使用Qualys配置ISE 2.1以威胁为中心的NAC (TC-NAC)
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
目录
简介
本文档介绍如何在身份服务引擎(ISE) 2.1上使用Qualys配置以威胁为中心的NAC。利用以威胁为中心的网络访问控制(TC-NAC)功能,您可以根据从威胁和漏洞适配器接收的威胁和漏洞属性创建授权策略。
先决条件
要求
Cisco 建议您具有以下主题的基础知识:
-
思科身份服务引擎
-
Qualys ScanGuard
使用的组件
本文档中的信息基于以下软件和硬件版本:
- 思科身份服务引擎版本2.1
- 无线局域网控制器(WLC) 8.0.121.0
- Qualys防护扫描程序8.3.36-1,签名2.3.364-2
- Windows 7 Service Pack 1
配置
高级流程图
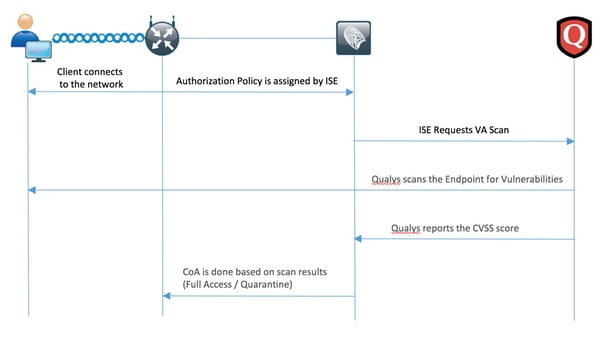
流程如下:
- 客户端连接到网络,授予有限的访问权限,并且分配已启用Assess Vulnerabilities复选框的配置文件
- PSN节点向MNT节点发送系统日志消息,确认身份验证已发生并且VA扫描是授权策略的结果
- MNT节点使用以下数据向TC-NAC节点(使用管理WebApp)提交扫描:
-Mac 地址
-IP Address
- 扫描间隔
- 定期扫描已启用
- 始发PSN - Qualys TC-NAC(封装在Docker容器中)与Qualys云(通过REST API)通信以在需要时触发扫描
- Qualys云指示Qualys扫描程序扫描终端
- Qualys扫描程序将扫描结果发送到Qualys云
- 扫描结果发送回TC-NAC:
-Mac 地址
- 所有CVSS评分
- 所有漏洞(QID、标题、CVEID) - TC-NAC使用步骤7中的所有数据更新PAN。
- 如果需要,将根据配置的授权策略触发CoA。
配置Qualys云和扫描仪
注意:本文档中的Qualys配置用于实验目的,请咨询Qualys工程师以了解设计注意事项
步骤1:部署Qualys扫描程序
可以从OVA文件部署Qualys扫描仪。登录到Qualys云,然后导航到Scans > Appliances并选择New > Virtual Scanner Appliance
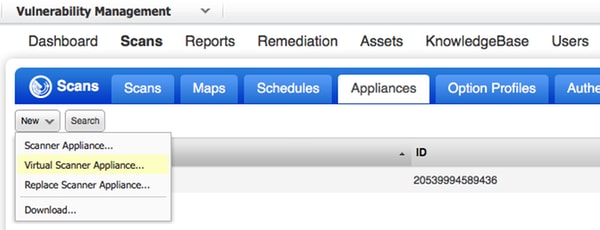
选择Download Image Only并选择适当的分发
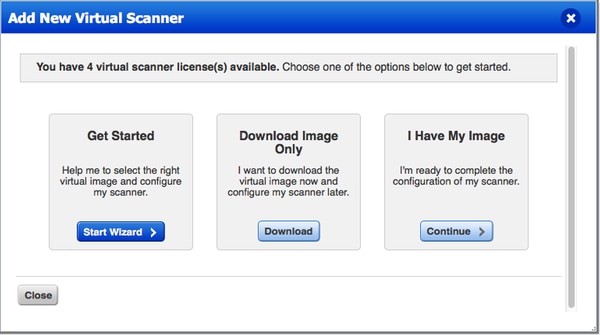
要获取激活代码,您可以转到扫描(Scans) >设备(Appliances),然后依次选择新建(New) >虚拟扫描器设备(Virtual Scanner Appliance),并选择我的映像(I Have My Image)
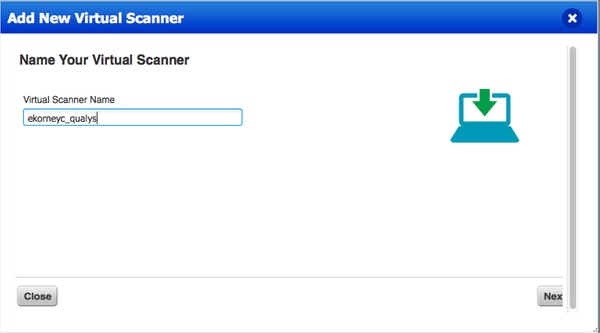
输入扫描仪名称后,您会获得授权码,稍后将使用该授权码。
第二步:配置Qualys扫描程序
在您选择的虚拟化平台上部署OVA。完成后,配置这些设置:
- 设置网络(LAN)
- WAN接口设置(如果使用两个接口)
- 代理设置(如果使用代理)
- 个性化此扫描仪
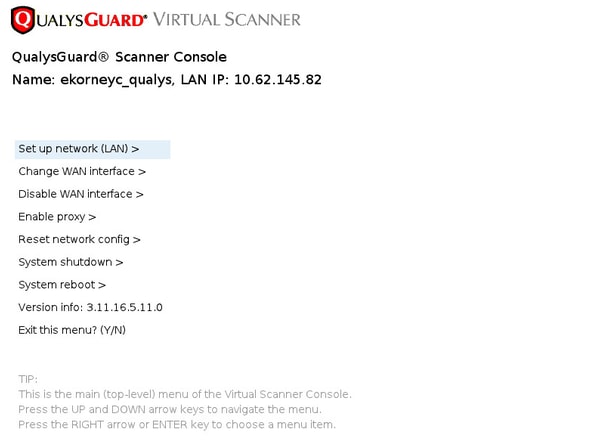
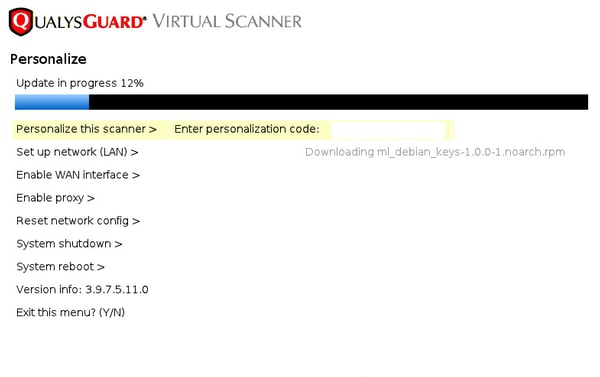
然后,扫描仪连接到Qualys并下载最新的软件和签名。
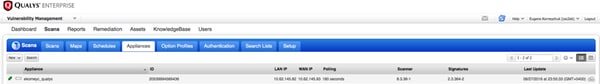
要验证扫描仪是否已连接,可以导航到Scans > Appliances。
左侧的绿色连接符号表示扫描仪已就绪,您还可以看到LAN IP、WAN IP、扫描仪版本和签名。
配置ISE
虽然您已配置Qualys扫描程序和云,但仍需调整云设置以确保与ISE的集成正常工作。注意,应在通过GUI配置适配器之前完成此步骤,因为在首次配置适配器之后会下载包含CVSS评分的知识库。
步骤1:调整Qualys云设置以便与ISE集成
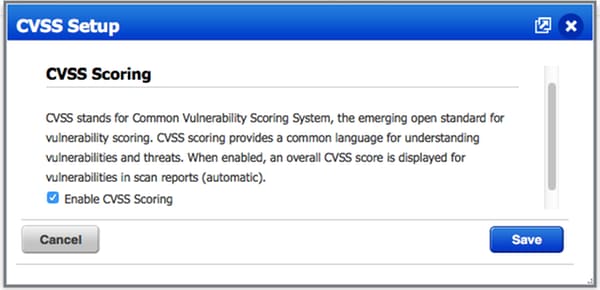
- 在漏洞管理>报告>设置> CVSS >启用CVSS评分时启用CVSS评分
