使用ASAv配置和驗證第2層服務圖配置
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本檔案介紹如何在思科以應用程式為中心的基礎架構(ACI)中設定和驗證第2層服務圖組態。
必要條件
需求
思科建議您瞭解以下主題:
- 瞭解第3層服務圖在ACI中的工作方式
- 瞭解如何在ACI中配置終端策略組、橋接域和合約
- 瞭解如何將(自適應安全裝置虛擬)ASAv配置為透明防火牆
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- APIC版本:6.0(3g)
- 枝葉H/W:N9K-C93180YC-FX
- 枝葉軟體:n9000-16.0(3g)
- 枝葉節點101、102、103
- 在ESXi伺服器上部署的ASAv
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
拓撲
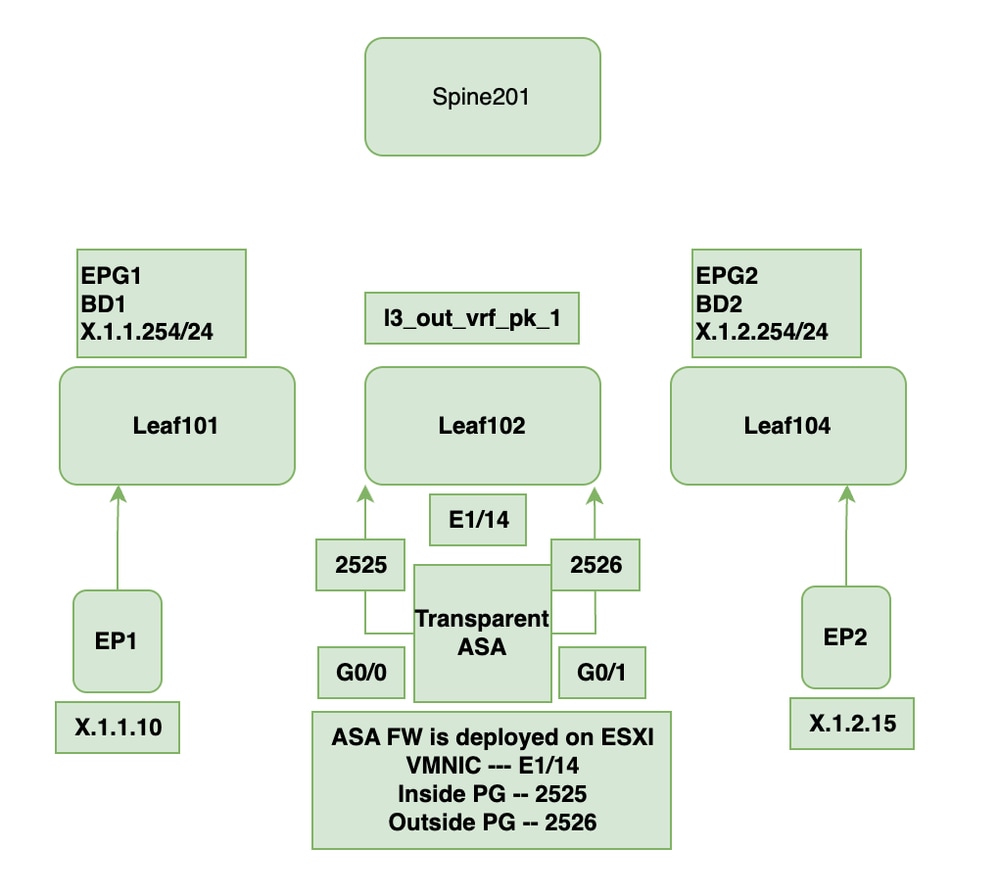 拓撲
拓撲
本文檔中未顯示EPG1和EPG2配置,必須在手動配置之前配置該配置,並且必須學習終結點。
1.驗證EPG1已獲ș知端點X.1.1.10(節點101)。
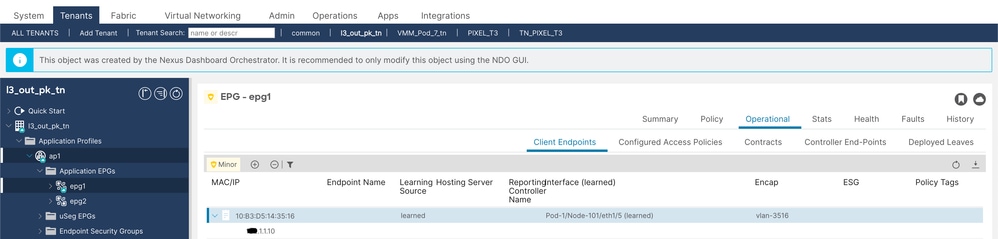 客戶端端點
客戶端端點
2.合約abc由EPG1使用。
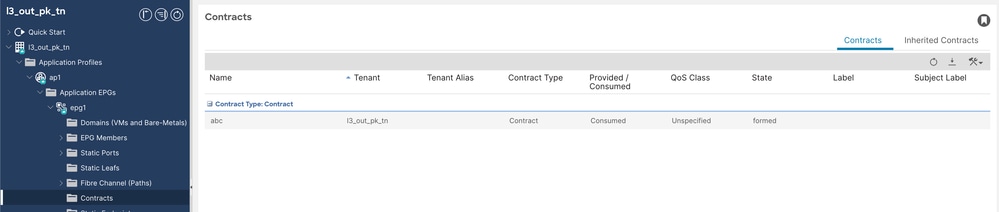 已消耗的合約
已消耗的合約
3.驗證EPG2具有終結點X.1.2.15已學習(節點104)。
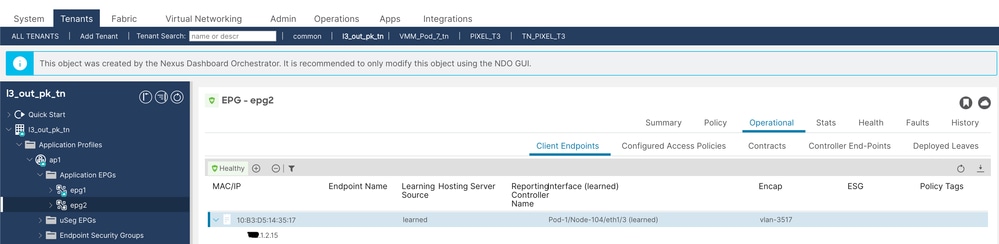 客戶端終結點
客戶端終結點
4.合約abc由EPG2提供。
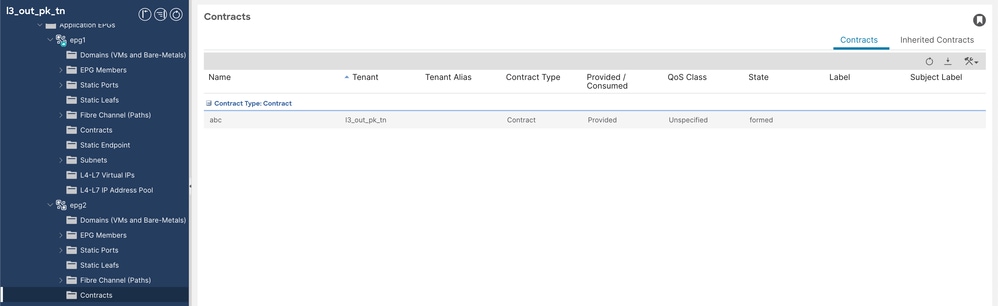 提供的合約
提供的合約
為什麼ACI中需要L2服務圖?
