Configurar e verificar o NAT no FTD
Opções de download
Linguagem imparcial
O conjunto de documentação deste produto faz o possível para usar uma linguagem imparcial. Para os fins deste conjunto de documentação, a imparcialidade é definida como uma linguagem que não implica em discriminação baseada em idade, deficiência, gênero, identidade racial, identidade étnica, orientação sexual, status socioeconômico e interseccionalidade. Pode haver exceções na documentação devido à linguagem codificada nas interfaces de usuário do software do produto, linguagem usada com base na documentação de RFP ou linguagem usada por um produto de terceiros referenciado. Saiba mais sobre como a Cisco está usando a linguagem inclusiva.
Sobre esta tradução
A Cisco traduziu este documento com a ajuda de tecnologias de tradução automática e humana para oferecer conteúdo de suporte aos seus usuários no seu próprio idioma, independentemente da localização. Observe que mesmo a melhor tradução automática não será tão precisa quanto as realizadas por um tradutor profissional. A Cisco Systems, Inc. não se responsabiliza pela precisão destas traduções e recomenda que o documento original em inglês (link fornecido) seja sempre consultado.
Contents
Introdução
Este documento descreve como configurar e verificar a Network Address Translation (NAT) básica no Firepower Threat Defense (FTD).
Pré-requisitos
Requisitos
Não existem requisitos específicos para este documento.
Componentes Utilizados
As informações neste documento são baseadas nestas versões de software e hardware:
- ASA5506X que executa o código FTD 6.1.0-226
- FireSIGHT Management Center (FMC) com 6.1.0-226
- 3 hosts do Windows 7
- Roteador Cisco IOS® 3925 que executa VPN LAN a LAN (L2L)
Hora de conclusão do laboratório: 1 hora
As informações neste documento foram criadas a partir de dispositivos em um ambiente de laboratório específico. Todos os dispositivos utilizados neste documento foram iniciados com uma configuração (padrão) inicial. Se a rede estiver ativa, certifique-se de que você entenda o impacto potencial de qualquer comando.
Informações de Apoio
O FTD oferece suporte às mesmas opções de configuração de NAT que o ASA (Adaptive Security Appliance) clássico:
- Regras de NAT antes - Isso equivale ao NAT duas vezes (seção 1) no ASA clássico.
- Regras de NAT automático - Seção 2 sobre ASA clássico
- Regras de NAT depois - Isso equivale a duas vezes o NAT (seção 3) no ASA clássico.
Como a configuração do FTD é feita no FMC quando se trata da configuração do NAT, é necessário estar familiarizado com a GUI do FMC e as várias opções de configuração.
Configurar
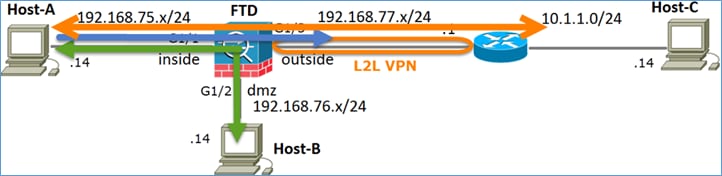
Diagrama de Rede
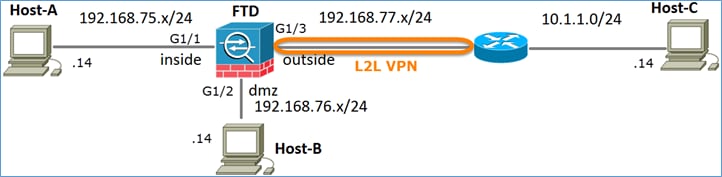
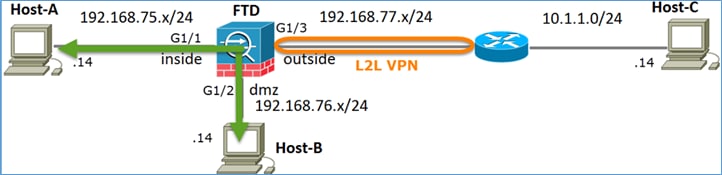
Tarefa 1. Configurar o NAT estático no FTD
Configure o NAT de acordo com estes requisitos:
| Nome da política de NAT |
Nome do dispositivo de FTD |
| Regra NAT |
Regra de NAT manual |
| Tipo de NAT |
Estático |
| Inserir |
Na Seção 1 |
| Interface de origem |
interno* |
| Interface de destino |
dmz* |
| Origem Original |
192.168.75.14 |
| Fonte traduzida |
192.168.76.100 |
*Usar Zonas de Segurança para a Regra NAT
NAT Estático
Solução:
No ASA clássico, você deve usar nameif nas regras de NAT. No FTD, você precisa usar Zonas de segurança ou Grupos de interface.
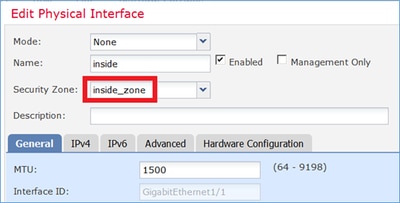
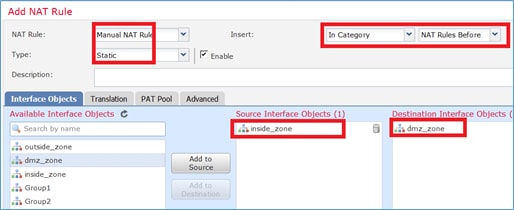
Etapa 1. Atribuir interfaces a Zonas de segurança/Grupos de interface.
Nesta tarefa, decidiu-se atribuir as interfaces de FTD que são usadas para NAT a Zonas de segurança. Como alternativa, você pode atribuí-los a Grupos de interface como mostrado na imagem.
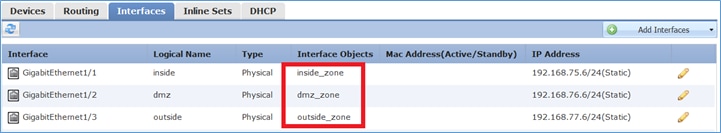
Etapa 2. O resultado é o mostrado na imagem.
Etapa 3. Você pode criar/editar Grupos de Interface e Zonas de Segurança na página Objetos > Gerenciamento de Objeto, conforme mostrado na imagem.