- 确保适配器配置中使用的用户凭证具有管理员权限。从左上角选择用户,然后单击User Profile。您在用户角色中应具有管理员权限。
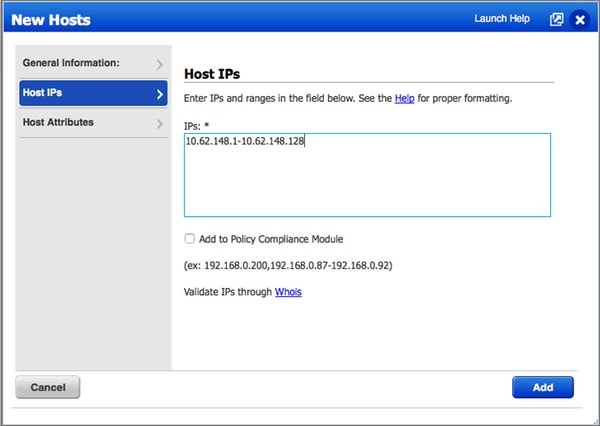
- 确保在Vulnerability Management > Assets > Host Assets > New > IP Tracked Hosts中将需要漏洞评估的终端的IP地址/子网添加到Qualys
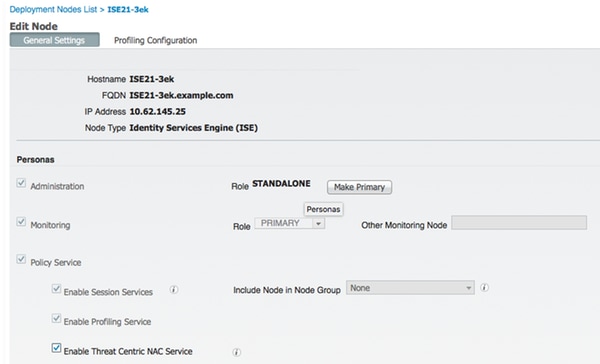
第二步:启用TC-NAC服务
在Administration > Deployment > Edit Node下启用TC-NAC服务。检查 复选框。
注意:每个部署只能有一个TC-NAC节点。
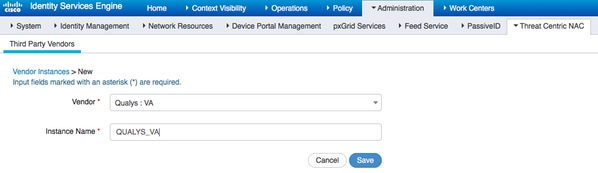
第三步:配置Qualys适配器与ISE VA框架的连接
导航到Administration > Threat Centric NAC > Third Party Vendors > Add。单击Save。
当Qualys实例转换为准备配置状态时,点击状态中的准备配置选项。
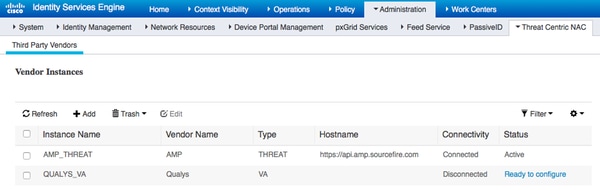
REST API主机应该是您的帐户所在的Qualys云使用的主机。在本示例中- qualysguard.qg2.apps.qualys.com
帐户应该是拥有管理员权限的帐户,然后单击Next。
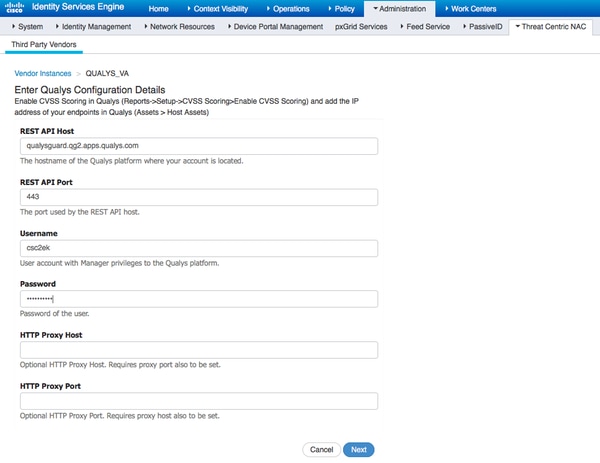
ISE下载有关连接到Qualys云的扫描仪的信息,您可以在此页面上配置PSN到扫描仪的映射。它确保根据授权终端的PSN选择选定的扫描仪。
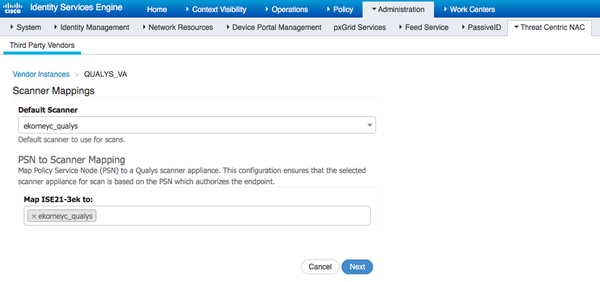
高级设置在《ISE 2.1管理员指南》中有详细介绍,链接可在本文档的“参考”部分找到。单击下一步和完成。Qualys实例转换为活动状态,并开始下载知识库。
注意:每个部署只能有一个Qualys实例。
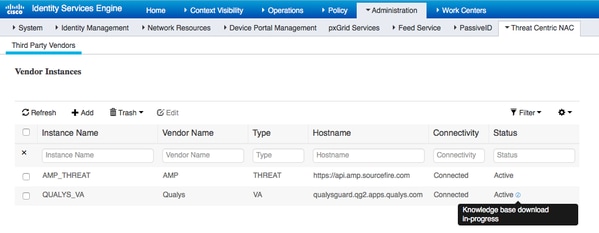
第四步:配置授权配置文件以触发VA扫描
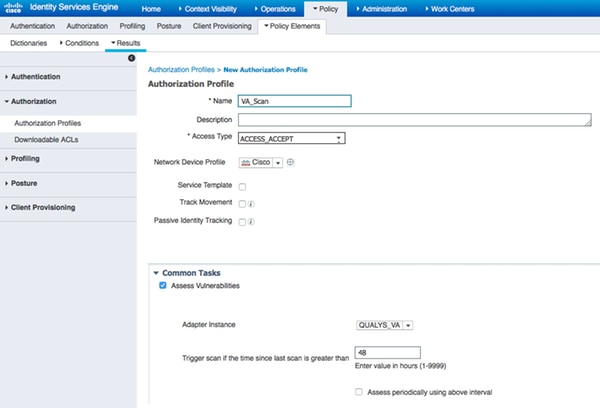
导航至Policy > Policy Elements > Results > Authorization > Authorization Profiles。添加新配置文件.在Common Tasks下,选中Vulnerability Assessment复选框。
按需扫描间隔应根据您的网络设计选择。
授权配置文件包含这些av对:
cisco-av-pair = on-demand-scan-interval=48
cisco-av-pair = periodic-scan-enabled=0
cisco-av-pair = va-adapter-instance=796440b7-09b5-4f3b-b611-199fb81a4b99
它们被发送到Access-Accept数据包中的网络设备,尽管它们的真正目的是告知MNT节点应该触发扫描。MNT指示TC-NAC节点与Qualys云通信。
第五步:配置授权策略
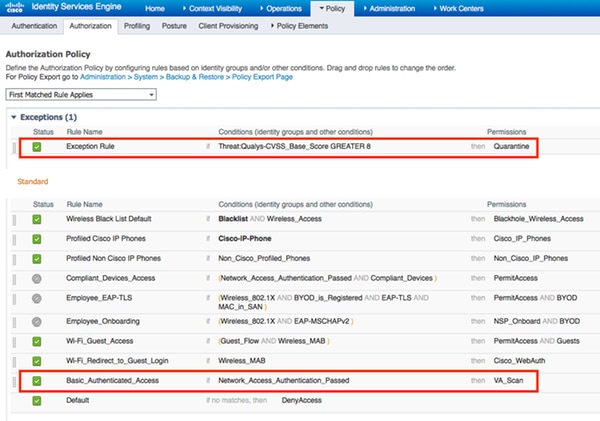
- 配置授权策略以使用步骤4中配置的新授权配置文件。导航到Policy > Authorization > Authorization Policy,找到Basic_Authenticated_Access规则,然后单击Edit。将权限从PermitAccess更改为新创建的标准VA_Scan。这会导致对所有用户进行漏洞扫描。单击Save。
- 为隔离的计算机创建授权策略。导航到策略>授权>授权策略>例外并创建例外规则。单击Conditions > Create New Condition (Advanced Option) > Select Attribute,向下滚动并选择Threat。展开Threat属性并选择Qualys-CVSS_Base_Score。将运算符更改为大于,然后根据您的安全策略输入值。隔离授权配置文件应提供对易受攻击计算机的有限访问权限。
验证
身份服务引擎
