Feedback Feedback
|
Contents
- Configuring SAF
- Finding Feature Information
- Prerequisites for Cisco SAF
- Restriction for Cisco SAF
- Information About Cisco SAF
- Cisco SAF Overview
- Cisco SAF Forwarder Overview
- Cisco SAF Client Overview
- External Cisco SAF Client using XMCP Overview
- Cisco SAF Service Identifier Number Formats
- Cisco SAF and Role of Domains in a Network
- Cisco SAF Virtual Routers
- Cisco SAF Neighbor Relationships
- Benefits of Cisco SAF
- How to Configure a Cisco SAF Forwarder
- Enabling Cisco SAF
- Configuring Interface-Specific Commands for Cisco SAF
- Configuring Cisco SAF for Multi-Topology Networks
- Configuring Static Neighbor Relationships for Cisco SAF
- Configuring Stub Routing for Cisco SAF
- Configuring Route Authentication for Cisco SAF
- Configuring Logs for Neighbor Changes and Warnings
- Configuring the Percentage of Link Bandwidth Used for Cisco SAF
- Setting Metric Dampening Intervals for Cisco SAF Interfaces
- Change-based Dampening Configuration
- Interval-based Dampening Configuration
- Adjusting the Interval Between Hello Packets and the Hold Time
- Disabling Split Horizon
- Setting Metric Maximum Hops
- How to Configure a Cisco SAF External Client
- Prerequisites
- Configuring a Cisco SAF External Client
- How to Display Cisco SAF Statistics
- How to Delete Information from a Cisco SAF Configuration
- Configuration Examples for Cisco SAF
- Example: Enabling Cisco SAF
- Example: Configuring Cisco SAF Interfaces
- Example: Configuring Cisco SAF Topology
- Example: Configuring Cisco SAF Stub Routing
- Example: Configuring Cisco SAF with IP-RIP
- Example: Configuring Cisco SAF with OSPF
- Example: Configuring Cisco SAF with EIGRP
- Example: Configuring Cisco SAF Forwarders Located on Separate LANs
- Configuring a Centralized Cisco SAF Forwarder Example
- Examples: Configuring a Cisco SAF Client
- Additional References
- Feature Information for Cisco SAF
Configuring SAF
- Finding Feature Information
- Prerequisites for Cisco SAF
- Restriction for Cisco SAF
- Information About Cisco SAF
- How to Configure a Cisco SAF Forwarder
- How to Configure a Cisco SAF External Client
- How to Display Cisco SAF Statistics
- How to Delete Information from a Cisco SAF Configuration
- Configuration Examples for Cisco SAF
- Additional References
- Feature Information for Cisco SAF
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Cisco SAF
- Before configuring Cisco SAF, you should understand the concepts in this guide.
- Before configuring neighbor relationships for Cisco SAF Forwarders located on separate LANs, ensure IP routing is configured between each Cisco SAF Forwarder.
Information About Cisco SAF
- Cisco SAF Overview
- Cisco SAF Service Identifier Number Formats
- Cisco SAF and Role of Domains in a Network
- Cisco SAF Virtual Routers
- Cisco SAF Neighbor Relationships
- Benefits of Cisco SAF
Cisco SAF Overview
Cisco SAF provides a framework that allows applications to discover the existence, location, and configuration of networked resources within networks. Cisco SAF allows a timely and reliable awareness of the services within networks, as applications advertise and discover services on networks. Service information distributes though a network of Cisco SAF cooperative nodes that assume specific functions to efficiently distribute knowledge of services and facilitate their discovery.
A non-SAF node is any node in a network that does not understand SAF. Non-SAF nodes are called "dark nets" and are required to traverse ISPs. Cisco SAF messages are IP-based and therefore are unaffected by dark nets.
These Cisco SAF cooperative network nodes are grouped into two major functional responsibilities:
- Cisco SAF Forwarder-- Distributes service information through the network and makes these services discoverable by clients in the network
- Cisco SAF Client --Services are advertised and can be discovered
An effective Cisco SAF network requires both roles to be configured.
