簡介
本檔案介紹如何在Cisco Nexus 3000(常規模式)系列交換器上設定和驗證服務反射功能。
必要條件
需求
您瞭解以下主題的一般建議:
- 通訊協定無關多點傳送(PIM)
- 開放最短路徑優先(OSPF)
- 網路位址轉譯(NAT)
- 網際網路群組管理協定(IGMP)
採用元件
本文中的資訊係根據以下軟體和硬體版本:
| Sw1# |
N9K-C93180YC-FX |
NXOS:版本9.3(5) |
| Sw2# |
N3K-C3548P-XL |
NXOS:版本7.0(3)I7(9) |
| Sw3# |
N3K-C3172TQ-10GT |
NXOS:版本7.0(3)I7(9) |
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
支援的Cisco Nexus 3k平台
組播服務反射功能僅在7.0(3)I7(2)版的Cisco Nexus 3548-X平台上受支援。
支援的服務反射方法
常規模式多點傳送NAT
在常規模式下,作為S1、G1介面傳入的包被轉換為S2、G2介面,並且傳出包的目的地媒體訪問控制(MAC)地址被轉換為G2介面(例如,轉換後的組)的組播MAC地址。
使用無重寫組播NAT的快速通道和快速通道
在快速傳遞模式中,S1、G1介面被轉換為S2、G2介面,並且傳出資料包的目的MAC地址具有與G1介面對應的組播MAC地址(例如,預轉換組的MAC地址)。
設定
拓撲
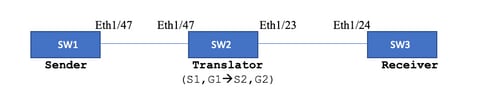
本地組:239.194.169.1(G1)
轉換後的組:233.193.40.196(G2)
原始來源:10.11.11.1(S1)
轉換後來源:172.16.0.1。(S2)
組態
Switch 1配置(傳送方)
SW1# show run int eth1/47
interface Ethernet1/47
no switchport
ip address 10.11.11.1/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
SW1# show run ospf
feature ospf
router ospf 1
router-id 192.168.1.1
interface Ethernet1/47
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
SW1# show run pim
feature pim
ip pim rp-address 10.10.10.10 group-list 239.194.169.1/32
ip pim ssm range 232.0.0.0/8
interface Ethernet1/47
ip pim sparse-mode
交換機2配置(轉換器)
SW2# show run int eth 1/23,eth1/47
interface Ethernet1/23
no switchport
ip address 10.0.0.1/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
no shutdown
interface Ethernet1/47
no switchport
ip address 10.11.11.2/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
no shutdown
SW2# show run int lo0,lo411
interface loopback0
ip address 10.10.10.10/32
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
interface loopback411
ip address 172.16.0.1/32
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
ip igmp join-group 239.194.169.1
SW2# show run ospf
feature ospf
router ospf 1
router-id 192.168.1.2
interface loopback0
ip router ospf 1 area 0.0.0.0
interface loopback411
ip router ospf 1 area 0.0.0.0
interface Ethernet1/23
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
interface Ethernet1/47
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
SW2# show run pim
feature pim
ip pim rp-address 10.10.10.10 group-list 239.194.169.1/32
ip pim rp-address 172.16.0.1 group-list 233.193.40.196/32
ip pim ssm range 232.0.0.0/8
interface loopback0
ip pim sparse-mode
interface loopback411
ip pim sparse-mode
interface Ethernet1/23
ip pim sparse-mode
interface Ethernet1/47
ip pim sparse-mode
ip service-reflect mode regular
ip service-reflect destination 239.194.169.1 to 233.193.40.196 mask-len 32 source 172.16.0.1
hardware profile multicast service-reflect port 7
Switch 3配置(接收器)
SW3# show run int eth 1/24
interface Ethernet1/24
ip address 10.0.0.2/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
ip igmp join-group 233.193.40.196
no shutdown
SW3# show run ospf
feature ospf
router ospf 1
router-id 192.168.1.3
interface Ethernet1/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
SW3# show run pim
feature pim
ip pim rp-address 172.16.0.1 group-list 233.193.40.196/32
ip pim ssm range 232.0.0.0/8