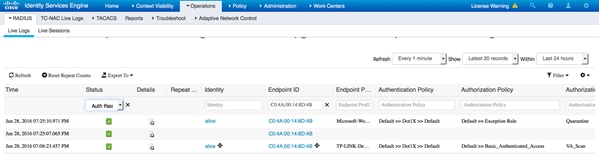
第一个连接触发VA扫描。扫描完成后,如果匹配,将触发CoA重新身份验证以应用新策略。
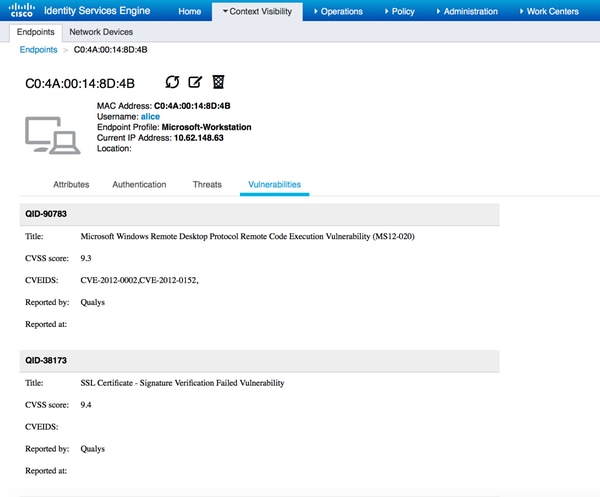
要验证检测到哪些漏洞,请导航到Context Visibility > Endpoints。使用Qualys向其提供的分数检查每个终端的漏洞。
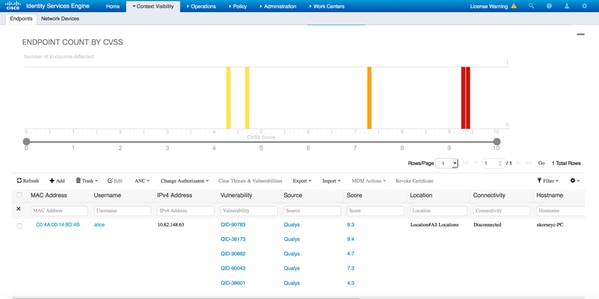
选择特定终端时,会显示有关每个漏洞的更多详细信息,包括Title和CVEID。
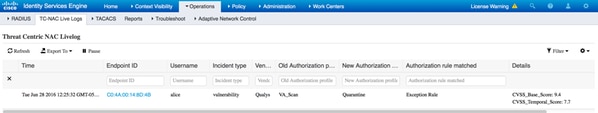
在操作(Operations) > TC-NAC实时日志(TC-NAC Live Logs)中,您可以查看应用的旧与新授权策略以及CVSS_Base_Score的详细信息。
注意:授权条件基于CVSS_Base_Score完成,CVSS_Base_Score等于在终端上检测到的最高漏洞得分。
Qualys云
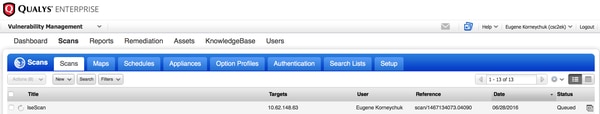
当VA扫描由TC-NAC Qualys队列触发时,可以在扫描>扫描中查看该扫描
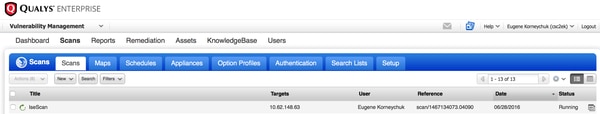
然后,它过渡到Running,这意味着Qualys云已指示Qualys扫描程序执行实际扫描
当扫描仪执行扫描时,您应该看到Qualys Guard右上角的“Scanning...”(扫描。.)符号
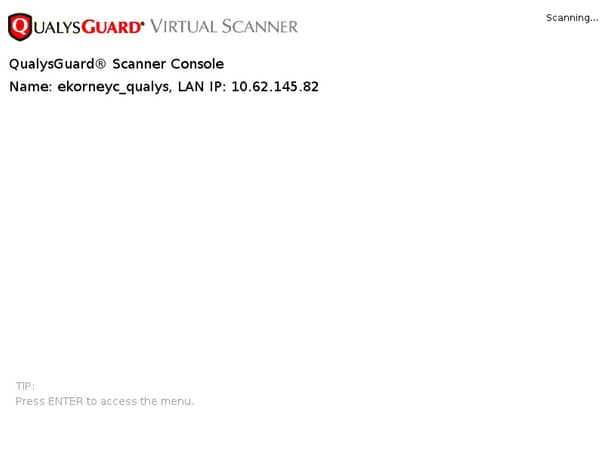
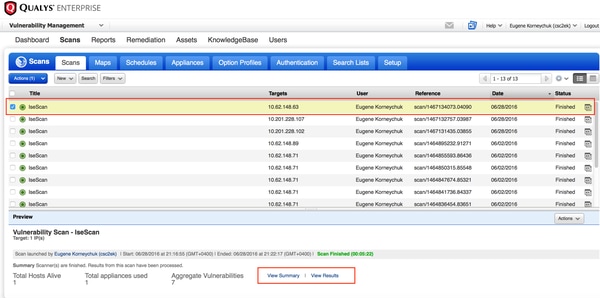
完成扫描后,扫描将转换为“已完成”状态。您可以查看扫描>扫描的结果,选择所需的扫描并单击View Summary或View Results。
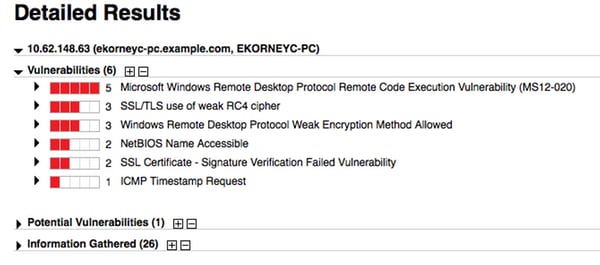
在报告本身中,您可以看到详细结果,其中显示了检测到的漏洞。
故障排除
ISE上的调试
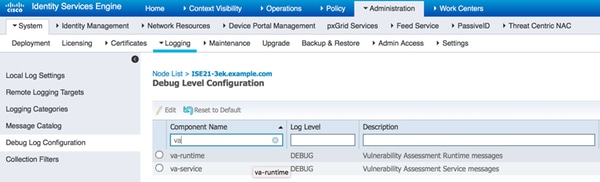
要在ISE上启用调试,请导航到管理>系统>记录>调试日志配置,选择TC-NAC节点并将日志级别va-runtime和va-service组件更改为调试
要检查的日志- varuntime.log。您可以直接从ISE CLI对其进行跟踪:
ISE21-3ek/admin# show logging application varuntime.log tail
TC-NAC Docker收到对特定终端执行扫描的指令。
2016-06-28 19:06:30,823 DEBUG [Thread-70][] va.runtime.admin.mnt.EndpointFileReader -::::- VA:通过运行时读取。[{"operationType":1,"macAddress":"C0:4A:00:14:8D:4B","ondemandScanInterval":"48","isPeriodicScanEnabled":false,"periodicScanEnabledString":"0","vendorInstance":"796440b7-09b5-4f3b-b611-199fb81a4b99","psnHostName":"ise 21-3ek","heartBeatTime":0,"lastScanTime":0}]
2016-06-28 19:06:30,824 DEBUG [Thread-70][] va.runtime.admin.vaservice.VaServiceRemotingHandler -:::- VA:从Mnt接收数据: {"operationType":1,"macAddress":"C0:4A:00:14:8D:4B","ondemandScanInterval":"48","isPeriodicScanEnabled", false" "periodicScanEnabledString":"0","vendorInstance":"796440b7-09b5-4f3b-b611-199fb81a4b99","psnHostName":"ISE21-3ek","heartBeatTime":0,"lastScanTime":0}
