令牌缓存设计和实施指南
目录
简介
本文档的范围是讨论TokenCaching的设置和故障排除。用于ISDN终端适配器(TA)用户的点对点协议(PPP)会话通常在用户PC上终止。这允许用户以与异步(调制解调器)拨号连接相同的方式控制PPP会话,这意味着可根据需要连接和断开会话。这允许用户使用密码身份验证协议(PAP)输入一次性密码(OTP)进行传输。
但是,如果第二个B信道设计为自动启动,则必须提示用户为第二个B信道设置新的OTP。PC PPP软件不收集第二个OTP。相反,软件会尝试使用与主B信道相同的密码。令牌卡服务器在设计上拒绝重复使用OTP。CiscoSecure ACS for UNIX(版本2.2及更高版本)和CiscoSecure ACS for Windows (2.1及更高版本)执行TokenCaching以支持在第二个B信道上使用相同的OTP。此选项要求身份验证、授权和记帐(AAA)服务器维护有关令牌用户连接的状态信息。
有关详细信息,请参阅支持ISDN上的一次性密码。
先决条件
要求
本文档假设您已正确配置以下内容:
-
工作正常的拨号调制解调器。
-
网络接入服务器(NAS)已正确配置,AAA指向CiscoSecure ACS UNIX或ACS Windows。
-
ACE/SDI已通过CiscoSecure ACS UNIX或ACS Windows进行设置,且工作正常。
使用的组件
本文档中的信息基于以下软件和硬件版本:
-
CiscoSecure ACS Unix 2.2或更高版本
-
CiscoSecure ACS Windows 2.1或更高版本
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您使用的是真实网络,请确保您已经了解所有命令的潜在影响。
规则
有关文档规则的详细信息,请参阅 Cisco 技术提示规则。
配置
本部分提供有关如何配置本文档所述功能的信息。
注意:要获取此部分中所用命令的更多信息,可使用命令查找工具(仅限已注册客户)。
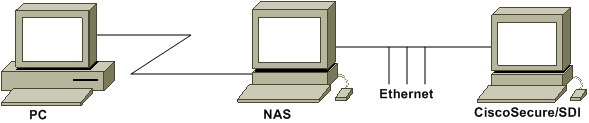
网络图
本文档使用以下网络设置:
PC拨入NAS和ISDN调制解调器,并配置用于ppp multilink命令。
配置
本文档使用以下配置:
配置用户名和密码输入
在本文档中,NAS对PPP会话使用质询握手身份验证协议(CHAP)以及SDI一次性密码。如果使用CHAP,请按照以下形式输入密码:
-
username - fadi*pin+code(注意用户名中的*)
-
password—chappassword
例如:username = fadi,chap password = cisco,pin = 1234,令牌上显示的代码为987654。因此,用户输入以下内容:
-
用户名— fadi*1234987654
-
口令 — cisco
注意:如果为PAP配置了CiscoSecure和NAS,则可以按如下方式输入用户名和令牌:
-
username - username*pin+code
-
密码—
或者:
-
username -用户名
-
密码- pin+code
在CiscoSecure ACS Windows上配置令牌缓存
CiscoSecure ACS Windows用户或组设置如常,如果使用TACACS+,则选中PPP IP和PPP LCP。如果使用RADIUS,则必须配置以下内容:
-
属性6 = Service_Type =成帧
-
属性7 = Framed_Protocol = PPP
此外,还可以检查组的TokenCaching参数,如本示例所示:
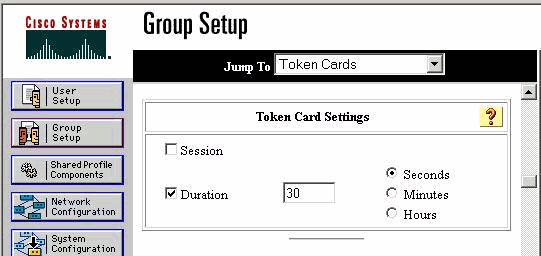
在CiscoSecure ACS UNIX中配置TokenCaching
有四个TokenCaching属性。在$install_directory/config/CSU.cfg文件中设置了config_token_cache_absolute_timeout属性(以秒为单位)。其他三个属性(set server token-caching、set server token-caching-expire-method和set server token-caching-timeout)是在用户或组配置文件中设置的。对于本文档,在$install_directory/config/CSU.cfg文件中将全局属性config_token_cache_absolute_timeout设置为以下值:
NUMBER config_token_cache_absolute_timeout = 300;
用户和组服务器TokenCaching属性配置文件已按本示例所示进行配置:
Group Profile:
Group Profile Information
group = sdi{
profile_id = 42
profile_cycle = 5
default service=permit
set server token-caching=enable
set server token-caching-expire-method=timeout
set server token-caching-timeout=30
set server max-failed-login-count=1000
}
User Profile:
user = fadi{
profile_id = 20
set server current-failed-logins = 0
profile_cycle = 168
member = sdi
profile_status = enabled
password = chap "********"
password = sdi
password = pap "********"
password = clear "********"
default service=permit
set server max-failed-login-count=1000
!--- The TACACS+ section of the profile.
service=ppp {
default protocol=permit
protocol=ip {
set addr=1.1.1.1
}
protocol=lcp {
}
!--- This allows the user to use the ppp multilink command.
protocol=multilink {
}
}
service=shell {
default attribute=permit
}
!--- The RADIUS section of the profile.
radius=Cisco12.05 {
check_items= {
200=0
}
}
}
验证
当前没有可用于此配置的验证过程。
故障排除
本部分提供的信息可用于对配置进行故障排除。
CiscoSecure ACS UNIX上的Debug TokenCaching
此CiscoSecure UNIX日志显示在两个BRI信道上发生身份验证时使用TokenCaching成功进行身份验证:
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AUTHENTICATION START request
(e7079cae)
!--- Detects the * in the username.
