IOS XE에서 VRF 누수 구성
다운로드 옵션
편견 없는 언어
본 제품에 대한 문서 세트는 편견 없는 언어를 사용하기 위해 노력합니다. 본 설명서 세트의 목적상, 편견 없는 언어는 나이, 장애, 성별, 인종 정체성, 민족 정체성, 성적 지향성, 사회 경제적 지위 및 교차성에 기초한 차별을 의미하지 않는 언어로 정의됩니다. 제품 소프트웨어의 사용자 인터페이스에서 하드코딩된 언어, RFP 설명서에 기초한 언어 또는 참조된 서드파티 제품에서 사용하는 언어로 인해 설명서에 예외가 있을 수 있습니다. 시스코에서 어떤 방식으로 포용적인 언어를 사용하고 있는지 자세히 알아보세요.
이 번역에 관하여
Cisco는 전 세계 사용자에게 다양한 언어로 지원 콘텐츠를 제공하기 위해 기계 번역 기술과 수작업 번역을 병행하여 이 문서를 번역했습니다. 아무리 품질이 높은 기계 번역이라도 전문 번역가의 번역 결과물만큼 정확하지는 않습니다. Cisco Systems, Inc.는 이 같은 번역에 대해 어떠한 책임도 지지 않으며 항상 원본 영문 문서(링크 제공됨)를 참조할 것을 권장합니다.
소개
이 문서에서는 VRF(Virtual Routing and Forwarding) 경로 유출의 일반적인 방법에 대한 컨피그레이션의 예를 설명하고 제공합니다.
사전 요구 사항
요구 사항
다음 주제에 대한 지식을 보유하고 있으면 유용합니다.
- BGP(Border Gateway Protocol)
- 라우팅 프로토콜 재배포
- VRF
- Cisco IOS® XE 소프트웨어
이러한 항목에 대한 자세한 내용은 다음을 참조하십시오.
사용되는 구성 요소
이 문서의 정보는 Cisco IOS® XE 버전 16.12.X 및 17.X의 라우터를 기반으로 합니다
이 문서의 정보는 특정 랩 환경의 디바이스를 토대로 작성되었습니다. 이 문서에 사용된 모든 디바이스는 초기화된(기본) 컨피그레이션으로 시작되었습니다. 현재 네트워크가 작동 중인 경우 모든 명령의 잠재적인 영향을 미리 숙지하시기 바랍니다.
배경 정보
VRF를 사용하면 라우터가 서로 다른 가상 네트워크에 대해 별도의 라우팅 테이블을 유지할 수 있습니다. 예외가 필요한 경우 VRF 경로 유출을 통해 고정 경로를 사용하지 않고 일부 트래픽을 VRF 간에 라우팅할 수 있습니다.
시나리오 1 - BGP와 IGP 간의 VRF 경로 유출( EIGRP )
시나리오 1은 BGP와 EIGRP 간의 VRF 경로 유출의 예를 제공합니다. 이 방법은 다른 IGP에 사용할 수 있습니다.
네트워크 다이어그램
이미지 1의 네트워크 다이어그램은 경로 유출이 필요한 레이어 3 토폴로지를 보여줍니다.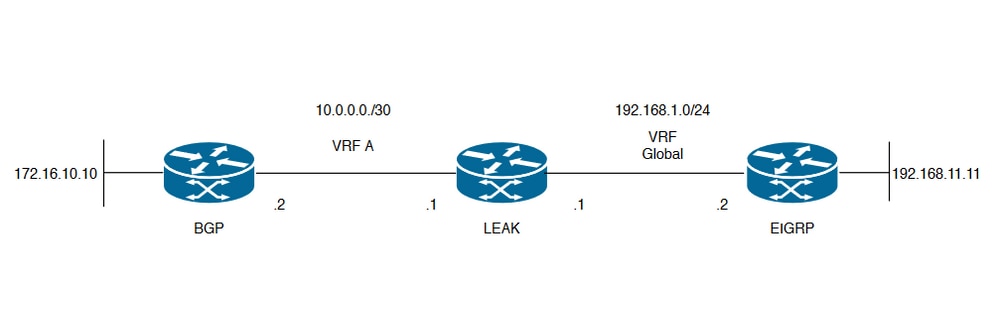
이미지 1. 시나리오 1의 경로 유출 토폴로지
라우터 LEAK는 VRF A의 인접 디바이스에 대한 BGP 인접 디바이스, 전역 VRF의 EIGRP 인접 디바이스에 대한 BGP 인접 디바이스를 갖습니다. 장치 192.168.11.11은 네트워크를 통해 장치 172.16.10.10에 연결할 수 있어야 합니다.
