discr.: 5Min tx interval: 50000 - Min rx interval: 50000Min Echo interval: 0OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int172.16.1.1 172.16.1.2 6/1 Up 0 (3 ) Up Fa0/1Session state is UP and using echo function with 50 ms interval.Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 1000000, MinRxInt: 1000000, Multiplier: 3Received MinRxInt: 1000000, Received Multiplier: 3Holdown (hits): 3000(0), Hello (hits): 1000(317)Rx Count: 305, Rx Interval (ms) min/max/avg: 1/1016/887 last: 448 ms agoTx Count: 319, Tx Interval (ms) min/max/avg: 1/1008/880 last: 532 ms agoRegistered protocols: EIGRPUptime: 00:04:30Last packet: Version: 1 - Diagnostic: 0State bit: Up - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 1 - Your Discr.: 6Min tx interval: 1000000 - Min rx interval: 1000000Min Echo interval: 50000The output from the show bfd neighbors details command on Router B verifies that BFD sessions have been created and that EIGRP is registered for BFD support. As previously noted, RouterA runs BFD Version 1, therefore echo mode is running, and RouterC runs BFD Version 0, so echo mode does not run. The relevant command output is shown in bold in the output.
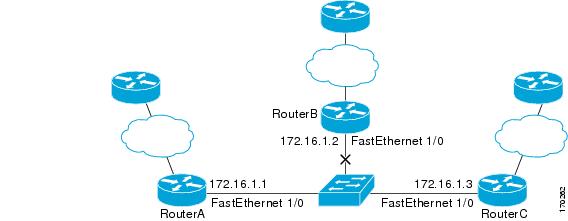
Router BRouterB# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int172.16.1.2 172.16.1.1 1/6 Up 0 (3 ) Up Fa0/1Session state is UP and using echo function with 50 ms interval.Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 1000000, MinRxInt: 1000000, Multiplier: 3Received MinRxInt: 1000000, Received Multiplier: 3Holdown (hits): 3000(0), Hello (hits): 1000(337)Rx Count: 341, Rx Interval (ms) min/max/avg: 1/1008/882 last: 364 ms agoTx Count: 339, Tx Interval (ms) min/max/avg: 1/1016/886 last: 632 ms agoRegistered protocols: EIGRPUptime: 00:05:00Last packet: Version: 1 - Diagnostic: 0State bit: Up - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 6 - Your Discr.: 1Min tx interval: 1000000 - Min rx interval: 1000000Min Echo interval: 50000OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int172.16.1.2 172.16.1.3 3/6 1(RH) 118 (3 ) Up Fa0/1Session state is UP and not using echo function.Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 50000, MinRxInt: 50000, Multiplier: 3Received MinRxInt: 50000, Received Multiplier: 3Holdown (hits): 150(0), Hello (hits): 50(5735)Rx Count: 5731, Rx Interval (ms) min/max/avg: 32/72/49 last: 32 ms agoTx Count: 5740, Tx Interval (ms) min/max/avg: 40/64/50 last: 44 ms agoRegistered protocols: EIGRPUptime: 00:04:45Last packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 6 - Your Discr.: 3Min tx interval: 50000 - Min rx interval: 50000Min Echo interval: 0Figure 4
Fast Ethernet interface 0/1 Failure
Figure 4 shows a that Fast Ethernet interface 0/1 on RouterB has failed. Without this neighbor, there is no way to reach the network beyond RouterB.
When Fast Ethernet interface 0/1 on RouterB fails, BFD will no longer detect Router B as a BFD neighbor for RouterA or for RouterC. In this example, Fast Ethernet interface 0/1 has been administratively shut down on RouterB.
The following output from the show bfd neighbors command on RouterA now shows only one BFD neighbor for RouterA in the EIGRP network. The relevant command output is shown in bold in the output.
RouterA# show bfd neighborsOurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int172.16.1.1 172.16.1.3 5/3 1(RH) 134 (3 ) Up Fa0/1The following output from the show bfd neighbors command on RouterC also now shows only one BFD neighbor for RouterC in the EIGRP network. The relevant command output is shown in bold in the output.
RouterC# show bfd neighborsOurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.1.3 172.16.1.1 3/5 1 114 (3 ) Up Fa0/1Configuring BFD in an OSPF Network: Example
12.0(31)S
In the following example, the simple OSPF network consists of Router A and Router B. Fast Ethernet interface 0/1 on Router A is connected to the same network as Fast Ethernet interface 6/0 in Router B. The example, starting in global configuration mode, shows the configuration of BFD. For both Routers A and B, BFD is configured globally for all interfaces associated with the OSPF process.
Configuration for Router A
!interface FastEthernet 0/1ip address 172.16.10.1 255.255.255.0bfd interval 50 min_rx 50 multiplier 3!interface FastEthernet 3/0.1ip address 172.17.0.1 255.255.255.0!router ospf 123log-adjacency-changes detailnetwork 172.16.0.0 0.0.0.255 area 0network 172.17.0.0 0.0.0.255 area 0bfd all-interfacesConfiguration for Router B
!interface FastEthernet 6/0ip address 172.16.10.2 255.255.255.0bfd interval 50 min_rx 50 multiplier 3!interface FastEthernet 6/1ip address 172.18.0.1 255.255.255.0!router ospf 123log-adjacency-changes detailnetwork 172.16.0.0 0.0.255.255 area 0network 172.18.0.0 0.0.255.255 area 0bfd all-interfacesThe output from the show bfd neighbors details command verifies that a BFD session has been created and that OSPF is registered for BFD support. The relevant command output is shown in bold in the output.
Router ARouterA# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.1 172.16.10.2 1/2 1 532 (3 ) Up Fa0/1Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 200000, MinRxInt: 200000, Multiplier: 5Received MinRxInt: 1000, Received Multiplier: 3Holdown (hits): 600(22), Hello (hits): 200(84453)Rx Count: 49824, Rx Interval (ms) min/max/avg: 208/440/332 last: 68 ms agoTx Count: 84488, Tx Interval (ms) min/max/avg: 152/248/196 last: 192 ms agoRegistered protocols: OSPF
Uptime: 02:18:49Last packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 2 - Your Discr.: 1Min tx interval: 50000 - Min rx interval: 1000Min Echo interval: 0The output from the show bfd neighbors details command from the line card on Router B verifies that a BFD session has been created:
Note
Router B is a Cisco 12000 series router. The show bfd neighbors details command must be run on the line cards. The show bfd neighbors details command will not display the registered protocols when it is entered on a line card.
Router BRouterB# attach 6Entering Console for 8 Port Fast Ethernet in Slot: 6Type "exit" to end this sessionPress RETURN to get started!LC-Slot6> show bfd neighbors detailsCleanup timer hits: 0OurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.2 172.16.10.1 8/1 1 1000 (5 ) Up Fa6/0Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 50000, MinRxInt: 1000, Multiplier: 3Received MinRxInt: 200000, Received Multiplier: 5Holdown (hits): 1000(0), Hello (hits): 200(5995)Rx Count: 10126, Rx Interval (ms) min/max/avg: 152/248/196 last: 0 ms agoTx Count: 5998, Tx Interval (ms) min/max/avg: 204/440/332 last: 12 ms agoLast packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 5 - Length: 24My Discr.: 1 - Your Discr.: 8Min tx interval: 200000 - Min rx interval: 200000Min Echo interval: 0Uptime: 00:33:13SSO Cleanup Timer called: 0SSO Cleanup Action Taken: 0Pseudo pre-emptive process count: 239103 min/max/avg: 8/16/8 last: 0 ms agoIPC Tx Failure Count: 0IPC Rx Failure Count: 0Total Adjs Found: 1The output of the show ip ospf command verifies that BFD has been enabled for OSPF. The relevant command output is shown in bold in the output.
Router A
RouterA# show ip ospfRouting Process "ospf 123" with ID 172.16.10.1Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)Initial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsIncremental-SPF disabledMinimum LSA interval 5 secsMinimum LSA arrival 1000 msecsLSA group pacing timer 240 secsInterface flood pacing timer 33 msecsRetransmission pacing timer 66 msecsNumber of external LSA 0. Checksum Sum 0x000000Number of opaque AS LSA 0. Checksum Sum 0x000000Number of DCbitless external and opaque AS LSA 0Number of DoNotAge external and opaque AS LSA 0Number of areas in this router is 1. 1 normal 0 stub 0 nssaExternal flood list length 0BFD is enabled
Area BACKBONE(0)Number of interfaces in this area is 2 (1 loopback)Area has no authenticationSPF algorithm last executed 00:00:08.828 agoSPF algorithm executed 9 timesArea ranges areNumber of LSA 3. Checksum Sum 0x028417Number of opaque link LSA 0. Checksum Sum 0x000000Number of DCbitless LSA 0Number of indication LSA 0Number of DoNotAge LSA 0Flood list length 0Router B
RouterB# show ip ospfRouting Process "ospf 123" with ID 172.18.0.1Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)Supports area transit capabilityInitial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsIncremental-SPF disabledMinimum LSA interval 5 secsMinimum LSA arrival 1000 msecsLSA group pacing timer 240 secsInterface flood pacing timer 33 msecsRetransmission pacing timer 66 msecsNumber of external LSA 0. Checksum Sum 0x0Number of opaque AS LSA 0. Checksum Sum 0x0Number of DCbitless external and opaque AS LSA 0Number of DoNotAge external and opaque AS LSA 0Number of areas in this router is 1. 1 normal 0 stub 0 nssaNumber of areas transit capable is 0External flood list length 0BFD is enabled
Area BACKBONE(0)Number of interfaces in this area is 2 (1 loopback)Area has no authenticationSPF algorithm last executed 02:07:30.932 agoSPF algorithm executed 7 timesArea ranges areNumber of LSA 3. Checksum Sum 0x28417Number of opaque link LSA 0. Checksum Sum 0x0Number of DCbitless LSA 0Number of indication LSA 0Number of DoNotAge LSA 0Flood list length 0The output of the show ip ospf interface command verifies that BFD has been enabled for OSPF on the interfaces connecting Router A and Router B. The relevant command output is shown in bold in the output.