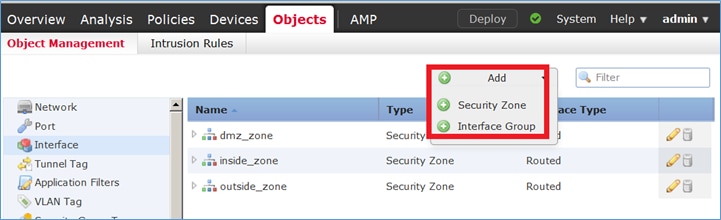
Zonas de segurança versus grupos de interface
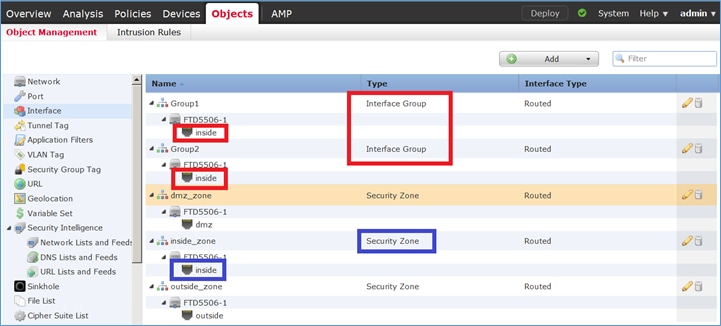
A principal diferença entre Zonas de segurança e Grupos de interface é que uma interface pode pertencer a apenas uma Zona de segurança, mas pode pertencer a vários Grupos de interface. Praticamente, os grupos de interface fornecem mais flexibilidade.
Você pode ver que a interface interna pertence a dois grupos de interface diferentes, mas apenas uma zona de segurança, como mostrado na imagem.
Etapa 4. Configurar o NAT estático no FTD.
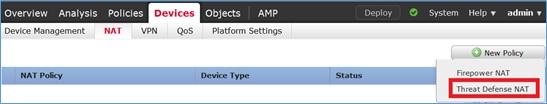
Navegue até Devices > NAT e crie uma política de NAT. Selecione New Policy > Threat Defense NAT como mostrado na imagem.
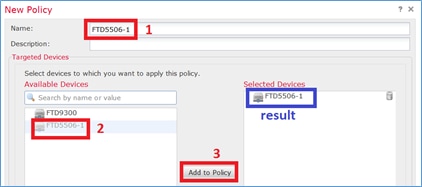
Etapa 5. Especifique o nome da política e atribua-o a um dispositivo de destino conforme mostrado na imagem.
Etapa 6. Adicione uma regra NAT à política, clique em Add Rule.
Especifique-os de acordo com os requisitos da tarefa, conforme mostrado nas imagens.
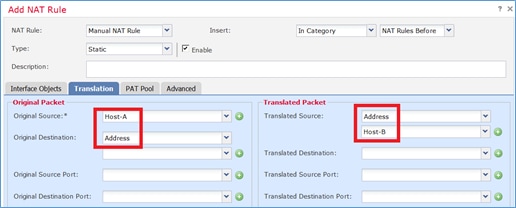
Host-A = 192.168.75.14
Host-B = 192.168.76.100
firepower# show run object object network Host-A host 192.168.75.14 object network Host-B host 192.168.76.100
aviso: Se você configurar o NAT estático e especificar uma interface como origem convertida, todo o tráfego destinado ao endereço IP da interface será redirecionado. Os usuários não podem acessar nenhum serviço habilitado na interface mapeada. Exemplos desses serviços incluem protocolos de roteamento como OSPF e EIGRP.
Etapa 7. O resultado é o mostrado na imagem.
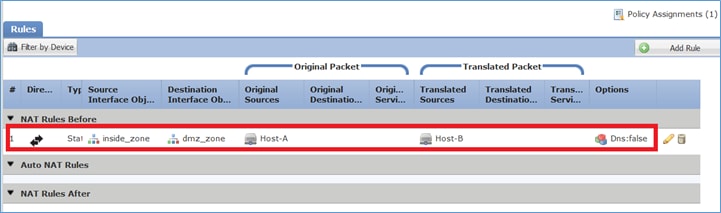
Etapa 8. Certifique-se de que haja uma política de controle de acesso que permita ao Host-B acessar o Host-A e vice-versa. Lembre-se de que o NAT estático é bidirecional por padrão. Semelhante aos ASAs clássicos, veja o uso de IPs reais. Isso é esperado, pois neste laboratório, o LINA executa o código 9.6.1.x, como mostrado na imagem.
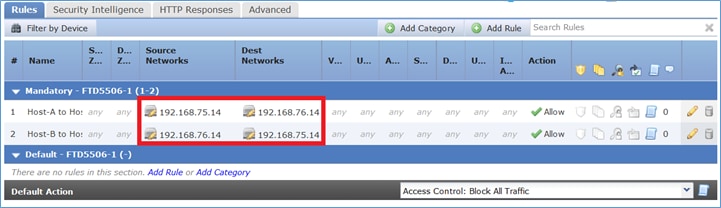
Verificação:
Do LINA CLI:
firepower# show run nat nat (inside,dmz) source static Host-A Host-B
A regra NAT foi inserida na Seção 1 como esperado:
firepower# show nat
Manual NAT Policies (Section 1)
1 (inside) to (dmz) source static Host-A Host-B
translate_hits = 0, untranslate_hits = 0
Note: Os 2 xlates criados em segundo plano.
firepower# show xlate
2 in use, 4 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.75.14 to dmz:192.168.76.100
flags sT idle 0:41:49 timeout 0:00:00
NAT from dmz:0.0.0.0/0 to inside:0.0.0.0/0
flags sIT idle 0:41:49 timeout 0:00:00
As tabelas NAT do ASP:
firepower# show asp table classify domain nat
Input Table
in id=0x7ff6036a9f50, priority=6, domain=nat, deny=false
hits=0, user_data=0x7ff60314dbf0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=dmz
in id=0x7ff603696860, priority=6, domain=nat, deny=false
hits=0, user_data=0x7ff602be3f80, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.76.100, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
Output Table:
L2 - Output Table:
L2 - Input Table:
Last clearing of hits counters: Never
firepower# show asp table classify domain nat-reverse
Input Table
Output Table:
out id=0x7ff603685350, priority=6, domain=nat-reverse, deny=false
hits=0, user_data=0x7ff60314dbf0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
out id=0x7ff603638470, priority=6, domain=nat-reverse, deny=false
hits=0, user_data=0x7ff602be3f80, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=dmz
L2 - Output Table:
L2 - Input Table:
Last clearing of hits counters: Never
Ative a captura com detalhes de rastreamento no FTD e faça ping do Host-B para o Host-A e como mostrado na imagem.
