在ISE和9800 WLC上配置Radius DTLS
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
目錄
簡介
本文檔介紹建立在ISE和9800 WLC之間配置RADIUS DTLS的必要證書的方法。
背景
RADIUS DTLS是RADIUS通訊協定的安全形式,其中RADIUS訊息透過資料傳輸層安全(DTLS)通道傳送。要在身份驗證伺服器和身份驗證器之間建立此隧道,需要一組證書。此憑證集需要設定某些擴充金鑰使用(EKU)憑證擴充模組,尤其是WLC憑證上的使用者端驗證、伺服器驗證以及ISE憑證的使用者端驗證。
必要條件
需求
思科建議您瞭解以下主題:
- 如何設定9800 WLC(存取點(AP))以達成基本操作
- 如何使用 OpenSSL 應用程式
- 公開金鑰基礎架構(PKI)和數位憑證
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- OpenSSL應用程式(3.0.2版)。
- ISE(版本3.1.0.518)
- 9800 WLC(版本17.12.3)
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
設定
概觀
其目的是建立具有根CA和中繼CA的兩級證書頒發機構來簽署終端證書。簽署憑證後,系統會將其匯入WLC和ISE。最後,裝置配置為使用這些證書執行RADIUS DTLS身份驗證。

附註:本文檔使用Linux特定命令來建立和排列檔案。解釋這些命令,以便您能在其它有OpenSSL的作業系統上執行相同的操作。
可選 — 建立WLC和ISE RADIUS DTLS裝置證書
RADIUS DTLS協定需要在ISE和WLC之間交換證書以建立DTLS隧道。如果您還沒有有效的證書,可以建立本地CA以生成證書,請參閱在OpenSSL上配置多級證書頒發機構以生成CIsco IOS® XE相容證書,並從開始到步驟結束時執行文檔中概述的步驟 建立中間CA證書。
在openssl.cnf檔案中新增配置部分
開啟您的openssl.cnf組態檔,並在底端複製並貼上用於產生有效憑證簽署請求(CSR)的WLC和ISE區段。
每個ISE_device_req_ext和WLC_device_req_ext部分都指向要包含在CSR上的SAN清單:
#Section used for CSR generation, it points to the list of subject alternative names to add them to CSR
[ ISE_device_req_ext ]
subjectAltName = @ISE_alt_names
[ WLC_device_req_ext ]
subjectAltName = @WLC_alt_names
#DEFINE HERE SANS/IPs NEEDED for **ISE** device certificates
[ISE_alt_names]
DNS.1 = ISE.example.com
DNS.2 = ISE2.example.com
#DEFINE HERE SANS/IPs NEEDED for **WLC** device certificates
[WLC_alt_names]
DNS.1 = WLC.example.com
DNS.2 = WLC2.example.com作為一項安全措施,CA會覆寫CSR上存在的任何SAN以對其進行簽署,如此一來,未授權裝置便無法接收其不允許使用的名稱的有效憑證。若要將SAN重新新增到已簽名的證書中,請使用subjectAltName引數指向與CSR生成所使用的清單SAN相同的清單SAN。
ISE需要serverAuth和clientAuth EKU都存在於憑證上,而WLC僅需要clientAuth。它們將使用extendedKeyUsage引數新增到簽名證書中。
在openssl.cnf檔案的底部複製貼上用於憑證簽名的區段:
#This section contains the extensions used for the device certificate sign
[ ISE_cert ]
basicConstraints=CA:FALSE
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer:always
#EKU client and server is needed for RADIUS DTLS on ISE
extendedKeyUsage = serverAuth, clientAuth
subjectAltName = @ISE_alt_names
[ WLC_cert ]
basicConstraints=CA:FALSE
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer:always
#EKU client is needed for RADIUS DTLS on WLC
extendedKeyUsage = clientAuth
subjectAltName = @WLC_alt_names
建立WLC裝置憑證
建立新資料夾以在安裝了名為IntermCA.db.certs的中間CA證書資料夾內的OpenSSL的電腦上儲存WLC證書。新資料夾稱為WLC:
mkdir ./IntermCA/IntermCA.db.certs/WLC修改openssl.cnf檔案的[WLC_alt_names]部分的DNS引數。更改為所需值提供的示例名稱。這些值會填寫WLC憑證的SAN欄位:
[WLC_alt_names]
DNS.1 = WLC.example.com <-----Change the values after the equals sign
DNS.2 = WLC2.example.com <-----Change the values after the equals sign使用WLC_device_req_ext(用於SAN)一節中的資訊建立WLC私鑰和WLC CSR:
openssl req -newkey rsa:4096 -keyout ./IntermCA/IntermCA.db.certs/WLC/WLC.key -nodes -config openssl.cnf -out ./IntermCA/IntermCA.db.certs/WLC/WLC.csr -reqexts WLC_device_req_extOpenSSL會開啟一個互動式提示,提示您輸入可分辨名稱(DN)詳細資訊:
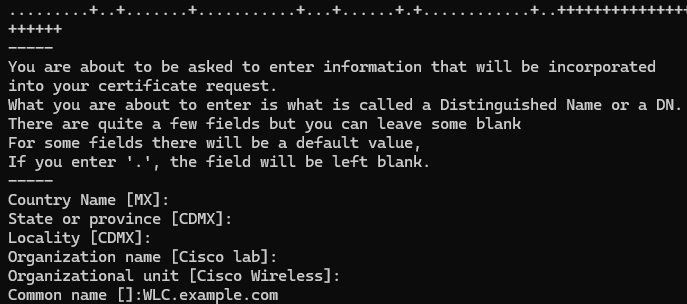 WLC憑證可分辨名稱互動提示
WLC憑證可分辨名稱互動提示

注意:在互動提示上提供的公用名(CN)必須與openssl.cnf檔案的[WLC_alt_names]部分中的名稱之一相同。
使用名為IntermCA的CA將名為WLC.csr的WLC CSR與[WLC_cert] 下定義的延伸部分簽名,並將簽署的憑證儲存在./IntermCA/IntermCA.db.certs/WLC內。WLC裝置憑證稱為WLC.crt:
openssl ca -config openssl.cnf -extensions WLC_cert -name IntermCA -out ./IntermCA/IntermCA.db.certs/WLC/WLC.crt -infiles ./IntermCA/IntermCA.db.certs/WLC/WLC.csr9800 WLC需要憑證為pfx格式才能匯入。建立包含簽署WLC憑證的CA鏈結的新檔案,這稱為certfile:
