設定在無線LAN控制器中驗證有線訪客及對其進行疑難排解
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
目錄
簡介
本檔案介紹如何在9800和IRCM中使用外部Web驗證來設定、驗證和疑難排解有線訪客存取。
必要條件
需求
思科建議您瞭解以下主題:
9800 WLC
AireOS WLC
行動通道
ISE
假設在設定有線訪客存取之前,兩個WLC之間已建立行動通道。
此方面超出此組態範例的範圍。有關詳細說明,請參閱標題為「Configuring Mobility Topologies on 9800」的附加文檔
採用元件
9800 WLC版本17.12.1
5520 WLC版本8.10.185.0
ISE版本3.1.0.518
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
在錨定到另一個catalyst 9800的catalyst 9800上配置有線訪客
網路圖表
 網路拓撲
網路拓撲
外部9800 WLC上的組態
配置Web引數對映
步驟1:導覽至Configuration > Security > Web Auth,選擇Global,驗證控制器的虛擬IP位址和信任點對應,並確保型別設定為webauth。
 全域性引數對映
全域性引數對映

附註:Web Auth intercept HTTPs是選用設定。如果需要HTTPS重新導向,必須啟用Web Auth intercept HTTPS選項。但是,不建議使用此配置,因為它會增加CPU使用率。
第2步:在Advanced索引標籤下,為使用者端重新導向設定外部網頁URL。設定「Redirect URL for Login」和「Redirect On-Failure」;「Redirect On-Success」是可選的。設定完成後,重新導向URL的預覽會顯示在Web驗證設定檔上。
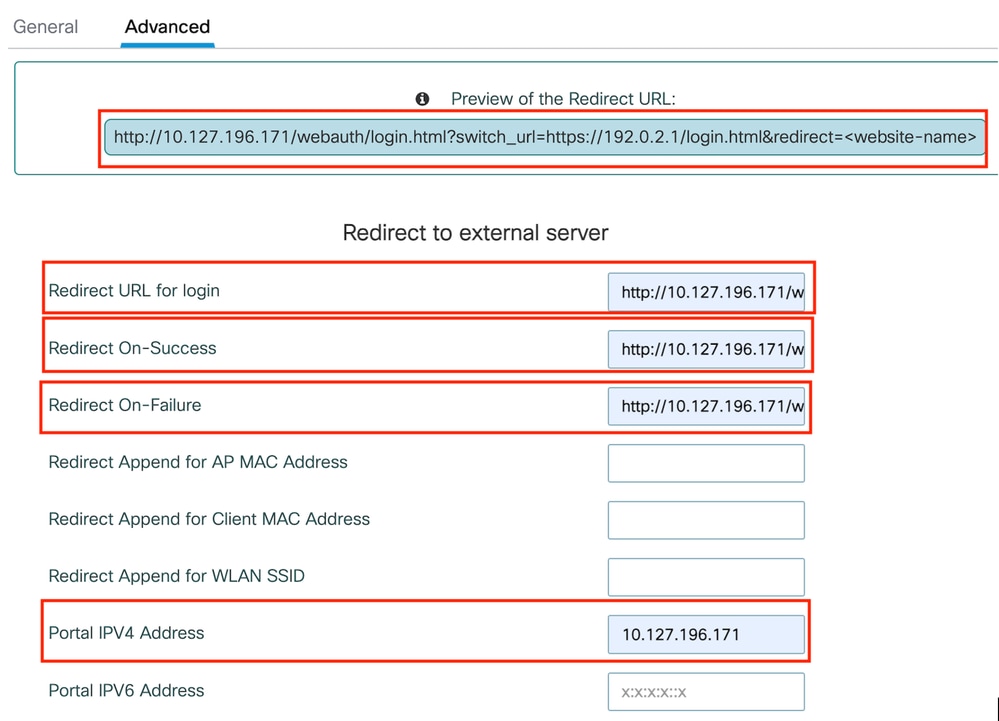 高級頁籤
高級頁籤
CLI組態
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
intercept-https-enable
trustpoint TP-self-signed-3915430211
webauth-http-enable
附註:在此場景中,使用全域性引數對映。根據要求,通過選擇Add和,配置自定義Web引數對映,在Advanced頁籤下設定重定向URL。信任點和虛擬IP設定從全域性配置檔案繼承。
AAA設定:
第1步:建立Radius伺服器:
導航到Configuration > Security > AAA,按一下Server/Group部分下的「Add」,然後在「Create AAA Radius Server」頁面上輸入伺服器名稱、IP地址和共用金鑰。
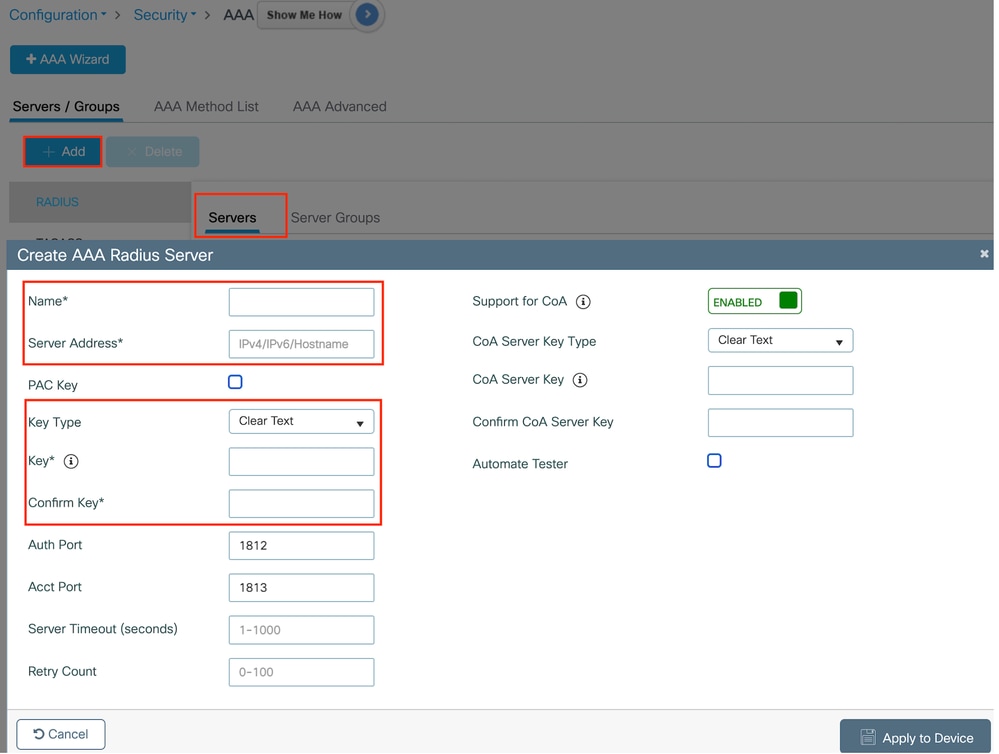 Radius伺服器配置
Radius伺服器配置
CLI組態
radius server ISE-Auth
address ipv4 10.197.224.122 auth-port 1812 acct-port 1813
key *****
server name ISE-Auth
步驟 2:建立RADIUS伺服器組:
選擇「伺服器組」部分下的「新增」以定義伺服器組,並切換要包括在組配置中的伺服器。
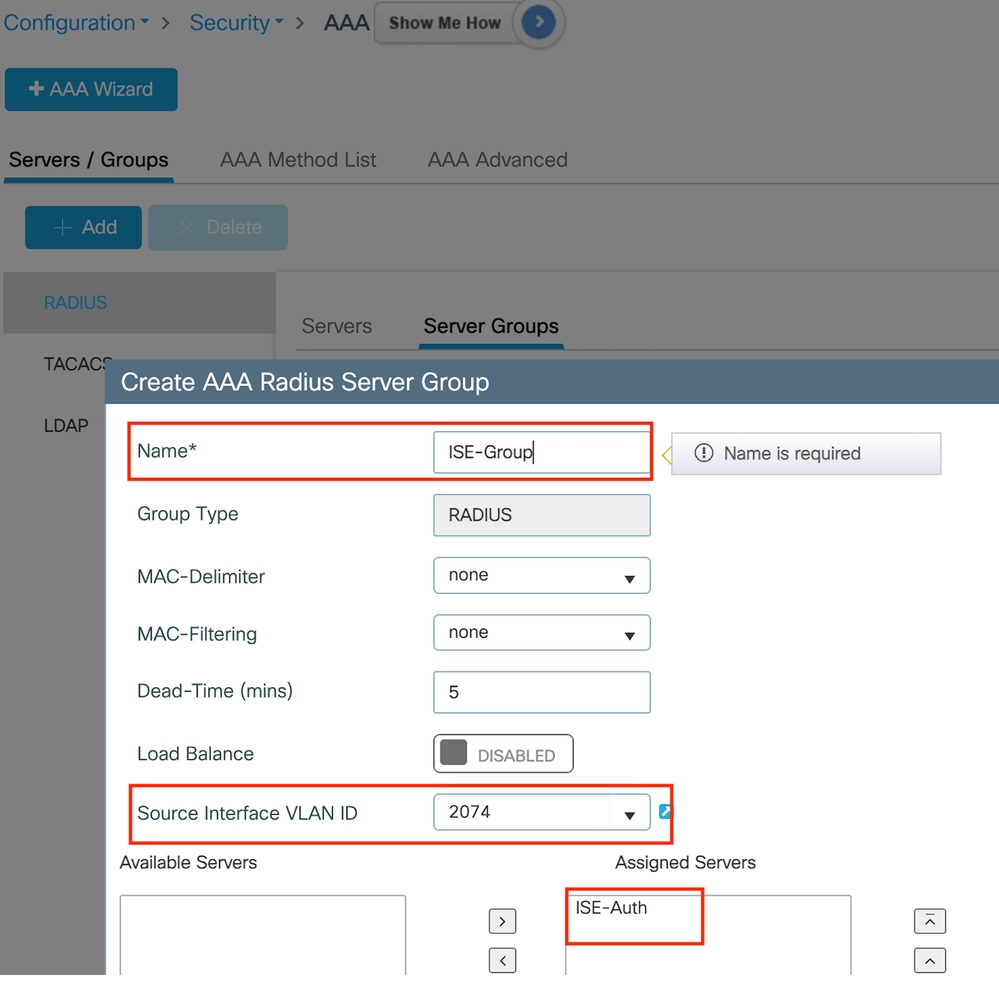 Radius伺服器組
Radius伺服器組
CLI組態
aaa group server radius ISE-Group
server name ISE-Auth
ip radius source-interface Vlan2074
deadtime 5
第3步:配置AAA方法清單:
導航到AAA Method List頁籤,在Authentication下選擇Add,將Type定義為「login」和Group type定義為「Group」的方法清單名稱,並在Assigned Server Group部分下對映已配置的身份驗證伺服器組。
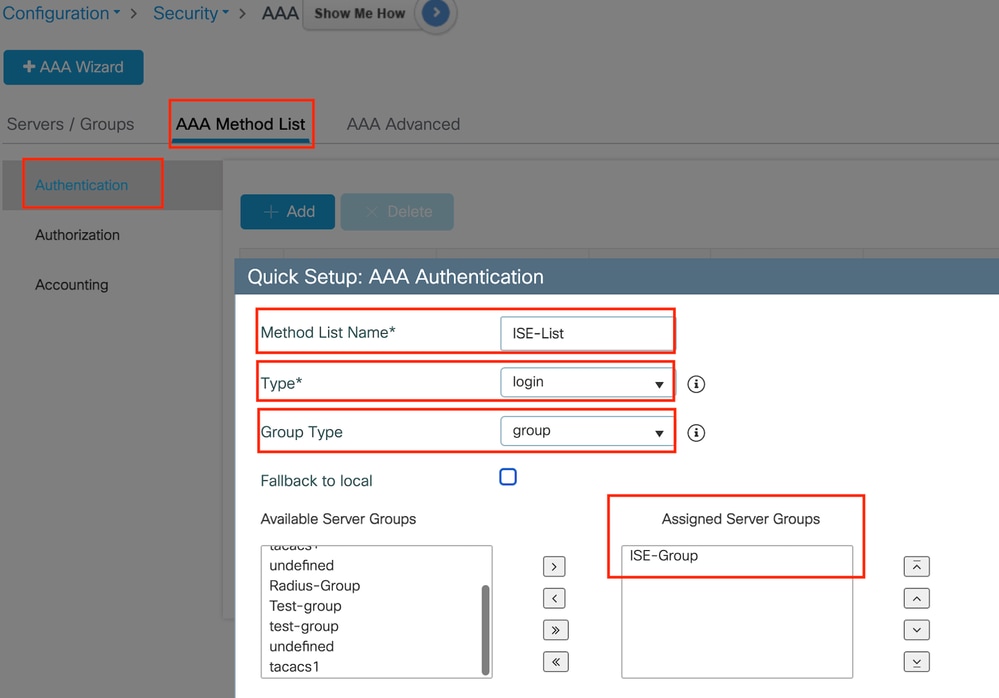 身份驗證方法清單
身份驗證方法清單
CLI配置
aaa authentication login ISE-List group ISE-Group
配置策略配置檔案
第1步: 導航到Configuration > Tags & Profiles > Policy,在General頁籤中命名新配置檔案,並使用狀態切換啟用它。
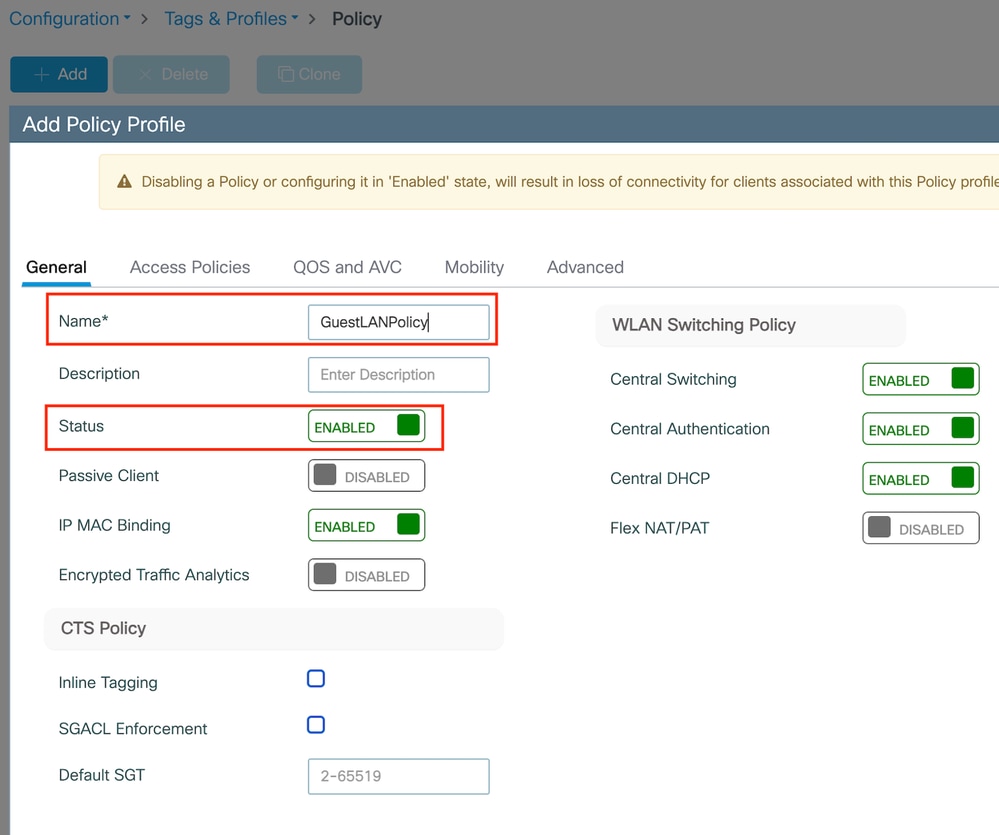 策略配置檔案
策略配置檔案
步驟2:在Access Policies頁籤下,在錨點控制器上完成VLAN對映時分配隨機VLAN。在此範例中,vlan 1已設定
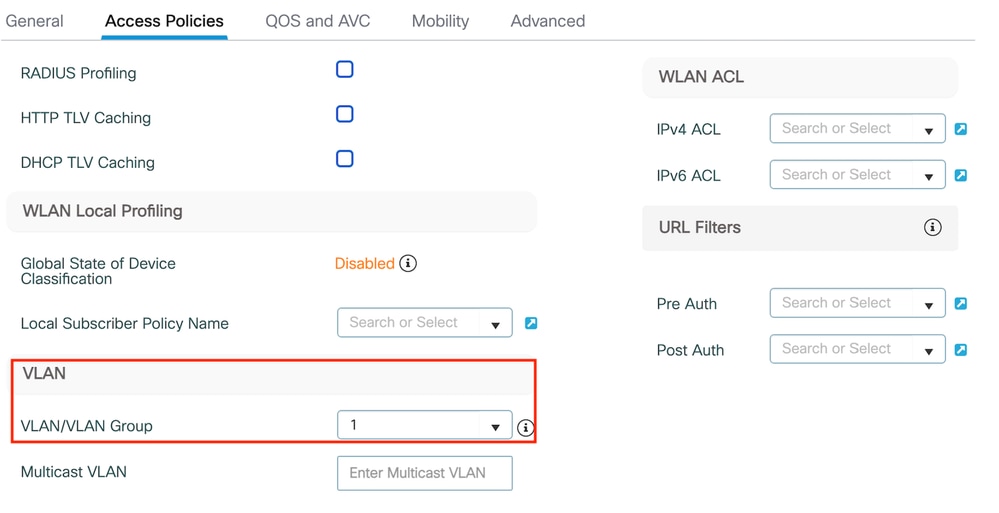 Access Policy頁籤
Access Policy頁籤
第3步:在Mobility頁籤下,將錨點控制器切換為Primary(1),並根據冗餘要求配置二級和三級移動隧道(可選)
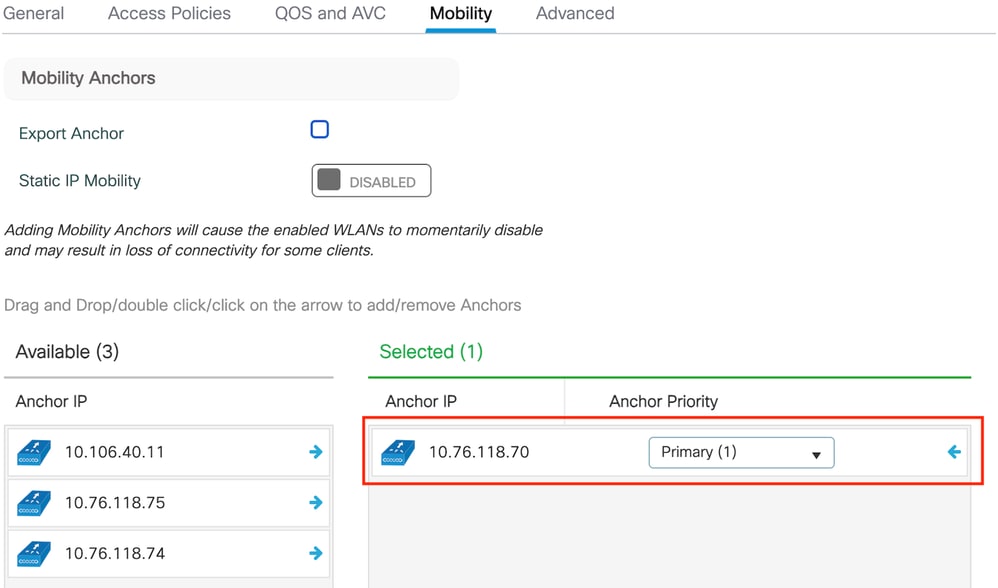 移動圖
移動圖
CLI組態
wireless profile policy GuestLANPolicy
mobility anchor 10.76.118.70 priority 1
no shutdown
設定訪客LAN設定檔
第1步:導覽至Configuration > Wireless > Guest LAN,選擇Add,設定唯一的設定檔名稱,啟用有線VLAN,輸入有線訪客使用者的VLAN ID,並將設定檔狀態切換為Enabled。
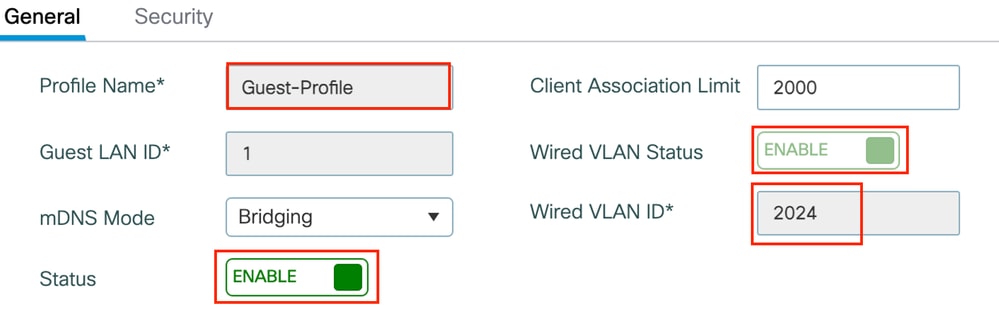 訪客LAN配置檔案
訪客LAN配置檔案
第2步:在「Security」頁籤下,啟用Web Auth,對映Web Auth引數對映,然後從「Authentication」下拉選單中選擇Radius伺服器。
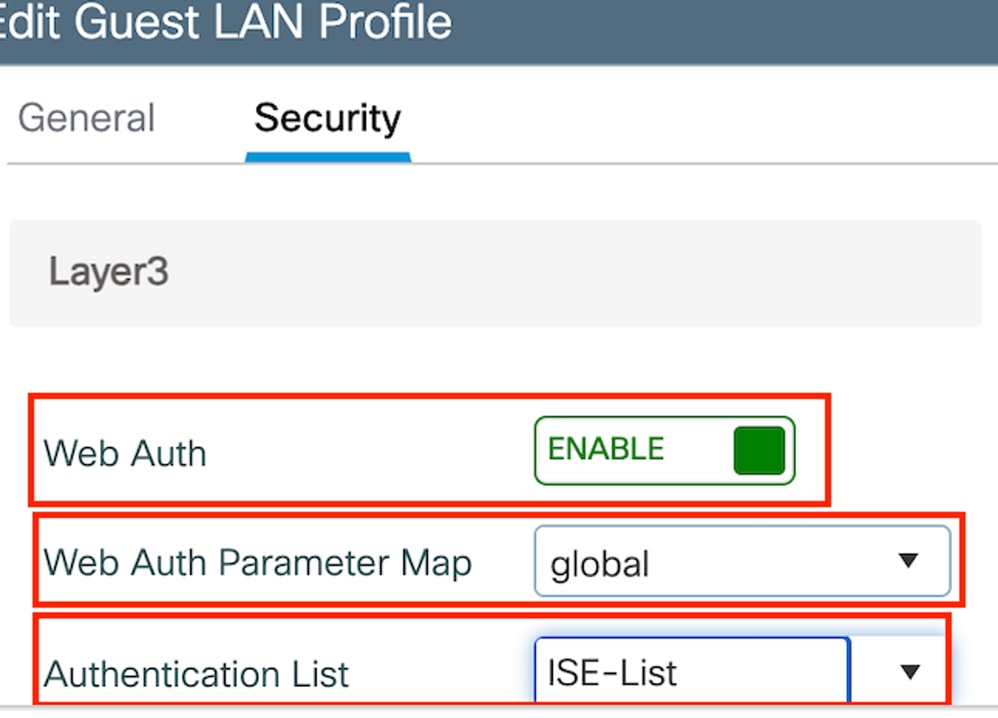 Guest LAN Security頁籤
Guest LAN Security頁籤CLI組態
guest-lan profile-name Guest-Profile 1 wired-vlan 2024
security web-auth authentication-list ISE-List