firepower# capture DMZ interface dmz trace detail match ip host 192.168.76.14 host 192.168.76.100 firepower# capture INSIDE interface inside trace detail match ip host 192.168.76.14 host 192.168.75.14
As contagens de ocorrências estão nas tabelas ASP:
firepower# show asp table classify domain nat
Input Table
in id=0x7ff6036a9f50, priority=6, domain=nat, deny=false
hits=0, user_data=0x7ff60314dbf0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=dmz
in id=0x7ff603696860, priority=6, domain=nat, deny=false
hits=4, user_data=0x7ff602be3f80, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.76.100, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
firepower# show asp table classify domain nat-reverse
Input Table
Output Table:
out id=0x7ff603685350, priority=6, domain=nat-reverse, deny=false
hits=4, user_data=0x7ff60314dbf0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
out id=0x7ff603638470, priority=6, domain=nat-reverse, deny=false
hits=0, user_data=0x7ff602be3f80, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=dmz
A captura de pacotes mostra:
firepower# show capture DMZ 8 packets captured 1: 17:38:26.324812 192.168.76.14 > 192.168.76.100: icmp: echo request 2: 17:38:26.326505 192.168.76.100 > 192.168.76.14: icmp: echo reply 3: 17:38:27.317991 192.168.76.14 > 192.168.76.100: icmp: echo request 4: 17:38:27.319456 192.168.76.100 > 192.168.76.14: icmp: echo reply 5: 17:38:28.316344 192.168.76.14 > 192.168.76.100: icmp: echo request 6: 17:38:28.317824 192.168.76.100 > 192.168.76.14: icmp: echo reply 7: 17:38:29.330518 192.168.76.14 > 192.168.76.100: icmp: echo request 8: 17:38:29.331983 192.168.76.100 > 192.168.76.14: icmp: echo reply 8 packets shown
Traços de um pacote (pontos importantes são destacados).
Note: A ID da regra NAT e sua correlação com a tabela ASP.
firepower# show capture DMZ packet-number 3 trace detail
8 packets captured
3: 17:38:27.317991 000c.2998.3fec d8b1.90b7.32e0 0x0800 Length: 74
192.168.76.14 > 192.168.76.100: icmp: echo request (ttl 128, id 9975)
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ff602c72be0, priority=13, domain=capture, deny=false
hits=55, user_data=0x7ff602b74a50, cs_id=0x0, l3_type=0x0
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
input_ifc=dmz, output_ifc=any
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ff603612200, priority=1, domain=permit, deny=false
hits=1, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=dmz, output_ifc=any
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,dmz) source static Host-A Host-B
Additional Information:
NAT divert to egress interface inside
Untranslate 192.168.76.100/0 to 192.168.75.14/0
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip host 192.168.76.14 host 192.168.75.14 rule-id 268434440
access-list CSM_FW_ACL_ remark rule-id 268434440: ACCESS POLICY: FTD5506-1 - Mandatory/2
access-list CSM_FW_ACL_ remark rule-id 268434440: L4 RULE: Host-B to Host-A
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Forward Flow based lookup yields rule:
in id=0x7ff602b72610, priority=12, domain=permit, deny=false
hits=1, user_data=0x7ff5fa9d0180, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.76.14, mask=255.255.255.255, port=0, tag=any, ifc=any
dst ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any, ifc=any, vlan=0, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 5
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ff60367cf80, priority=7, domain=conn-set, deny=false
hits=1, user_data=0x7ff603677080, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=any
Phase: 6
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,dmz) source static Host-A Host-B
Additional Information:
Static translate 192.168.76.14/1 to 192.168.76.14/1
Forward Flow based lookup yields rule:
in id=0x7ff603696860, priority=6, domain=nat, deny=false
hits=1, user_data=0x7ff602be3f80, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.76.100, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
Phase: 7
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ff602220020, priority=0, domain=nat-per-session, deny=true
hits=2, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ff6035c0af0, priority=0, domain=inspect-ip-options, deny=true
hits=1, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=any
Phase: 9
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ff602b5f020, priority=70, domain=inspect-icmp, deny=false
hits=2, user_data=0x7ff602be7460, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=any
Phase: 10
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ff602b3a6d0, priority=70, domain=inspect-icmp-error, deny=false
hits=2, user_data=0x7ff603672ec0, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=any
Phase: 11
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (inside,dmz) source static Host-A Host-B
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7ff603685350, priority=6, domain=nat-reverse, deny=false
hits=2, user_data=0x7ff60314dbf0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
Phase: 12
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7ff602220020, priority=0, domain=nat-per-session, deny=true
hits=4, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 13
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7ff602c56d10, priority=0, domain=inspect-ip-options, deny=true
hits=2, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=any
Phase: 14
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 5084, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_snort
snp_fp_inspect_icmp
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Module information for reverse flow ...
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_inspect_icmp
snp_fp_snort
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Phase: 15
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 16
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Verdict: (pass-packet) allow this packet
Phase: 17
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 192.168.75.14 using egress ifc inside
Phase: 18
Type: ADJACENCY-LOOKUP
Subtype: next-hop and adjacency
Result: ALLOW
Config:
Additional Information:
adjacency Active
next-hop mac address 000c.2930.2b78 hits 140694538708414
Phase: 19
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7ff6036a94e0, priority=13, domain=capture, deny=false
hits=14, user_data=0x7ff6024aff90, cs_id=0x0, l3_type=0x0
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
input_ifc=inside, output_ifc=any
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: allow
1 packet shown
Tarefa 2. Configurar a Conversão de Endereço de Porta (PAT) no FTD
Configure o NAT de acordo com estes requisitos:
| Regra NAT |
Regra de NAT manual |
| Tipo de NAT |
Dinâmico |
| Inserir |
Na Seção 1 |
| Interface de origem |
interno* |
| Interface de destino |
externo* |
| Origem Original |
192.168.75.0/24 |
| Fonte traduzida |
Interface externa (PAT) |
*Usar Zonas de Segurança para a Regra NAT
NAT Estático
PAT
Solução:
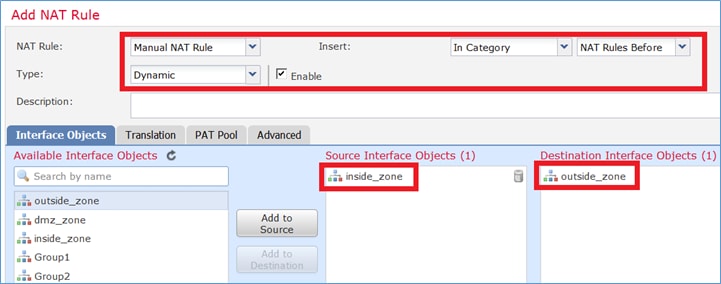
Etapa 1. Adicione uma segunda regra de NAT e configure de acordo com os requisitos da tarefa, conforme mostrado na imagem.