收到结果后,会将所有漏洞数据存储在Context Directory中。
2016-06-28 19:25:02,020 DEBUG [pool-311-thread-8][] va.runtime.admin.vaservice.VaServiceMessageListener -::::-从VaService获取消息: [{"macAddress":"C0:4A:00:14:8D:4B","ipAddress":"10.62.148.63","lastScanTime" 1467134394000,"vulnerabilities":["{\"vulnerabilityId\":\"QID-90783\",\"cveIds\":\"CVE-2012-0002,CVE-2012-0152,\",\"cvssBaseScore\":\"9.3\",\"cvssTemporalScore\":\"7.7\",\"vulnerabilityTitle\":\"Microsoft Windows远程桌面协议远程代码执行漏洞12-020)\",\"vulnerabilityVendor\":\"Qualys\"}","{\"vulnerabilityId\":\"QID-38173\",\"cveIds\":\"\",\"cvssBaseScore\":\"9.4\",\"cvssTemporalScore\":\"6.9\",\"vulnerabilityTitle\":\"SSL证书-签名验证失败的漏洞\",\"vulnerabilityVendor\":\"Qualys\" ","{\"vulnerabilityId\":\"QID-90882 90043\",\"cveIds\":\"\",\"cvssBaseScore\":\"4.7\",\"cvssTemporalScore\":\"4\",\"vulnerabilityTitle\":\"Windows远程桌面协议弱加密方法允许\",\"vulnerabilityVendor\":\"Qualys\"}","{\"vulnerabilityId\":\"cveIds :\"\",\"cvssBaseScore\":\"7.3\",\"cvssTemporalScore\":\"6.3\",\"vulnerabilityTitle\":\"SMB Signing Disabled or SMB Signing Not Required\",\"vulnerabilityVendor\":\"Qualys\"}",{\"vulnerabilityId\":\"QID-38601\",\"cveIds\"CVE-2013-2566,CVE-26666,CVE 015-2808,\",\"cvssBaseScore\":\"4.3\",\"cvssTemporalScore\":\"3.7\",\"vulnerabilityTitle\":\"SSL/TLS使用弱RC4密码\",\"vulnerabilityVendor\":\"Qualys\"}]}]
2016-06-28 19:25:02,127 DEBUG [pool-311-thread-8][] va.runtime.admin.vaservice.VaServiceMessageListener -::::- VA:保存到上下文数据库,lastscantime: 1467134394000,mac: C0:4A:00:14:8D:4B
2016-06-28 19:25:02,268 DEBUG [pool-311-thread-8][] va.runtime.admin.vaservice.VaAdminServiceContext -::::- VA:正在将弹性搜索json发送到pri-lan