cat ./RootCA/RootCA.crt ./IntermCA/IntermCA.crt > ./IntermCA/IntermCA.db.certs/WLC/certfile.crt
若要建立.pfx檔案,請根據WLC版本運行以下命令之一。
對於早於17.12.1的版本:
openssl pkcs12 -export -macalg sha1 -legacy -descert -out ./IntermCA/IntermCA.db.certs/WLC/WLC.pfx -inkey ./IntermCA/IntermCA.db.certs/WLC/WLC.key -in ./IntermCA/IntermCA.db.certs/WLC/WLC.crt -certfile ./IntermCA/IntermCA.db.certs/WLC/certfile.crt
對於版本17.12.1或更高版本:
openssl pkcs12 -export -out ./IntermCA/IntermCA.db.certs/WLC/WLC.pfx -inkey ./IntermCA/IntermCA.db.certs/WLC/WLC.key -in ./IntermCA/IntermCA.db.certs/WLC/WLC.crt -certfile ./IntermCA/IntermCA.db.certs/WLC/certfile.crt建立ISE裝置證書
建立一個新資料夾,以在安裝了名為IntermCA.db.certs的中間CA證書資料夾內的OpenSSL的電腦上儲存ISE證書。新資料夾稱為ISE:
mkdir ./IntermCA/IntermCA.db.certs/ISE修改openssl.cnf檔案的[ISE_alt_names]部分的DNS引數。更改為您所需的值提供的示例名稱,這些值將填充WLC證書的SAN欄位:
[ISE_alt_names]
DNS.1 = ISE.example.com <-----Change the values after the equals sign
DNS.2 = ISE2.example.com <-----Change the values after the equals sign
使用ISE_device_req_ext部分的資訊為SAN建立ISE私鑰和ISE CSR:
openssl req -newkey rsa:2048 -sha256 -keyout ./IntermCA/IntermCA.db.certs/ISE/ISE.key -nodes -config openssl.cnf -out ./IntermCA/IntermCA.db.certs/ISE/ISE.csr -reqexts ISE_device_req_extOpenSSL會開啟一個互動式提示,提示您輸入可分辨名稱(DN)詳細資訊:
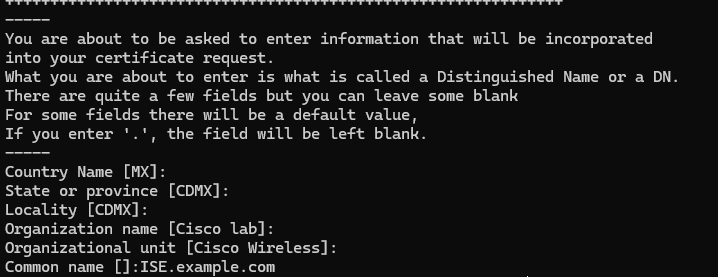 ISE證書可分辨名稱互動式提示
ISE證書可分辨名稱互動式提示

注意:互動式提示中提供的CN必須與openssl.cnf檔案的[ISE_alt_names]部分中的名稱完全相同。
使用名為IntermCA的CA使用在[ISE_cert] 下定義的擴展對名為ISE.csr的ISE CSR進行簽名,並將簽名的證書儲存在./IntermCA/IntermCA.db.certs/WLC內。ISE裝置證書稱為ISE.crt:
openssl ca -config openssl.cnf -extensions ISE_cert -name IntermCA -out ./IntermCA/IntermCA.db.certs/ISE/ISE.crt -infiles ./IntermCA/IntermCA.db.certs/ISE/ISE.csr
可選 — 在ISE和WLC上使用自簽名證書
信任ISE上的WLC證書
- 檢索WLC自簽名證書並將其上傳到ISE
9800-controller# show crypto pki certificates | include self
並記下證書名稱(例如<TP-Self>)。
2.獲取自簽名證書的CA證書
9800-controller# show crypto pki certificate pem < self signed cert name>複製憑證並使用檔名<certname>.pem儲存
3.完成此步驟後,將證書上傳到「受信任證書」下的ISE。
ISE導航路徑:受信→證書→系統→證管理
信任WLC上的ISE證書
到目前為止,我們已經信任ISE上的WLC證書。現在,我們需要下載ISE證書並將其配置為WLC上的受信任證書。
1.在ISE上,導航至:
管理→統→證和→統證書
2.下載.pem格式的證書(由RADIUS DTLS使用)。
3.下載後,以文本格式開啟檔案,然後以十六進位制格式複製證書內容。
4.接下來,導覽至WLC,建立信任點,並將複製憑證貼上到該信任點中。
9800-controller# conf t
crypto pki trustpoint iseself
revocation-check none
enrollment none
exit
9800-controller# crypto pki trustpoint authenticate iseself
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
--- paste the hex certifcate ---
將伺服器和客戶端用於DTLS
按如下方式使用信任點:DTLS伺服器必須引用ISE信任點,而DTLS客戶端必須引用WLC信任點。
可選 — 在WLC上使用自簽名證書,在ISE上使用第三方簽名證書
首先上傳證書以在ISE上獲得信任
由於這涉及第三方證書,因此要建立裝置信任,我們需要將根證書和中間證書都匯入到受信任的證書儲存中。請參閱「將證書匯入裝置」部分進行導航。
信任WLC上的第三方證書進行DTLS通訊
由於WLC CA和第三方CA不同,我們已透過繼續中間的鏈驗證在WLC上為根網路建立新的兩個信任點。
9800-controller(config)#crypto pki trustpoint ISEroot
9800-controller(ca-trustpoint)#revocation-check none
9800-controller(ca-trustpoint)#enrollment terminal
9800-controller(ca-trustpoint)#chain-validation stop
9800-controller(ca-trustpoint)#exit
9800-controller(config)#crypto pki authenticate ISEroot
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
------Paste the ISE root CA-----
在ISE CA鏈上匯入下一個中間CA證書,即根CA頒發的CA證書:
hamariomed1(config)#crypto pki trustpoint ISEintermediate
hamariomed1(ca-trustpoint)#revocation-check none
hamariomed1(ca-trustpoint)#chain-validation continue ISErootCA
hamariomed1(ca-trustpoint)#enrollment terminal
hamariomed1(ca-trustpoint)#exit
hamariomed1(config)#crypto pki authenticate ISEintermediate
Enter the base 64 encoded CA certificate.