-
在Cisco ACI中,L4-L7服務裝置可插入第3層(L3)、第2層(L2)或第1層(L1)。
-
第3層服務插入:外部裝置(例如防火牆、入侵防禦系統(IPS))根據IP地址制定路由決策並轉發流量。
-
第2層服務插入:根據MAC地址轉發流量,無需路由參與。這對於透明防火牆或IPS裝置非常有用。
-
在ACI中插入L2服務裝置(例如IPS或透明防火牆)時,會使用L2基於策略的路由(PBR)。
-
第3層和第2層PBR的流量轉發機制保持不變。
-
關鍵區別在於:
-
L3 PBR:流量被重定向到IP地址(裝置參與路由)。
-
L2 PBR:流量被重定向到MAC地址(裝置在第2層運行)。
-
-
在第2層PBR中,MAC地址被靜態繫結到枝葉介面,以確保正確的流量轉發。
有關主用/備用或主用/主用L1/L2 PBR使用案例的詳細資訊,請參閱PBR白皮書。
L2服務圖的配置
步驟1.配置名為con-bd1的使用者bd。
必須啟用單播路由,L2未知單播必須設定為硬體代理,並且con和prov網橋域(BD)不需要子網。
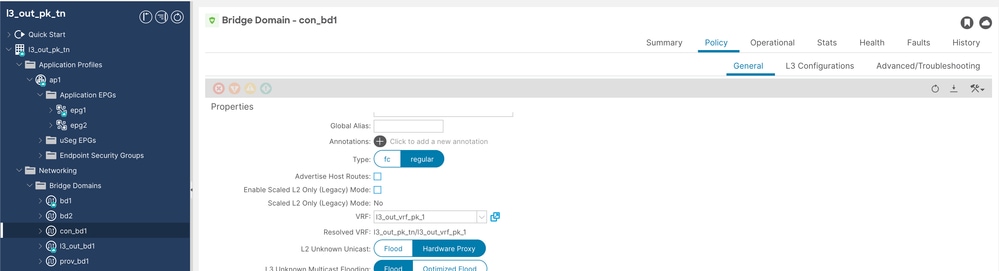 Cons BD配置
Cons BD配置
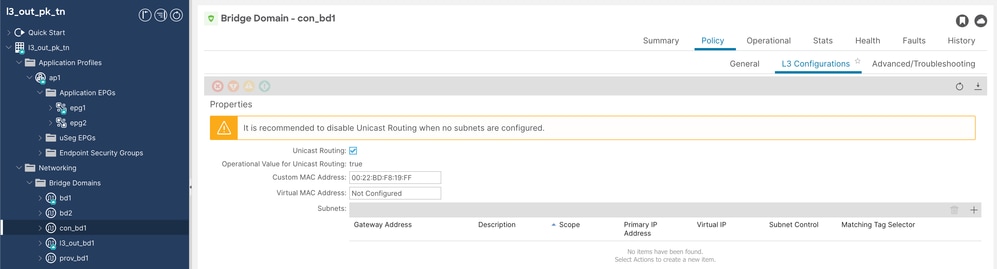 Cons BD配置2
Cons BD配置2
步驟2.配置名為prov-bd1的提供程式bd。
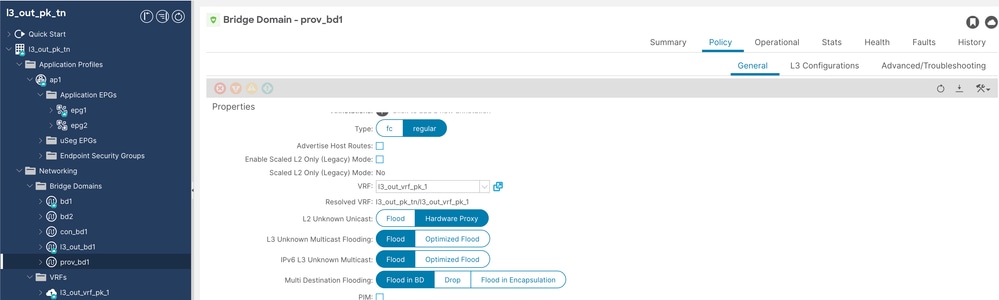 Prov BD配置
Prov BD配置
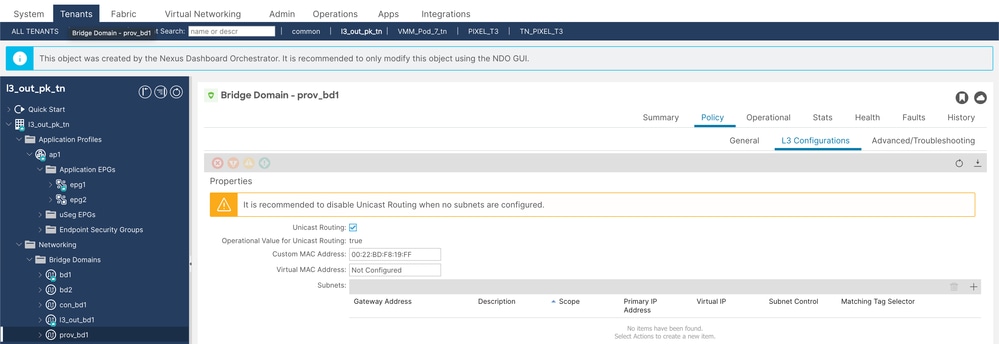 Prov BD Config 2
Prov BD Config 2
步驟3.使用SLA型別L2Ping配置IP服務級別協定(SLA)策略。
導航到Tenant > Policies > Protocol > IP SLA > IP SLA Monitoring Policies,然後按一下右鍵並建立策略。
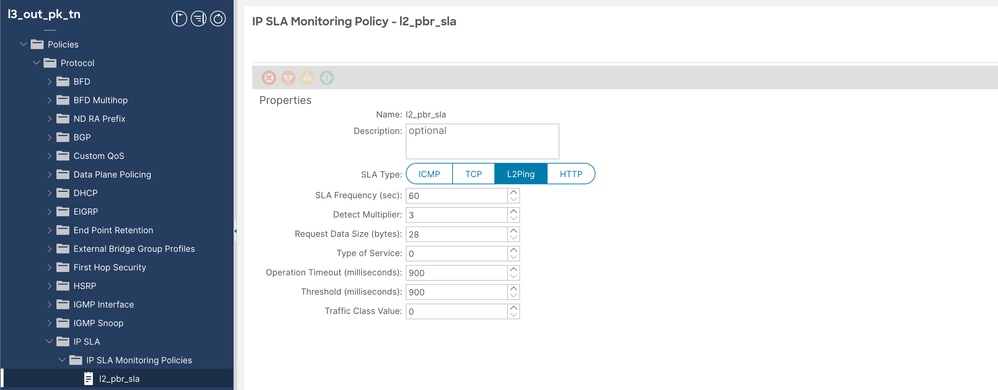 IP SLA策略
IP SLA策略
步驟4.配置第4/7層裝置。
導航到Tenant > Services > Devices,然後按一下右鍵並建立L4-L7裝置。
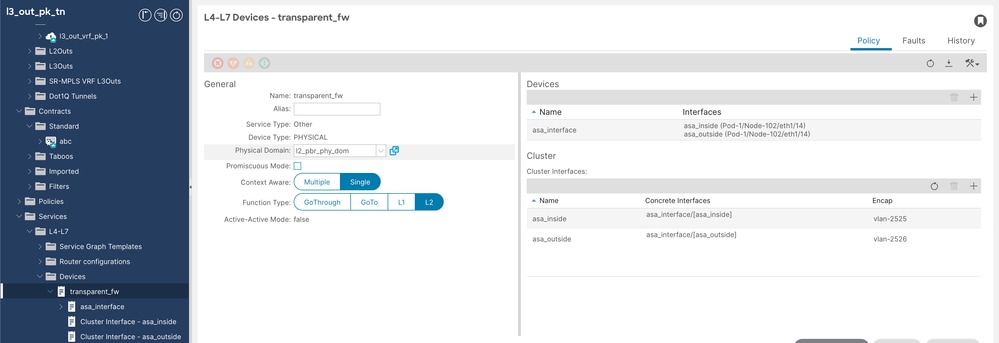 L4-L7裝置
L4-L7裝置
步驟5.驗證基於策略的重定向概述(配置5a和5b後可檢查這一點)。
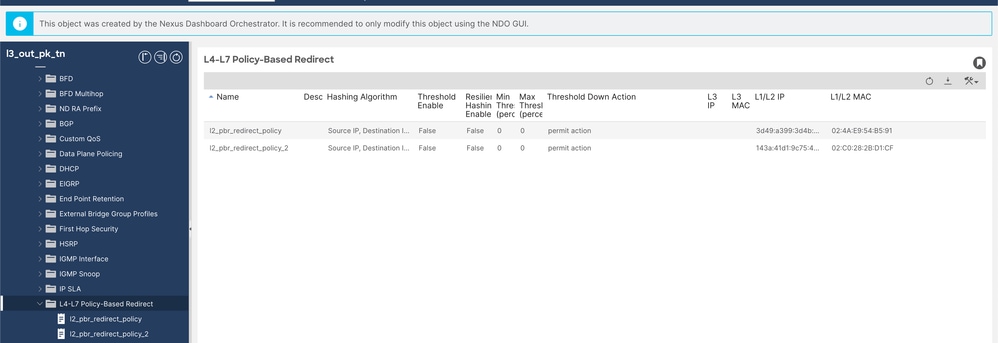 L4-L7重定向策略
L4-L7重定向策略
步驟5.1.為自適應安全裝置(ASA)內部介面配置基於L4-L7策略的重定向策略(無需指定MAC或IP,由APIC自身填充)。
導航到Tenant > Policies > Protocol > L4-L7 Policy based redirect,然後按一下右鍵並創建策略。
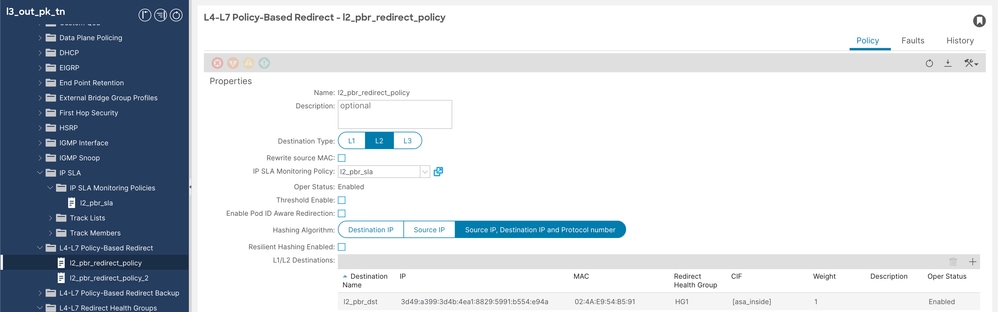 L4-L7重定向策略配置
L4-L7重定向策略配置
步驟5.2.為ASA外部介面配置基於L4-L7策略的重定向策略(無需指定MAC或IP,由APIC自身填充)。
導航到Tenant > Policies > Protocol > L4-L7 Policy based redirect,然後按一下右鍵並創建策略。
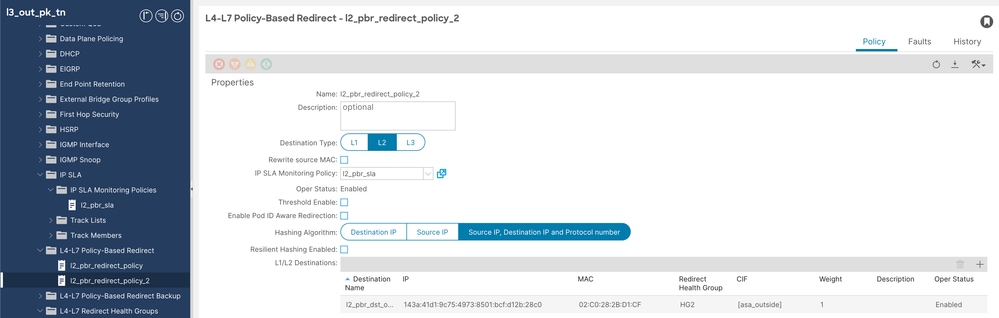 L4-L7重定向策略配置2
L4-L7重定向策略配置2
步驟6.配置服務圖模板。
導航到Tenant > Services > Service Graph Template,然後按一下右鍵並建立L4-L7服務圖形模板。
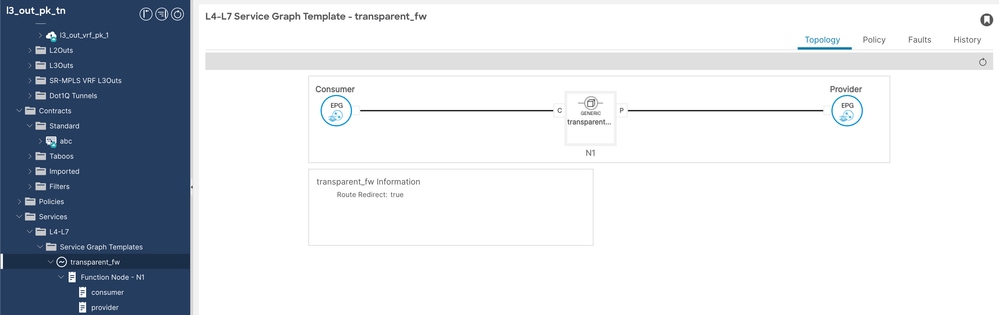 服務圖配置
服務圖配置
步驟7.配置裝置選擇策略。
導航到Tenant > Services > Device Selection Policy,然後按一下右鍵並建立Device Selection Policy。
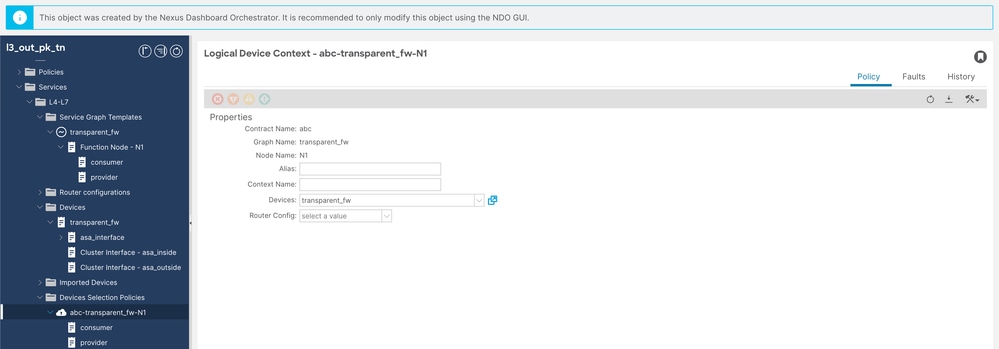 服務圖配置2
服務圖配置2
++ Consumer邏輯介面上下文
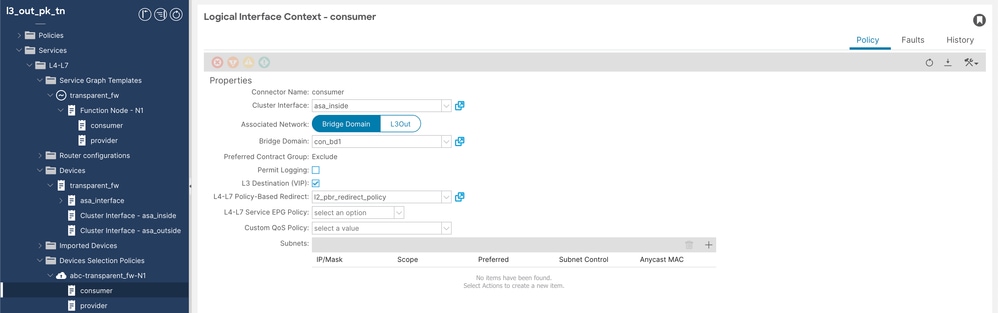 裝置選擇策略使用者配置
裝置選擇策略使用者配置
++ Provider邏輯介面上下文
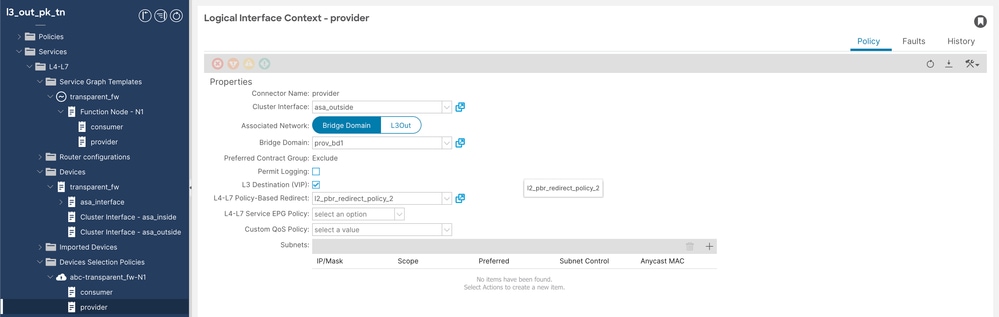 裝置選擇策略提供程式配置
裝置選擇策略提供程式配置

附註:如果將要自動建立裝置選擇策略,則使用Apply Service Graph Option。
步驟8.應用PBR以合約ABC主題。
導航到Tenant > Contract > Contract Subject > L4-L7 Service Graph > transparent_fw。
Con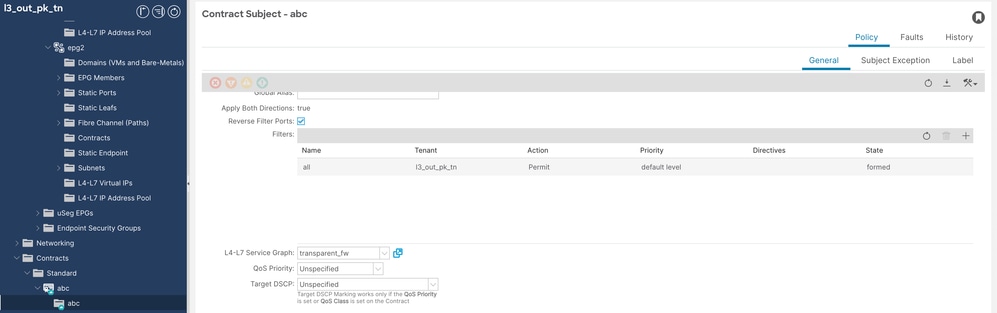 合約配置
合約配置
步驟9.如果部署成功,則在「已部署的例項」圖下驗證(查詢狀態)。
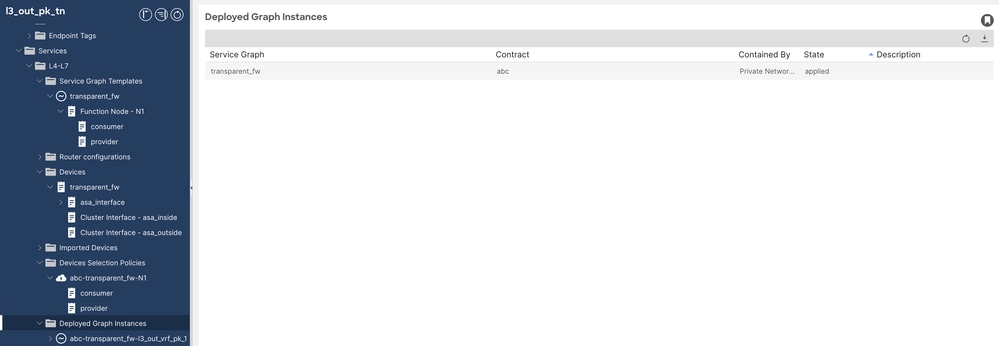 服務圖驗證
服務圖驗證
++驗證群集介面、封裝VLAN和功能聯結器類ID。
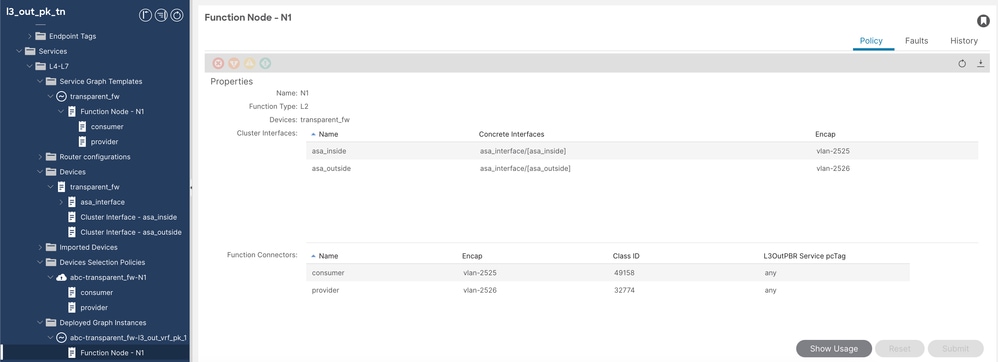 服務圖驗證2
服務圖驗證2
驗證ASA上的L2 PBR流量
從Src端點到dst端點的安全外殼(SSH),您可以在ASA上的連線表條目中看到。
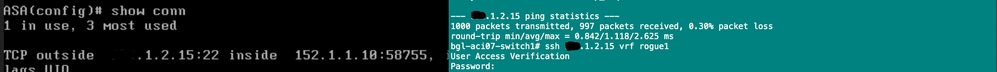 ASA驗證
ASA驗證
檢驗枝葉上的L2 PBR
1.枝葉節點102上的VLAN程式設計。
PBR vlan 2525 and 2526 will get programmed on leaf node 102 and mac addresses will be statically tied to interfaces
bgl-aci07-apic100# fabric 102 show endpoint
----------------------------------------------------------------
