Catalyst交換器中的動態ARP檢查(DAI)和IP來源防護(IPSG)疑難排解
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本文說明動態ARP檢測(DAI)和IP源保護(IPSG)的工作原理,以及如何在Catalyst 9K交換機中驗證它們。
DHCP窺探和相關功能
在進入DAI和IPSG之前,您需要簡要討論DHCP監聽,這是DAI和IPSG的前提條件。
動態主機設定通訊協定(DHCP)是一種使用者端/伺服器通訊協定,可自動為網際網路通訊協定(IP)主機提供其IP位址以及其他相關組態資訊,例如子網路遮罩和預設閘道。RFC 2131和2132將DHCP定義為基於Bootstrap協定(BOOTP)的網際網路工程任務組(IETF)標準,BOOTP是DHCP共用許多實施詳細資訊的協定。DHCP允許主機從DHCP伺服器獲取所需的TCP/IP配置資訊。
DHCP監聽是一種安全功能,其作用類似於不可信主機和可信DHCP伺服器之間的防火牆。DHCP監聽功能執行以下活動:
- 驗證從不可信源接收的DHCP消息並過濾出無效消息。
- 對來自可信和不可信源的DHCP流量進行速率限制。
- 建立並維護DHCP監聽繫結資料庫,該資料庫包含有關具有租用IP地址的不可信主機的資訊。
- 利用DHCP監聽繫結資料庫來驗證來自不受信任主機的後續請求。
DAI是一項安全功能,用於驗證網路中的地址解析協定(ARP)資料包。DAI允許網路管理員擷取、記錄並丟棄具有無效MAC地址到IP地址繫結的ARP資料包。此功能可保護網路免受某些「中間人」攻擊。
IPSG是一項安全功能,它通過根據DHCP監聽繫結資料庫和手動配置的IP源繫結過濾流量,限制非路由第2層介面上的IP流量。如果主機嘗試使用其鄰居的IP地址,則可以使用IPSG來防止通訊攻擊。
沒有DHCP監聽的場景

1.在此圖中,您可以看到多個客戶端希望從連線到核心交換機的DHCP伺服器接收IP地址。
2.但是,惡意/惡意DHCP伺服器連線到可以接收DHCP的接入層交換機之一,它發現並傳送DHCP提供的速度比實際的DHCP伺服器更快。
3.攻擊者可以設定提議消息中的網關地址,使其可以接收來自客戶端的所有流量,從而損害通訊的機密性。
4.這被稱為「中間人」。
使用DHCP窺探的案例

1.通過在接入交換機中啟用DHCP監聽,將交換機配置為監聽DHCP流量,並停止在不可信埠上接收的任何惡意DHCP資料包。
2.一旦在交換機中啟用DHCP監聽,所有介面都會自動變為不可信。
3.使連線到終端裝置的埠不受信任,並將連線到正版DHCP伺服器的埠配置為受信任。
4.不可信介面將阻止DHCP提供消息。DHCP提供消息僅在受信任埠上被允許。
5.您可以限制終端主機每秒可以傳送到不受信任介面的DHCP發現資料包的數量。這是一種安全機制,可以保護DHCP伺服器免受傳入的DHCP發現數量異常高的影響,從而可以在短時間內耗盡地址池。
本節介紹如何在交換網路中配置DHCP監聽:
拓撲:

接入交換機的介面Gi1/0/1-4連線到DHCP客戶端。您可以啟用這些客戶端從正版DHCP伺服器接收IP地址,並通過利用DHCP監聽功能保護它們免受惡意DHCP伺服器的攻擊。
請參閱以下步驟瞭解如何實現此目的:
步驟1.在接入交換機的VLAN下全域性啟用DHCP監聽:
ip dhcp snooping
ip dhcp snooping vlan 10,20,30
步驟2.在接收來自正版DHCP伺服器的DHCP提供的接入交換機的所有介面上配置DHCP監聽信任。此類介面的數量取決於DHCP伺服器的網路設計和位置。這些介面正流向正版DHCP伺服器。
Access Switch:
interface TenGigabitEthernet1/0/2
switchport mode trunk
ip dhcp snooping trust
步驟3.全域性配置DHCP監聽後,交換機中的所有埠都會自動變為不可信(手動信任的連線埠除外,如前所示)。 但是,您可以配置終端主機每秒可以傳送到不受信任介面的DHCP發現資料包數。
這是一種安全機制,可保護DHCP伺服器免受異常大量的傳入DHCP發現的影響,從而可在短時間內耗盡地址池。
interface range Gi1/0/1-5
ip dhcp snooping limit rate 10
驗證:
Access_SW#show ip dhcp snooping
Switch DHCP snooping is enabled
Switch DHCP gleaning is disabled
DHCP snooping is configured on following VLANs:
10,20,30
DHCP snooping is operational on following VLANs:
10,20,30
DHCP snooping is configured on the following L3 Interfaces:
Insertion of option 82 is disabled