security web-auth parameter-map global訪客LAN對映
導覽至Configuration > Wireless > Guest LAN。
在Guest LAN MAP configuration部分下,選擇Add並對映Policy profile和Guest LAN profile
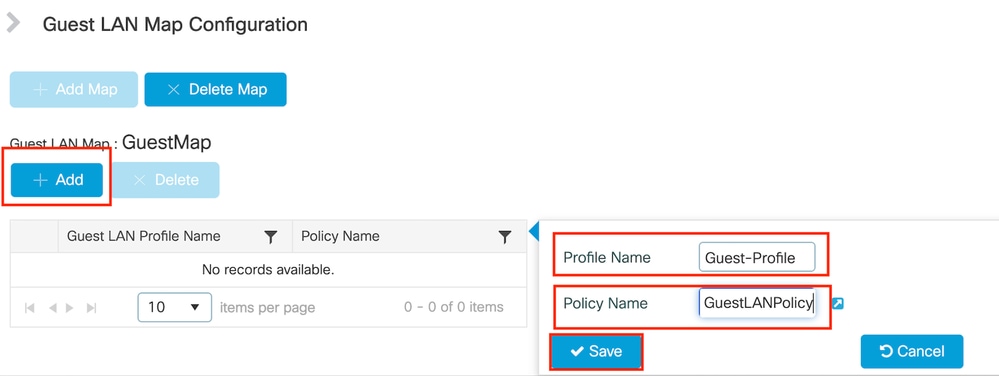 訪客LAN對映
訪客LAN對映
CLI組態
wireless guest-lan map GuestMap
guest-lan Guest-Profile policy GuestLANPolicy
錨點9800 WLC上的組態
配置Web引數對映
步驟1:導覽至Configuration > Security > Web Auth,選擇Global,驗證控制器的虛擬IP位址和信任點對應,並確保型別設定為webauth。
 全域性引數對映
全域性引數對映
第2步:在Advanced索引標籤下,為使用者端重新導向設定外部網頁URL。設定「Redirect URL for Login」和「Redirect On-Failure」;「Redirect On-Success」是可選的。
設定完成後,重新導向URL的預覽會顯示在Web驗證設定檔上。
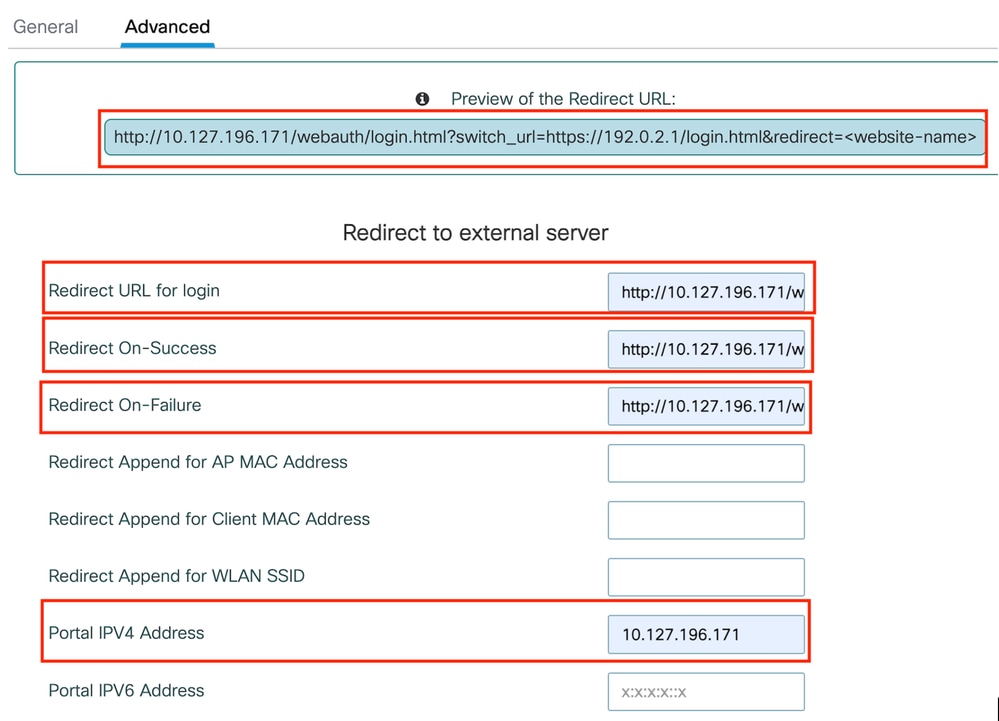 高級頁籤
高級頁籤
CLI組態
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
intercept-https-enable.
trustpoint TP-self-signed-3915430211
webauth-http-enable
AAA設定:
第1步:建立Radius伺服器:
導航到Configuration > Security > AAA,在Server/Group部分下按一下Add,然後在「Create AAA Radius Server」頁面上輸入伺服器名稱、IP地址和共用金鑰。
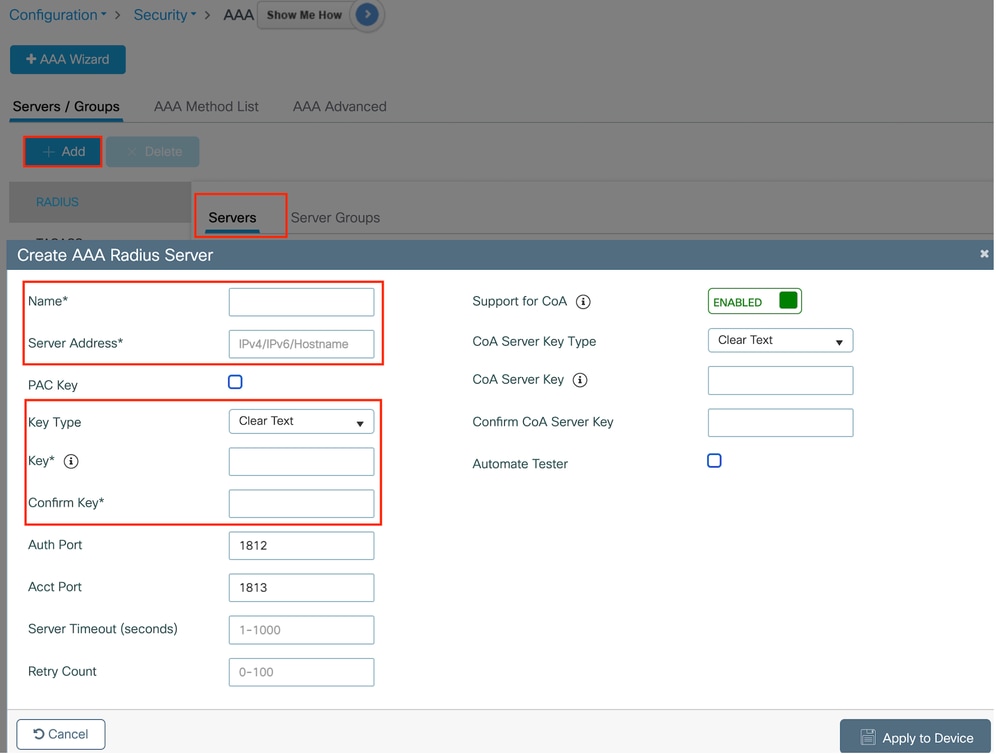 Radius伺服器配置
Radius伺服器配置
CLI組態
radius server ISE-Auth
address ipv4 10.197.224.122 auth-port 1812 acct-port 1813
key *****
server name ISE-Auth
步驟 2:建立RADIUS伺服器組:
在Server Groups部分下選擇Add以定義伺服器組,並切換要包括在組配置中的伺服器。
 錨點radius組
錨點radius組
CLI組態
aaa group server radius ISE-Group
server name ISE-Auth
ip radius source-interface Vlan2081
deadtime 5
第3步:配置AAA方法清單:
導航到AAA Method List頁籤,在Authentication下選擇Add,定義方法清單名稱,將Type定義為「login」,Group type定義為「Group」,並在Assigned Server Group部分下對映配置的身份驗證伺服器組。
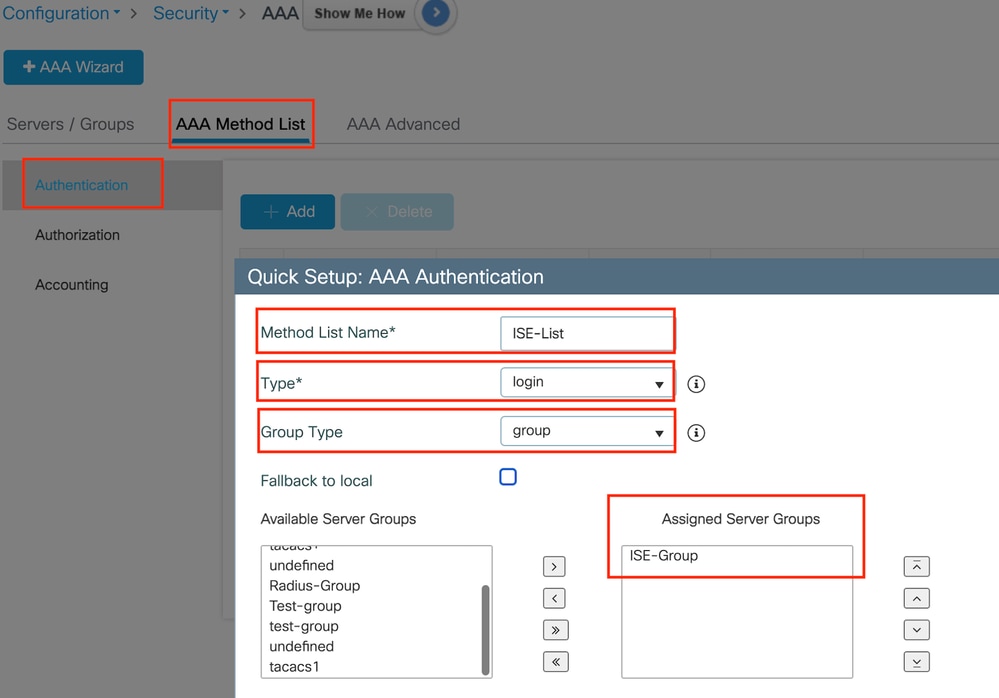 身份驗證方法清單
身份驗證方法清單
CLI配置
aaa authentication login ISE-List group ISE-Group配置策略配置檔案
第1步:導覽至Configuration > Tag & Profiles > Policy,使用與外部控制器上相同的名稱配置策略配置檔案並啟用該配置檔案。
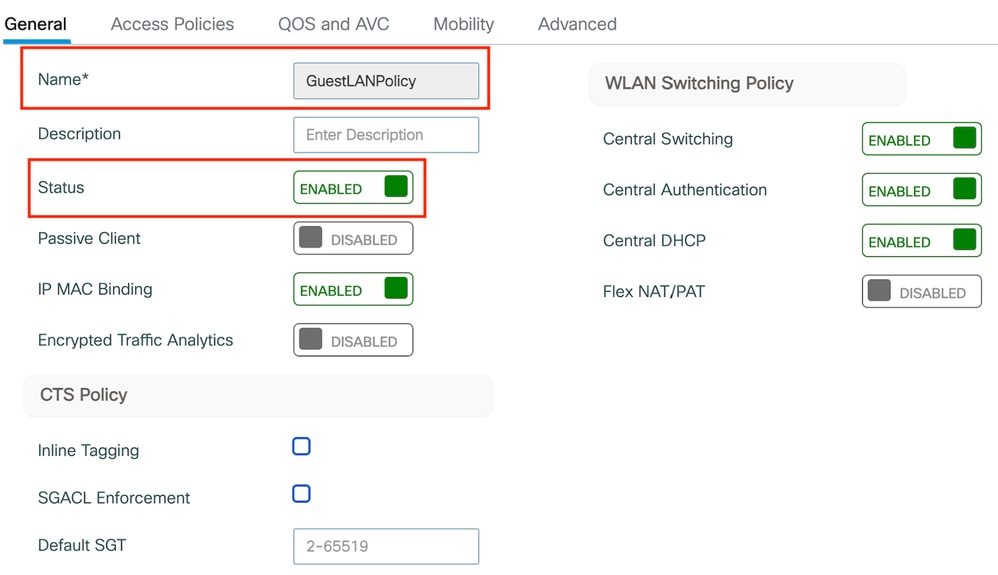 錨點策略配置檔案
錨點策略配置檔案
第2步:在Access Policies下,從下拉選單中對映有線客戶端vlan
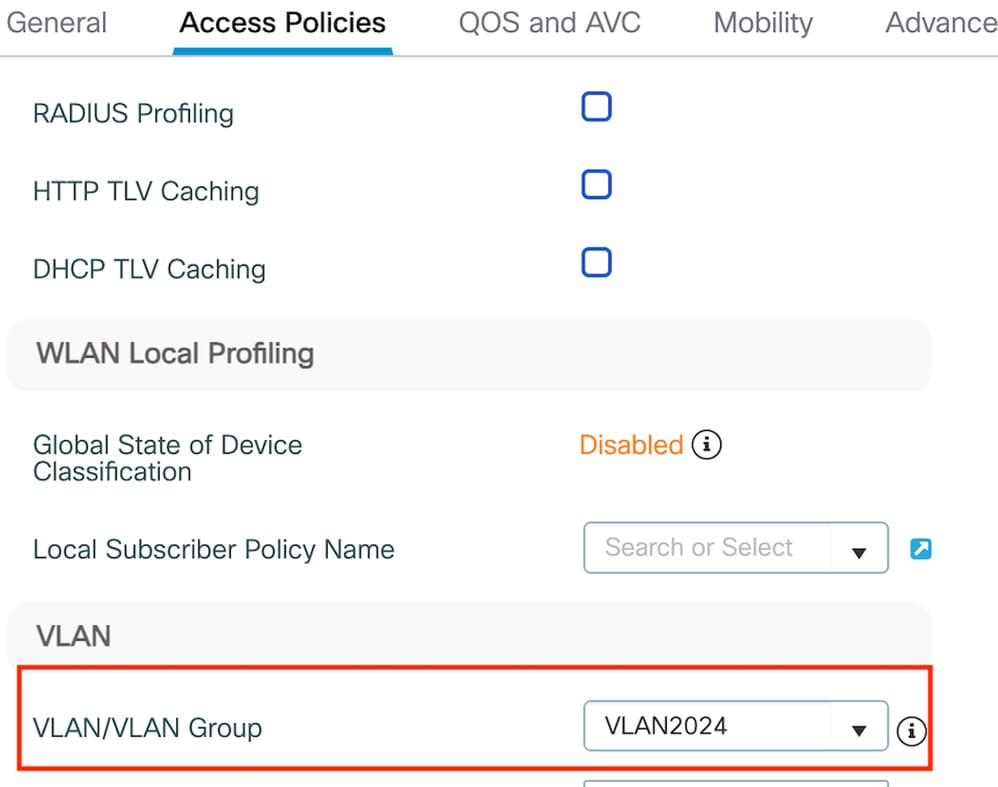 訪問策略頁籤
訪問策略頁籤

附註:除了VLAN外,策略配置檔案的配置必須在外部控制器和錨點控制器上匹配。
第3步:在Mobility頁籤下,選中Export Anchor覈取方塊。
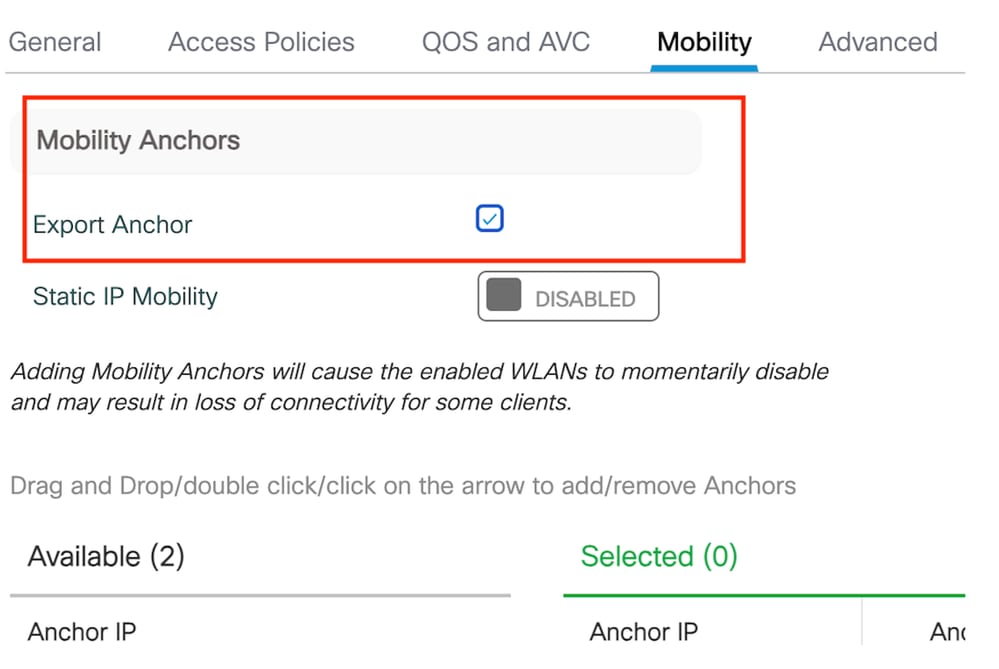 匯出錨點
匯出錨點

附註:此組態會指定9800無線LAN控制器(WLC)為與指定原則設定檔相關聯的任何WLAN的錨點WLC。外部9800 WLC將使用者端重新導向到錨點WLC時,會提供指派給使用者端的無線區域網和原則設定檔的詳細資訊。這樣錨點WLC就可以根據收到的資訊應用適當的本地策略配置檔案。
CLI組態
wireless profile policy GuestLANPolicy
mobility anchor
vlan VLAN2024
no shutdown
設定訪客LAN設定檔
第1步:導航到Configuration > Wireless > Guest LAN,然後選擇Add以建立和配置Guest LAN配置檔案。確保配置檔名稱與外部控制器的配置檔名稱相匹配。請注意,錨點控制器上必須停用有線VLAN。
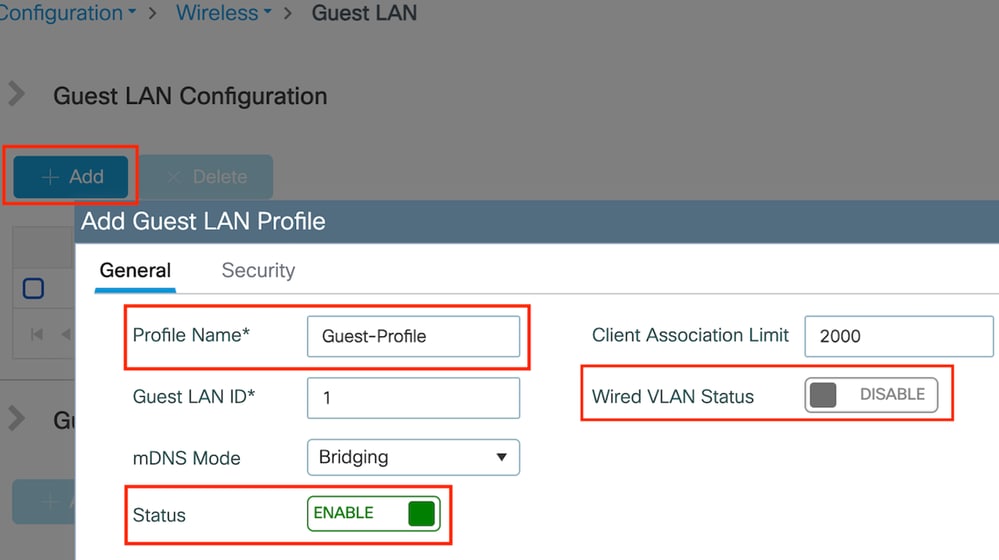 訪客LAN配置檔案
訪客LAN配置檔案
第2步:在安全設定中,啟用Web Auth,然後配置Web Auth引數對映和身份驗證清單。
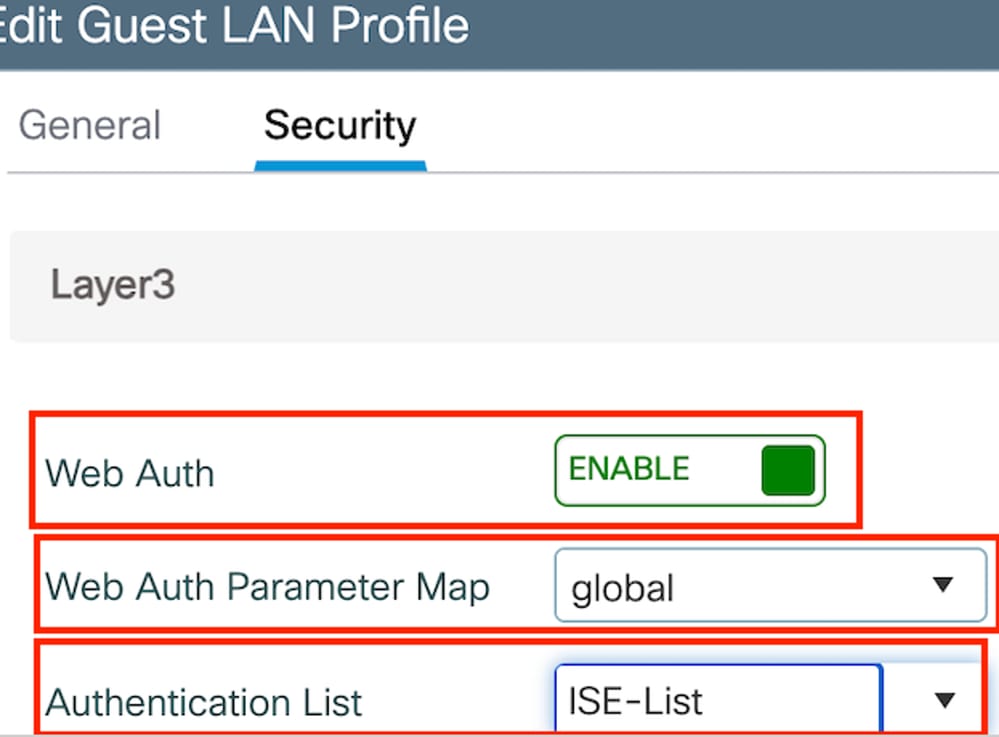

附註:除了有線VLAN狀態,外部控制器和錨點控制器之間的訪客LAN配置檔案配置必須相同
CLI組態
guest-lan profile-name Guest-Profile 1
security web-auth authentication-list ISE-List
security web-auth parameter-map global
訪客LAN對映
第1步:導覽至Configuration > Wireless > Guest LAN。在Guest LAN MAP configuration部分,選擇Add並將Policy Profile對映到Guest LAN profile。
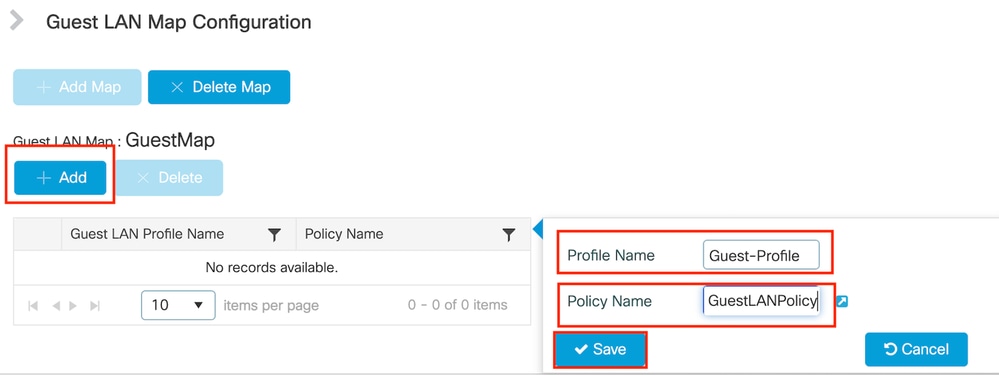 訪客LAN對映
訪客LAN對映
wireless guest-lan map GuestMap
guest-lan Guest-Profile policy GuestLANPolicy