This section provides the following information:
- Cisco SAF Forwarder Overview
- Cisco SAF Client Overview
- External Cisco SAF Client using XMCP Overview
Cisco SAF Forwarder Overview
A Cisco SAF Forwarder receives services advertised by Cisco SAF Clients, distributes the services reliably through the network, and make services available for Cisco SAF Clients to use. A Cisco SAF Forwarder:
- Ensures reliable delivery of service advertisements
- Maintains knowledge of path redundancy
- Is scalable
- Minimizes the use of network bandwidth by using targeted multicast and unicast messages.
The Cisco SAF Forwarder can propagate service advertisements to other Cisco SAF Forwarders and can propagate across a LAN, campus network, WAN, or ISP.
A basic Cisco SAF Forwarder provides the relationship between Cisco SAF Clients and the framework. A Cisco SAF Forwarder is normally located at the edges or boundaries of a network. The Cisco SAF Forwarder receives service advertisements and stores a copy before forwarding the advertisement to its neighbor SAF nodes. The Client and forwarder relationship is to maintain the advertisement. If a Client removes a service or disconnects from the forwarder node, the node will inform the framework about the services that are no longer available. When the forwarder node receives advertisements from other forwarder nodes, it will keep a copy of the entire advertisement (Header and opaque data) and forward to other SAF peers.
You can configure a Cisco SAF Forwarder on a LAN to automatically allow dynamic discovery of services to all enabled interfaces, and at the same time, specify interfaces (static configuration) you want blocked to other interfaces attempting to discover their services.
You can configure a Cisco SAF Forwarder across a non-SAF node to automatically allow dynamic discovery of services. For example, Cisco SAF Forwarders join a common peer-group. You can also create static configurations (Unicast) between pairs of Cisco SAF Forwarders.
 Note | Multicast routing is required to allow dynamic discovery of services. |
Cisco SAF Client Overview
A Cisco SAF Client is a producer (advertises to the network) or consumer of services (requests a service from the network), or both. When a Cisco SAF Client sends a register message to a Cisco SAF Forwarder, it establishes a relationship with the Cisco SAF Forwarder. The Cisco SAF Forwarder uses this register message to obtain a unique handle that distinctly identifies this Cisco SAF Client from others connected to the same forwarder. Only after a Cisco SAF Client registers is it able to advertise (publish) to, or request (subscribe), services. The figure below shows a typical Cisco SAF network.
When advertising a service, a Cisco SAF Client publishes (sends) advertisements to the Cisco SAF Forwarder that contain information about the service it offers. Services are identified by a unique service ID, sub-service ID, and instance ID, and are described by service data. For more information on service identifiers, see "Cisco SAF Service Identifier Number Formats". The Cisco SAF Client can send multiple publish requests, each advertising a distinct service. The Cisco SAF Forwarder advertises all services published by the Cisco SAF Client. The Cisco SAF Client can update an existing service advertisement by sending a new publish request for the same service. The client can also generate an unpublish request, which removes one of its existing service advertisements.
When requesting a service, the Cisco SAF Client sends a request notification of services using a subscribe request. The subscribe request contains a filter that describes the set of services in which the Cisco SAF Client is interested. In response to this request, the Cisco SAF Forwarder sends the current set of services that match the filter to the Cisco SAF Client in a series of notify requests. As with a publish request, the Cisco SAF Client can generate multiple subscribe requests, each with a different filter. The Cisco SAF Client can also generate an unsubscribe request, which removes one of its existing subscriptions.
Cisco SAF clients can be internal (existing within a Cisco SAF Forwarder) or external (existing on a separate device and communicating with a Cisco SAF forwarder using the XMCP protocol). Internal Cisco SAF clients include Capabilities Manager (see Configuring Capabilities Manager) and Cisco Unified Communications Manager Express (Cisco Unified CME). External Cisco SAF clients using XMCP include Cisco Unified Communications Manager.
External Cisco SAF Client using XMCP Overview
An external Cisco SAF Client initiates a TCP connection to a Cisco SAF Forwarder that has been configured as an XMCP server. Once the TCP connection is established, the client begins an XMCP session over this connection by sending an XMCP register message to the Cisco SAF Forwarder.
When an XMCP server receives a request, it locates the username attribute in that request and uses it to access its local copy of the password, and then computes its own message-integrity value for the request. If the computations match, then the passwords must match and the request is authenticated, permitting the XMCP client to act as a Cisco SAF Client. If they do not match, the password is incorrect and the request will be rejected.