Node 102 (bgl-aci07-leaf2)
----------------------------------------------------------------
Legend:
S - static s - arp L - local O - peer-attached
V - vpc-attached a - local-aged p - peer-aged M - span
B - bounce H - vtep R - peer-attached-rl D - bounce-to-proxy
E - shared-service m - svc-mgr
+-----------------------------------+---------------+-----------------+--------------+-------------+
VLAN/ Encap MAC Address MAC Info/ Interface
Domain VLAN IP Address IP Info
+-----------------------------------+---------------+-----------------+--------------+-------------+
28/l3_out_pk_tn:l3_out_vrf_pk_1 vlan-2525 024a.e954.b591 LS eth1/14
1/l3_out_pk_tn:l3_out_vrf_pk_1 vlan-2526 02c0.282b.d1cf LS eth1/14
2.重定向使用者(101)和提供者(104)節點上的策略和分割槽規則。
++ Redirect policy on consumer node
bgl-aci07-apic100# fabric 101 show service redir info
----------------------------------------------------------------
Node 101 (bgl-aci07-leaf1)
----------------------------------------------------------------
===============================================================================================================================================================
LEGEND
TL: Threshold(Low) | TH: Threshold(High) | HP: HashProfile | HG: HealthGrp | BAC: Backup-Dest | TRA: Tracking | RES: Resiliency | W: Weight
===============================================================================================================================================================
List of Dest Groups
GrpID Name destination HG-name BAC W operSt operStQual TL TH HP TRA RES
===== ==== =========== ============== === === ======= ============ === === === === ===
7 destgrp-7 dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224] l3_out_pk_tn::HG1 N 1 enabled no-oper-grp 0 0 sym yes no
8 destgrp-8 dest-[143a:41d1:9c75:4973:8501:bcf:d12b:28c0]-[vxlan-2228224] l3_out_pk_tn::HG2 N 1 enabled no-oper-grp 0 0 sym yes no
List of destinations
Name bdVnid vMac vrf operSt operStQual HG-name
==== ====== ==== ==== ===== ========= =======
dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224] vxlan-16744328 02:4A:E9:54:B5:91 l3_out_pk_tn:l3_out_vrf_pk_1 enabled no-oper-dest l3_out_pk_tn::HG1
dest-[143a:41d1:9c75:4973:8501:bcf:d12b:28c0]-[vxlan-2228224] vxlan-16056296 02:C0:28:2B:D1:CF l3_out_pk_tn:l3_out_vrf_pk_1 enabled no-oper-dest l3_out_pk_tn::HG2
List of Health Groups
HG-Name HG-OperSt HG-Dest HG-Dest-OperSt
======= ========= ======= ==============
l3_out_pk_tn::HG1 enabled dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224]] up
l3_out_pk_tn::HG2 enabled dest-[143a:41d1:9c75:4973:8501:bcf:d12b:28c0]-[vxlan-2228224]] up
List of Backup Destinations
Name primaryDestName DestGroup
==== ============== =========
