Configurar túneis de site a site IKEv1 IPsec com o ASDM ou CLI no ASAv1
Opções de download
Linguagem imparcial
O conjunto de documentação deste produto faz o possível para usar uma linguagem imparcial. Para os fins deste conjunto de documentação, a imparcialidade é definida como uma linguagem que não implica em discriminação baseada em idade, deficiência, gênero, identidade racial, identidade étnica, orientação sexual, status socioeconômico e interseccionalidade. Pode haver exceções na documentação devido à linguagem codificada nas interfaces de usuário do software do produto, linguagem usada com base na documentação de RFP ou linguagem usada por um produto de terceiros referenciado. Saiba mais sobre como a Cisco está usando a linguagem inclusiva.
Sobre esta tradução
A Cisco traduziu este documento com a ajuda de tecnologias de tradução automática e humana para oferecer conteúdo de suporte aos seus usuários no seu próprio idioma, independentemente da localização. Observe que mesmo a melhor tradução automática não será tão precisa quanto as realizadas por um tradutor profissional. A Cisco Systems, Inc. não se responsabiliza pela precisão destas traduções e recomenda que o documento original em inglês (link fornecido) seja sempre consultado.
Introdução
Este documento descreve como configurar um túnel IPsec site a site IKEv1 entre dois Cisco Secure Firewall Virtual (ASAv) executando v9.18.3.
Pré-requisitos
Requisitos
A Cisco recomenda que você tenha conhecimento destes tópicos:
- A conectividade IP de ponta a ponta deve ser estabelecida
- Estes protocolos devem ser permitidos:
- User Datagram Protocol (UDP) 500 e 4500 para o plano de controle IPsec
- Encapsulating Security Payload (ESP) IP Protocol 50 para o plano de dados IPsec
Componentes Utilizados
As informações neste documento são baseadas nestas versões de software e hardware:
- Cisco Secure Firewall ASA Virtual que executa a versão de software 9.18.3
As informações neste documento foram criadas a partir de dispositivos em um ambiente de laboratório específico. Todos os dispositivos utilizados neste documento foram iniciados com uma configuração (padrão) inicial. Se a rede estiver ativa, certifique-se de que você entenda o impacto potencial de qualquer comando.
Configurar
Esta seção descreve como configurar o túnel VPN site a site por meio do assistente de VPN do ASDM (Adaptive Security Device Manager) ou por meio da CLI.
Diagrama de Rede
Esta topologia é usada para os exemplos deste documento:
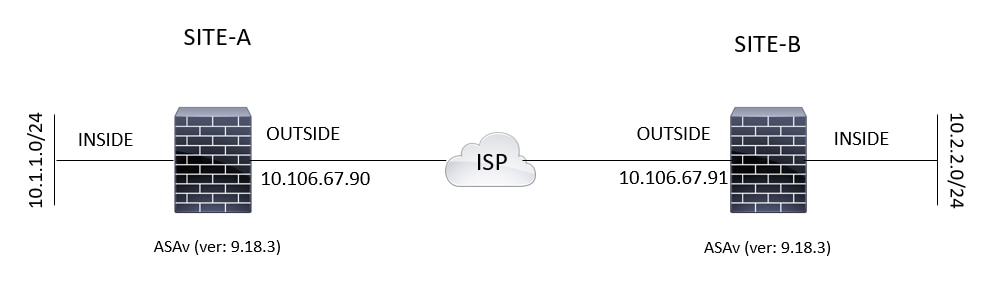 Diagrama de topologia
Diagrama de topologia
Configurar por meio do assistente de VPN do ASDM
Siga estas etapas para configurar o túnel VPN site a site por meio do assistente do ASDM:
- Abra o ASDM e navegue até
Wizards > VPN Wizards > Site-to-site VPN Wizard.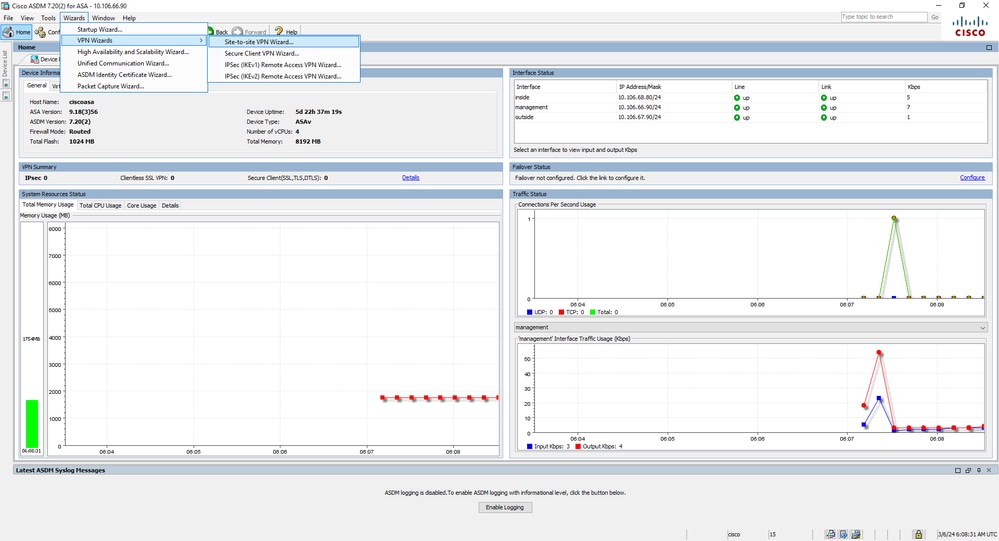 Navegação do Assistente de VPN
Navegação do Assistente de VPN - Clique
Next em quando chegar à home page do assistente. Janela 1 do Assistente de VPN
Janela 1 do Assistente de VPN Observação: as versões mais recentes do ASDM fornecem um link para um vídeo que explica essa configuração.
