带TrustSec SGT内联标记和SGT感知区域防火墙配置示例的GETVPN
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
目录
简介
本文将介绍如何配置GETVPN以推送策略,允许在加密数据包中发送和接收安全组标记(SGT)。示例包括两个分支机构,用特定SGT标记所有流量,并基于收到的SGT标记应用基于区域的防火墙(ZBF)策略。
先决条件
要求
Cisco 建议您了解以下主题:
- IOS命令行界面(CLI)配置和GETVPN配置的基本知识
- Trustsec服务的基本知识。
- 基于区域的防火墙基础知识
使用的组件
本文档中的信息基于以下软件版本:
- 带软件15.3(2)T及更高版本的Cisco 2921路由器
拓扑
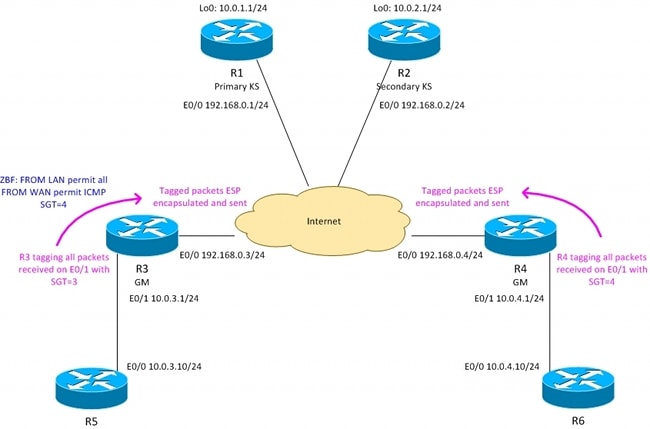
R3 - Branch1中的边界路由器,GETVPN组成员
R4 - Branch2中的边界路由器,GETVPN组成员
R1、R2 — 中心站点中的GETVPN密钥服务器
在所有路由器上运行的OSPF
从KS推送的ACL强制加密10.0.0.0/16 <-> 10.0.0.0/16之间的流量
R3路由器使用SGT标记= 3标记从Branch1发送的所有流量
R4路由器使用SGT标记= 4标记从Branch2发送的所有流量
R3在向LAN发送流量时删除SGT标记(假设R5不支持内联标记)
R4在向LAN发送流量时删除SGT标记(假设R6不支持内联标记)
R4没有防火墙(接受所有数据包)
R3使用以下策略配置ZBF:
— 接受从LAN到WAN的所有流量
— 仅接受从WAN到LAN的带有SGT=4标记的ICMP
配置
R1(中心站点中的密钥服务器)
要发送允许发送和接收标记数据包的策略“tac cts sgt”命令,需要显示:
interface Loopback0
ip address 10.0.1.1 255.255.255.0
!
interface Ethernet0/0
ip address 192.168.0.1 255.255.255.0
crypto ipsec transform-set TS esp-aes esp-sha256-hmac
mode tunnel
!
crypto ipsec profile prof1
set transform-set TS
!
crypto gdoi group group1
identity number 1
server local
rekey authentication mypubkey rsa GETKEY
rekey transport unicast
sa ipsec 1
profile prof1
match address ipv4 GET-IPV4
replay counter window-size 64
tag cts sgt
address ipv4 192.168.0.1
redundancy
local priority 100
peer address ipv4 192.168.0.2
router ospf 1
network 10.0.0.0 0.0.255.255 area 0
network 192.168.0.0 0.0.0.255 area 0
ip access-list extended GET-IPV4
permit icmp 10.0.0.0 0.0.255.255 10.0.0.0 0.0.255.255
R2的配置非常相似。
R3(Branch1中的组成员)
GETVPN配置与无SGT标记的场景相同。LAN接口已配置了手动trustsec:
- "policy static sgt 3 trusted" — 标记从LAN使用SGT=3接收的所有数据包
- “no propagate sgt” — 在向LAN传输数据包时删除所有SGT标记
crypto gdoi group group1
identity number 1
server address ipv4 192.168.0.1
server address ipv4 192.168.0.2
!