Router A
RouterA# show ip ospf interface fastethernet 0/1show ip ospf interface fastethernet 0/1FastEthernet0/1 is up, line protocol is upInternet Address 172.16.10.1/24, Area 0Process ID 123, Router ID 172.16.10.1, Network Type BROADCAST, Cost: 1Transmit Delay is 1 sec, State BDR, Priority 1, BFD enabledDesignated Router (ID) 172.18.0.1, Interface address 172.16.10.2Backup Designated router (ID) 172.16.10.1, Interface address 172.16.10.1Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5oob-resync timeout 40Hello due in 00:00:03Supports Link-local Signaling (LLS)Index 1/1, flood queue length 0Next 0x0(0)/0x0(0)Last flood scan length is 1, maximum is 1Last flood scan time is 0 msec, maximum is 0 msecNeighbor Count is 1, Adjacent neighbor count is 1Adjacent with neighbor 172.18.0.1 (Designated Router)Suppress hello for 0 neighbor(s)Router B
RouterB# show ip ospf interface fastethernet 6/1FastEthernet6/1 is up, line protocol is upInternet Address 172.18.0.1/24, Area 0Process ID 123, Router ID 172.18.0.1, Network Type BROADCAST, Cost: 1Transmit Delay is 1 sec, State DR, Priority 1, BFD enabledDesignated Router (ID) 172.18.0.1, Interface address 172.18.0.1No backup designated router on this networkTimer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5oob-resync timeout 40Hello due in 00:00:01Supports Link-local Signaling (LLS)Index 1/1, flood queue length 0Next 0x0(0)/0x0(0)Last flood scan length is 0, maximum is 0Last flood scan time is 0 msec, maximum is 0 msecNeighbor Count is 0, Adjacent neighbor count is 0Suppress hello for 0 neighbor(s)Configuring BFD in a BGP Network: Example
12.0(31)S
In the following example, the simple BGP network consists of Router A and Router B. Fast Ethernet interface 0/1 on Router A is connected to the same network as Fast Ethernet interface 6/0 in Router B. The example, starting in global configuration mode, shows the configuration of BFD.
Configuration for Router A
!interface FastEthernet 0/1ip address 172.16.10.1 255.255.255.0bfd interval 50 min_rx 50 multiplier 3!interface FastEthernet 3/0.1ip address 172.17.0.1 255.255.255.0!!router bgp 40000bgp log-neighbor-changesneighbor 172.16.10.2 remote-as 45000neighbor 172.16.10.2 fall-over bfd!address-family ipv4neighbor 172.16.10.2 activateno auto-summaryno synchronizationnetwork 172.18.0.0 mask 255.255.255.0exit-address-family!Configuration for Router B
!interface FastEthernet 6/0ip address 172.16.10.2 255.255.255.0bfd interval 50 min_rx 50 multiplier 3!interface FastEthernet 6/1ip address 172.18.0.1 255.255.255.0!router bgp 45000bgp log-neighbor-changesneighbor 172.16.10.1 remote-as 40000neighbor 172.16.10.1 fall-over bfd!address-family ipv4neighbor 172.16.10.1 activateno auto-summaryno synchronizationnetwork 172.17.0.0 mask 255.255.255.0exit-address-family!The output from the show bfd neighbors details command from Router A verifies that a BFD session has been created and that BGP is registered for BFD support. The relevant command output is shown in bold in the output.
Router ARouterA# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.1 172.16.10.2 1/8 1 332 (3 ) Up Fa0/1Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 200000, MinRxInt: 200000, Multiplier: 5Received MinRxInt: 1000, Received Multiplier: 3Holdown (hits): 600(0), Hello (hits): 200(15491)Rx Count: 9160, Rx Interval (ms) min/max/avg: 200/440/332 last: 268 ms agoTx Count: 15494, Tx Interval (ms) min/max/avg: 152/248/197 last: 32 ms agoRegistered protocols: BGPUptime: 00:50:45Last packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 8 - Your Discr.: 1Min tx interval: 50000 - Min rx interval: 1000Min Echo interval: 0The output from the show bfd neighbors details command from the line card on Router B verifies that a BFD session has been created:
Note
Router B is a Cisco 12000 series router. The show bfd neighbors details command must be run on the line cards. The show bfd neighbors details command will not display the registered protocols when it is entered on a line card.
Router BRouterB# attach 6Entering Console for 8 Port Fast Ethernet in Slot: 6Type "exit" to end this sessionPress RETURN to get started!LC-Slot6> show bfd neighbors detailsCleanup timer hits: 0OurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.2 172.16.10.1 8/1 1 1000 (5 ) Up Fa6/0Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 50000, MinRxInt: 1000, Multiplier: 3Received MinRxInt: 200000, Received Multiplier: 5Holdown (hits): 1000(0), Hello (hits): 200(5995)Rx Count: 10126, Rx Interval (ms) min/max/avg: 152/248/196 last: 0 ms agoTx Count: 5998, Tx Interval (ms) min/max/avg: 204/440/332 last: 12 ms agoLast packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 5 - Length: 24My Discr.: 1 - Your Discr.: 8Min tx interval: 200000 - Min rx interval: 200000Min Echo interval: 0Uptime: 00:33:13SSO Cleanup Timer called: 0SSO Cleanup Action Taken: 0Pseudo pre-emptive process count: 239103 min/max/avg: 8/16/8 last: 0 ms agoIPC Tx Failure Count: 0IPC Rx Failure Count: 0Total Adjs Found: 1The output of the show ip bgp neighbors command verifies that BFD has been enabled for the BGP neighbors:
Router A
RouterA# show ip bgp neighborsBGP neighbor is 172.16.10.2, remote AS 45000, external linkUsing BFD to detect fast fallover...Router B
RouterB# show ip bgp neighborsBGP neighbor is 172.16.10.1, remote AS 40000, external linkUsing BFD to detect fast fallover...Configuring BFD in an IS-IS Network: Example
12.0(31)S
In the following example, the simple IS-IS network consists of Router A and Router B. Fast Ethernet interface 0/1 on Router A is connected to the same network as Fast Ethernet interface 6/0 for Router B. The example, starting in global configuration mode, shows the configuration of BFD.
Configuration for Router A
!interface FastEthernet 0/1ip address 172.16.10.1 255.255.255.0ip router isisbfd interval 50 min_rx 50 multiplier 3!interface FastEthernet 3/0.1ip address 172.17.0.1 255.255.255.0ip router isis!router isisnet 49.0001.1720.1600.1001.00bfd all-interfaces!Configuration for Router B
!interface FastEthernet 6/0ip address 172.16.10.2 255.255.255.0ip router isisbfd interval 50 min_rx 50 multiplier 3!interface FastEthernet 6/1ip address 172.18.0.1 255.255.255.0ip router isis!router isisnet 49.0000.0000.0002.00bfd all-interfaces!The output from the show bfd neighbors details command from Router A verifies that a BFD session has been created and that IS-IS is registered for BFD support:
Router ARouterA# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.1 172.16.10.2 1/8 1 536 (3 ) Up Fa0/1Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 200000, MinRxInt: 200000, Multiplier: 5Received MinRxInt: 1000, Received Multiplier: 3Holdown (hits): 600(0), Hello (hits): 200(23543)Rx Count: 13877, Rx Interval (ms) min/max/avg: 200/448/335 last: 64 ms agoTx Count: 23546, Tx Interval (ms) min/max/avg: 152/248/196 last: 32 ms agoRegistered protocols: ISISUptime: 01:17:09Last packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 8 - Your Discr.: 1Min tx interval: 50000 - Min rx interval: 1000Min Echo interval: 0The output from the show bfd neighbors details command from the line card on Router B verifies that a BFD session has been created:
Note
Router B is a Cisco 12000 series router. The show bfd neighbors details command must be run on the line cards. The show bfd neighbors details command will not display the registered protocols when it is entered on a line card.
Router BRouterB# attach 6Entering Console for 8 Port Fast Ethernet in Slot: 6Type "exit" to end this sessionPress RETURN to get started!LC-Slot6> show bfd neighbors detailsCleanup timer hits: 0OurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.2 172.16.10.1 8/1 1 1000 (5 ) Up Fa6/0Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 50000, MinRxInt: 1000, Multiplier: 3Received MinRxInt: 200000, Received Multiplier: 5Holdown (hits): 1000(0), Hello (hits): 200(5995)Rx Count: 10126, Rx Interval (ms) min/max/avg: 152/248/196 last: 0 ms agoTx Count: 5998, Tx Interval (ms) min/max/avg: 204/440/332 last: 12 ms agoLast packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 5 - Length: 24My Discr.: 1 - Your Discr.: 8Min tx interval: 200000 - Min rx interval: 200000Min Echo interval: 0Uptime: 00:33:13SSO Cleanup Timer called: 0SSO Cleanup Action Taken: 0Pseudo pre-emptive process count: 239103 min/max/avg: 8/16/8 last: 0 ms agoIPC Tx Failure Count: 0IPC Rx Failure Count: 0Total Adjs Found: 1Configuring BFD in an HSRP Network: Example
In the following example, the HSRP network consists of Router A and Router B. Fast Ethernet interface 2/0 on Router A is connected to the same network as Fast Ethernet interface 2/0 on Router B. The example, starting in global configuration mode, shows the configuration of BFD.
Note
In the following example, the standby bfd and the standby bfd all-interfaces commands are not displayed. HSRP support for BFD peering is enabled by default when BFD is configured on the router or interface using the bfd interval command. The standby bfd and standby bfd all-interfaces commands are needed only if BFD has been manually disabled on a router or interface.
Router A
ip cefinterface FastEthernet2/0no shutdownip address 10.0.0.2 255.0.0.0ip router-cache cefbfd interval 200 min_rx 200 multiplier 3standby 1 ip 10.0.0.11standby 1 preemptstandby 1 priority 110standby 2 ip 10.0.0.12standby 2 preemptstandby 2 priority 110Router B
interface FastEthernet2/0ip address 10.1.0.22 255.255.0.0no shutdownbfd interval 200 min_rx 200 multiplier 3standby 1 ip 10.0.0.11standby 1 preemptstandby 1 priority 90standby 2 ip 10.0.0.12standby 2 preemptstandby 2 priority 80The output from the show standby neighbors command verifies that a BFD session has been created:
RouterA# show standby neighborsHSRP neighbors on FastEthernet2/010.1.0.22No active groupsStandby groups: 1BFD enabled !RouterB# show standby neighborsHSRP neighbors on FastEthernet2/010.0.0.2Active groups: 1No standby groupsBFD enabled !Additional References
The following sections provide references related to the BFD feature.
Related Documents
Configuring and monitoring BGP
"BGP" module of the Cisco IOS IP Routing Protocols Configuration Guide, Release 12.4
Configuring and monitoring EIGRP
"EIGRP" module of the Cisco IOS IP Routing Protocols Configuration Guide, Release 12.4
Configuring and monitoring IS-IS
"Configuring Integrated IS-IS" module of the Cisco IOS IP Routing Protocols Configuration Guide, Release 12.4
Configuring and monitoring OSPF
"OSPF" module of the Cisco IOS IP Routing Protocols Configuration Guide, Release 12.4
Configuring and monitoring HSRP
"Configuring HSRP" module of the Cisco IOS IP Application Services Configuration Guide, Release 12.4T
Standards
MIBs
RFCs
No new or modified RFCs are supported by this feature, and support for existing RFCs has not been modified by this feature.