- Configure o endereço IP do par. Neste exemplo, o endereço IP do par é definido como 10.106.67.91 no site B. Se você configurar o endereço IP do par no site A, ele deve ser alterado para 10.106.67.90. A interface através da qual a extremidade remota pode ser alcançada também é especificada. Clique em
Next depois de concluir.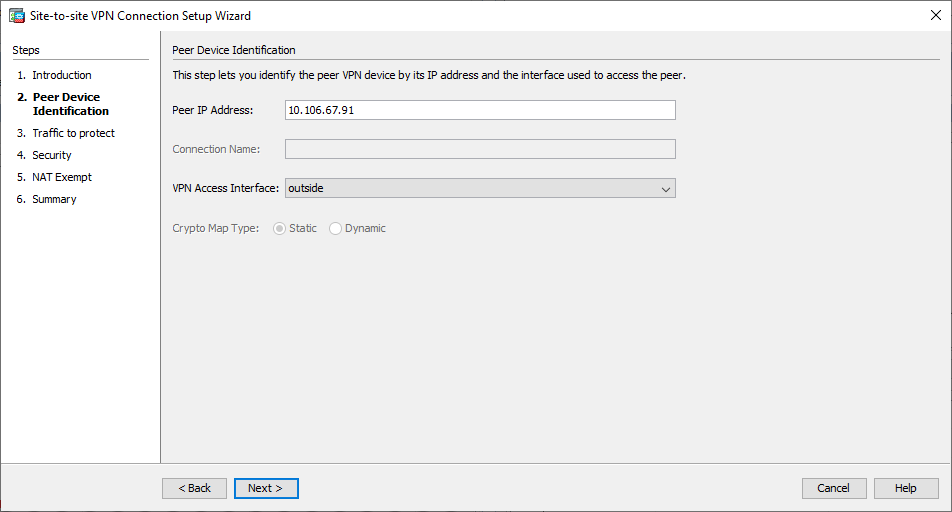 Janela 2 do Assistente de VPN
Janela 2 do Assistente de VPN - Configure as redes locais e remotas (origem e destino do tráfego). Esta imagem mostra a configuração para o Site B (o inverso se aplica ao Site A).
