Walkthroughs Supported in Secure Firewall Management Center
Walkthroughs in Firewall Management Center guide you to perform the steps required to achieve a task by taking you through each step, one after the other, until you complete the task. To access walkthroughs in Firewall Management
Center, choose Help ( ).
).
You can also use the global search feature of the Firewall Management Center to quickly find walkthroughs of your interest. Search for the walkthrough title or terms in the walkthrough title for better search results.
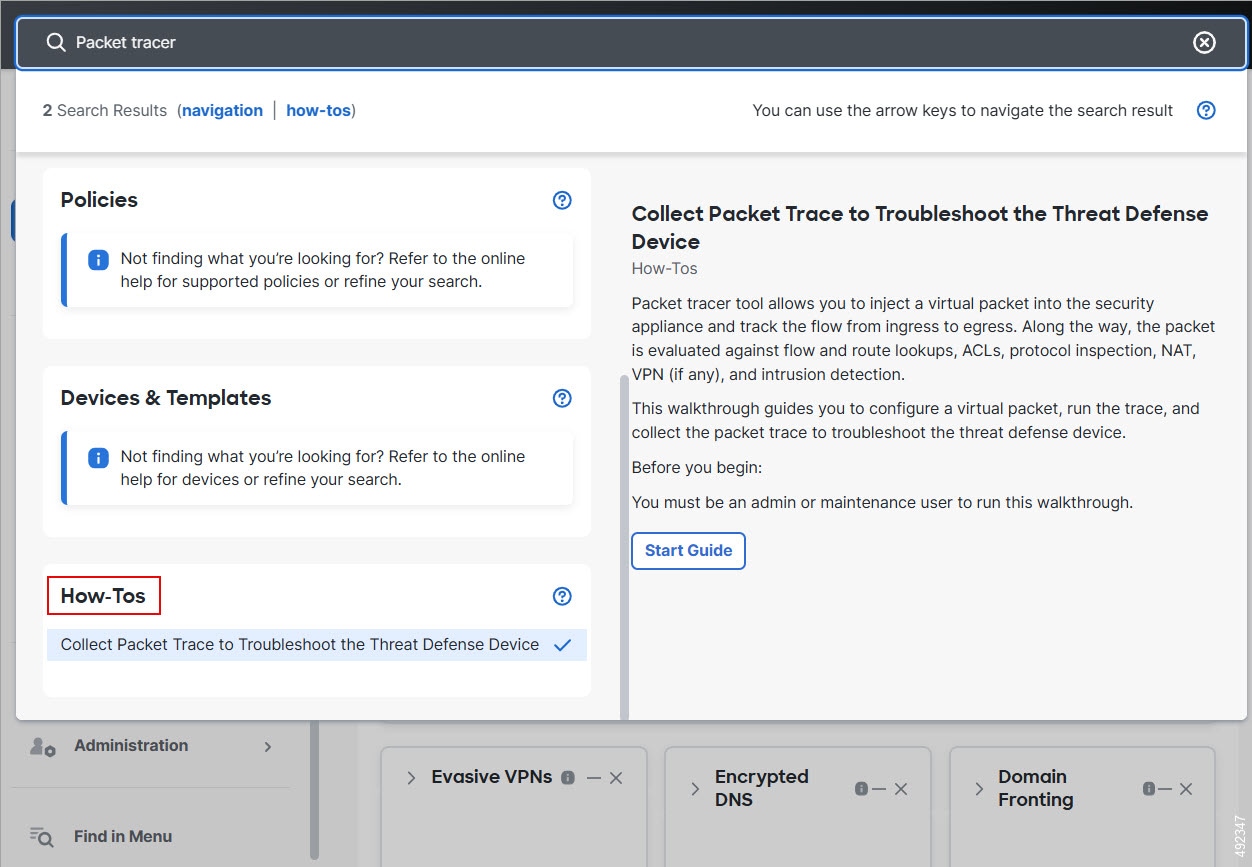
For more information about searching and finding walkthroughs of your interest in Firewall Management Center, see Search for How To Walkthroughs in Cisco Secure Firewall Management Center Administration Guide.