Once the XMCP session has been established successfully, the XMCP client may send XMCP publish, unpublish, subscribe, and unsubscribe requests. When the server receives and successfully authenticates these requests, it translates the requests into the equivalent Cisco SAF Client requests and sends them to the Cisco SAF Forwarder. Similarly, Cisco SAF Client notify requests from the forwarder will be translated into XMCP notify requests and sent to the XMCP client.
Because an external Cisco SAF Client may lose connectivity to the Cisco SAF network in the event of a network outage, a Cisco SAF Forwarder requires periodic verification regarding the liveliness of the Cisco SAF Client to advertise its services into the Cisco SAF network. In XMCP, this is accomplished by exchanging a liveliness timer between the client and server at the time of registration. The XMCP client is responsible for ensuring that the interval between requests never exceeds this value. An XMCP client has no data (publish or subscribe) to send, so it generates a small keepalive message to refresh the timer on the server.
A Cisco SAF forwarder considers an external Cisco SAF Client failed if it has not seen an XMCP request from the client in a time period equal to the liveliness timer. When a Cisco SAF Forwarder detects that the Cisco SAF Client has failed, it withdraws the services advertised on behalf of that Cisco SAF Client from the network and removes any subscriptions that the Cisco SAF Client had established. As an alternative to waiting for the liveliness timer to expire, a Cisco SAF Client can be manually unregistered (sending an unregister request to terminate the XMCP session) to gracefully cause a Cisco SAF Forwarder to withdraw all services and subscriptions.
Cisco SAF Service Identifier Number Formats
A service is any information that a Cisco SAF Client application wishes to advertise, that can then be used by other Cisco SAF Client applications. A service advertisement consists of service data. Service advertisements are propagated between forwarders using header data. Cisco SAF Clients that are interested in a service receive, and may inspect, service header and service data.
A service identifier number uniquely identifies the service on a network. The following example shows the format of a service identifier number:
service:sub-service:instance.instance.instance.instance
The service identifier is a 16-bit decimal identifier for the major service being advertised. A major service refers to a specific technology area, such as Cisco Unified Communications (UC). Service identifiers are assigned by Cisco to various customers requiring an SAF client.
The following example shows the service ID values for IP Everywhere and Cisco Unified Communications:
Cisco Defined Numbers
SAF_SERVICE_ID_IPE = 100 ! IP Everywhere
SAF_SERVICE_ID_UC = 101 ! Unified Communications
The sub-service identifier is a 16-bit decimal identifier for the minor service being advertised. A sub-service (also referred to as a minor service) refers to the type of service within a technology. For example, within UC:
- Sub-service 1 is TDM gateway.
- Sub-service 2 is hosted-DN.
- Instance identifies a specific service advertisement for this kind of service. For example, service identifier 101:1:abcd.1234.ef.678 could be an advertisement of a UC (service 101) TDM gateway (sub-service 1) announced by the Communications Manager cluster in a certain location (instance abcd.1234.ef.678).
The instance identifier is a unique 128-bit number that identifies the specific service advertised.
Client teams define the use of sub-service and instance values for their applications. Clients must ensure instance uniqueness within a Cisco SAF domain.
Cisco SAF and Role of Domains in a Network
As the variety and number of network services grows, providing timely and reliable awareness of these services starts to play a more significant role in increasing productivity and efficiency. One of the biggest challenges in propagating service availability awareness over a WAN is one of scalability. As networks grow, the services offered by the devices on these networks increases. Protocols responsible for the service advertisement need to scale to handle this increased load. These protocols also need to react to rapid changes efficiently and propagate the new information in a timely manner.
Cisco SAF is designed to be a scalable solution for enterprise service locations and is capable of spanning LAN and WAN internet segments. As an enterprise solution, you can configure Cisco SAF to use domains to scale for very large networks. Just as Cisco Enhanced Interior Gateway Routing Protocol (EIGRP) defines the concept of an autonomous system in which routes can be searched for in a hierarchical manner, Cisco SAF employs the similar concept of a domain and sub-domains.
Cisco SAF provides a dynamic peer discovery and service advertisement propagation technique known as IP multicast. IP multicast requires the cooperation of IP Cisco SAF Forwarders (the devices that connect IP subnets together to form intranets). IP multicasting, however, may not be completely implemented across some intranets. In the absence of IP multicasting, Cisco SAF operates within the configured subnet, or within the groups of subnets over which IP multicast is supported.