List of AclRules
AclRuleVnid DestGroup OperSt OperStQual
=========== ========= ====== ==========
++ Zoning rule on consumer Node
bgl-aci07-apic100# fabric 101 show zoning-rule | grep redir
| 4228 | 32771 | 49157 | default | bi-dir | enabled | 2228224 | | redir(destgrp-7) | src_dst_any(9) |
| 4231 | 49157 | 32771 | default | uni-dir-ignore | enabled | 2228224 | | redir(destgrp-8) | src_dst_any(9) |
| 4230 | 32771 | 15 | default | uni-dir | enabled | 2228224 | | redir(destgrp-7) | src_dst_any(9) |
| 4229 | 16386 | 32771 | default | uni-dir | enabled | 2228224 | | redir(destgrp-8) | src_dst_any(9) |
++ Redirect Policy on Provider Node
bgl-aci07-apic100# fabric 104 show service redir info
----------------------------------------------------------------
Node 104 (bgl-aci07-leaf4)
----------------------------------------------------------------
===============================================================================================================================================================
LEGEND
TL: Threshold(Low) | TH: Threshold(High) | HP: HashProfile | HG: HealthGrp | BAC: Backup-Dest | TRA: Tracking | RES: Resiliency | W: Weight
===============================================================================================================================================================
List of Dest Groups
GrpID Name destination HG-name BAC W operSt operStQual TL TH HP TRA RES
===== ==== =========== ============== === === ======= ============ === === === === ===
3 destgrp-3 dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224] l3_out_pk_tn::HG1 N 1 enabled no-oper-grp 0 0 sym yes no
4 destgrp-4 dest-[143a:41d1:9c75:4973:8501:bcf:d12b:28c0]-[vxlan-2228224] l3_out_pk_tn::HG2 N 1 enabled no-oper-grp 0 0 sym yes no
List of destinations
Name bdVnid vMac vrf operSt operStQual HG-name
==== ====== ==== ==== ===== ========= =======
dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224] vxlan-16744328 02:4A:E9:54:B5:91 l3_out_pk_tn:l3_out_vrf_pk_1 enabled no-oper-dest l3_out_pk_tn::HG1
dest-[143a:41d1:9c75:4973:8501:bcf:d12b:28c0]-[vxlan-2228224] vxlan-16056296 02:C0:28:2B:D1:CF l3_out_pk_tn:l3_out_vrf_pk_1 enabled no-oper-dest l3_out_pk_tn::HG2
List of Health Groups
HG-Name HG-OperSt HG-Dest HG-Dest-OperSt
======= ========= ======= ==============
l3_out_pk_tn::HG1 enabled dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224]] up
l3_out_pk_tn::HG2 enabled dest-[143a:41d1:9c75:4973:8501:bcf:d12b:28c0]-[vxlan-2228224]] up
List of Backup Destinations
Name primaryDestName DestGroup
==== ============== =========
++ Zoning rule on provider node
bgl-aci07-apic100# fabric 104 show zoning-rule | grep redir
| 4220 | 32771 | 49157 | default | bi-dir | enabled | 2228224 | | redir(destgrp-3) | src_dst_any(9) |