circuit-id default format: vlan-mod-port
remote-id: 00fc.ba9e.3980 (MAC)
Option 82 on untrusted port is not allowed
Verification of hwaddr field is enabled
Verification of giaddr field is enabled
DHCP snooping trust/rate is configured on the following Interfaces:
Interface Trusted Allow option Rate limit (pps)
----------------------- ------- ------------ ----------------
GigabitEthernet1/0/1 no no 10
Custom circuit-ids:
GigabitEthernet1/0/2 no no 10
Custom circuit-ids:
GigabitEthernet1/0/3 no no 10
Custom circuit-ids:
GigabitEthernet1/0/4 no no 10
Custom circuit-ids:
GigabitEthernet1/0/5 no no 10
Custom circuit-ids:
TenGigabitEthernet1/0/2 yes yes unlimited
Custom circuit-ids:

附註:如果您檢視此輸出,您會看到輸出中提到連線到惡意DHCP伺服器的Gi1/0/5為show ip dhcp snooping不可信。
因此,DHCP監聽將對這些埠執行所有檢查。
例如,這將導致此埠(Gi1/0/5)上的所有傳入DHCP提供被丟棄。
以下是DHCP監聽繫結表,顯示Gi1/0/1、Gi1/0/2、Gi1/0/3上3個客戶端的IP地址、MAC地址和介面:
Access_SW#show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
00:FC:BA:9E:39:82 10.10.10.2 62488 dhcp-snooping 10 GigabitEthernet1/0/1
00:FC:BA:9E:39:A6 10.10.20.2 62492 dhcp-snooping 20 GigabitEthernet1/0/2
00:FC:BA:9E:39:89 10.10.30.3 62492 dhcp-snooping 30 GigabitEthernet1/0/3
Total number of bindings: 3
出於演示目的ip dhcp snooping trust,配置會從接入交換機的Te1/0/2下移除。請檢視Switch:
Access_SW#sh cdp neigh
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone,
D - Remote, C - CVTA, M - Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
Dist_SW Ten 1/0/2 175 R S I C9300-48U Ten 1/1/3
Total cdp entries displayed : 1
Access_SW#show run int Te1/0/2
Building configuration...
Current configuration : 64 bytes
!
interface TenGigabitEthernet1/0/2
switchport mode trunk
*Apr 4 01:12:47.149: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca65
*Apr 4 01:14:07.161: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca65
*Apr 4 01:29:30.634: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca56
*Apr 4 01:30:03.286: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca46
- 您可以看到,接入交換機正在丟棄Te1/0/2上的傳入DHCP提供資料包,因為它不再受信任。
- 日誌中的MAC地址屬於VLAN 10、20和30的SVI,因為它們是從DHCP伺服器向這些客戶端傳送這些提供的地址。
ARP中毒
ARP通過將IP地址對映到MAC地址來提供第2層廣播域中的IP通訊。它是一種簡單的協定,但容易受到稱為ARP中毒的攻擊。
ARP中毒是一種攻擊,攻擊者通過網路傳送虛假的ARP應答資料包。
惡意使用者可以通過毒化連線到子網的系統的ARP快取並擷取用於子網中其他主機的流量來攻擊連線到第2層網路的主機、交換機和路由器