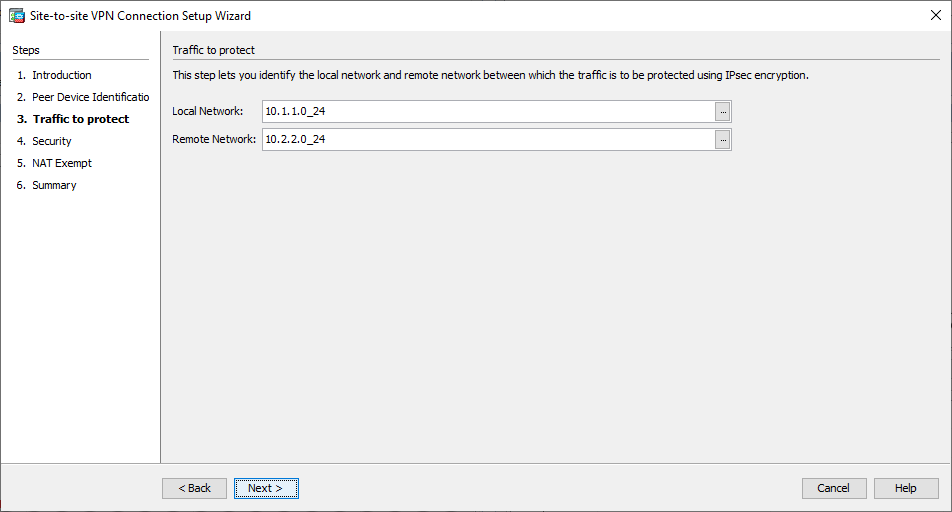 Janela 3 do Assistente de VPN
Janela 3 do Assistente de VPN - Na página Segurança, configure a chave pré-compartilhada (ela deve corresponder em ambas as extremidades). Clique em
Next depois de concluir.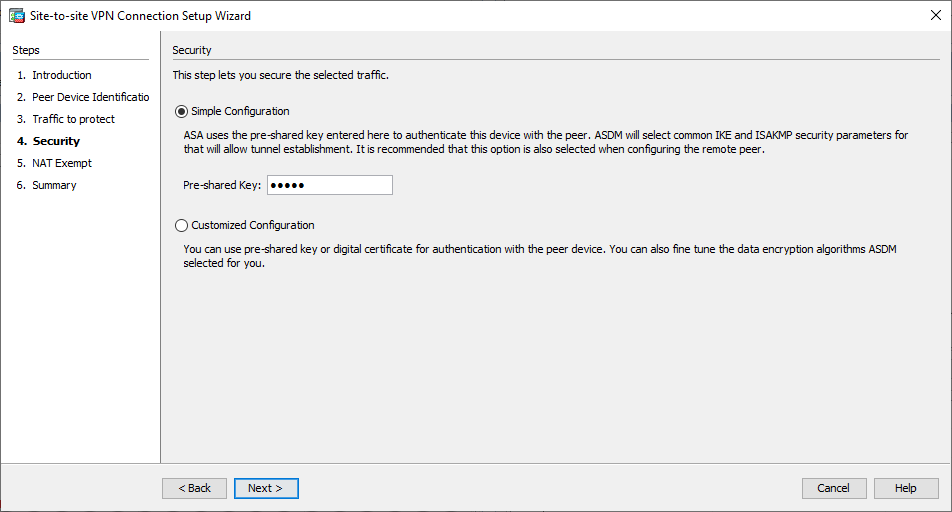 Janela 4 do assistente de VPN
Janela 4 do assistente de VPN - Configure a interface de origem para o tráfego no ASA. O ASDM cria automaticamente a regra de Network Address Translation (NAT) com base na versão do ASA e a envia com o restante da configuração na etapa final.
Observação: no exemplo usado neste documento, 'inside' é a origem do tráfego.
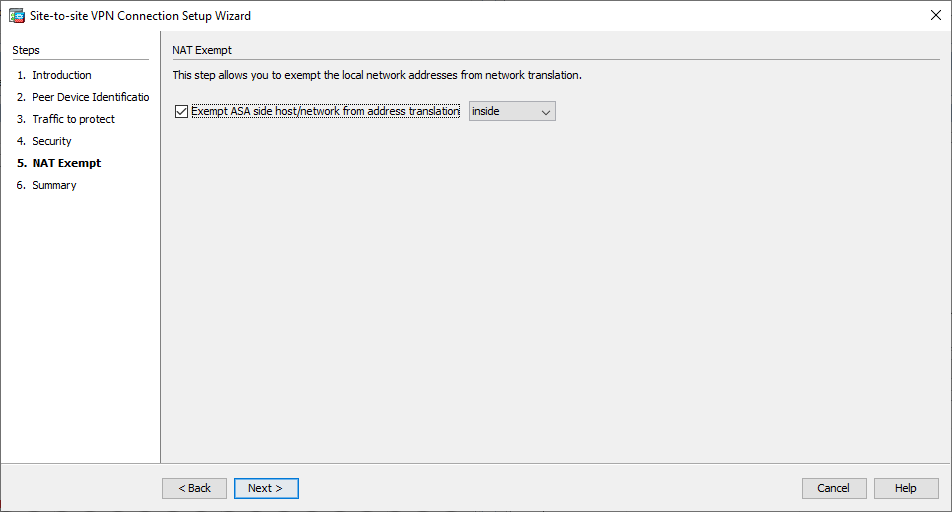 Janela 5 do Assistente de VPN
Janela 5 do Assistente de VPN - O assistente agora fornece um resumo da configuração que é enviada para o ASA. Revise e verifique as definições de configuração e clique em
Finish.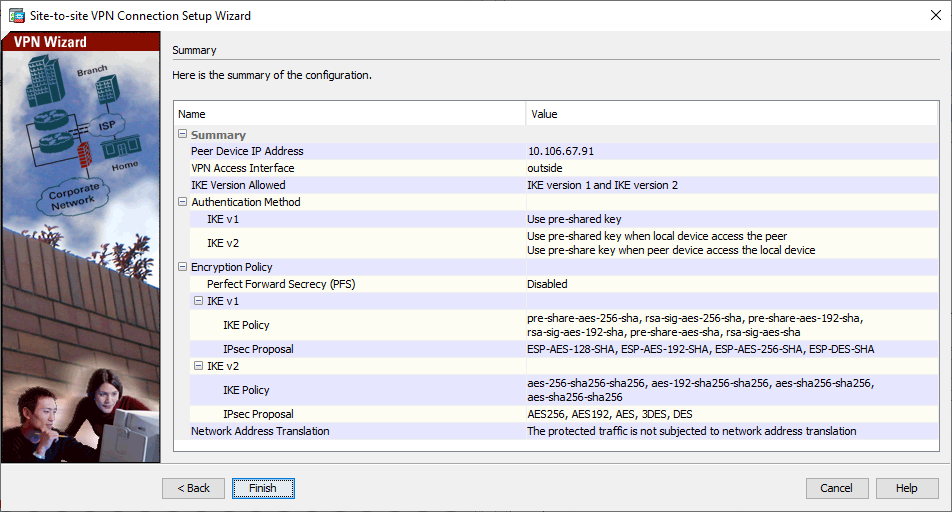 Janela 6 do Assistente de VPN
Janela 6 do Assistente de VPN
Configurar por meio da CLI
Configurar por meio da CLIEsta seção descreve como configurar o túnel site a site IPsec IKEv1 por meio da CLI.
Configurar Site B
Configurar Site BDica: para obter um exemplo de configuração IKEv2 com o ASA, consulte o documento IKEv2 Tunnel entre sites do ASA e Exemplos de Configuração de Roteador da Cisco.
Fase 1 (IKEv1)
Siga estas etapas para a configuração da Fase 1:
- Digite este comando na CLI para ativar o IKEv1 na interface externa:
crypto ikev1 enable outside
- Crie uma política de IKEv1 que defina os algoritmos/métodos a serem usados para hash, autenticação, grupo Diffie-Hellman, vida útil e criptografia:
crypto ikev1 policy 1
! The 1 in the above command refers to the Policy suite priority (1 highest, 65535 lowest)
authentication pre-share
encryption aes-256
hash sha
group 14
lifetime 86400 - Crie um grupo de túneis nos atributos de IPsec e configure o endereço IP do par e a chave pré-compartilhada do túnel:
tunnel-group 10.106.67.90 type ipsec-l2l
tunnel-group 10.106.67.90 ipsec-attributes
ikev1 pre-shared-key cisco
! Note the IKEv1 keyword at the beginning of the pre-shared-key command.
Fase 2 (IPsec)
Siga estas etapas para a configuração da Fase 2:
- Crie uma lista de acesso que defina o tráfego a ser criptografado e encapsulado. Neste exemplo, o tráfego de interesse é o tráfego do túnel originado da sub-rede 10.2.2.0 para 10.1.1.0. Ele pode conter várias entradas, se houver várias sub-redes envolvidas entre os sites.
object network 10.2.2.0_24
subnet 10.2.2.0 255.255.255.0
object network 10.1.1.0_24
subnet 10.1.1.0 255.255.255.0
access-list 100 extended permit ip object 10.2.2.0_24 object 10.1.1.0_24 - Configure o Transform Set (TS), que deve envolver a palavra-chave
IKEv1. Um TS idêntico também deve ser criado na extremidade remota.
crypto ipsec ikev1 transform-set myset esp-aes-256 esp-sha-hmac
- Configure um mapa de criptografia que contenha estes componentes:
- O endereço IP do par
- A lista de acesso definida que contenha o tráfego de interesse
- O TS
- Uma configuração opcional de PFS (Perfect Forward Secrecy), que cria um novo par de chaves Diffie-Hellman usadas para proteger os dados (ambos os lados devem ser habilitados para PFS, antes que a Fase 2 seja iniciada)
- Aplique o mapa de criptografia na interface externa:
crypto map outside_map 20 match address 100
crypto map outside_map 20 set peer 10.106.67.90
crypto map outside_map 20 set ikev1 transform-set myset
crypto map outside_map 20 set pfs
crypto map outside_map interface outside
Isenção de NAT
Verifique se o tráfego de VPN não está sujeito a outras regras de NAT. Esta é a regra de NAT usada:
nat (inside,outside) 1 source static 10.2.2.0_24 10.2.2.0_24 destination static 10.1.1.0_24 10.1.1.0_24 no-proxy-arp route-lookupObservação: quando várias sub-redes são usadas, você deve criar grupos de objetos com todas as sub-redes de origem e de destino e usá-las na regra NAT.
