Configuring IPsec Profile Manual Keying Mode on RV160 and RV260
Available Languages
Objective
The objective of this document is to show you how to configure IPsec Profile for Manual Keying mode on RV160 and RV260 series routers.
Introduction
IPsec ensures that you have secure private communication over the Internet. It gives two or more hosts privacy, integrity, and authenticity for transmitting sensitive information over the Internet. IPsec is commonly used in a Virtual Private Network (VPN), implemented at the IP layer, and can assist many applications that lack security. A VPN is used to provide a secure communication mechanism for sensitive data and IP information that is transmitted through an unsecure network such as the Internet. It provides a flexible solution for remote users and the organization to protect any sensitive information from other parties on the same network.
Manual keying mode reduces the flexibility and options of IPsec. It requires the user to provide the keying material and necessary security association information to each device that is being configured. Manual keying does not scale well as it is usually best used in a small environment.
It is only advisable to use this method if the implementation of Internet Key Exchange (IKE)v1 or IKEv2 on this router is not the same as your remote router or if one of the routers doesn’t support IKE. In these cases, you could manually input the keys. It is recommended to configure auto keying mode for IPsec profile instead of manual keying mode if your router both supports either IKEv1 or IKEv2 and follows the same standards.
When using manual keying mode, make sure that your Key In on your local router is the Key Out on the remote router and the Key In on your remote router is the Key Out on your local router.
An example of the configuration for the two routers would be:
| Field | Router A | Router B |
| SPI Incoming | 100 | 100 |
| SPI Outgoing | 100 | 100 |
| Encryption | AES-256 | AES-256 |
| Key-In | …91bb2b489ba0d28c7741b | …858b8c5ec355505650b16 |
| Key-Out | …858b8c5ec355505650b16 | …91bb2b489ba0d28c7741b |
| Authentication | SHA2-256 | SHA2-256 |
| Key-In | …A00997ec3a195061c81e4 | …2f2de681af020b9ad5f3e3 |
| Key-Out | …2f2de681af020b9ad5f3e3 | …A00997ec3a195061c81e4 |
Additional information about Cisco IPsec technology can be found in this link: Introduction to Cisco IPSec Technology.
To learn how to configure IPsec profiles using auto keying mode on the RV160 and RV260, click here.
To learn how to configure site-to-site VPN on the RV160 and RV260, click here.
To configure site-to-site VPN using the setup wizard, please see the article on: Configuring VPN Setup Wizard on the RV160 and RV260.
Applicable Devices
· RV160
· RV260
Software Version
· 1.0.00.15
Configuring IPsec Profile using Manual Keying Mode
Step 1. Log in to the web configuration utility.
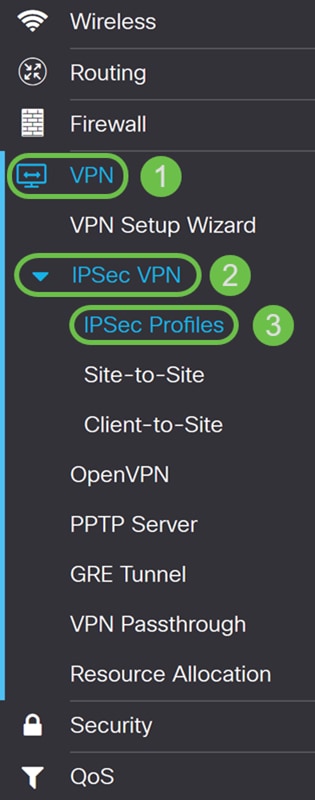
Step 2. Navigate to VPN > IPSec VPN > IPSec Profiles.