End with a blank line or the word "quit" on a line by itself
------Paste the ISE intermediate CA-------
鏈上的每個附加CA都需要一個單獨的信任點。鏈中的每個信任點必須引用包含要使用chain-validation continue <Issuer trustpoint name>命令匯入的證書的頒發者證書的信任點。
匯入與您的CA鏈包含的CA證書數量相等的CA證書。匯入ISE裝置證書的頒發者CA後,請記下此信任點的名稱。
您無需在WLC上匯入ISE裝置證書即可使RADIUS DTLS正常工作。
將證書匯入到裝置
將證書匯入到ISE
1.將根CA證書從ISE證書鏈匯入到受信任的證書庫。
2.導航到管理>系統>證書>受信任證書。
3.按一下「瀏覽」並選擇Root.crt檔案。
4.選中Trust for authentication within ISE和Trust for client authentication and Syslog覈取方塊,然後按一下Submit:
 ISE根CA證書匯入對話方塊
ISE根CA證書匯入對話方塊
對中間證書(如果存在)執行相同操作。

附註:對作為ISE證書驗證鏈一部分的任何CA證書重複這些步驟。請始終從根CA證書開始,並以鏈的最低中間CA證書結束。
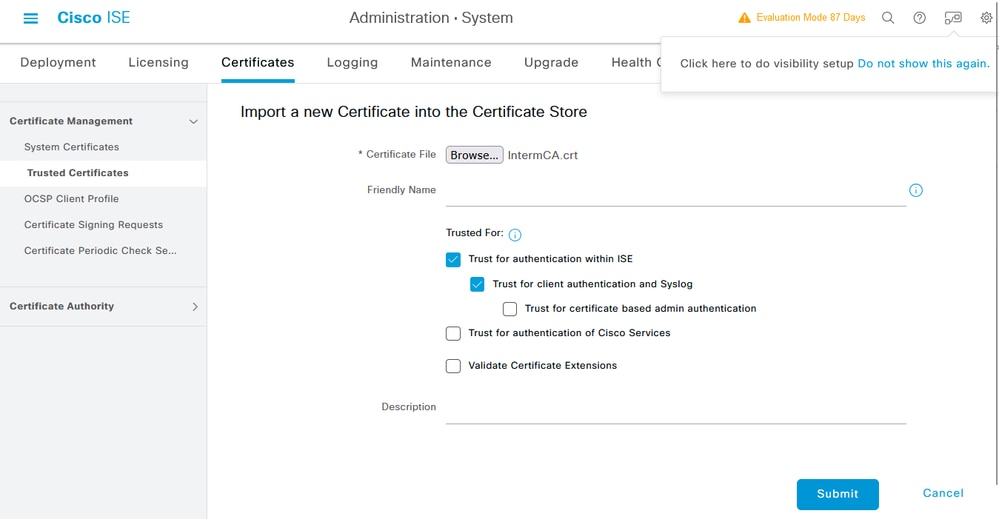 ISE中繼CA證書匯入對話方塊
ISE中繼CA證書匯入對話方塊

注意:如果ISE證書和WLC證書由不同的CA頒發,您必須同時匯入屬於WLC證書鏈的所有CA證書。在您匯入這些CA證書之前,ISE不會接受DTLS證書交換上的WLC證書。
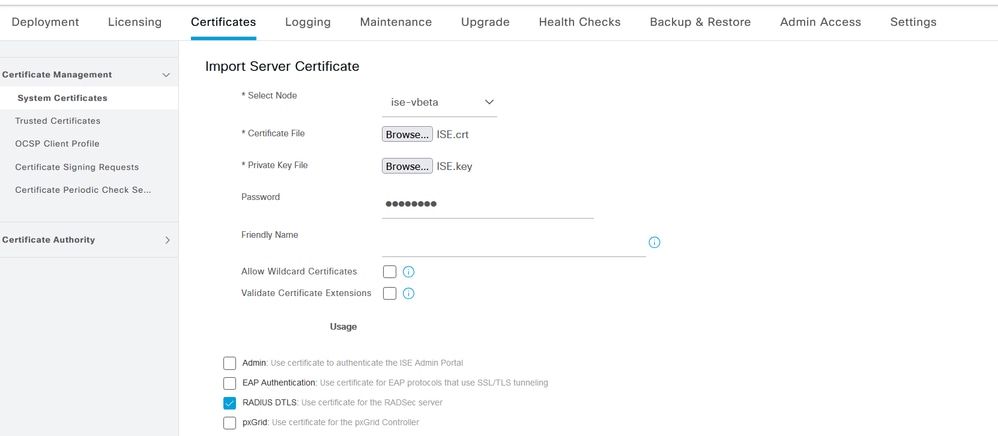 ISE裝置證書匯入選單
ISE裝置證書匯入選單

提示:您只需在此步驟中匯入ISE裝置證書。此證書是建立DTLS隧道的ISE交換。沒有必要匯入WLC裝置憑證和私密金鑰,因為已使用先前匯入的CA憑證驗證WLC憑證。
將憑證匯入WLC
- 在WLC上導覽至Configuration > Security > PKI Management,然後前往Add Certificate索引標籤。
- 按一下Import PKCS12 Certificate下拉選單,將傳輸型別設定為Desktop(HTTPS)。
- 按一下Select File 按鈕,然後選擇.pfx之前準備的檔案。
- 鍵入匯入密碼,最後按一下Import。
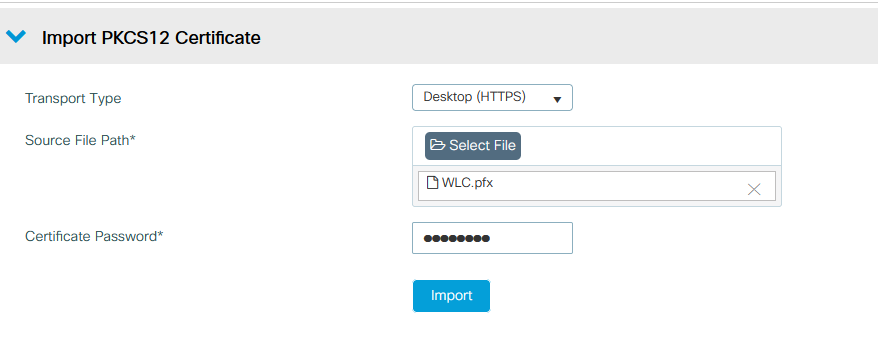 WLC Certificate Import對話方塊
WLC Certificate Import對話方塊
有關匯入過程的詳細資訊,請參閱在Catalyst 9800 WLC上產生和下載CSR憑證。
如果WLC沒有可以通過網路檢查的證書吊銷清單,請在每個自動建立的信任點內禁用吊銷檢查:
9800#configure terminal
9800(config)#crypto pki trustpoint WLC.pfx
9800(config)#revocation-check none
9800(config)#exit
9800(config)#crypto pki trustpoint WLC.pfx-rrr1
9800(config)#revocation-check none
9800(config)#exit
附註:如果使用在OpenSSL上設定多級CA以產生Cisco IOS XE憑證檔案在OpenSSL上建立多級CA,則必須在未建立CRL伺服器時停用撤銷檢查。
自動匯入會建立包含WLC證書及其CA證書所需的信任點。

提示:如果WLC證書由與ISE證書相同的CA頒發,則您可以使用從WLC證書匯入中自動建立的相同信任點。無需單獨匯入ISE證書。
配置RADIUS DTLS
ISE 組態
將WLC作為網路裝置新增到ISE中,為此,請導航到管理>網路資源>網路裝置>新增
輸入裝置名稱以及產生RADIUS流量的WLC介面的IP。通常是無線管理介面IP。向下滾動並選中RADIUS Authentication Settings以及DTLS Required,然後按一下Submit:
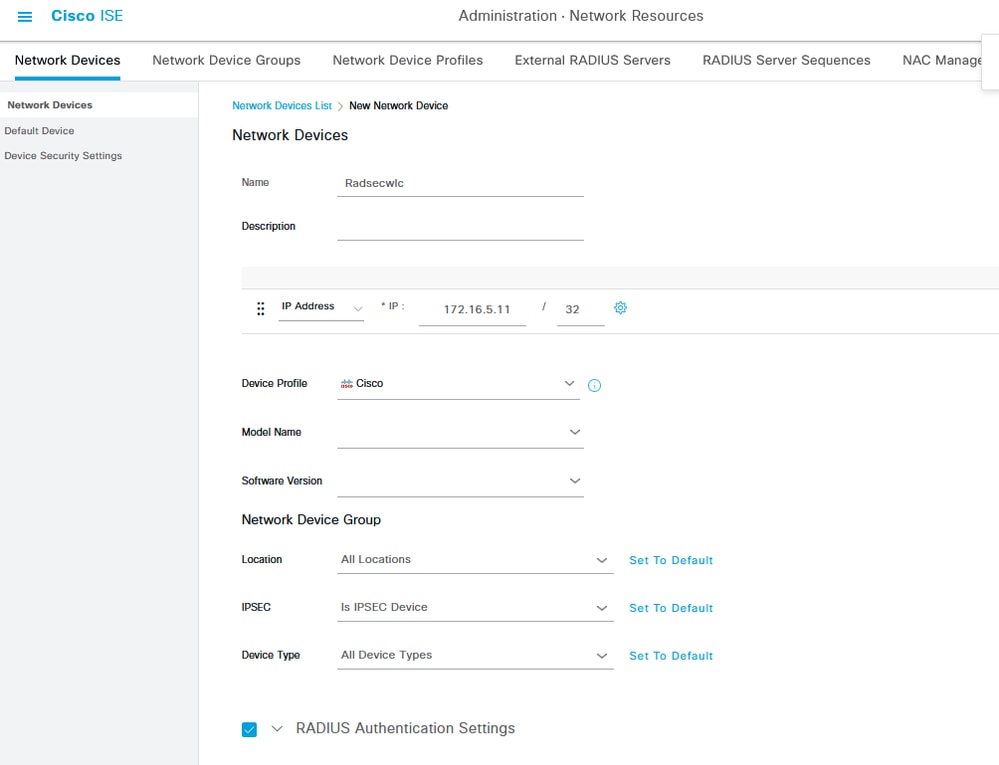 新網路裝置配置
新網路裝置配置
 ISE上網路裝置的RADIUS DTLS設定
ISE上網路裝置的RADIUS DTLS設定
WLC組態
定義新的Radius伺服器以及ISE IP地址和預設埠Radius DTLS。此配置僅在CLI上可用:
9800#configure terminal