—
Technical Assistance
Command Reference
New Commands in Cisco IOS Release 12.2(18)SXE
•
bfd
Modified Commands in Cisco IOS Release 12.2(18)SXE
New Commands in Cisco IOS Release 12.0(31)S
•
bfd
Modified Commands in Cisco IOS Release 12.0(31)S
New Commands in Cisco IOS Release 12.4(4)T
•
bfd
Modified Commands in Cisco IOS Release 12.4(4)T
New Commands in Cisco IOS Release 12.0(32)S
•
None
Modified Commands in Cisco IOS Release 12.0(32)S
•
None
New Commands in Cisco IOS Release 12.2(33)SRA
•
None
Modified Commands in Cisco IOS Release 12.2(33)SRA
•
None
Modified Commands in Cisco IOS Release 12.2(33)SRB
•
None
New Commands in Cisco IOS Release 12.4(9)T
Modified Commands in Cisco IOS Release 12.4(9)T
New Commands in Cisco IOS Release 12.4(11)T
Modified Commands in Cisco IOS Release 12.4(11)T
bfd
To set the baseline Bidirectional Forwarding Detection (BFD) session parameters on an interface, use the bfd command in interface configuration mode. To remove the baseline BFD session parameters, use the no form of this command.
bfd interval milliseconds min_rx milliseconds multiplier multiplier-value
no bfd interval milliseconds min_rx milliseconds multiplier multiplier-value
Syntax Description
Command Default
No baseline BFD session parameters are set.
Command Modes
Interface configuration
Command History
Examples
The following example shows the BFD session parameters set for FastEthernet interface 3/0:
Router> enableRouter# configure terminalRouter(config)# interface fastethernet 3/0Router(config-if)# bfd interval 50 min_rx 2 multiplier 3Router(config-if)# endRelated Commands
bfd all-interfaces
To enable Bidirectional Forwarding Detection (BFD) for all interfaces participating in the routing process, use the bfd all-interfaces command in router configuration mode. To disable BFD for all interfaces, use the no form of this command.
bfd all-interfaces
no bfd all-interfaces
Syntax Description
This command has no arguments or keywords.
Command Default
BFD is not enabled on the interfaces participating in the routing process.
Command Modes
Router configuration
Command History
Usage Guidelines
There are two methods to configure routing protocols to use BFD for failure detection. To enable BFD for all neighbors of a routing protocol, enter the bfd all-interfaces command in router configuration mode. If you do not want to enable BFD on all interfaces, enter the bfd interface command in router configuration mode.
Examples
The following example shows BFD enabled for all Enhanced Interior Gateway Routing Protocol (EIGRP) neighbors:
Router> enableRouter# configure terminalRouter(config)# router eigrp 123Router(config-router)# bfd all-interfacesRouter(config-router)# endThe following example shows BFD enabled for all Intermediate System-to-Intermediate System (IS-IS) neighbors:
Router> enableRouter# configure terminalRouter(config)# router isis tag1Router(config-router)# bfd all-interfacesRouter(config-router)# endThe following example shows BFD enabled for all Open Shortest Path First (OSPF) neighbors:
Router> enableRouter# configure terminalRouter(config)# router ospf 123Router(config-router)# bfd all-interfacesRouter(config-router)# endRelated Commands
bfd
Sets the baseline BFD session parameters on an interface.
bfd interface
Enables BFD on a per-interface basis for a BFD peer.
bfd echo
To enable Bidirectional Forwarding Detection (BFD) echo mode, use the bfd echo command in interface configuration mode. To disable BFD echo mode, use the no form of this command.
bfd echo
no bfd echo
Syntax Description
This command has no arguments or keywords.
Command Default
BFD echo mode is enabled by default.
Command Modes
Interface configuration
Command History
12.4(9)T
This command was introduced.
12.2(33)SRB
This command was integrated into Cisco IOS Release 12.2(33)SRB.
Usage Guidelines
Echo mode is enabled by default. Entering the no bfd echo command without any keywords turns off the sending of echo packets and signifies that the router is unwilling to forward echo packets received from BFD neighbor routers.
When echo mode is enabled, the desired minimum echo transmit interval and required minimum transmit interval values are taken from the bfd interval milliseconds min_rx milliseconds parameters, respectively.
Note
If the no ip route-cache same-interface command is configured, the bfd echo accept command will not be accepted.
Note
Before using BFD echo mode, you must disable the sending of Internet Control Message Protocol (ICMP) redirect messages by entering the no ip redirects command, in order to avoid high CPU utilization.
Echo Mode Without Asymmetry
Echo mode is described as without asymmetry when it is running on both sides (both BFD neighbors are running echo mode).
Examples
The following example configures echo mode between BFD neighbors.
Router> enableRouter# configure terminalRouter(config)# interface Ethernet 0/1Router(config-if)# bfd echoThe following output from the show bfd neighbors details command shows that the BFD session neighbor is up and using BFD echo mode. The relevant command output is shown in bold in the output.
Router# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH/RS Holdown(mult)State Int172.16.1.2 172.16.1.1 1/6 Up 0 (3 ) Up Fa0/1Session state is UP and using echo function with 50 ms interval.Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 1000000, MinRxInt: 1000000, Multiplier: 3Received MinRxInt: 1000000, Received Multiplier: 3Holdown (hits): 3000(0), Hello (hits): 1000(337)Rx Count: 341, Rx Interval (ms) min/max/avg: 1/1008/882 last: 364 ms agoTx Count: 339, Tx Interval (ms) min/max/avg: 1/1016/886 last: 632 ms agoRegistered protocols: EIGRPUptime: 00:05:00Last packet: Version: 1 - Diagnostic: 0State bit: Up - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 6 - Your Discr.: 1Min tx interval: 1000000 - Min rx interval: 1000000Min Echo interval: 50000Related Commands
bfd interface
To enable Bidirectional Forwarding Detection (BFD) on a per-interface basis for a BFD peer, use the bfd interface command in router configuration mode. To disable BFD on a per-interface basis, use the no form of this command.
bfd interface type number
no bfd interface type number
Syntax Description
type
Interface type for the interface to be enabled for BFD.
number
Interface number for the interface to be enabled for BFD.
Command Default
BFD is not enabled on the interface.
Command Modes
Router configuration
Command History
Usage Guidelines
There are two methods to configure routing protocols to use BFD for failure detection. To enable BFD for all neighbors of a routing protocol, enter the bfd all-interfaces command in router configuration mode. If you do not want to enable BFD on all interfaces, enter the bfd interface command in router configuration mode.
Examples
The following example shows BFD enabled for the Enhanced Interior Gateway Routing Protocol (EIGRP) neighbor Fast Ethernet interface 3/0:
Router> enableRouter# configure terminalRouter(config)# router eigrp 123Router(config-router)# bfd interface fastethernet 3/0Router(config-if)# endRelated Commands
bfd
Sets the baseline BFD session parameters on an interface.
bfd all-interfaces
Enables BFD for all interfaces for a BFD peer.
bfd slow-timer
To configure the Bidirectional Forwarding Detection (BFD) slow timer value, use the bfd slow-timer command in global configuration mode. This command does not have a no form.
bfd slow-timer [milliseconds]
Syntax Description
milliseconds
(Optional) BFD slow timer value, in milliseconds. Range is from 1000 30000. If unspecified, the default is 1000.
Command Default
The BFD slow timer value is 1000 milliseconds.
Command Modes
Global configuration
Command History
12.4(9)T
This command was introduced.
12.2(33)SRB
This command was integrated into Cisco IOS Release 12.2(33)SRB.
Examples
In the following example, the BFD slow timer value is configured to 14,000 milliseconds.
Router(config)# bfd slow-timer 14000The following output from the show bfd neighbors details command shows that the BFD slow timer value of 14,000 milliseconds has been implemented. The values for the MinTxInt and MinRxInt will correspond to the configured value for the BFD slow timer. The relevant command output is shown in bold.
Router# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int172.16.10.1 172.16.10.2 1/1 Up 0 (3 ) Up Et2/0Session state is UP and using echo function with 50 ms interval.Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 14000, MinRxInt: 14000, Multiplier: 3Received MinRxInt: 10000, Received Multiplier: 3Holdown (hits): 3600(0), Hello (hits): 1200(418)Rx Count: 422, Rx Interval (ms) min/max/avg: 1/1480/1087 last: 112 ms agoTx Count: 420, Tx Interval (ms) min/max/avg: 1/2088/1090 last: 872 ms agoRegistered protocols: OSPFUptime: 00:07:37Last packet: Version: 1 - Diagnostic: 0State bit: Up - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 1 - Your Discr.: 1Min tx interval: 14000 - Min rx interval: 14000Min Echo interval: 4000Related Commands
debug bfd
To display debugging messages about Bidirectional Forwarding Detection (BFD), use the debug bfd command in privileged EXEC mode. To disable debugging output, use the no form of this command.
Cisco IOS Release 12.2(18)SXE, 12.4(4)T, and 12.2(33)SRA
debug bfd {event | packet [ip-address]}
no debug bfd {event | packet [ip-address]}
Cisco IOS Release 12.0(31)S
debug bfd {event | packet [ip-address] | ipc-error | ipc-event | oir-error | oir-event}
no debug bfd {event | packet [ip-address] | ipc-error | ipc-event | oir-error | oir-event}
Syntax Description
Command Modes
Privileged EXEC
Command History
Usage Guidelines
The debug bfd command can be used to troubleshoot the BFD feature.
Note
Because BFD is designed to send and receive packets at a very high rate, consider the potential effect on system resources before enabling this command, especially if there are a large number of BFD peers. The debug bfd packet command should be enabled only on a live network at the direction of Cisco Technical Assistance Center personnel.
