通过EIGRP配置分支到分支的FlexVPN并对其进行故障排除
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
目录
简介
本文档介绍使用IKEv2和NHRP为直接客户端加密隧道部署和排除Cisco FlexVPN分支到分支的故障。
先决条件
- Flex VPN中心和Flex VPN客户端配置
要求
Cisco 建议您了解以下主题:
- IKEv2
- 基于路由的VPN
- 虚拟隧道接口(VTI)
- NHRP
- IPsec
- EIGRP
- VRF-Lite
使用的组件
本文档中的信息基于:
- 思科IOS XE 17.9.4a
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
可扩展性
FlexVPN可以轻松地从小型办公室扩展到大型企业网络。它可以管理许多VPN连接,而无需大量额外工作,这对于正在发展或拥有许多远程用户的组织而言非常棒。
主要特点
- 动态配置和按需隧道:
- 虚拟隧道接口(VTI):FlexVPN使用可根据需要创建和删除的VTI。这意味着仅在存在流量时设置VPN隧道,并在不需要时删除VPN隧道,从而节省资源并提高可扩展性。
- 动态路由协议:它与OSPF、EIGRP和BGP over VPN隧道等路由协议配合使用。这可以保持路由信息的自动更新,这对于大型和动态网络非常重要。
- 部署灵活性:
- 中心辐射型模型:一个中心集线器连接到多个分支机构。FlexVPN通过单一框架简化了这些连接的设置,使其成为大型网络的理想选择。
- 全网状拓扑和部分网状拓扑:所有站点可以直接通信,无需通过中央集线器,从而减少了延迟并提高了性能。
- 高可用性和冗余:
- 冗余集线器:支持多个集线器进行备份。如果一台集线器发生故障,分支机构可以连接到另一台集线器,确保连续连接。
- 负载均衡:跨多个设备分布VPN连接,以避免任何单个设备过载,这对于在大型部署中保持性能至关重要。
- 可扩展的身份验证和授权:
- AAA集成:与Cisco ISE或RADIUS等AAA服务器配合使用,集中管理用户凭证和策略,这对于大规模使用至关重要。
- PKI和证书:支持用于安全身份验证的公钥基础设施(PKI)和数字证书,其可扩展性比使用预共享密钥更高,特别是在大型环境中。
背景信息
FlexVPN和NHRP
FlexVPN服务器提供FlexVPN的服务器端功能。FlexVPN客户端在FlexVPN客户端和另一个FlexVPN服务器之间建立安全IPsec VPN隧道。
NHRP是一种类似地址解析协议(ARP)的协议,可缓解非广播多路访问(NBMA)网络问题。通过NHRP,连接到NBMA网络的NHRP实体动态获取属于该网络的其他实体的NBMA地址,从而允许这些实体直接通信,而无需流量使用中间跃点。
FlexVPN分支到分支功能集成了NHRP和FlexVPN客户端(分支),以与现有FlexVPN网络中的其他客户端建立直接加密通道。连接是使用虚拟隧道接口(VTI)、IKEv2和NHRP构建的,其中NHRP用于解析网络中的FlexVPN客户端。
思科建议确保:
-
分支之间不交换路由条目。一个关键的考虑因素,稍后将在我们排除基于EIGRP的拓扑故障时说明。
- 分支使用不同的配置文件,并且没有为分支配置config-exchange命令。
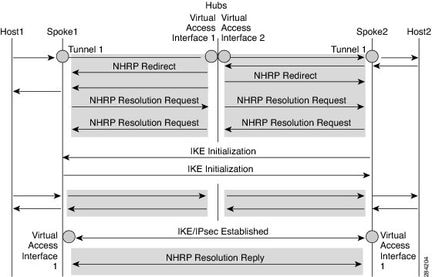
NHRP流程
下图显示了分支1和分支2之间的流量,其中网络198.51.100.0/29/24和198.51.100.8/29都是通过EIGRP对等(通过集线器直接通告到分支)。下面是在分支1(198.51.100.0/29/24)和分支2(198.51.100.8/29)之间建立通信时流量的样子图。
- Host1发送目的地为Host2的流量。在主机1上执行路由查找会导致流量转发到集线器隧道接口,因为集线器正在通过EIGRP通告该网络。
- 当流量到达中心时,中心端路由查找确认分支2网络198.51.100.8/29是通过分支2虚拟访问获取的。
- 由于两个虚拟访问接口(分支1和分支2)属于具有相同NHRP网络ID的同一NHRP网络,因此集线器启动NHRP重定向。
- 收到重定向后,Spoke1通过隧道接口(接收重定向的同一接口)发起对分支2网络的解析请求。 分支2对分支1网络的解析请求重复相同的过程。
- Spoke2在隧道接口上接收解析请求并检索配置中定义的虚拟模板编号。虚拟模板编号用于创建虚拟访问接口,以便在两个分支之间建立加密会话。一旦两个辐射点之间的加密SA启动,两个辐射点都会安装通过IPSEC建立虚拟访问接口后获取的下一跳IP地址的路由。
- 然后,两个分支在通过新创建的用于分支到分支连接的接口virtual-access向外发送解析应答之前,继续验证下一跳可达性。
- 一旦到达下一跳,两个辐射点会相互发送解析应答。
- 现在,两个分支都可以覆盖其每个网络下一跳IP地址,以便通过NHO进行虚拟访问。
- Spoke1为Spoke2的下一跳IP及其网络安装必要的缓存条目。Spoke1还会删除指向集线器的临时缓存条目,以解析隧道接口1下的网络。