interface Ethernet1/24
ip pim sparse-mode
驗證
使用本節內容,確認您的組態是否正常運作。
驗證服務反射功能
交換機1驗證
SW1# show ip mroute
IP Multicast Routing Table for VRF "default"
(*, 232.0.0.0/8), uptime: 3w6d, pim ip
Incoming interface: Null, RPF nbr: 0.0.0.0
Outgoing interface list: (count: 0)
(10.11.11.1/32, 239.194.169.1/32), uptime: 00:06:57, pim ip
Incoming interface: Ethernet1/47, RPF nbr: 10.11.11.1
Outgoing interface list: (count: 1)
Ethernet1/47, uptime: 00:06:57, pim, (RPF)
交換機2驗證
SW2# show ip mroute
IP Multicast Routing Table for VRF "default"
(*, 232.0.0.0/8), uptime: 00:04:39, pim ip
Incoming interface: Null, RPF nbr: 0.0.0.0
Outgoing interface list: (count: 0)
(*, 233.193.40.196/32), uptime: 00:04:11, pim ip
Incoming interface: loopback411, RPF nbr: 172.16.0.1 <-- Translation (ingress) Loopback interface
Outgoing interface list: (count: 1)
Ethernet1/23, uptime: 00:03:59, pim <-- Egress interface for S2,G2
(172.16.0.1/32, 233.193.40.196/32), uptime: 00:00:15, ip mrib pim
Incoming interface: loopback411, RPF nbr: 172.16.0.1
Outgoing interface list: (count: 1)
Ethernet1/23, uptime: 00:00:15, pim
(*, 239.194.169.1/32), uptime: 00:04:34, static pim ip <-- (The NAT router would pull the traffic by using a (*,G) join on loopback )
Incoming interface: loopback0, RPF nbr: 10.10.10.10
Outgoing interface list: (count: 1)
loopback411, uptime: 00:04:34, static <-- Translation (egress) Loopback interface
(10.11.11.1/32, 239.194.169.1/32), uptime: 00:00:17, ip mrib pim
Incoming interface: Ethernet1/47, RPF nbr: 10.11.11.1, internal <-- Ingress interface for S1,G1
Outgoing interface list: (count: 1)
loopback411, uptime: 00:00:17, mrib
SW2# show ip mroute sr <-- (Only SR nat routes)
IP Multicast Routing Table for VRF "default"
(*, 239.194.169.1/32), uptime: 00:09:29, static pim ip
NAT Mode: Ingress
NAT Route Type: Pre
Incoming interface: loopback0, RPF nbr: 10.10.10.10
Translation list: (count: 1)
SR: (172.16.0.1, 233.193.40.196)
(10.11.11.1/32, 239.194.169.1/32), uptime: 00:05:12, ip mrib pim
NAT Mode: Ingress
NAT Route Type: Pre
Incoming interface: Ethernet1/47, RPF nbr: 10.11.11.1, internal
Translation list: (count: 1)
SR: (172.16.0.1, 233.193.40.196)
交換機3驗證
SW3# show ip mroute
IP Multicast Routing Table for VRF "default"
(*, 232.0.0.0/8), uptime: 02:45:09, pim ip
Incoming interface: Null, RPF nbr: 0.0.0.0
Outgoing interface list: (count: 0)
(*, 233.193.40.196/32), uptime: 01:47:02, ip pim igmp
Incoming interface: Ethernet1/24, RPF nbr: 10.0.0.1
Outgoing interface list: (count: 1)
Ethernet1/24, uptime: 01:43:27, igmp, (RPF)
(172.16.0.1/32, 233.193.40.196/32), uptime: 00:02:59, ip mrib pim
Incoming interface: Ethernet1/24, RPF nbr: 10.0.0.1
Outgoing interface list: (count: 1)
Ethernet1/24, uptime: 00:02:59, mrib, (RPF)
疑難排解
本節提供的資訊可用於對組態進行疑難排解。
如果S2和G2未建立,或者使用者遇到隨機轉換問題,您可以檢查以下幾點:
1.一旦收到流量(預轉換),就會根據mcastfwd中的pkt建立轉換後的條目。
2.如果您沒有看到在mcastfwd中傳送pkt,可以檢查是否透過ACL在輸入介面上取得所請求的流量。
3如果您在ACL中看到計數器增加,請通過ethanalyzer檢查相同流量命中CPU。
4還可以檢查MRIB event-history中的轉換:
SW2# show system internal mfwd ip mroute --> Packets Punted in Mcast Forwarding.