| 4221 | 49157 | 32771 | default | uni-dir-ignore | enabled | 2228224 | | redir(destgrp-4) | src_dst_any(9) |
L2Ping失敗時出現的故障
如果PBR裝置上的L2ping失敗,您會發現PBR仍處於部署狀態,並且故障F4203、F2833和F2911出現的狀態track/health group已關閉。
捕獲L2 Ping
您可以在tahoe介面上使用tcpdump擷取L2Ping,以便知道是否已正確傳送和接收L2Ping。如果只看到CPU傳輸已傳送但未接收,則上述故障應為預期故障,您必須進一步排除ASA丟棄這些故障的原因(請參閱ASA配置部分)。
Capturing L2Pings using tcpdump on PBR Node 102
bgl-aci07-leaf2# tcpdump -i tahoe0 -w /data/techsupport/l2_pbr1.pcap
tcpdump: listening on tahoe0, link-type EN10MB (Ethernet), capture size 262144 bytes
^C4858 packets captured
4875 packets received by filter
0 packets dropped by kernel
In order to deocde the tcpdump
cat /data/techsupport/l2_pbr1.pcap | knet_parser.py --decode tahoe --pcap | less
** Search for mac 00ab.8752.3100
++ CPU transmit packets
Frame 505
Time: 2024-10-29T05:55:28.707136+00:00
Header: ieth CPU Transmit
sup_tx:1, ttl_bypass:0, opcode:0x0, bd:0x207, outer_bd:0x0, dl:0, span:0, traceroute:0, tclass:5
src_idx:0x0, src_chip:0x0, src_port:0x0, src_is_tunnel:0, src_is_peer:0
dst_idx:0x0, dst_chip:0x0, dst_port:0x0, dst_is_tunnel:0
Len: 72
Eth: 00ab.8752.3100 > 024a.e954.b591, len/ethertype:0x721
Frame 506
Time: 2024-10-29T05:55:28.707297+00:00
Header: ieth CPU Transmit
sup_tx:1, ttl_bypass:0, opcode:0x0, bd:0x208, outer_bd:0x0, dl:0, span:0, traceroute:0, tclass:5
src_idx:0x0, src_chip:0x0, src_port:0x0, src_is_tunnel:0, src_is_peer:0
dst_idx:0x0, dst_chip:0x0, dst_port:0x0, dst_is_tunnel:0
Len: 72
Eth: 00ab.8752.3100 > 02c0.282b.d1cf, len/ethertype:0x721
++CPU recived packets
Frame 509
Time: 2024-10-10T20:16:37.580855+00:00
Header: ieth_extn CPU Receive
sup_qnum:0x33, sup_code:0x4d, istack:ISTACK_SUP_CODE_PBR_TRACK_REFRESH(0x4d)
Header: ieth
sup_tx:0, ttl_bypass:0, opcode:0x0, bd:0x209, outer_bd:0x2, dl:0, span:0, traceroute:0, tclass:0
src_idx:0x32, src_chip:0x0, src_port:0x6, src_is_tunnel:0, src_is_peer:0
dst_idx:0x1, dst_chip:0x0, dst_port:0x3d, dst_is_tunnel:0
Len: 76
Eth: 00ab.8752.3100 > 024a.e954.b591, len/ethertype:0x8100(802.1q)
802.1q: vlan:2526, cos:0, len/ethertype:0x721
Frame 510
Time: 2024-10-10T20:16:37.580891+00:00
Header: ieth_extn CPU Receive
sup_qnum:0x33, sup_code:0x4d, istack:ISTACK_SUP_CODE_PBR_TRACK_REFRESH(0x4d)
Header: ieth
sup_tx:0, ttl_bypass:0, opcode:0x0, bd:0x20a, outer_bd:0x2, dl:0, span:0, traceroute:0, tclass:0
src_idx:0x32, src_chip:0x0, src_port:0x6, src_is_tunnel:0, src_is_peer:0
dst_idx:0x1, dst_chip:0x0, dst_port:0x3d, dst_is_tunnel:0
Len: 76
Eth: 00ab.8752.3100 > 02c0.282b.d1cf, len/ethertype:0x8100(802.1q)
802.1q: vlan:2525, cos:0, len/ethertype:0x721
從Src到Dst端點的流量
++ Endpoint X.1.1.10 want to send traffic to X.1.2.15