9800(config)#radius server ISE
9800(config-radius-server)#address ipv4
9800(config-radius-server)#dtls port 2083 Radius DTLS必須使用共用密碼radius/dtls,9800 WLC會忽略除以下金鑰以外的任何已配置金鑰:
9800(config-radius-server)#key radius/dtls
使用dtls trustpoint client 命令配置包含WLC裝置證書的信任點,以交換DTLS隧道。
使用dtls trustpoint server 命令配置包含ISE裝置證書頒發者CA的信任點。
僅當由同一CA頒發WLC和ISE證書時,客戶端和伺服器信任點名稱相同:
9800(config-radius-server)#dtls trustpoint client WLC.pfx
9800(config-radius-server)#dtls trustpoint server WLC.pfx配置WLC以檢查ISE證書上是否存在一個主題備用名稱(SAN)。此配置必須與證書的SAN字段中存在的其中一個SAN完全匹配。
9800 WLC不會對SAN欄位執行基於正則表達式的相符。 dtls match-server-identity hostname *.example.com例如,這表示在其SAN欄位上具有*.example.com的萬用字元憑證的命令正確,但在SAN欄位上包含www.example.com的憑證的命令不正確。
WLC不會針對任何名稱伺服器檢查此名稱:
9800(config-radius-server)#dtls match-server-identity hostname ISE.example.com
9800(config-radius-server)#exit 建立新的伺服器組以使用新的Radius DTLS進行身份驗證:
9800(config)#aaa group server radius Radsec
9800(config-sg-radius)#server name ISE
9800(config-sg-radius)#exit
從此以後,您可以像使用WLC上的任何其他伺服器群組一樣使用此伺服器群組。請參閱在Catalyst 9800無線控制器系列上配置802.1X身份驗證,以使用此伺服器進行無線客戶端身份驗證。
驗證
驗證憑證資訊
要驗證所建立證書的證書資訊,請在linux終端中運行命令:
openssl x509 -in -text -noout 它顯示完整的證書資訊。這對於確定給定證書的頒發者CA或證書是否包含所需的EKU和SAN非常有用:
 Cisco IOS XE裝置證書資訊,如OpenSSL所示
Cisco IOS XE裝置證書資訊,如OpenSSL所示
執行測試身份驗證
您可以在WLC中使用命令測試Radius DTLS功能 test aaa group
9800#test aaa group Radsec testuser Cisco123 new-code
User successfully authenticated
USER ATTRIBUTES
username 0 "testuser"

附註:測試命令上的訪問拒絕輸出表示WLC收到Access-Reject RADIUS消息,在這種情況下RADIUS DTLS工作正常。但是,這也可能表示無法建立DTLS隧道。test命令無法區分這兩種情況,請參閱故障排除部分以確定是否存在問題。
疑難排解
要檢查身份驗證失敗的原因,可以在執行測試身份驗證之前啟用這些命令。
9800#debug radius
9800#debug radius radsec
9800#terminal monitor 以下是啟用調試後成功進行身份驗證的輸出:
9800#test aaa group Radsec testuser Cisco123 new-code
User successfully authenticated
USER ATTRIBUTES
username 0 "testuser"
9800#
Jul 18 21:24:38.301: %PARSER-5-HIDDEN: Warning!!! ' test platform-aaa group server-group Radsec user-name testuser Cisco123 new-code blocked count delay level profile rate users ' is a hidden command. Use of this command is not recommended/supported and will be removed in future.