在錨定到AireOS 5520控制器的Catalyst 9800上配置有線訪客
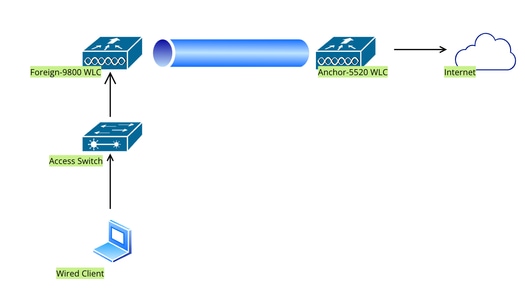 網路拓撲
網路拓撲
外部9800 WLC上的組態
配置Web引數對映
步驟1:導航至Configuration > Security > Web Auth,然後選擇Global。確認在型別設定為webauth的情況下,控制器和信任點的虛擬IP位址是否已正確對映到設定檔上。
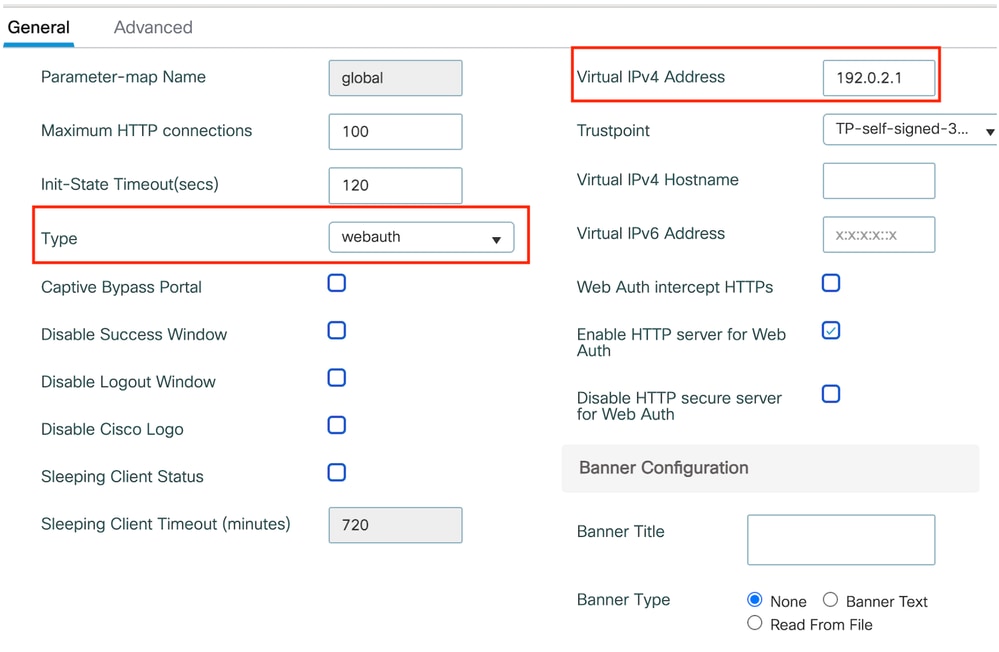 Web引數對映
Web引數對映
第2步:在Advanced頁籤下,指定客戶端必須重定向到的外部網頁URL。配置Redirect URL for Login和Redirect On-Failure。Redirect On-Success設定是可選配置。
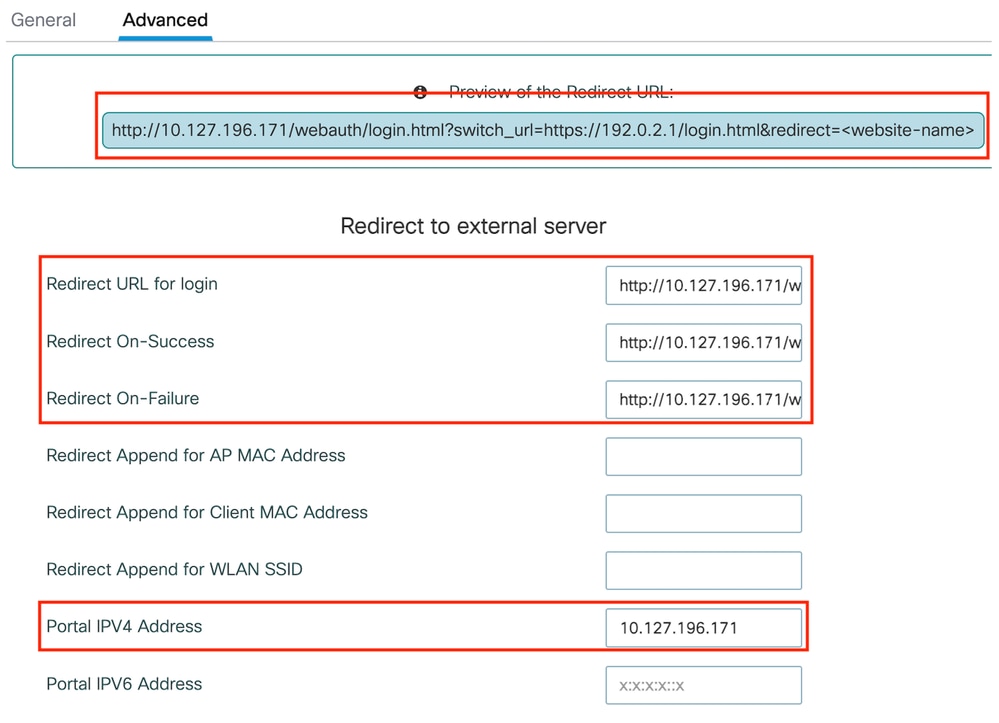 高級頁籤
高級頁籤
CLI配置
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
trustpoint TP-self-signed-3010594951
webauth-http-enable

附註:有關AAA配置,請參閱「」部分中提供的外部9800 WLC的配置詳細資訊。
配置策略配置檔案
第1步:導航到Configuration > Tags & Profiles > Policy。選擇Add,然後在General頁籤中為配置檔案提供名稱並啟用狀態切換。
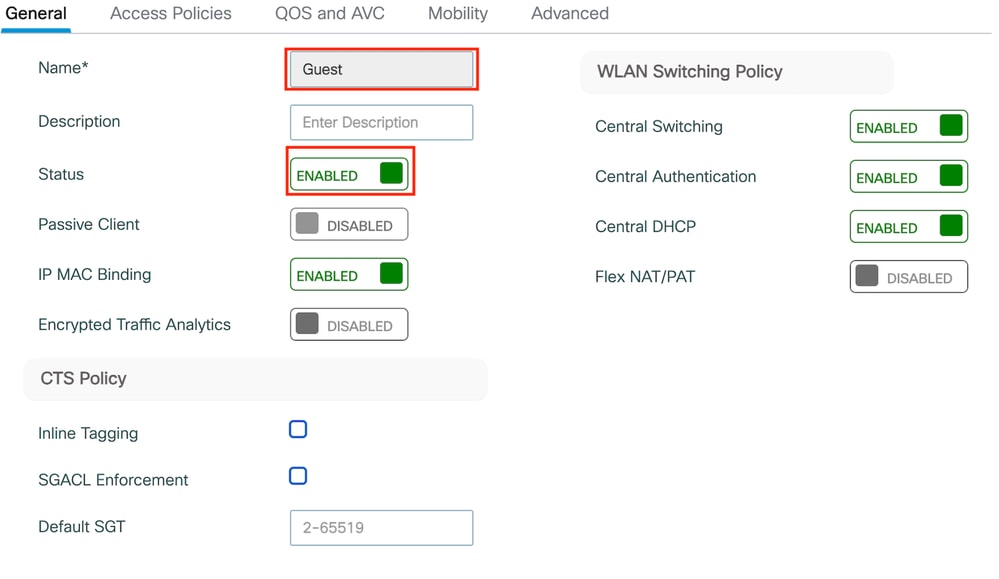 策略配置檔案
策略配置檔案
第2步:在訪問策略頁籤中,分配隨機VLAN。
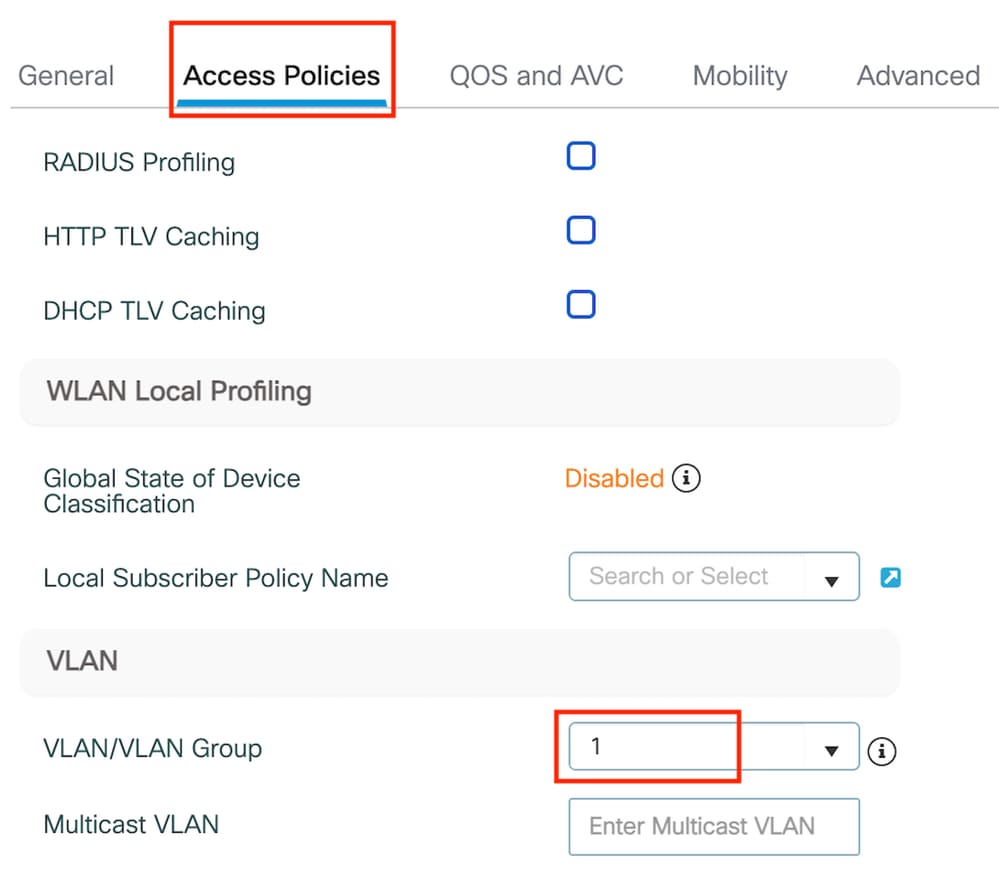 訪問策略
訪問策略
第3步:在Mobility選項卡中,切換錨點控制器並將其優先順序設置為Primary(1)
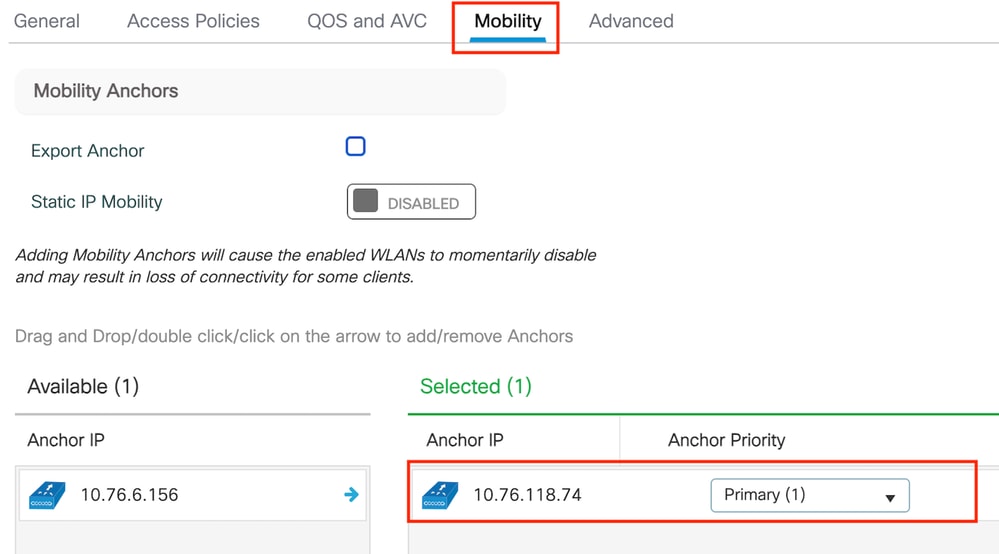 Mobility頁籤
Mobility頁籤

附註:9800外部WLC的原則設定檔必須與5520錨點WLC的訪客LAN設定檔相符,vlan設定除外
CLI組態
wireless profile policy Guest
no accounting-interim
exclusionlist timeout 180
no flex umbrella dhcp-dns-option
mobility anchor 10.76.118.74 priority 1
no shutdown
設定訪客LAN設定檔
步驟1:導覽至Configuration > Wireless > Guest LAN,然後選擇Add。配置唯一的配置檔名稱並啟用有線VLAN,指定有線訪客使用者專用的VLAN ID。最後,將配置檔案狀態切換為Enabled。
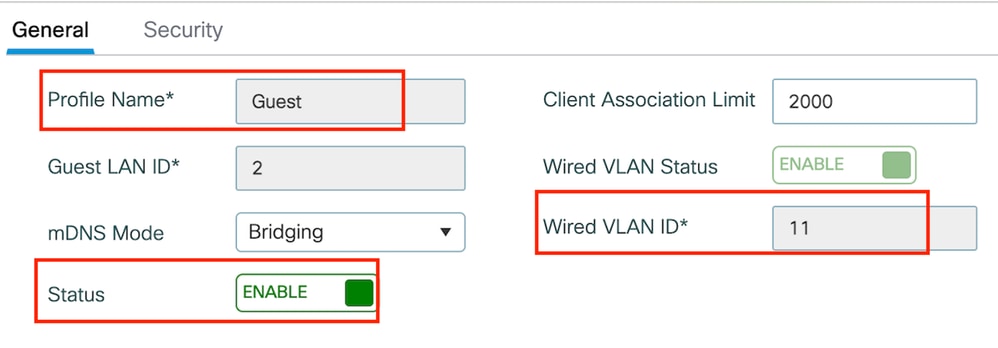 訪客LAN策略
訪客LAN策略
第2步:在Security索引標籤下,啟用Web Auth,對應Web Auth引數對應,然後從Authentication下拉選單中選擇RADIUS伺服器。
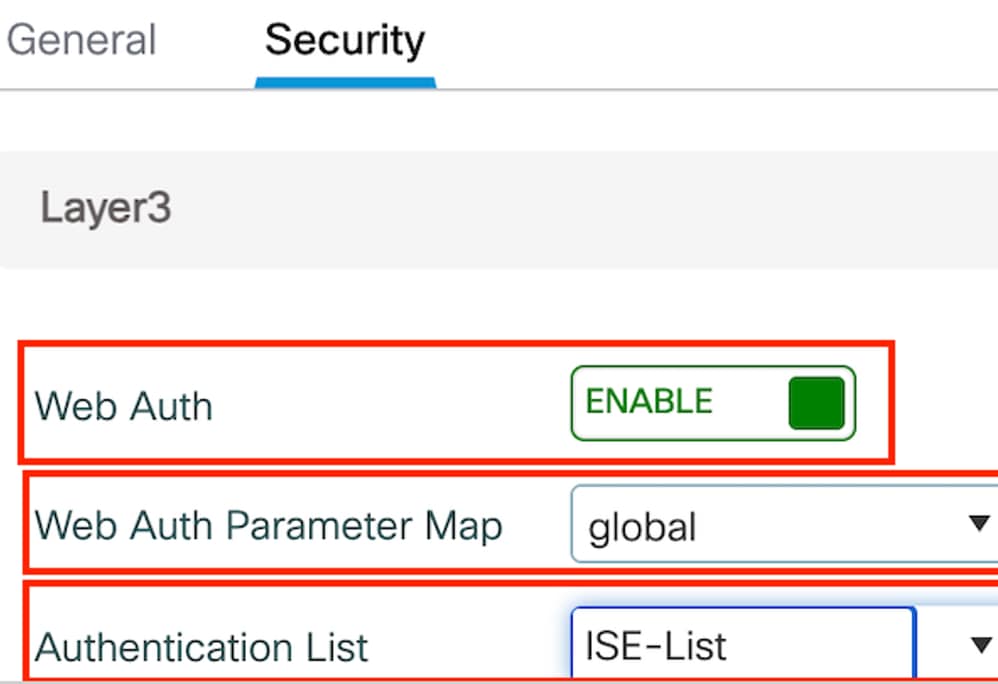 「安全」頁籤
「安全」頁籤

附註:9800外部和5520錨點控制器的訪客LAN設定檔名稱必須相同
CLI組態
guest-lan profile-name Guest 2 wired-vlan 11
security web-auth authentication-list ISE-List
security web-auth parameter-map global
訪客LAN對映
步驟1:導覽至Configuration > Wireless > Guest LAN。在Guest LAN MAP configuration部分中,選擇Add,並將Policy Profile對映到Guest LAN配置檔案。
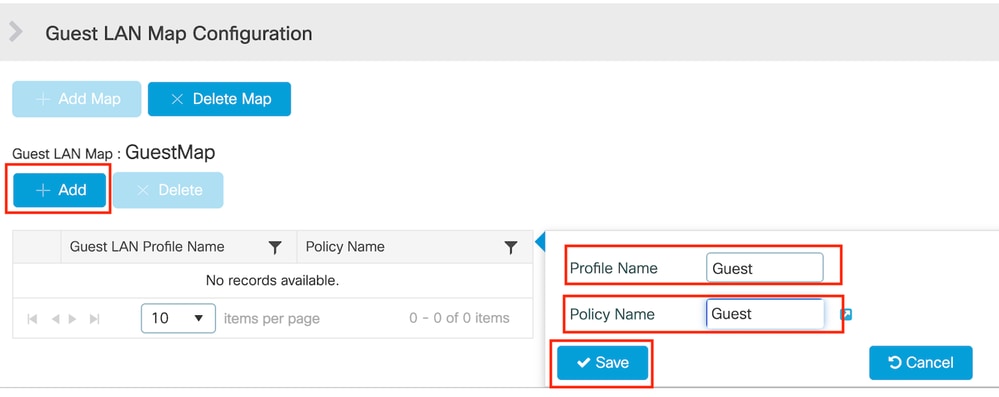 訪客LAN對映
訪客LAN對映
CLI組態
wireless guest-lan map GuestMap
guest-lan Guest policy Guest
錨點5520 WLC上的組態
設定Web驗證
步驟1:導覽至Security > Web Auth > Web Login Page。將Web Authentication type(Web身份驗證型別)設定為External(重定向到外部伺服器),並配置外部Web Auth URL。登入後可選擇Redirect URL,如果客戶端需要在成功身份驗證後重定向到專用頁面,則可以配置該客戶端。
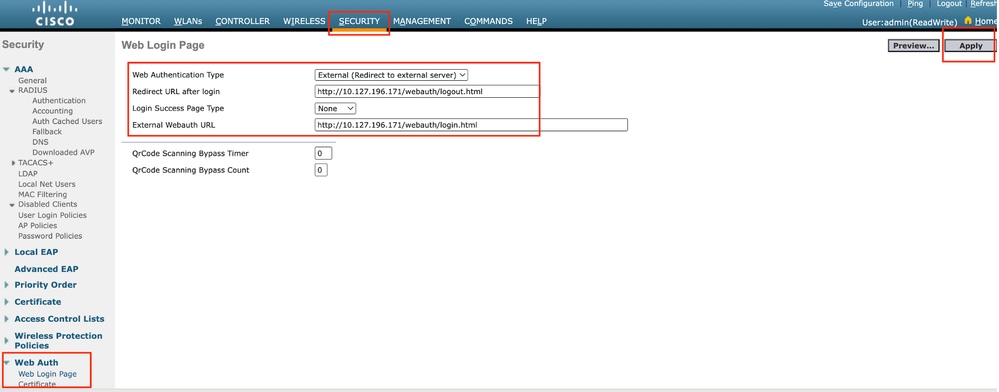 Web身份驗證設定
Web身份驗證設定
AAA設定:
第1步:設定radius伺服器
導覽至Security > Radius > Authentication > New。
 Radius伺服器
Radius伺服器
第2步:在控制器上配置RADIUS伺服器IP和共用金鑰。將伺服器狀態切換為Enabled,並選中Network User覈取方塊。
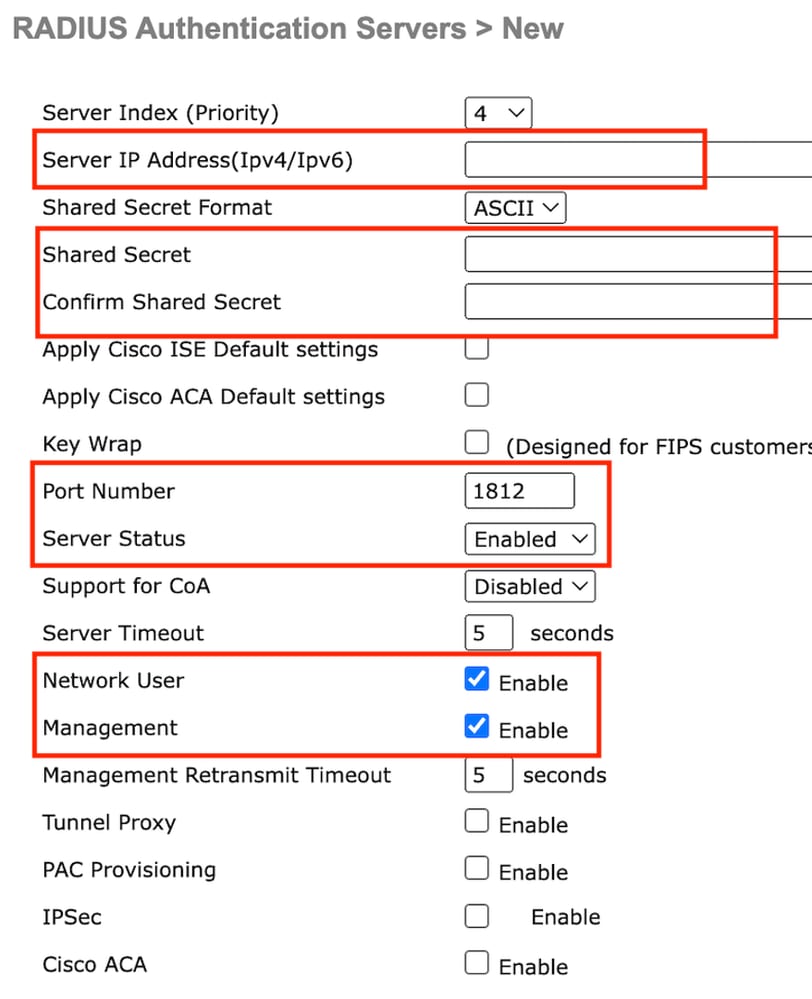 伺服器配置
伺服器配置
配置訪問控制清單
第1步:導航到安全>訪問控制清單,然後選擇新建。建立允許流量進入DNS和外部Web伺服器的預先驗證ACL。
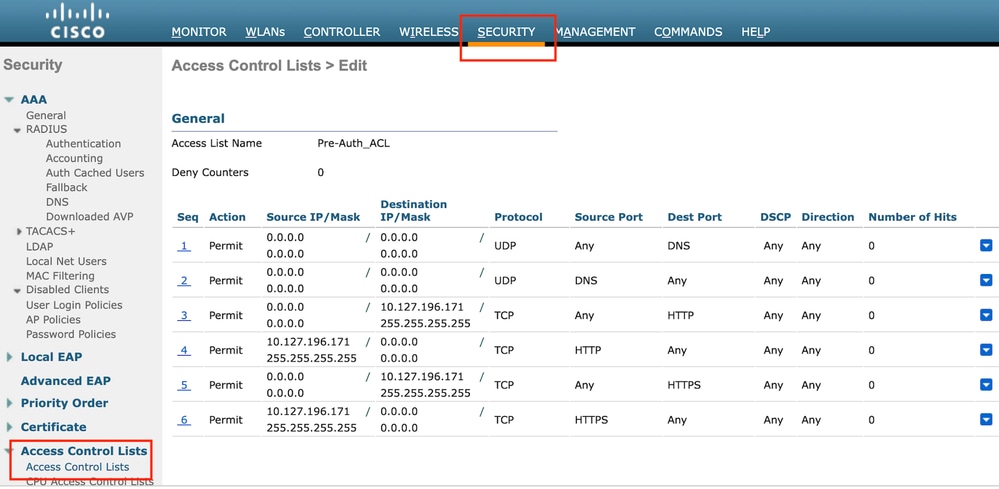 允許流量進入Web伺服器的訪問清單
允許流量進入Web伺服器的訪問清單
設定訪客LAN設定檔
第1步:導覽至WLANs >選擇Create New。
選擇Type作為Guest LAN,並配置與9800外部控制器的策略配置檔案相同的名稱。
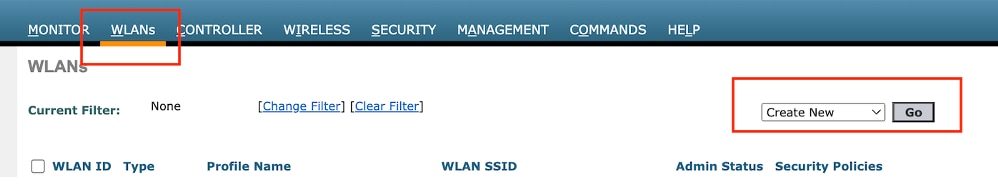 建立訪客LAN
建立訪客LAN
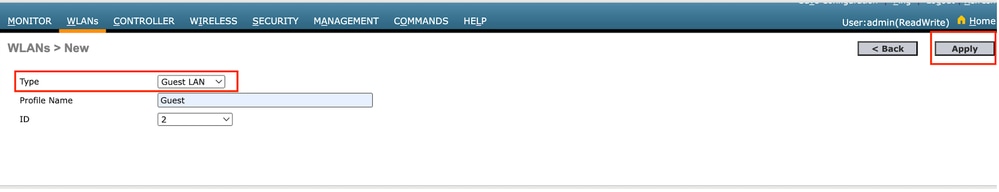 訪客LAN配置檔案
訪客LAN配置檔案
第2步:在訪客LAN配置檔案中對映入口和出口介面。
在此案例中,輸入介面選擇了「無」,因為輸入介面是來自外部控制器的EoIP通道。
Egress介面是有線使用者端實體連線的VLAN。
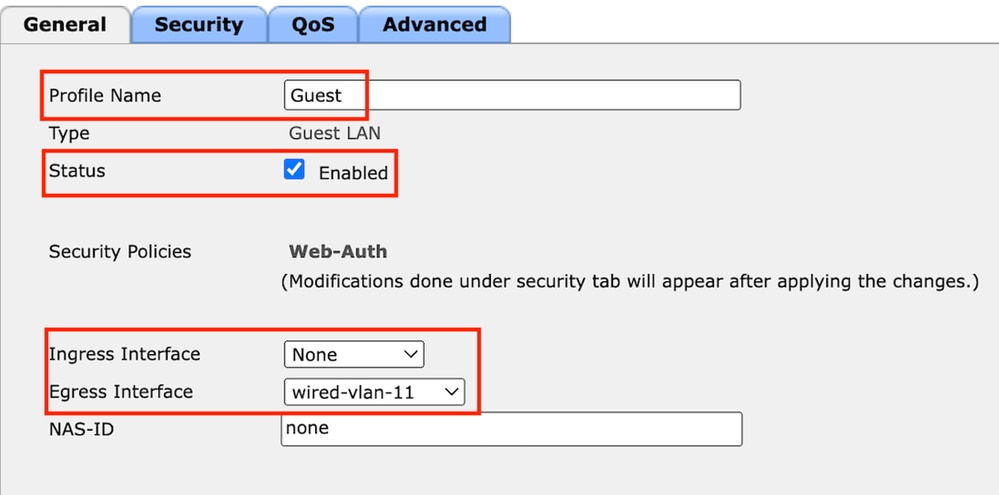 訪客LAN設定檔
訪客LAN設定檔