++ If destination is not learned on consumer/source leaf, PBR will be performed on destination leaf
++ For this case we are assuming endpoint X.1.2.15 is learned on Leaf 101 so PBR/Redirection will be performed on Leaf101 ( consumer Leaf)
bgl-aci07-apic100# fabric 101 show endpoint
----------------------------------------------------------------
Node 101 (bgl-aci07-leaf1)
----------------------------------------------------------------
Legend:
S - static s - arp L - local O - peer-attached
V - vpc-attached a - local-aged p - peer-aged M - span
B - bounce H - vtep R - peer-attached-rl D - bounce-to-proxy
E - shared-service m - svc-mgr
+-----------------------------------+---------------+-----------------+--------------+-------------+
VLAN/ Encap MAC Address MAC Info/ Interface
Domain VLAN IP Address IP Info
+-----------------------------------+---------------+-----------------+--------------+-------------+
l3_out_pk_tn:l3_out_vrf_pk_1 X.1.2.15 tunnel6 ===> Remote EP Entry
17 vlan-3516 10b3.d514.3516 L eth1/5 ===> Local EP Entry
l3_out_pk_tn:l3_out_vrf_pk_1 vlan-3516 X.1.1.10 L eth1/5
++ EPM entry to get the PC TAG
bgl-aci07-apic100# fabric 101 show system internal epm endpoint ip X.1.1.10
----------------------------------------------------------------
Node 101 (bgl-aci07-leaf1)
---------------------------------------------------------------
MAC : 10b3.d514.3516 ::: Num IPs : 1
IP# 0 : X.1.1.10 ::: IP# 0 flags : ::: l3-sw-hit: No
Vlan id : 17 ::: Vlan vnid : 11792 ::: VRF name : l3_out_pk_tn:l3_out_vrf_pk_1
BD vnid : 16744307 ::: VRF vnid : 2228224
Phy If : 0x1a004000 ::: Tunnel If : 0
Interface : Ethernet1/5
Flags : 0x80005c04 ::: sclass : 32771 ::: Ref count : 5 ==> sclass
EP Create Timestamp : 10/11/2024 09:15:44.430334
EP Update Timestamp : 10/29/2024 10:45:35.458416
EP Flags : local|IP|MAC|host-tracked|sclass|timer|
bgl-aci07-apic100# fabric 101 show system internal epm endpoint ip X.1.2.15
----------------------------------------------------------------
Node 101 (bgl-aci07-leaf1)
----------------------------------------------------------------
MAC : 0000.0000.0000 ::: Num IPs : 1
IP# 0 : X.1.2.15 ::: IP# 0 flags : ::: l3-sw-hit: No
Vlan id : 0 ::: Vlan vnid : 0 ::: VRF name : l3_out_pk_tn:l3_out_vrf_pk_1
BD vnid : 0 ::: VRF vnid : 2228224
Phy If : 0 ::: Tunnel If : 0x18010006
Interface : Tunnel6
Flags : 0x80004400 ::: sclass : 49157 ::: Ref count : 3 ==> sclass
EP Create Timestamp : 10/29/2024 10:38:34.949150
EP Update Timestamp : 10/29/2024 10:45:55.571786
EP Flags : IP|sclass|timer|
++ Traffic will be redirected based on redir(destgrp-7)
bgl-aci07-apic100# fabric 101 show zoning-rule src-epg 32771 dst-epg 49157
----------------------------------------------------------------
Node 101 (bgl-aci07-leaf1)