MCASTFWD Multicast Routing Table for VRF "default"
(0.0.0.0/0, 232.0.0.0/8)
Software switched packets: 0, bytes: 0
RPF fail packets: 0, bytes: 0
(0.0.0.0/0, 233.193.40.196/32)
Software switched packets: 1, bytes: 84
RPF fail packets: 0, bytes: 0
(172.16.0.1/32, 233.193.40.196/32), data-alive
Software switched packets: 1, bytes: 84
RPF fail packets: 8, bytes: 672
(0.0.0.0/0, 239.194.169.1/32)
Software switched packets: 1, bytes: 84
RPF fail packets: 0, bytes: 0
(10.11.11.1/32, 239.194.169.1/32), data-alive
Software switched packets: 10, bytes: 840
RPF fail packets: 0, bytes: 0
SW2# show ip access-lists test
IP access list test
statistics per-entry
10 permit ip any 239.194.169.1/32 [match=105] <-- Intrested traffic hitting ingress interface
20 permit ip any any [match=11]
interface Ethernet1/47
no switchport
ip access-group test in <-- ACL applied on ingress interface
ip address 10.11.11.2/24
ip ospf network point-to-point
ip router ospf 1 area 0.0.0.0
ip pim sparse-mode
no shutdown
SW2# ethanalyzer loca int inband display-filter "ip.addr == 239.194.169.1" limit-captured-frames 0 --> Confirm (S1,G1) seen on CPU
Capturing on inband
wireshark-cisco-mtc-dissector: ethertype=0xde09, devicetype=0x0
2022-09-18 04:21:37.840227 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.841275 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.860153 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.861199 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.880072 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
2022-09-18 04:21:37.881113 10.11.11.1 -> 239.194.169.1 ICMP Echo (ping) request
SW2# ethanalyzer local interface inband capture-filter "host 172.16.0.1" limit-captured-frames 0 --> Confirm (S2,G2) seen on CPU
Capturing on inband
wireshark-cisco-mtc-dissector: ethertype=0xde09, devicetype=0x0
2022-09-18 03:12:51.423484 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:51.423978 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:53.425754 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:53.425761 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:55.426719 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:55.426726 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:57.428669 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:57.429175 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
2022-09-18 03:12:59.429890 172.16.0.1 -> 233.193.40.196 ICMP Echo (ping) request
2022-09-18 03:12:59.430386 10.0.0.2 -> 172.16.0.1 ICMP Echo (ping) reply
10 packets captured
SW2# show ip pim event-history mrib --> Event history to confirm that the translation is being done
2022 Sep 18 04:28:39.970688: E_DEBUG pim [19433]: Sending ack: xid: 0xeeee00d2
2022 Sep 18 04:28:39.970255: E_DEBUG pim [19433]: MRIB Join notify for (10.11.11.1/32, 239.194.169.1/32)
2022 Sep 18 04:28:39.968875: E_DEBUG pim [19433]: MRIB sr route type notif for (10.11.11.1/32, 239.194.169.1/32) : 1