Cisco SAF Forwarders offer two primary types of administrative domains (AD); a domain and a subdomain. A domain and a subdomain function the same with one notable exception; subdomains do not form unique neighbor relationships, but instead rely on a single peering.
Ideally, a network would only require a single domain to use for advertising all services. However, due to scaling and policy issues, some networks require the creation of multiple domains. The recommendation is to use a single domain. Consider using multiple domains when:
- More than 30,000 services are registered in a single domain
- Logical grouping of services is needed to restrict propagation of services
Closed groups are needed to prevent users from browsing services they are not allowed to access
Service redistribution allows different domains to exchange service information. Services may need to be bound to specific areas of the network, or the number of services in a given network my need to be limited. If you cannot use a single domain, service advertisement redistribution might be the solution.
Each domain on a network is separated into an administrative domain (AD). All Cisco SAF Forwarders in the same AD (running the same domain) have complete knowledge of the entire AS. A Cisco Forwarder that connects two (or more) administrative domains is known as a border Forwarder. A border Forwarder advertises service information from one AS to another AS. Proper design should also be considered if multiple border Forwarders are used to avoid loops (information learned from one AD being sent back to the same AD).
Cisco SAF Virtual Routers
Cisco EIGRP Service-Family Support extends the named configuration to allow configuration of multiple instances, which operate independently. The addition of a Virtual Router ID (VRID) to the base Cisco EIGRP packet encoding allows for multiple instances.
As each virtual router is created, a VRID is assigned to the top level router and shared with the address families and service families that are configured under it.
Cisco SAF Neighbor Relationships
Cisco SAF Forwarders can operate in networks that do not have routers that support the Cisco SAF Forwarder protocol. These networks are referred to as "dark nets." There are two methods for configuring Cisco SAF Forwarders over IP networks that do not support Cisco SAF (IP clouds); unicast Cisco SAF neighbors and multicast Cisco SAF neighbors.
You can use a unicast configuration to provide a reliable point-to-point adjacency with neighbors. As the number of Cisco SAF Forwarders increases, you can use multicast to provide an efficient transport between multiple Cisco SAF neighbors. A single IP multicast group address can be used for multiple Cisco SAF neighbors to exchange SAF information in a peer-group.
Benefits of Cisco SAF
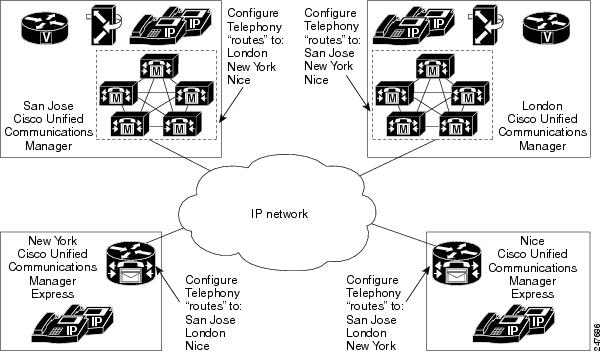
Traditionally, to locate services on a network, network applications must be configured with the hostname and the network address of the desired service or must use an overlay mechanism such as DNS. Existing protocols that support service advertisement provide periodic-based announcements of resource utilization. These network services are typically LAN-based.
The figure below shows a Cisco Unified Communications Manager network requiring a traditional configuration methodology.
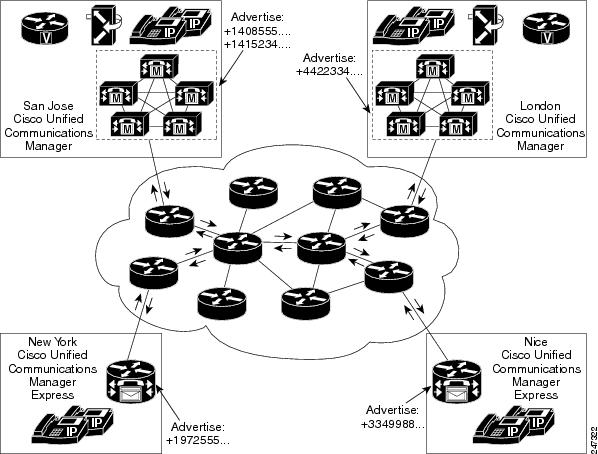
Cisco SAF provides a framework that allows networking applications to automatically discover the existence, location, and configuration of networked services within networks. This automated discovery of services replaces the manual entry of complex configurations such as dial plans, that often require repetitive configuration changes. Cisco SAF also allows applications to advertise and discover their services. Cisco SAF allows you to create a configuration once, and then have it propagate to all devices that require the information.