----------------------------------------------------------------
+---------+--------+--------+----------+--------+---------+---------+------+------------------+----------------+
| Rule ID | SrcEPG | DstEPG | FilterID | Dir | operSt | Scope | Name | Action | Priority |
+---------+--------+--------+----------+--------+---------+---------+------+------------------+----------------+
| 4228 | 32771 | 49157 | default | bi-dir | enabled | 2228224 | | redir(destgrp-7) | src_dst_any(9) |
+---------+--------+--------+----------+--------+---------+---------+------+------------------+----------------+
++ Based on redirect policy traffic will be redirected to mac 02:4A:E9:54:B5:91
bgl-aci07-apic100# fabric 101 show service redir info
----------------------------------------------------------------
Node 101 (bgl-aci07-leaf1)
----------------------------------------------------------------
===============================================================================================================================================================
LEGEND
TL: Threshold(Low) | TH: Threshold(High) | HP: HashProfile | HG: HealthGrp | BAC: Backup-Dest | TRA: Tracking | RES: Resiliency | W: Weight
===============================================================================================================================================================
List of Dest Groups
GrpID Name destination HG-name BAC W operSt operStQual TL TH HP TRA RES
===== ==== =========== ============== === === ======= ============ === === === === ===
7 destgrp-7 dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224] l3_out_pk_tn::HG1 N 1 enabled no-oper-grp 0 0 sym yes no
List of destinations
Name bdVnid vMac vrf operSt operStQual HG-name
==== ====== ==== ==== ===== ========= =======
dest-[3d49:a399:3d4b:4ea1:8829:5991:b554:e94a]-[vxlan-2228224] vxlan-16744328 02:4A:E9:54:B5:91 l3_out_pk_tn:l3_out_vrf_pk_1 enabled no-oper-dest l3_out_pk_tn::HG
1
++ PBR mac addresses are never learnt remotely as IP/MAC learning is disabled for PBR BD
++ PBR mac addresses are statically binded to interfaces where L4/L7 device is connected and reported to Spine COOP
++ Traffic will be forwarded to SPINE PROXY
++ Spine has an COOP entry for 02:4A:E9:54:B5:91
bgl-aci07-apic100# fabric 201 show coop internal info repo ep key 16744328 02:4A:E9:54:B5:91
----------------------------------------------------------------
Node 201 (bgl-aci07-spine1)
----------------------------------------------------------------
Repo Hdr Checksum : 49503
Repo Hdr record timestamp : 10 29 2024 10:15:07 658496921
Repo Hdr last pub timestamp : 10 29 2024 10:15:07 661679296
Repo Hdr last dampen timestamp : 01 01 1970 00:00:00 0
Repo Hdr dampen penalty : 0