 Note | In Firewall Management Center, Version 10.0, the availability of Walkthroughs is limited. Also, some of the previously available Walkthroughs may no longer be accessible in Version 10.0. |
The following is the list of feature walkthroughs supported in the Firewall Management Center:
|
Use case |
Walkthrough Title |
Firewall Management Center Version |
|---|---|---|
|
Register and Preprovision SD-WAN Branch Office Devices Using Device Template |
|
7.6.0 through 7.7.x |
|
Set Up Your Device |
|
7.6.0 and later |
|
Configure Identity Policies |
|
7.6.0 and later |
|
Configure SD-WAN Capabilities |
|
7.4.1 through 7.7.x |
| Manage Your Chassis |
|
7.4.1 and later |
|
Set Up Your Device |
Configure External Authentication |
7.4.1 through 7.7.x |
|
Configure a Site-to-Site VPN Topology with Dynamic VTI |
|
7.4.0 through 7.7.x |
|
Loopback Support for BGP Routing |
|
7.4.0 and later |
|
Snort 3 IPS – A Feature Walkthrough |
View the Summary Layer |
7.4.0 and later |
|
Working with Snort 3 |
Convert all Snort 2 Custom Rules to Snort 3 |
7.4.0 and later |
|
Configure Decryption Policies |
|
7.3.0 through 7.7.x |
|
Snort 3 IPS – A Feature Walkthrough |
|
|
|
Configuring VPN |
|
7.2.6 and later |
|
Configure Dynamic Access Policy for Remote Access VPN |
|
7.2.6 and later |
|
Troubleshoot Your Device |
|
7.2.6 and later |
|
The New Access Control Policy UI–A Feature Walkthrough |
|
7.2.0 through 7.7.x |
|
Working with Snort 3 |
|
7.2.0 and later |
|
Configure User Identity–Dynamic Objects |
|
7.2.0 through 7.7.x |
|
Create and Install an Identity Certificate on Device for Remote Access VPN Configuration |
|
7.2.0 and later |
|
Working with Snort 3 |
|
7.1.0 and later |
|
Create and Manage a Cluster |
|
7.1.0 through 7.7.x |
|
Change the Firewall Management Center Access Interface from Management to Data |
|
7.1.0 through 7.7.x |
|
Change the Firewall Management Center Access Interface from Data to Management |
|
7.1.0 through 7.7.x |
|
Upgrade |
Upgrade Secure Firewall Threat Defense |
7.1.0 through 7.7.x |
|
Working with Snort 3 |
|
7.1.0 through 7.7.x |
| Getting Started |
Enabling the SecureX Ribbon (Deprecated) |
|
|
Add a Device to Firewall Management Center Using Remote Branch Deployment |
|
7.0.0 through 7.7.x |
|
Configuring Identity Policies |
|
6.7.0 through 7.4.1 |
|
Set Up Your Device. |
|
6.7.0 and later |
|
Configure Network Discovery Policies |
|
6.7.0 and later |
|
Create a Decryption Policy With One or More Do Not Decrypt Rules (formerly known as Create an SSL Do Not Decrypt Policy) |
|
6.7.0 through 7.7.x |
|
Create a Decryption Policy With One or More Decrypt–Resign Rules (formerly known as Create an SSL Decrypt–Resign Policy) |
|
6.7.0 through 7.7.x |
|
Create a Decryption Policy With One or More Decrypt–Known Key Rules (formerly known as Create an SSL Decrypt–Known Key Policy) |
|
6.7.0 through 7.7.x |
|
Create a Decryption Policy With One or More Block Rules (formerly known as Create an SSL Decrypt–Known Key Policy) |
|
6.7.0 through 7.7.x |
|
Create Intrusion Policies |
|
6.7.0 and later |
|
Create File (Malware) Policies |
|
6.7.0 and later |
|
Configure Identity Policies |
|
6.7.0 and later |
|
Configure and Customize Site-to-Site VPN |
|
6.7.0 and later |
|
Certificate Authentication for Remote Access (RA) VPN |
|
6.7.0 and later |
|
Configuring Traffic Filtering for Remote Access (RA) VPN Connections |
|
6.7.0 and later |
|
Configure a VTI tunnel. |
|
6.7.0 and later |
|
Configure Virtual Routing for Secure Firewall Threat Defense |
|
6.7.0 and later |
| Configure Routing |
Configure SSL Cipher Suites |
6.7.0 and later |
|
Getting Started |
Change the Theme of the Web Interface (formerly known as Switch to Classic or Dusk Theme) |
6.7.0 and later |
|
Set Up Your Device |
Set up a Device and add it to Management Center |
6.7.0 through 7.7.x |
 Feedback
Feedback