2016-06-28 19:25:02,272 DEBUG [pool-311-thread-8][] va.runtime.admin.vaservice.VaPanRemotingHandler -:::- VA:已保存到弹性搜索: {C0:4A:00:14:8D:4B=[{"vulnerabilityId":"QID-90783","cveIds":"CVE-2012-00000 2,CVE-2012-0152,","cvssBaseScore":"9.3","cvssTemporalScore":"7.7","vulnerabilityTitle":"Microsoft Windows远程桌面协议远程代码执行漏洞(MS12-020)","vulnerabilityVendor":"Qualys"}, {"vulnerabilityId":"QID-38173","cveIds":","cvssBaseScore":"9.9 ","cvssTemporalScore":"6.9","vulnerabilityTitle":"SSL Certificate - Signature Verification Failed Vulnerability","vulnerabilityVendor":"Qualys"},{"vulnerabilityId":"QID-90882","cveIds":","cvssBaseScore":"4.7","cvssTemporalScore":"4","vulnerabilityTitle":"Windows Remote Protocol Weak Weak Weak Vendor F弱加密方法允许","vulnerability供应商":"qualys":"qualys"} vulnerabilityId":"QID-90043","cveIds":"","cvssBaseScore":"7.3","cvssTemporalScore":"6.3","vulnerabilityTitle":"SMB Signing Disabled or SMB Signing Not Required","vulnerabilityVendor":"Qualys"}, {"vulnerabilityId":"QID-38601","cveIds":"CVE-2013-256666,CVE-2001 5-2808,","cvssBaseScore":"4.3","cvssTemporalScore":"3.7","vulnerabilityTitle":"SSL/TLS使用弱RC4密码","vulnerabilityVendor":"Qualys"}]}
要检查的日志- vaservice.log。您可以直接从ISE CLI对其进行跟踪:
ISE21-3ek/admin# show logging application vaservice.log tail
漏洞评估请求已提交至适配器
2016-06-28 17:07:13,200 DEBUG [endpointPollerScheduler-3][] cpm.va.service.util.VaServiceUtil -:::- VA SendSyslog systemMsg : [{"systemMsg":"91019","isAutoInsertSelfAcsInstance":true,"attributes":["TC-NAC.ServiceName","Vulnerability Assessment Service","TC-TC Status”、“VA request submitted to adapter”、“TC-NAC.Details”、“VA request submitted to adapter for processing”、“TC-NAC.MACAddress”、“C0:4A:00:14:8D:4B”、“TC-NAC.IpAddress”、“10.62.148.63”、“TC-NAC.AdapterInstanceUid”、“796440b7-09b5-3f 611-199fb81a4b99","TC-NAC.VendorName","Qualys","TC-NAC.AdapterInstanceName","QUALYS_VA"]}]
AdapterMessageListener每5分钟检查一次扫描的状态,直到扫描完成。
2016-06-28 17:09:43,459 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-来自适配器的消息: {"AdapterInstanceName":"QUALYS_VA","AdapterInstanceUid":"a70031d6-6e3b-484a-adb0-627f30248ad0","Vendor0":" Qualys","OperationMessageText":"排队等待检查扫描结果的终端数:1,排队等待扫描的终端数:0,正在扫描的终端数:0"}