這是典型的中間人攻擊。
預防機制
動態ARP檢查(DAI)
動態ARP檢查是一項安全功能,用於驗證網路中的ARP資料包。它會攔截、記錄並丟棄具有無效IP到MAC地址繫結的ARP資料包。此功能可保護網路免受某些中間人攻擊。
動態ARP檢查可確保僅中繼有效的ARP請求和響應。交換機執行以下活動:
- 攔截不可信埠上的所有ARP請求和響應
- 在更新本地ARP快取或將資料包轉發到適當的目標之前,驗證這些截獲的資料包中每個資料包是否都具有有效的IP到MAC地址繫結
- 丟棄無效ARP資料包
動態ARP檢測根據儲存在可信資料庫(DHCP監聽繫結資料庫)中的有效IP到MAC地址繫結確定ARP資料包的有效性。
如果在VLAN和交換機上啟用了DHCP監聽,則此資料庫由DHCP監聽構建。如果在受信任的介面上收到ARP資料包,交換機將轉發該資料包,而不進行任何檢查。
在不受信任的介面上,交換機只有在資料包有效時才轉發該資料包。
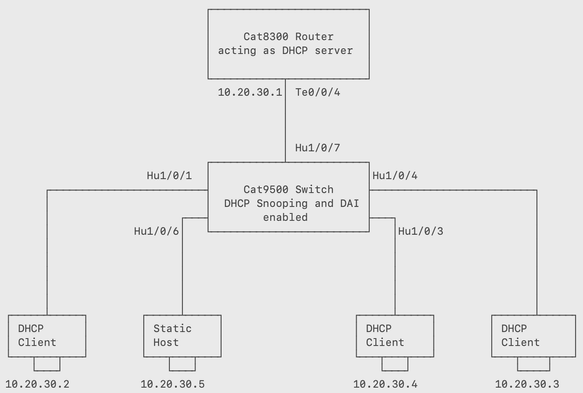
此圖顯示連線到四台主機的Cat9500交換機,其中3台主機是DHCP客戶端,1台主機具有靜態IP地址(10.20.30.5)。 DHCP伺服器是配置有DHCP池的Cat8300系列路由器。
上面的拓撲用於演示DAI如何檢測介面上的無效ARP請求,並保護網路免受惡意攻擊者的攻擊。
組態:
步驟1.在交換機中全域性配置DHCP監聽和DAI。
F241.24.02-9500-1#sh run | i dhcp
ip dhcp snooping vlan 10
no ip dhcp snooping information option
ip dhcp snooping
F241.24.02-9500-1#sh run | i ip arp
ip arp inspection vlan 10
步驟2.將連線到DHCP伺服器的介面Hu1/0/7配置為受信任埠。這將允許DHCP提供輸入介面並隨後到達DHCP客戶端。
F241.24.02-9500-1#sh run int Hu1/0/7
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/7
switchport access vlan 10
ip dhcp snooping trust
end
步驟3.將連線到DHCP客戶端的埠配置為允許VLAN 10的接入埠。
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
end
步驟4.驗證DHCP使用者端是否已從DHCP伺服器以及Cat9500交換器中的DHCP窺探繫結表收到IP位址。
F241.24.02-9500-1#sh ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 85046 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 85065 dhcp-snooping 10 HundredGigE1/0/4
2C:4F:52:01:AA:CC 10.20.30.4 85085 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 3
您還可以檢查DHCP伺服器中的繫結。
DHCP_Server#show ip dhcp binding
Bindings from all pools not associated with VRF:
IP address Client-ID/ Lease expiration Type State Interface
Hardware address/
User name
10.20.30.2 0063.6973.636f.2d37. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
3837.322e.3564.3162.
2e37.6633.662d.4875.
312f.302f.31
10.20.30.3 0063.6973.636f.2d35. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
6337.312e.3064.6364.
2e65.6530.632d.5465.
312f.302f.35
10.20.30.4 0063.6973.636f.2d32. Apr 08 2024 07:05 AM Automatic Active TenGigabitEthernet0/0/4
6334.662e.3532.3031.
2e61.6163.632d.5465.
312f.302f.35
步驟 5:將連線到Hu1/0/6的主機的IP地址從10.20.30.5更改為10.20.30.2,並嘗試從該主機ping其它DHCP客戶端。
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.....