Repo Hdr flags : IN_OBJ ACTIVE
EP bd vnid : 16744328
EP mac : 02:4A:E9:54:B5:91 <<<<========== ASA MAC
flags : 0x480
repo flags : 0x102
Vrf vnid : 2228224
PcTag : 0x100c006
EVPN Seq no : 0
Remote publish timestamp: 01 01 1970 00:00:00 0
Snapshot timestamp: 10 29 2024 10:15:07 658496921
Tunnel nh : 10.0.144.66
MAC Tunnel : 10.0.144.66
IPv4 Tunnel : 10.0.144.66
IPv6 Tunnel : 10.0.144.66
ETEP Tunnel : 0.0.0.0
num of active ipv4 addresses : 0
num of anycast ipv4 addresses : 0
num of ipv4 addresses : 0
num of active ipv6 addresses : 0
num of anycast ipv6 addresses : 0
num of ipv6 addresses : 0
Primary Path:
Current published TEP : 10.0.144.66
Backup Path:
BackupTunnel nh : 0.0.0.0
Current Backup (publisher_id): 0.0.0.0
Anycast_flags : 0
Current citizen (publisher_id): 10.0.144.66
Previous citizen : 10.0.144.66
Prev to Previous citizen : 10.0.144.66
Synthetic Flags : 0x5
Synthetic Vrf : 411
Synthetic IP : X.X.83.223
Tunnel EP entry: 0x7f20900167a8
Backup Tunnel EP entry: (nil)
TX Status: COOP_TX_DONE\
Damp penalty: 0
Damp status: NORMAL
Exp status: 0
Exp timestamp: 01 01 1970 00:00:00 0
Hash: 3209430840 owner: 10.0.144.65
++ Spine will forward this to PBR Leaf Node 102 based on COOP entry
++ PBR Leaf Node will forward this to ASA FW on interface E1/14
++ ASA FW will forward the traffic based on mac address table and send it back to PBR Leaf Node 102
++ PBR Leaf Node will look for Dst IP in the traffic and route it to Leaf 104 if remote endpoint entry exist else will do spine proxy
++ Leaf 104 will get this traffic forwarded to actual EP X.1.2.15 (Leaf4 does not learn the client IP address from this traffic because Endpoint Dataplane Learning is disabled for the PBR node bridge domain)
ASA配置
步驟1.介面配置。
ASA(config)# show running-config interface
!
interface GigabitEthernet0/0
bridge-group 1
nameif inside
security-level 100
!
interface GigabitEthernet0/1
bridge-group 1
nameif outside
security-level 0
!
interface BVI1
ip address 192.168.100.1 255.255.255.0 ==> In case BVI IP is not defined ASA will not switch the packets
!
步驟2.必須禁用MAC學習。
ASA(config)# show run mac-learn
mac-learn inside disable
mac-learn outside disable
PBR:
步驟3.用於PBR Mac的靜態mac地址表。
The mac statically binded to inside interface is the PBR mac generated by provider and vice versa
ASA(config)# show run mac-address-table
mac-address-table static outside 024a.e954.b591
mac-address-table static inside 02c0.282b.d1cf
步驟4.設定存取控制清單(ACL)以便通過L2ping。
ASA(config)# show access-list
access-list L2_PBR ethertype permit 721
ASA(config)# show run access-group
access-group L2_PBR in interface inside
access-group L2_PBR in interface outside
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
07-Apr-2025
|
初始版本 |
由思科工程師貢獻
- 皮尤什·卡塔利亞Cisco TAC工程師
 意見
意見