在AWS中使用多TxQs提高Catalyst 8000V的吞吐量
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本文檔介紹如何在AWS環境中部署的Catalyst 8000V上啟用和利用多TXQ以提高吞吐量效能。
背景資訊
多個隊列的存在簡化並加速了將傳入和傳出資料包對映到特定vCPU的過程。在Catalyst 8000V上利用多TXQ可跨分配的可用資料平面核心實現有效的核心利用率,從而提高吞吐量效能。本文簡要概述多TXQ的工作原理、配置方式、顯示自治和SD-WAN Catalyst 8000V部署的CLI配置示例,並檢視故障排除命令以幫助發現效能瓶頸。
Catalyst 8000V不使用多TxQs時的行為
在17.18軟體發行版之前,進入Catalyst 8000V的資料包會被分配到所有vCPU(資料包處理核心),與資料流無關。PP完成資料包處理後,流順序將恢復為通過介面傳送。
將封包放入傳輸佇列(TxQ)之前,Catalyst 8000V會為每個介面建立一個TxQ。因此,如果只有一個可用的輸出介面,則多個串流會進入一個TxQ。
如果只有一個可用的介面,Catalyst 8000V無法利用此多TxQ過程。這會導致吞吐量效能瓶頸和可用資料平面核心之間的負載分佈不均。如果只有一個輸出介面用於從C8000V例項傳輸資料,則只有一個TxQ可用於傳輸網路流量,並且可能導致資料包因單個隊列填充速度較快而丟棄。
如需參考,您可以在圖1中找到在AWS中部署的Catalyst 8000V的單一TxQ架構模型。
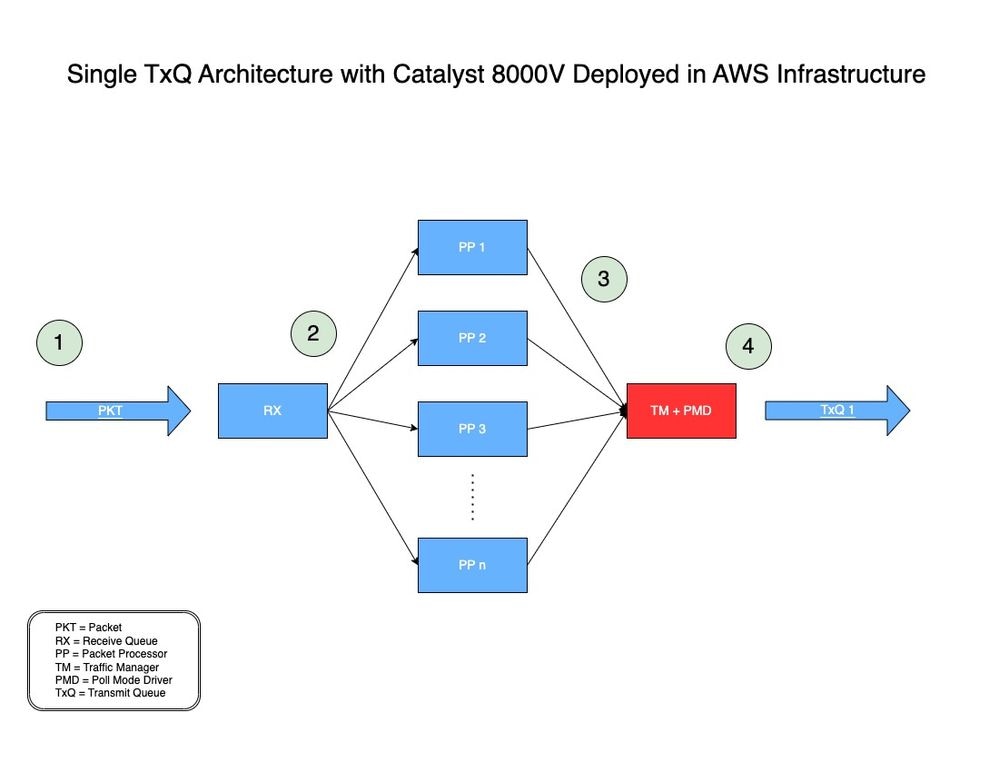
圖 1:在AWS中部署的Catalyst 8000V的單一TxQ架構模型。
-
- 網路資料包(PKT)通過VPC並在C8000V的輸入介面上接收。
- PKT被置於接收隊列(RX)上,然後被轉發到由演算法決定的分組處理器(PP)引擎。
- 封包處理器(PP)處理封包後,會將封包傳送到流量管理員(TM)。
- 在TM處理結束時,一個核心負責將資料包放入一個可用TxQ中,然後將該TxQ轉發到Catalyst 8000V的出口介面。
什麼是AWS基礎設施中的多業務交叉隊列
AWS ENA提供多個傳輸隊列(多TxQ)以減少內部開銷並提高可擴充性。多個隊列的存在簡化並加速了將傳入和傳出資料包對映到特定vCPU的過程。AWS和DPDK網路參考模型基於流,其中每個vCPU處理一個流並將來自該流的資料包傳送到指定的傳輸隊列(TxQ)。每個vCPU的RX/TX隊列對基於流的模型是有效的。
因為Catalyst 8000V不基於流,所以語句「每個vCPU的RX/TX隊列對」不適用於Catalyst 8000V。
在這種情況下,RX/TX隊列不是每個vCPU,而是每個介面。RX/TX隊列充當應用程式(Catalyst 8000V)和AWS基礎設施/硬體之間的介面,用於傳送資料/網路流量。AWS控制每個介面在每個例項上可用的RX/TX隊列的數量和速度。
Catalyst 8000V必須具有多個介面才能建立多個TxQ。為了保持流順序,使多個流從介面流出(在Catalyst 8000V啟用此流程後的多個TxQ後),Catalyst 8000V將基於5元組的流雜湊以選擇適當的TxQ。通過使用環回介面或輔助IP地址,使用者可以使用連線到例項的同一物理NIC在Catalyst 8000V上建立多個介面。
在圖2中,您可以找到在AWS中使用帶Catalyst 8000V的多重TxQ架構處理資料包的方式。
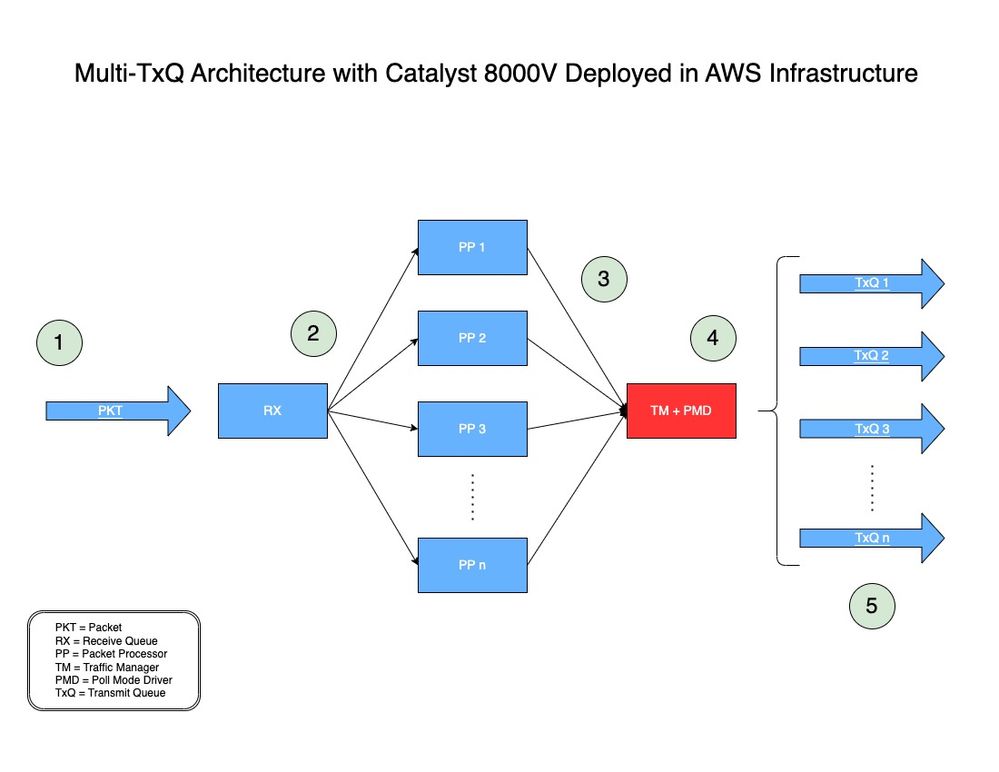
圖2:在AWS中部署的Catalyst 8000V的多TxQ架構模型。
-
- 網路資料包(PKT)通過VPC並在C8000V的輸入介面上接收。
- PKT被置於接收隊列(RX)上,然後被轉發到由演算法決定的分組處理器(PP)引擎。
- 封包處理器(PP)處理封包後,會將封包傳送到流量管理員(TM)。
- 在TM處理結束時,在將資料包放入傳輸隊列(TxQ)之前,TM會檢視資料包報頭並對資料包進行雜湊(下一節將對此進行說明)。 另一個元件,即輪詢模式驅動程式(PMD),用於配置例項支援的TXQ數量。一個核心專用於TM + PMD功能,該功能對分配的TxQ進行雜湊和資料包傳送。
- TxQ基於五個元組進行雜湊和模數提取,該元組具有例項支援的TxQ數。封包會被放置到選取的TxQ上,並轉送到Catalyst 8000V的出口介面。
流量如何雜湊到多個TxQ
如圖2的步驟4所示,在TM處理結束時,在將資料包放入TxQ之前,TM會檢視資料包報頭並提取5個元組(目的地址、源地址、協定、目標埠和源埠),然後將資料包雜湊到TxQ。
TxQ基於五個元組進行雜湊和模數提取,該元組具有例項支援的TxQ數。
支援多TxQs的Catalyst 8000V軟體版本
相同例項系列型別的AWS EC2例項都支援不同數量的TXQ,具體取決於例項大小。C8000V開始支援從IOS® XE 17.7開始的多個TxQ。
從IOS® XE 17.7開始,C8000V在C5n.9xlarge上支援多個TxQ ,最多可有8個TXQ。
從IOS® XE 17.9開始,C8000V支援C5n.18xlarge例項大小,該大小最多可以有12個TXQ(比C5n.9xlarge多50%)。
雖然IOS® XE 17.7支援多TxQ,但強烈建議使用IOS® XE 17.9來實現軟體生命週期和更高吞吐量效能以及12 TxQ支援。
如何設計IP編址方案以計算雜湊
若要在所有可用的TxQ之間均勻雜湊流量,在Catalyst 8000V終止IPsec/GRE通道時,需要使用特殊的IP位址。
有公共指令碼可用於生成這些特殊的IP地址,用於配置負責終止這些隧道的Catalyst 8000V介面。本節提供有關如何下載和使用指令碼來設計即使多TxQ雜湊所需的IP地址的說明。
如果Catalyst 8000V正在處理TCP/UDP等明文流量,則不需要特殊的IP編址方案。
可以在以下位置找到原始說明:https://github.com/CiscoDevNet/python-c8000v-aws-multitx-queues/
附註:對於運行17.18或更高版本的Catalyst 8000V,資料包的分配方式不同。因此,需要使用不同的雜湊演算法。
必要條件
- 必須具有能夠運行Python指令碼的Linux/MacOS或Windows電腦。
- 驗證Python版本是否為3.8.9或更高版本;使用「python3 —version」檢查Python版本
- 如果尚未安裝,請安裝PIP。如果不是,請運行:
- curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
- python3 get-pip.py
您可以使用命令「python3 —version」檢查電腦使用的Python版本。
user@computer ~ % python3 --version
Python 3.9.6
Python版本經驗證且運行後(版本等於或高於3.8.9),安裝最新版本的PIP。
user@computer ~ % curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2570k 100 2570k 0 0 6082k 0 --:--:-- --:--:-- --:--:-- 6135k
user@computer ~ % python3 get-pip.py
Defaulting to user installation because normal site-packages is not writeable
Collecting pip
Downloading pip-23.3.1-py3-none-any.whl.metadata (3.5 kB)