- 分支2重复相同步骤,它还为分支1下一跳IP及其网络安装缓存条目,并通过隧道删除旧的中心条目。
- NHRP添加快捷方式路由作为下一跳覆盖(NHO)或H(NHRP)路由。
使用EIGRP配置FlexVPN分支到分支
拓扑图
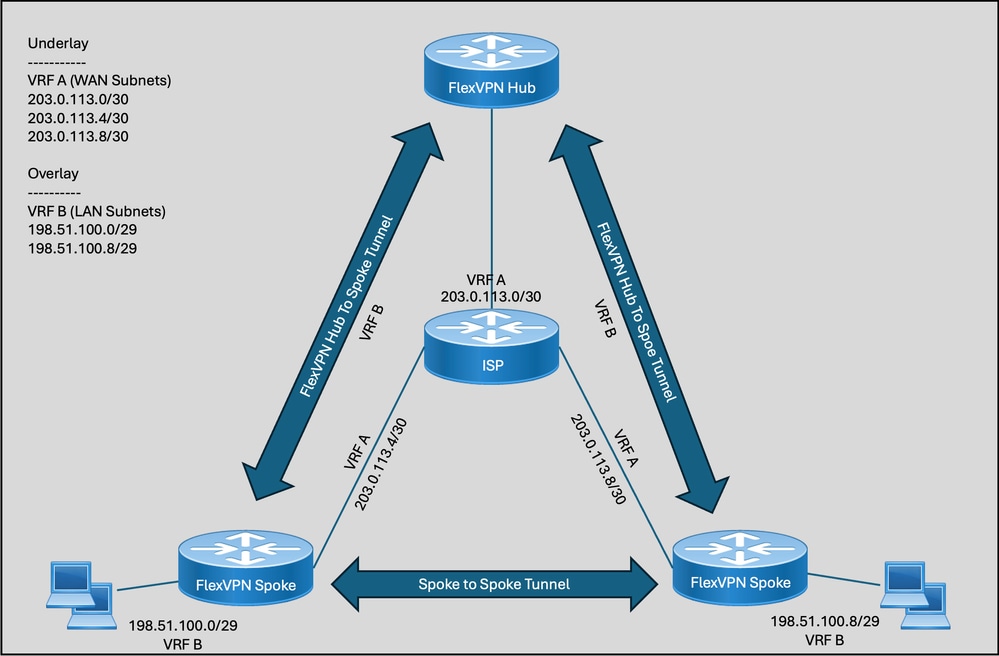
基于EIGRP的拓扑的关键注意事项
在继续配置之前,我们必须了解一些关键概念:
- 对于任何EIGRP部署,如果分支正在接收包含其他分支的完整路由表或仅接收汇总路由,则需要在中心端安装前缀列表以进行出站路由更新,以过滤要通告给彼此的分支的隧道IP地址。
-
EIGRP中的水平分割与IBGP中的水平分割不同。EIGRP仅停止从获取网络的接口通告网络。例如,集线器有两个分支,一个通过virtual-access 1连接,另一个通过virtual-access 2接口连接。集线器通过VA 1从分支1获知的路由通过VA 2通告回分支2,反之亦然,因为VA 1和VA 2是不同的接口。对于IBGP,它不会将从其对等体获知的任何网络通告回另一个对等体。在类似示例中,配置了IBGP的集线器不会将其从VA 1获知的回传到VA 2,反之亦然。
-
EIGRP中的此行为会在下一跳IP地址(分支到分支隧道的虚拟访问接口的IP地址)的CEF邻接中产生冲突,因为首先使用中心隧道接口通过EIGRP获取该地址,然后使用虚拟访问接口通过IPsec获取该地址。这会导致NHRP流量出现非对称路由,还会导致NHRP表中出现重复的NHRP条目,路由表中出现重复的NHO条目,以及下一跳接口(通过集线器的隧道)和(通过分支的虚拟访问)都出现这种情况。
-
由于我们希望过滤传出EIGRP更新,以确保中心与分支的EIGRP对等不受影响,因此中心端虚拟模板需要来自与分支隧道接口不同的池的IP。
以下两个示例展示如何在FlexVPN服务器和FlexVPN客户端上使用EIGRP配置FlexVPN分支到分支。我们遵循了将底层流量和重叠流量都放在特定VRF中的最佳实践。VRF A用于衬底,而B用于重叠。
示例1 — 利用NHO(下一跳覆盖)进行分支到分支通信
FlexVPN服务器
ip local pool FLEXPOOL 192.0.2.129 192.0.2.254
crypto ikev2 authorization policy CISCO_FLEX
pool FLEXPOOL
def-domain cisco.com
route set interface
crypto ikev2 proposal CISCO_PROP
encryption aes-gcm-256
prf sha256
group 21
crypto ikev2 policy CISCO_POL
match fvrf A
proposal CISCO_PROP
crypto ikev2 profile CISCO_IKEV2
match fvrf A
match identity remote fqdn domain cisco.com
identity local fqdn hub.cisco.com
authentication remote pre-share key cisco
authentication local pre-share key cisco
aaa authorization group psk list default CISCO_FLEX
virtual-template 1
crypto ipsec transform-set CISCO_TRANSFORM esp-aes 256 esp-sha256-hmac
mode transport
crypto ipsec profile CISCO_PROF
set transform-set CISCO_TRANSFORM
set pfs group19
set ikev2-profile CISCO_IKEV2
interface Loopback0
ip vrf forwarding B
ip address 192.0.2.1 255.255.255.255
interface GigabitEthernet1
ip vrf forwarding A
ip address 203.0.113.2 255.255.255.252
interface Virtual-Template1 type tunnel
ip vrf forwarding B
ip unnumbered Loopback0
ip nhrp network-id 1
ip nhrp redirect
tunnel vrf A
tunnel protection ipsec profile CISCO_PROF
ip prefix-list CISCO_PREFIX seq 5 deny 192.0.2.128/25 le 32
ip prefix-list CISCO_PREFIX seq 6 permit 0.0.0.0/0 le 32
router eigrp B
!