The figure below shows a Cisco Unified Communications Manager network using Cisco SAF.
You can configure a Cisco SAF Client either on the same router as the Cisco SAF Forwarder or on an external router.
How to Configure a Cisco SAF Forwarder
- Enabling Cisco SAF
- Configuring Interface-Specific Commands for Cisco SAF
- Configuring Cisco SAF for Multi-Topology Networks
- Configuring Static Neighbor Relationships for Cisco SAF
- Configuring Stub Routing for Cisco SAF
- Configuring Route Authentication for Cisco SAF
- Configuring Logs for Neighbor Changes and Warnings
- Configuring the Percentage of Link Bandwidth Used for Cisco SAF
- Setting Metric Dampening Intervals for Cisco SAF Interfaces
- Adjusting the Interval Between Hello Packets and the Hold Time
- Disabling Split Horizon
- Setting Metric Maximum Hops
Enabling Cisco SAF
DETAILED STEPS
Configuring Interface-Specific Commands for Cisco SAF
Cisco SAF provides an inheritance precedence for interface-specific commands. Configurations made in sf-interface configuration mode have priority over specific sf-interface and factory default configurations. To configure interface-specific commands under the service-family for Cisco SAF, use the following commands:
DETAILED STEPS
Configuring Cisco SAF for Multi-Topology Networks
Use the following configuration to register clients and publish or subscribe services into a named topology. If you configure a second topology using an existing topology name, but with a different ID, it will replace the existing topology, rather than create two IDs for the same topology.
To configure Cisco SAF for multi-topology networks, use the following commands:
DETAILED STEPS
Configuring Static Neighbor Relationships for Cisco SAF
DETAILED STEPS
Configuring Stub Routing for Cisco SAF
You can configure a Cisco SAF Forwarder as a stub router. For complete information on Cisco EIGRP stub routing, refer to the Configuring EIGRP module in the Cisco IOS IP Routing: EIGRP Configuration Guide .
To create an Cisco SAF stub router, use the following commands:
DETAILED STEPS
Configuring Route Authentication for Cisco SAF
Cisco SAF route authentication provides Message Digest 5 (MD5) authentication of routing updates from the routing protocol. The MD5 keyed digest in each packet prevents the introduction of unauthorized or false routing messages from unapproved sources. To configure route authentication for Cisco SAF, use the following commands:
DETAILED STEPS
Configuring Logs for Neighbor Changes and Warnings
By default, the system logs neighbor adjacency changes to help you monitor the stability of the routing system and detect problems. If you disabled logging of such changes and want to reenable logging, use the following commands:
DETAILED STEPS
Configuring the Percentage of Link Bandwidth Used for Cisco SAF
By default, packets consume a maximum of 50 percent of the link bandwidth, as configured with the bandwidth interface configuration command. You may want to change the value if a different level of link utilization is required or if the configured bandwidth does not match the actual link bandwidth (it may have been configured to influence route metric calculations). Use the following commands to configure the percentage of link bandwidth used for Cisco SAF.
DETAILED STEPS
Setting Metric Dampening Intervals for Cisco SAF Interfaces
Because metric components can be changed rapidly, the frequency of the changes can have an impact on the network. Frequent changes require that prefixes learned though the SAF interface be updated and sent to all adjacencies. This update can result in further updates and in a worst-case scenario, cause network-wide churn. To prevent such effects, metrics can be dampened or thresholds set so that any change that does not exceed the dampening threshold is ignored.
Network changes that cause an immediate update include any change in a metric that results in the router selecting a new nexthop or a down interface or router.
Dampening the metric changes can be configured based on a change or on a time interval.
If the dampening method is:
- Change-based, changes in routes learned though a specific interface or in the metrics for a specific interface will not be advertised to adjacencies until the computed metric changes from the last advertised value are significant enough to cause an update to be sent.