Jul 18 21:24:38.313: RADIUS/ENCODE(00000000):Orig. component type = Invalid
Jul 18 21:24:38.313: RADIUS/ENCODE(00000000): dropping service type, "radius-server attribute 6 on-for-login-auth" is off
Jul 18 21:24:38.313: RADIUS(00000000): Config NAS IP: 0.0.0.0
Jul 18 21:24:38.313: vrfid: [65535] ipv6 tableid : [0]
Jul 18 21:24:38.313: idb is NULL
Jul 18 21:24:38.313: RADIUS(00000000): Config NAS IPv6: ::
Jul 18 21:24:38.313: RADIUS(00000000): sending
Jul 18 21:24:38.313: RADIUS/DECODE(00000000): There is no General DB. Want server details may not be specified
Jul 18 21:24:38.313: RADSEC: DTLS default secret
Jul 18 21:24:38.313: RADIUS/ENCODE: Best Local IP-Address 172.16.5.11 for Radius-Server 172.16.18.123
Jul 18 21:24:38.313: RADSEC: DTLS default secret
Jul 18 21:24:38.313: RADIUS(00000000): Send Access-Request to 172.16.18.123:2083 id 53808/10, len 54
RADIUS: authenticator C3 4E 34 0A 91 EF 42 53 - 7E C8 BB 50 F3 98 B3 14
Jul 18 21:24:38.313: RADIUS: User-Password [2] 18 *
Jul 18 21:24:38.313: RADIUS: User-Name [1] 10 "testuser"
Jul 18 21:24:38.313: RADIUS: NAS-IP-Address [4] 6 172.16.5.11
Jul 18 21:24:38.313: RADIUS_RADSEC_ENQ_WAIT_Q: Success Server(172.16.18.123)/Id(10)
Jul 18 21:24:38.313: RADIUS_RADSEC_CLIENT_PROCESS: Got DATA SEND MSG
Jul 18 21:24:38.313: RADIUS_RADSEC_SOCK_SET: 0 Success
Jul 18 21:24:38.313: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 18 21:24:38.313: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 18 21:24:38.313: RADIUS_RADSEC_HASH_KEY_ADD_CTX: add [radius_radsec ctx(0x7522CE91BAC0)] succeedd for sock_no(0)
Jul 18 21:24:38.313: RADIUS_RADSEC_GET_SOURCE_ADDR: Success
Jul 18 21:24:38.313: RADIUS_RADSEC_GET_SOCK_ADDR: Success
Jul 18 21:24:38.313: RADIUS_RADSEC_SET_LOCAL_SOCK: Success
Jul 18 21:24:38.313: RADIUS_RADSEC_SOCK_SET: Success
Jul 18 21:24:38.314: RADIUS_RADSEC_BIND_SOCKET: Success
Jul 18 21:24:38.314: RADIUS_RADSEC_CONN_SET_LPORT: Success
Jul 18 21:24:38.314: RADIUS_RADSEC_CONN_SET_SERVER_PORT: Success
Jul 18 21:24:38.314: RADIUS_RADSEC_CLIENT_HS_START: local port = 54509
Jul 18 21:24:38.314: RADIUS_RADSEC_SOCKET_CONNECT: Success
Jul 18 21:24:38.315: RADIUS_RADSEC_UPDATE_SVR_REF_CNT: Got radsec_data
Jul 18 21:24:38.315: RADIUS_RADSEC_UPDATE_SVR_REF_CNT: Got valid rctx, with server_handle B0000019
Jul 18 21:24:38.316: RADIUS_RADSEC_CLIENT_HS_START: TLS handshake in progress...(172.16.18.123/2083)
Jul 18 21:24:38.316: RADIUS_RADSEC_START_CONN_TIMER: Started (172.16.18.123/2083) for 5 secs
Jul 18 21:24:38.316: RADIUS_RADSEC_CONN_STATE_UPDATE: Success - State = 2
Jul 18 21:24:38.318: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 18 21:24:38.318: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 18 21:24:38.318: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 18 21:24:38.318: RADIUS_RADSEC_HASH_KEY_MATCH: hashkey1(0) matches hashkey2(0) TRUE
Jul 18 21:24:38.318: RADIUS_RADSEC_HASH_KEY_GET_CTX: radius radsec sock_ctx(0x7522CE91BAC0:0) get for key sock_no(0) succeeded
Jul 18 21:24:38.318: RADIUS_RADSEC_PROCESS_SOCK_EVENT: Handle socket event for TLS handshake(172.16.18.123/2083)
Jul 18 21:24:38.318: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 18 21:24:38.318: RADIUS_RADSEC_START_CONN_TIMER: Started (172.16.18.123/2083) for 5 secs
Jul 18 21:24:38.318: RADIUS_RADSEC_HS_CONTINUE: TLS handshake in progress...(172.16.18.123/2083)
Jul 18 21:24:38.318: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Success
Jul 18 21:24:38.318: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 18 21:24:38.327: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 18 21:24:38.327: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 18 21:24:38.327: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 18 21:24:38.327: RADIUS_RADSEC_HASH_KEY_MATCH: hashkey1(0) matches hashkey2(0) TRUE
Jul 18 21:24:38.327: RADIUS_RADSEC_HASH_KEY_GET_CTX: radius radsec sock_ctx(0x7522CE91BAC0:0) get for key sock_no(0) succeeded
Jul 18 21:24:38.327: RADIUS_RADSEC_PROCESS_SOCK_EVENT: Handle socket event for TLS handshake(172.16.18.123/2083)
Jul 18 21:24:38.327: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 18 21:24:38.391: RADIUS_RADSEC_START_CONN_TIMER: Started (172.16.18.123/2083) for 5 secs
Jul 18 21:24:38.391: RADIUS_RADSEC_HS_CONTINUE: TLS handshake in progress...(172.16.18.123/2083)
Jul 18 21:24:38.391: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Success
Jul 18 21:24:38.391: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 18 21:24:38.397: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 18 21:24:38.397: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 18 21:24:38.397: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 18 21:24:38.397: RADIUS_RADSEC_HASH_KEY_MATCH: hashkey1(0) matches hashkey2(0) TRUE
Jul 18 21:24:38.397: RADIUS_RADSEC_HASH_KEY_GET_CTX: radius radsec sock_ctx(0x7522CE91BAC0:0) get for key sock_no(0) succeeded
Jul 18 21:24:38.397: RADIUS_RADSEC_PROCESS_SOCK_EVENT: Handle socket event for TLS handshake(172.16.18.123/2083)
Jul 18 21:24:38.397: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 18 21:24:38.397: RADIUS_RADSEC_HS_CONTINUE: TLS handshake success!(172.16.18.123/2083) <-------- TLS tunnel establishes succesfully
Jul 18 21:24:38.397: RADIUS_RADSEC_CONN_STATE_UPDATE: Success - State = 3
Jul 18 21:24:38.397: RADIUS_RADSEC_UPDATE_SVR_REF_CNT: Got radsec_data
Jul 18 21:24:38.397: RADIUS_RADSEC_UPDATE_SVR_REF_CNT: Got valid rctx, with server_handle B0000019
Jul 18 21:24:38.397: RADIUS-RADSEC-HS-SUCCESS: Negotiated Cipher is ECDHE-RSA-AES256-GCM-SHA384
Jul 18 21:24:38.397: RADIUS_RADSEC_START_DATA_SEND: RADSEC HS Done, Start data send (172.16.18.123/2083)
Jul 18 21:24:38.397: RADIUS_RADSEC_UNQUEUE_WAIT_Q: Success Server(172.16.18.123)/Id(10)
Jul 18 21:24:38.397: RADIUS_RADSEC_MSG_SEND: RADSEC Write SUCCESS(id=10)
Jul 18 21:24:38.397: RADIUS(00000000): Started 5 sec timeout
Jul 18 21:24:38.397: RADIUS_RADSEC_UNQUEUE_WAIT_Q: Empty Server(172.16.18.123)/Id(-1)
Jul 18 21:24:38.397: RADIUS_RADSEC_START_DATA_SEND: no more data available
Jul 18 21:24:38.397: RADIUS_RADSEC_IDLE_TIMER: Started (172.16.18.123/2083)
Jul 18 21:24:38.397: RADIUS-RADSEC-HS-SUCCESS: Success
Jul 18 21:24:38.397: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Success