경로가 서로 다른 VRF에 있으므로 라우터 LEAK에서 둘 사이를 라우팅할 수 없습니다. 이러한 라우팅 테이블은 VRF별 현재 경로를 보여주며, 글로벌 VRF와 VRF A 간에 어떤 경로를 유출해야 하는지를 나타냅니다.
누수 라우팅 테이블:
| EIGRP 라우팅 테이블(전역 라우팅) |
LEAK#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet2
L 192.168.1.1/32 is directly connected, GigabitEthernet2
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/130816] via 192.168.1.2, 02:30:29, GigabitEthernet2 >> Route to be exchange to the VRF A routing table.
| VRF A 라우팅 테이블 |
LEAK#show ip route vrf A
Routing Table: A
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, GigabitEthernet1
L 10.0.0.1/32 is directly connected, GigabitEthernet1
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.2, 01:47:58 >> Route to be exchange to the global routing table.
구성
두 라우팅 테이블 간에 누수를 생성하는 절차를 완료합니다.
Step 1.
Create route-maps to filter the routes to be injected in both routing tables.
LEAK(config)#Route-map VRF_TO_EIGRP
LEAK(config-route-map)#match ip address prefix-list VRF_TO_EIGRP
LEAK(config-route-map)#exit
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list VRF_TO_EIGRP permit 172.16.10.10/32
or
LEAK(config)#Route-map VRF_TO_EIGRP
LEAK(config-route-map)# match ip address 10
LEAK(config-route-map)#exit
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-lists 10
10 permit 172.16.10.10
LEAK(config)#Route-map EIGRP_TO_VRF
LEAK(config-route-map)#match ip address prefix-list EIGRP_TO_VRF
LEAK(config-route-map)#exit
LEAK(config)#
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list EIGRP_TO_VRF permit 192.168.11.11/32
or
LEAK(config)#Route-map EIGRP_TO_VRF
LEAK(config-route-map)#match ip address 20
LEAK(config-route-map)#exit
LEAK(config)#
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-list 20
10 permit 192.168.11.11
Step 2.
Define the import/export maps and add the route-map names.
LEAK(config)#vrf definition A
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#import ipv4 unicast map EIGRP_TO_VRF >> Import the global routing table routes at the VRF routing table.
LEAK(config-vrf-af)#export ipv4 unicast map VRF_TO_EIGRP >> Export the VRF routes to the Global Routing Table.
LEAK(config-vrf-af)#end
Step 3.
Proceed with the dual redistribution.
Redistribute EIGRP
LEAK(config)#router bgp 1
LEAK(config-router)#redistribute eigrp 1
LEAK(config-router)#end
Redistribution BGP
LEAK(config)#router eigrp 1
LEAK(config-router)#redistribute bgp 1 metric 100 1 255 1 1500
LEAK(config-router)#end
다음을 확인합니다.
Routing table from VRF A
LEAK#show ip route vrf A
Routing Table: A
< Snip for resume >
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, GigabitEthernet1
L 10.0.0.1/32 is directly connected, GigabitEthernet1
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.2, 00:58:53
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
B 192.168.1.0/24 is directly connected, 00:01:00, GigabitEthernet2
L 192.168.1.1/32 is directly connected, GigabitEthernet2
192.168.11.0/32 is subnetted, 1 subnets
B 192.168.11.11 [20/130816] via 192.168.1.2, 00:01:00, GigabitEthernet2 >> Route from global routing table at VRF A routing table.
Global Routing Table (EIGRP)
LEAK#show ip route
< snip for resume >
Gateway of last resort is not set
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.2 (A), 00:04:47 >> Route from VRF A at global routing table.
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet2
L 192.168.1.1/32 is directly connected, GigabitEthernet2
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/130816] via 192.168.1.2, 01:03:35, GigabitEthernet2
LEAK#
시나리오 2 - VRF A와 VRF B 간의 VRF 유출
시나리오 2는 서로 다른 두 VRF 간의 누수를 설명합니다.
네트워크 다이어그램
이 문서에서는 다음 네트워크 설정을 사용합니다.