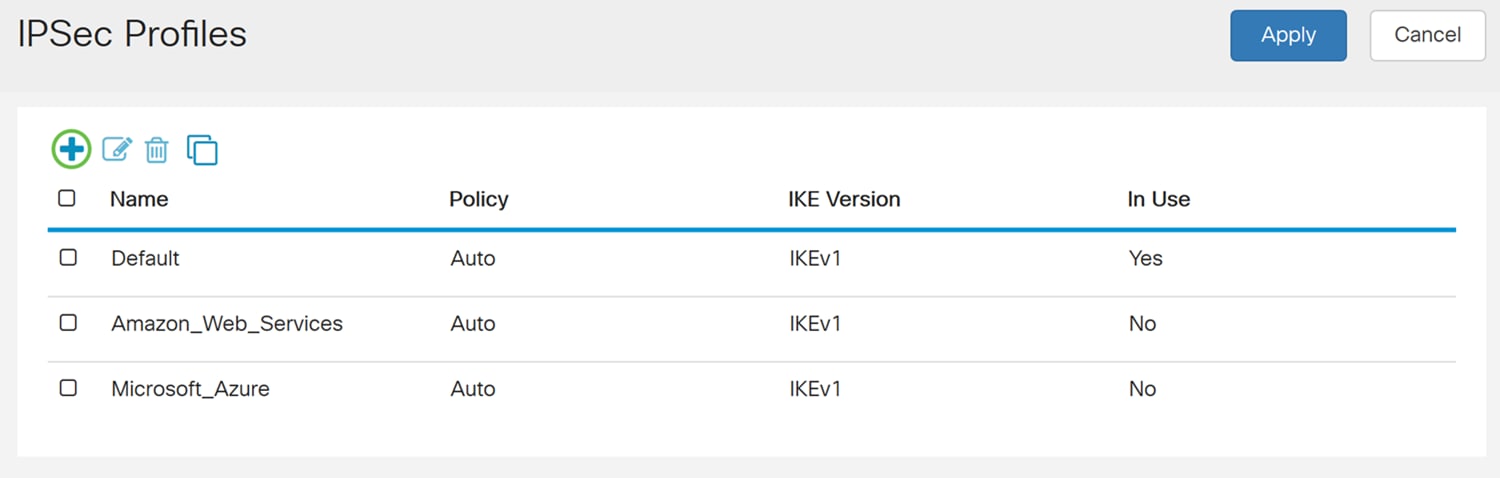
Step 3. Press the plus icon to create a new IPsec profile.
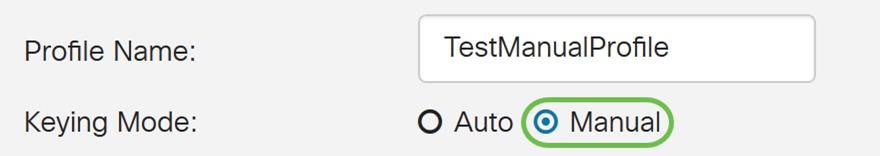
Step 4. Enter a profile name in the Profile Name field.
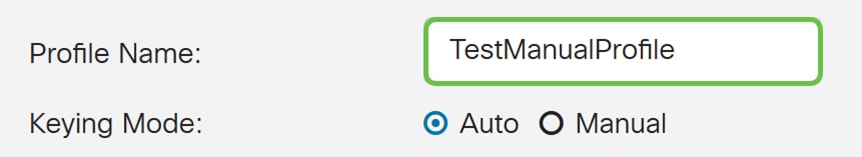
Step 5. Select Manual for the Keying Mode.
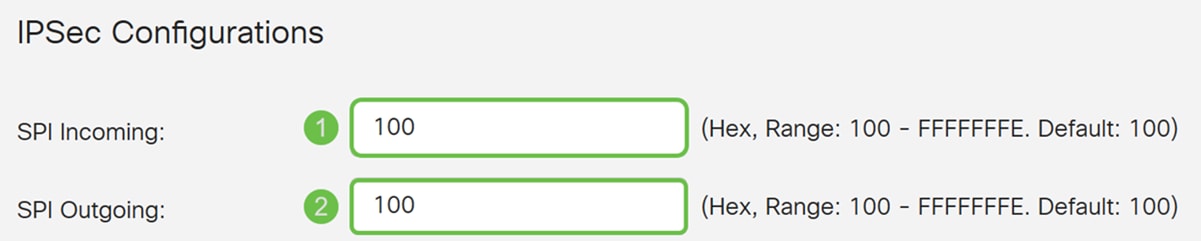
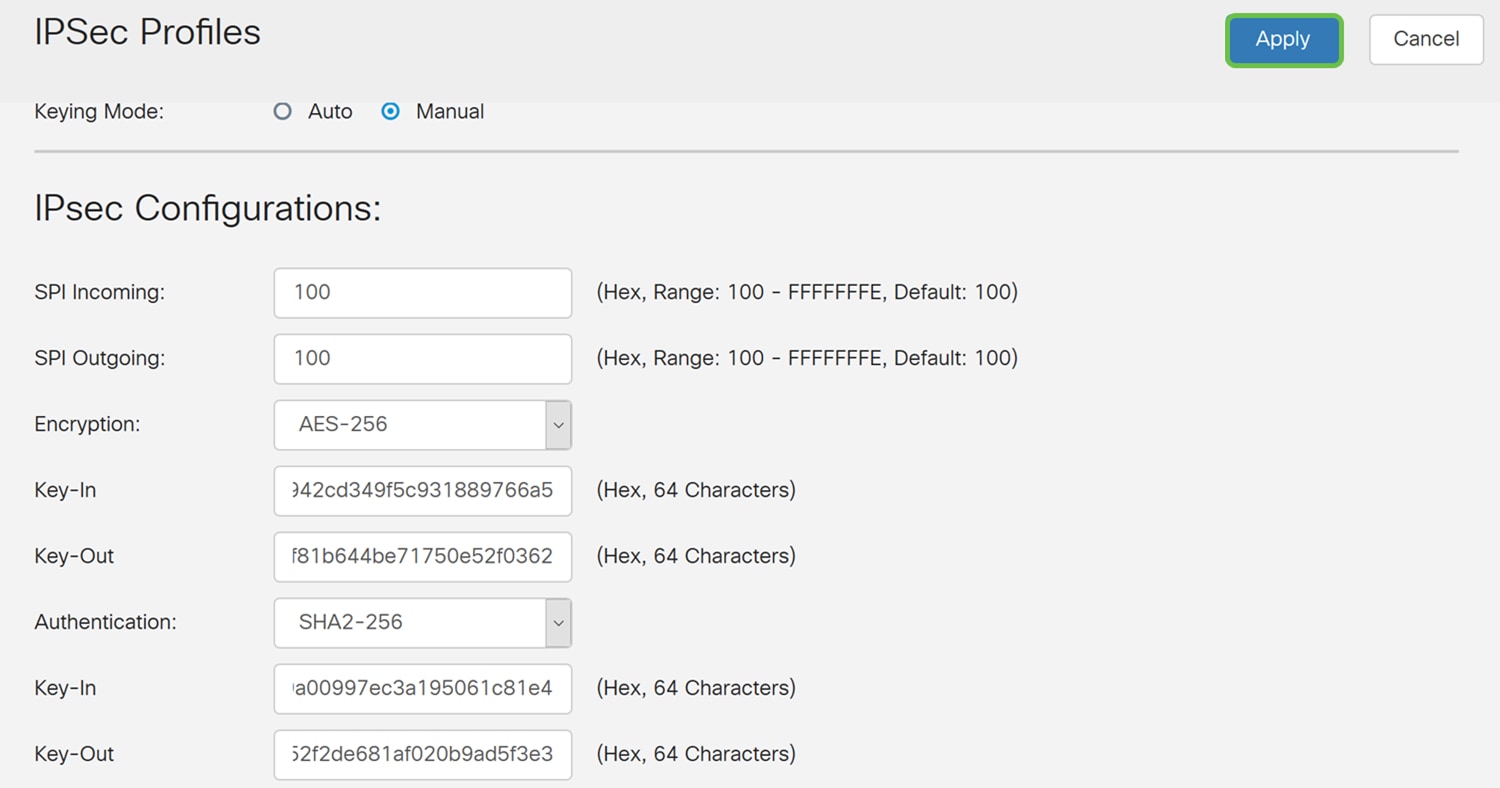
Step 6. In the IPSec Configuration section, enter the Security Parameter Index (SPI) Incoming and SPI Outgoing. The SPI is an identification tag added to the header while using IPsec for tunneling the IP traffic. This tag helps the kernel discern between the two traffic streams where different encryption rules and algorithms may be in use. The hexadecimal range is from 100-FFFFFFFF.
We will be using the default value of 100 for both SPI Incoming and Outgoing.