第3步:在「Security(安全)」頁籤下,選擇「Layer 3 security as Web Authentication(第3層安全)」並對映預身份驗證ACL。
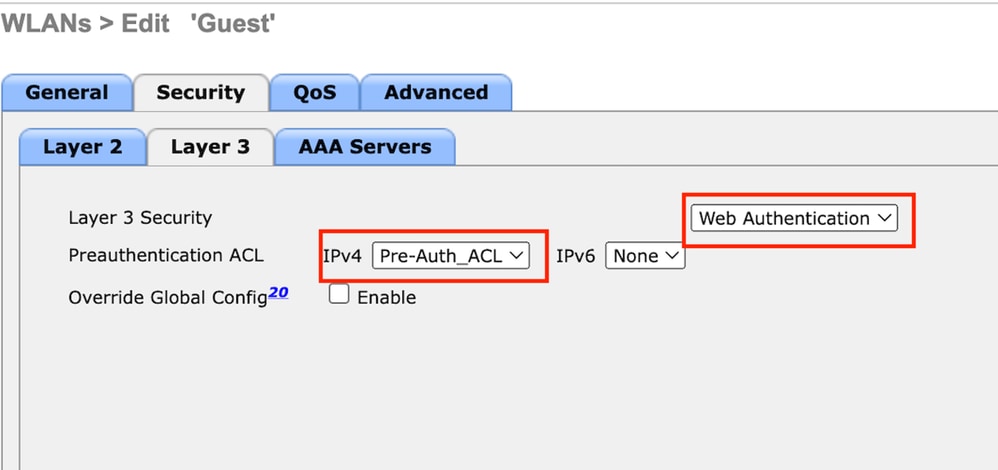 Guest LAN Security頁籤
Guest LAN Security頁籤
第4步:導覽至Security > AAA Server。
選擇下拉選單,並將radius伺服器對映到訪客LAN配置檔案。
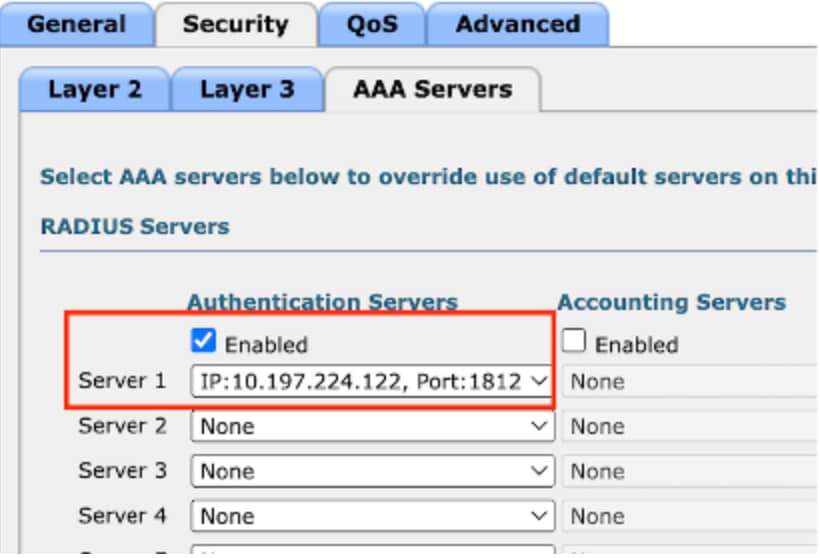 將radius伺服器對應到訪客LAN設定檔
將radius伺服器對應到訪客LAN設定檔
第5步:導覽至WLAN。將滑鼠懸停在訪客LAN配置檔案的下拉圖示上,然後選擇Mobility Anchor。

第6步:選擇Mobility Anchor Create將控制器配置為此訪客LAN配置檔案的匯出錨點。
 行動錨點建立
行動錨點建立
在AireOS 5520上配置錨點到Catalyst 9800的有線訪客
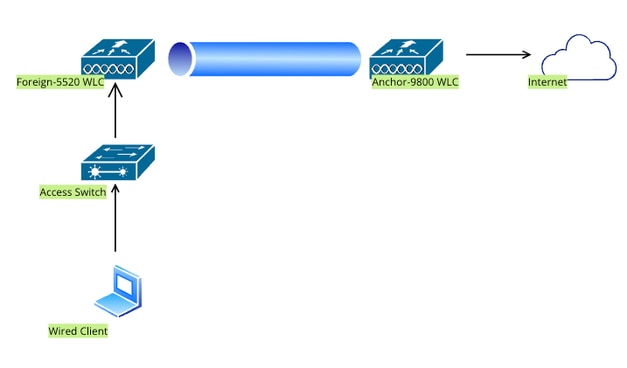 網路拓撲
網路拓撲
外部5520 WLC上的組態
控制器介面配置
步驟1:導覽至Controller > Interfaces > New。配置介面名稱、VLAN ID並啟用訪客LAN。
有線訪客需要兩個動態介面。
首先,建立一個第2層動態介面,並將其指定為Guest LAN。此介面擔任訪客LAN的輸入介面,有線使用者端可以在其中進行實體連線。
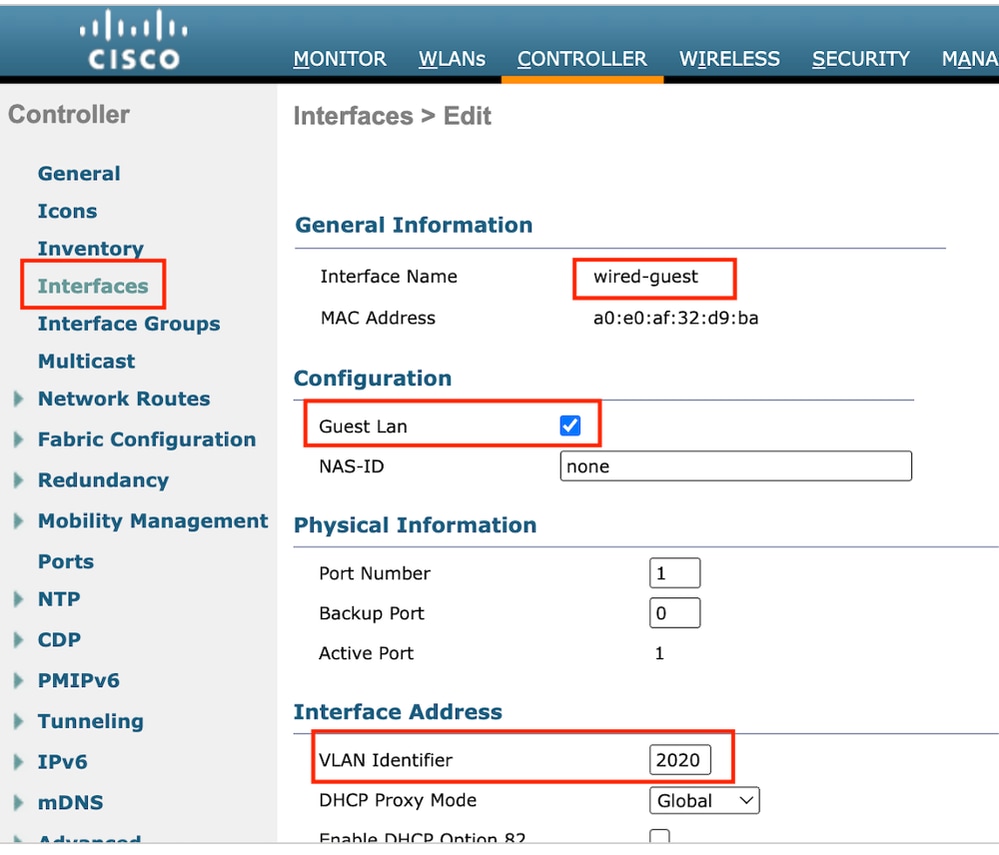 輸入介面
輸入介面
步驟2:導覽至Controller > Interfaces > New。配置介面名稱、VLAN ID。
第二個動態介面必須是控制器上的第3層介面,有線客戶端從此VLAN子網接收IP地址。此介面擔任訪客LAN設定檔的輸出介面。
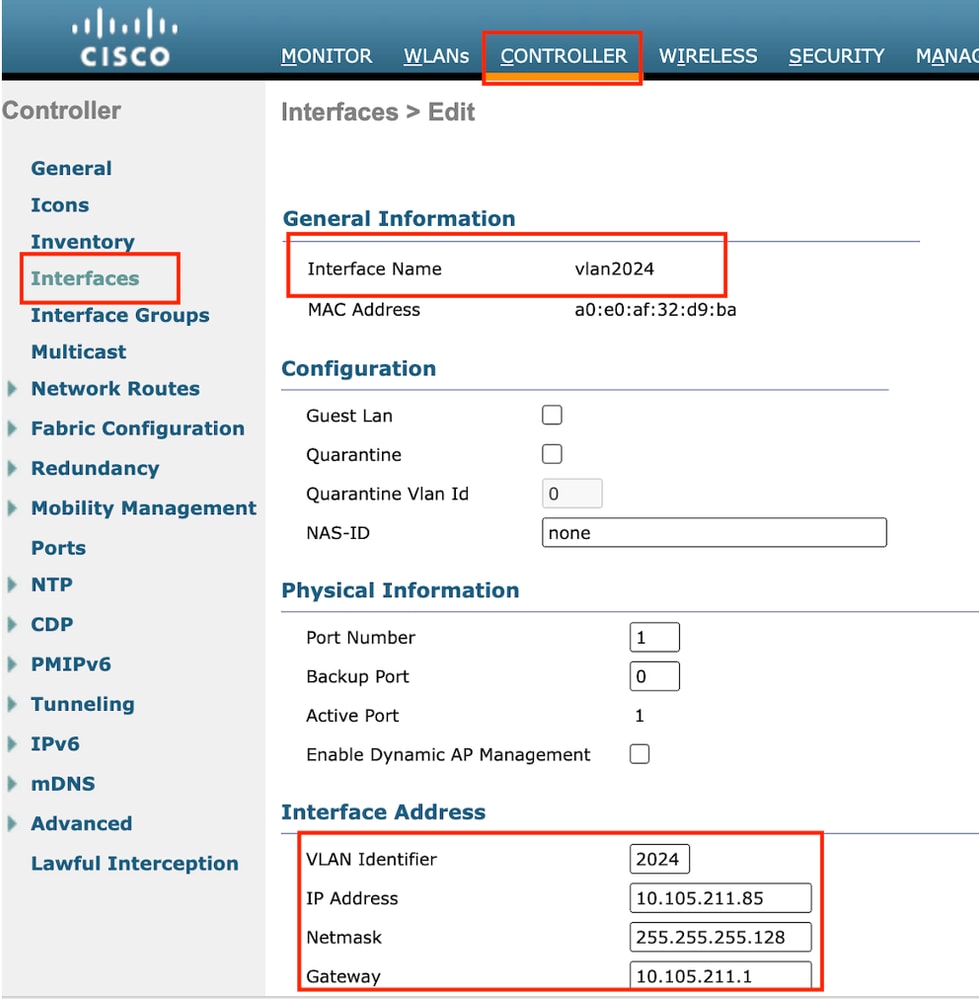 輸出介面
輸出介面
交換機埠配置
有線訪客使用者連線到存取層交換器,這些指定連線埠必須設定為在控制器上啟用訪客LAN的VLAN
接入層交換機埠配置
interface gigabitEthernet <x/x/x>
說明有線訪客接入
switchport access vlan 2020
switchport mode access
end
外部控制器上行鏈路埠配置
interface TenGigabitEthernet<x/x/x>
說明到外部WLC的中繼埠
switchport mode trunk
switchport trunk native vlan 2081
switchport trunk allowed vlan 2081,2020
end
錨點控制器上行鏈路埠配置
interface TenGigabitEthernet<x/x/x>
說明連線到錨點WLC的中繼埠
switchport mode trunk
switchport trunk native vlan 2081
交換機埠中繼允許的vlan 2081,2024
end
設定Web驗證
步驟1:導覽至Security > Web Auth > Web Login Page。將Web Authentication type(Web身份驗證型別)設定為External(重定向到外部伺服器),並配置外部Web Auth URL。登入後可選擇Redirect URL,如果客戶端需要在成功身份驗證後重定向到專用頁面,則可以配置該客戶端。
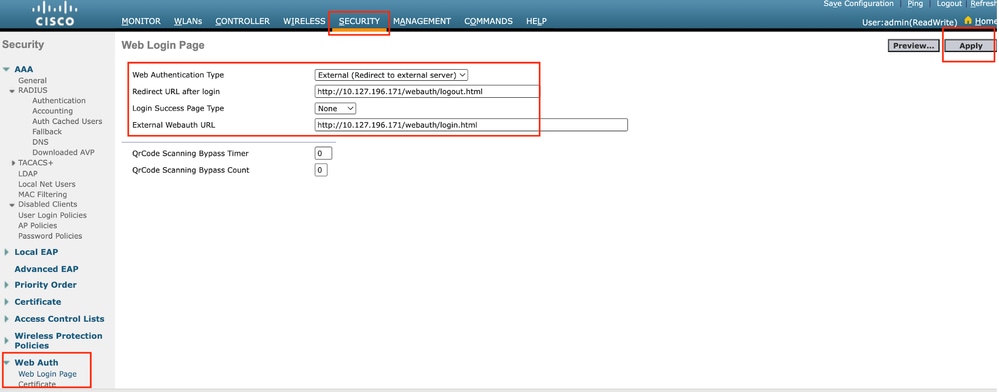 Web身份驗證設定
Web身份驗證設定
AAA設定:
第1步:設定radius伺服器
導覽至Security > Radius > Authentication > New。
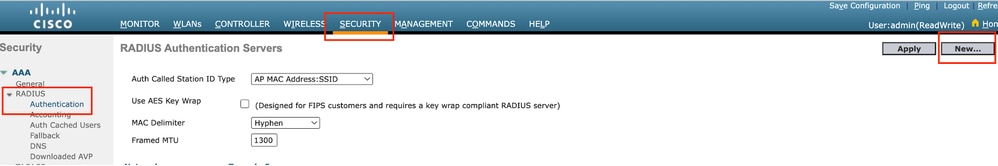 Radius伺服器
Radius伺服器
第2步:在控制器上配置RADIUS伺服器IP和共用金鑰。將伺服器狀態切換為Enabled,並選中Network User覈取方塊。
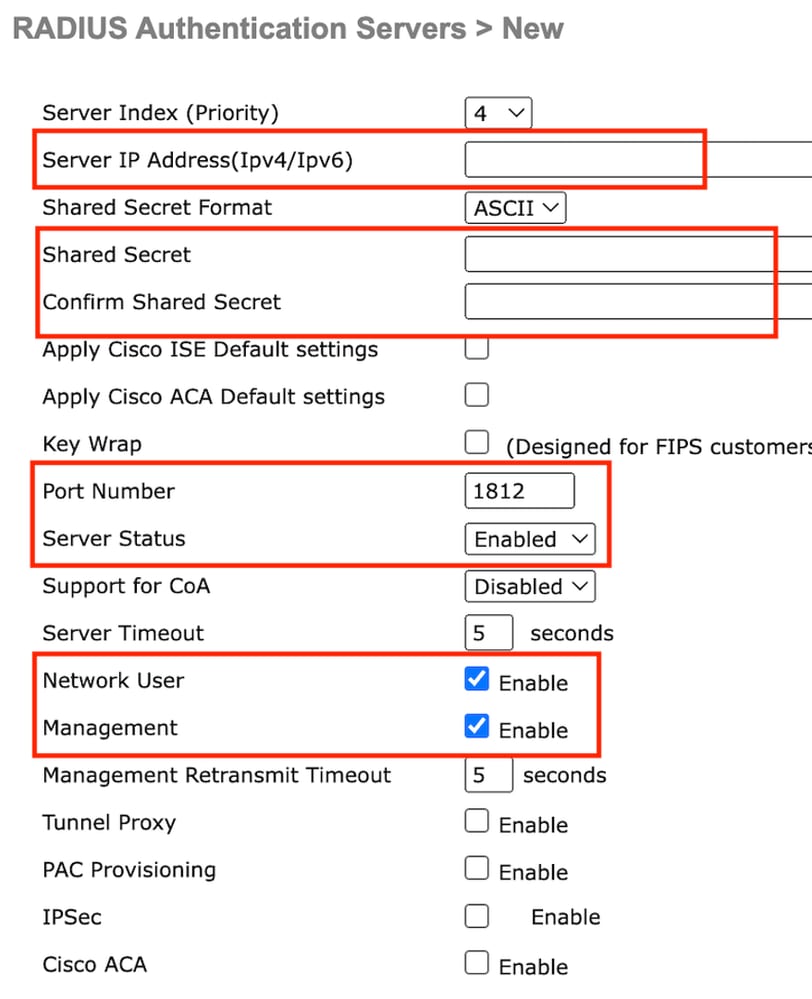 伺服器配置
伺服器配置
配置訪問控制清單
第1步:導航到安全>訪問控制清單,然後選擇新建。建立允許流量進入DNS和外部Web伺服器的預先驗證ACL。
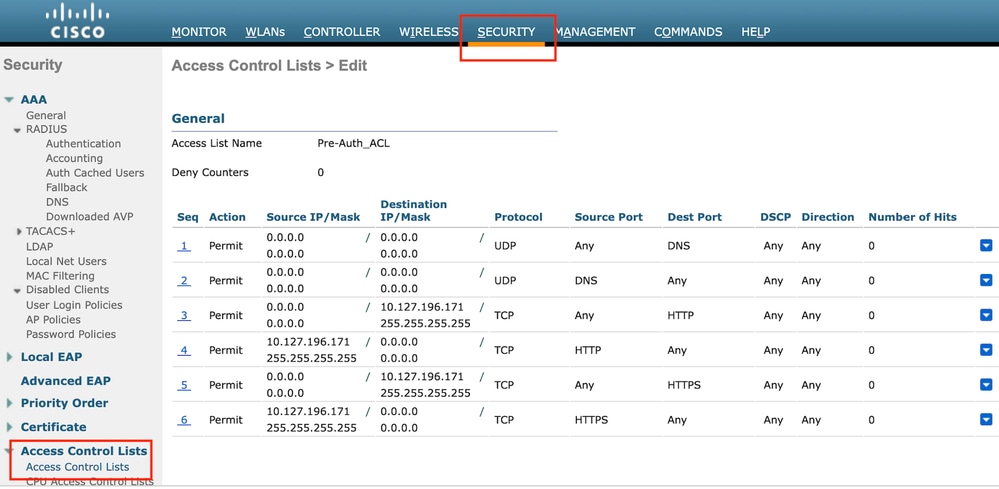 允許流量進入Web伺服器的訪問清單
允許流量進入Web伺服器的訪問清單
設定訪客LAN設定檔
第1步:導覽至WLAN > Create New > Go。
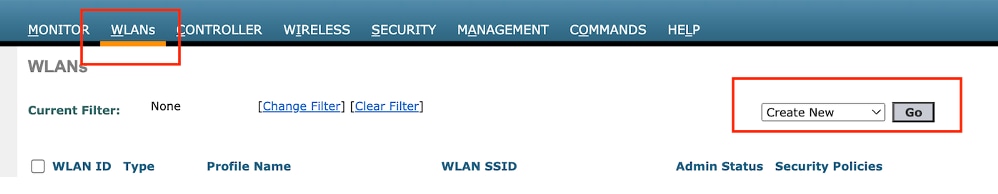 訪客LAN配置檔案
訪客LAN配置檔案
選擇Type as Guest LAN並配置配置檔名稱。在9800錨點控制器的原則設定檔和訪客LAN設定檔上必須設定相同的名稱。
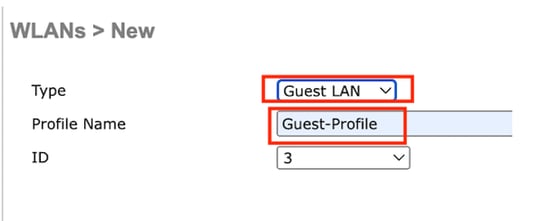 訪客LAN配置檔案
訪客LAN配置檔案
第2步:在General索引標籤下,在訪客LAN設定檔上對應輸入和輸出介面。
輸入介面是有線使用者端實體連線到的vlan。
輸出介面是客戶端請求的IP地址的VLAN子網。
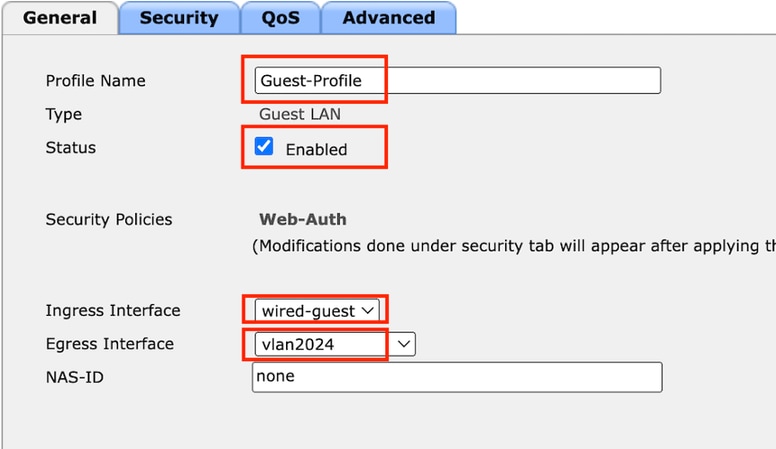 訪客LAN配置檔案
訪客LAN配置檔案
第3步:導航到安全>第3層。
選擇Layer 3 Security作為Web Authentication,然後對映預身份驗證ACL。
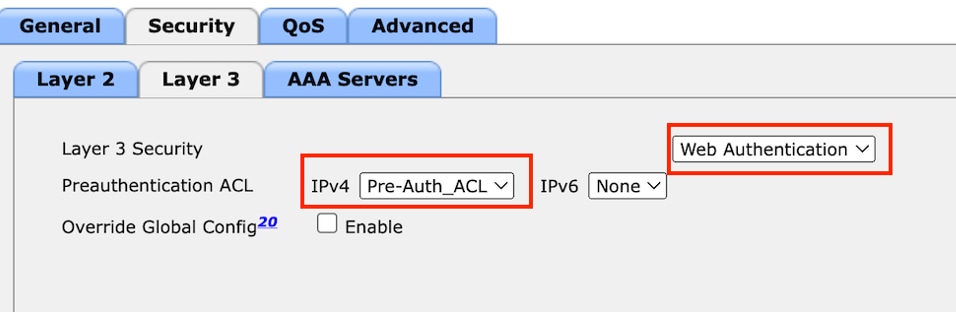 第3層安全頁籤
第3層安全頁籤
第4步:
在AAA servers頁籤下,對映Radius伺服器和Enabled覈取方塊。
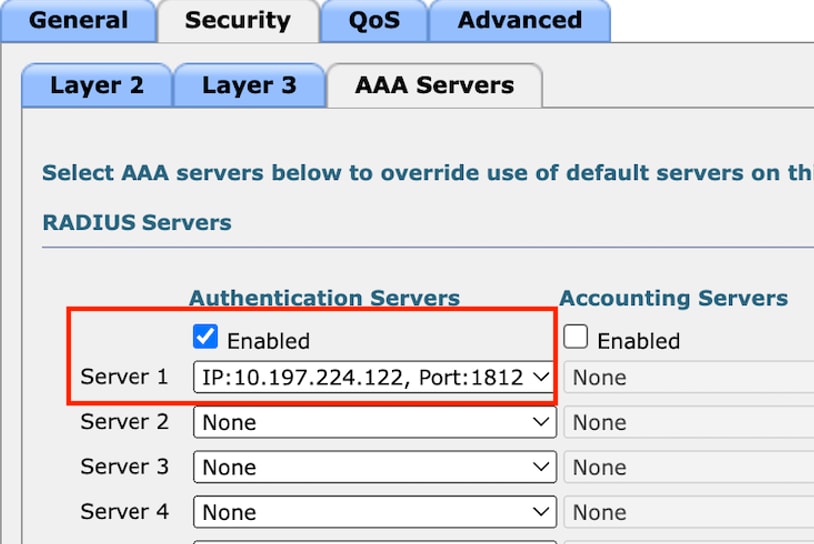 將RADIUS伺服器對應到訪客LAN設定檔
將RADIUS伺服器對應到訪客LAN設定檔
第5步:導航到WLAN頁面,將滑鼠懸停在訪客LAN配置檔案的向下按鈕圖示上,然後選擇移動錨點。
 行動錨點
行動錨點
第6步:將移動錨點從下拉選單對映到訪客LAN配置檔案。
 將行動錨點對應到訪客LAN
將行動錨點對應到訪客LAN
錨點9800 WLC上的組態
配置Web引數對映
步驟1:導航至Configuration > Security > Web Auth,然後選擇Global。確認在型別設定為webauth的情況下,控制器和信任點的虛擬IP位址是否已正確對映到設定檔上。