在Cat9500交換器上可以看到以下無效ARP記錄:
F241.24.02-9500-1#
*Apr 7 09:29:24.520: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:23 UTC Sun Apr 7 2024])
*Apr 7 09:29:26.520: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:25 UTC Sun Apr 7 2024])
*Apr 7 09:29:28.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:27 UTC Sun Apr 7 2024])
*Apr 7 09:29:30.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:29 UTC Sun Apr 7 2024])
*Apr 7 09:29:32.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:31 UTC Sun Apr 7 2024])
F241.24.02-9500-1#
*Apr 7 09:29:47.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:46 UTC Sun Apr 7 2024])
*Apr 7 09:29:49.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:48 UTC Sun Apr 7 2024])
*Apr 7 09:29:51.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:50 UTC Sun Apr 7 2024])
*Apr 7 09:29:53.522: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:52 UTC Sun Apr 7 2024])
*Apr 7 09:29:55.523: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:54 UTC Sun Apr 7 2024])
- 您可以看到,當您嘗試從Static_Host ping 10.20.30.3和10.20.30.4時,您做不到。
即使Static_Host嘗試欺騙合法的DHCP客戶端的IP地址,也無法這樣做,因為到達Hu1/0/6的任何ARP資料包都將由交換機進行檢查,並與DHCP監聽繫結表中存在的資料進行比較。 - Cat9500交換機的後續日誌確認從Static_Host傳送到DHCP客戶端的ARP請求被丟棄。
- Cat9500交換機通過引用DHCP監聽繫結資料庫實現這一點。
- 當ARP請求以源MAC-IP與DHCP監聽繫結資料庫中存在的值不匹配的方式進入Hu1/0/6時,交換機將丟棄ARP請求。
步驟6.驗證:
F241.24.02-9500-1#show ip arp inspection
Source Mac Validation : Disabled
Destination Mac Validation : Disabled
IP Address Validation : Disabled
Vlan Configuration Operation ACL Match Static ACL
---- ------------- --------- --------- ----------
10 Enabled Active DAI No
Vlan ACL Logging DHCP Logging Probe Logging
---- ----------- ------------ -------------
10 Deny Deny Off
Vlan Forwarded Dropped DHCP Drops ACL Drops
---- --------- ------- ---------- ---------
10 9 39 39 0
Vlan DHCP Permits ACL Permits Probe Permits Source MAC Failures
---- ------------ ----------- ------------- -------------------
10 6 3 0 0
Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data
---- ----------------- ---------------------- ---------------------
10 0 0 0
在此輸出中,您可以看到在Cat9500交換器的VLAN 10中DAI丟棄和允許的資料包數量。

附註:一個非常重要的情況可能是網路中分配了靜態IP地址(例如10.20.30.5)地址的合法主機?
雖然主機沒有嘗試偽裝任何內容,但它仍會與網路隔離,因為其MAC-IP繫結資料不在DHCP監聽繫結資料庫中。
這是因為靜態主機從未使用DHCP來接收IP地址,因為它是靜態分配的。
我們可以實施一些變通方案,為具有靜態IP地址的合法主機提供連線。
選項 1.
使用ip arp檢測信任配置連線到主機的介面。
F241.24.02-9500-1#sh run int HundredGigE 1/0/6
Building configuration...
Current configuration : 110 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
switchport mode access
ip arp inspection trust
end
Static_Host#ping 10.20.30.4
*Apr 7 18:44:45.299 JST: %SYS-5-CONFIG_I: Configured from console by admin on vty0 (192.168.1.5)
F241.24.02-9300-STACK#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
選項 2.
使用ARP Access-List允許靜態主機:
F241.24.02-9500-1#sh run | s arp access-list
arp access-list DAI
permit ip host 10.20.30.5 mac host 7035.0956.7ee4
F241.24.02-9500-1#sh run | i ip arp ins
ip arp inspection filter DAI vlan 10
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
選項 3.
為靜態主機配置繫結表條目。
F241.24.02-9500-1#sh run | i binding
ip source binding 7035.0956.7EE4 vlan 10 10.20.30.5 interface Hu1/0/6
F241.24.02-9500-1#show ip source binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 80640 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 80659 dhcp-snooping 10 HundredGigE1/0/4
70:35:09:56:7E:E4 10.20.30.5 infinite static 10 HundredGigE1/0/6
2C:4F:52:01:AA:CC 10.20.30.4 80679 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 4
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
DAI提供的其他選項:
F241.24.02-9500-1(config)#ip arp inspection validate ?