address-family ipv4 unicast vrf B autonomous-system 1
!
af-interface default
hello-interval 2
hold-time 10
exit-af-interface
!
topology base
distribute-list prefix CISCO_PREFIX out
exit-af-topology
network 192.0.2.128 0.0.0.127
network 192.0.2.1 0.0.0.0
exit-address-family
FlexVPN客户端1
ip host vrf A hub.cisco.com 203.0.113.2
crypto ikev2 authorization policy CISCO_FLEX
route set interface
crypto ikev2 proposal CISCO_PROP
encryption aes-gcm-256
prf sha256
group 21
crypto ikev2 policy CISCO_POL
match fvrf A
proposal CISCO_PROP
crypto ikev2 client flexvpn CISCO_CLIENT
peer 1 fqdn hub.cisco.com dynamic
client connect Tunnel1
crypto ikev2 profile CISCO_IKEV2
match fvrf A
match identity remote fqdn domain cisco.com
identity local fqdn spoke1.cisco.com
authentication remote pre-share key cisco
authentication local pre-share key cisco
aaa authorization group psk list default CISCO_FLEX
virtual-template 1
crypto ipsec transform-set CISCO_TRANSFORM esp-aes 256 esp-sha256-hmac
mode transport
crypto ipsec profile CISCO_PROF
set transform-set CISCO_TRANSFORM
set pfs group19
set ikev2-profile CISCO_IKEV2
interface Tunnel1
ip vrf forwarding B
ip address negotiated
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
tunnel source GigabitEthernet1
tunnel destination dynamic
tunnel vrf A
tunnel protection ipsec profile CISCO_PROF
end
interface GigabitEthernet1
ip vrf forwarding A
ip address 203.0.113.6 255.255.255.252
interface Loopback1
ip vrf forwarding B
ip address 198.51.100.1 255.255.255.248
interface Virtual-Template1 type tunnel
ip vrf forwarding B
ip unnumbered Tunnel1
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
tunnel vrf A
tunnel protection ipsec profile CISCO_PROF
router eigrp B
address-family ipv4 unicast vrf B autonomous-system 1
af-interface default
hello-interval 2
hold-time 10
passive-interface
exit-af-interface
af-interface Tunnel1
no passive-interface
exit-af-interface
topology base
exit-af-topology
network 198.51.100.0 0.0.0.7
network 192.0.2.128 0.0.0.127
exit-address-family
FlexVPN客户端2
ip host vrf A hub.cisco.com 203.0.113.2
crypto ikev2 authorization policy CISCO_FLEX
route set interface
crypto ikev2 proposal CISCO_PROP
encryption aes-gcm-256
prf sha256
group 21
crypto ikev2 policy CISCO_POL
match fvrf A
proposal CISCO_PROP
crypto ikev2 client flexvpn CISCO_CLIENT
peer 1 fqdn hub.cisco.com dynamic
client connect Tunnel1
crypto ikev2 profile CISCO_IKEV2
match fvrf A
match identity remote fqdn domain cisco.com
identity local fqdn spoke2.cisco.com
authentication remote pre-share key cisco
authentication local pre-share key cisco
aaa authorization group psk list default CISCO_FLEX
virtual-template 1
crypto ipsec transform-set CISCO_TRANSFORM esp-aes 256 esp-sha256-hmac
mode transport
crypto ipsec profile CISCO_PROF
set transform-set CISCO_TRANSFORM
set pfs group19
set ikev2-profile CISCO_IKEV2
interface Tunnel1
ip vrf forwarding B
ip address negotiated
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
tunnel source GigabitEthernet1
tunnel destination dynamic
tunnel vrf A
tunnel protection ipsec profile CISCO_PROF
end
interface GigabitEthernet1
ip vrf forwarding A
ip address 203.0.113.10 255.255.255.252
interface Loopback1
ip vrf forwarding B
ip address 198.51.100.9 255.255.255.248
interface Virtual-Template1 type tunnel
ip vrf forwarding B
ip unnumbered Tunnel1
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
tunnel vrf A
tunnel protection ipsec profile CISCO_PROF
router eigrp B
address-family ipv4 unicast vrf B autonomous-system 1
af-interface default
hello-interval 2
hold-time 10
passive-interface
exit-af-interface
af-interface Tunnel1
no passive-interface
exit-af-interface
topology base
exit-af-topology
network 198.51.100.8 0.0.0.7
network 192.0.2.128 0.0.0.127
exit-address-family
示例2 — 利用NHRP安装的路由进行分支到分支通信
FlexVPN服务器
EIGRP配置中的唯一更改是在分支上引入总结路由,而不是完整的路由表。请确保关闭虚拟模板,以将汇总配置推送到EIGRP拓扑中。请参阅Cisco Bug ID CSCwn84303。
router eigrp B
!