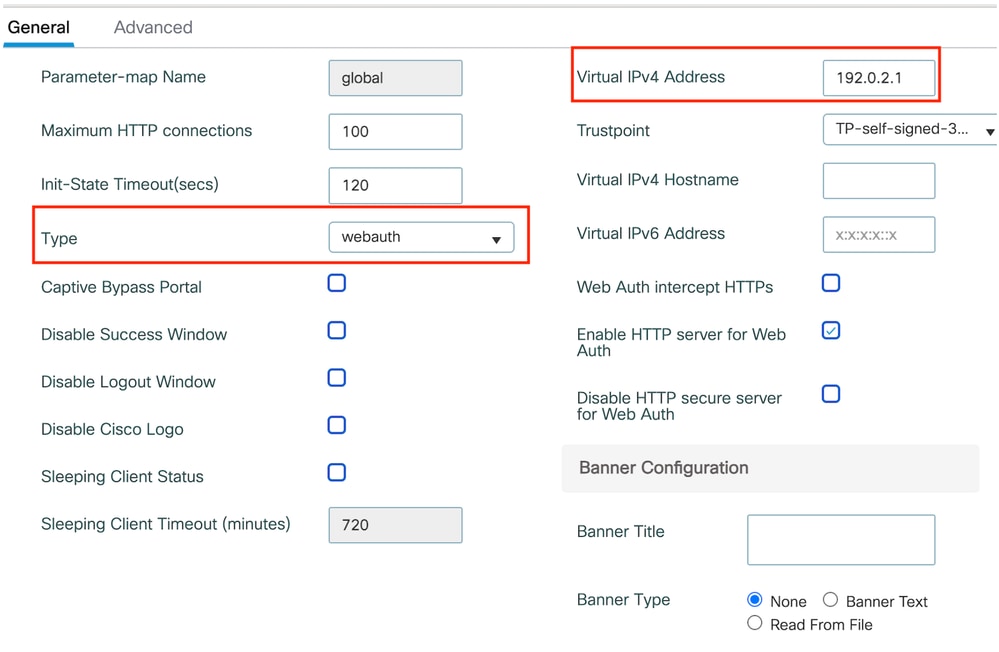 Web引數對映
Web引數對映
第2步:在Advanced頁籤下,指定客戶端必須重定向到的外部網頁URL。配置Redirect URL for Login和Redirect On-Failure。Redirect On-Success設定是可選配置。
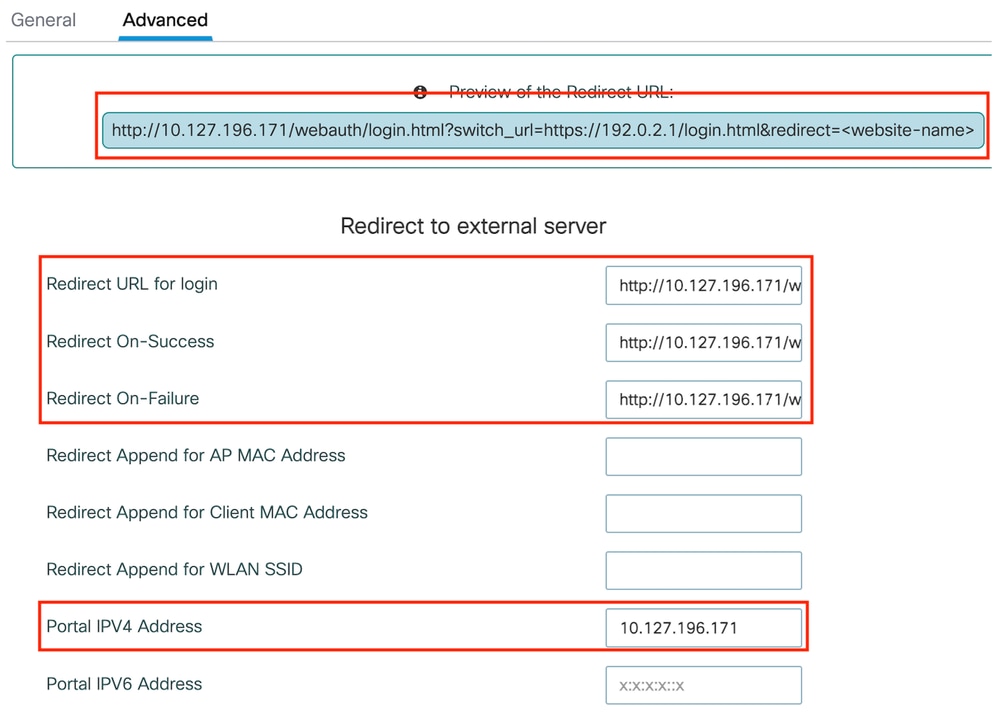 高級頁籤
高級頁籤
CLI配置
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
trustpoint TP-self-signed-3010594951
webauth-http-enable
附註:有關AAA設定,請參閱外部9800 WLC的「在Catalyst 9800上設定錨定到另一個Catalyst 9800的有線訪客」一節中提供的設定詳細資訊。
配置策略配置檔案
步驟1:導航到Configuration > Tags & Profiles > Policy。使用與外部控制器的訪客LAN配置檔案相同的名稱配置策略配置檔案。
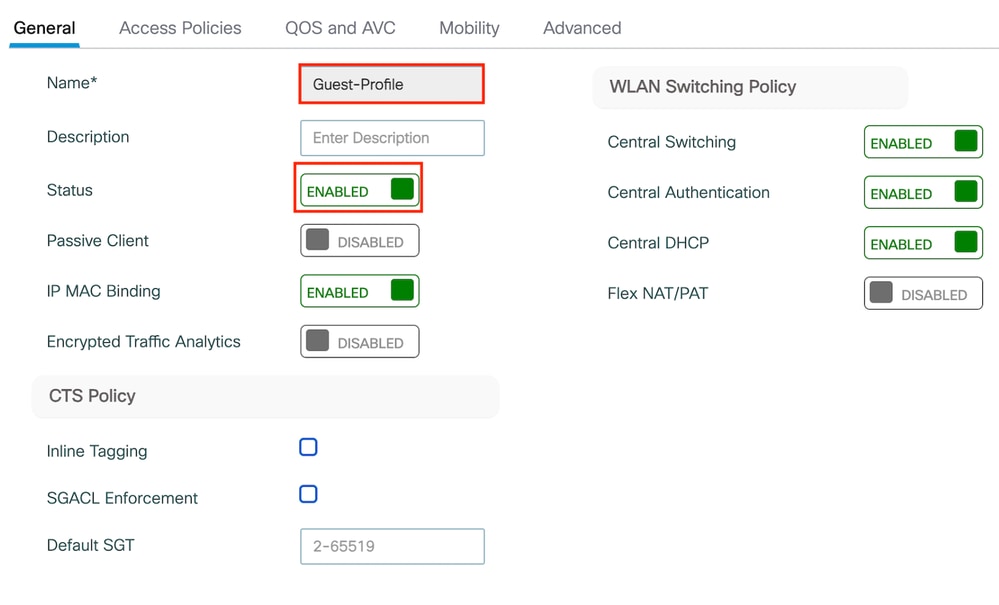 策略配置檔案
策略配置檔案
第2步:在Access Policies頁籤下,從下拉選單中對映有線客戶端VLAN
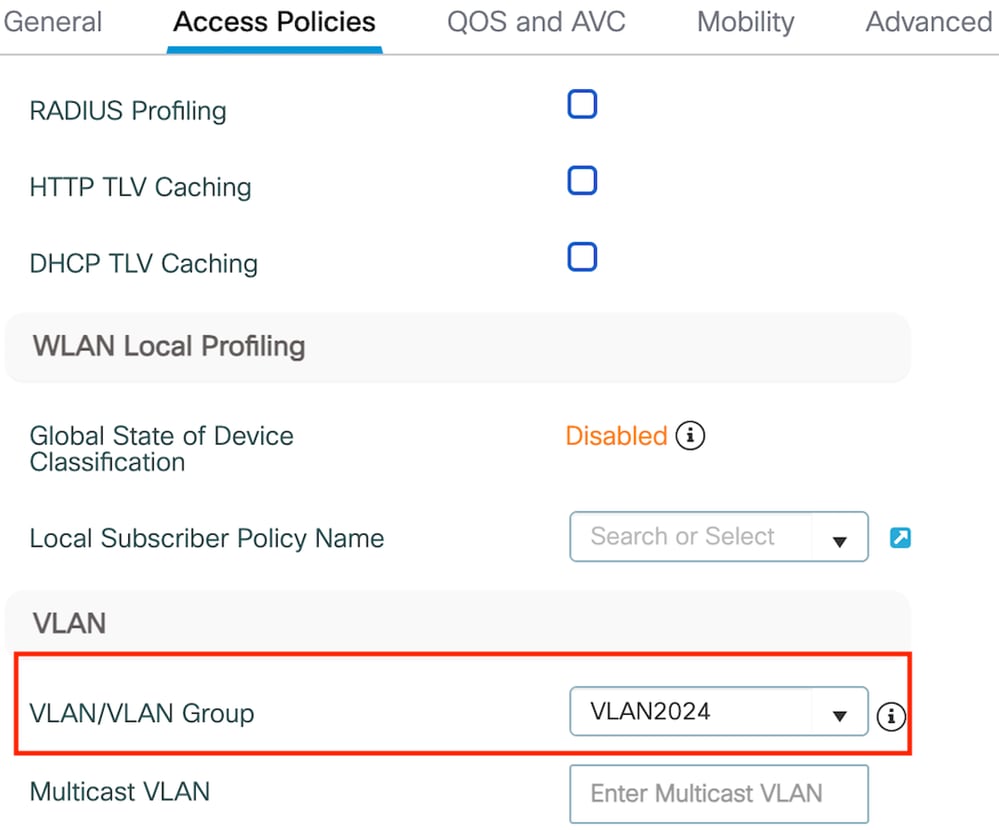 訪問策略
訪問策略
第3步:在Mobility頁籤下,選中Export Anchor。
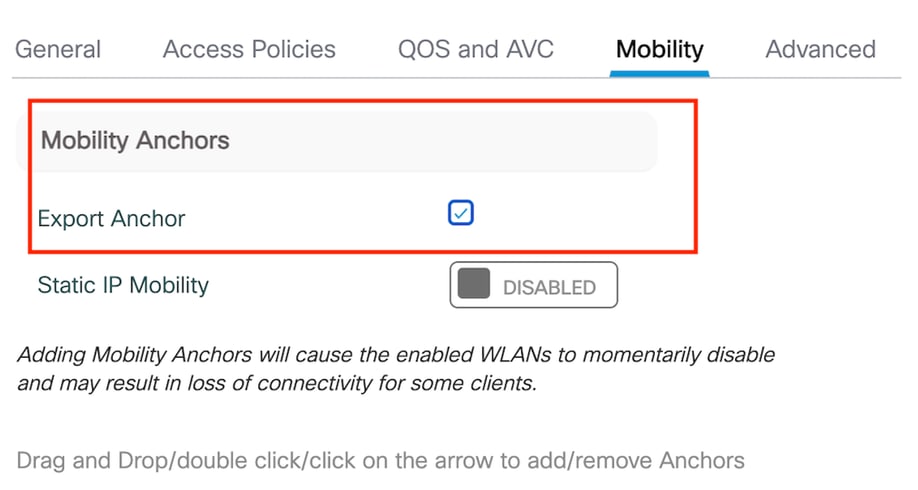 Mobility頁籤
Mobility頁籤
CLI組態
wireless profile policy Guest-Profile
no accounting-interim
exclusionlist timeout 180
no flex umbrella dhcp-dns-option
mobility anchor
vlan VLAN2024
no shutdown
設定訪客LAN設定檔
步驟1:導覽至Configuration > Wireless > Guest LAN,然後選擇Add以設定訪客LAN設定檔並停用有線VLAN狀態。
錨點上的訪客LAN設定檔名稱必須與外部WLC上的訪客LAN設定檔相同。
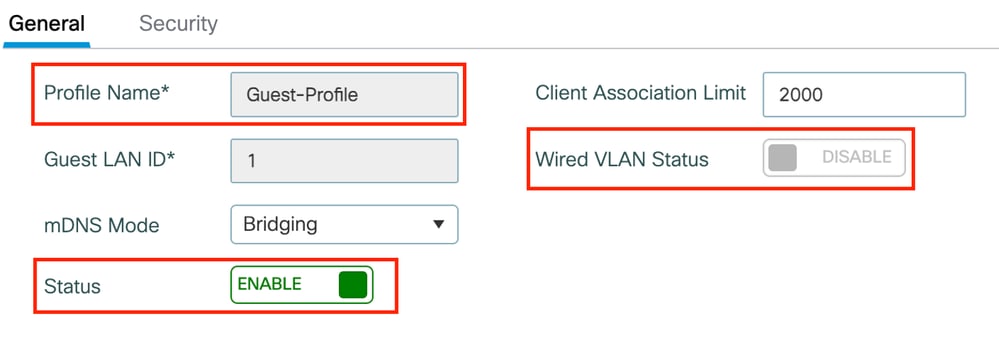 訪客LAN配置檔案
訪客LAN配置檔案
步驟2:在Security索引標籤下,啟用Web Auth。 從下拉選單中選擇Web Auth引數對映和身份驗證清單
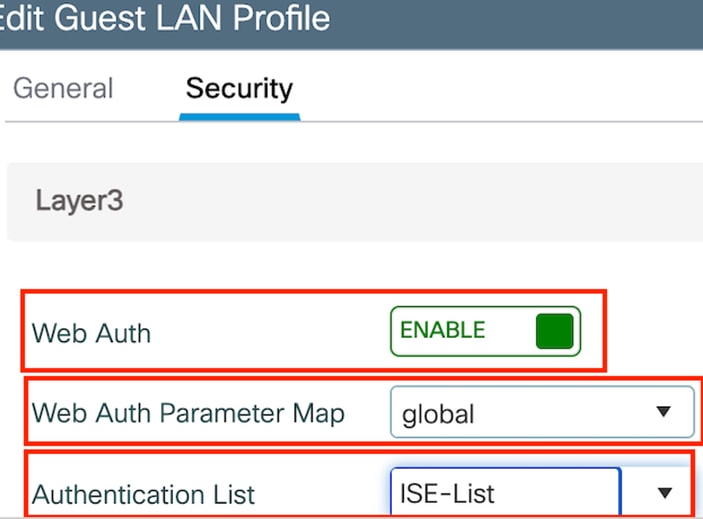 Guest LAN Security頁籤
Guest LAN Security頁籤
CLI組態
guest-lan profile-name Guest-Profile 1
security web-auth authentication-list ISE-List
security web-auth parameter-map global
訪客LAN對映
步驟1:導覽至Configuration > Wireless > Guest LAN。在Guest LAN MAP configuration部分中,選擇Add,並將Policy Profile對映到Guest LAN配置檔案。
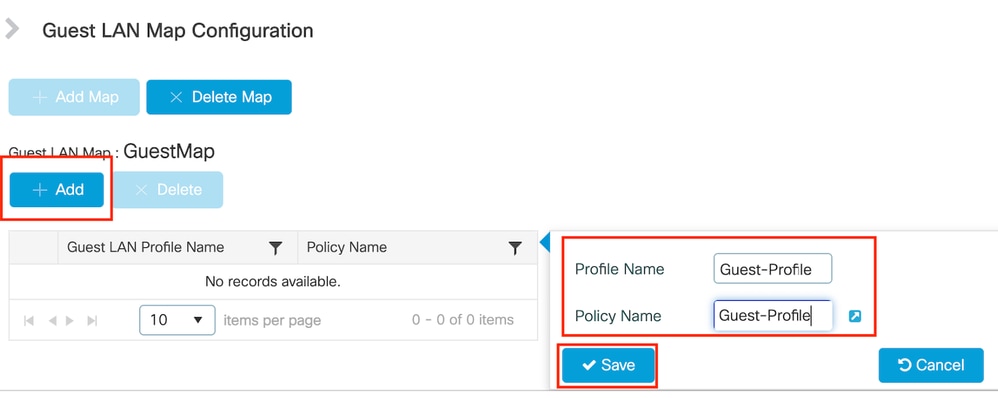 訪客LAN對映
訪客LAN對映
驗證
驗證控制器配置
#show guest-lan summary
GLAN GLAN Profile Name Status
------------------------------------------------
1 Guest-Profile UP
2 Guest UP
#show guest-lan id 1
Guest-LAN Profile Name : Guest
================================================
Guest-LAN ID : 2
Wired-Vlan : 11
Status : Enabled
Number of Active Clients : 0
Max Associated Clients : 2000
Security
WebAuth : Enabled
Webauth Parameter Map : global
Webauth Authentication List : ISE-List
Webauth Authorization List : Not configured
mDNS Gateway Status : Bridge
#show parameter-map type webauth global
Parameter Map Name : global
Type : webauth
Redirect:
For Login : http://10.127.196.171/webauth/login.html
On Success : http://10.127.196.171/webauth/logout.html
On Failure : http://10.127.196.171/webauth/failed.html
Portal ipv4 : 10.127.196.171
Virtual-ipv4 : 192.0.2.1
#show parameter-map type webauth name <profile name>(如果使用自定義web引數配置檔案)
#show wireless guest-lan-map summary
GLAN Profile Name Policy Name
------------------------------------------------------------------------------
Guest Guest
#show無線移動摘要
IP Public Ip MAC Address Group Name Multicast IPv4 Multicast IPv6 Status PMTU
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
10.76.118.70 10.76.118.70 f4bd.9e59.314b cisco1 0.0.0.0 :: Up 1385