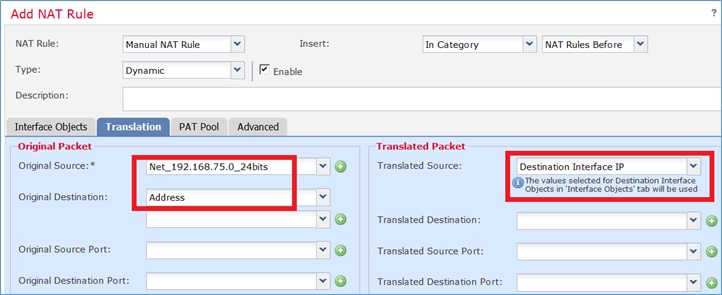
Etapa 2. Veja como o PAT é configurado conforme mostrado na imagem.
Etapa 3. O resultado é como mostrado na imagem.
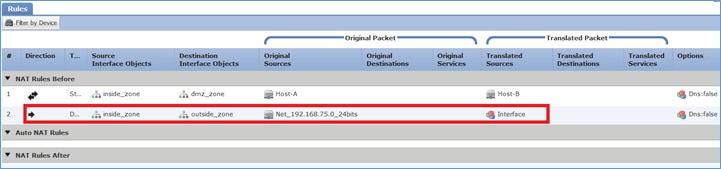
Etapa 4. Para o restante deste laboratório, configure a Política de Controle de Acesso para permitir a passagem de todo o tráfego.
Verificação:
Configuração de NAT:
firepower# show nat
Manual NAT Policies (Section 1)
1 (inside) to (dmz) source static Host-A Host-B
translate_hits = 26, untranslate_hits = 26
2 (inside) to (outside) source dynamic Net_192.168.75.0_24bits interface
translate_hits = 0, untranslate_hits = 0
No LINA CLI, observe a nova entrada:
firepower# show xlate
3 in use, 19 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.75.14 to dmz:192.168.76.100
flags sT idle 1:15:14 timeout 0:00:00
NAT from dmz:0.0.0.0/0 to inside:0.0.0.0/0
flags sIT idle 1:15:14 timeout 0:00:00
NAT from outside:0.0.0.0/0 to inside:0.0.0.0/0
flags sIT idle 0:04:02 timeout 0:00:00
Ative a captura na interface interna e externa. Na captura interna, habilite o rastreamento:
firepower# capture CAPI trace interface inside match ip host 192.168.75.14 host 192.168.77.1 firepower# capture CAPO interface outside match ip any host 192.168.77.1
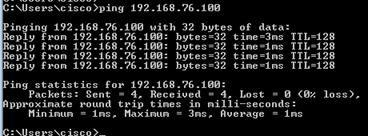
Faça um ping do Host-A (192.168.75.14) para o IP 192.168.77.1 como mostrado na imagem.
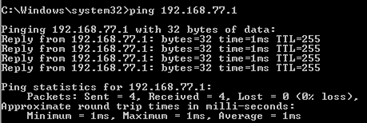
Nas capturas LINA, você pode ver a tradução PAT:
firepower# show cap CAPI 8 packets captured 1: 18:54:43.658001 192.168.75.14 > 192.168.77.1: icmp: echo request 2: 18:54:43.659099 192.168.77.1 > 192.168.75.14: icmp: echo reply 3: 18:54:44.668544 192.168.75.14 > 192.168.77.1: icmp: echo request 4: 18:54:44.669505 192.168.77.1 > 192.168.75.14: icmp: echo reply 5: 18:54:45.682368 192.168.75.14 > 192.168.77.1: icmp: echo request 6: 18:54:45.683421 192.168.77.1 > 192.168.75.14: icmp: echo reply 7: 18:54:46.696436 192.168.75.14 > 192.168.77.1: icmp: echo request 8: 18:54:46.697412 192.168.77.1 > 192.168.75.14: icmp: echo reply
firepower# show cap CAPO 8 packets captured 1: 18:54:43.658672 192.168.77.6 > 192.168.77.1: icmp: echo request 2: 18:54:43.658962 192.168.77.1 > 192.168.77.6: icmp: echo reply 3: 18:54:44.669109 192.168.77.6 > 192.168.77.1: icmp: echo request 4: 18:54:44.669337 192.168.77.1 > 192.168.77.6: icmp: echo reply 5: 18:54:45.682932 192.168.77.6 > 192.168.77.1: icmp: echo request 6: 18:54:45.683207 192.168.77.1 > 192.168.77.6: icmp: echo reply 7: 18:54:46.697031 192.168.77.6 > 192.168.77.1: icmp: echo request 8: 18:54:46.697275 192.168.77.1 > 192.168.77.6: icmp: echo reply
Rastreamentos de um pacote com seções importantes destacadas:
firepower# show cap CAPI packet-number 1 trace 8 packets captured 1: 18:54:43.658001 192.168.75.14 > 192.168.77.1: icmp: echo request Phase: 1 Type: CAPTURE Subtype: Result: ALLOW Config: Additional Information: MAC Access list Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: MAC Access list Phase: 3 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 192.168.77.1 using egress ifc outside Phase: 4 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group CSM_FW_ACL_ global access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268434434 access-list CSM_FW_ACL_ remark rule-id 268434434: ACCESS POLICY: FTD5506-1 - Default/1 access-list CSM_FW_ACL_ remark rule-id 268434434: L4 RULE: DEFAULT ACTION RULE Additional Information: This packet will be sent to snort for additional processing where a verdict will be reached Phase: 5 Type: CONN-SETTINGS Subtype: Result: ALLOW Config: class-map class-default match any policy-map global_policy class class-default set connection advanced-options UM_STATIC_TCP_MAP service-policy global_policy global Additional Information: Phase: 6 Type: NAT Subtype: Result: ALLOW Config: nat (inside,outside) source dynamic Net_192.168.75.0_24bits interface Additional Information: Dynamic translate 192.168.75.14/1 to 192.168.77.6/1 Phase: 7 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 8 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: class-map inspection_default match default-inspection-traffic policy-map global_policy class inspection_default inspect icmp service-policy global_policy global Additional Information: Phase: 10 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: Additional Information: Phase: 11 Type: NAT Subtype: rpf-check Result: ALLOW Config: nat (inside,outside) source dynamic Net_192.168.75.0_24bits interface Additional Information: Phase: 12 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 13 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 14 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 6981, packet dispatched to next module Phase: 15 Type: EXTERNAL-INSPECT Subtype: Result: ALLOW Config: Additional Information: Application: 'SNORT Inspect' Phase: 16 Type: SNORT Subtype: Result: ALLOW Config: Additional Information: Snort Verdict: (pass-packet) allow this packet Phase: 17 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 192.168.77.1 using egress ifc outside Phase: 18 Type: ADJACENCY-LOOKUP Subtype: next-hop and adjacency Result: ALLOW Config: Additional Information: adjacency Active next-hop mac address c84c.758d.4980 hits 140694538709114 Phase: 19 Type: CAPTURE Subtype: Result: ALLOW Config: Additional Information: MAC Access list Result: input-interface: outside input-status: up input-line-status: up output-interface: outside output-status: up output-line-status: up Action: allow 1 packet shown