address-family ipv4 unicast vrf B autonomous-system 1
!
af-interface default
hello-interval 2
hold-time 10
exit-af-interface
!
af-interface Virtual-Template1
summary-address 198.51.100.0 255.255.255.0 <<<<<<<<<<< Summary address
exit-af-interface
!
topology base
distribute-list prefix CISCO_PREFIX out
exit-af-topology
network 192.0.2.128 0.0.0.127
network 192.0.2.1 0.0.0.0
exit-address-family
验证和故障排除
示例1 — 利用NHO(下一跳覆盖)进行分支到分支通信
辐射点1(辐射点到辐射点NHRP解析和隧道建立之前)
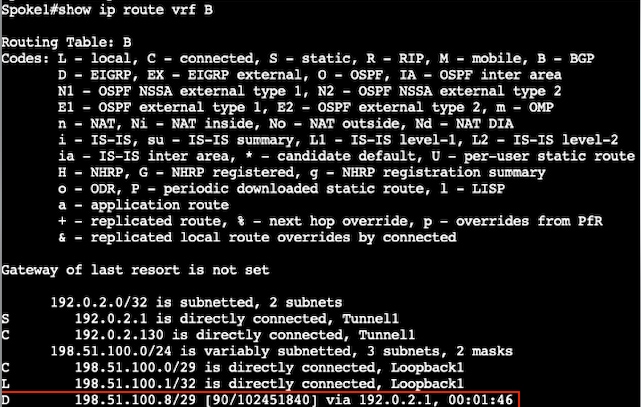
辐射点2(辐射点到辐射点NHRP解析和隧道建立之前)
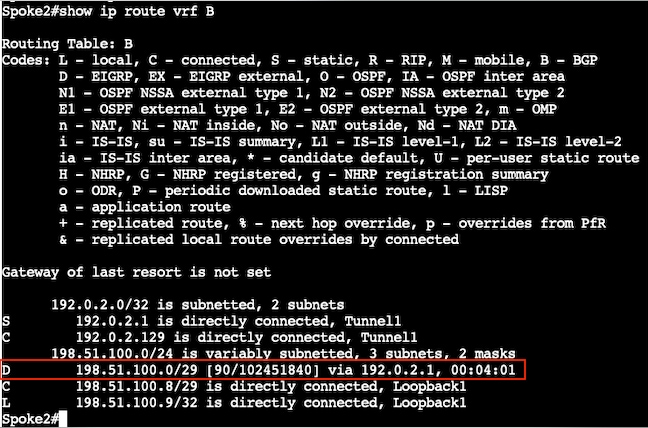
辐射点1(辐射点到辐射点NHRP解析和隧道建立后)
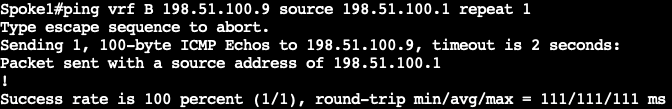
启动ICMP以触发分支到分支隧道:
验证NHRP快捷方式:
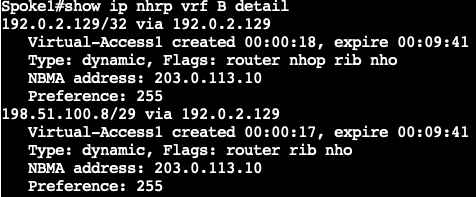
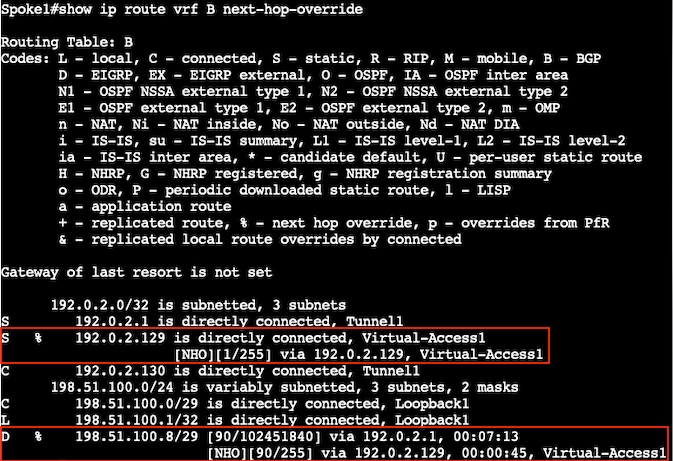
验证创建快捷方式后的NHO路由:
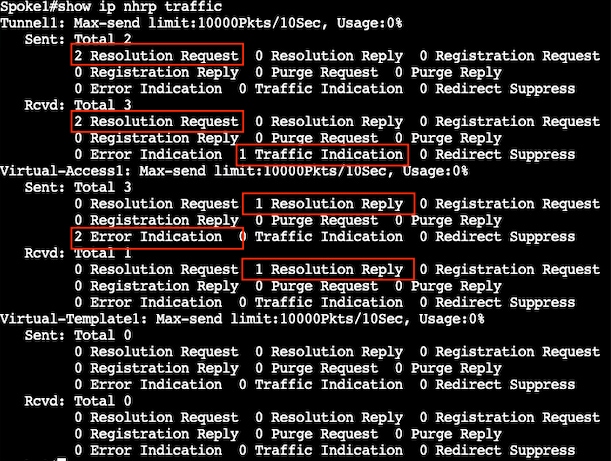
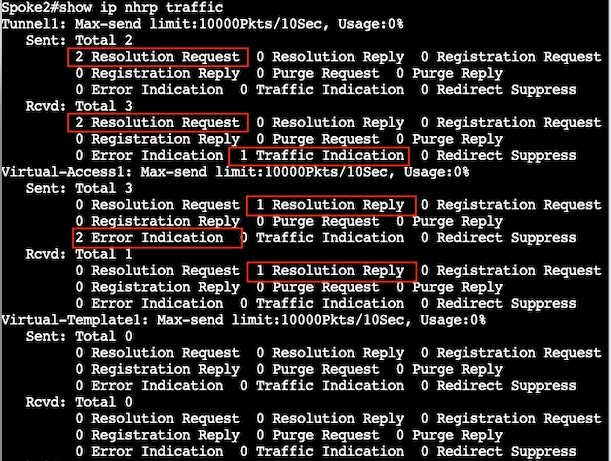
验证NHRP计数器:
分支2(在分支到分支NHRP解析和隧道建立后)
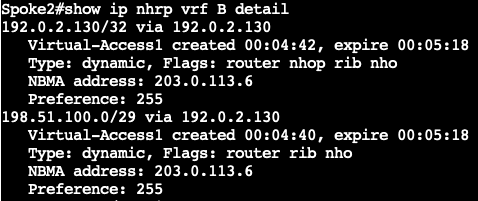
验证NHRP快捷方式:
验证创建快捷方式后的NHO路由:

验证NHRP计数器:
以下分步说明如何在其中一个分支的调试帮助下建立直接分支到分支隧道。
- 分支1发起的ICMP:
Spoke1#ping vrf B 198.51.100.9 source 198.51.100.1 repeat 1
Type escape sequence to abort.
Sending 1, 100-byte ICMP Echos to 198.51.100.9, timeout is 2 seconds:
Packet sent with a source address of 198.51.100.1
!