Downloading pip-23.3.1-py3-none-any.whl (2.1 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 2.1/2.1 MB 7.4 MB/s eta 0:00:00
Installing collected packages: pip
WARNING: The scripts pip, pip3 and pip3.9 are installed in '/Users/name/Library/Python/3.9/bin' which is not on PATH.
Consider adding this directory to PATH or, if you prefer to suppress this warning, use --no-warn-script-location.
Successfully installed pip-23.3.1
[notice] A new release of pip is available: 21.2.4 -> 23.3.1
[notice] To update, run: /Applications/Xcode.app/Contents/Developer/usr/bin/python3 -m pip install --upgrade pip
建立虛擬環境
安裝先決條件後,建立虛擬環境並下載用於生成多TxQ唯一IP地址方案的IP地址雜湊指令碼。
命令摘要:
- python3 -m venv c8kv-hash
- cd c8kv-hash
- source bin/activate
- git克隆https://github.com/CiscoDevNet/python-c8000v-aws-multitx-queues/
- cd c8kv-aws-pmd-hash
- python3 -m pip安裝 — 升級pip
- pip install -r requirements.txt
Python中的虛擬環境用於建立不影響其他專案或依賴項的隔離工作區。使用以下命令建立虛擬環境「c8kv-hash」:
user@computer Desktop % python3 -m venv c8kv-hash在虛擬環境中導航到「c8kv-hash」資料夾(之前建立)。
user@computer Desktop % cd c8kv-hash啟用虛擬環境。
user@computer c8kv-hash % source bin/activate克隆具有Multi-TxQ雜湊python指令碼的儲存庫。
(c8kv-hash) user@computer c8kv-hash % git clone https://github.com/CiscoDevNet/python-c8000v-aws-multitx-queues.git
Cloning into 'c8kv-aws-pmd-hash'...
remote: Enumerating objects: 82, done.
remote: Counting objects: 100% (82/82), done.
remote: Compressing objects: 100% (59/59), done.
remote: Total 82 (delta 34), reused 57 (delta 19), pack-reused 0
Receiving objects: 100% (82/82), 13.01 KiB | 2.60 MiB/s, done.
Resolving deltas: 100% (34/34), done.
在克隆儲存庫後,導航到「c8kv-aws-pmd-hash」資料夾。由於它位於建立的虛擬環境中,因此請安裝最新版本的PIP。
(c8kv-hash) user@computer c8kv-hash % cd c8kv-aws-pmd-hash
(c8kv-hash) user@computer c8kv-aws-pmd-hash % python3 -m pip install --upgrade pip
Requirement already satisfied: pip in /Users/name/Desktop/c8kv-hash/lib/python3.9/site-packages (21.2.4)
Collecting pip
Downloading pip-23.3.1-py3-none-any.whl (2.1 MB)
|████████████████████████████████| 2.1 MB 2.7 MB/s
Installing collected packages: pip
Attempting uninstall: pip
Found existing installation: pip 21.2.4
Uninstalling pip-21.2.4:
Successfully uninstalled pip-21.2.4
Successfully installed pip-23.3.1
升級PIP後,安裝資料夾中requirements.txt檔案中的依賴項。
(c8kv-hash) user@computer c8kv-aws-pmd-hash % pip install -r requirements.txt
Collecting crc32c==2.3 (from -r requirements.txt (line 1))
Downloading crc32c-2.3-cp39-cp39-macosx_11_0_arm64.whl (27 kB)
Installing collected packages: crc32c
Successfully installed crc32c-2.3虛擬環境現已更新,可用於生成多TxQ的IP地址方案。
使用Python雜湊索引指令碼計算17.7和17.8版本的IP地址方案(棄用)

附註:7.7和17.8雜湊指令碼即將被棄用。強烈建議使用17.9雜湊指令碼
命令摘要:
- python3 c8kv_multitxq_hash.py —old_crc 1 —dest_network 192.168.1.0/24 —src_network 192.168.2.0/24 --unique_hash 1
「 — old_crc 1」生成基於17.7和17.8發行版的雜湊索引(模數為8),以匹配支援的PMD TXQ(請勿修改)
「 — dest_network」定義目標網路地址子網(根據您的網路IP地址方案進行修改)
「 — src_network」定義源網路地址子網(根據您的網路IP地址方案進行修改)
「 — unique_hash 1」生成一組唯一雜湊IP地址(8對,用於8個TXQ)。可以修改此項。
(c8kv-hash) user@computer c8kv-aws-pmd-hash % python3 c8kv_multitxq_hash.py --old_crc 1 --dest_network 192.168.1.0/24 --src_network 192.168.2.0/24 --unique_hash 1
Dest: Src: Prot dstport srcport Hash: Rev-hash:
192.168.1.0 192.168.2.0 2 5
192.168.1.0 192.168.2.1 2 7
192.168.1.0 192.168.2.2 2 1
192.168.1.0 192.168.2.3 2 3
192.168.1.0 192.168.2.4 2 5
192.168.1.0 192.168.2.5 2 7
192.168.1.0 192.168.2.6 2 1
192.168.1.0 192.168.2.7 2 3
192.168.1.0 192.168.2.8 2 5
192.168.1.0 192.168.2.9 2 7
192.168.1.0 192.168.2.10 2 1
.
. ### trimmed output ###
.