dst-mac Validate destination MAC address
ip Validate IP addresses
src-mac Validate source MAC address
若是src-mac,請根據ARP正文中的傳送方MAC地址檢查乙太網報頭中的源MAC地址。對ARP請求和響應執行此檢查。啟用時,具有不同MAC位址的封包會分類為無效且遭捨棄
若是dst-mac,請根據ARP正文中的目標MAC地址檢查乙太網報頭中的目標MAC地址。對ARP響應執行此檢查。啟用時,具有不同MAC位址的封包會分類為無效且遭捨棄。
對於IP,檢查ARP正文是否有無效和意外的IP地址。地址包括0.0.0.0、255.255.255.255和所有IP組播地址。在所有ARP請求和響應中檢查傳送方IP地址,僅在ARP響應中檢查目標IP地址。
您還可以設定ARP速率限制。預設情況下,不可信介面上的ARP流量限製為15 pps:
Switch(config)#interface Gigabitethernet<>
Switch(config-if)#ip arp inspection limit rate 10
IP來源防護
- IPSG是一項安全功能,它通過基於DHCP監聽繫結資料庫和手動配置的IP源繫結過濾流量,限制非路由第2層介面上的IP流量。
- 如果主機嘗試使用其鄰居的IP地址,則可以使用IPSG來防止通訊攻擊。
- 在不可信介面上啟用DHCP監聽時,可以啟用IPSG。在介面上啟用IPSG後,交換機將阻止在該介面上接收的所有IP流量,但DHCP監聽允許的DHCP資料包除外。
- 交換機在硬體中使用源IP查詢表將IP地址繫結到埠。對於IP和MAC過濾,使用源IP和源MAC查詢的組合。允許繫結表中具有源IP地址的IP流量,但拒絕所有其他流量。
- IP源繫結表具有通過DHCP監聽獲取或手動配置的繫結(靜態IP源繫結)。 此表中的條目具有IP地址、其關聯的MAC地址及其關聯的VLAN編號。僅當啟用IP源保護時,交換機才使用IP源繫結表。
- 您可以使用源IP地址過濾或通過源IP和MAC地址過濾來配置IPSG。
適用於靜態主機的IPSG
- 靜態主機的IPSG允許IPSG在沒有DHCP的情況下工作。靜態主機的IPSG依賴IP裝置跟蹤表條目來安裝埠ACL。交換機根據ARP請求或其他IP資料包建立靜態條目,以維護給定埠的有效主機清單。
參考資料:

Cat9500交換機連線到四台主機,其中3台主機是DHCP客戶端,1台主機具有靜態IP地址。DHCP伺服器是配置有DHCP池的Cat8300系列路由器。
您可以使用此拓撲來演示IPSG如何檢測和阻止來自MAC-IP繫結未出現在DHCP監聽繫結資料庫中的主機的流量。
設定:
步驟1.在Cat9500交換機中全域性配置DHCP監聽。
F241.24.02-9500-1#sh run | i dhcp
ip dhcp snooping vlan 10
no ip dhcp snooping information option
ip dhcp snooping
步驟2.將連線到DHCP伺服器的介面Te1/0/7配置為受信任埠。這允許DHCP提供輸入介面並隨後到達DHCP客戶端。
F241.24.02-9500-1#sh run int Hu1/0/7
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/7
switchport access vlan 10
ip dhcp snooping trust
end
步驟3.將連線到DHCP客戶端的埠配置為允許VLAN 10的接入埠。
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
end
步驟4.檢驗DHCP客戶端是否已從DHCP伺服器收到IP地址。
F241.24.02-9500-1#sh ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 85046 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 85065 dhcp-snooping 10 HundredGigE1/0/4
2C:4F:52:01:AA:CC 10.20.30.4 85085 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 3
F241.24.02-9500-1#show ip source binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 64764 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 64783 dhcp-snooping 10 HundredGigE1/0/4
2C:4F:52:01:AA:CC 10.20.30.4 64803 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 3
DHCP_Server#show ip dhcp binding
Bindings from all pools not associated with VRF:
IP address Client-ID/ Lease expiration Type State Interface
Hardware address/
User name
10.20.30.2 0063.6973.636f.2d37. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
3837.322e.3564.3162.
2e37.6633.662d.4875.
312f.302f.31
10.20.30.3 0063.6973.636f.2d35. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
6337.312e.3064.6364.
2e65.6530.632d.5465.
312f.302f.35
10.20.30.4 0063.6973.636f.2d32. Apr 08 2024 07:05 AM Automatic Active TenGigabitEthernet0/0/4
6334.662e.3532.3031.
2e61.6163.632d.5465.