Success rate is 100 percent (1/1), round-trip min/avg/max = 111/111/111 ms
- 集线器收到ICMP并向两个分支发起重定向(流量指示):
*Feb 3 16:15:35.280: NHRP: Receive Traffic Indication via Tunnel1 vrf: B(0x4), packet size: 104
.
*Feb 3 16:15:35.280: (M) traffic code: redirect(0)
*Feb 3 16:15:35.280: src NBMA: 203.0.113.2
*Feb 3 16:15:35.280: src protocol: 192.0.2.1, dst protocol: 198.51.100.1
.
*Feb 3 16:15:35.281: NHRP-DETAIL: NHRP traffic indication for afn 1 received on interface Tunnel1 , for vrf: B(0x4) label: 0
- 两个分支都触发了通过tunnel1的解析请求:
*Feb 3 16:15:35.295: NHRP: Sending NHRP Resolution Request for dest: 198.51.100.9 to nexthop: 198.51.100.9 using our src: 192.0.2.130 vrf: B(0x4)
*Feb 3 16:15:35.295: NHRP: Attempting to send packet through interface Tunnel1 via DEST dst 198.51.100.9
*Feb 3 16:15:35.295: NHRP-DETAIL: First hop route lookup for 198.51.100.9 yielded 192.0.2.1, Tunnel1
*Feb 3 16:15:35.295: NHRP: Send Resolution Request via Tunnel1 vrf: B(0x4), packet size: 72
*Feb 3 16:15:35.295: src: 192.0.2.130, dst: 198.51.100.9
.
*Feb 3 16:15:35.296: src NBMA: 203.0.113.6
*Feb 3 16:15:35.296: src protocol: 192.0.2.130, dst protocol: 198.51.100.9
- 两个分支都通过Tunnel1收到解析请求:
*Feb 3 16:15:35.392: NHRP: Receive Resolution Request via Tunnel1 vrf: B(0x4), packet size: 92
.