192.168.1.255 192.168.2.247 5 2
192.168.1.255 192.168.2.248 5 4
192.168.1.255 192.168.2.249 5 6
192.168.1.255 192.168.2.250 5 0
192.168.1.255 192.168.2.251 5 2
192.168.1.255 192.168.2.252 5 4
192.168.1.255 192.168.2.253 5 6
192.168.1.255 192.168.2.254 5 0
192.168.1.255 192.168.2.255 5 2
Unique hash:
------ Tunnels set 0 ---------
192.168.1.37<===>192.168.2.37<===>0
192.168.1.129<===>192.168.2.129<===>1
192.168.1.36<===>192.168.2.36<===>2
192.168.1.128<===>192.168.2.128<===>3
192.168.1.39<===>192.168.2.39<===>4
192.168.1.131<===>192.168.2.131<===>5
192.168.1.38<===>192.168.2.38<===>6
192.168.1.130<===>192.168.2.130<===>7
使用Python雜湊索引指令碼計算IP地址方案,用於17.9及更高版本
命令摘要:
- python3 c8kv_multitxq_hash.py —dest_network 192.168.1.0/24 —src_network 192.168.2.0/24 —prot udp —src_port 12346 —dst_port 12346 —unique_hash 1
請注意,在IOS® XE 17.9版及更高版本中,指令碼使用模12而不帶 — old_crc選項,與支援的PMD TXQ匹配。
「 — dest_network」定義目標網路地址子網(根據您的網路IP地址方案進行修改)
「 — src_network」定義源網路地址子網(根據您的網路IP地址方案進行修改)
「 — 埠udp」定義使用的協定。使用者可以指定協定引數為「gre」、「tcp」或「udp」或任何十進位制值(可選)
「 — src_port」定義使用的源埠(可選)
「 — dst_port」定義使用的目標埠(可選)
「 — unique_hash 1」生成一組唯一雜湊IP地址(12對,用於12個TXQ)。可以修改此項。
(c8kv-hash) user@computer c8kv-aws-pmd-hash % python3 c8kv_multitxq_hash.py --dest_network 192.168.1.0/24 --src_network 192.168.2.0/24 --prot udp --src_port 12346 --dst_port 12346 --unique_hash 1
Dest: Src: Prot dstport srcport Hash: Rev-hash:
192.168.1.0 192.168.2.0 17 12346 12346 ==> 4 4 <-- Unique Hash Value
192.168.1.0 192.168.2.1 17 12346 12346 ==> 4 4
192.168.1.0 192.168.2.2 17 12346 12346 ==> 8 8 <-- Unique Hash Value
192.168.1.0 192.168.2.3 17 12346 12346 ==> 0 0 <-- Unique Hash Value
192.168.1.0 192.168.2.4 17 12346 12346 ==> 0 0
192.168.1.0 192.168.2.5 17 12346 12346 ==> 0 0
192.168.1.0 192.168.2.6 17 12346 12346 ==> 4 4
192.168.1.0 192.168.2.7 17 12346 12346 ==> 0 0
192.168.1.0 192.168.2.8 17 12346 12346 ==> 9 9 <-- Unique Hash Value
192.168.1.0 192.168.2.9 17 12346 12346 ==> 9 9
192.168.1.0 192.168.2.10 17 12346 12346 ==> 9 9
192.168.1.0 192.168.2.11 17 12346 12346 ==> 1 1 <-- Unique Hash Value
192.168.1.0 192.168.2.12 17 12346 12346 ==> 1 1
.
. ### trimmed output ###
.
192.168.1.255 192.168.2.250 17 12346 12346 ==> 1 1
192.168.1.255 192.168.2.251 17 12346 12346 ==> 1 1
192.168.1.255 192.168.2.252 17 12346 12346 ==> 9 9
192.168.1.255 192.168.2.253 17 12346 12346 ==> 1 1
192.168.1.255 192.168.2.254 17 12346 12346 ==> 5 5 <-- Unique Hash Value
192.168.1.255 192.168.2.255 17 12346 12346 ==> 9 9
Unique hash:
------ Tunnels set 0 ---------
192.168.1.38 <===> 192.168.2.38<===>0
192.168.1.37 <===> 192.168.2.37<===>1
192.168.1.53 <===> 192.168.2.53<===>2
192.168.1.39 <===> 192.168.2.39<===>3
192.168.1.48 <===> 192.168.2.48<===>4
192.168.1.58 <===> 192.168.2.58<===>5
192.168.1.42 <===> 192.168.2.42<===>6
192.168.1.46 <===> 192.168.2.46<===>7
192.168.1.40 <===> 192.168.2.40<===>8
192.168.1.43 <===> 192.168.2.43<===>9
192.168.1.36 <===> 192.168.2.36<===>10
192.168.1.56 <===> 192.168.2.56<===>11
使用8個帶有環回介面的TXQ的拓撲和CLI配置示例

圖 3:使用環回介面使用八個TxQ的拓撲示例。
這是「c8kv-ut」的CLI配置示例(圖3),使用上一節中計算出的雜湊IP地址(192.168.1.X)建立八條帶環回介面的IPsec隧道。
另一個路由器端點(c8kv-peer)將應用類似的配置,其餘八個計算得到的雜湊IP地址(192.168.2.X)。
ip cef load-sharing algorithm include-ports source destination 00ABC123
crypto keyring tunnel0
local-address Loopback0
pre-shared-key address 192.168.2.37 key cisco
crypto keyring tunnel1
local-address Loopback1
pre-shared-key address 192.168.2.129 key cisco
crypto keyring tunnel2
local-address Loopback2
pre-shared-key address 192.168.2.36 key cisco
crypto keyring tunnel3
local-address Loopback3
pre-shared-key address 192.168.2.128 key cisco
crypto keyring tunnel4
local-address Loopback4
pre-shared-key address 192.168.2.39 key cisco
crypto keyring tunnel5
local-address Loopback5
pre-shared-key address 192.168.2.131 key cisco
crypto keyring tunnel6
local-address Loopback6
pre-shared-key address 192.168.2.38 key cisco
crypto keyring tunnel7
local-address Loopback7
pre-shared-key address 192.168.2.130 key cisco
crypto isakmp policy 200
encryption aes
hash sha
authentication pre-share
group 16
lifetime 28800
crypto isakmp profile isakmp-tunnel0
keyring tunnel0
match identity address 0.0.0.0
local-address Loopback0
crypto isakmp profile isakmp-tunnel1
keyring tunnel1
match identity address 0.0.0.0
local-address Loopback1
crypto isakmp profile isakmp-tunnel2
keyring tunnel2
match identity address 0.0.0.0
local-address Loopback2
crypto isakmp profile isakmp-tunnel3
keyring tunnel3
match identity address 0.0.0.0
local-address Loopback3
crypto isakmp profile isakmp-tunnel4
keyring tunnel4
match identity address 0.0.0.0
local-address Loopback4
crypto isakmp profile isakmp-tunnel5
keyring tunnel5
match identity address 0.0.0.0
local-address Loopback5
crypto isakmp profile isakmp-tunnel6
keyring tunnel6
match identity address 0.0.0.0
local-address Loopback6
crypto isakmp profile isakmp-tunnel7
keyring tunnel7
match identity address 0.0.0.0
local-address Loopback7
crypto ipsec transform-set ipsec-prop-vpn-tunnel esp-gcm 256
mode tunnel
crypto ipsec df-bit clear
crypto ipsec profile ipsec-vpn-tunnel
set transform-set ipsec-prop-vpn-tunnel
set pfs group16
interface Loopback0
ip address 192.168.1.37 255.255.255.255
!
interface Loopback1
ip address 192.168.1.129 255.255.255.255
!
interface Loopback2
ip address 192.168.1.36 255.255.255.255
!
interface Loopback3
ip address 192.168.1.128 255.255.255.255
!
interface Loopback4
ip address 192.168.1.39 255.255.255.255
!
interface Loopback5
ip address 192.168.1.131 255.255.255.255
!
interface Loopback6
ip address 192.168.1.38 255.255.255.255
!
interface Loopback7
ip address 192.168.1.130 255.255.255.255
!