O xlate dinâmico foi criado (observe os sinalizadores ri):
firepower# show xlate
4 in use, 19 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:192.168.75.14 to dmz:192.168.76.100
flags sT idle 1:16:47 timeout 0:00:00
NAT from dmz:0.0.0.0/0 to inside:0.0.0.0/0
flags sIT idle 1:16:47 timeout 0:00:00
NAT from outside:0.0.0.0/0 to inside:0.0.0.0/0
flags sIT idle 0:05:35 timeout 0:00:00
ICMP PAT from inside:192.168.75.14/1 to outside:192.168.77.6/1 flags ri idle 0:00:30 timeout 0:00:30
Nos registros LINA você vê:
firepower# show log May 31 2016 18:54:43: %ASA-7-609001: Built local-host inside:192.168.75.14 May 31 2016 18:54:43: %ASA-6-305011: Built dynamic ICMP translation from inside:192.168.75.14/1 to outside:192.168.77.6/1 May 31 2016 18:54:43: %ASA-7-609001: Built local-host outside:192.168.77.1 May 31 2016 18:54:43: %ASA-6-302020: Built inbound ICMP connection for faddr 192.168.75.14/1 gaddr 192.168.77.1/0 laddr 192.168.77.1/0 May 31 2016 18:54:43: %ASA-6-302021: Teardown ICMP connection for faddr 192.168.75.14/1 gaddr 192.168.77.1/0 laddr 192.168.77.1/0 May 31 2016 18:54:43: %ASA-7-609002: Teardown local-host outside:192.168.77.1 duration 0:00:00 May 31 2016 18:55:17: %ASA-6-305012: Teardown dynamic ICMP translation from inside:192.168.75.14/1 to outside:192.168.77.6/1 duration 0:00:34
Seções NAT:
firepower# show nat
Manual NAT Policies (Section 1)
1 (inside) to (dmz) source static Host-A Host-B
translate_hits = 26, untranslate_hits = 26
2 (inside) to (outside) source dynamic Net_192.168.75.0_24bits interface
translate_hits = 94, untranslate_hits = 138
As tabelas ASP mostram:
firepower# show asp table classify domain nat
Input Table
in id=0x7ff6036a9f50, priority=6, domain=nat, deny=false
hits=0, user_data=0x7ff60314dbf0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=dmz
in id=0x7ff603696860, priority=6, domain=nat, deny=false
hits=4, user_data=0x7ff602be3f80, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.76.100, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
in id=0x7ff602c75f00, priority=6, domain=nat, deny=false
hits=94, user_data=0x7ff6036609a0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.75.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=outside
in id=0x7ff603681fb0, priority=6, domain=nat, deny=false
hits=276, user_data=0x7ff60249f370, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.77.6, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=inside
firepower# show asp table classify domain nat-reverse
Input Table
Output Table:
out id=0x7ff603685350, priority=6, domain=nat-reverse, deny=false
hits=4, user_data=0x7ff60314dbf0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=dmz, output_ifc=inside
out id=0x7ff603638470, priority=6, domain=nat-reverse, deny=false
hits=0, user_data=0x7ff602be3f80, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.75.14, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=dmz
out id=0x7ff60361bda0, priority=6, domain=nat-reverse, deny=false
hits=138, user_data=0x7ff6036609a0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=192.168.75.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=inside
out id=0x7ff60361c180, priority=6, domain=nat-reverse, deny=false
hits=94, user_data=0x7ff60249f370, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.75.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=outside
Tarefa 3. Configurar a isenção de NAT no FTD
Configure o NAT de acordo com estes requisitos:
| Regra NAT |
Regra de NAT manual |
| Tipo de NAT |
Estático |
| Inserir |
Na seção 1, todas as regras |
| Interface de origem |
interno* |
| Interface de destino |
externo* |
| Origem Original |
192.168.75.0/24 |
| Fonte traduzida |
192.168.75.0/24 |
| Destino original |
10.1.1.0/24 |
| Destino traduzido |
10.1.1.0/24 |
*Usar Zonas de Segurança para a Regra NAT
NAT Estático
PAT
Isenção de NAT
Solução:
Etapa 1. Adicione uma terceira regra de NAT e configure os requisitos por tarefa conforme mostrado na imagem.
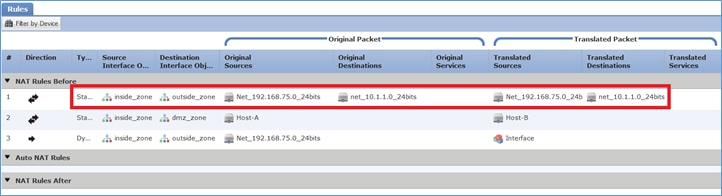
Etapa 2. Executar Pesquisa de Rota para determinação da interface de saída.
Note: Para regras de NAT de identidade, como a que você adicionou, você pode alterar como a interface de saída é determinada e usar a pesquisa de rota normal como mostrado na imagem.