*Feb 3 16:15:35.392: src NBMA: 203.0.113.10
*Feb 3 16:15:35.392: src protocol: 192.0.2.129, dst protocol: 198.51.100.1
*Feb 3 16:15:35.392: (C-1) code: no error(0), flags: none
.
*Feb 3 16:15:35.392: NHRP-DETAIL: Resolution request for afn 1 received on interface Tunnel1 , for vrf: B(0x4) label: 0
- 两个分支对其本地网络198.51.100.0/29/24和198.51.100.8/29执行路由查找:
*Feb 3 16:15:35.392: NHRP-DETAIL: Multipath IP route lookup for 198.51.100.1 in vrf: B(0x4) yielded Loopback1, pfx:198.51.100.0/29 (netid_in:1 if_in:Tunnel1)
*Feb 3 16:15:35.392: NHRP: Route lookup for destination 198.51.100.1 in vrf: B(0x4) yielded interface Loopback1, prefixlen 29
.
*Feb 3 16:15:35.392: NHRP: We are egress router. Process the NHRP Resolution Request.
.
*Feb 3 16:15:35.393: NHRP-DETAIL: Multipath IP route lookup for 198.51.100.1 in vrf: B(0x4) yielded Loopback1, pfx:198.51.100.0/29 (netid_in:1 if_in:Tunnel1)
*Feb 3 16:15:35.393: NHRP: nhrp_rtlookup for 198.51.100.1 in vrf: B(0x4) yielded interface Loopback1, prefixlen 29, label none(0)
*Feb 3 16:15:35.393: NHRP-DETAIL: netid_out 0, netid_in 1
*Feb 3 16:15:35.393: NHRP: We are egress router for target 198.51.100.1, recevied via Tunnel1 vrf: B(0x4)
- 解析应答已入队,IPsec建立已启动,因为两个分支现在知道彼此的NBMA地址:
*Feb 3 16:15:35.393: NHRP: Checking for delayed event 192.0.2.129/198.51.100.1 on list (Tunnel1 vrf: B(0x4))
*Feb 3 16:15:35.393: NHRP: No delayed event node found.
*Feb 3 16:15:35.394: NHRP-DETAIL: Updated delayed event with ep src:203.0.113.6 dst:203.0.113.10 ivrf:B
*Feb 3 16:15:35.394: NHRP: Enqueued Delaying resolution request nbma src:203.0.113.6 nbma dst:203.0.113.10 reason:IPSEC-IFC: need to wait for IPsec SAs.
*Feb 3 16:15:35.394: NHRP: Interface: Tunnel1 configured with FlexVPN. Deferring cache creation for nhop 192.0.2.129
*Feb 3 16:15:35.406: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to down
*Feb 3 16:15:35.456: NHRP: Virtual-Access1: Tunnel mode changed from
'Uninitialized tunnel mode' to 'GRE over point to point IPV4 tunnel mode'
*Feb 3 16:15:35.456: NHRP: Virtual-Access1: NHRP not enabled in delay_if_up
*Feb 3 16:15:35.511: NHRP: Registration with Tunnels Decap Module succeeded
*Feb 3 16:15:35.511: NHRP: Rejecting addr type 1
*Feb 3 16:15:35.511: NHRP: Adding all static maps to cache
*Feb 3 16:15:35.511: NHRP-DETAIL: Adding summary-prefix entry: nhrp router block not configured
*Feb 3 16:15:35.512: NHRP:
*Feb 3 16:15:35.512: Instructing NHRP to create Virtual-Access from Virtual template 1 for interface Virtual-Access1
*Feb 3 16:15:35.537: %SYS-5-CONFIG_P: Configured programmatically by process Crypto INT from console as console
*Feb 3 16:15:35.539: NHRP-CACHE: Virtual-Access1: Cache add for target 192.0.2.130/32 vrf: B(0x4) label none next-hop 192.0.2.130
*Feb 3 16:15:35.540: 203.0.113.6 (flags:0x20)
.
*Feb 3 16:15:35.548: NHRP: Updating delayed event with destination 203.0.113.10 on interfaceTunnel1 with the new interface Virtual-Access1
*Feb 3 16:15:35.788: NHRP:
*Feb 3 16:15:35.788: Fetched address from underlying IKEv2 for interfaceVirtual-Access1. Pre-NATed = 203.0.113.6, Post-NATed = UNKNOWN
*Feb 3 16:15:35.788: %DMVPN-5-CRYPTO_SS: Virtual-Access1: local address : 203.0.113.6 remote address : 203.0.113.10 socket is UP
- 在IPSEC建立和NHRP快捷方式创建过程中,两个分支相互学习并安装了各自路由表中的IP地址作为IPSEC路由和探测下一跳可达性:
*Feb 3 16:15:35.788: NHRP: Processing delayed event on interface Tunnel1 with NBMA 203.0.113.10
.