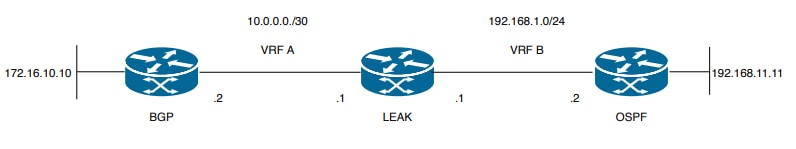
이미지 2. 시나리오 2의 경로 유출 토폴로지
라우터 LEAK에는 VRF A의 인접 디바이스에 대한 BGP 인접 디바이스, VRF B의 OSPF 인접 디바이스가 있습니다. 디바이스 192.168.11.11은 네트워크를 통해 디바이스 172.16.10.10에 연결해야 합니다.
경로가 서로 다른 VRF에 있으므로 라우터 LEAK에서 둘 사이를 라우팅할 수 없습니다. 이러한 라우팅 테이블은 VRF별 현재 경로를 보여주며, VRF A와 VRF B 간에 어떤 경로를 유출해야 하는지를 나타냅니다.
누수 라우팅 테이블:
| VRF A 라우팅 테이블 |
LEAK#show ip route vrf A
Routing Table: A
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.1, 00:03:08 >> Route to be exchange to routing table VRF B.
| VRF B 라우팅 테이블 |
LEAK#show ip route vrf B
Routing Table: B
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.2/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
O 192.168.11.11 [110/11] via 192.168.1.1, 00:58:45, Ethernet0/1 >> Route to be exchange to routing table VRF A.
구성
두 라우팅 테이블 간에 누수를 생성하려면 다음 절차를 완료합니다.
Step 1.
Create route-maps to filter the routes to be injected in both routing tables.
LEAK(config)#Route-map VRFA_TO_VRFB
LEAK(config-route-map)#match ip address prefix-list VRFA_TO_VRFB
LEAK(config-route-map)#exit
!
Prefix-list created to match the host and IP segment that is attached to the previous route-map configured.
!
ip prefix-list VRFA_TO_VRFB permit 172.16.10.10/32
ip prefix-list VRFA_TO_VRFB permit 10.0.0.0/30
or
LEAK(config)#Route-map VRFA_TO_VRFB
LEAK(config-route-map)#match ip address 10
LEAK(config-route-map)#exit
!
ACL created to match the host and IP segment that is attached to the previous route-map.
!
LEAK#show ip access-lists 10
10 permit 172.16.10.10
20 permit 10.0.0.0
LEAK(config)#Route-map VRFB_TO_VRFA
LEAK(config-route-map)#match ip address prefix-list VRFB_TO_VRFA
LEAK(config-route-map)#exit
!
Prefix-list created to match the host and IP segment that is attached to the previous route-map configured.
!
ip prefix-list VRFB_TO_VRFA permit 192.168.11.11/32
ip prefix-list VRFB_TO_VRFA permit 192.168.1.0/24
or
LEAK(config)#Route-map VRFB_TO_VRFA
LEAK(config-route-map)#match ip address 20
LEAK(config-route-map)#exit
!
ACL created to match the host and IP segment that is attached to the previous route-map configured.
!
LEAK#show ip access-lists 20
10 permit 192.168.11.11
20 permit 192.168.1.0
Step 2.
At the VRFs configure the import/export map, use the route-map names to leak the routes.
LEAK(config)#vrf definition A
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#export map VRFA_TO_VRFB
LEAK(config-vrf-af)#import map VRFB_TO_VRFA
LEAK(config)#vrf definition B
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#export map VRFB_TO_VRFA
LEAK(config-vrf-af)#import map VRFA_TO_VRFB
Step 3.
Add the route-target to import and export the route distinguisher from both VRFs.
! --- Current configuration for VRF A
vrf definition A
rd 1:2
!
address-family ipv4
route-target export 1:2
route-target import 1:1
exit-address-family
! --- Current configuration from VRF B
vrf definition B
rd 2:2
!
address-family ipv4
exit-address-family
! --- Import the routes from VRF B into VRF A
LEAK(config)#vrf definition A
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#route-target import 2:2
! --- Import routes from VRF A to VRF B and export routes from VRF B
LEAK(config-vrf-af)#vrf definition B
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#route-target import 1:2
LEAK(config-vrf-af)#route-target export 2:2
다음을 확인합니다.