#show ip http server status
HTTP server status: Enabled
HTTP server port: 80
HTTP server active supplementary listener ports: 21111
HTTP server authentication method: local
HTTP secure server capability: Present
HTTP secure server status: Enabled
HTTP secure server port: 443
HTTP secure server trustpoint: TP-self-signed-3010594951
>show guest-lan summary
Number of Guest LANs............................. 1
GLAN ID GLAN Profile Name Status Interface Name
------- ------------------------------------- -------- --------------------
2 Guest Enabled wired-vlan-11
>show guest-lan 2
Guest LAN Identifier............................. 2
Profile Name..................................... Guest
Status........................................... Enabled
Interface........................................ wired-vlan-11
Radius Servers
Authentication................................ 10.197.224.122 1812 *
Web Based Authentication...................... Enabled
Web Authentication Timeout.................... 300
IPv4 ACL........................................ Pre-Auth_ACL
Mobility Anchor List
GLAN ID IP Address Status
------- --------------- ------
2 10.76.118.74 Up
>show custom-web all
Radius Authentication Method..................... PAP
Cisco Logo....................................... Enabled
CustomLogo....................................... None
Custom Title..................................... None
Custom Message................................... None
Custom Redirect URL.............................. http://10.127.196.171/webauth/logout.html
Web Authentication Login Success Page Mode....... None
Web Authentication Type.......................... External
Logout-popup..................................... Enabled
External Web Authentication URL.................. http://10.127.196.171/webauth/login.html
QR Code Scanning Bypass Timer.................... 0
QR Code Scanning Bypass Count.................... 0
>show custom-web guest-lan 2
Guest LAN Status.............................. Enabled
Web Security Policy........................... Web Based Authentication
WebAuth Type.................................. External
Global Status................................. Enabled驗證客戶端策略狀態
關於外國,
#show線使用者端摘要
客戶端成功關聯後,外部控制器上的客戶端策略管理器狀態將運行。
MAC Address AP Name Type ID State Protocol Method Role
-------------------------------------------------------------------------------------------------------------------------
a0ce.c8c3.a9b5 N/A GLAN 1 Run 802.3 Web Auth Export Foreign
>show client detail a0ce.c8c3.a9b5
Client MAC Address............................... a0:ce:c8:c3:a9:b5
Client Username ................................. N/A
Client Webauth Username ......................... N/A
Client State..................................... Associated
User Authenticated by ........................... None
Client User Group................................