Jun 14 13:44:29 cholera CiscoSecure: INFO - The character * was found
in username: username=fadi,passcode=3435598216
!--- Initializes ACE modules in CiscoSecure.
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - sdi_challenge response timeout 5
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceInit()
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceInit(17477), ace rc=150,
ed=1039800
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - acsWaitForSingleObject
(17477) begin
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - aceCB(17477)
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - aceCB(17477) AceGetUserData,
ace rc=1, ed=1039800
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - aceCB(17477):
AceGetAuthenticationStatus, ace rc=1, acm rc=0
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - aceCB(17477): return
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - acsWaitForSingleObject(0) (17477)
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - acsWaitForSingleObject
(17477) end, rc=0
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceInit(17477), continue, acm rc=0
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceSetUsername(17477),
username=fadi
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceSetUsername(17477), ace rc=1
Jun 14 13:44:29 cholera CiscoSecure: INFO - sdi_challenge(17477): rtn 1,
state=GET_PASSCODE, user=fadi
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - Token Caching. timeout_value is: 30
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - Token Caching.
timeout enabled value: 30
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - profile_valid_tcaching TRUE ending.
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - Token Caching. MISS.
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceSetPasscode(17477),
passcode=3435598216
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceSetPasscode(17477), ace rc=1
!--- Checks credentials with ACE server.
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceCheck(17477)
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - AceCheck(17477), ace rc=150
Jun 14 13:44:29 cholera CiscoSecure: DEBUG - acsWaitForSingleObject
(17477) begin
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(17477)
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(17477) AceGetUserData,
ace rc=1, ed=1039800
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(17477):
AceGetAuthenticationStatus, ace rc=1, acm rc=0
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(17477): return
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - acsWaitForSingleObject(0) (17477)
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - acsWaitForSingleObject (17477) end,
rc=0
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceCheck(17477), continue, acm rc=0
Jun 14 13:44:31 cholera CiscoSecure: INFO - sdi_verify(17477):
fadi authenticated by ACE Srvr
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceClose(17477)
Jun 14 13:44:31 cholera CiscoSecure: INFO - sdi(17477):
fadi free external_data memory, state=GET_PASSCODE
!--- The TokenCaching timeout is set to 30 seconds.
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Token Caching. timeout_value is: 30
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Token Caching.
timeout enabled value: 30
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - profile_valid_tcaching TRUE ending.
!--- The TokenCaching takes place.
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - cache_insert
(key<4>, val<10><3435598216>, port_type<3>)
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Cisco Cached Tokens : 1
Jun 14 13:44:31 cholera CiscoSecure: INFO - sdi_verify(17477): rtn 1
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Authentication - LOGIN successful;
[NAS=lynch.cisco.com, Port=BRI0:1, User=fadi, Priv=1]
!--- The authentication of the second BRI channel begins.
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AUTHENTICATION START request (76f91a6c)
Jun 14 13:44:31 cholera CiscoSecure: INFO - The character * was found in username:
username=fadi,passcode=3435598216
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - sdi_challenge response timeout 5
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceInit()
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceInit(29111), ace rc=150, ed=1039984
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - acsWaitForSingleObject (29111) begin
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(29111)
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(29111) AceGetUserData, ace rc=1,
ed=1039984
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(29111): AceGetAuthenticationStatus,
ace rc=1, acm rc=0
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - aceCB(29111): return
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - acsWaitForSingleObject(0) (29111)
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - acsWaitForSingleObject (29111) end, rc=0
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceInit(29111), continue, acm rc=0
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceSetUsername(29111), username=fadi
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceSetUsername(29111), ace rc=1
Jun 14 13:44:31 cholera CiscoSecure: INFO - sdi_challenge(29111): rtn 1,
state=GET_PASSCODE, user=fadi
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Token Caching. timeout_value is: 30
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Token Caching. timeout enabled value: 30
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - profile_valid_tcaching TRUE ending.
!--- Checks with the cached token for the user "fadi".
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Token Caching. USER : fadi
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - PASSWORD : 3435598216 len: 10
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - hashval_str: 3435598216 len: 10
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - port_type : BRI len: 3
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Token Caching. HIT.
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - AceClose(29111)
Jun 14 13:44:31 cholera CiscoSecure: INFO - sdi(29111): fadi free external_data memory,
state=GET_PASSCODE
Jun 14 13:44:31 cholera CiscoSecure: INFO - sdi_verify(29111): rtn 1
Jun 14 13:44:31 cholera CiscoSecure: DEBUG - Authentication - LOGIN successful;
[NAS=lynch.cisco.com, Port=BRI0:2, User=fadi, Priv=1]
!--- After 30 seconds the cached token expires.
Jun 14 13:45:03 cholera CiscoSecure: DEBUG - Expiring Cisco Token Cache Entry
Jun 14 13:45:03 cholera CiscoSecure: DEBUG - Cisco Cached Tokens : 0
相关信息
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
29-Nov-2001 |
初始版本 |
 反馈
反馈