object-group network 10.x.x.x_SOURCE
network-object 10.4.4.0 255.255.255.0
network-object 10.2.2.0 255.255.255.0
object network 10.x.x.x_DESTINATION
network-object 10.3.3.0 255.255.255.0
network-object 10.1.1.0 255.255.255.0
nat (inside,outside) 1 source static 10.x.x.x_SOURCE 10.x.x.x_SOURCE destination static 10.x.x.x_DESTINATION 10.x.x.x_DESTINATION no-proxy-arp route-lookup
Exemplo de configuração completa
Esta é a configuração completa do site B:
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 14
lifetime 86400
tunnel-group 10.106.67.90 type ipsec-l2l
tunnel-group 10.106.67.90 ipsec-attributes
ikev1 pre-shared-key cisco
!Note the IKEv1 keyword at the beginning of the pre-shared-key command.
object network 10.2.2.0_24
subnet 10.2.2.0 255.255.255.0
object network 10.1.1.0_24
subnet 10.1.1.0 255.255.255.0
access-list 100 extended permit ip object 10.2.2.0_24 object 10.1.1.0_24
crypto ipsec ikev1 transform-set myset esp-aes esp-sha-hmac
crypto map outside_map 20 match address 100
crypto map outside_map 20 set peer 10.106.67.90
crypto map outside_map 20 set ikev1 transform-set myset
crypto map outside_map 20 set pfs
crypto map outside_map interface outside
nat (inside,outside) 1 source static 10.2.2.0_24 10.2.2.0_24 destination static 10.1.1.0_24 10.1.1.0_24 no-proxy-arp route-lookupPolítica de grupo
Política de grupoAs políticas de grupo são usadas para definir configurações específicas aplicáveis ao túnel. Essas políticas são usadas juntamente com o grupo de túneis.
A política de grupo pode ser definida como interna, o que significa que os atributos são extraídos do que é definido no ASA, ou pode ser definida como externa, na qual os atributos são consultados em um servidor externo. Este é o comando usado para definir a política de grupo:
group-policy SITE_A internalObservação: Você pode definir vários atributos na política de grupo. Para obter uma lista de todos os atributos possíveis, consulte a seção Configuração de Políticas de Grupo.
Atributos opcionais da política de grupo
O atributovpn-tunnel-protocol determina o tipo de túnel ao qual essas configurações devem ser aplicadas. Neste exemplo, o IPsec é usado:
vpn-tunnel-protocol ?
group-policy mode commands/options:
IPSec IP Security Protocol l2tp-ipsec L2TP using IPSec for security
svc SSL VPN Client
webvpn WebVPN
vpn-tunnel-protocol ikev1 - Version 8.4 and later
Você tem a opção de configurar o túnel para que ele permaneça ocioso (sem tráfego) e não seja desativado. Para configurar essa opção, o valor do atributovpn-idle-timeout deve usar minutos, ou você pode definir o valor como none, o que significa que o túnel nunca fica inativo.
Aqui está um exemplo:
group-policy SITE_A attributes
vpn-idle-timeout ?
group-policy mode commands/options:
<1-35791394> Number of minutes
alert-interval Specify timeout alert interval in minutes
none Site-to-Site (IKEv1, IKEv2) and IKEv1 remote-access: Disable
timeout and allow an unlimited idle period; AnyConnect (SSL,
IPSec/IKEv2): Use value of default-idle-timeout
O comandodefault-group-policy sob os atributos gerais do grupo de túneis define a política de grupo que é usada para enviar certas configurações de política para o túnel que é estabelecido. As configurações padrão das opções definidas na política de grupo são derivadas de uma política de grupo geral padrão:
tunnel-group 10.106.67.91 general-attributes
default-group-policy SITE_AVerificar
VerificarUse as informações fornecidas nesta seção para verificar se a configuração funciona corretamente.
ASDM
ASDMPara visualizar o status do túnel a partir do ASDM, navegue até Monitoring > VPN. Estas informações são fornecidas:
- O endereço IP do par
- O protocolo usado para criar o túnel
- O algoritmo de criptografia usado
- A hora em que o túnel foi criado e o tempo de atividade
- O número de pacotes recebidos e transferidos
Dica: clique em Refresh para exibir os valores mais recentes, pois os dados não são atualizados em tempo real.