- Interval-based, changes in routes learned though a specific interface or in the metrics for a specific interface will not be advertised to adjacencies until the specified interval is met or unless the change results in a new route path selection. When the timer expires, routes that have outstanding changes to report are sent. If a route changes and the final metric of the route matches the last updated metric, no updated routes are sent.
Refer to the following sections for information on configuring change-based and interval-based metric dampening parameters.
Change-based Dampening Configuration
Use the following commands to set the maximum change-based dampening percentage for Cisco SAF interfaces.
DETAILED STEPS
Interval-based Dampening Configuration
Use the following commands to configure the interval-based dampening for Cisco SAF interfaces. The value you configure sets the interval when updates occur for topology changes that affect Cisco SAF interfaces and peers.
DETAILED STEPS
Adjusting the Interval Between Hello Packets and the Hold Time
Routing devices periodically send hello packets to each other to dynamically learn of other routers on their directly attached networks. This information is used to discover neighbors and to learn when neighbors become unreachable or inoperative.
By default, hello packets are sent every 5 seconds. The exception is on low-speed, nonbroadcast multiaccess (NBMA) media on which the default hello interval is 60 seconds. Low speed is considered to be a rate of T1 or slower as specified in the bandwidth interface configuration command. The default hello interval remains at 5 seconds for high-speed NBMA networks. Note that for the purposes of Frame Relay and Switched Multimegabit Data Service (SMDS), networks may or may not be considered to be NBMA. These networks are considered NBMA if the interface has not been configured to use physical multicasting; otherwise they are not considered NBMA.
The hold time is advertised in hello packets and indicates to neighbors the length of time they should consider the sender valid. The default hold time is three times the hello interval, or 15 seconds. For slow-speed NBMA networks, the default hold time is 180 seconds. On congested and large networks, the default hold time might not be sufficient time for all routers to receive hello packets from their neighbors. In this case, you may want to increase the hold time. Do not adjust the hold time without advising your technical support personnel. To change the hold time on a specific interface for a particular routing process designated by the autonomous system number, use the hold time command.
You can adjust the interval between hello packets and the hold time. To change the interval between hello packets and the hold time, use the following commands in interface configuration mode.
DETAILED STEPS
Disabling Split Horizon
When split horizon is enabled on an interface, it blocks route information (such as update and query packets) from being advertised by a router out of any interface from which that information originates. Controlling update and query packets in this manner reduces the possibility of routing loops.
This behavior usually optimizes communications among multiple routing devices, particularly when links are broken. However, with nonbroadcast networks (such as Frame Relay and SMDS), situations can arise for which this behavior is less than ideal. For these situations, including networks in which you have Cisco SAF configured, you may want to disable split horizon.
By default, split horizon is enabled on all interfaces. To disable split horizon, use the no split-horizon command in interface configuration mode.
DETAILED STEPS
Setting Metric Maximum Hops
Maximum hops limits the number of hops a service can propagate to advertise its service. The default number of maximum hops is 100.
To limit the number of hops used to advertise a service, use the following commands:
DETAILED STEPS
How to Configure a Cisco SAF External Client
This section describes the tasks to configure a Cisco SAF External Client.
Cisco SAF Clients connect to the Cisco SAF network in one of two ways:
- Reside on the same router as a Cisco SAF Forwarder, in which case the Cisco SAF Client uses an internal API to connect to a Cisco SAF Forwarder. See the "Configuring Capabilities Manager" section for more information.
- Is external to a Cisco SAF Forwarder. In this configuration, the SAF Client is referred to as a Cisco SAF External Client, and it requires a protocol interface for connecting to the Cisco SAF Forwarder.
Configuring a Cisco SAF External Client
DETAILED STEPS
How to Display Cisco SAF Statistics
DETAILED STEPS
How to Delete Information from a Cisco SAF Configuration
To delete service-family information from a Cisco SAF configuration, use the following commands in EXEC mode.