interface Tunnel0
ip address 10.101.100.101 255.255.255.0
load-interval 30
tunnel source Loopback0
tunnel mode ipsec ipv4
tunnel destination 192.168.2.37
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel1
ip address 10.101.101.101 255.255.255.0
load-interval 30
tunnel source Loopback1
tunnel mode ipsec ipv4
tunnel destination 192.168.2.129
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel2
ip address 10.101.102.101 255.255.255.0
load-interval 30
tunnel source Loopback2
tunnel mode ipsec ipv4
tunnel destination 192.168.2.36
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel3
ip address 10.101.103.101 255.255.255.0
load-interval 30
tunnel source Loopback3
tunnel mode ipsec ipv4
tunnel destination 192.168.2.128
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel4
ip address 10.101.104.101 255.255.255.0
load-interval 30
tunnel source Loopback4
tunnel mode ipsec ipv4
tunnel destination 192.168.2.39
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel5
ip address 10.101.105.101 255.255.255.0
load-interval 30
tunnel source Loopback5
tunnel mode ipsec ipv4
tunnel destination 192.168.2.131
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel6
ip address 10.101.106.101 255.255.255.0
load-interval 30
tunnel source Loopback6
tunnel mode ipsec ipv4
tunnel destination 192.168.2.38
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel7
ip address 10.101.107.101 255.255.255.0
load-interval 30
tunnel source Loopback7
tunnel mode ipsec ipv4
tunnel destination 192.168.2.130
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface GigabitEthernet2
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
! ### IP route from servers to c8kv-uut
ip route 10.1.0.0 255.255.0.0 GigabitEthernet2 10.0.1.10
! ### IP routes from c8kv-uut to clients on c8kv-peer side, routes are evenly distributed to all 8 TXQ’s
ip route 10.10.0.0 255.255.0.0 Tunnel0
ip route 10.10.0.0 255.255.0.0 Tunnel1
ip route 10.10.0.0 255.255.0.0 Tunnel2
ip route 10.10.0.0 255.255.0.0 Tunnel3
ip route 10.10.0.0 255.255.0.0 Tunnel4
ip route 10.10.0.0 255.255.0.0 Tunnel5
ip route 10.10.0.0 255.255.0.0 Tunnel6
ip route 10.10.0.0 255.255.0.0 Tunnel7
! ### IP route from c8kv-uut Loopback int tunnel endpoint to c8kv-peer Loopback int tunnel endpoints
ip route 192.168.2.0 255.255.255.0 GigabitEthernet3 10.0.2.30 使用帶環回介面的12個TXQ的拓撲和CLI配置示例

圖4.使用環回介面的十二個TxQ的拓撲示例。
這是「c8kv-ut」(圖4)的CLI配置示例,使用上一節中計算出的雜湊IP地址(192.168.1.X)建立具有環回介面的12個IPsec隧道。
另一個路由器端點(c8kv-peer)將應用類似的配置,其餘八個計算得到的雜湊IP地址(192.168.2.X)。
ip cef load-sharing algorithm include-ports source destination 00ABC123
crypto keyring tunnel0
local-address Loopback0
pre-shared-key address 192.168.2.38 key cisco
crypto keyring tunnel1
local-address Loopback1
pre-shared-key address 192.168.2.37 key cisco
crypto keyring tunnel2
local-address Loopback2
pre-shared-key address 192.168.2.53 key cisco
crypto keyring tunnel3
local-address Loopback3
pre-shared-key address 192.168.2.39 key cisco
crypto keyring tunnel4
local-address Loopback4
pre-shared-key address 192.168.2.48 key cisco
crypto keyring tunnel5
local-address Loopback5
pre-shared-key address 192.168.2.58 key cisco
crypto keyring tunnel6
local-address Loopback6
pre-shared-key address 192.168.2.42 key cisco
crypto keyring tunnel7
local-address Loopback7
pre-shared-key address 192.168.2.46 key cisco
crypto keyring tunnel8
local-address Loopback8
pre-shared-key address 192.168.2.40 key cisco
crypto keyring tunnel9
local-address Loopback9
pre-shared-key address 192.168.2.43 key cisco
crypto keyring tunnel10
local-address Loopback10
pre-shared-key address 192.168.2.36 key cisco
crypto keyring tunnel11
local-address Loopback11
pre-shared-key address 192.168.2.56 key cisco
crypto isakmp policy 200
encryption aes
hash sha
authentication pre-share
group 16
lifetime 28800
crypto isakmp profile isakmp-tunnel0
keyring tunnel0
match identity address 0.0.0.0
local-address Loopback0
crypto isakmp profile isakmp-tunnel1
keyring tunnel1
match identity address 0.0.0.0
local-address Loopback1
crypto isakmp profile isakmp-tunnel2
keyring tunnel2
match identity address 0.0.0.0
local-address Loopback2
crypto isakmp profile isakmp-tunnel3
keyring tunnel3
match identity address 0.0.0.0
local-address Loopback3
crypto isakmp profile isakmp-tunnel4
keyring tunnel4
match identity address 0.0.0.0
local-address Loopback4
crypto isakmp profile isakmp-tunnel5
keyring tunnel5
match identity address 0.0.0.0
local-address Loopback5
crypto isakmp profile isakmp-tunnel6
keyring tunnel6
match identity address 0.0.0.0
local-address Loopback6
crypto isakmp profile isakmp-tunnel7
keyring tunnel7
match identity address 0.0.0.0
local-address Loopback7
crypto isakmp profile isakmp-tunnel8
keyring tunnel8
match identity address 0.0.0.0
local-address Loopback8
crypto isakmp profile isakmp-tunnel9
keyring tunnel9
match identity address 0.0.0.0
local-address Loopback9
crypto isakmp profile isakmp-tunnel10
keyring tunnel10
match identity address 0.0.0.0
local-address Loopback10
crypto isakmp profile isakmp-tunnel11
keyring tunnel11
match identity address 0.0.0.0
local-address Loopback11
crypto ipsec transform-set ipsec-prop-vpn-tunnel esp-gcm 256
mode tunnel
crypto ipsec df-bit clear
crypto ipsec profile ipsec-vpn-tunnel
set transform-set ipsec-prop-vpn-tunnel
set pfs group16
interface Loopback0
ip address 192.168.1.38 255.255.255.255
!
interface Loopback1
ip address 192.168.1.37 255.255.255.255
!
interface Loopback2
ip address 192.168.1.53 255.255.255.255
!
interface Loopback3
ip address 192.168.1.39 255.255.255.255
!
interface Loopback4
ip address 192.168.1.48 255.255.255.255
!
interface Loopback5
ip address 192.168.1.58 255.255.255.255
!
interface Loopback6
ip address 192.168.1.42 255.255.255.255
!
interface Loopback7
ip address 192.168.1.46 255.255.255.255
!
interface Loopback8
ip address 192.168.1.40 255.255.255.255
!
interface Loopback9
ip address 192.168.1.43 255.255.255.255
!
interface Loopback10
ip address 192.168.1.36 255.255.255.255
!