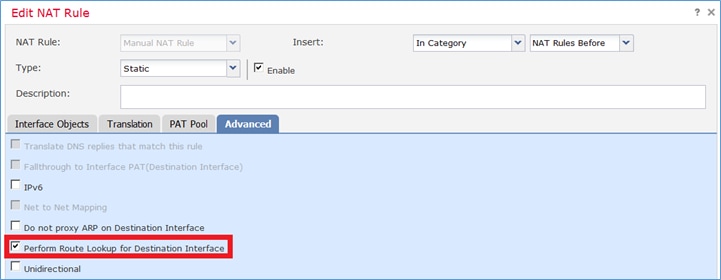
Verificação:
firepower# show run nat nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits nat (inside,dmz) source static Host-A Host-B nat (inside,outside) source dynamic Net_192.168.75.0_24bits interface
firepower# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits
translate_hits = 0, untranslate_hits = 0
2 (inside) to (dmz) source static Host-A Host-B
translate_hits = 26, untranslate_hits = 26
3 (inside) to (outside) source dynamic Net_192.168.75.0_24bits interface
translate_hits = 96, untranslate_hits = 138
Execute o packet-tracer para o tráfego não VPN originado na rede interna. A regra PAT é usada como esperado:
firepower# packet-tracer input inside tcp 192.168.75.14 1111 192.168.77.1 80 Phase: 1 Type: CAPTURE Subtype: Result: ALLOW Config: Additional Information: MAC Access list Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: MAC Access list Phase: 3 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 192.168.77.1 using egress ifc outside Phase: 4 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group CSM_FW_ACL_ global access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268434434 access-list CSM_FW_ACL_ remark rule-id 268434434: ACCESS POLICY: FTD5506-1 - Default/1 access-list CSM_FW_ACL_ remark rule-id 268434434: L4 RULE: DEFAULT ACTION RULE Additional Information: This packet will be sent to snort for additional processing where a verdict will be reached Phase: 5 Type: CONN-SETTINGS Subtype: Result: ALLOW Config: class-map class-default match any policy-map global_policy class class-default set connection advanced-options UM_STATIC_TCP_MAP service-policy global_policy global Additional Information: Phase: 6 Type: NAT Subtype: Result: ALLOW Config: nat (inside,outside) source dynamic Net_192.168.75.0_24bits interface Additional Information: Dynamic translate 192.168.75.14/1111 to 192.168.77.6/1111 Phase: 7 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 8 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: NAT Subtype: rpf-check Result: ALLOW Config: nat (inside,outside) source dynamic Net_192.168.75.0_24bits interface Additional Information: Phase: 10 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 11 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 12 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 7227, packet dispatched to next module Result: input-interface: inside input-status: up input-line-status: up output-interface: outside output-status: up output-line-status: up Action: allow
Execute o packet-tracer para o tráfego que deve passar pelo túnel VPN (execute-o duas vezes desde a primeira tentativa ativa o túnel VPN).
Note: Você deve escolher a Regra de isenção de NAT.
Primeira tentativa do packet-tracer:
firepower# packet-tracer input inside tcp 192.168.75.14 1111 10.1.1.1 80 Phase: 1 Type: CAPTURE Subtype: Result: ALLOW Config: Additional Information: MAC Access list Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: MAC Access list Phase: 3 Type: UN-NAT Subtype: static Result: ALLOW Config: nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits Additional Information: NAT divert to egress interface outside Untranslate 10.1.1.1/80 to 10.1.1.1/80 Phase: 4 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group CSM_FW_ACL_ global access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268434434 access-list CSM_FW_ACL_ remark rule-id 268434434: ACCESS POLICY: FTD5506-1 - Default/1 access-list CSM_FW_ACL_ remark rule-id 268434434: L4 RULE: DEFAULT ACTION RULE Additional Information: This packet will be sent to snort for additional processing where a verdict will be reached Phase: 5 Type: CONN-SETTINGS Subtype: Result: ALLOW Config: class-map class-default match any policy-map global_policy class class-default set connection advanced-options UM_STATIC_TCP_MAP service-policy global_policy global Additional Information: Phase: 6 Type: NAT Subtype: Result: ALLOW Config: nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits Additional Information: Static translate 192.168.75.14/1111 to 192.168.75.14/1111 Phase: 7 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 8 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: VPN Subtype: encrypt Result: DROP Config: Additional Information: Result: input-interface: inside input-status: up input-line-status: up output-interface: outside output-status: up output-line-status: up Action: drop Drop-reason: (acl-drop) Flow is denied by configured rule
Segunda tentativa do packet-tracer:
firepower# packet-tracer input inside tcp 192.168.75.14 1111 10.1.1.1 80 Phase: 1 Type: CAPTURE Subtype: Result: ALLOW Config: Additional Information: MAC Access list Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: MAC Access list Phase: 3 Type: UN-NAT Subtype: static Result: ALLOW Config: nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits Additional Information: NAT divert to egress interface outside Untranslate 10.1.1.1/80 to 10.1.1.1/80 Phase: 4 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group CSM_FW_ACL_ global access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268434434 access-list CSM_FW_ACL_ remark rule-id 268434434: ACCESS POLICY: FTD5506-1 - Default/1 access-list CSM_FW_ACL_ remark rule-id 268434434: L4 RULE: DEFAULT ACTION RULE Additional Information: This packet will be sent to snort for additional processing where a verdict will be reached Phase: 5 Type: CONN-SETTINGS Subtype: Result: ALLOW Config: class-map class-default match any policy-map global_policy class class-default set connection advanced-options UM_STATIC_TCP_MAP service-policy global_policy global Additional Information: Phase: 6 Type: NAT Subtype: Result: ALLOW Config: nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits Additional Information: Static translate 192.168.75.14/1111 to 192.168.75.14/1111 Phase: 7 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 8 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: VPN Subtype: encrypt Result: ALLOW Config: Additional Information: Phase: 10 Type: NAT Subtype: rpf-check Result: ALLOW Config: nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits Additional Information: Phase: 11 Type: VPN Subtype: ipsec-tunnel-flow Result: ALLOW Config: Additional Information: Phase: 12 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 13 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 14 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 7226, packet dispatched to next module Result: input-interface: inside input-status: up input-line-status: up output-interface: outside output-status: up output-line-status: up Action: allow
Verificação de contagem de ocorrências de NAT:
firepower# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits
translate_hits = 9, untranslate_hits = 9
2 (inside) to (dmz) source static Host-A Host-B
translate_hits = 26, untranslate_hits = 26
3 (inside) to (outside) source dynamic Net_192.168.75.0_24bits interface
translate_hits = 98, untranslate_hits = 138
Tarefa 4. Configurar o NAT do objeto no FTD
Configure o NAT de acordo com estes requisitos:
| Regra NAT |
Regra de NAT automática |
| Tipo de NAT |
Estático |
| Inserir |
Na Seção 2 |
| Interface de origem |
interno* |
| Interface de destino |
dmz* |
| Origem Original |
192.168.75.99 |
| Fonte traduzida |
192.168.76.99 |
| Traduzir respostas DNS que correspondam a esta regra |
Habilitado |
*Usar Zonas de Segurança para a Regra NAT
Solução:
Etapa 1. Configure a regra de acordo com os requisitos da tarefa conforme mostrado nas imagens.
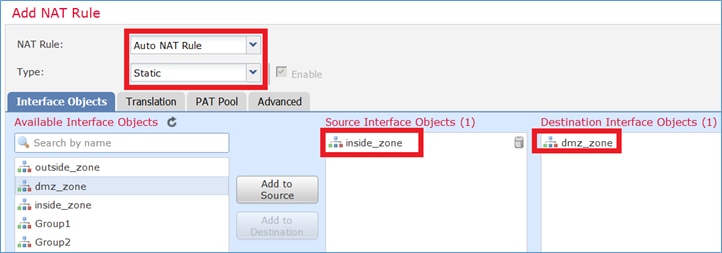
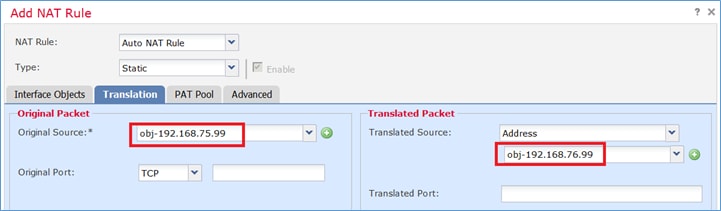
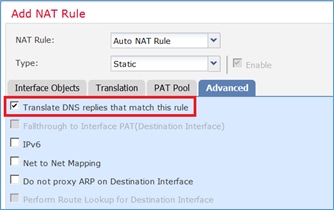
Etapa 2. O resultado é como mostrado na imagem.