Examples
The following example shows output from the debug bfd packet command. The IP address has been specified in order to limit the packet information to one interface:
Router# debug bfd packet 172.16.10.5BFD packet debugging is on*Jan 26 14:47:37.645: Tx*IP: dst 172.16.10.1, plen 24. BFD: diag 2, St/D/P/F (1/0/0/0), mult 5, len 24, loc/rem discr 1 1, tx 1000000, rx 1000000 100000, timer 1000 ms, #103*Jan 26 14:47:37.645: %OSPF-5-ADJCHG: Process 10, Nbr 172.16.10.12 on Ethernet1/4 from FULL to DOWN, Neighbor Down: BFD node down*Jan 26 14:47:50.685: %OSPF-5-ADJCHG: Process 10, Nbr 172.16.10.12 on Ethernet1/4 from LOADING to FULL, Loading Done*Jan 26 14:48:00.905: Rx IP: src 172.16.10.1, plen 24. BFD: diag 0, St/D/P/F (1/0/0/0), mult 4, len 24, loc/rem discr 2 1, tx 1000000, rx 1000000 100000, timer 4000 ms, #50*Jan 26 14:48:00.905: Tx IP: dst 172.16.10.1, plen 24. BFD: diag 2, St/D/P/F (2/0/0/0), mult 5, len 24, loc/rem discr 1 2, tx 1000000, rx 1000000 100000, timer 1000 ms, #131*Jan 26 14:48:00.905: Rx IP: src 172.16.10.1, plen 24. BFD: diag 0, St/D/P/F (3/0/0/0), mult 4, len 24, loc/rem discr 2 1, tx 1000000, rx 1000000 100000, timer 4000 ms, #51*Jan 26 14:48:00.905: Tx IP: dst 172.16.10.1, plen 24. BFD: diag 0, St/D/P/F (3/0/0/0), mult 5, len 24, loc/rem discr 1 2, tx 1000000, rx 1000000 100000, timer 1000 ms, #132The following example shows output from the debug bfd event command when an interface between two BFD neighbor routers fails and then comes back online:
Router# debug bfd event22:53:48: BFD: bfd_neighbor - action:DESTROY, proc:1024, idb:FastEthernet0/1, neighbor:172.16.10.222:53:48: BFD: bfd_neighbor - action:DESTROY, proc:512, idb:FastEthernet0/1, neighbor:172.16.10.222:53:49: Session [172.16.10.1,172.16.10.2,Fa0/1,1], event DETECT TIMER EXPIRED, state UP -> FAILING...22:56:35: BFD: bfd_neighbor - action:CREATE, proc:1024, idb:FastEthernet0/1, neighbor:172.16.10.222:56:37: Session [172.16.10.1,172.16.10.2,Fa0/1,1], event RX IHY 0, state FAILING -> DOWN22:56:37: Session [172.16.10.1,172.16.10.2,Fa0/1,1], event RX IHY 0, state DOWN -> INIT22:56:37: Session [172.16.10.1,172.16.10.2,Fa0/1,1], event RX IHY 1, state INIT -> UPTable 1 describes the significant fields shown in the display.
The following example shows output from the debug bfd packet command when an interface between two BFD neighbor routers fails and then comes back online. The diagnostic code changes from 0 (No Diagnostic) to 1 (Control Detection Time Expired) because no BFD control packets could be sent (and therefore detected by the BFD peer) after the interface fails. When the interface comes back online, the diagnostic code changes back to 0 to signify that BFD packets can be sent and received by the BFD peers.
Router# debug bfd packet23:03:25: Rx IP: src 172.16.10.2, plen 24. BFD: diag 0, H/D/P/F (0/0/0/0), mult 3, len 24, loc/rem discr 5 1, tx 1000000, rx 10000723:03:25: Tx IP: dst 172.16.10.2, plen 24. BFD: diag 1, H/D/P/F (0/0/0/0), mult 5, len 24, loc/rem discr 1 5, tx 1000000, rx 100000823:03:25: Tx IP: dst 172.16.10.2, plen 24. BFD: diag 1, H/D/P/F (1/0/0/0), mult 5, len 24, loc/rem discr 1 5, tx 1000000, rx 1000009Table 2 describes the significant fields shown in the display.
ip ospf bfd
To enable Bidirectional Forwarding Detection (BFD) on a specific interface configured for Open Shortest Path First (OSPF), use the ip ospf bfd command in interface configuration mode. To disable BFD on the OSPF interface, use the disable keyword. To remove the ospf bfd command, use the no form of this command.
ip ospf bfd [disable]
no ip ospf bfd
Syntax Description
Defaults
When the disable keyword is not used, the default behavior is to enable BFD support for OSPF on the interface.
Command Modes
Interface configuration
Command History
Usage Guidelines
Enter the ip ospf bfd command to configure an OSPF interface to use BFD for failure detection. If you have used the bfd-all interfaces command in router configuration mode to globally configure all OSPF interfaces for an OSPF process to use BFD, you can enter the ip ospf bfd command in interface configuration mode with the disable keyword to disable BFD for a specific OSPF interface.
Examples
In the following example, the interface associated with OSPF, Fast Ethernet interface 3/0, is configured for BFD:
Router> enableRouter# configure terminalRouter(config)# interface fastethernet 3/0Router(config-if)# ip ospf bfdRouter(config-if)# endRelated Commands
isis bfd
To enable or disable Bidirectional Forwarding Detection (BFD) on a specific interface configured for Intermediate System-to-Intermediate System (IS-IS), use the isis bfd command in interface configuration mode. To disable BFD on the IS-IS interface, use the disable keyword. To remove the isis bfd command, use the no form of this command.
isis bfd [disable]
no isis bfd
Syntax Description
Defaults
When the disable keyword is not used, the default behavior is to enable BFD support for IS-IS on the interface.
Command Modes
Interface configuration
Command History
Usage Guidelines
Enter the isis bfd command in interface mode to configure an IS-IS interface to use BFD for failure detection. If you have used the bfd-all interfaces command in router configuration mode to globally configure all IS-IS interfaces for an IS-IS process to use BFD, you can enter the isis bfd command with the disable keyword in interface configuration mode to disable BFD for a specific IS-IS interface.
Entering the no isis bfd command will remove the command. In that case, whether or not an IS-IS interface for a particular IS-IS process is registered with the BFD protocol will depend on whether or not you have entered the bfd all-interfaces command in router configuration mode for the specific IS-IS process.
Examples
In the following example, the interface associated with OSPF, Fast Ethernet interface 3/0, is configured for BFD:
Router> enableRouter# configure terminalRouter(config)# interface fastethernet 3/0Router(config-if)# isis bfdRouter(config-if)# endRelated Commands
show bfd neighbors
To display a line-by-line listing of existing Bidirectional Forwarding Detection (BFD) adjacencies, use the show bfd neighbors command in user EXEC or privileged EXEC mode.
show bfd neighbors [details]
Syntax Description
Command Modes
User EXEC
Privileged EXECCommand History
Usage Guidelines
The show bfd neighbors command can be used to help troubleshoot the BFD feature.
The full output for the details keyword is not supported on the Route Processor (RP) for the Cisco 12000 series Internet router. If you want to enter the show bfd neighbors command with the details keyword for the Cisco 12000 series Internet router, you must enter it on the line card. Use the attach slot command to establish a command-line interface (CLI) session with a line card.
Examples
Examples for 12.0(31)S, 12.2(18)SXE, 12.2(33)SRA, and 12.3(4)T
The following sample output shows the status of the adjacency or neighbor:
Router# show bfd neighborsOurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.1 172.16.10.2 1/6 1 260 (3 ) Up Fa0/1The following sample output from the show bfd neighbors command entered with the details keyword shows BFD protocol parameters and timers for each neighbor:
Router# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.1 172.16.10.2 1/2 1 460 (3 ) Up Fa0/1Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 200000, MinRxInt: 200000, Multiplier: 5Received MinRxInt: 1000, Received Multiplier: 3Holdown (hits): 600(0), Hello (hits): 200(390169)Rx Count: 229225, Rx Interval (ms) min/max/avg: 208/440/332 last: 144 ms agoTx Count: 388219, Tx Interval (ms) min/max/avg: 148/248/196 last: 48 ms agoRegistered protocols: OSPF StubUptime: 17:44:37Last packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 2 - Your Discr.: 1Min tx interval: 50000- Min rx interval: 1000Min Echo interval: 0The following sample output from the RP on a Cisco 12000 series router shows the status of the adjacency or neighbor:
Router# show bfd neighborsCleanup timer hits: 0OurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.2 172.16.10.1 2/0 0 0 (0 ) Up Fa6/0Total Adjs Found: 1The following sample output from the RP on a Cisco 12000 series router shows the status of the adjacency or neighbor with the details keyword:
RouterB# show bfd neighbors detailsCleanup timer hits: 0OurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.2 172.16.10.1 2/0 0 0 (0 ) Up Fa6/0Registered protocols: OSPFUptime: never%% BFD Neighbor statistics are not available on RP. Please execute this command on Line Card.The following sample output from a line card on a Cisco 12000 series router shows the status of the adjacency or neighbor:
Router# attach 6Entering Console for 8 Port Fast Ethernet in Slot: 6Type "exit" to end this sessionPress RETURN to get started!LC-Slot6> show bfd neighborsCleanup timer hits: 0OurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.2 172.16.10.1 2/1 1 848 (5 ) Up Fa6/0Total Adjs Found: 1The following sample output from a line card on a Cisco 12000 series router shows the status of the adjacency or neighbor with the details keyword:
Router# attach 6Entering Console for 8 Port Fast Ethernet in Slot: 6Type "exit" to end this sessionPress RETURN to get started!LC-Slot6> show bfd neighbors detailsCleanup timer hits: 0OurAddr NeighAddr LD/RD RH Holdown(mult) State Int172.16.10.2 172.16.10.1 2/1 1 892 (5 ) Up Fa6/0Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 50000, MinRxInt: 1000, Multiplier: 3Received MinRxInt: 200000, Received Multiplier: 5Holdown (hits): 1000(0), Hello (hits): 200(193745)Rx Count: 327406, Rx Interval (ms) min/max/avg: 152/248/196 last: 108 ms agoTx Count: 193748, Tx Interval (ms) min/max/avg: 204/440/331 last: 408 ms agoLast packet: Version: 0 - Diagnostic: 0I Hear You bit: 1 - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 5 - Length: 24My Discr.: 1 - Your Discr.: 2Min tx interval: 200000 - Min rx interval: 200000Min Echo interval: 0Uptime: 17:54:07SSO Cleanup Timer called: 0SSO Cleanup Action Taken: 0Pseudo pre-emptive process count: 7728507 min/max/avg: 8/16/8 last: 12 ms agoIPC Tx Failure Count: 0IPC Rx Failure Count: 0Total Adjs Found: 1LC-Slot6>Example for 12.4(9)T and Later Releases
The following sample output Sverifies that the BFD neighbor router is also running BFD Version 1 and that the BFD session is up and running in echo mode.