2022 Sep 18 04:28:39.968859: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (10.11.11.1/32, 239.194.169.1/32), old RPF info: 10.11.11.1 (Ethernet1/47), new RPF info: 10.11.11.1 (Ethernet1/47). LISP source RLOC address
: 0.0.0.0, route-type 1
2022 Sep 18 04:28:39.968307: E_DEBUG pim [19433]: Copied the flags from MRIB for route (10.11.11.1/32, 239.194.169.1/32), (before/after): att F/F, sta F/F, z-oifs T/F, ext F/F, fabric F/F, fabric_src: F/F mofrr F/F
2022 Sep 18 04:28:39.968301: E_DEBUG pim [19433]: MRIB Join notify for (10.11.11.1/32, 239.194.169.1/32)
2022 Sep 18 04:28:39.968294: E_DEBUG pim [19433]: Received a notify message from MRIB xid: 0xeeee00cf for 1 mroutes
2022 Sep 18 04:28:35.904652: E_DEBUG pim [19433]: Sending ack: xid: 0xeeee00cc
2022 Sep 18 04:28:35.904625: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (172.16.0.1/32, 233.193.40.196/32), old RPF info: 172.16.0.1 (loopback411), new RPF info: 172.16.0.1 (loopback411). LISP sourc
e RLOC address: 0.0.0.0, route-type 0
2022 Sep 18 04:28:35.904484: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: After copying the values for route (0.0.0.0/32, 233.193.40.196/32) we got RPF info: 172.16.0.1 (loopback411). LISP source RLOC address: 0.0.0.0, route-t
ype 0
2022 Sep 18 04:28:35.904476: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (0.0.0.0/32, 233.193.40.196/32), old RPF info: 0.0.0.0 ((null)), new RPF info: 172.16.0.1 (loopback411). LISP source RLOC address: 0
.0.0.0, route-type 0
2022 Sep 18 04:28:35.904400: E_DEBUG pim [19433]: MRIB Join notify for (172.16.0.1/32, 233.193.40.196/32)
2022 Sep 18 04:28:35.904343: E_DEBUG pim [19433]: MRIB Join notify for (0.0.0.0/32, 233.193.40.196/32)
2022 Sep 18 04:27:49.862827: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: After copying the values for route (*, 239.194.169.1/32) we got RPF info: 10.10.10.10 (loopback0). LISP source RLOC address: 0.0.0.0, route-type 0
2022 Sep 18 04:27:49.862812: E_DEBUG pim [19433]: pim_process_mrib_rpf_notify: MRIB RPF notify for (*, 239.194.169.1/32), old RPF info: 0.0.0.0 ((null)), new RPF info: 10.10.10.10 (loopback0). LISP source RLOC address: 0.0.0.0, route-
type 0
2022 Sep 18 04:27:49.862798: E_DEBUG pim [19433]: MRIB Join notify for (*, 239.194.169.1/32)
2022 Sep 18 04:27:49.862795: E_DEBUG pim [19433]: MRIB Join notify for (172.16.0.1/32, 233.193.40.196/32)
2022 Sep 18 04:27:49.862789: E_DEBUG pim [19433]: MRIB Join notify for (0.0.0.0/32, 233.193.40.196/32)
2022 Sep 18 04:27:49.861870: E_DEBUG pim [19433]: Creating PIM route for (*, 239.194.169.1/32)
2022 Sep 18 04:27:49.861868: E_DEBUG pim [19433]: MRIB Join notify for (*, 239.194.169.1/32)
摘要
- 在常規模式下,流量在第一次通過時到達原始S、G條目,由於傳出介面清單(OIFL)只有環回埠而重新循環。在第二個通道中,它獲取重寫的目標MAC。
- 在第三步中,組播路由查詢在轉換後的S、G上進行,並將資料包轉發到相應的轉換組OIFL埠。
- 新增了環回上的靜態連線,強制在NAT盒上接收流量。
- 當(s1,g1)接收到第一個資料包時,交換機將使用新的SR標誌(s1,g—> s2,g2)對(s1,g1)進行程式設計。
- 交換機將使用此後設資料對資料包進行重新循環,並為g2丟棄該資料包。將(S2、G2)資料包轉發到sup後,在s2、g2的NAT裝置上會觸發FHR(第一跳路由器)功能。
- 收到流量後,即會根據在mcastfwd中列印的pkt建立翻譯前和翻譯後條目。
- 如果您沒有看到各組在mccastfwd中傳送的封包,可以使用上述疑難排解程式來確認是否有興趣的流量到達交換器
相關資訊
.