*Feb 3 16:15:35.789: NHRP-CACHE: Virtual-Access1: Cache add for target 192.0.2.129/32 vrf: B(0x4) label none next-hop 192.0.2.129
*Feb 3 16:15:35.789: 203.0.113.10 (flags:0x2080)
*Feb 3 16:15:35.789: NHRP-RT: Adding route entry for 192.0.2.129/32 via 192.0.2.129, Virtual-Access1 vrf: B(0x4)) to RIB
*Feb 3 16:15:35.791: NHRP-RT: Route addition to RIB Successful
*Feb 3 16:15:35.791: NHRP-EVE: NHP-UP: 192.0.2.129, NBMA: 203.0.113.10
*Feb 3 16:15:35.791: %DMVPN-5-NHRP_NHP_UP: Virtual-Access1: Next Hop NHP : (Tunnel: 192.0.2.129 NBMA: 203.0.113.10) for (Tunnel: 192.0.2.130 NBMA: 203.0.113.6) is UP
*Feb 3 16:15:35.791: NHRP-CACHE:
*Feb 3 16:15:35.791: Next-hop not reachable for 192.0.2.129
*Feb 3 16:15:35.791: %NHRP-5-NHOP_UNREACHABLE: Nexthop address 192.0.2.129 for 192.0.2.129/32 is not routable
- 在完成快捷方式安装和NHO之前,分支A对分支B的虚拟访问IP地址执行下一跳查找,反之亦然,但下一次希望查找返回“已产生N/A”,因为分支A向分支B发送错误指示,确认下一跳无法到达。特定查找可称为多路径查找:
*Feb 3 16:15:35.791: NHRP-DETAIL: Multipath recursive nexthop lookup(if_in:, netid:1) for 192.0.2.129 in vrf: B(0x4) yielded N/A, Virtual-Access1
*Feb 3 16:15:35.791: NHRP: Sending error indication. Reason: 'Cache pak failure' LINE: 13798
*Feb 3 16:15:35.791: NHRP: Attempting to send packet through interface Virtual-Access1 via DEST dst 192.0.2.129
*Feb 3 16:15:35.791: NHRP-DETAIL: Multipath recursive nexthop lookup(if_in:, netid:1) for 192.0.2.129 in vrf: B(0x4) yielded 192.0.2.129, Virtual-Access1
*Feb 3 16:15:35.791: NHRP: Send Error Indication via Virtual-Access1 vrf: B(0x4), packet size: 132
*Feb 3 16:15:35.791: src: 192.0.2.130, dst: 192.0.2.129
.
*Feb 3 16:15:35.791: (M) error code: protocol address unreachable(6), offset: 0
*Feb 3 16:15:35.791: src NBMA: 203.0.113.6
*Feb 3 16:15:35.791: src protocol: 192.0.2.130, dst protocol: 192.0.2.129
- NHO启动下一跳并创建快捷方式后,两个分支再次发出各自网络的解析请求:
*Feb 3 16:15:35.813: NHRP: No need to delay processing of resolution event nbma src:203.0.113.6 nbma dst:203.0.113.10
*Feb 3 16:15:35.813: NHRP-CACHE: Virtual-Access1: Cache update for target 192.0.2.129/32 vrf: B(0x4) label none next-hop 192.0.2.129
*Feb 3 16:15:35.813: 203.0.113.10 (flags:0x2280)
*Feb 3 16:15:35.813: NHRP-RT: Adding route entry for 192.0.2.129/32 via 192.0.2.129, Virtual-Access1 vrf: B(0x4)) to RIB
*Feb 3 16:15:35.814: NHRP-RT: Route addition to RIB Successful
.
*Feb 3 16:15:35.841: NHRP-RT: Route entry 192.0.2.129/32 via 192.0.2.129 (Vi1) clobbered by distance
*Feb 3 16:15:35.847: NHRP-RT: Unable to stop route watch for 192.0.2.129/32 interface Virtual-Access1 . No handle
*Feb 3 16:15:35.847: NHRP-RT: Adding route entry for 192.0.2.129/32 via 192.0.2.129, Virtual-Access1 vrf: B(0x4)) to RIB
*Feb 3 16:15:35.847: NHRP-RT: Route addition failed (admin-distance)
*Feb 3 16:15:35.847: NHRP-RT: nexthop-override added to RIB
.
*Feb 3 16:15:37.167: NHRP: Sending NHRP Resolution Request for dest: 198.51.100.9 to nexthop: 198.51.100.9 using our src: 192.0.2.130 vrf: B(0x4)
*Feb 3 16:15:37.167: NHRP: Attempting to send packet through interface Tunnel1 via DEST dst 198.51.100.9
*Feb 3 16:15:37.167: NHRP-DETAIL: First hop route lookup for 198.51.100.9 yielded 192.0.2.1, Tunnel1
*Feb 3 16:15:37.167: NHRP: Send Resolution Request via Tunnel1 vrf: B(0x4), packet size: 72
*Feb 3 16:15:37.167: src: 192.0.2.130, dst: 198.51.100.9
.