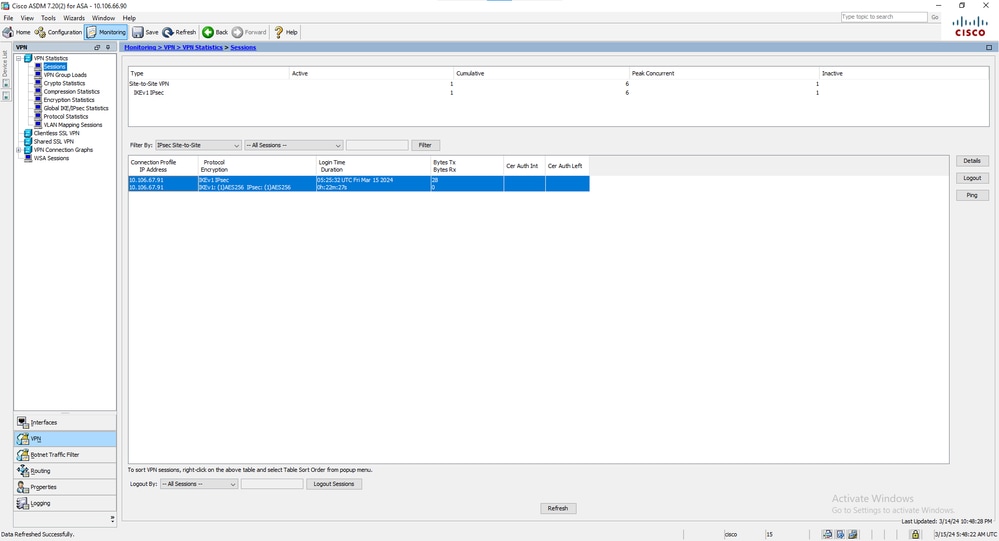 Janela de monitoramento de VPN
Janela de monitoramento de VPN
CLI
CLIEsta seção descreve como verificar a configuração por meio da CLI.
Fase 1
Fase 1Digite este comando no CLI para verificar a configuração da Fase 1 no lado B do Site:
show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 10.106.67.91
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVEFase 2
Fase 2O comandoshow crypto ipsec sa mostra as SAs de IPsec que são criadas entre os correspondentes. O túnel criptografado é criado entre os endereços IP 10.106.67.90 e 10.106.67.91 para o tráfego que flui entre as redes 10.1.1.0 e 10.2.2.0. Você pode ver as duas SAs de ESP criadas para o tráfego de entrada e de saída. O cabeçalho de autenticação (AH) não é usado porque não há SAs de AH.
Digite este comando no CLI para verificar a configuração da Fase 2 no lado do Site A:
interface: outside
Crypto map tag: outside_map, seq num: 20, local addr: 10.106.67.90
access-list 100 extended permit ip 10.1.1.0 255.255.255.0 10.2.2.0 255.255.255.0
local ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.2.2.0/255.255.255.0/0/0)
current_peer: 10.106.67.91
#pkts encaps: 20, #pkts encrypt: 20, #pkts digest: 20
#pkts decaps: 20, #pkts decrypt: 20, #pkts verify: 20
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 20, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.106.67.90/0, remote crypto endpt.: 10.106.67.91/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: F8951DA2
current inbound spi : 662C7ABE
inbound esp sas:
spi: 0x662C7ABE (1714191038)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (3914998/28074)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x001FFFFF
outbound esp sas:
spi: 0xF8951DA2 (4170522018)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (3914998/28073)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Digite este comando no CLI para verificar a configuração da Fase 2 no lado B do Site:
interface: outside
Crypto map tag: outside_map, seq num: 20, local addr: 10.106.67.91
access-list 100 extended permit ip 10.2.2.0 255.255.255.0 10.1.1.0 255.255.255.0
local ident (addr/mask/prot/port): (10.2.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0)
current_peer: 10.106.67.90
#pkts encaps: 20, #pkts encrypt: 20, #pkts digest: 20
#pkts decaps: 20, #pkts decrypt: 20, #pkts verify: 20
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 20, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.106.67.91/0, remote crypto endpt.: 10.106.67.90/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 662C7ABE
current inbound spi : F8951DA2
inbound esp sas:
spi: 0xF8951DA2 (4170522018)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (4373998/27737)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x001FFFFF
outbound esp sas:
spi: 0x662C7ABE (1714191038)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (4373998/27737)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001Troubleshooting
TroubleshootingUse as informações fornecidas nesta seção para solucionar problemas de configuração.
Digite estes comandos debug para determinar o local da falha de túnel:
debug crypto ikev1 127 (Fase 1)debug crypto ipsec 127 (Fase 2)
Aqui está um exemplo completo de saída de depuração:
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=10.1.1.10, sport=23043, daddr=10.2.2.10, dport=23043
IPSEC(crypto_map_check)-3: Checking crypto map outside_map 20: matched.
Mar 15 05:41:39 [IKEv1 DEBUG]Pitcher: received a key acquire message, spi 0x0
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=10.1.1.10, sport=23043, daddr=10.2.2.10, dport=23043
IPSEC(crypto_map_check)-3: Checking crypto map outside_map 20: matched.