Router# show bfd neighbors detailsOurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int172.16.1.2 172.16.1.1 1/6 Up 0 (3 ) Up Fa0/1Session state is UP and using echo function with 50 ms interval.Local Diag: 0, Demand mode: 0, Poll bit: 0MinTxInt: 1000000, MinRxInt: 1000000, Multiplier: 3Received MinRxInt: 1000000, Received Multiplier: 3Holdown (hits): 3000(0), Hello (hits): 1000(337)Rx Count: 341, Rx Interval (ms) min/max/avg: 1/1008/882 last: 364 ms agoTx Count: 339, Tx Interval (ms) min/max/avg: 1/1016/886 last: 632 ms agoRegistered protocols: EIGRPUptime: 00:05:00Last packet: Version: 1 - Diagnostic: 0State bit: Up - Demand bit: 0Poll bit: 0 - Final bit: 0Multiplier: 3 - Length: 24My Discr.: 6 - Your Discr.: 1Min tx interval: 1000000 - Min rx interval: 1000000Min Echo interval: 50000Table 3 describes the significant fields shown in the display.
Related Commands
attach
Connects to a specific line card for the purpose of executing monitoring and maintenance commands on that line card only.
show clns interface
To list the CLNS-specific information about each interface, use the show clns interface command in privileged EXEC mode.
show clns interface [type number]
Syntax Description
Command Modes
Privileged EXEC
Command History
Examples
The following is sample output from the show clns interface command that includes information for Token Ring and serial interfaces:
Router# show clns interfaceTokenRing 0 is administratively down, line protocol is downCLNS protocol processing disabledTokenRing 1 is up, line protocol is upChecksums enabled, MTU 4461, Encapsulation SNAPERPDUs enabled, min. interval 10 msec.RDPDUs enabled, min. interval 100 msec., Addr Mask enabledCongestion Experienced bit set at 4 packetsCLNS fast switching disabledDEC compatibility mode OFF for this interfaceNext ESH/ISH in 18 secondsRouting Protocol: ISO IGRPRouting Domain/Area: <39.0003> <0020>Serial 2 is up, line protocol is upChecksums enabled, MTU 1497, Encapsulation HDLCERPDUs enabled, min. interval 10 msec.RDPDUs enabled, min. interval 100 msec., Addr Mask enabledCongestion Experienced bit set at 4 packetsCLNS fast switching enabledDEC compatibility mode OFF for this interfaceCLNS cluster alias enabled on this interfaceNext ESH/ISH in 48 secondsRouting Protocol: IS-ISCircuit Type: level-1-2Level-1 Metric: 10, Priority: 64, Circuit ID: 0000.0C00.2D55.0ANumber of active level-1 adjacencies: 0Level-2 Metric: 10, Priority: 64, Circuit ID: 0000.0000.0000.00Number of active level-2 adjacencies: 0Next IS-IS LAN Level-1 hello in 3 secondsNext IS-IS LAN Level-2 hello in 3 secondsCisco IOS Release 12.2(18)SXE, 12.0(31)S, and 12.4(4)T
The following is sample output from the show clns interface command that verifies that the BFD feature has been enabled on Ethernet interface 3/0. The relevant command output is shown in bold in the output.
Router# show clns interface ethernet 3/0Ethernet3/0 is up, line protocol is upChecksums enabled, MTU 1497, Encapsulation SAPERPDUs enabled, min. interval 10 msec.CLNS fast switching enabledCLNS SSE switching disabledDEC compatibility mode OFF for this interfaceNext ESH/ISH in 42 secondsRouting Protocol: IS-ISCircuit Type: level-1-2Interface number 0x1, local circuit ID 0x2Level-1 Metric: 10, Priority: 64, Circuit ID: RouterA.02DR ID: 0000.0000.0000.00Level-1 IPv6 Metric: 10Number of active level-1 adjacencies: 0Level-2 Metric: 10, Priority: 64, Circuit ID: RouterA.02DR ID: 0000.0000.0000.00Level-2 IPv6 Metric: 10Number of active level-2 adjacencies: 0Next IS-IS LAN Level-1 Hello in 3 secondsNext IS-IS LAN Level-2 Hello in 5 secondsBFD enabledTable 4 describes the significant fields shown in the display.
show ip bgp neighbors
To display information about Border Gateway Protocol (BGP) and TCP connections to neighbors, use the show ip bgp neighbors command in user or privileged EXEC mode.
show ip bgp neighbors [ip-address [advertised-routes | dampened-routes | flap-statistics |
paths [reg-exp] | received prefix-filter | received-routes | routes | policy [detail]]]Syntax Description
Command Default
The output of this command displays information for all neighbors.
Command Modes
User EXEC
Privileged EXECCommand History
Usage Guidelines
Use the show ip bgp neighbors command to display BGP and TCP connection information for neighbor sessions. For BGP, this includes detailed neighbor attribute, capability, path, and prefix information. For TCP, this includes statistics related to BGP neighbor session establishment and maintenance.
Prefix activity is displayed based on the number of prefixes that are advertised and withdrawn. Policy denials display the number of routes that were advertised but then ignored based the function or attribute that is displayed in the output.
Cisco IOS Release 12.0(25)S, 12.4(11)T, 12.2(33)SRB, and Later Releases
When BGP neighbors use multiple levels of peer templates it can be difficult to determine which policies are applied to the neighbor. In Cisco IOS Release 12.0(25)S, 12.4(11)T, 12.2(33)SRB and later releases, the policy and detail keywords were added to display the inherited policies and the policies configured directly on the specified neighbor. Inherited policies are policies that the neighbor inherits from a peer-group or a peer-policy template.
Examples
Example output is different for the various keywords available for the show ip bgp neighbors command. To view the appropriate output, choose one of the following sections:
•
show ip bgp neighbors: Example
•
show ip bgp neighbors advertised-routes: Example
•
show ip bgp neighbors paths: Example
•
show ip bgp neighbors received prefix-filter: Example
•
show ip bgp neighbors policy: Example
•
Cisco IOS Release 12.0(31)S and 12.4(4)T: Example
•
Cisco IOS Release 12.2(33)SRA: Example
show ip bgp neighbors: Example
The following example shows output for the BGP neighbor at 10.108.50.2. This neighbor is an internal BGP (iBGP) peer. This neighbor supports the route refresh and graceful restart capabilities.
Router# show ip bgp neighbors 10.108.50.2BGP neighbor is 10.108.50.2, remote AS 1, internal linkBGP version 4, remote router ID 192.168.252.252BGP state = Established, up for 00:24:25Last read 00:00:24, last write 00:00:24, hold time is 180, keepalive interval is 60 secondsNeighbor capabilities:Route refresh: advertised and received(old & new)MPLS Label capability: advertised and receivedGraceful Restart Capability:advertised and receivedAddress family IPv4 Unicast: advertised and receivedMessage statistics:InQ depth is 0OutQ depth is 0Sent RcvdOpens: 3 3Notifications: 0 0Updates: 0 0Keepalives: 113 112Route Refresh: 0 0Total: 116 115Default minimum time between advertisement runs is 5 secondsFor address family: IPv4 UnicastBGP table version 1, neighbor version 1/0Output queue size : 0Index 1, Offset 0, Mask 0x21 update-group memberSent RcvdPrefix activity: ---- ----Prefixes Current: 0 0Prefixes Total: 0 0Implicit Withdraw: 0 0Explicit Withdraw: 0 0Used as bestpath: n/a 0Used as multipath: n/a 0Outbound InboundLocal Policy Denied Prefixes: -------- -------Total: 0 0Number of NLRIs in the update sent: max 0, min 0Connections established 3; dropped 2Last reset 00:24:26, due to Peer closed the sessionExternal BGP neighbor may be up to 2 hops away.Connection state is ESTAB, I/O status: 1, unread input bytes: 0Connection is ECN DisabledLocal host: 10.108.50.1, Local port: 179Foreign host: 10.108.50.2, Foreign port: 42698Enqueued packets for retransmit: 0, input: 0 mis-ordered: 0 (0 bytes)Event Timers (current time is 0x68B944):Timer Starts Wakeups NextRetrans 27 0 0x0TimeWait 0 0 0x0AckHold 27 18 0x0SendWnd 0 0 0x0KeepAlive 0 0 0x0GiveUp 0 0 0x0PmtuAger 0 0 0x0DeadWait 0 0 0x0iss: 3915509457 snduna: 3915510016 sndnxt: 3915510016 sndwnd: 15826irs: 233567076 rcvnxt: 233567616 rcvwnd: 15845 delrcvwnd: 539SRTT: 292 ms, RTTO: 359 ms, RTV: 67 ms, KRTT: 0 msminRTT: 12 ms, maxRTT: 300 ms, ACK hold: 200 msFlags: passive open, nagle, gen tcbsIP Precedence value : 6Datagrams (max data segment is 1460 bytes):Rcvd: 38 (out of order: 0), with data: 27, total data bytes: 539Sent: 45 (retransmit: 0, fastretransmit: 0, partialack: 0, Second Congestion: 08Table 5 describes the significant fields shown in the display. Fields that are preceded by the asterisk character are displayed only when the counter has a nonzero value.
show ip bgp neighbors advertised-routes: Example
The following example displays routes advertised for only the 172.16.232.178 neighbor:
Router# show ip bgp neighbors 172.16.232.178 advertised-routesBGP table version is 27, local router ID is 172.16.232.181Status codes: s suppressed, d damped, h history, * valid, > best, i - internalOrigin codes: i - IGP, e - EGP, ? - incompleteNetwork Next Hop Metric LocPrf Weight Path*>i10.0.0.0 172.16.232.179 0 100 0 ?*> 10.20.2.0 0.0.0.0 0 32768 iTable 6 describes the significant fields shown in the display.
show ip bgp neighbors paths: Example
The following is example output from the show ip bgp neighbors command entered with the paths keyword:
Router# show ip bgp neighbors 172.29.232.178 paths ^10Address Refcount Metric Path0x60E577B0 2 40 10 ?Table 7 describes the significant fields shown in the display.
show ip bgp neighbors received prefix-filter: Example
The following example shows that a prefix-list the filters all routes in the 10.0.0.0 network has be received from the 192.168.20.72 neighbor:
Router# show ip bgp neighbors 192.168.20.72 received prefix-filterAddress family:IPv4 Unicastip prefix-list 192.168.20.72:1 entriesseq 5 deny 10.0.0.0/8 le 32Table 8 describes the significant fields shown in the display.
show ip bgp neighbors policy: Example
The following sample output shows the policies applied to the neighbor at 192.168.1.2. The output displays both inherited policies and policies configured on the neighbor device. Inherited polices are policies that the neighbor inherits from a peer-group or a peer-policy template.