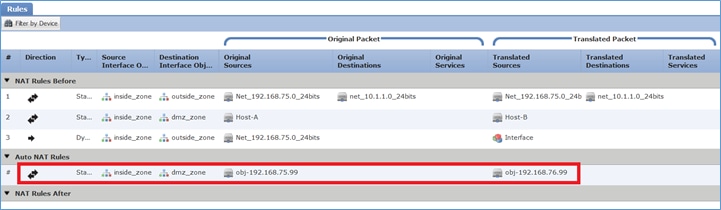
Verificação:
firepower# show run nat nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits nat (inside,dmz) source static Host-A Host-B nat (inside,outside) source dynamic Net_192.168.75.0_24bits interface ! object network obj-192.168.75.99 nat (inside,dmz) static obj-192.168.76.99 dns
firepower# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits
translate_hits = 9, untranslate_hits = 9
2 (inside) to (dmz) source static Host-A Host-B
translate_hits = 26, untranslate_hits = 26
3 (inside) to (outside) source dynamic Net_192.168.75.0_24bits interface
translate_hits = 98, untranslate_hits = 138
Auto NAT Policies (Section 2)
1 (inside) to (dmz) source static obj-192.168.75.99 obj-192.168.76.99 dns
translate_hits = 0, untranslate_hits = 0
Verificação com o packet-tracer:
firepower# packet-tracer input inside tcp 192.168.75.99 1111 192.168.76.100 80 Phase: 1 Type: CAPTURE Subtype: Result: ALLOW Config: Additional Information: MAC Access list Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: MAC Access list Phase: 3 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 192.168.76.100 using egress ifc dmz Phase: 4 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group CSM_FW_ACL_ global access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268434434 access-list CSM_FW_ACL_ remark rule-id 268434434: ACCESS POLICY: FTD5506-1 - Default/1 access-list CSM_FW_ACL_ remark rule-id 268434434: L4 RULE: DEFAULT ACTION RULE Additional Information: This packet will be sent to snort for additional processing where a verdict will be reached Phase: 5 Type: CONN-SETTINGS Subtype: Result: ALLOW Config: class-map class-default match any policy-map global_policy class class-default set connection advanced-options UM_STATIC_TCP_MAP service-policy global_policy global Additional Information: Phase: 6 Type: NAT Subtype: Result: ALLOW Config: object network obj-192.168.75.99 nat (inside,dmz) static obj-192.168.76.99 dns Additional Information: Static translate 192.168.75.99/1111 to 192.168.76.99/1111 Phase: 7 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 8 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 10 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 11 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 7245, packet dispatched to next module Result: input-interface: inside input-status: up input-line-status: up output-interface: dmz output-status: up output-line-status: up Action: allow
Tarefa 5. Configurar o pool PAT no FTD
Configure o NAT de acordo com estes requisitos:
| Regra NAT |
Regra de NAT manual |
| Tipo de NAT |
Dinâmico |
| Inserir |
Na Seção 3 |
| Interface de origem |
interno* |
| Interface de destino |
dmz* |
| Origem Original |
192.168.75.0/24 |
| Fonte traduzida |
192.168.76.20-22 |
| Usar todo o intervalo (1-65535) |
Habilitado |
*Usar Zonas de Segurança para a Regra NAT
Solução:
Etapa 1. Configure os requisitos da regra por tarefa conforme mostrado nas imagens.
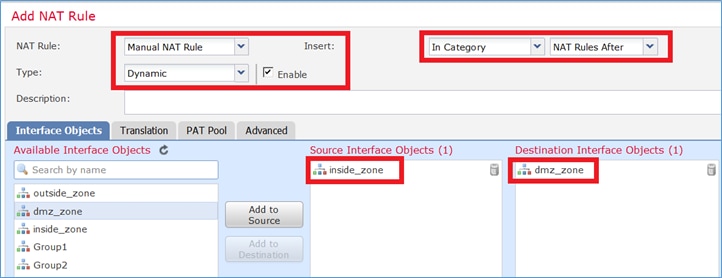
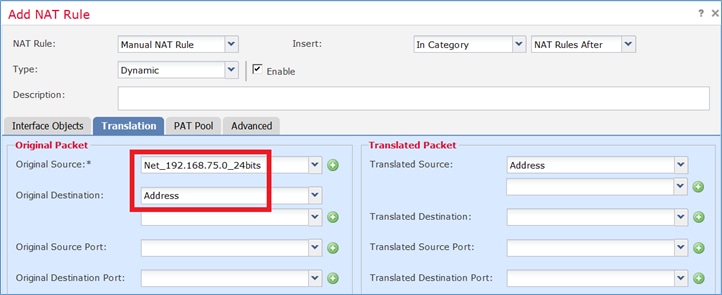
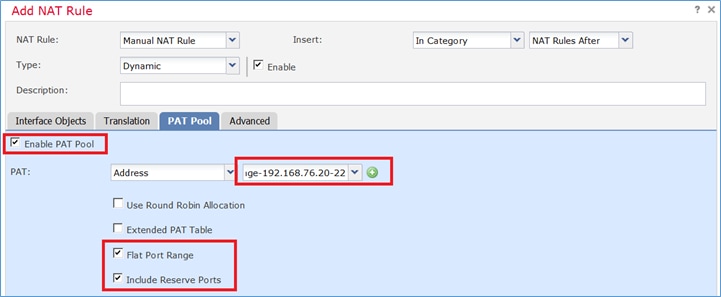
Etapa 2. Ative Flat Port Range com Include Reserver Ports que permite o uso de todo o intervalo (1-65535) conforme mostrado na imagem.
Etapa 3. O resultado é como mostrado na imagem.