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE Initiator: New Phase 1, Intf inside, IKE Peer 10.106.67.91 local Proxy Address 10.1.1.0, remote Proxy Address 10.2.2.0, Crypto map (outside_map)
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing ISAKMP SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Traversal VID ver 02 payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Traversal VID ver 03 payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Traversal VID ver RFC payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing Fragmentation VID + extended capabilities payload
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 172
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 132
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Oakley proposal is acceptable
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received NAT-Traversal RFC VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received Fragmentation VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, IKE Peer included IKE fragmentation capability flags: Main Mode: True Aggressive Mode: True
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing Cisco Unity VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing xauth V6 VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Send IOS VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Constructing ASA spoofing IOS Vendor ID payload (version: 1.0.0, capabilities: 20000001)
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Send Altiga/Cisco VPN3000/Cisco ASA GW VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NAT-D (20) + NAT-D (20) + NONE (0) total length : 432
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NAT-D (20) + NAT-D (20) + NONE (0) total length : 432
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing ISA_KE payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received Cisco Unity client VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received xauth V6 VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Processing VPN3000/ASA spoofing IOS Vendor ID payload (version: 1.0.0, capabilities: 20000001)
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received Altiga/Cisco VPN3000/Cisco ASA GW VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, Connection landed on tunnel_group 10.106.67.91
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Generating keys for Initiator...
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing ID payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Computing hash for ISAKMP
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Constructing IOS keep alive payload: proposal=32767/32767 sec.
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing dpd vid payload
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Automatic NAT Detection Status: Remote end is NOT behind a NAT device This end is NOT behind a NAT device
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ID payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, ID_IPV4_ADDR ID received 10.106.67.91
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Computing hash for ISAKMP
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Processing IOS keep alive payload: proposal=32767/32767 sec.
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Received DPD VID
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, Connection landed on tunnel_group 10.106.67.91
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Oakley begin quick mode
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator starting QM: msg id = ad712fa9
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, PHASE 1 COMPLETED
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, Keep-alive type for this connection: DPD
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Starting P1 rekey timer: 73440 seconds.
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Add to IKEv1 Tunnel Table succeeded for SA with logical ID 8192
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Add to IKEv1 MIB Table succeeded for SA with logical ID 8192
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0001B739
IPSEC: New embryonic SA created @ 0x00007f05294f4620,
SCB : 0x294CFE60,
Direction : inbound
SPI : 0x50EF49AD
Session ID : 0x00002000
VPIF num : 0x00000002
Tunnel type : l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0001B739
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, IKE got SPI from key engine: SPI = 0x50ef49ad
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, oakley constructing quick mode
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing blank hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing IPSec SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing IPSec nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing pfs ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing proxy ID
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Transmitting Proxy Id:
Local subnet: 10.1.1.0 mask 255.255.255.0 Protocol 0 Port 0
Remote subnet: 10.2.2.0 Mask 255.255.255.0 Protocol 0 Port 0
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator sending Initial Contact
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing qm hash payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator sending 1st QM pkt: msg id = ad712fa9
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=ad712fa9) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + KE (4) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 464
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=ad712fa9) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + KE (4) + ID (5) + ID (5) + NONE (0) total length : 436
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ISA_KE for PFS in phase 2
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ID payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, ID_IPV4_ADDR_SUBNET ID received--10.1.1.0--255.255.255.0
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ID payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, ID_IPV4_ADDR_SUBNET ID received--10.2.2.0--255.255.255.0
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, loading all IPSEC SAs
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Generating Quick Mode Key!
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Generating Quick Mode Key!