Client NAC OOB State............................. Access
guest-lan........................................ 1
Wireless LAN Profile Name........................ Guest-Profile
Mobility State................................... Export Foreign
Mobility Anchor IP Address....................... 10.76.118.70
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Pre-auth IPv4 ACL Name........................... Pre-Auth_ACL
EAP Type......................................... Unknown
Interface........................................ wired-guest-egress
VLAN............................................. 2024
Quarantine VLAN.................................. 0
在錨點上,
必須在錨點控制器上監視客戶端狀態轉換。
客戶端策略管理器狀態為Web身份驗證掛起。
MAC Address AP Name Type ID State Protocol Method Role
-------------------------------------------------------------------------------------------------------------------------
a0ce.c8c3.a9b5 10.76.6.156 GLAN 1 Webauth Pending 802.3 Web Auth Export Anchor
客戶端進行身份驗證後,策略管理器狀態將轉換為RUN狀態。
MAC Address AP Name Type ID State Protocol Method Role
-------------------------------------------------------------------------------------------------------------------------
a0ce.c8c3.a9b5 10.76.6.156 GLAN 1 Run 802.3 Web Auth Export Anchor
#show無線客戶端mac-address a0ce.c8c3.a9b5 detail
Client MAC Address : a0ce.c8c3.a9b5
Client MAC Type : Universally Administered Address
Client DUID: NA
Client IPv4 Address : 10.105.211.69
Client State : Associated
Policy Profile : Guest-Profile
Flex Profile : N/A
Guest Lan:
GLAN Id: 1
GLAN Name: Guest-Profile
Mobility:
Foreign IP Address : 10.76.118.74
Point of Attachment : 0xA0000003
Point of Presence : 0
Move Count : 1
Mobility Role : Export Anchor
Mobility Roam Type : L3 Requested
Policy Manager State: Webauth Pending
Last Policy Manager State : IP Learn Complete
Client Entry Create Time : 35 seconds
VLAN : VLAN2024
Session Manager:
Point of Attachment : mobility_a0000003
IIF ID : 0xA0000003
Authorized : FALSE
Session timeout : 28800
Common Session ID: 4a764c0a0000008ea0285466
Acct Session ID : 0x00000000
Auth Method Status List
Method : Web Auth
Webauth State : Login
Webauth Method : Webauth
Server Policies:
Resultant Policies:
URL Redirect ACL : WA-v4-int-10.127.196.171
Preauth ACL : WA-sec-10.127.196.171
VLAN Name : VLAN2024
VLAN : 2024
Absolute-Timer : 28800
成功進行Web身份驗證後,客戶端將進入RUN狀態。
show wireless client mac-address a0ce.c8c3.a9b5 detail
Client MAC Address : a0ce.c8c3.a9b5
Client MAC Type : Universally Administered Address
Client DUID: NA
Client IPv4 Address : 10.105.211.69
Client Username : testuser
Client State : Associated
Policy Profile : Guest-Profile
Flex Profile : N/A
Guest Lan:
GLAN Id: 1
GLAN Name: Guest-Profile
Wireless LAN Network Name (SSID) : N/A
BSSID : N/A
Connected For : 81 seconds
Protocol : 802.3
Policy Manager State: Run
Last Policy Manager State : Webauth Pending
Client Entry Create Time : 81 seconds
VLAN : VLAN2024
Last Tried Aaa Server Details:
Server IP : 10.197.224.122
Auth Method Status List
Method : Web Auth
Webauth State : Authz
Webauth Method : Webauth
Resultant Policies:
URL Redirect ACL : IP-Adm-V4-LOGOUT-ACL
VLAN Name : VLAN2024
VLAN : 2024
Absolute-Timer : 28800
>show client detail a0:ce:c8:c3:a9:b5
Client MAC Address............................... a0:ce:c8:c3:a9:b5
Client Username ................................. N/A
Client Webauth Username ......................... N/A
Client State..................................... Associated
Wireless LAN Profile Name........................ Guest
WLAN Profile check for roaming................... Disabled
Hotspot (802.11u)................................ Not Supported
Connected For ................................... 90 secs
IP Address....................................... 10.105.211.75
Gateway Address.................................. 10.105.211.1
Netmask.......................................... 255.255.255.128
Mobility State................................... Export Anchor
Mobility Foreign IP Address...................... 10.76.118.70
Security Policy Completed........................ No
Policy Manager State............................. WEBAUTH_REQD
Pre-auth IPv4 ACL Name........................... Pre-Auth_ACLPre-auth
IPv4 ACL Applied Status................. Yes
Pre-auth IPv4 ACL Applied Status................. Yes
身份驗證客戶端轉換為RUN狀態之後。
show client detail a0:ce:c8:c3:a9:b5
Client MAC Address............................... a0:ce:c8:c3:a9:b5
Client Username ................................. testuser
Client Webauth Username ......................... testuser
Client State..................................... Associated
User Authenticated by ........................... RADIUS Server
Client User Group................................ testuser
Client NAC OOB State............................. Access
Connected For ................................... 37 secs
IP Address....................................... 10.105.211.75
Gateway Address.................................. 10.105.211.1
Netmask.......................................... 255.255.255.128
Mobility State................................... Export Anchor
Mobility Foreign IP Address...................... 10.76.118.70
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Pre-auth IPv4 ACL Name........................... Pre-Auth_ACL
Pre-auth IPv4 ACL Applied Status................. Yes
EAP Type......................................... Unknown
Interface........................................ wired-vlan-11
VLAN............................................. 11
Quarantine VLAN.................................. 0
疑難排解
AireOS控制器調試
啟用客戶端調試
>debug client <H.H.H>
驗證是否已啟用調試
>show debugging
禁用調試
debug disable-all
9800放射性痕跡
啟用無線活動跟蹤以在CLI中為指定的MAC地址生成客戶端調試跟蹤。
啟用放射性跟蹤的步驟:
確保禁用所有條件調試。
clear platform condition all為指定的MAC地址啟用調試。
debug wireless mac monitor-time 重現問題後,禁用調試以停止RA跟蹤收集。
no debug wireless mac
RA追蹤停止後,會在控制器的bootflash中產生偵錯檔案。
show bootflash: | include ra_trace
2728 179 Jul 17 2024 15:13:54.0000000000 +00:00 ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
將檔案複製到外部伺服器。
copy bootflash:ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log tftp:///ra-FILENAME.txt
顯示調試日誌:
more bootflash:ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
在GUI中啟用RA跟蹤,
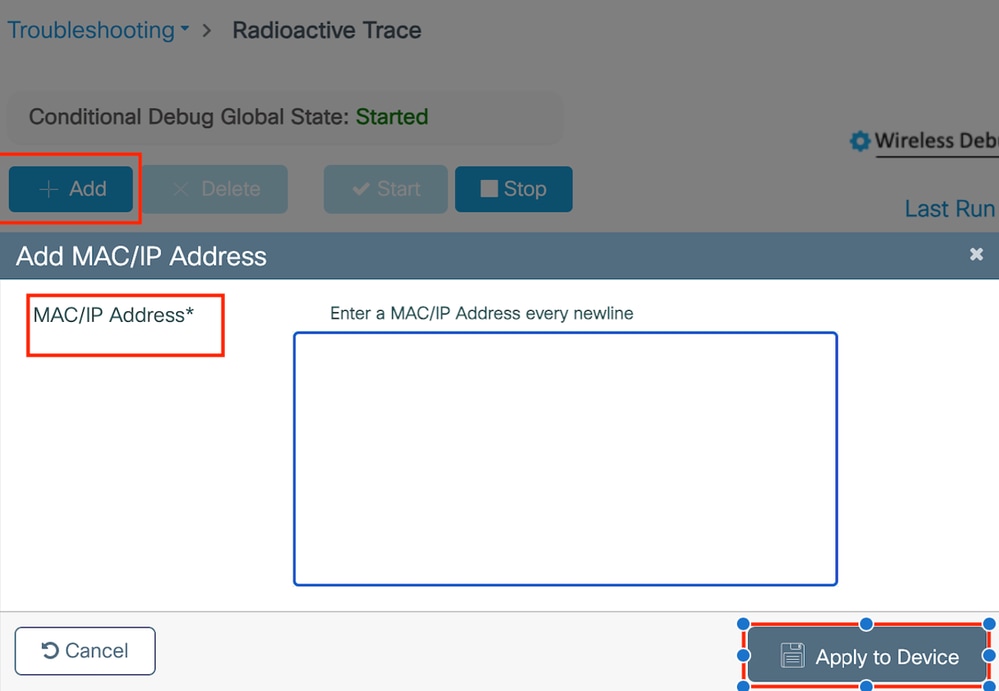 在WebUI上啟用RA跟蹤
在WebUI上啟用RA跟蹤
嵌入式封包擷取
導覽至Troubleshooting > Packet Capture。輸入捕獲名稱並指定客戶端的MAC地址作為內部過濾器MAC。將緩衝區大小設定為100,並選擇上行鏈路介面以監控傳入和傳出資料包。
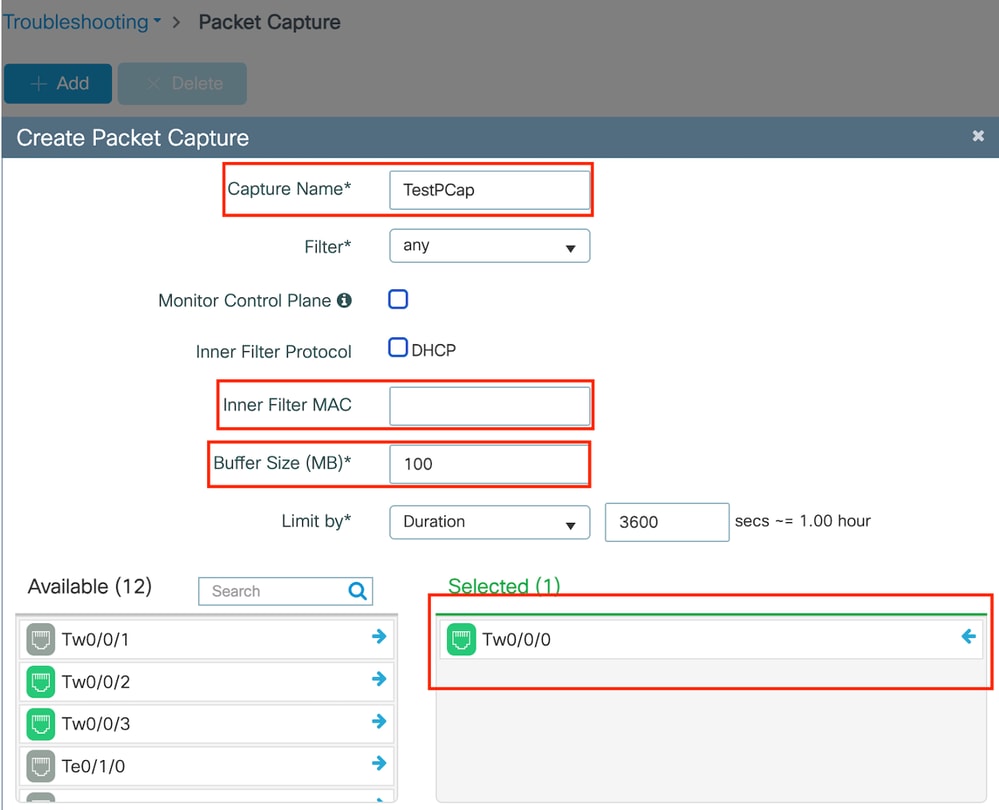 嵌入式封包擷取
嵌入式封包擷取

附註:選擇「監控控制流量」選項,檢視重定向到系統CPU並重新注入資料平面的流量。
導覽至Troubleshooting > Packet Capture,然後選擇Start以捕獲資料包。
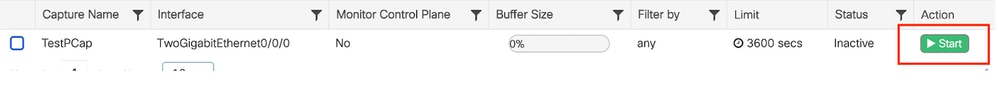 開始資料包捕獲
開始資料包捕獲
CLI配置
monitor capture TestPCap inner mac
monitor capture TestPCap buffer size 100
monitor capture TestPCap interface twoGigabitEthernet 0/0/0 both
monitor capture TestPCap start
monitor capture TestPCap stop show monitor capture TestPCap
Status Information for Capture TestPCap
Target Type:
Interface: TwoGigabitEthernet0/0/0, Direction: BOTH
Status : Inactive
Filter Details:
Capture all packets
Inner Filter Details:
Mac: 6c7e.67e3.6db9
Continuous capture: disabled
Buffer Details:
Buffer Type: LINEAR (default)
Buffer Size (in MB): 100
Limit Details:
Number of Packets to capture: 0 (no limit)
Packet Capture duration: 3600
Packet Size to capture: 0 (no limit)
Maximum number of packets to capture per second: 1000
Packet sampling rate: 0 (no sampling)
將封包擷取匯出到外部TFTP伺服器。
monitor capture TestPCap export tftp:/// TestPCap.pcap
導覽至Troubleshooting > Packet Capture,然後選擇Export將捕獲檔案下載到本地電腦上。
 下載EPC
下載EPC
工作日誌片段
AireOS外部控制器客戶端調試日誌
從有線客戶端接收的有線資料包
*apfReceiveTask: May 27 12:00:55.127: a0:ce:c8:c3:a9:b5 Wired Guest packet from 10.105.211.69 on mobile
外部控制器構建匯出錨點請求
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 Attempting anchor export for mobile a0:ce:c8:c3:a9:b5
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 mmAnchorExportSend: Building ExportForeignLradMac Payload Lrad Mac: 00:00:00:00:00:00
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 SGT Payload built in Export Anchor Req 0
外部控制器向錨點控制器傳送匯出錨點請求。
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 Export Anchor request sent to 10.76.118.70
錨點控制器為客戶端的錨點請求傳送確認
*Dot1x_NW_MsgTask_5: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 Recvd Exp Anchor Ack for mobile a0:ce:c8:c3:a9:b5 from 10.76.118.70
外部控制器上客戶端的移動角色已更新為匯出外部。
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 0.0.0.0 DHCP_REQD (7) mobility role update request from Unassociated to Export Foreign
Peer = 10.76.118.70, Old Anchor = 10.76.118.70, New Anchor = 10.76.118.70
客戶端轉換為RUN狀態。
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=ExpForeign, client state=APF_MS_STATE_ASSOCIATED
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 Stopping deletion of Mobile Station: (callerId: 75)
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 Moving client to run state
9800放射性核素監測儀
使用者端會與控制器建立關聯。
2024/07/15 04:10:29.087608331 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
關聯後正在進行移動性發現。
2024/07/15 04:10:29.091585813 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_MOBILITY_DISCOVERY_IN_PROGRESS
2024/07/15 04:10:29.091605761 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_MOBILITY_DISCOVERY_IN_PROGRESS -> S_CO_MOBILITY_DISCOVERY_IN_PROGRESS
處理移動性發現後,客戶端漫遊型別即更新為請求的L3。
2024/07/15 04:10:29.091664605 {wncd_x_R0-0}{1}: [mm-transition] [17765]: (info): MAC: a0ce.c8c3.a9b5 MMIF FSM transition: S_MA_INIT -> S_MA_MOBILITY_DISCOVERY_PROCESSED_TR on E_MA_MOBILITY_DISCOVERY
2024/07/15 04:10:29.091693445 {wncd_x_R0-0}{1}: [mm-client] [17765]: (info): MAC: a0ce.c8c3.a9b5 Roam type changed - None -> L3 Requested
外部控制器正在將匯出錨點請求傳送到錨點WLC。
2024/07/15 04:10:32.093245394 {mobilityd_R0-0}{1}: [mm-client] [18316]: (debug): MAC: a0ce.c8c3.a9b5 Export Anchor Request successfully processed.
2024/07/15 04:10:32.093253788 {mobilityd_R0-0}{1}: [mm-client] [18316]: (debug): MAC: a0ce.c8c3.a9b5 Forwarding Export Anchor Request to Anchor.
2024/07/15 04:10:32.093274405 {mobilityd_R0-0}{1}: [mm-client] [18316]: (info): MAC: a0ce.c8c3.a9b5 Forwarding export_anchor_req, sub type: 0 of XID (6396) from (WNCD[0]) to (ipv4: 10.76.118.70 )
從錨點控制器接收匯出錨點響應,並從使用者配置檔案應用vlan。
2024/07/15 04:10:32.106775213 {mobilityd_R0-0}{1}: [mm-transition] [18316]: (info): MAC: a0ce.c8c3.a9b5 MMFSM transition: S_MC_WAIT_EXP_ANC_RSP -> S_MC_EXP_ANC_RSP_RCVD_TR on E_MC_EXP_ANC_RSP_RCVD from ipv4: 10.76.118.70
2024/07/15 04:10:32.106811183 {mobilityd_R0-0}{1}: [mm-client] [18316]: (debug): MAC: a0ce.c8c3.a9b5 Export Anchor Response successfully processed.
2024/07/15 04:10:32.107183692 {wncd_x_R0-0}{1}: [epm-misc] [17765]: (info): [a0ce.c8c3.a9b5:Tw0/0/0] Anchor Vlan-id 2024 processed
2024/07/15 04:10:32.107247304 {wncd_x_R0-0}{1}: [svm] [17765]: (info): [a0ce.c8c3.a9b5] Applied User Profile: :
2024/07/15 04:10:32.107250258 {wncd_x_R0-0}{1}: [aaa-attr-inf] [17765]: (info): Applied User Profile: anchor-vlan 0 2024 (0x7e8)
處理匯出錨點請求後,客戶端移動角色將更新為匯出外部。
2024/07/15 04:10:32.107490972 {wncd_x_R0-0}{1}: [mm-client] [17765]: (debug): MAC: a0ce.c8c3.a9b5 Processed Export Anchor Response.