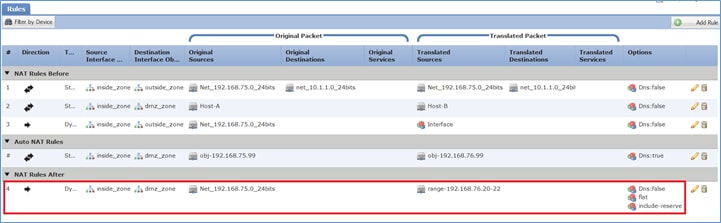
Verificação:
firepower# show run nat nat (inside,outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits nat (inside,dmz) source static Host-A Host-B nat (inside,outside) source dynamic Net_192.168.75.0_24bits interface ! object network obj-192.168.75.99 nat (inside,dmz) static obj-192.168.76.99 dns ! nat (inside,dmz) after-auto source dynamic Net_192.168.75.0_24bits pat-pool range-192.168.76.20-22 flat include-reserve
A regra está na Seção 3:
firepower# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static Net_192.168.75.0_24bits Net_192.168.75.0_24bits destination static net_10.1.1.0_24bits net_10.1.1.0_24bits
translate_hits = 9, untranslate_hits = 9
2 (inside) to (dmz) source static Host-A Host-B
translate_hits = 26, untranslate_hits = 26
3 (inside) to (outside) source dynamic Net_192.168.75.0_24bits interface
translate_hits = 98, untranslate_hits = 138
Auto NAT Policies (Section 2)
1 (inside) to (dmz) source static obj-192.168.75.99 obj-192.168.76.99 dns
translate_hits = 1, untranslate_hits = 0
Manual NAT Policies (Section 3)
1 (inside) to (dmz) source dynamic Net_192.168.75.0_24bits pat-pool range-192.168.76.20-22 flat include-reserve
translate_hits = 0, untranslate_hits = 0
Verificação do Packet Tracer:
firepower# packet-tracer input inside icmp 192.168.75.15 8 0 192.168.76.5 Phase: 1 Type: CAPTURE Subtype: Result: ALLOW Config: Additional Information: MAC Access list Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: MAC Access list Phase: 3 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 192.168.76.5 using egress ifc dmz Phase: 4 Type: ACCESS-LIST Subtype: log Result: ALLOW Config: access-group CSM_FW_ACL_ global access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268434434 access-list CSM_FW_ACL_ remark rule-id 268434434: ACCESS POLICY: FTD5506-1 - Default/1 access-list CSM_FW_ACL_ remark rule-id 268434434: L4 RULE: DEFAULT ACTION RULE Additional Information: This packet will be sent to snort for additional processing where a verdict will be reached Phase: 5 Type: CONN-SETTINGS Subtype: Result: ALLOW Config: class-map class-default match any policy-map global_policy class class-default set connection advanced-options UM_STATIC_TCP_MAP service-policy global_policy global Additional Information: Phase: 6 Type: NAT Subtype: Result: ALLOW Config: nat (inside,dmz) after-auto source dynamic Net_192.168.75.0_24bits pat-pool range-192.168.76.20-22 flat include-reserve Additional Information: Dynamic translate 192.168.75.15/0 to 192.168.76.20/11654 Phase: 7 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 8 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 9 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: class-map inspection_default match default-inspection-traffic policy-map global_policy class inspection_default inspect icmp service-policy global_policy global Additional Information: Phase: 10 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: Additional Information: Phase: 11 Type: NAT Subtype: rpf-check Result: ALLOW Config: nat (inside,dmz) after-auto source dynamic Net_192.168.75.0_24bits pat-pool range-192.168.76.20-22 flat include-reserve Additional Information: Phase: 12 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 13 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 14 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 7289, packet dispatched to next module Result: input-interface: inside input-status: up input-line-status: up output-interface: dmz output-status: up output-line-status: up Action: allow
Verificar
Use esta seção para confirmar se a sua configuração funciona corretamente.
A verificação foi explicada nas seções de tarefas individuais.
Troubleshooting
Esta seção disponibiliza informações para a solução de problemas de configuração.
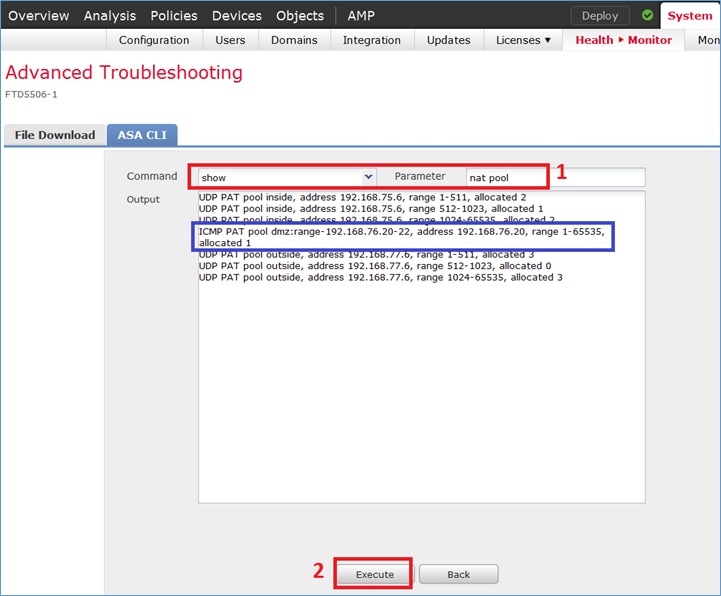
Abra a página Advanced Troubleshooting no FMC, execute o packet-tracer e execute o comando show nat pool.

Note: A entrada que usa todo o intervalo como mostrado na imagem.
Informações Relacionadas
- Todas as versões do guia de configuração do Cisco Firepower Management Center podem ser encontradas aqui:
Navegação na documentação do Cisco Secure Firewall Threat Defense
- O Cisco Global Technical Assistance Center (TAC) recomenda enfaticamente este guia visual para conhecimento prático aprofundado sobre as tecnologias de segurança de próxima geração Cisco Firepower, que inclui as mencionadas neste artigo:
Cisco Press - Defesa contra ameaças do Firepower
- Para todas as Notas técnicas de configuração e solução de problemas referentes às tecnologias do Firepower:
Histórico de revisões
| Revisão | Data de publicação | Comentários |
|---|---|---|
3.0 |
19-Dec-2024
|
Código da caixa de informações internas da Cisco atualizado para vermelho e formatação. |
2.0 |
02-Aug-2023
|
Texto Alt adicionado.
Otimização de mecanismo de pesquisa, tradução automática, requisitos de estilo e formatação atualizados. |
1.0 |
29-Jan-2018
|
Versão inicial |
Colaborado por engenheiros da Cisco
- Mikis ZafeiroudisEngenheiro de consultoria técnica
- John LongEngenheiro de consultoria técnica
Contate a Cisco
- Abrir um caso de suporte

- (É necessário um Contrato de Serviço da Cisco)
 Feedback
Feedback