2016-06-28 17:14:43,760 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-来自适配器的消息: {"AdapterInstanceName":"QUALYS_VA","AdapterInstanceUid":"a70031d6-6e3b-484a-adb0-627f30248ad0","Vendor0":" Qualys","OperationMessageText":"排队等待检查扫描结果的终端数:0,排队等待扫描的终端数:0,正在扫描的终端数:1"}
2016-06-28 17:19:43,837 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-来自适配器的消息: {"AdapterInstanceName":"QUALYS_VA","AdapterInstanceUid":"a70031d6-6e3b-484a-adb0-627f30248ad0","Vendor0":"Vendor0" Qualys","OperationMessageText":"排队等待检查扫描结果的终端数:0,排队等待扫描的终端数:0,正在扫描的终端数:1"}
2016-06-28 17:24:43,867 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-来自适配器的消息: {"AdapterInstanceName":"QUALYS_VA","AdapterInstanceUid":"a70031d6-6e3b-484a-adb0-627f30248ad0","Vendor":"Vendor0" Qualys","OperationMessageText":"排队等待检查扫描结果的终端数:0,排队等待扫描的终端数:0,正在扫描的终端数:1"}
适配器获得QID、CVE以及CVSS分数
2016-06-28 17:24:57,556 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-来自适配器的消息: {"requestedMacAddress":"C0:4A:00:14:8D:4B","scanStatus":"ASSESSMENT_SUCCESS","lastScanTimeLong":1467134394000,"ipAddress":"1Address": 0.62.148.63","vulnerabilities":[{"vulnerabilityId":"QID-38173","cveIds":","cvssBaseScore":"9.4","cvssTemporalScore":"6.9","vulnerabilityTitle":"SSL Certificate - Signature Verification Failed Vulnerability","vulnerabilityVendor":"Qualys"},{"vulnerabilityId":"QID-90043","cveIds":","cveScoreBase ":"7.3","cvssTemporalScore":"6.3","vulnerabilityTitle":"SMB Signing Disabled or SMB Signing Not Required","vulnerabilityVendor":"Qualys"},{"vulnerabilityId":"QID-90783","cveIds":"CVE-2012-0002,CVE-2012-0152",",","cvssBaseScore":"9.3",","cvss0003":"temporalScore": Score":"7.7","vulnerabilityTitle":"Microsoft