interface Loopback11
ip address 192.168.1.56 255.255.255.255
interface Tunnel0
ip address 10.101.100.101 255.255.255.0
load-interval 30
tunnel source Loopback0
tunnel mode ipsec ipv4
tunnel destination 192.168.2.38
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel1
ip address 10.101.101.101 255.255.255.0
load-interval 30
tunnel source Loopback1
tunnel mode ipsec ipv4
tunnel destination 192.168.2.37
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel2
ip address 10.101.102.101 255.255.255.0
load-interval 30
tunnel source Loopback2
tunnel mode ipsec ipv4
tunnel destination 192.168.2.53
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel3
ip address 10.101.103.101 255.255.255.0
load-interval 30
tunnel source Loopback3
tunnel mode ipsec ipv4
tunnel destination 192.168.2.39
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel4
ip address 10.101.104.101 255.255.255.0
load-interval 30
tunnel source Loopback4
tunnel mode ipsec ipv4
tunnel destination 192.168.2.48
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel5
ip address 10.101.105.101 255.255.255.0
load-interval 30
tunnel source Loopback5
tunnel mode ipsec ipv4
tunnel destination 192.168.2.58
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel6
ip address 10.101.106.101 255.255.255.0
load-interval 30
tunnel source Loopback6
tunnel mode ipsec ipv4
tunnel destination 192.168.2.42
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel7
ip address 10.101.107.101 255.255.255.0
load-interval 30
tunnel source Loopback7
tunnel mode ipsec ipv4
tunnel destination 192.168.2.46
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel8
ip address 10.101.108.101 255.255.255.0
load-interval 30
tunnel source Loopback8
tunnel mode ipsec ipv4
tunnel destination 192.168.2.40
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel9
ip address 10.101.109.101 255.255.255.0
load-interval 30
tunnel source Loopback9
tunnel mode ipsec ipv4
tunnel destination 192.168.2.43
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel10
ip address 10.101.110.101 255.255.255.0
load-interval 30
tunnel source Loopback10
tunnel mode ipsec ipv4
tunnel destination 192.168.2.36
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel11
ip address 10.101.111.101 255.255.255.0
load-interval 30
tunnel source Loopback11
tunnel mode ipsec ipv4
tunnel destination 192.168.2.56
tunnel protection ipsec profile ipsec-vpn-tunnel
interface GigabitEthernet2
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
! ### IP route from c8kv-uut to local servers
ip route 10.1.0.0 255.255.0.0 GigabitEthernet2 10.0.1.10
! ### IP routes from c8kv-uut to clients on c8kv-peer side, routes are evenly distributed to all 12 TXQ’s
ip route 10.10.0.0 255.255.0.0 Tunnel0
ip route 10.10.0.0 255.255.0.0 Tunnel1
ip route 10.10.0.0 255.255.0.0 Tunnel2
ip route 10.10.0.0 255.255.0.0 Tunnel3
ip route 10.10.0.0 255.255.0.0 Tunnel4
ip route 10.10.0.0 255.255.0.0 Tunnel5
ip route 10.10.0.0 255.255.0.0 Tunnel6
ip route 10.10.0.0 255.255.0.0 Tunnel7
ip route 10.10.0.0 255.255.0.0 Tunnel8
ip route 10.10.0.0 255.255.0.0 Tunnel9
ip route 10.10.0.0 255.255.0.0 Tunnel10
ip route 10.10.0.0 255.255.0.0 Tunnel11
! ### IP route from c8kv-uut Loopback int tunnel endpoint to c8kv-peer Loopback int tunnel endpoints
ip route 192.168.2.0 255.255.255.0 GigabitEthernet3 10.0.2.30 使用具有輔助IP地址的12個TXQ的拓撲和CLI配置示例

圖5.使用輔助IP地址的十二個TxQ的拓撲示例。
如果環回地址不能在AWS環境中使用,則可以改用連線到ENI的輔助IP地址。
這是「c8kv-ut」的CLI配置示例(圖5),使用計算出的雜湊IP地址(10.0.2.X)建立12個IPsec隧道,源地址為1個主IP地址+連線到GigabitEthernet3介面的11個輔助IP地址。另一個路由器端點(c8kv-peer)上會套用類似的組態,餘下十二個已計算的雜湊IP位址(20.0.2.X)。

附註:在本示例中,我們使用第二個C8000V作為隧道端點,但也可以使用其他雲網路端點,如TGW或DX。
ip cef load-sharing algorithm include-ports source destination 00ABC123
crypto keyring tunnel0
local-address 10.0.2.20
pre-shared-key address 20.0.2.30 key cisco
crypto keyring tunnel1
local-address 10.0.2.21
pre-shared-key address 20.0.2.31 key cisco
crypto keyring tunnel2
local-address 10.0.2.22
pre-shared-key address 20.0.2.32 key cisco
crypto keyring tunnel3
local-address 10.0.2.23
pre-shared-key address 20.0.2.33 key cisco
crypto keyring tunnel4
local-address 10.0.2.24
pre-shared-key address 20.0.2.36 key cisco
crypto keyring tunnel5
local-address 10.0.2.25
pre-shared-key address 20.0.2.35 key cisco
crypto keyring tunnel6
local-address 10.0.2.26
pre-shared-key address 20.0.2.37 key cisco
crypto keyring tunnel7
local-address 10.0.2.27
pre-shared-key address 20.0.2.38 key cisco
crypto keyring tunnel8
local-address 10.0.2.28
pre-shared-key address 20.0.2.40 key cisco
crypto keyring tunnel9
local-address 10.0.2.29
pre-shared-key address 20.0.2.41 key cisco
crypto keyring tunnel10
local-address 10.0.2.30
pre-shared-key address 20.0.2.44 key cisco
crypto keyring tunnel11
local-address 10.0.2.31
pre-shared-key address 20.0.2.46 key cisco
crypto isakmp policy 200
encryption aes
hash sha
authentication pre-share
group 16
lifetime 28800
crypto isakmp profile isakmp-tunnel0
keyring tunnel0
match identity address 20.0.2.30 255.255.255.255
local-address 10.0.2.20
crypto isakmp profile isakmp-tunnel1
keyring tunnel1
match identity address 20.0.2.31 255.255.255.255
local-address 10.0.2.21
crypto isakmp profile isakmp-tunnel2
keyring tunnel2
match identity address 20.0.2.32 255.255.255.255
local-address 10.0.2.22
crypto isakmp profile isakmp-tunnel3
keyring tunnel3
match identity address 20.0.2.33 255.255.255.255
local-address 10.0.2.23
crypto isakmp profile isakmp-tunnel4
keyring tunnel4
match identity address 20.0.2.36 255.255.255.255
local-address 10.0.2.24
crypto isakmp profile isakmp-tunnel5
keyring tunnel5
match identity address 20.0.2.35 255.255.255.255
local-address 10.0.2.25
crypto isakmp profile isakmp-tunnel6
keyring tunnel6
match identity address 20.0.2.37 255.255.255.255
local-address 10.0.2.26
crypto isakmp profile isakmp-tunnel7
keyring tunnel7
match identity address 20.0.2.38 255.255.255.255
local-address 10.0.2.27
crypto isakmp profile isakmp-tunnel8
keyring tunnel8
match identity address 20.0.2.40 255.255.255.255
local-address 10.0.2.28
crypto isakmp profile isakmp-tunnel9
keyring tunnel9
match identity address 20.0.2.41 255.255.255.255
local-address 10.0.2.29
crypto isakmp profile isakmp-tunnel10
keyring tunnel10
match identity address 20.0.2.44 255.255.255.255
local-address 10.0.2.30
crypto isakmp profile isakmp-tunnel11
keyring tunnel11
match identity address 20.0.2.46 255.255.255.255
local-address 10.0.2.31
crypto ipsec transform-set ipsec-prop-vpn-tunnel esp-gcm 256
mode tunnel
crypto ipsec df-bit clear
crypto ipsec profile ipsec-vpn-tunnel
set transform-set ipsec-prop-vpn-tunnel
set pfs group16
interface Tunnel0
ip address 10.101.100.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.20
tunnel mode ipsec ipv4
tunnel destination 20.0.2.30
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel1
ip address 10.101.101.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.21
tunnel mode ipsec ipv4
tunnel destination 20.0.2.31
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel2
ip address 10.101.102.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.22
tunnel mode ipsec ipv4
tunnel destination 20.0.2.32
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel3
ip address 10.101.103.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.23
tunnel mode ipsec ipv4
tunnel destination 20.0.2.33
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel4
ip address 10.101.104.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.24
tunnel mode ipsec ipv4
tunnel destination 20.0.2.36
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel5
ip address 10.101.105.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.25
tunnel mode ipsec ipv4
tunnel destination 20.0.2.35
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel6
ip address 10.101.106.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.26
tunnel mode ipsec ipv4
tunnel destination 20.0.2.37
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel7
ip address 10.101.107.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.27
tunnel mode ipsec ipv4