Router# show ip bgp neighbors 192.168.1.2 policyNeighbor: 192.168.1.2, Address-Family: IPv4 UnicastLocally configured policies:route-map ROUTE inInherited polices:prefix-list NO-MARKETING inroute-map ROUTE inweight 300maximum-prefix 10000Cisco IOS Release 12.0(31)S and 12.4(4)T: Example
The following is sample output from the show ip bgp neighbors command that verifies that BFD is being used to detect fast fallover for the BGP neighbor that is a BFD peer.
Router# show ip bgp neighborsBGP neighbor is 172.16.10.2, remote AS 45000, external link...Using BFD to detect fast falloverCisco IOS Release 12.2(33)SRA: Example
The following is sample output from the show ip bgp neighbors command that verifies that BGP TCP path MTU discovery is enabled for the BGP neighbor at 172.16.1.2.
Router# show ip bgp neighbors 172.16.1.2BGP neighbor is 172.16.1.2, remote AS 45000, internal linkBGP version 4, remote router ID 172.16.1.99...For address family: IPv4 UnicastBGP table version 5, neighbor version 5/0...Address tracking is enabled, the RIB does have a route to 172.16.1.2Address tracking requires at least a /24 route to the peerConnections established 3; dropped 2Last reset 00:00:35, due to Router ID changedTransport(tcp) path-mtu-discovery is enabled...SRTT: 146 ms, RTTO: 1283 ms, RTV: 1137 ms, KRTT: 0 msminRTT: 8 ms, maxRTT: 300 ms, ACK hold: 200 msFlags: higher precedence, retransmission timeout, nagle, path mtu capableRelated Commands
show ip eigrp interfaces
To display information about interfaces configured for Enhanced Interior Gateway Routing Protocol (EIGRP), use the show ip eigrp interfaces command in privileged EXEC mode.
show ip eigrp interfaces [type number] [as-number] [detail]
Syntax Description
Command Modes
Privileged EXEC
Command History
Usage Guidelines
Use the show ip eigrp interfaces command to determine on which interfaces EIGRP is active, and to learn information about EIGRP relating to those interfaces.
If an interface is specified, only that interface is displayed. Otherwise, all interfaces on which EIGRP is running are displayed.
If an autonomous system is specified, only the routing process for the specified autonomous system is displayed. Otherwise, all EIGRP processes are displayed.
Examples
The following is sample output from the show ip eigrp interfaces command:
Router# show ip eigrp interfacesIP EIGRP interfaces for process 109Xmit Queue Mean Pacing Time Multicast PendingInterface Peers Un/Reliable SRTT Un/Reliable Flow Timer RoutesDi0 0 0/0 0 11/434 0 0Et0 1 0/0 337 0/10 0 0SE0:1.16 1 0/0 10 1/63 103 0Tu0 1 0/0 330 0/16 0 0Cisco IOS Release 12.2(18)SXE
The following is sample output from the show ip eigrp interfaces command to verify that the BFD feature has been enabled on the EIGRP interfaces for process 123. The relevant command output is shown in bold in the output.
Router# show ip eigrp interfaces detailIP-EIGRP interfaces for process 1Xmit Queue Mean Pacing Time Multicast PendingInterface Peers Un/Reliable SRTT Un/Reliable Flow Timer RoutesIP-EIGRP interfaces for process 100Xmit Queue Mean Pacing Time Multicast PendingInterface Peers Un/Reliable SRTT Un/Reliable Flow Timer RoutesFa0/1 0 0/0 0 0/10 0 0Next xmit serial <none>Un/reliable mcasts: 0/0 Un/reliable ucasts: 0/0Mcast exceptions: 0 CR packets: 0 ACKs suppressed: 0Retransmissions sent: 0 Out-of-sequence rcvd: 0Authentication mode is not setBFD is enabledEt3/0 0 0/0 0 0/10 0 0Next xmit serial <none>Un/reliable mcasts: 0/0 Un/reliable ucasts: 0/0Mcast exceptions: 0 CR packets: 0 ACKs suppressed: 0Retransmissions sent: 0 Out-of-sequence rcvd: 0Authentication mode is not setBFD is enabledTable 9 describes the significant fields shown in the display.
Related Commands
show ip ospf
To display general information about Open Shortest Path First (OSPF) routing processes, use the show ip ospf command in user EXEC or privileged EXEC mode.
show ip ospf [process-id]
Syntax Description
process-id
(Optional) Process ID. If this argument is included, only information for the specified routing process is included.
Command Modes
User EXEC
Privileged EXECCommand History
Examples
The following is sample output from the show ip ospf command when entered without a specific OSPF process ID:
Router# show ip ospfRouting Process "ospf 201" with ID 10.0.0.1 and Domain ID 10.20.0.1Supports only single TOS(TOS0) routesSupports opaque LSASPF schedule delay 5 secs, Hold time between two SPFs 10 secsMinimum LSA interval 5 secs. Minimum LSA arrival 1 secsLSA group pacing timer 100 secsInterface flood pacing timer 55 msecsRetransmission pacing timer 100 msecsNumber of external LSA 0. Checksum Sum 0x0Number of opaque AS LSA 0. Checksum Sum 0x0Number of DCbitless external and opaque AS LSA 0Number of DoNotAge external and opaque AS LSA 0Number of areas in this router is 2. 2 normal 0 stub 0 nssaExternal flood list length 0Area BACKBONE(0)Number of interfaces in this area is 2Area has message digest authenticationSPF algorithm executed 4 timesArea ranges areNumber of LSA 4. Checksum Sum 0x29BEBNumber of opaque link LSA 0. Checksum Sum 0x0Number of DCbitless LSA 3Number of indication LSA 0Number of DoNotAge LSA 0Flood list length 0Area 172.16.26.0Number of interfaces in this area is 0Area has no authenticationSPF algorithm executed 1 timesArea ranges are192.168.0.0/16 Passive AdvertiseNumber of LSA 1. Checksum Sum 0x44FDNumber of opaque link LSA 0. Checksum Sum 0x0Number of DCbitless LSA 1Number of indication LSA 1Number of DoNotAge LSA 0Flood list length 0Cisco IOS Release 12.2(18)SXE, 12.0(31)S, and 12.4(4)T
The following is sample output from the show ip ospf command to verify that the BFD feature has been enabled for OSPF process 123. The relevant command output is shown in bold in the output.
Router# show ip ospfRouting Process "ospf 123" with ID 172.16.10.1Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)Initial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsIncremental-SPF disabledMinimum LSA interval 5 secsMinimum LSA arrival 1000 msecsLSA group pacing timer 240 secsInterface flood pacing timer 33 msecsRetransmission pacing timer 66 msecsNumber of external LSA 0. Checksum Sum 0x000000Number of opaque AS LSA 0. Checksum Sum 0x000000Number of DCbitless external and opaque AS LSA 0Number of DoNotAge external and opaque AS LSA 0Number of areas in this router is 1. 1 normal 0 stub 0 nssaExternal flood list length 0BFD is enabledArea BACKBONE(0)Number of interfaces in this area is 2Area has no authenticationSPF algorithm last executed 00:00:03.708 agoSPF algorithm executed 27 timesArea ranges areNumber of LSA 3. Checksum Sum 0x00AEF1Number of opaque link LSA 0. Checksum Sum 0x000000Number of DCbitless LSA 0Number of indication LSA 0Number of DoNotAge LSA 0Flood list length 0Table 10 describes the significant fields shown in the display.
The following is an excerpt of output from the show ip ospf command when the OSPF Forwarding Address Suppression in Type-5 LSAs feature is configured:
Router# show ip ospf...Area 2Number of interfaces in this area is 4It is a NSSA areaPerform type-7/type-5 LSA translation, suppress forwarding address...Routing Process "ospf 1" with ID 192.168.0.1Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)Initial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsIncremental-SPF disabledMinimum LSA interval 5 secsMinimum LSA arrival 1000 msecsLSA group pacing timer 240 secsInterface flood pacing timer 33 msecsRetransmission pacing timer 66 msecsNumber of external LSA 0. Checksum Sum 0x0Number of opaque AS LSA 0. Checksum Sum 0x0Number of DCbitless external and opaque AS LSA 0Number of DoNotAge external and opaque AS LSA 0Number of areas in this router is 0. 0 normal 0 stub 0 nssaExternal flood list length 0Table 11 describes the significant fields shown in the display.
The following is sample output from the show ip ospf command. In this example, the user had configured the redistribution maximum-prefix command to set a limit of 2000 redistributed routes. Shortest Path First (SPF) throttling was configured with the timers throttle spf command.
Router# show ip ospf 1Routing Process "ospf 1" with ID 10.0.0.1Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)It is an autonomous system boundary routerRedistributing External Routes from,static, includes subnets in redistributionMaximum limit of redistributed prefixes 2000Threshold for warning message 75%Initial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsTable 12 describes the significant fields shown in the display.
The following is sample output from the show ip ospf command. In this example, the user had configured LSA throttling, and those lines of output are displayed in bold.
Router# show ip ospf 1Routing Process "ospf 4" with ID 10.10.24.4Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)Initial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsIncremental-SPF disabledInitial LSA throttle delay 100 msecsMinimum hold time for LSA throttle 10000 msecsMaximum wait time for LSA throttle 45000 msecsMinimum LSA arrival 1000 msecsLSA group pacing timer 240 secsInterface flood pacing timer 33 msecsRetransmission pacing timer 66 msecsNumber of external LSA 0. Checksum Sum 0x0Number of opaque AS LSA 0. Checksum Sum 0x0Number of DCbitless external and opaque AS LSA 0Number of DoNotAge external and opaque AS LSA 0Number of areas in this router is 1. 1 normal 0 stub 0 nssaExternal flood list length 0Area 24Number of interfaces in this area is 2Area has no authenticationSPF algorithm last executed 04:28:18.396 agoSPF algorithm executed 8 timesArea ranges areNumber of LSA 4. Checksum Sum 0x23EB9Number of opaque link LSA 0. Checksum Sum 0x0Number of DCbitless LSA 0Number of indication LSA 0Number of DoNotAge LSA 0Flood list length 0The following is sample show ip ospf command. In this example, the user had configured the redistribution maximum-prefix command to set a limit of 2000 redistributed routes. SPF throttling was configured with the timers throttle spf command.
Router# show ip ospf 1Routing Process "ospf 1" with ID 192.168.0.0Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)It is an autonomous system boundary routerRedistributing External Routes from,static, includes subnets in redistributionMaximum limit of redistributed prefixes 2000Threshold for warning message 75%Initial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsTable 13 describes the significant fields shown in the display.