*Feb 3 16:15:37.167: src NBMA: 203.0.113.6
*Feb 3 16:15:37.167: src protocol: 192.0.2.130, dst protocol: 198.51.100.9
- 两个分支收到各自网络的解析请求后,NHO将通过Tunnel(HUB)的EIGRP路由替换为虚拟访问:
*Feb 3 16:30:57.768: NHRP-CACHE: Virtual-Access1: Cache add for target 198.51.100.8/29 vrf: B(0x4) label none next-hop 192.0.2.129
*Feb 3 16:30:57.768: 203.0.113.10 (flags:0x1000)
*Feb 3 16:30:57.768: NHRP-RT: Adding route entry for 198.51.100.8/29 via 192.0.2.129, Virtual-Access1 vrf: B(0x4)) to RIB
*Feb 3 16:30:57.769: NHRP-RT: Route addition failed (admin-distance)
*Feb 3 16:30:57.769: NHRP-RT: nexthop-override added to RIB
*Feb 3 16:30:57.769: NHRP-EVE: NHP-UP: 192.0.2.129, NBMA: 203.0.113.10
*Feb 3 16:30:57.769: %DMVPN-5-NHRP_NHP_UP: Virtual-Access1: Next Hop NHP : (Tunnel: 192.0.2.129 NBMA: 203.0.113.10) for (Tunnel: 192.0.2.130 NBMA: 203.0.113.6) is UP
*Feb 3 16:30:57.769: NHRP-CACHE: Deleting incomplete entry for 198.51.100.9/32 interface Tunnel1 vrf: B(0x4)
*Feb 3 16:30:57.769: NHRP-EVE: NHP-DOWN: 198.51.100.9, NBMA: 198.51.100.9
- 之后,两个分支通过虚拟访问接口发出解析应答:
*Feb 3 16:30:57.436: NHRP-CACHE: Virtual-Access1: Internal Cache add for target 198.51.100.0/29 vrf: B(0x4) label none next-hop 192.0.2.130
*Feb 3 16:30:57.436: 203.0.113.6 (flags:0x20)
*Feb 3 16:30:57.436: NHRP: Attempting to send packet through interface Virtual-Access1 via DEST dst 192.0.2.129
*Feb 3 16:30:57.436: NHRP-DETAIL: Multipath recursive nexthop lookup(if_in:, netid:1) for 192.0.2.129 in vrf: B(0x4) yielded 192.0.2.129, Virtual-Access1
*Feb 3 16:30:57.436: NHRP: Send Resolution Reply via Virtual-Access1 vrf: B(0x4), packet size: 120
*Feb 3 16:30:57.436: src: 192.0.2.130, dst: 192.0.2.129
.
*Feb 3 16:30:57.437: src NBMA: 203.0.113.10
*Feb 3 16:30:57.437: src protocol: 192.0.2.129, dst protocol: 198.51.100.1
.
*Feb 3 16:30:57.437: client NBMA: 203.0.113.6
*Feb 3 16:30:57.437: client protocol: 192.0.2.130
*Feb 3 16:30:57.437: NHRP: 144 bytes out Virtual-Access1
示例2 — 利用NHRP安装的路由进行分支到分支通信
FlexVPN服务器
检验引入的总结路由的EIGRP拓扑:

FlexVPN客户端
检验是否存在总结路由:

尝试通过启动流量来建立分支到分支隧道:
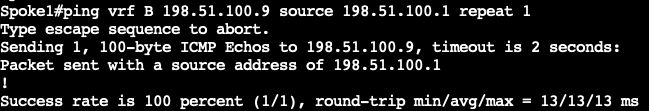
再次验证:
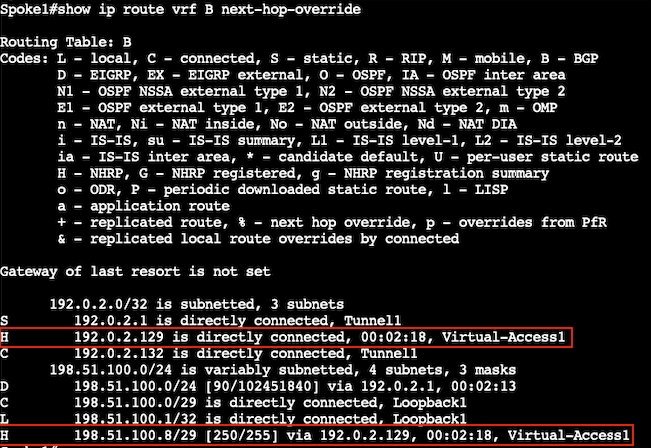
分支网络安装的调试输出有一个非常小的变化,其中显示路由安装成功而不是RIB故障并添加NHO:
*Feb 3 16:43:38.957: NHRP-CACHE: Virtual-Access1: Cache add for target 198.51.100.8/29 vrf: B(0x4) label none next-hop 192.0.2.131
*Feb 3 16:43:38.957: 203.0.113.10 (flags:0x1000)
*Feb 3 16:43:38.957: NHRP-RT: Adding route entry for 198.51.100.8/29 via 192.0.2.131, Virtual-Access1 vrf: B(0x4)) to RIB
*Feb 3 16:43:38.957: NHRP-RT: Route addition to RIB Successful
*Feb 3 16:43:38.957: NHRP-EVE: NHP-UP: 192.0.2.131, NBMA: 203.0.113.10
相关信息
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
2.0 |
06-May-2025
|
初始版本,格式设置。 |
1.0 |
25-Feb-2025
|
初始版本 |
 反馈
反馈