tunnel destination 20.0.2.38
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel8
ip address 10.101.108.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.28
tunnel mode ipsec ipv4
tunnel destination 20.0.2.40
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel9
ip address 10.101.109.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.29
tunnel mode ipsec ipv4
tunnel destination 20.0.2.41
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel10
ip address 10.101.110.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.30
tunnel mode ipsec ipv4
tunnel destination 20.0.2.44
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel11
ip address 10.101.111.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.31
tunnel mode ipsec ipv4
tunnel destination 20.0.2.46
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface GigabitEthernet2
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
mtu 9216
ip address 10.0.2.20 255.255.255.0
ip address 10.0.2.21 255.255.255.0 secondary
ip address 10.0.2.22 255.255.255.0 secondary
ip address 10.0.2.23 255.255.255.0 secondary
ip address 10.0.2.24 255.255.255.0 secondary
ip address 10.0.2.25 255.255.255.0 secondary
ip address 10.0.2.26 255.255.255.0 secondary
ip address 10.0.2.27 255.255.255.0 secondary
ip address 10.0.2.28 255.255.255.0 secondary
ip address 10.0.2.29 255.255.255.0 secondary
ip address 10.0.2.30 255.255.255.0 secondary
ip address 10.0.2.31 255.255.255.0 secondary
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
! ### IP route from c8kv-uut to local servers
ip route 10.1.0.0 255.255.255.0 GigabitEthernet2 10.0.1.10
! ### IP routes from c8kv-uut to clients on c8kv-peer side, routes are evenly distributed to all 12 TXQ’s
ip route 10.10.0.0 255.255.0.0 Tunnel0
ip route 10.10.0.0 255.255.0.0 Tunnel1
ip route 10.10.0.0 255.255.0.0 Tunnel2
ip route 10.10.0.0 255.255.0.0 Tunnel3
ip route 10.10.0.0 255.255.0.0 Tunnel4
ip route 10.10.0.0 255.255.0.0 Tunnel5
ip route 10.10.0.0 255.255.0.0 Tunnel6
ip route 10.10.0.0 255.255.0.0 Tunnel7
ip route 10.10.0.0 255.255.0.0 Tunnel8
ip route 10.10.0.0 255.255.0.0 Tunnel9
ip route 10.10.0.0 255.255.0.0 Tunnel10
ip route 10.10.0.0 255.255.0.0 Tunnel11
! ### IP route from c8kv-uut Gi3 int tunnel endpoint to c8kv-peer Gi3
int tunnel endpoints (secondary IP addresses on c8kv-peer side)
ip route 20.0.2.30 255.255.255.255 10.0.2.1
ip route 20.0.2.31 255.255.255.255 10.0.2.1
ip route 20.0.2.32 255.255.255.255 10.0.2.1
ip route 20.0.2.33 255.255.255.255 10.0.2.1
ip route 20.0.2.36 255.255.255.255 10.0.2.1
ip route 20.0.2.35 255.255.255.255 10.0.2.1
ip route 20.0.2.37 255.255.255.255 10.0.2.1
ip route 20.0.2.38 255.255.255.255 10.0.2.1
ip route 20.0.2.40 255.255.255.255 10.0.2.1
ip route 20.0.2.41 255.255.255.255 10.0.2.1
ip route 20.0.2.44 255.255.255.255 10.0.2.1
ip route 20.0.2.46 255.255.255.255 10.0.2.1 AWS中的典型Catalyst 8000V部署
自治模式
請參閱先前的CLI配置和拓撲示例。可以根據網路編址方案和生成的雜湊IP地址來複製和修改CLI配置。
要成功建立隧道,請務必在C8000V和AWS VPC的路由表中建立IP路由。
SD-WAN模式
這是一個拓撲和SD-WAN配置示例,它使用位於AWS VPC中的C8000Vs上的環回介面建立TLOC。
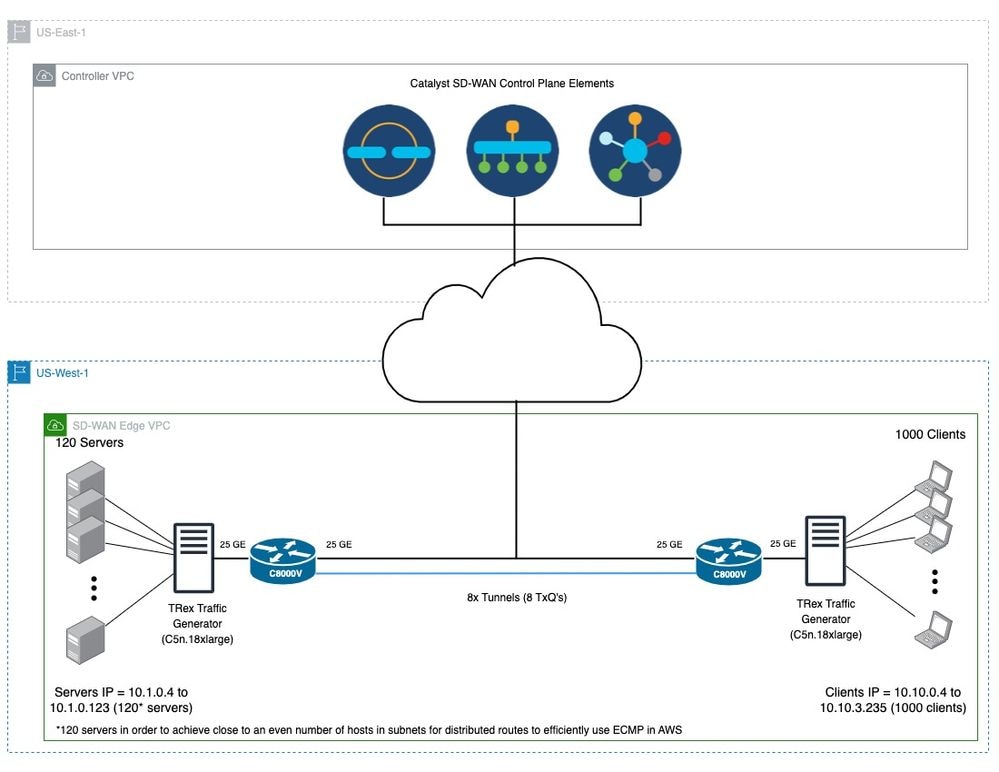
圖6.在AWS VPC中的C8000Vs上使用帶環回介面的TLOC的SD-WAN拓撲示例。

附註:在圖6中,黑色連線表示SD-WAN控制平面元素和SD-WAN邊緣裝置之間的控制(VPN0)連線。藍色連線表示使用TLOC的兩個SD-WAN邊緣裝置之間的隧道。
您可以找到圖6的SD-WAN CLI配置示例(此處)。
csr_uut#show sdwan run
system
system-ip 29.173.249.161
site-id 5172
admin-tech-on-failure
sp-organization-name SP_ORG_NAME
organization-name ORG_NAME
upgrade-confirm 15
vbond X.X.X.X
!
memory free low-watermark processor 68484
service timestamps debug datetime msec
service timestamps log datetime msec
no service tcp-small-servers
no service udp-small-servers
platform console virtual
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
hostname csr_uut
username ec2-user privilege 15 secret 5 $1$4P16$..ag88eFsOMLIemjNcWSt0
vrf definition 11
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
!
vrf definition Mgmt-intf
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
!
no ip finger
no ip rcmd rcp-enable
no ip rcmd rsh-enable
no ip dhcp use class
ip route 0.0.0.0 0.0.0.0 X.X.X.X
ip route 0.0.0.0 0.0.0.0 X.X.X.X
ip route 0.0.0.0 0.0.0.0 X.X.X.X
ip route vrf 11 10.1.0.0 255.255.0.0 X.X.X.X
ip route vrf Mgmt-intf 0.0.0.0 0.0.0.0 X.X.X.X
no ip source-route
ip ssh pubkey-chain
username ec2-user
key-hash ssh-rsa 353158c28c7649710b3c933da02e384b ec2-user
!
!
!
no ip http server
ip http secure-server
ip nat settings central-policy
ip nat settings gatekeeper-size 1024
ipv6 unicast-routing
class-map match-any class0
match dscp 1
!
class-map match-any class1
match dscp 2
!
class-map match-any class2
match dscp 3
!
class-map match-any class3
match dscp 4
!
class-map match-any class4
match dscp 5
!
class-map match-any class5
match dscp 6
!
class-map match-any class6
match dscp 7
!
class-map match-any class7
match dscp 8
!
policy-map qos_map1
class class0
priority percent 20
!
class class1
bandwidth percent 18
random-detect
!
class class2
bandwidth percent 15
random-detect
!
class class3
bandwidth percent 12
random-detect
!
class class4
bandwidth percent 10
random-detect
!
class class5
bandwidth percent 10
random-detect
!
class class6
bandwidth percent 10
random-detect
!
class class7
bandwidth percent 5
random-detect
!
!
interface GigabitEthernet1
no shutdown
ip address dhcp
no mop enabled
no mop sysid
negotiation auto
exit
interface GigabitEthernet2
no shutdown
ip address dhcp
load-interval 30
speed 10000
no negotiation auto
service-policy output qos_map1
exit
interface GigabitEthernet3
shutdown
ip address dhcp
load-interval 30
speed 10000
no negotiation auto
exit
interface GigabitEthernet4
no shutdown
vrf forwarding 11
ip address X.X.X.X 255.255.255.0
load-interval 30
speed 10000
no negotiation auto
exit
interface Loopback1
no shutdown
ip address 192.168.1.21 255.255.255.255
exit
interface Loopback2
no shutdown
ip address 192.168.1.129 255.255.255.255
exit
interface Loopback3
no shutdown
ip address 192.168.1.20 255.255.255.255
exit
interface Loopback4
no shutdown
ip address 192.168.1.128 255.255.255.255
exit
interface Loopback5
no shutdown
ip address 192.168.1.23 255.255.255.255
exit
interface Loopback6
no shutdown
ip address 192.168.1.131 255.255.255.255
exit
interface Loopback7
no shutdown
ip address 192.168.1.22 255.255.255.255
exit
interface Loopback8
no shutdown
ip address 192.168.1.130 255.255.255.255
exit
interface Tunnel1
no shutdown
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode sdwan
exit
interface Tunnel14095001
no shutdown
ip unnumbered Loopback1
no ip redirects
ipv6 unnumbered Loopback1
no ipv6 redirects
tunnel source Loopback1
tunnel mode sdwan
exit
interface Tunnel14095002
no shutdown
ip unnumbered Loopback2
no ip redirects
ipv6 unnumbered Loopback2
no ipv6 redirects
tunnel source Loopback2
tunnel mode sdwan
exit
interface Tunnel14095003
no shutdown
ip unnumbered Loopback3
no ip redirects
ipv6 unnumbered Loopback3
no ipv6 redirects
tunnel source Loopback3
tunnel mode sdwan
exit
interface Tunnel14095004
no shutdown
ip unnumbered Loopback4
no ip redirects
ipv6 unnumbered Loopback4
no ipv6 redirects
tunnel source Loopback4
tunnel mode sdwan
exit
interface Tunnel14095005
no shutdown
ip unnumbered Loopback5
no ip redirects
ipv6 unnumbered Loopback5
no ipv6 redirects
tunnel source Loopback5
tunnel mode sdwan
exit
interface Tunnel14095006
no shutdown
ip unnumbered Loopback6
no ip redirects
ipv6 unnumbered Loopback6
no ipv6 redirects
tunnel source Loopback6
tunnel mode sdwan
exit
interface Tunnel14095007
no shutdown
ip unnumbered Loopback7
no ip redirects
ipv6 unnumbered Loopback7
no ipv6 redirects
tunnel source Loopback7
tunnel mode sdwan
exit
interface Tunnel14095008
no shutdown
ip unnumbered Loopback8
no ip redirects
ipv6 unnumbered Loopback8
no ipv6 redirects
tunnel source Loopback8
tunnel mode sdwan
exit
no logging console
aaa authentication enable default enable
aaa authentication login default local
aaa authorization console
aaa authorization exec default local none
login on-success log
license smart transport smart
license smart url https://smartreceiver.cisco.com/licservice/license
line aux 0
!