Windows远程桌面协议远程代码执行漏洞(MS12-020)","vulnerabilityVendor":"Qualys"},{"vulnerabilityId":"QID-38601","cveIds":"CVE-2013-2566,CVE-2015-2808",","cvssBaseScore":"4.3","cvss TemporalScore":"3.7","vulnerabilityTitle":"SSL/TLS使用弱RC4加密方法","vulnerabilityVendor":"Qualys"},{"vulnerabilityId":"QID-90882","cveIds":","cvssBaseScore":"4.7","cvssTemporalScore":"4","vulnerabilityTitle":"Windows远程桌面协议弱加密方法允许","vulnerabilityVendor":"VulnerabilityVendor":"Qualys":"Qualys"}]}]}
2016-06-28 17:25:01,282 INFO [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-发送到IRF的终端详细信息为{"C0:C 4A:00:14:8D:4B":[{"vulnerability":{"CVSS_Base_Score":9.4,"CVSS_Temporal_Score":7.7},"time-stamp":1467134394000,"title":"Vulnerability","vendor":"Qualys"}]}
2016-06-28 17:25:01,853 DEBUG [endpointPollerScheduler-2][] cpm.va.service.util.VaServiceUtil -:::- VA SendSyslog systemMsg : [{"systemMsg":"91019","isAutoInsertSelfAcsInstance":true,"attributes":["TC-NAC.ServiceName","Vulnerability Assessment Service","TC-TC Status”、“VA successfully completed”、“TC-NAC.Details”、“VA completed;找到的漏洞数:5","TC-NAC.MACAddress","C0:4A:00:14:8D:4B","TC-NAC.IpAddress","10.62.148.63","TC-NAC.AdapterInstanceUid","796440b7-09b5-4f3b-b611-199fb81a4b99","TC-NAC .VendorName","Qualys","TC-NAC.AdapterInstanceName","QUALYS_VA"]}]
典型问题
问题 1.ISE获得CVSS_Base_Score为0.0且CVSS_Temporal_Score为0.0的漏洞报告,而Qualys Cloud报告包含检测到的漏洞。
问题:
检查来自Qualys云的报告时,您可以看到检测到的漏洞,但在ISE上您看不到它们。
在vaservice.log中看到的调试:
2016-06-02 08:30:10,323信息[SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-发送到IRF的终端详细信息为{"C0:C 4A:00:15:75:C8":[{"vulnerability":{"CVSS_Base_Score":0.0,"CVSS_Temporal_Score":0.0},"time-stamp":1464855905000,"title":"Vulnerability","vendor":"Qualys"}]}
解决方案:
cvss分数为零的原因可能是,在您通过UI配置适配器之前,该适配器没有漏洞或者在Qualys云中未启用cvss评分。首次配置适配器后,即可下载包含已启用cvss评分功能的知识库。您必须确保之前启用了CVSS评分,在ISE上创建适配器实例。此操作可在Vulnerability Management > Reports > Setup > CVSS > Enable CVSS Scoring下完成
问题 2.ISE无法从Qualys云获得结果,即使命中了正确的授权策略。
问题:
已匹配更正的授权策略,应触发VA扫描。尽管如此,没有进行扫描。
在vaservice.log中看到的调试:
2016-06-28 16:19:15,401 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-来自适配器的消息: (Body:'[B@6da5e620(byte[311])'MessageProperties [headers={}, timestamp=null, messageId=null, userId=null, appId=null, clusterId=null, type=null, correlationId=null, null contentType=application/octet-stream, contentEncoding=null, contentLength=0, deliveryMode=PERSISTENT, expiration=null, priority=0, redelivered=false, receivedExchange=irf.topic.va-reports, receivedRoutingKey=, deliveryTag=9830, messageCount=0])
2016-06-28 16:19:15,401 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::-来自适配器的消息: {"requestedMacAddress":"24:77:03:3D:CF:20","scanStatus":"SCAN_ERROR","scanStatusMessage":"错误触发扫描:错误触发错误运行按需扫描代码和错误,如下所示1904:指定的IP都不符合漏洞管理扫描的条件。","lastScanTimeLong":0,"ipAddress":"10.201.228.102"}
2016-06-28 16:19:15,771 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -::::- Macaddress的适配器扫描结果失败:24:77:03:3D:CF:20,IP地址(DB): 10.201.228.102设置失败
2016-06-28 16:19:16,336 DEBUG [endpointPollerScheduler-2][] cpm.va.service.util.VaServiceUtil -:::- VA SendSyslog systemMsg : [{"systemMsg":"91008","isAutoInsertSelfAcsInstance":true,"attributes":["TC-NAC.ServiceName","Vulnerability Assessment Service","TC-TC Status”、“VA Failure”、“TC-NAC.Details”、“Error triggering scan: Error while triggering on-demand scan code”和“error following 1904: none of the specified IPs are eligible for Vulnerability Management scanning”。、“TC-NAC.MACAddress”、“24:77:03:3D:CF:20”、“TC-NAC.IpAddress”、“10.2228.1022” "TC-NAC.AdapterInstanceUuid","796440b7-09b5-4f3b-b611-199fb81a4b99","TC-NAC.VendorName","Qualys","TC-NAC.AdapterInstanceName","QUALYS_VA"]}]
解决方案:
Qualys Cloud指示终端的IP地址不符合扫描条件,请确保已将终端的IP地址添加到Vulnerability Management > Assets > Host Assets > New > IP Tracked Hosts
参考
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
29-Jun-2016
|
初始版本 |
 反馈
反馈