The following is sample output from the show ip ospf command. In this example, the user had configured LSA throttling, and those lines of output are displayed in bold.
Router# show ip ospf 1Routing Process "ospf 4" with ID 10.10.24.4Supports only single TOS(TOS0) routesSupports opaque LSASupports Link-local Signaling (LLS)Initial SPF schedule delay 5000 msecsMinimum hold time between two consecutive SPFs 10000 msecsMaximum wait time between two consecutive SPFs 10000 msecsIncremental-SPF disabledInitial LSA throttle delay 100 msecsMinimum hold time for LSA throttle 10000 msecsMaximum wait time for LSA throttle 45000 msecsMinimum LSA arrival 1000 msecsLSA group pacing timer 240 secsInterface flood pacing timer 33 msecsRetransmission pacing timer 66 msecsNumber of external LSA 0. Checksum Sum 0x0Number of opaque AS LSA 0. Checksum Sum 0x0Number of DCbitless external and opaque AS LSA 0Number of DoNotAge external and opaque AS LSA 0Number of areas in this router is 1. 1 normal 0 stub 0 nssaExternal flood list length 0Area 24Number of interfaces in this area is 2Area has no authenticationSPF algorithm last executed 04:28:18.396 agoSPF algorithm executed 8 timesArea ranges areNumber of LSA 4. Checksum Sum 0x23EB9Number of opaque link LSA 0. Checksum Sum 0x0Number of DCbitless LSA 0Number of indication LSA 0Number of DoNotAge LSA 0Flood list length 0show monitor event-trace
To display event trace messages for Cisco IOS software subsystem components, use the show monitor event-trace command in privileged EXEC mode.
show monitor event-trace [all-traces] [component {all | back time | clock time | from-boot seconds | latest | parameters}]
Syntax Description
Command Modes
Privileged EXEC
Command History
Usage Guidelines
Use the show monitor event-trace command to display trace message information.
The trace function is not locked while information is being displayed to the console, which means that new trace messages can accumulate in memory. If entries accumulate faster than they can be displayed, some messages can be lost. If this happens, the show monitor event-trace command will generate a message indicating that some messages might be lost; however, messages will continue to display on the console. If the number of lost messages is excessive, the show monitor event-trace command will stop displaying messages.
Use the bfd keyword for the component argument to display trace messages relating to the Bidirectional Forwarding Detection (BFD) feature.
Use the cfd keyword for the component argument to display trace messages relating to the crypto fault detection feature. This keyword displays the contents of the error trace buffers in an encryption data path.
Examples
IPC Component Example
The following is sample output from the show monitor event-trace component command for the IPC component. Notice that each trace message is numbered and is followed by a timestamp (derived from the device uptime). Following the time stamp is the component-specific message data.
Router# show monitor event-trace ipc3667: 6840.016:Message type:3 Data=01234567893668: 6840.016:Message type:4 Data=01234567893669: 6841.016:Message type:5 Data=01234567893670: 6841.016:Message type:6 Data=0123456BFD Component for Cisco IOS Release 12.2(18)SXE, 12.0(31)S, and 12.4(4)T
Use the show monitor event-trace bfd all command to display logged messages for important BFD events in the recent past. The following trace messages show BFD session state changes:
Router# show monitor event-trace bfd all3d03h: EVENT: Session [172.16.10.2,172.16.10.1,Fa6/0,1], event Sessioncreate, state Unknown -> Fail3d03h: EVENT: Session [172.16.10.2,172.16.10.1,Fa6/0,1], state Fail -> Down(from LC)3d03h: EVENT: Session [172.16.10.2,172.16.10.1,Fa6/0,1], state Down -> Init(from LC)3d03h: EVENT: Session [172.16.10.2,172.16.10.1,Fa6/0,1], state Init -> Up(from LC)3d07h: EVENT: Session [172.16.10.2,172.16.10.1,Fa6/0,2], event Sessioncreate, state Unknown -> Fail3d07h: EVENT: Session [172.16.10.2,172.16.10.1,Fa6/0,2], state Fail -> Down(from LC)3d07h: EVENT: Session [172.16.10.2,172.16.10.1,Fa6/0,2], state Down -> Up(from LC)To view trace information for all components configured for event tracing on the networking device, enter the show monitor event-trace all-traces command. In this example, separate output is provided for each event, and message numbers are interleaved between the events.
Router# show monitor event-trace all-tracesTest1 event trace:3667: 6840.016:Message type:3 Data=01234567893669: 6841.016:Message type:4 Data=01234567893671: 6842.016:Message type:5 Data=01234567893673: 6843.016:Message type:6 Data=0123456789Test2 event trace:3668: 6840.016:Message type:3 Data=01234567893670: 6841.016:Message type:4 Data=01234567893672: 6842.016:Message type:5 Data=01234567893674: 6843.016:Message type:6 Data=0123456789SPA Component Example
The following is sample output from the show monitor event-trace component latest command for the spa component:
Router# show monitor event-trace spa latest00:01:15.364: subslot 2/3: 4xOC3 POS SPA, TSM Event:inserted New state:wait_psm_readyspa type 0x44000:02:02.308: subslot 2/0: not present, TSM Event:empty New state:removespa type 0x0, fail code 0x0(none)00:02:02.308: subslot 2/0: not present, TSM Event:remove_complete New state:idle00:02:02.308: subslot 2/1: not present, TSM Event:empty New state:removespa type 0x0, fail code 0x0(none)00:02:02.308: subslot 2/1: not present, TSM Event:remove_complete New state:idle00:02:02.308: subslot 2/2: not present, TSM Event:empty New state:removespa type 0x0, fail code 0x0(none)00:02:02.308: subslot 2/2: not present, TSM Event:remove_complete New state:idle00:02:02.312: subslot 2/3: not present(plugin 4xOC3 POS SPA), TSM Event:empty Newstate:removespa type 0x0, fail code 0x0(none)00:02:02.312: subslot 2/3: not present, TSM Event:remove_complete New state:idleCisco Express Forwarding Component Examples
If you select Cisco Express Forwarding as the component for which to display event messages, you can use the following additional arguments and keywords: show monitor event-trace cef [events | interface | ipv6 | ipv4][all].
The following example shows the IPv6 or IPv4 events related to the Cisco Express Forwarding component. Each trace message is numbered and is followed by a time stamp (derived from the device uptime). Following the time stamp is the component-specific message data.
Router# show monitor event-trace cef ipv6 all00:00:24.612: [Default] *::*/*'00 New FIB table [OK]Router# show monitor event-trace cef ipv4 all00:00:24.244: [Default] 127.0.0.81/32'01 FIB insert [OK]In the following example, all event trace messages for the Cisco Express Forwarding component are displayed:
Router# show monitor event-trace cef events all00:00:18.884: SubSys fib_ios_chain init00:00:18.884: Inst unknown -> RP00:00:24.584: SubSys fib init00:00:24.592: SubSys fib_ios init00:00:24.592: SubSys fib_ios_if init00:00:24.596: SubSys ipv4fib init00:00:24.608: SubSys ipv4fib_ios init00:00:24.612: SubSys ipv6fib_ios init00:00:24.620: Flag IPv4 CEF enabled set to yes00:00:24.620: Flag 0x7BF6B62C set to yes00:00:24.620: Flag IPv4 CEF switching enabled set to yes00:00:24.624: GState CEF enabled00:00:24.628: SubSys ipv4fib_les init00:00:24.628: SubSys ipv4fib_pas init00:00:24.632: SubSys ipv4fib_util init00:00:25.304: Process Background created00:00:25.304: Flag IPv4 CEF running set to yes00:00:25.304: Process Background event loop enter00:00:25.308: Flag IPv4 CEF switching running set to yesThe following example shows Cisco Express Forwarding interface events:
Router# show monitor event-trace cef interface all00:00:24.624: <empty> (sw 4) Create new00:00:24.624: <empty> (sw 4) SWIDBLnk FastEthernet0/0(4)00:00:24.624: Fa0/0 (sw 4) NameSet00:00:24.624: <empty> (hw 1) Create new00:00:24.624: <empty> (hw 1) HWIDBLnk FastEthernet0/0(1)00:00:24.624: Fa0/0 (hw 1) NameSet00:00:24.624: <empty> (sw 3) Create new00:00:24.624: <empty> (sw 3) SWIDBLnk FastEthernet0/1(3)00:00:24.624: Fa0/1 (sw 3) NameSet00:00:24.624: <empty> (hw 2) Create newCisco Express Forwarding Component Examples for Cisco 10000 Series Routers Only
The following example shows the IPv4 events related to the Cisco Express Forwarding component. Each trace message is numbered and is followed by a the time stamp (derived from the device uptime). Following the time stamp is the component-specific message data.
Router# show monitor event-trace cef ipv4 all00:00:48.244: [Default] 127.0.0.81/32'01 FIB insert [OK]In the following example, all event trace message for the Cisco Express Forwarding component are displayed:
Router# show monitor event-trace cef events all00:00:18.884: SubSys fib_ios_chain init00:00:18.884: Inst unknown -> RP00:00:24.584: SubSys fib init00:00:24.592: SubSys fib_ios init00:00:24.592: SubSys fib_ios_if init00:00:24.596: SubSys ipv4fib init00:00:24.608: SubSys ipv4fib_ios init00:00:24.620: Flag IPv4 CEF enabled set to yes00:00:24.620: Flag 0x7BF6B62C set to yes00:00:24.620: Flag IPv4 CEF switching enabled set to yes00:00:24.624: GState CEF enabled00:00:24.628: SubSys ipv4fib_les init00:00:24.628: SubSys ipv4fib_pas init00:00:24.632: SubSys ipv4fib_util init00:00:25.304: Process Background created00:00:25.304: Flag IPv4 CEF running set to yes00:00:25.304: Process Background event loop enter00:00:25.308: Flag IPv4 CEF switching running set to yesThe following examples show Cisco Express Forwarding interface events:
Router# show monitor event-trace cef interface all00:00:24.624: <empty> (sw 4) Create new00:00:24.624: <empty> (sw 4) SWIDBLnk FastEthernet1/0/0(4)00:00:24.624: Fa0/0 (sw 4) NameSet00:00:24.624: <empty> (hw 1) Create new00:00:24.624: <empty> (hw 1) HWIDBLnk FastEthernet1/0/0(1)00:00:24.624: Fa0/0 (hw 1) NameSet00:00:24.624: <empty> (sw 3) Create new00:00:24.624: <empty> (sw 3) SWIDBLnk FastEthernet1/1/0(3)00:00:24.624: Fa0/1 (sw 3) NameSet00:00:24.624: <empty> (hw 2) Create newCFD Component for Cisco IOS Release 12.4(9)T
To troubleshoot errors in an encryption datapath, enter the show monitor event-trace cfd all command. In this example, events are shown separately, each beginning with a timestamp, followed by data from the error trace buffer. Cisco TAC engineers can use this information to diagnose the cause of the errors.