Check the Routing Tables
VRF A Routing Table
LEAK#show ip route vrf A
Routing Table: A
< Snip for resume >
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.1, 00:07:20
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
B 192.168.1.0/24 is directly connected, 00:00:10, Ethernet0/1
L 192.168.1.2/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
B 192.168.11.11 [20/11] via 192.168.1.1 (B), 00:00:10, Ethernet0/1 >> Route from VRF B routing table at VRF A.
VRF B Routing Table
LEAK#show ip route vrf B
Routing Table: B
< Snip for resume >
10.0.0.0/30 is subnetted, 1 subnets
B 10.0.0.0 [200/0] via 10.0.0.1 (A), 00:00:15
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [200/0] via 10.0.0.1 (A), 00:00:15 >> Route from VRF A routing table at VRF B.
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.2/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
O 192.168.11.11 [110/11] via 192.168.1.1, 01:05:12, Ethernet0/1
시나리오 3 - BGP를 사용하는 OSPF(VRF)와 EIGRP(글로벌) 간의 VRF 유출(선택 사항)
시나리오 3은 두 IGP(VRF B 및 Global VRF) 간의 경로 누수에 대해 설명합니다.
네트워크 다이어그램
이 문서에서는 이 네트워크 설정을 사용합니다.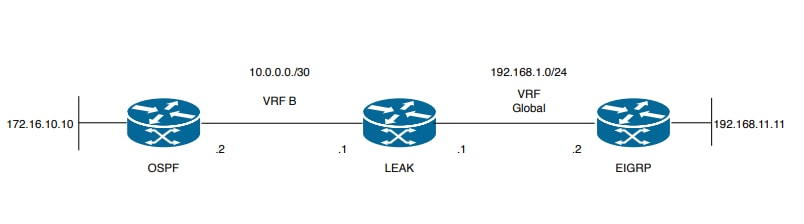
이미지 3. 시나리오 3의 경로 유출 토폴로지
라우터 LEAK에는 VRF B의 인접 디바이스와 OSPF 인접 디바이스, 전역 VRF의 EIGRP 인접 디바이스가 있습니다. 장치 172.16.10.10은 네트워크를 통해 장치 192.168.11.11에 연결할 수 있어야 합니다.
라우터 LEAK에서 이 두 호스트를 연결할 수 없습니다. 이러한 라우팅 테이블은 VRF별 현재 경로를 보여주며, VRF B와 글로벌 VRF 간에 어떤 경로를 유출해야 하는지를 나타냅니다.
누수 라우팅 테이블:
| EIGRP 라우팅 테이블(EIGRP) |
LEAK#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.1/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/1024640] via 192.168.1.2, 01:08:38, Ethernet0/1 >> Route to be exchange from global routing table at VRF B routing table.
| VRF B 라우팅 테이블(OSPF) |
LEAK#show ip route vrf B
Routing Table: B
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
O 172.16.10.10 [110/11] via 10.0.0.1, 01:43:45, Ethernet0/0 >> Route to be exchange from routing table VRF B at global routing table.
구성
두 라우팅 테이블 간에 누수를 생성하려면 다음 절차를 완료합니다.
Step 1.
Create route-maps for import and export to be injected in both routing tables.
LEAK(config)#Route-map OSPF_TO_EIGRP
LEAK(config-route-map)#match ip address prefix-list OSPF_TO_EIGRP
LEAK(config-route-map)#exit
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list OSPF_TO_EIGRP permit 172.16.10.10/32
ip prefix-list OSPF_TO_EIGRP permit 10.0.0.0/30
or
LEAK(config)#Route-map OSPF_TO_EIGRP
LEAK(config-route-map)#match ip address 10
LEAK(config-route-map)#exit
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-lists 10
10 permit 172.16.10.10
20 permit 10.0.0.0
LEAK(config)#Route-map EIGRP_TO_OSPF
LEAK(config-route-map)#match ip address prefix-list EIGRP_TO_OSPF
LEAK(config-route-map)#exit
!
Prefix-list created to match the host that is attached to the previous route-map configured.
!
ip prefix-list EIGRP_TO_OSPF permit 192.168.11.11/32
ip prefix-list EIGRP_TO_OSPF permit 192.168.1.0/24
or
LEAK(config)#Route-map EIGRP_TO_OSPF
LEAK(config-route-map)#match ip address 20
LEAK(config-route-map)#exit
!
ACL created to match the host that is attached to the previous route-map.
!
LEAK#show ip access-lists 20
10 permit 192.168.11.11
20 permit 192.168.1.0/24
Step 2.