Jul 18 21:24:38.397: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 18 21:24:38.453: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 18 21:24:38.453: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 18 21:24:38.453: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 18 21:24:38.453: RADIUS_RADSEC_HASH_KEY_MATCH: hashkey1(0) matches hashkey2(0) TRUE
Jul 18 21:24:38.453: RADIUS_RADSEC_HASH_KEY_GET_CTX: radius radsec sock_ctx(0x7522CE91BAC0:0) get for key sock_no(0) succeeded
Jul 18 21:24:38.453: RADIUS_RADSEC_MSG_RECV: RADSEC Bytes read= 20, Err= 0
Jul 18 21:24:38.453: RADIUS_RADSEC_SOCK_READ_EVENT_HANDLE: Radius length is 113
Jul 18 21:24:38.453: RADIUS_RADSEC_SOCK_READ_EVENT_HANDLE: Going to read rest 93 bytes
Jul 18 21:24:38.453: RADIUS_RADSEC_MSG_RECV: RADSEC Bytes read= 93, Err= 0
Jul 18 21:24:38.453: RADIUS_RADSEC_SOCK_READ_EVENT_HANDLE: linktype = 7 - src port = 2083 - dest port = 54509 - udp len = 121 - datagram size = 141
Jul 18 21:24:38.453: RADIUS: Received from id 54509/10 172.16.18.123:2083, Access-Accept, len 113 <----------Radius response from ISE
RADIUS: authenticator 4E CE 96 63 41 4B 43 04 - C7 A2 B5 05 C2 78 A7 0D
Jul 18 21:24:38.453: RADIUS: User-Name [1] 10 "testuser"
Jul 18 21:24:38.453: RADIUS: Class [25] 83
RADIUS: 43 41 43 53 3A 61 63 31 30 31 32 37 62 64 38 74 [CACS:ac10127bd8t]
RADIUS: 47 58 50 47 4E 63 6C 57 76 2F 39 67 44 66 51 67 [GXPGNclWv/9gDfQg]
RADIUS: 63 4A 76 6C 35 47 72 33 71 71 47 36 4C 66 35 59 [cJvl5Gr3qqG6Lf5Y]
RADIUS: 52 42 2F 7A 57 55 39 59 3A 69 73 65 2D 76 62 65 [RB/zWU9Y:ise-vbe]
RADIUS: 74 61 6E 63 6F 2F 35 31 30 34 33 39 38 32 36 2F [tanco/510439826/]
RADIUS: 39 [ 9]
Jul 18 21:24:38.453: RADSEC: DTLS default secret
Jul 18 21:24:38.453: RADIUS/DECODE(00000000): There is no General DB. Reply server details may not be recorded
Jul 18 21:24:38.453: RADIUS(00000000): Received from id 54509/10WLC報告的未知CA
當WLC無法驗證ISE提供的證書時,它將無法建立DTLS隧道並且身份驗證失敗。
以下是出現以下情況時顯示的偵錯訊息範例:
9800#test aaa group Radsec testuser Cisco123 new-code
Jul 19 00:59:09.695: %PARSER-5-HIDDEN: Warning!!! ' test platform-aaa group server-group Radsec user-name testuser Cisco123 new-code blocked count delay level profile rate users ' is a hidden command. Use of this command is not recommended/supported and will be removed in future.
Jul 19 00:59:09.706: RADIUS/ENCODE(00000000):Orig. component type = Invalid
Jul 19 00:59:09.707: RADIUS/ENCODE(00000000): dropping service type, "radius-server attribute 6 on-for-login-auth" is off
Jul 19 00:59:09.707: RADIUS(00000000): Config NAS IP: 0.0.0.0
Jul 19 00:59:09.707: vrfid: [65535] ipv6 tableid : [0]
Jul 19 00:59:09.707: idb is NULL
Jul 19 00:59:09.707: RADIUS(00000000): Config NAS IPv6: ::
Jul 19 00:59:09.707: RADIUS(00000000): sending
Jul 19 00:59:09.707: RADIUS/DECODE(00000000): There is no General DB. Want server details may not be specified
Jul 19 00:59:09.707: RADSEC: DTLS default secret
Jul 19 00:59:09.707: RADIUS/ENCODE: Best Local IP-Address 172.16.5.11 for Radius-Server 172.16.18.123
Jul 19 00:59:09.707: RADSEC: DTLS default secret
Jul 19 00:59:09.707: RADIUS(00000000): Send Access-Request to 172.16.18.123:2083 id 52764/13, len 54
RADIUS: authenticator E8 09 1D B0 72 50 17 E6 - B4 27 F6 E3 18 25 16 64
Jul 19 00:59:09.707: RADIUS: User-Password [2] 18 *
Jul 19 00:59:09.707: RADIUS: User-Name [1] 10 "testuser"
Jul 19 00:59:09.707: RADIUS: NAS-IP-Address [4] 6 172.16.5.11
Jul 19 00:59:09.707: RADIUS_RADSEC_ENQ_WAIT_Q: Success Server(172.16.18.123)/Id(13)
Jul 19 00:59:09.707: RADIUS_RADSEC_CLIENT_PROCESS: Got DATA SEND MSG
Jul 19 00:59:09.707: RADIUS_RADSEC_SOCK_SET: 0 Success
Jul 19 00:59:09.707: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 19 00:59:09.707: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 19 00:59:09.707: RADIUS_RADSEC_HASH_KEY_ADD_CTX: add [radius_radsec ctx(0x7522CE91BAC0)] succeedd for sock_no(0)
Jul 19 00:59:09.707: RADIUS_RADSEC_GET_SOURCE_ADDR: Success
Jul 19 00:59:09.707: RADIUS_RADSEC_GET_SOCK_ADDR: Success
Jul 19 00:59:09.707: RADIUS_RADSEC_SET_LOCAL_SOCK: Success
Jul 19 00:59:09.707: RADIUS_RADSEC_SOCK_SET: Success
Jul 19 00:59:09.707: RADIUS_RADSEC_BIND_SOCKET: Success
Jul 19 00:59:09.707: RADIUS_RADSEC_CONN_SET_LPORT: Success
Jul 19 00:59:09.707: RADIUS_RADSEC_CONN_SET_SERVER_PORT: Success
Jul 19 00:59:09.707: RADIUS_RADSEC_CLIENT_HS_START: local port = 49556
Jul 19 00:59:09.707: RADIUS_RADSEC_SOCKET_CONNECT: Success
Jul 19 00:59:09.709: RADIUS_RADSEC_UPDATE_SVR_REF_CNT: Got radsec_data
Jul 19 00:59:09.709: RADIUS_RADSEC_UPDATE_SVR_REF_CNT: Got valid rctx, with server_handle B0000019
Jul 19 00:59:09.709: RADIUS_RADSEC_CLIENT_HS_START: TLS handshake in progress...(172.16.18.123/2083)
Jul 19 00:59:09.709: RADIUS_RADSEC_START_CONN_TIMER: Started (172.16.18.123/2083) for 5 secsUser rejected
uwu-9800#
Jul 19 00:59:09.709: RADIUS_RADSEC_CONN_STATE_UPDATE: Success - State = 2
Jul 19 00:59:09.711: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 19 00:59:09.711: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 19 00:59:09.711: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 19 00:59:09.711: RADIUS_RADSEC_HASH_KEY_MATCH: hashkey1(0) matches hashkey2(0) TRUE
Jul 19 00:59:09.711: RADIUS_RADSEC_HASH_KEY_GET_CTX: radius radsec sock_ctx(0x7522CE91BAC0:0) get for key sock_no(0) succeeded
Jul 19 00:59:09.711: RADIUS_RADSEC_PROCESS_SOCK_EVENT: Handle socket event for TLS handshake(172.16.18.123/2083)
Jul 19 00:59:09.711: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 19 00:59:09.711: RADIUS_RADSEC_START_CONN_TIMER: Started (172.16.18.123/2083) for 5 secs
Jul 19 00:59:09.711: RADIUS_RADSEC_HS_CONTINUE: TLS handshake in progress...(172.16.18.123/2083)
Jul 19 00:59:09.711: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Success
Jul 19 00:59:09.713: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 19 00:59:09.720: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 19 00:59:09.720: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 19 00:59:09.720: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 19 00:59:09.720: RADIUS_RADSEC_HASH_KEY_MATCH: hashkey1(0) matches hashkey2(0) TRUE
Jul 19 00:59:09.720: RADIUS_RADSEC_HASH_KEY_GET_CTX: radius radsec sock_ctx(0x7522CE91BAC0:0) get for key sock_no(0) succeeded
Jul 19 00:59:09.720: RADIUS_RADSEC_PROCESS_SOCK_EVENT: Handle socket event for TLS handshake(172.16.18.123/2083)
Jul 19 00:59:09.720: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 19 00:59:09.722: RADIUS_RADSEC_HS_CONTINUE: TLS handshake failed!