DETAILED STEPS
Configuration Examples for Cisco SAF
- Example: Enabling Cisco SAF
- Example: Configuring Cisco SAF Interfaces
- Example: Configuring Cisco SAF Topology
- Example: Configuring Cisco SAF Stub Routing
- Example: Configuring Cisco SAF with IP-RIP
- Example: Configuring Cisco SAF with OSPF
- Example: Configuring Cisco SAF with EIGRP
- Example: Configuring Cisco SAF Forwarders Located on Separate LANs
- Configuring a Centralized Cisco SAF Forwarder Example
- Examples: Configuring a Cisco SAF Client
Example: Configuring Cisco SAF Interfaces
The following example places the router in service-family configuration mode and enables all interfaces.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# sf-interface default Router(config-router-sf-interface)# no shutdown
The following example places the router in service-family configuration mode and enables Ethernet interface 0/0.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# sf-interface ethernet0/0
The following example places the router in service-family configuration mode and enables SAF on all interfaces, except the Ethernet0/0 interface.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 3 Router(config-router-sf)# interface default Router(config-router-sf)# sf-interface ethernet0/0 Router(config-router-sf-interface)# shutdown Router(config-router-sf-interface)# end
The following example places the router in service-family configuration mode and enables SAF on the Ethernet2/0 and Ethernet2/1 interfaces and disables all other interfaces.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 2 Router(config-router-sf)# sf-interface default Router(config-router-sf-interface)# shutdown Router(config-router-sf-interface)# sf-interface ethernet2/0 Router(config-router-sf-interface)# no shutdown Router(config-router-sf-interface)# sf-interface ethernet2/1 Router(config-router-sf-interface)# no shutdown Router(config-router-sf-interface)# end
Example: Configuring Cisco SAF Topology
The following examples configures a Cisco SAF topology base.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# sf-interface default Router(config-router-sf-interface)# no shutdown Router(config-router-sf-interface)# topology base
Example: Configuring Cisco SAF with IP-RIP
The following configuration example enables Cisco SAF with IP-RIP routing on network 10.0.0.0.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# topology base Router(config-router-sf-topology)# exit-sf-topology Router(config-router-sf)# exit service-family Router(config-router)# router rip Router(config-router)# network 10.0.0.0
Example: Configuring Cisco SAF with OSPF
The following configuration example enables Cisco SAF with OSPF routing on network 10.0.0.0, area 0.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# topology base Router(config-router-sf-topology)# exit-sf-topology Router(config-router-sf)# exit service-family Router(config-router)# router ospf 787 Router(config-router)# network 10.0.0.0 0.0.0.255 area 0
Example: Configuring Cisco SAF with EIGRP
The following configuration example enables Cisco SAF with EIGRP routing on network 10.0.0.0.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 6476 Router(config-router-sf)# network 10.0.0.0 0.0.0.255 Router(config-router-sf)# topology base Router(config-router-sf-topology)# exit-af-topology Router(config-router-sf)# exit-service-family Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# topology base
 Note | There is no requirement to run routing over the same interfaces or networks in which services are distributed, however this could lead to services being distributed to areas where reachability is not guaranteed. |
Example: Configuring Cisco SAF Forwarders Located on Separate LANs
The following examples configures two Cisco SAF Forwarders located on separate LANs.
 Note | Use loopback mode to configure remote neighbors. |
Cisco SAF Forwarder 1:
Router(config)# interface loopback1 Router(config-if)# ip address 10.1.1.1 255.255.255.255 Router(config-if)# exit Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 1 Router(config-router-sf)# neighbor 10.2.2.2 loopback1 remote 10
Cisco SAF Forwarder 2:
Router(config)# interface loopback1 Router(config-if)# ip address 10.2.2.2 255.255.255.255 Router(config-if)# exit Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 1 Router(config-router-sf)# neighbor 10.1.1.1 loopback1 remote 10
 Note | This example assumes IP routing is configured between the two routers and the routers can ping both loopbacks. |
Configuring a Centralized Cisco SAF Forwarder Example
The following example configures a centralized Cisco SAF Forwarder from which all service advertisements will send to neighbors on IP addresses 10.4.15.5 and 10.4.15.1.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# sf-interface loopback0 Router(config-router-sf-interface)# no split-horizon Router(config-router-sf-interface)# exit-sf-interface Router(config-router-sf)# topology base Router(config-router-sf-topology)# exit-sf-topology Router(config-router-sf)# neighbor 10.4.15.5 Loopback0 remote 20 Router(config-router-sf)# neighbor 10.4.15.1 Loopback0 remote 20 Router(config-router-sf)# exit-service-family
Examples: Configuring a Cisco SAF Client
The following example configures a Cisco SAF External Client named example, with a username of username_example, a password of password_example, and a keepalive setting of 360000 seconds.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# topology base Router(config-router-sf-topology)# external-client example Router(config-router-sf-topology)# exit-sf-topology Router(config-router-sf)# exit-service-family Router(config-router)# exit Router(config)# service-family external-client listen ipv4 3444 Router(config-external-client)# external-client example Router(config-external-client-mode)# username username_example Router(config-external-client-mode)# password password_example Router(config-external-client-mode)# keepalive 360000
The following example configures eight Cisco SAF External Clients named example1 through example5, with usernames of username_example1 through username_example5, passwords of password_example1 through password_example5, and keepalive settings of 360000 seconds.