!
crypto map cmap 10 gdoi
set group group1
interface Ethernet0/0
ip address 192.168.0.3 255.255.255.0
crypto map cmap
!
interface Ethernet0/1
ip address 10.0.3.1 255.255.255.0
cts manual
no propagate sgt
policy static sgt 3 trusted
router ospf 1
network 10.0.0.0 0.0.255.255 area 0
network 192.168.0.0 0.0.0.255 area 0
R3上的ZBF配置:
将接受来自LAN的所有数据包。仅从WAN接受标有SGT=4的ICMP数据包:
class-map type inspect match-all TAG_4_ICMP
match security-group source tag 4
match protocol icmp
!
policy-map type inspect FROM_LAN
class class-default
pass log
policy-map type inspect FROM_WAN
class type inspect TAG_4_ICMP
pass log
class class-default
drop log
!
zone security lan
zone security wan
zone-pair security WAN-LAN source wan destination lan
service-policy type inspect FROM_WAN
zone-pair security LAN-WAN source lan destination wan
service-policy type inspect FROM_LAN
interface Ethernet0/0
zone-member security wan
!
interface Ethernet0/1
zone-member security lan
Branch2的R4配置非常相似,但ZBF未在其中配置。
R5、R6配置
R5和R6在两个分支中模拟本地LAN。R5的配置示例:
interface Ethernet0/0
ip address 10.0.3.10 255.255.255.0
router ospf 1
network 10.0.0.0 0.0.255.255 area 0
确认
测试SGT感知GETVPN
检查Branch1(R3)中的组成员是否支持SGT标记:
R3#show crypto gdoi feature cts-sgt
Version Feature Supported
1.0.8 Yes
检查推送到Branch1(R3)中的组成员的TEK策略是否使用SGT:
R3#show crypto gdoi
GROUP INFORMATION
<...some output ommited for clarity...>
TEK POLICY for the current KS-Policy ACEs Downloaded:
Ethernet0/0:
IPsec SA:
spi: 0xD100D58E(3506492814)
transform: esp-aes esp-sha256-hmac
sa timing:remaining key lifetime (sec): expired
Anti-Replay(Counter Based) : 64
tag method : cts sgt
alg key size: 16 (bytes)
sig key size: 32 (bytes)
encaps: ENCAPS_TUNNEL
IPsec SA:
spi: 0x52B3CA86(1387514502)
transform: esp-aes esp-sha256-hmac
sa timing:remaining key lifetime (sec): (1537)
Anti-Replay(Counter Based) : 64
tag method : cts sgt
alg key size: 16 (bytes)
sig key size: 32 (bytes)
encaps: ENCAPS_TUNNEL
从R6向R5发送ICMP流量:
R6#ping 10.0.3.10 repeat 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 10.0.3.10, timeout is 2 seconds:
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 1/1/6 ms
检查R3是否将SGT标记附加到加密数据包:
R3#show crypto ipsec sa detail
interface: Ethernet0/0
Crypto map tag: cmap, local addr 192.168.0.3
protected vrf: (none)
local ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/1/0)
remote ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/1/0)
Group: group1
current_peer 0.0.0.0 port 848
PERMIT, flags={}
#pkts encaps: 39, #pkts encrypt: 39, #pkts digest: 39
#pkts decaps: 39, #pkts decrypt: 39, #pkts verify: 39
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#pkts no sa (send) 0, #pkts invalid sa (rcv) 0
#pkts encaps failed (send) 0, #pkts decaps failed (rcv) 0
#pkts invalid prot (recv) 0, #pkts verify failed: 0