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Security negotiation complete for LAN-to-LAN Group (10.106.67.91) Initiator, Inbound SPI = 0x50ef49ad, Outbound SPI = 0xea689811
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, oakley constructing final quick mode
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator sending 3rd QM pkt: msg id = ad712fa9
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=ad712fa9) with payloads : HDR + HASH (8) + NONE (0) total length : 76
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x00024311
IPSEC: New embryonic SA created @ 0x00007f05294fd920,
SCB : 0x294CCDB0,
Direction : outbound
SPI : 0xEA689811
Session ID : 0x00002000
VPIF num : 0x00000002
Tunnel type : l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x00024311
Rule Lookup for local 10.1.1.0 to remote 10.2.2.0
Peer matched map outside_map sequence 20
PROXY MATCH on crypto map outside_map seq 20
IPSEC DEBUG: Using NP outbound permit rule for SPI 0xEA689811
IPSEC: Completed host OBSA update, SPI 0xEA689811
IPSEC: Creating outbound VPN context, SPI 0xEA689811
Flags : 0x00000005
SA : 0x00007f05294fd920
SPI : 0xEA689811
MTU : 1500 bytes
VCID : 0x00000000
Peer : 0x00000000
SCB : 0x02CEE703
Channel: 0x00007f0533c4f700
IPSEC: Completed outbound VPN context, SPI 0xEA689811
VPN handle: 0x000000000000763c
IPSEC: New outbound encrypt rule, SPI 0xEA689811
Src addr: 10.1.1.0
Src mask: 255.255.255.0
Dst addr: 10.2.2.0
Dst mask: 255.255.255.0
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 0
Use protocol: false
SPI: 0x00000000
Use SPI: false
IPSEC: Completed outbound encrypt rule, SPI 0xEA689811
Rule ID: 0x00007f05294f8a60
IPSEC: New outbound permit rule, SPI 0xEA689811
Src addr: 10.106.67.90
Src mask: 255.255.255.255
Dst addr: 10.106.67.91
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0xEA689811
Use SPI: true
IPSEC: Completed outbound permit rule, SPI 0xEA689811
Rule ID: 0x00007f05294f9110
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, IKE got a KEY_ADD msg for SA: SPI = 0xea689811
IPSEC: New embryonic SA created @ 0x00007f05294f4620,
SCB : 0x294CFE60,
Direction : inbound
SPI : 0x50EF49AD
Session ID : 0x00002000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0001B739
Rule Lookup for local 10.1.1.0 to remote 10.2.2.0
Peer matched map outside_map sequence 20
PROXY MATCH on crypto map outside_map seq 20
IPSEC DEBUG: Using NP inbound permit rule for SPI 0x50EF49AD
IPSEC: Completed host IBSA update, SPI 0x50EF49AD
IPSEC: Creating inbound VPN context, SPI 0x50EF49AD
Flags: 0x00000006
SA : 0x00007f05294f4620
SPI : 0x50EF49AD
MTU : 0 bytes
VCID : 0x00000000
Peer : 0x0000763C
SCB : 0x02CE8BB3
Channel: 0x00007f0533c4f700
IPSEC: Completed inbound VPN context, SPI 0x50EF49AD
VPN handle: 0x00000000000086bc
IPSEC: Updating outbound VPN context 0x0000763C, SPI 0xEA689811
Flags: 0x00000005
SA : 0x00007f05294fd920
SPI : 0xEA689811
MTU : 1500 bytes
VCID : 0x00000000
Peer : 0x000086BC
SCB : 0x02CEE703
Channel: 0x00007f0533c4f700
IPSEC: Completed outbound VPN context, SPI 0xEA689811
VPN handle: 0x000000000000763c
IPSEC: Completed outbound inner rule, SPI 0xEA689811
Rule ID: 0x00007f05294f8a60
IPSEC: Completed outbound outer SPD rule, SPI 0xEA689811
Rule ID: 0x00007f05294f9110
IPSEC: New inbound tunnel flow rule, SPI 0x50EF49AD
Src addr: 10.2.2.0
Src mask: 255.255.255.0
Dst addr: 10.1.1.0
Dst mask: 255.255.255.0
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 0
Use protocol: false
SPI: 0x00000000
Use SPI: false
IPSEC: Completed inbound tunnel flow rule, SPI 0x50EF49AD
Rule ID: 0x00007f05294f8180
IPSEC: New inbound decrypt rule, SPI 0x50EF49AD
Src addr: 10.106.67.91
Src mask: 255.255.255.255
Dst addr: 10.106.67.90
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0x50EF49AD
Use SPI: true
IPSEC: Completed inbound decrypt rule, SPI 0x50EF49AD
Rule ID: 0x00007f05294f7ad0
IPSEC: New inbound permit rule, SPI 0x50EF49AD
Src addr: 10.106.67.91
Src mask: 255.255.255.255
Dst addr: 10.106.67.90
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0x50EF49AD
Use SPI: true
IPSEC: Completed inbound permit rule, SPI 0x50EF49AD
Rule ID: 0x00007f05294f4510
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Pitcher: received KEY_UPDATE, spi 0x50ef49ad
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Starting P2 rekey timer: 24480 seconds.
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, PHASE 2 COMPLETED (msgid=ad712fa9) Histórico de revisões
| Revisão | Data de publicação | Comentários |
|---|---|---|
1.0 |
10-Jul-2015
|
Versão inicial |
Colaborado por engenheiros da Cisco
- Venkata Aditya BEngenheiro do Cisco TAC
- Rahul GovindanEngenheiro do Cisco TAC
- Pavan GunduEngenheiro de consultoria técnica
Contate a Cisco
- Abrir um caso de suporte

- (É necessário um Contrato de Serviço da Cisco)
 Feedback
Feedback