Note
If no packets have been dropped, this command does not display any output.
Router# show monitor event-trace cfd all00:00:42.452: 450000B4 00060000 FF33B306 02020203 02020204 32040000 F672999C 00000001 7A7690C2 A0A4F8BC E732985C D6FFDCC8 00000001 C0902BD0 A99127AE 8EAA22D4 00:00:44.452: 450000B4 00070000 FF33B305 02020203 02020204 32040000 F672999C 00000002 93C01218 2325B697 3C384CF1 D6FFDCC8 00000002 BFA13E8A D21053ED 0F62AB0E 00:00:46.452: 450000B4 00080000 FF33B304 02020203 02020204 32040000 F672999C 00000003 7D2E11B7 A0BA4110 CC62F91E D6FFDCC8 00000003 7236B930 3240CA8C 9EBB44FF 00:00:48.452: 450000B4 00090000 FF33B303 02020203 02020204 32040000 F672999C 00000004 FB6C80D9 1AADF938 CDE57ABA D6FFDCC8 00000004 E10D8028 6BBD748F 87F5E253 00:00:50.452: 450000B4 000A0000 FF33B302 02020203 02020204 32040000 F672999C 00000005 697C8D9D 35A8799A 2A67E97B D6FFDCC8 00000005 BC21669D 98B29FFF F32670F6 00:00:52.452: 450000B4 000B0000 FF33B301 02020203 02020204 32040000 F672999C 00000006 CA18CBC4 0F387FE0 9095C27C D6FFDCC8 00000006 87A54811 AE3A0517 F8AC4E64Related Commands
show standby
To display Hot Standby Router Protocol (HSRP) information, use the show standby command in user EXEC or privileged EXEC mode.
show standby [type number [group]] [all | brief]
Syntax Description
Command Modes
User EXEC
Privileged EXECCommand History
Usage Guidelines
To specify a group, you must specify an interface type and number.
Examples
The following is sample output from the show standby command:
Router# show standbyEthernet0/1 - Group 1State is Active2 state changes, last state change 00:30:59Virtual IP address is 10.1.0.20Secondary virtual IP address 10.1.0.21Active virtual MAC address is 0004.4d82.7981Local virtual MAC address is 0004.4d82.7981 (bia)Hello time 4 sec, hold time 12 secNext hello sent in 1.412 secsPreemption enabled, min delay 50 sec, sync delay 40 secActive router is localStandby router is 10.1.0.6, priority 75 (expires in 9.184 sec)Priority 95 (configured 120)Tracking 2 objects, 0 upIP redundancy name is "HSRP1" (cfgd)Follow by groups:Et1/0.3 Grp 2 Active 10.0.0.254 0000.0c07.ac02 refresh 30 secs (next 19.666)Et1/0.4 Grp 2 Active 10.0.0.254 0000.0c07.ac02 refresh 30 secs (next 19.491)Down Interface Ethernet0/2, pri 15Down Interface Ethernet0/3IP redundancy name is "HSRP1", advertisement interval is 34 secThe following is sample output from the show standby command when HSRP version 2 is configured:
Router# show standbyEthernet0/1 - Group 1 (version 2)State is SpeakVirtual IP address is 10.21.0.10Active virtual MAC address is unknownLocal virtual MAC address is 0000.0c9f.f001 (v2 default)Hello time 3 sec, hold time 10 secNext hello sent in 1.804 secsPreemption enabledActive router is unknownStandby router is unknownPriority 20 (configured 20)IP redundancy name is "hsrp-Et0/1-1" (default)Ethernet0/2 - Group 1State is SpeakVirtual IP address is 10.22.0.10Active virtual MAC address is unknownLocal virtual MAC address is 0000.0c07.ac01 (v1 default)Hello time 3 sec, hold time 10 secNext hello sent in 1.804 secsPreemption disabledActive router is unknownStandby router is unknownPriority 90 (default 100)Track interface Serial2/0 state Down decrement 10IP redundancy name is "hsrp-Et0/2-1" (default)The following is sample output from the show standby command with the brief keyword specified:
Router# show standby briefInterface Grp Prio P State Active addr Standby addr Group addrEt0 0 120 Init 10.0.0.1 unknown 10.0.0.12The following is sample output from the show standby command when HSRP MD5 authentication is configured:
Router# show standbyEthernet0/1 - Group 1State is Active5 state changes, last state change 00:17:27Virtual IP address is 10.21.0.10Active virtual MAC address is 0000.0c07.ac01Local virtual MAC address is 0000.0c07.ac01 (default)Hello time 3 sec, hold time 10 secNext hello sent in 2.276 secsAuthentication MD5, key-string "f33r45", timeout 30 secsPreemption enabledActive router is localStandby router is unknownPriority 110 (configured 110)IP redundancy name is "hsrp-Et0/1-1" (default)The following is sample output from the show standby command when HSRP group shutdown is configured:
Router# show standbyEthernet0/0 - Group 1State is Init (tracking shutdown)3 state changes, last state change 00:30:59Track object 100 state UpTrack object 101 state DownTrack object 103 state UpThe following is sample output from the show standby command when HSRP BFD peering is enabled:
Router# show standbyEthernet0/0 - Group 2State is Listen2 state changes, last state change 01:18:18Virtual IP address is 10.0.0.1Active virtual MAC address is 0000.0c07.ac02Local virtual MAC address is 0000.0c07.ac02 (v1 default)Hello time 3 sec, hold time 10 secPreemption enabledActive router is 10.0.0.250, priority 120 (expires in 9.396 sec)Standby router is 10.0.0.251, priority 110 (expires in 8.672 sec)BFD enabledPriority 90 (configured 90)IP redundancy name is "hsrp-Et0/0-1" (default)Table 14 describes the significant fields shown in the displays.
Related Commands
show standby neighbors
To display information about Hot Standby Router Protocol (HSRP) peer routers on an interface, use the show standby neighbors command in privileged EXEC mode.
show standby neighbors [interface-type interface-number]
Syntax Description
Command Default
HSRP neighbor information is displayed for all interfaces.
Command Modes
Privileged EXEC
Command History
Usage Guidelines
Use this command to display information about HSRP peer neighbors. This command displays the HSRP groups for which each neighbor is acting as the active and standby router and whether Bidirectional Forwarding Detection (BFD) peering is enabled for each neighbor.
Examples
The following example displays the HSRP neighbors on Ethernet interface 0/0. Neighbor 10.0.0.250 is active for group 2 and standby for groups 1 and 8, and is registered with BFD:
Router# show standby neighbors Ethernet0/0HSRP neighbors on Ethernet0/010.0.0.250Active groups: 2Standby groups: 1, 8BFD enabled10.0.0.251Active groups: 5, 8Standby groups: 2BFD enabled10.0.0.253No Active groupsNo Standby groupsBFD enabledThe following example displays information for all HSRP neighbors:
Router# show standby neighborsHSRP neighbors on FastEthernet2/010.0.0.2No active groupsStandby groups: 1BFD enabledHSRP neighbors on FastEthernet2/010.0.0.1Active groups: 1No standby groupsBFD enabledTable 15 describes the significant fields shown in the displays.
Related Commands
standby bfd
To reenable Hot Standby Router Protocol (HSRP) Bidirectional Forwarding Detection (BFD) peering if it has been disabled on an interface, use the standby bfd command in interface configuration mode. To disable HSRP support for BFD, use the no form of this command.
standby bfd
no standby bfd
Syntax Description
This command has no arguments or keywords.
Command Default
HSRP support for BFD is enabled.
Command Modes
Interface configuration
Command History
Usage Guidelines
HSRP BFD peering is enabled by default when the router is configured for BFD. Use this command to reenable HSRP BFD peering on the specified interface when it has previously been manually disabled.
To enable HSRP BFD peering globally on the router, use the standby bfd all-interfaces command in global configuration mode.
Examples
The following example shows how to reenable HSRP BFD peering if it has been disabled:
Router(config)# interface ethernet0/0Router(config-if)# standby bfdRelated Commands
standby bfd all-interfaces
To reenable Hot Standby Router Protocol (HSRP) Bidirectional Forwarding Detection (BFD) peering on all interfaces if it has been disabled, use the standby bfd all-interfaces command in global configuration mode. To disable HSRP support for BFD peering, use the no form of this command.
standby bfd all-interfaces
no standby bfd all-interfaces
Syntax Description
This command has no arguments or keywords.
Command Default
HSRP BFD peering is enabled.
Command Modes
Global configuration
Command History
Usage Guidelines
The HSRP BFD peering feature introduces BFD in the HSRP group member health monitoring system. Previously, group member monitoring relied exclusively on HSRP multicast messages, which are relatively large and consume CPU memory to produce and check. In architectures where a single interface hosts a large number of groups, there is a need for a protocol with low CPU memory consumption and processing overhead. BFD addresses this issue and offers subsecond health monitoring (failure detection in milliseconds) with a relatively low CPU impact. This command is enabled by default.
To enable HSRP support for BFD on a per-interface basis, use the standby bfd command in interface configuration mode.
Examples
The following example shows how to reenable HSRP BFD peering if it has been disabled on a router:
Router(config)# standby bfd all-interfacesRelated Commands
Feature Information for Bidirectional Forwarding Detection
Table 16 lists the release history for this feature.
Not all commands may be available in your Cisco IOS software release. For release information about a specific command, see the command reference documentation.
Cisco IOS software images are specific to a Cisco IOS software release, a feature set, and a platform. Use Cisco Feature Navigator to find information about platform support and software image support. Cisco Feature Navigator enables you to determine which Cisco IOS and Catalyst OS software images support a specific software release, feature set, or platform. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Note
Table 16 lists only the Cisco IOS software release that introduced support for a given feature in a given Cisco IOS software release train. Unless noted otherwise, subsequent releases of that Cisco IOS software release train also support that feature.
Glossary
BFD—Bidirectional Forwarding Detection. A detection protocol designed to provide fast failure detection times for all media types, encapsulations, topologies, and routing protocols.
Note
See Internetworking Terms and Acronyms for terms not included in this glossary.
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2004-2007 Cisco Systems, Inc. All rights reserved.

 Feedback
Feedback