312f.302f.35
步驟5.在連線到所有終端主機(3個DHCP客戶端和1個具有靜態IP地址的主機)的介面下配置IPSG。
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 79 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
ip verify source
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 79 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
ip verify source
end
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 79 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
ip verify source
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 103 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
ip verify source
end
驗證:
F241.24.02-9500-1#show ip verify source
Interface Filter-type Filter-mode IP-address Mac-address Vlan
--------- ----------- ----------- --------------- ----------------- ----
Hu1/0/1 ip active 10.20.30.2 10
Hu1/0/3 ip active 10.20.30.4 10
Hu1/0/4 ip active 10.20.30.3 10
Hu1/0/6 ip active deny-all 10
從該輸出中,您可以看到Hu1/0/6的IP Address欄位被設定為deny-all,因為DHCP監聽繫結表中沒有與此介面對應的MAC-IP繫結。
步驟6.嘗試從Static_Host對IP地址為10.20.30.2、10.20.30.3和10.20.30.4的DHCP客戶端執行ping操作。
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.....
F241.24.02-9500-1(config)# ip source binding <mac-address-of-static-host> vlan 10 10.20.30.5 interface Hu1/0/6
F241.24.02-9500-1#show run int Hu1/0/6
*Apr 7 15:13:48.449: %SYS-5-CONFIG_I: Configured from console by console
F241.24.02-9500-1#show ip verify source
Interface Filter-type Filter-mode IP-address Mac-address Vlan
--------- ----------- ----------- --------------- ----------------- ----
Hu1/0/1 ip active 10.20.30.2 10
Hu1/0/3 ip active 10.20.30.4 10
Hu1/0/4 ip active 10.20.30.3 10
Hu1/0/6 ip active 10.20.30.5 10
F241.24.02-9500-1#show ip source binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 62482 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 62501 dhcp-snooping 10 HundredGigE1/0/4
70:35:09:56:7E:E4 10.20.30.5 infinite static 10 HundredGigE1/0/6
2C:4F:52:01:AA:CC 10.20.30.4 62521 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 4
Verification:
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
IPSG提供的其它選項:
預設情況下,IPSG僅基於IP地址過濾不可信埠上的傳入流量。
如果要根據IP和MAC地址執行過濾,請執行以下步驟。
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 89 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
ip verify source mac-check
end
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 89 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
ip verify source mac-check
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 89 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
ip verify source mac-check
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 113 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
switchport mode access
ip verify source mac-check
end
F241.24.02-9500-1#show ip verify source
Interface Filter-type Filter-mode IP-address Mac-address Vlan
--------- ----------- ----------- --------------- ----------------- ----
Hu1/0/1 ip-mac active 10.20.30.2 78:72:5D:1B:7F:3F 10
Hu1/0/3 ip-mac active 10.20.30.4 2C:4F:52:01:AA:CC 10
Hu1/0/4 ip-mac active 10.20.30.3 5C:71:0D:CD:EE:0C 10
Hu1/0/6 ip-mac active deny-all deny-all 10
在此輸出中,您可以看到Filter-type為ip-mac。因此,交換器現在會根據來源IP和MAC位址,過濾這些介面上的傳入封包。
DAI和IPSG故障排除提示
- 在排查DAI和IPSG相關問題時首先要檢查的是驗證DHCP監聽繫結表是否已正確填充。
- 啟用這些功能之前,請使用靜態IP地址處理終端。如果不想讓這些裝置失去可達性,請配置靜態繫結或採用前面提到的方法之一使交換機信任這些端點。
- 在尚未啟用DHCP監聽且客戶端已經從DHCP伺服器接收IP的環境中配置DAI或IPSG時,請先啟用DHCP監聽,並執行以下兩個步驟之一:
- 退回客戶端連線的介面,以便其續訂租約。
- 等待客戶端自動續訂租約。這可能需要花費更多的時間,但省去了手動退回所有客戶端連線的埠的麻煩。
- 執行上述兩個步驟之一將觸發新的DORA事務。交換機將嗅探DORA資料包並更新繫結表。如果未執行此操作,並且在配置DHCP監聽後立即啟用DAI或IPSG,則可能會遇到網路中所有DHCP客戶端都失去與網路的連線的問題。
- 在配置DAI或IPSG的環境中排除連線問題時,請確保DHCP監聽繫結表未損壞。確保交換機可以訪問儲存此表的資料結構。
- 某些情況下,繫結表可能會匯出到介質中,該介質在交換機啟動後需要一段時間才能初始化,或者由於某種原因導致交換機無法訪問。您可能會注意到此類情形中的連線問題。
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
05-Aug-2024
|
初始版本 |

 意見
意見