line con 0
stopbits 1
!
line vty 0 4
transport input ssh
!
line vty 5 80
transport input ssh
!
sdwan
interface GigabitEthernet1
tunnel-interface
encapsulation ipsec
color private1 restrict
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface GigabitEthernet2
exit
interface GigabitEthernet3
exit
interface Loopback1
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private2 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback2
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private3 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback3
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private4 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback4
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private5 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback5
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private6 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback6
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color red restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback7
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color blue restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback8
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color green restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
appqoe
no tcpopt enable
no dreopt enable
no httpopt enable
!
omp
no shutdown
send-path-limit 16
ecmp-limit 16
graceful-restart
no as-dot-notation
timers
graceful-restart-timer 43200
exit
address-family ipv4
advertise connected
advertise static
!
address-family ipv6
advertise connected
advertise static
!
!
!
security
ipsec
replay-window 8192
integrity-type ip-udp-esp esp
!
!
sslproxy
no enable
rsa-key-modulus 2048
certificate-lifetime 730
eckey-type P256
ca-tp-label PROXY-SIGNING-CA
settings expired-certificate drop
settings untrusted-certificate drop
settings unknown-status drop
settings certificate-revocation-check none
settings unsupported-protocol-versions drop
settings unsupported-cipher-suites drop
settings failure-mode close
settings minimum-tls-ver TLSv1
dual-side optimization enable
!
policy
app-visibility
flow-visibility
!AWS中的吞吐量效能故障排除

附註:在公共雲環境中執行效能測試引入可能會影響吞吐量效能的新變數。在執行此類測試時,需要考慮以下幾點:
- 對等體在運行測試時的基礎資源使用情況
- 不使用專用主機(使用專用主機將雲成本提高16倍)
- 雲在不同地區運行,效能可能有所不同
- 在某些情況下,無論特徵輪廓如何,數字都是相似的;這可能是由於AWS限制介面每例項大小
- AWS在EC2例項上限制每秒資料包速率,這同樣會導致資料包丟棄
- AWS不披露限制速率,但由於pps限制而丟棄的資料可通過「pps_allowance_exceeded」計數器進行觀察
實用的CLI故障排除命令
進行吞吐量效能測試時,可以使用這些故障排除命令來查明效能下降的瓶頸或原因。
「show platform hardware qfp active statistics drop」 — 允許我們瞭解c8kv上是否有任何丟包。我們需要確保沒有顯著的尾部丟棄或任何相關的計數器增加。
"show platform hardware qfp active statistics drop clear" — 此命令清除計數器。
"show platform hardware qfp active datapath infrastructure sw-cio" — 此命令向我們詳細說明了效能運行期間資料包處理器(PP)、流量管理器(TM)的利用率情況。這使我們能夠從c8kv確定是否有足夠的處理能力。
"show platform hardware qfp active datapath util summary" — 此命令提供從所有埠傳送/接收c8kv的輸入/輸出的完整資訊。
確保檢查輸入/輸出速率並檢視是否有任何丟棄。此外,請確保檢查處理負載百分比。如果達到100%;這意味著c8kv已達到其容量。
"show platt hardware qfp active infrastructure bqs interface GigabitEthernetX" — 此命令允許我們檢查介面層級統計資料,以瞭解佇列編號、頻寬、尾部捨棄。
"show controller" — 此指令提供有關rx/tx正常封包、遺失封包的詳細資訊。
此命令可用於我們看不到任何尾部丟棄,但流量生成器仍顯示丟棄的情形。
在資料利用率已達到100%,PP也達到100%的情況下,可能發生這種情況。
如果rx_missed_errors計數器持續增加,則意味著CSR對雲基礎設施進行反向壓力,因為它無法處理任何其他流量。
「show platform hardware qfp active datapath infrastructure sw-hqf」 — 可用於檢查是否因AWS的背壓而發生擁塞。
「show platt hardware qfp active datapath infrastructure sw-nic」 — 確定如何在多個隊列之間對流量進行負載均衡。17.7之後,我們有8個多TXQ。
此外,它還可以確定是否有任何特定隊列正在接收所有流量或正正確進行負載均衡。
"顯示控制器 |in errors|exceeded|Giga" — 顯示由於AWS端的pps限制而丟棄的資料包,可通過pps_allowance_exceeded計數器觀察此情況。
CLI輸出示例
尾部丟棄計數器不斷遞增的輸出示例 — 多次發出命令以檢視計數器是否遞增,從而讓我們確認計數器確實是尾部丟棄。
csr_uut#show platform hardware qfp active statistics drop
Last clearing of QFP drops statistics : never
-------------------------------------------------------------------------
Global Drop Stats Packets Octets
-------------------------------------------------------------------------
Disabled 30 3693
IpFragErr 192 290976
Ipv4NoRoute 43 3626
Ipv6NoRoute 4 224
SdwanImplicitAclDrop 31 3899
TailDrop 19099700 22213834441
UnconfiguredIpv6Fia 3816 419760
此處顯示的輸出示例 — 每30秒發出一次命令以獲取即時資料
csr_uut#show platform hardware qfp active datapath infrastructure sw-cio
Credits Usage:
ID Port Wght Global WRKR0 WRKR1 WRKR2 WRKR3 WRKR4 WRKR5 WRKR6 WRKR7 WRKR8 WRKR9 WRKR10 WRKR11 WRKR12 WRKR13 Total
1 rcl0 16: 455 0 4 1 2 3 2 2 4 4 4 4 0 4 23 512
1 rcl0 32: 496 0 0 0 0 0 0 0 0 0 0 0 0 0 16 512
2 ipc 1: 468 4 2 4 3 0 1 1 4 0 2 0 4 0 18 511
3 vxe_punti 4: 481 0 0 0 0 0 0 0 0 0 0 0 0 0 31 512
4 Gi1 4: 446 0 0 1 1 0 2 3 0 3 2 0 1 1 52 512
5 Gi2 4: 440 4 4 4 3 2 1 1 3 2 4 4 3 2 59 504
6 Gi3 4: 428 1 1 1 0 4 4 1 0 4 4 0 0 2 43 494
7 Gi4 4: 427 1 1 0 1 4 2 0 4 3 4 1 1 7 56 512
Core Utilization over preceding 12819.5863 seconds
--------------------------------------------------
ID: 0 1 2 3 4 5 6 7 8 9 10 11 12 13
% PP: 6.11 6.23 6.09 6.09 6.04 6.05 6.06 6.07 6.05 6.03 6.04 6.06 0.00 0.00
% RX: 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 2.23
% TM:0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 4.79 0.00
% IDLE: 93.89 93.77 93.91 93.91 93.96 93.95 93.94 93.93 93.95 93.97 93.96 93.94 95.21 97.77
此處顯示的輸出範例 — 確保檢查輸入/輸出速率並檢視是否有任何下降。此外,請確保檢查處理負載百分比。如果達到100%;這意味著節點已達到其容量。
csr_uut#show platform hardware qfp active datapath util summary
CPP 0: 5 secs 1 min 5 min 60 min
Input: Total (pps)900215 980887 903176 75623
(bps) 10276623992 11197595912 10310265440 863067008
Output: Total (pps)900216 937459 865930 72522
(bps) 10276642720 10712432752 9894215928 828417104
Processing: Load (pct)56 58 54 4
此處顯示的介面級別統計資訊輸出示例:
csr_uut#sh plat hardware qfp active infrastructure bqs interface GigabitEthernet2
Interface: GigabitEthernet2, QFP interface: 7
Queue: QID: 111 (0x6f)
bandwidth (cfg) : 0 , bandwidth (hw) : 1050000000
shape (cfg) : 0 , shape (hw) : 0
prio level (cfg) : 0 , prio level (hw) : n/a
limit (pkts ) : 1043
Statistics:
depth (pkts ) : 0
tail drops (bytes): 0 , (packets) : 0
total enqs (bytes): 459322360227 , (packets) : 374613901
licensed throughput oversubscription drops:
(bytes): 0 , (packets) : 0
Schedule: (SID:0x8a)
Schedule FCID : n/a
bandwidth (cfg) : 10500000000 , bandwidth (hw) : 10500000000
shape (cfg) : 10500000000 , shape (hw) : 10500000000