Add the import/export maps in order to match the route-map names.
Current configuration
!
vrf definition B
rd 1:2
!
address-family ipv4
exit-address-family
!
!
LEAK(config-vrf)#vrf definition B
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#import ipv4 unicast map EIGRP_TO_OSPF
LEAK(config-vrf-af)#export ipv4 unicast map OSPF_TO_EIGRP
Step 3.
To perform the leak is necessary to create a BGP process, in order to redistribute
the IGPs protocols.
router bgp 1
bgp log-neighbor-changes
!
address-family ipv4 vrf B >> Include the address-family to inject VRF B routing table (OSPF)
!
exit-address-family
참고: 오류를 방지하기 위해 VRF에 Route Distinguisher가 구성되어 있는지 확인합니다."%vrf B does not have rd configured, configure "rd" before configuring import route-map"
Step 4.
Create a Dual Redistribution.
IGPs redistribution.
LEAK(config-router)#router bgp 1
LEAK(config-router)#redistribute eigrp 1
!
LEAK(config-router)#address-family ipv4 vrf B
LEAK(config-router-af)#redistribute ospf 1 match internal external 1 external 2
LEAK(config-router-af)#end
BGP Redistribution
LEAK(config)#router ospf 1 vrf B
LEAK(config-router)#redistribute bgp 1
!
LEAK(config-router)#router eigrp TAC
LEAK(config-router)#
LEAK(config-router)# address-family ipv4 unicast autonomous-system 1
LEAK(config-router-af)#
LEAK(config-router-af)# topology base
LEAK(config-router-af-topology)#redistribute bgp 1 metric 100 1 255 1 1500
다음을 확인합니다.
라우팅 테이블 확인
| 전역 라우팅 테이블 |
LEAK#show ip route
< Snip for resume >
172.16.0.0/32 is subnetted, 1 subnets
B 172.16.10.10 [20/11] via 10.0.0.1, 00:14:48, Ethernet0/0 >> Route from VRF B routing table at global routing table ( EIGRP ).
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Ethernet0/1
L 192.168.1.1/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
D 192.168.11.11 [90/1024640] via 192.168.1.2, 02:16:51, Ethernet0/1
| VRF B 라우팅 테이블 |
LEAK#show ip route vrf B
Routing Table: B
< Snip for resume >
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/30 is directly connected, Ethernet0/0
L 10.0.0.2/32 is directly connected, Ethernet0/0
172.16.0.0/32 is subnetted, 1 subnets
O 172.16.10.10 [110/11] via 10.0.0.1, 00:34:25, Ethernet0/0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
B 192.168.1.0/24 is directly connected, 00:08:51, Ethernet0/1
L 192.168.1.1/32 is directly connected, Ethernet0/1
192.168.11.0/32 is subnetted, 1 subnets
B 192.168.11.11 [20/1024640] via 192.168.1.2, 00:08:51, Ethernet0/1 >> Route from global routing table ( EIGRP ) at VRF B routing table.
시나리오 4 - OSPF에서 BGP로의 VRF 기본 경로 유출
시나리오 4는 OSPF에서 BGP로 유출되는 VRF 기본 경로의 예를 제공합니다.
네트워크 다이어그램
이미지 4의 네트워크 다이어그램은 기본 경로 유출이 필요한 레이어 3 토폴로지를 보여줍니다.

이미지 4. 시나리오 4의 경로 유출 토폴로지
OSPF 및 BGP 프로세스가 라우터 누수의 서로 다른 VRF에서 실행되고 있습니다. 기본 경로는 Router OSPF에 있습니다. Router LEAK는 VRF A에서 라우터 BGP와 BGP 네이버십을, VRF B에서 라우터 OSPF와 OSPF 네이버십을 가집니다.
다음은 OSPF에서 라우터 LEAK의 BGP로의 기본 경로 유출에 대한 설명입니다.
구성
Step 1
Check if a static default route is present in Router OSPF.
OSPF#sh ip route
<output snipped>
Gateway of last resort is 192.168.10.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.10.2 >>> default route is present in the routing table.
C 192.168.0.0/24 is directly connected, GigabitEthernet2
L 192.168.0.2/32 is directly connected, GigabitEthernet2
192.168.10.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.10.0/24 is directly connected, GigabitEthernet1
L 192.168.10.1/32 is directly connected, GigabitEthernet1
Step 2
From the OSPF router, the default route needs to be advertised in OSPF to Router LEAK.