2024/07/15 04:10:32.107502336 {wncd_x_R0-0}{1}: [mm-client] [17765]: (info): MAC: a0ce.c8c3.a9b5 Mobility role changed - Unassoc -> Export Foreign
2024/07/15 04:10:32.107533732 {wncd_x_R0-0}{1}: [sanet-shim-translate] [17765]: (info): Anchor Vlan: 2024
2024/07/15 04:10:32.107592251 {wncd_x_R0-0}{1}: [mm-client] [17765]: (note): MAC: a0ce.c8c3.a9b5 Mobility Successful Guest Lan Client. Roam Type L3 Requested, Client IFID: 0xa0000007, Client Role: Export Foreign PoA: phy IfId PoP: 0xa0000005
客戶端轉換為IP學習狀態。
2024/07/15 04:10:32.108210365 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_DPATH_PLUMB_IN_PROGRESS -> S_CO_IP_LEARN_IN_PROGRESS
2024/07/15 04:10:32.108293096 {wncd_x_R0-0}{1}: [client-orch-sm] [17765]: (debug): MAC: a0ce.c8c3.a9b5 Received ip learn response. method: IPLEARN_METHOD_ROAMING
學習IP後,使用者端在外部WLC上移至RUN狀態。
2024/07/15 04:10:32.108521618 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_IP_LEARN_IN_PROGRESS -> S_CO_RUN
AireOS錨點控制器客戶端調試日誌
從外部控制器接收匯出錨點請求。
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 Anchor Export Request Recvd for mobile a0:ce:c8:c3:a9:b5 from 10.76.118.70 type : 16 subtype : 0 seq no : 0 xid : 1292566528
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 mmAnchorExportRcv: Extracting mmPayloadExportForeignLradMac
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 mmAnchorExportRcv Ssid=Guest useProfileName=0 profileNameToUse=0Security Policy=0x2010
為客戶端應用本地橋接vlan。
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 Updated local bridging VLAN to 11 while applying WLAN policy
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 Applying Interface(wired-vlan-11) policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 0
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 After applying Interface(wired-vlan-11) policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 11
移動角色更新為「匯出錨點」,客戶端狀態轉換為「關聯」。
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 0.0.0.0 START (0) mobility role update request from Unassociated to Export Anchor
Peer = 10.76.118.70, Old Anchor = 0.0.0.0, New Anchor = 10.76.118.74
Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5
add client MAC a0:ce:c8:c3:a9:b5 IP 10.76.118.70
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5
Sent message to add a0:ce:c8:c3:a9:b5 on member IP 10.76.118.70
*Dot1x_NW_MsgTask_5: May 28 10:46:27.832: a0:ce:c8:c3:a9:b5 mmAnchorExportRcv (mm_listen.c:7933) Changing state for mobile a0:ce:c8:c3:a9:b5 on AP 00:00:00:00:00:00 from Idle to Associated
移動性完成,客戶端狀態關聯,移動性角色為匯出錨點。
*Dot1x_NW_MsgTask_5: May 28 10:46:27.832: a0:ce:c8:c3:a9:b5 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=ExpAnchor, client state=APF_MS_STATE_ASSOCIATED
客戶端IP地址在控制器上獲取,並且狀態從所需的DHCP轉換到所需的Web身份驗證。
*dtlArpTask: May 28 10:46:58.356: a0:ce:c8:c3:a9:b5 Static IP client associated to interface wired-vlan-11 which can support client subnet.
*dtlArpTask: May 28 10:46:58.356: a0:ce:c8:c3:a9:b5 dtlArpSetType: Changing ARP Type from 0 ---> 1 for station a0:ce:c8:c3:a9:b5
*dtlArpTask: May 28 10:46:58.356: a0:ce:c8:c3:a9:b5 10.105.211.75 DHCP_REQD (7) Change state to WEBAUTH_REQD (8) last state DHCP_REQD (7)
Webauth URL是透過新增外部重新導向url和控制器虛擬IP位址來制定。
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Preparing redirect URL according to configured Web-Auth type
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Web-auth type External, using URL:http://10.127.196.171/webauth/login.html
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added switch_url, redirect URL is now http://10.127.196.171/webauth/login.html?switch_url=https://192.0.2.1/login.html
已將客戶端MAC地址和WLAN新增到URL。
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added client_mac , redirect URL is now http://10.127.196.171/webauth/login.html?switch_url= https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added wlan, redirect URL is now
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added wlan, redirect URL is now http://10.127.196.171/webauth/login.html?switch_url= https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5&wlan=Guest
為主機10.105.211.1解析HTTP GET後的最終URL
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- parser host is 10.105.211.1
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- parser path is /auth/discovery
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5-added redirect=, URL is now http://10.127.196.171/webauth/login.html?switch_url=https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5&wlan=Guest&redirect=10.105.211.1/auth/discovery?architecture=9
重定向URL在200 OK響應資料包中傳送到客戶端。
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- 200 send_data =HTTP/1.1 200 OK
Location:http://10.127.196.171/webauth/login.html?switch_url=https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5&wlan=Guest&redirect=10.105.211.1/auth/discovery?architecture=9 客戶端與重定向url主機建立TCP連線。使用者端在入口端提交登入使用者名稱和密碼後,控制器會將radius要求傳送到radius伺服器
控制器收到Access-Accept後,客戶端關閉TCP會話並進入RUN狀態。
*aaaQueueReader: May 28 10:46:59:077: a0:ce:c8:c3:a9:b5 Sending the packet to v4 host 10.197.224.122:1812
*aaaQueueReader: May 28 10:46:59:077: a0:ce:c8:c3:a9:b5 Successful transmission of Authentication Packet (pktId 127) to 10.197.224.122:1812
*aaaQueueReader: May 28 10:46:59:077: AVP[01] User-Name................................testuser (17 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[03] Calling-Station-Id.......................a0-ce-c8-c3-a9-b5 (17 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[04] Nas-Port.................................0x00000008 (8) (4 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[05] Nas-Ip-Address...........................0x0a4c7646 (184548604) (4 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[06] NAS-Identifier...........................POD1586-CT5520 (14 bytes)
*aaaQueueReader: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 radiusServerFallbackPassiveStateUpdate: RADIUS server is ready 10.197.224.122 port 1812 index 0 active 1
*radiusTransportThread: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 Access-Accept received from RADIUS server 10.197.224.122 (qid:5) with port:1812, pktId:127
*Dot1x_NW_MsgTask_5: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 Processing Access-Accept for mobile a0:ce:c8:c3:a9:b5
*apfReceiveTask: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 Moving client to run state
9800 Anchor放射性追蹤控制器
來自外部控制器的客戶端移動通告消息。
2024/07/15 15:10:20.614677358 {mobilityd_R0-0}{1}: [mm-client] [15259]: (debug): MAC: a0ce.c8c3.a9b5 Received mobile_announce, sub type: 0 of XID (6394) from (ipv4: 10.76.6.156 )
當客戶端正在關聯時,從外部控制器接收的匯出錨點請求,該外部控制器的匯出錨點響應由錨點控制器傳送,可以在外部控制器RA跟蹤上驗證。
2024/07/15 15:10:22.615246594 {mobilityd_R0-0}{1}: [mm-transition] [15259]: (info): MAC: a0ce.c8c3.a9b5 MMFSM transition: S_MC_INIT -> S_MC_ANCHOR_EXP_ANC_REQ_RCVD_TR on E_MC_EXP_ANC_REQ_RCVD from ipv4: 10.76.6.156
客戶端被移動到關聯狀態,移動角色被轉換為匯出錨點。
2024/07/15 15:10:22.616156811 {wncd_x_R0-0}{1}: [client-orch-state] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2024/07/15 15:10:22.627358367 {wncd_x_R0-0}{1}: [mm-client] [14709]: (note): MAC: a0ce.c8c3.a9b5 Mobility Successful. Roam Type L3 Requested, Sub Roam Type MM_SUB_ROAM_TYPE_NONE, Client IFID: 0xa0000005, Client Role: Export Anchor PoA: 0xa0000001 PoP: 0x0
2024/07/15 15:10:22.627462963 {wncd_x_R0-0}{1}: [dot11] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client datapath entry params - ssid:Guest-Profile,slot_id:0 bssid ifid: 0x0, radio_ifid: 0x0, wlan_ifid: 0xf0408001
2024/07/15 15:10:22.627490485 {mobilityd_R0-0}{1}: [mm-client] [15259]: (debug): MAC: a0ce.c8c3.a9b5 Export Anchor Response successfully processed.
2024/07/15 15:10:22.627494963 {mobilityd_R0-0}{1}: [mm-client] [15259]: (debug): MAC: a0ce.c8c3.a9b5 Forwarding Anchor Response to Foreign.
IP學習完成,客戶端IP通過ARP學習。
2024/07/15 15:10:22.628124206 {wncd_x_R0-0}{1}: [client-iplearn] [14709]: (info): MAC: a0ce.c8c3.a9b5 IP-learn state transition: S_IPLEARN_INIT -> S_IPLEARN_IN_PROGRESS
2024/07/15 15:10:23.627064171 {wncd_x_R0-0}{1}: [sisf-packet] [14709]: (info): RX: ARP from interface mobility_a0000001 on vlan 2024 Source MAC: a0ce.c8c3.a9b5 Dest MAC: ffff.ffff.ffff ARP REQUEST, ARP sender MAC: a0ce.c8c3.a9b5 ARP target MAC: 0000.0000.0000 ARP sender IP: 10.105.211.69, ARP target IP: 10.105.211.1,
2024/07/15 15:10:24.469704913 {wncd_x_R0-0}{1}: [client-iplearn] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client IP learn successful. Method: ARP IP: 10.105.211.69
2024/07/15 15:10:24.470527056 {wncd_x_R0-0}{1}: [client-iplearn] [14709]: (info): MAC: a0ce.c8c3.a9b5 IP-learn state transition: S_IPLEARN_IN_PROGRESS -> S_IPLEARN_COMPLETE
2024/07/15 15:10:24.470587596 {wncd_x_R0-0}{1}: [client-orch-sm] [14709]: (debug): MAC: a0ce.c8c3.a9b5 Received ip learn response. method: IPLEARN_METHOD_ARP
2024/07/15 15:10:24.470613094 {wncd_x_R0-0}{1}: [client-orch-sm] [14709]: (debug): MAC: a0ce.c8c3.a9b5 Triggered L3 authentication. status = 0x0, Success
客戶端策略狀態為Web身份驗證掛起。
2024/07/15 15:10:24.470748350 {wncd_x_R0-0}{1}: [client-auth] [14709]: (info): MAC: a0ce.c8c3.a9b5 Client auth-interface state transition: S_AUTHIF_L2_WEBAUTH_DONE -> S_AUTHIF_WEBAUTH_PENDING
TCP交握被控制器偽裝。當使用者端傳送HTTP GET時,會傳送一個200 OK回應訊框,其中包含重新導向URL。
使用者端必須使用重新導向URL建立TCP交握並載入頁面。
2024/07/15 15:11:37.579177010 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]HTTP GET request
2024/07/15 15:11:37.579190912 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]Parse GET, src [10.105.211.69] dst [10.3.3.3] url [http://10.3.3.3/favicon.ico]
2024/07/15 15:11:37.579226658 {wncd_x_R0-0}{1}: [webauth-state] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]Param-map used: global
2024/07/15 15:11:37.579230650 {wncd_x_R0-0}{1}: [webauth-state] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]State LOGIN -> LOGIN
2024/07/15 15:11:47.123072893 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]GET rcvd when in LOGIN state
2024/07/15 15:11:47.123082753 {wnc2024/07/15 15:12:04.280574375 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]POST rcvd when in LOGIN state
使用者端在Web入口頁面提交登入憑證時,會向radius伺服器傳送存取要求封包以進行驗證。
2024/07/15 15:12:04.281076844 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Send Access-Request to 10.197.224.122:1812 id 0/0, len 363
2024/07/15 15:12:04.281087672 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: authenticator e3 01 8f 5d 8e 52 fc cb - e0 d7 03 da c1 a2 09 e6
2024/07/15 15:12:04.281093278 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Calling-Station-Id [31] 19 "a0-ce-c8-c3-a9-b5"
2024/07/15 15:12:04.281097034 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: User-Name [1] 10 "testuser"
2024/07/15 15:12:04.281148298 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Cisco AVpair [1] 16 "method=webauth"
從radius伺服器收到Access-Accept,webauth成功。
2024/07/15 15:12:04.683597101 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Received from id 1812/0 10.197.224.122:0, Access-Accept, len 105
2024/07/15 15:12:04.683607762 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: authenticator 52 3e b0 13 99 ab a7 15 - 57 76 47 a1 fb e3 b8 99
2024/07/15 15:12:04.683614780 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: User-Name [1] 10 "testuser"
身份驗證成功,客戶端策略狀態為RUN。
2024/07/15 15:12:04.683901842 {wncd_x_R0-0}{1}: [webauth-state] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]State AUTHENTICATING -> AUTHC_SUCCESS
2024/07/15 15:12:04.690643388 {wncd_x_R0-0}{1}: [errmsg] [14709]: (info): %CLIENT_ORCH_LOG-6-CLIENT_ADDED_TO_RUN_STATE: R0/0: wncd: Username entry (testuser) joined with ssid (Guest-Profile) for device with MAC: a0ce.c8c3.a9b5 on channel (0)
2024/07/15 15:12:04.690726966 {wncd_x_R0-0}{1}: [aaa-attr-inf] [14709]: (info): [ Applied attribute :bsn-vlan-interface-name 0 "VLAN2024" ]
2024/07/15 15:12:04.691064276 {wncd_x_R0-0}{1}: [client-orch-state] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_L3_AUTH_IN_PROGRESS -> S_CO_RUN
嵌入式資料包捕獲分析
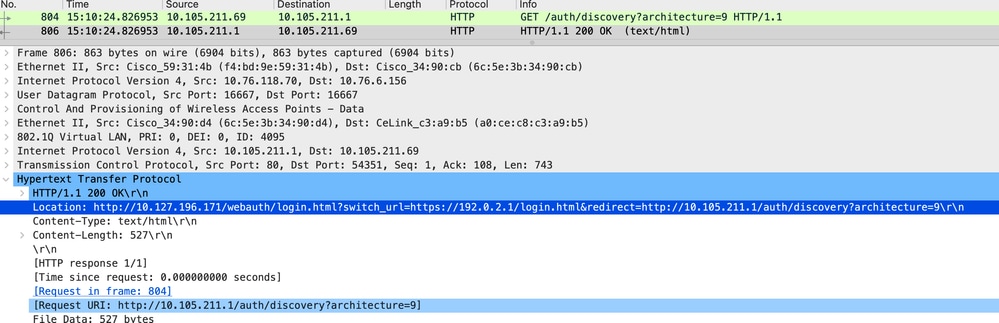 使用者端已重新導向到入口頁面
使用者端已重新導向到入口頁面
作業階段在收到重新導向URL後關閉。
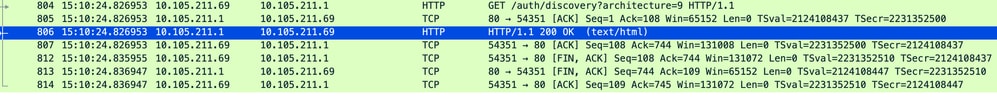 收到重新導向URL後,TCP作業階段關閉
收到重新導向URL後,TCP作業階段關閉
客戶端發起到重定向URL主機的TCP 3次握手,並傳送HTTP GET請求。
頁面載入後,登入憑證會提交到入口上,控制器會向radius伺服器傳送存取要求,以驗證使用者端。
身份驗證成功後,與Web伺服器的TCP會話將關閉,並且在控制器上,客戶端策略管理器狀態將轉換為RUN。
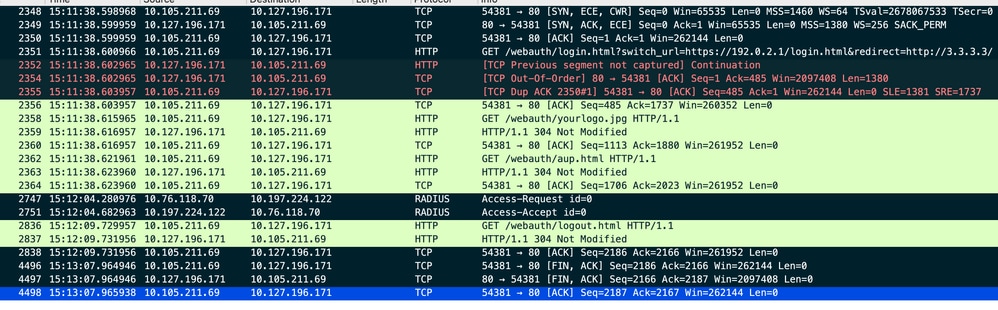 客戶端向門戶頁面傳送HTTP GET請求並成功完成身份驗證
客戶端向門戶頁面傳送HTTP GET請求並成功完成身份驗證
Radius存取要求封包
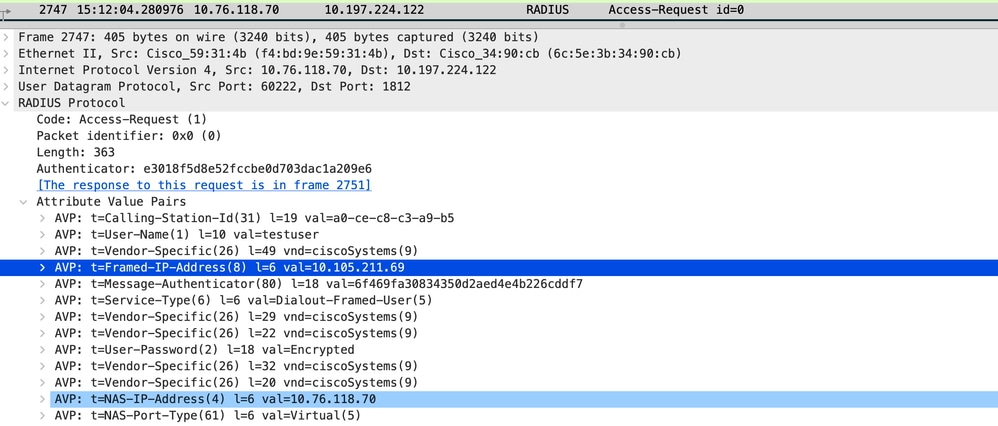 存取要求封包
存取要求封包
Radius存取接受封包
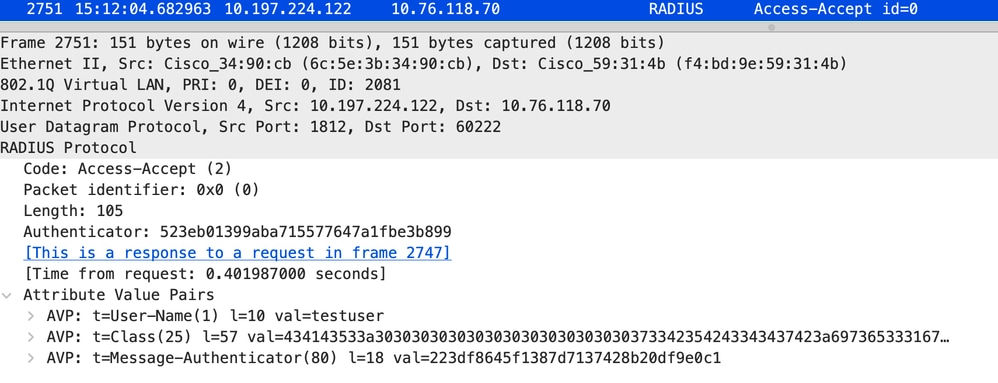 Access Accept資料包
Access Accept資料包
相關文章
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
29-Jul-2024
|
初始版本 |
由思科工程師貢獻
- Vinesh VeerarasuTechnical Consulting Engineer
 意見
意見