Jul 19 00:59:09.722: RADIUS_RADSEC_UNQUEUE_WAIT_Q: Success Server(172.16.18.123)/Id(13)
Jul 19 00:59:09.722: RADIUS_RADSEC_FAILOVER_HANDLER:Failng-over to new server = 0x0
Jul 19 00:59:09.722: RADIUS_RADSEC_UNQUEUE_WAIT_Q: Empty Server(172.16.18.123)/Id(-1)
Jul 19 00:59:09.722: RADIUS_RADSEC_FAILOVER_HANDLER: no more data available
Jul 19 00:59:09.722: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 19 00:59:09.722: RADIUS_RADSEC_CONN_CLOSE: Cleaned up timers for Radius RADSEC ctx
Jul 19 00:59:09.722: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 19 00:59:09.722: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 19 00:59:09.722: RADIUS_RADSEC_HASH_KEY_DEL_CTX: remove [radius_radsec ctx(0x7522CE91BAC0)] succeeded for sock_no(0)
Jul 19 00:59:09.722: RADIUS_RADSEC_CONN_CLOSE: Hash table entry removed for RADSEC sock ctx
Jul 19 00:59:09.723: RADIUS_RADSEC_CONN_CLOSE: Success
Jul 19 00:59:09.723: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Failed to complete TLS handshake <----------DTLS tunnel failed to negociate
Jul 19 00:59:09.723: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 19 00:59:09.723: RADIUS_RADSEC_CONN_CLOSE: Cleaned up timers for Radius RADSEC ctx
Jul 19 00:59:09.723: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(-1) generated for sock(-1)
Jul 19 00:59:09.723: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(-1) generated for sock(-1)
uwu-9800#
Jul 19 00:59:09.723: RADIUS_RADSEC_HASH_KEY_DEL_CTX: remove [radius_radsec ctx(0x7522CE91BAC0)] succeeded for sock_no(-1)
Jul 19 00:59:09.723: RADIUS_RADSEC_CONN_CLOSE: Hash table entry removed for RADSEC sock ctx
Jul 19 00:59:09.723: RADIUS_RADSEC_CONN_CLOSE: Success
Jul 19 00:59:09.723: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Error
Jul 19 00:59:09.723: RADIUS_RADSEC_PROCESS_SOCK_EVENT: failed to hanlde radsec hs event
Jul 19 00:59:09.723: RADIUS/DECODE: No response from radius-server; parse response; FAIL
Jul 19 00:59:09.723: RADIUS/DECODE: Case error(no response/ bad packet/ op decode);parse response; FAIL
Jul 19 00:59:09.723: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event
Jul 19 00:59:10.718: %RADSEC_AUDIT_MESSAGE-3-FIPS_AUDIT_FCS_RADSEC_SERVER_CERTIFICATE_VALIDATION_FAILURE: Chassis 1 R0/0: sessmgrd: RADSEC server certificate validation failed with server 172.16.18.123
Jul 19 00:59:10.718: %RADSEC_AUDIT_MESSAGE-3-FIPS_AUDIT_FCS_RADSEC_SERVER_IDENTITY_CHECK_FAILURE: Chassis 1 R0/0: sessmgrd: RADSEC server identity check failed with server 172.16.18.123 <-----WLC fails to validate the identity on the certificate
Jul 19 00:59:10.718: %RADSEC_AUDIT_MESSAGE-6-FIPS_AUDIT_FCS_DTLSC_DTLS_SESSION_CLOSED: Chassis 1 R0/0: sessmgrd: RADSEC DTLS connection closed with peer 172.16.18.123若要更正此問題,請確保WLC上配置的標識與ISE證書中包含的其中一個SAN完全匹配:
9800(config)#radius server
9800(config)#dtls match-server-identity hostname 請確保已在控制器上正確匯入CA證書鏈,並確保 dtls trustpoint server
ISE報告的未知CA
當ISE無法驗證WLC提供的證書時,它將無法建立DTLS隧道並且身份驗證失敗。這在RADIUS即時日誌中顯示為錯誤。導覽至操作>Radius>Live logs以驗證。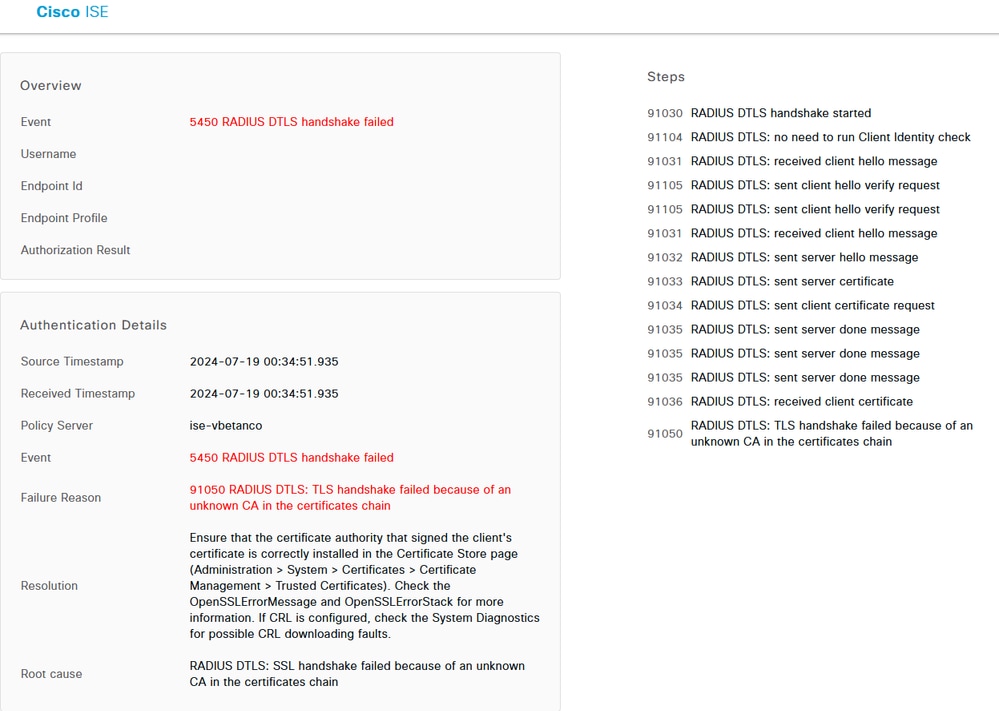 ISE即時日誌報告DTLS握手由於未知CA而失敗
ISE即時日誌報告DTLS握手由於未知CA而失敗
要更正此問題,請確保中間證書和根證書,選中管理>系統>證書>受信任證書下的信任客戶端身份驗證和系統日誌覈取方塊。
已進行吊銷檢查
將憑證匯入到WLC時,新建立的信任點已啟用撤銷檢查。這會使WLC嘗試搜尋無法使用或連線的憑證撤銷清單,且憑證驗證失敗。
確保證書的驗證路徑中的每個信任點都包含命revocation-check none令。
Jul 17 21:50:39.064: RADIUS_RADSEC_HASH_KEY_MATCH: hashkey1(0) matches hashkey2(0) TRUE
Jul 17 21:50:39.064: RADIUS_RADSEC_HASH_KEY_GET_CTX: radius radsec sock_ctx(0x780FB0715978:0) get for key sock_no(0) succeeded
Jul 17 21:50:39.064: RADIUS_RADSEC_PROCESS_SOCK_EVENT: Handle socket event for TLS handshake(172.16.18.123/2083)
Jul 17 21:50:39.064: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 17 21:50:39.068: %PKI-3-CRL_FETCH_FAIL: CRL fetch for trustpoint WLC1.pfx failed
Reason : Enrollment URL not configured. <------ WLC tries to perform revocation check
Jul 17 21:50:39.070: RADIUS_RADSEC_HS_CONTINUE: TLS handshake failed!