Router(config)# router eigrp saf Router(config-router)# service-family ipv4 autonomous-system 4533 Router(config-router-sf)# topology base Router(config-router-sf-topology)# external-client example1 Router(config-router-sf-topology)# external-client example2 Router(config-router-sf-topology)# external-client example3 Router(config-router-sf-topology)# external-client example4 Router(config-router-sf-topology)# external-client example5 Router(config-router-sf-topology)# exit-sf-topology Router(config-router-sf)# exit-service-family Router(config-router)# exit Router(config)# service-family external-client listen ipv4 3444 Router(config-external-client)# external-client example1 Router(config-external-client-mode)# username username_example1 Router(config-external-client-mode)# password password_example1 Router(config-external-client-mode)# keepalive 360000 Router(config-external-client-mode)# external-client example2 Router(config-external-client-mode)# username username_example2 Router(config-external-client-mode)# password password_example2 Router(config-external-client-mode)# keepalive 360000 Router(config-external-client-mode)# external-client example3 Router(config-external-client-mode)# username username_example3 Router(config-external-client-mode)# password password_example3 Router(config-external-client-mode)# keepalive 360000 Router(config-external-client-mode)# external-client example4 Router(config-external-client-mode)# username username_example4 Router(config-external-client-mode)# password password_example4 Router(config-external-client-mode)# keepalive 360000 Router(config-external-client-mode)# external-client example5 Router(config-external-client-mode)# username username_example5 Router(config-external-client-mode)# password password_example5 Router(config-external-client-mode)# keepalive 360000
Additional References
Related Documents
| Related Topic | Document Title |
|---|---|
|
Cisco IOS commands |
|
|
Service Advertisement Framework commands |
Cisco IOS Service Advertisement Framework Technology Command Reference |
Technical Assistance
| Description | Link |
|---|---|
|
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for Cisco SAF
| Table 1 | Feature Information for Cisco Service Advertisement Framework |
|
Feature Name |
Software Releases |
Feature Configuration Information |
|---|---|---|
|
Cisco Service Advertisement Framework |
15.0M, 12.2(33)SRE, 12.2(33)XNE, 15.1T, 12.2(33)SXI4, 15.0(1)S, 15.1(2)S, 12.2(50)SY, 15.2(1)T, 15.2(3)T, 15.2(2)S, 15.1(1)SG Cisco IOS XE Release 2.5, Cisco IOS XE Release 3S, Cisco IOS XE Release 3.3SG |
This feature allows applications to discover the existence, location, and configuration of networked resources within networks, and provides a timely and reliable awareness of the services within networks, as applications advertise and discover services on networks. This feature was introduced in Cisco IOS Release 15.0M. In Cisco IOS XE Release 2.5, this feature was introduced on the Cisco ASR 1000 Series Aggregation Services Routers. The following commands were introduced in this feature:
|
|
Cisco Service Advertisement Framework |
15.0M, 12.2(33)SRE, 12.2(33)XNE, 15.0(1)S, 15.1(2)S, 15.2(3)T, 15.2(2)S Cisco IOS XE Release 2.5, Cisco IOS XE Release 3S, Cisco IOS XE Release 3.4S, Cisco IOS XE Release 3.6S |
The following commands were modified in this feature: |
|
Dynamic Neighbor |
15.1(2)S, 15.2(3)T, 15.2(2)S, XE 3.6S |
The following commands were introduced or modified: |
|
Capabilities Manager |
15.0(1)SY, 15.2(3)T, 15.2(2)S, XE 3.6S |
The following commands were introduced or modified: |
|
XMCP (Extensible Messaging Client Protocol) |
15.2(2)T, 15.2(1)S, 15.2(3)T, 15.2(2)S, XE 3.6S |
The following commands were introduced or modified: |
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.