#pkts invalid identity (recv) 0, #pkts invalid len (rcv) 0
#pkts replay rollover (send): 0, #pkts replay rollover (rcv) 0
##pkts replay failed (rcv): 0
#pkts tagged (send): 39, #pkts untagged (rcv): 39
<...some output ommited for clarity...>
在Branch2(R3)中检查组成员上GETVPN的数据平面计数器:
R3#show crypto gdoi gm dataplane counters
Data-plane statistics for group group1:
#pkts encrypt : 53 #pkts decrypt : 53
#pkts tagged (send) : 53 #pkts untagged (rcv) : 53
#pkts no sa (send) : 0 #pkts invalid sa (rcv) : 0
#pkts encaps fail (send) : 0 #pkts decap fail (rcv) : 0
#pkts invalid prot (rcv) : 0 #pkts verify fail (rcv) : 0
#pkts not tagged (send) : 0 #pkts not untagged (rcv) : 0
#pkts internal err (send): 0 #pkts internal err (rcv) : 0
根据平台的不同,可以使用调试来揭示更多详细信息。例如,在R3上:
R3#debug cts platform l2-sgt rx
R3#debug cts platform l2-sgt tx
R3从LAN接收的数据包应标记为SGT:
01:48:08: cts-l2sgt_rx:l2cts-policysgt:[in=Ethernet0/1 src=0100.5e00.0005 dst=aabb.cc00.6800] Policy SGT Assign [pak=F1B00E00:flag=0x1:psgt=3]
此外,通过隧道发送的加密数据包将被标记:
01:49:28: cts_ether_cmd_handle_post_encap_feature:pak[36BF868]:size=106 in=Ethernet0/1 out=Ethernet0/0 enctype=1 encsize=0 sgt_offset=18 [adj]:idb=Ethernet0/0 is_dot1q=0 linktype=7 mac_length=22 SGT=3
测试SGT感知ZBF
R3将只接受来自WAN的标记有SGT=4的ICMP数据包。从R6向R5发送ICMP数据包时:
R6#ping 10.0.3.10 repeat 11
Type escape sequence to abort.
Sending 1, 100-byte ICMP Echos to 10.0.3.10, timeout is 2 seconds:
!
Success rate is 100 percent (1/1), round-trip min/avg/max = 1/1/6 ms
R3将收到带标记的ESP数据包,将其解密。然后ZBF将接受流量:
*Mar 17 12:45:28.039: %FW-6-PASS_PKT: (target:class)-(WAN-LAN:TAG_4_ICMP) Passing icmp pkt 10.0.4.10:0 => 10.0.3.10:0 with ip ident 57
此外,策略映射将显示包含接受的数据包数的计数器:
R3#show policy-firewall stats all
Global Stats:
Session creations since subsystem startup or last reset 0
Current session counts (estab/half-open/terminating) [0:0:0]
Maxever session counts (estab/half-open/terminating) [0:0:0]
Last session created never
Last statistic reset never
Last session creation rate 0
Maxever session creation rate 0
Last half-open session total 0
policy exists on zp WAN-LAN
Zone-pair: WAN-LAN
Service-policy inspect : FROM_WAN
Class-map: TAG_4_ICMP (match-all)
Match: security-group source tag 4
Match: protocol icmp
Pass
18 packets, 1440 bytes
Class-map: class-default (match-any)
Match: any
Drop
3 packets, 72 bytes
policy exists on zp LAN-WAN
Zone-pair: LAN-WAN
Service-policy inspect : FROM_LAN
Class-map: class-default (match-any)
Match: any
Pass
18 packets, 1440 bytes
尝试从R6 telnet至R5时,R3将丢弃该流量,因为不允许telnet:
*Mar 17 12:49:30.475: %FW-6-DROP_PKT: Dropping tcp session 10.0.4.10:37500 10.0.3.10:23 on zone-pair WAN-LAN class class-default due to DROP action found in policy-map with ip ident 36123
参考
由思科工程师提供
- 米哈拉Garcarz思科TAC工程师
 反馈
反馈