Use the command "default-information originate" on Router OSPF under OSPF process:( if there is static route in the OSPF router, routing table as verified in Step 1)
OSPF(config)#router ospf 1
OSPF(config-router)#default-information originate
If there is no static route in the Router OSPF routing table then we can generate and advertise a default route to the OSPF neighbour.
OSPF(config)#router ospf 1
OSPF(config-router)#default-information originate always
This forces the router to advertise a default route even if it doesn't have one in its routing table.
Step 3.1
Verify on Router LEAK, if an external OE2 route is installed in the VRF B routing table:
LEAK#sh ip route VRF B
Routing Table: B
<output snipped>
Gateway of last resort is 192.168.0.2 to network 0.0.0.0
O*E2 0.0.0.0/0 [110/1] via 192.168.0.2, 00:05:51, GigabitEthernet2 >>> OE2 route is installed in the VRF B routing table (This needs to be leaked in BGP)
192.168.0.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.0.0/24 is directly connected, GigabitEthernet2
L 192.168.0.1/32 is directly connected, GigabitEthernet2
Step 3.2
Configure a prefix-list on Router LEAK
LEAK# conf t
LEAK(config)# ip prefix-list OSPF_TO_BGP seq 5 permit 0.0.0.0/0
Configure a route-map to match the prefix-list.
LEAK(config-route-map)#route-map OSPF_TO_BGP permit 10
LEAK(config-route-map)# match ip address prefix-list OSPF_TO_BGP
LEAK(config-route-map)#exit
Step 3.3
Verify on Router LEAK, that required VRFs , Route Distinguishers (RD) an Route Targets (RT) are configured.
LEAK(config)#vrf definition A
LEAK(config-vrf)#rd 1:1
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#route-target import 6500:1
LEAK(config-vrf-af)#exit-address-family
LEAK(config-vrf-af)#end
LEAK#
LEAK(config)#vrf definition B
LEAK(config-vrf)#rd 2:2
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#route-target export 6500:1
LEAK(config-vrf-af)#exit-address-family
LEAK(config-vrf-af)#end
LEAK#
Step 3.4
Configure import map in VRF A.
LEAK#conf t
LEAK(config)#vrf definition A
LEAK(config-vrf)#address-family ipv4
LEAK(config-vrf-af)#import map OSPF_TO_BGP
LEAK(config-vrf-af)#end
LEAK#
Step 3.5
Create an address family VRF B in the BGP configuration and advertise “0.0.0.0”
LEAK#sh run | sec bgp
redistribute bgp 6501
router bgp 6501
bgp router-id 10.0.0.1
bgp log-neighbor-changes
!
address-family ipv4 vrf A
neighbor 10.0.0.2 remote-as 6500
neighbor 10.0.0.2 activate
exit-address-family
!
address-family ipv4 vrf B
network 0.0.0.0
exit-address-family
참고: BGP에서 주소군 VRF를 생성하는 것은 인접 디바이스를 활성화하지 않아도 작동합니다. VRF 간 경로를 유출하려면 BGP 프로세스를 스내핑하기만 하면 됩니다.
다음을 확인합니다.
Verify the default route available in BGP.
LEAK#sh ip route vrf A
Routing Table: A
<output snipped>
Gateway of last resort is 192.168.0.2 to network 0.0.0.0
B* 0.0.0.0/0 [20/1] via 192.168.0.2 (B), 00:15:36, GigabitEthernet2 >>> Default route of VRF B routing table in VRF A routing table.
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.0/24 is directly connected, GigabitEthernet1
L 10.0.0.1/32 is directly connected, GigabitEthernet1
추가 리소스
개정 이력
| 개정 | 게시 날짜 | 의견 |
|---|---|---|
4.0 |
16-Oct-2024
|
서식이 업데이트되었습니다. |
3.0 |
12-Jan-2023
|
제목 조정 및 작성자 이름 수정 다시 인증되었습니다. |
2.0 |
26-Oct-2021
|
제목 조정 및 작성자 이름 수정 |
1.0 |
16-Dec-2020
|
최초 릴리스 |
Cisco 엔지니어가 작성
- 아드리아나 파체코기술 컨설팅 엔지니어
- 호세 폰세카기술 컨설팅 엔지니어
- 모하메드 스한 A기술 컨설팅 엔지니어
지원 문의
- 지원 케이스 접수

- (시스코 서비스 계약 필요)
 피드백
피드백