Jul 17 21:50:39.070: RADIUS_RADSEC_UNQUEUE_WAIT_Q: Success Server(172.16.18.123)/Id(2)
Jul 17 21:50:39.070: RADIUS_RADSEC_FAILOVER_HANDLER:Failng-over to new server = 0x0
Jul 17 21:50:39.070: RADIUS_RADSEC_UNQUEUE_WAIT_Q: Empty Server(172.16.18.123)/Id(-1)
Jul 17 21:50:39.070: RADIUS_RADSEC_FAILOVER_HANDLER: no more data available
Jul 17 21:50:39.070: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 17 21:50:39.070: RADIUS_RADSEC_CONN_CLOSE: Cleaned up timers for Radius RADSEC ctx
Jul 17 21:50:39.070: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(0) generated for sock(0)
Jul 17 21:50:39.070: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(0) generated for sock(0)
Jul 17 21:50:39.070: RADIUS_RADSEC_HASH_KEY_DEL_CTX: remove [radius_radsec ctx(0x780FB0715978)] succeeded for sock_no(0)
Jul 17 21:50:39.070: RADIUS_RADSEC_CONN_CLOSE: Hash table entry removed for RADSEC sock ctx
Jul 17 21:50:39.070: RADIUS_RADSEC_CONN_CLOSE: Success
Jul 17 21:50:39.070: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Failed to complete TLS handshake
Jul 17 21:50:39.070: RADIUS_RADSEC_STOP_TIMER: Stopped (172.16.18.123/2083)
Jul 17 21:50:39.070: RADIUS_RADSEC_CONN_CLOSE: Cleaned up timers for Radius RADSEC ctx
Jul 17 21:50:39.070: RADIUS_RADSEC_GENERATE_HASHKEY: hash key(-1) generated for sock(-1)
Jul 17 21:50:39.070: RADIUS_RADSEC_GENERATE_HASHBUCKET: hash bucket(-1) generated for sock(-1)
Jul 17 21:50:39.070: RADIUS_RADSEC_HASH_KEY_DEL_CTX: remove [radius_radsec ctx(0x780FB0715978)] succeeded for sock_no(-1)
Jul 17 21:50:39.070: RADIUS_RADSEC_CONN_CLOSE: Hash table entry removed for RADSEC sock ctx
Jul 17 21:50:39.070: RADIUS_RADSEC_CONN_CLOSE: Success
Jul 17 21:50:39.070: RADIUS_RADSEC_SOCK_TLS_EVENT_HANDLE: Error
Jul 17 21:50:39.070: RADIUS_RADSEC_PROCESS_SOCK_EVENT: failed to hanlde radsec hs event
Jul 17 21:50:39.070: RADIUS_RADSEC_CLIENT_PROCESS: Got Socket Event對資料包捕獲上的DTLS隧道建立進行故障排除
9800 WLC提供嵌入式封包擷取(EPC)功能,允許您擷取指定介面的所有已傳送和已接收流量。ISE提供稱為TCP轉儲的類似功能來監控傳入和傳出流量。 當同時使用時,它們允許您從兩台裝置的角度分析DTLS會話建立流量。
有關在ISE上配置TCP轉儲的詳細步驟,請參閱思科身份服務引擎管理員指南。另請參閱疑難排解Catalyst 9800無線LAN控制器,瞭解在WLC上設定EPC功能的資訊。
以下是成功建立DTLS通道的範例。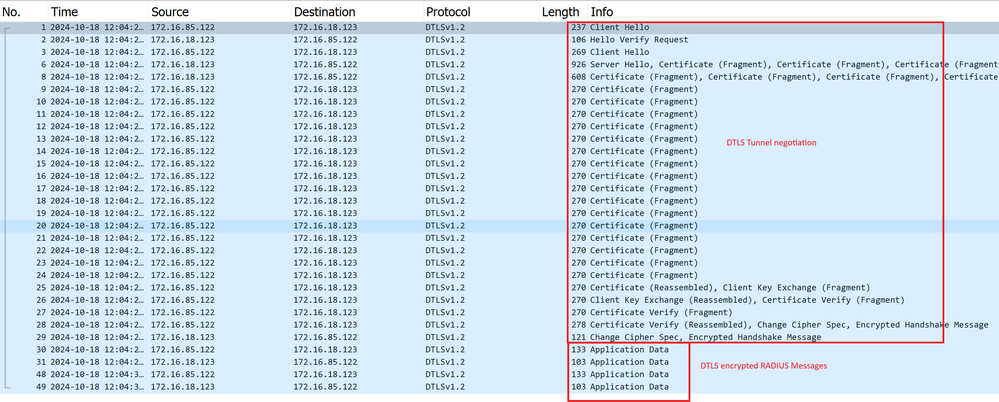 RADIUS DTLS通道交涉和加密訊息的封包擷取
RADIUS DTLS通道交涉和加密訊息的封包擷取
資料包捕獲顯示DTLS隧道建立過程。如果裝置之間或DTLS加密的警報資料包之間的通訊丟失存在協商問題,則資料包捕獲將幫助您識別問題。
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
2.0 |
10-Sep-2025
|
初始版本 |
1.0 |
24-Oct-2024
|
初始版本 |
由思科工程師貢獻
- Mario MedinaTechnical Consulting Engineer
- Sri Pavan GurajalaTechnical Consulting Engineer
 意見
意見