Schedule: (SID:0x87)
Schedule FCID : n/a
bandwidth (cfg) : 200000000000 , bandwidth (hw) : 200000000000
shape (cfg) : 200000000000 , shape (hw) : 200000000000
Schedule: (SID:0x86)
Schedule FCID : n/a
bandwidth (cfg) : 500000000000 , bandwidth (hw) : 500000000000
shape (cfg) : 500000000000 , shape (hw) : 500000000000
csr_uut#sh plat hardware qfp active infrastructure bqs interface GigabitEthernet3 | inc tail
tail drops (bytes): 55815791988 , (packets) : 43177643
RX/TX正常資料包、丟失資料包統計資訊的輸出示例
c8kv-aws-1#show controller
GigabitEthernet1 - Gi1 is mapped to UIO on VXE
rx_good_packets 346
tx_good_packets 243
rx_good_bytes 26440
tx_good_bytes 31813
rx_missed_errors 0
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
GigabitEthernet2 - Gi2 is mapped to UIO on VXE
rx_good_packets 96019317
tx_good_packets 85808651
rx_good_bytes 12483293931
tx_good_bytes 11174853219
rx_missed_errors 522036
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
GigabitEthernet3 - Gi3 is mapped to UIO on VXE
rx_good_packets 171596935
tx_good_packets 191911304
rx_good_bytes 11668588022
tx_good_bytes 13049984257
rx_missed_errors 21356065
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
GigabitEthernet4 - Gi4 is mapped to UIO on VXE
rx_good_packets 95922932
tx_good_packets 85831238
rx_good_bytes 12470124252
tx_good_bytes 11158486786
rx_missed_errors 520328
rx_errors 46
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
用於檢查因AWS背壓引起的任何擁塞的輸出示例:
csr_uut#show platform hardware qfp active datapath infrastructure sw-hqf
Name : Pri1 Pri2 None / Inflight pkts
GigabitEthernet4 : XON XON XOFF / 43732
HQF[0] IPC: send 514809 fc 0 congested_cnt 0
HQF[0] recycle: send hi 0 send lo 228030112
fc hi 0 fc lo 0
cong hi 0 cong lo 0
HQF[0] pkt: send hi 433634 send lo 2996661158
fc/full hi 0 fc/full lo 34567275
cong hi 0 cong lo 4572971630**************Congestion counters keep incrementing
HQF[0] aggr send stats 3225639713 aggr send lo state 3225206079
aggr send hi stats 433634
max_tx_burst_sz_hi 0 max_tx_burst_sz_lo 0
HQF[0] gather: failed_to_alloc_b4q 0
HQF[0] ticks 662109543, max ticks accumulated 348
HQF[0] mpsc stats: count: 0
enq 3225683472 enq_spin 0 enq_post 0 enq_flush 0
sig_cnt:0 enq_cancel 0
deq 3225683472 deq_wait 0 deq_fail 0 deq_cancel 0
deq_wait_timeout
如何在多個隊列之間對流量進行負載均衡的輸出示例:
um-csr-uut#sh plat hardware qfp active datapath infrastructure sw-nic
pmd b1c5a400 device Gi1
RX: pkts 50258 bytes 4477620 return 0 badlen 0
pkts/burst 1 cycl/pkt 579 ext_cycl/pkt 996
Total ring read 786244055, empty 786197491
TX: pkts 57860 bytes 6546349
pri-0: pkts 7139 bytes 709042
pkts/send 1
pri-1: pkts 3868 bytes 451352
pkts/send 1
pri-2: pkts 1875 bytes 219403
pkts/send 1
pri-3: pkts 2417 bytes 242527
pkts/send 1
pri-4: pkts 8301 bytes 984022
pkts/send 1
pri-5: pkts 10268 bytes 1114859
pkts/send 1
pri-6: pkts 1740 bytes 175353
pkts/send 1
pri-7: pkts 22252 bytes 2649791
pkts/send 1
Total: pkts/send 1 cycl/pkt 1091
send 56756 sendnow 0
forced 56756 poll 0 thd_poll 0
blocked 0 retries 0 mbuf alloc err 0
TX Queue 0: full 0 current index 0 hiwater 0
TX Queue 1: full 0 current index 0 hiwater 0
TX Queue 2: full 0 current index 0 hiwater 0
TX Queue 3: full 0 current index 0 hiwater 0
TX Queue 4: full 0 current index 0 hiwater 0
TX Queue 5: full 0 current index 0 hiwater 0
TX Queue 6: full 0 current index 0 hiwater 0
TX Queue 7: full 0 current index 0 hiwater 0
pmd b1990b00 device Gi2
RX: pkts 1254741010 bytes 511773562848 return 0 badlen 0
pkts/burst 16 cycl/pkt 792 ext_cycl/pkt 1342
Total ring read 1012256968, empty 937570790
TX: pkts 1385120320 bytes 564465308380
pri-0: pkts 168172786 bytes 68650796972
pkts/send 1
pri-1: pkts 177653235 bytes 72542203822
pkts/send 1
pri-2: pkts 225414300 bytes 91947701824
pkts/send 1
pri-3: pkts 136817435 bytes 55908224442
pkts/send 1
pri-4: pkts 256461818 bytes 104687120554
pkts/send 1
pri-5: pkts 176043289 bytes 71879529606
pkts/send 1
pri-6: pkts 83920827 bytes 34264110122
pkts/send 1
pri-7: pkts 160636635 bytes 64585622696
pkts/send 1
Total: pkts/send 1 cycl/pkt 442
send 1033104466 sendnow 41250092
forced 1776500651 poll 244223290 thd_poll 0
blocked 1060879040 retries 3499069 mbuf alloc err 0
TX Queue 0: full 0 current index 0 hiwater 31
TX Queue 1: full 718680 current index 0 hiwater 255
TX Queue 2: full 0 current index 0 hiwater 31
TX Queue 3: full 0 current index 0 hiwater 31
TX Queue 4: full 15232240 current index 0 hiwater 255
TX Queue 5: full 0 current index 0 hiwater 31
TX Queue 6: full 0 current index 0 hiwater 31
TX Queue 7: full 230668 current index 0 hiwater 224
pmd b1712d00 device Gi3
RX: pkts 1410702537 bytes 498597093510 return 0 badlen 0
pkts/burst 18 cycl/pkt 269 ext_cycl/pkt 321
Total ring read 1011915032, empty 934750846
TX: pkts 754803798 bytes 266331910366
pri-0: pkts 46992577 bytes 16616415156
pkts/send 1
pri-1: pkts 49194201 bytes 17379760716
pkts/send 1
pri-2: pkts 46991555 bytes 16616509252
pkts/send 1
pri-3: pkts 49195026 bytes 17381741474
pkts/send 1
pri-4: pkts 48875656 bytes 17283423414
pkts/send 1
pri-5: pkts 417370776 bytes 147056906106
pkts/send 6
pri-6: pkts 46992860 bytes 16617923068
pkts/send 1
pri-7: pkts 49191147 bytes 17379231180
pkts/send 1
Total: pkts/send 2 cycl/pkt 0
send 339705775 sendnow 366141927
forced 3138709511 poll 2888466204 thd_poll 0
blocked 1758644571 retries 27927046 mbuf alloc err 0
TX Queue 0: full 0 current index 0 hiwater 0
TX Queue 1: full 0 current index 0 hiwater 0
TX Queue 2: full 0 current index 0 hiwater 0
TX Queue 3: full 0 current index 0 hiwater 0
TX Queue 4: full 0 current index 1 hiwater 0
TX Queue 5: full 27077270 current index 0 hiwater 224
TX Queue 6: full 0 current index 0 hiwater 0
TX Queue 7: full 0 current index 0 hiwater 0
顯示因AWS端完成的pps限制而丟棄的資料包的輸出示例(可通過pps_allowance_exceeded計數器觀察到):
C8k-AWS-2#show controllers | in errors|exceeded|Giga
GigabitEthernet1 - Gi1 is mapped to UIO on VXE
rx_missed_errors 1750262
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0_errors 0
rx_q1_errors 0
rx_q2_errors 0
rx_q3_errors 0
bw_in_allowance_exceeded 0
bw_out_allowance_exceeded 0
pps_allowance_exceeded 11750
conntrack_allowance_exceeded 0
linklocal_allowance_exceeded 0
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
07-Aug-2025
|
初始版本 |
 意見
意見