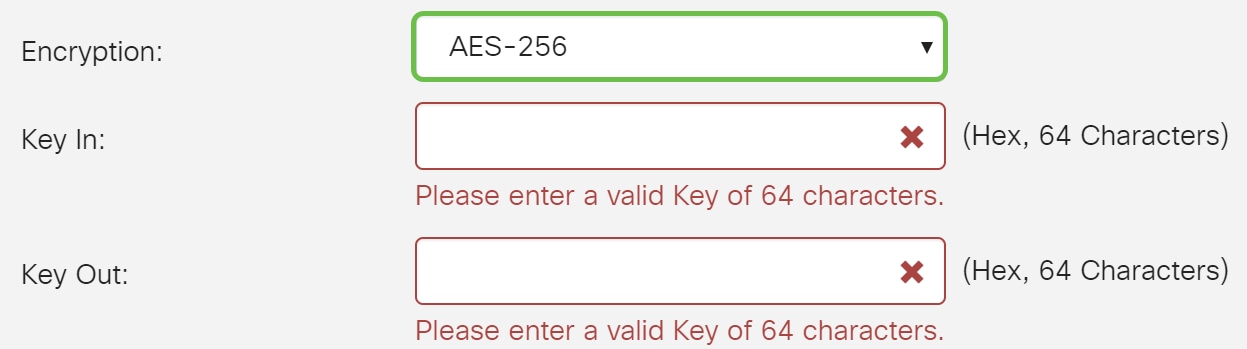
Step 7. Select an encryption (3DES, AES-128, AES-192, or AES-256) from the drop-down list. This method determines the algorithm used to encrypt or decrypt ESP/ISAKMP packets. Triple Data Encryption Standard (3DES) uses DES encryption three times but is now a legacy algorithm. This means that it should only be used when there are no better alternatives since it still provides a marginal but acceptable security level. Users should only use it if it’s required for backwards compatibility as it’s vulnerable to some “block collision” attacks. It is not recommended to use 3DES as it is not considered secure.
Advanced Encryption Standard (AES) is a cryptographic algorithm that is designed to be more secure than 3DES. AES uses a larger key size which ensures that the only known approach to decrypt a message is for an intruder to try every possible key. It is recommended to use AES if your device can support it.
In this example, we will be using AES-256 as our encryption.
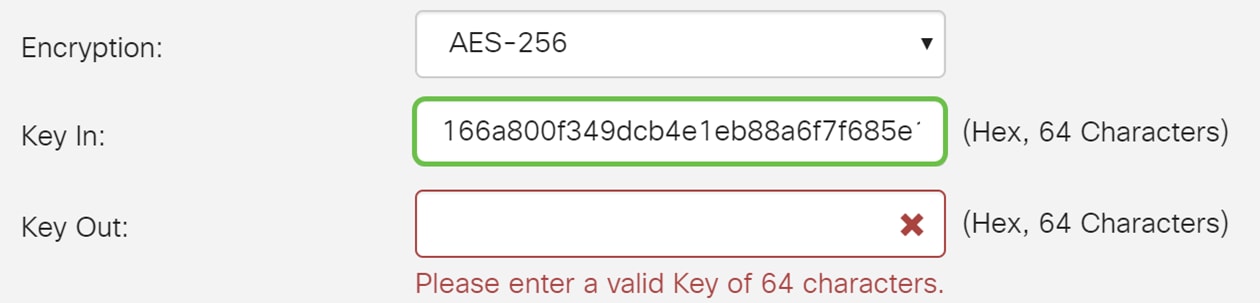
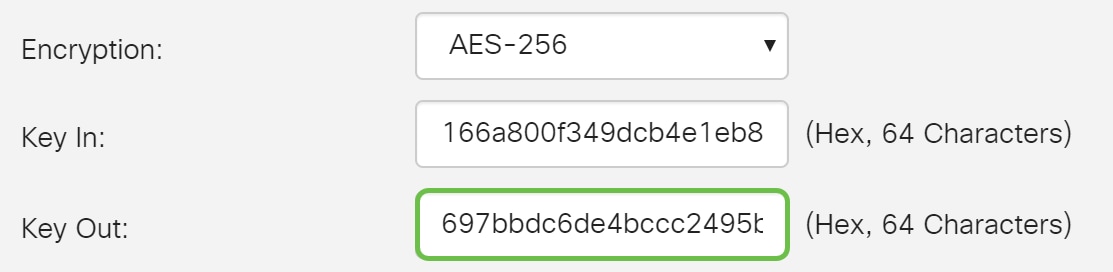
Step 8. Enter a 64 characters hexadecimal number in the Key In field. This is the key for decrypting ESP packets received in hex format.
Best Practice: Use a random hex generator to configure your key in and key out. Make sure that the remote router has the same hexadecimal number.
Step 9. Enter a 64 characters hexadecimal number in the Key Out field. This is the key for encrypting the plain packets in hex format.
Step 10. The authentication method determines how the ESP header packets are validated. This is the hashing algorithm used in the authentication to validate that side A and side B really are who they say they are.
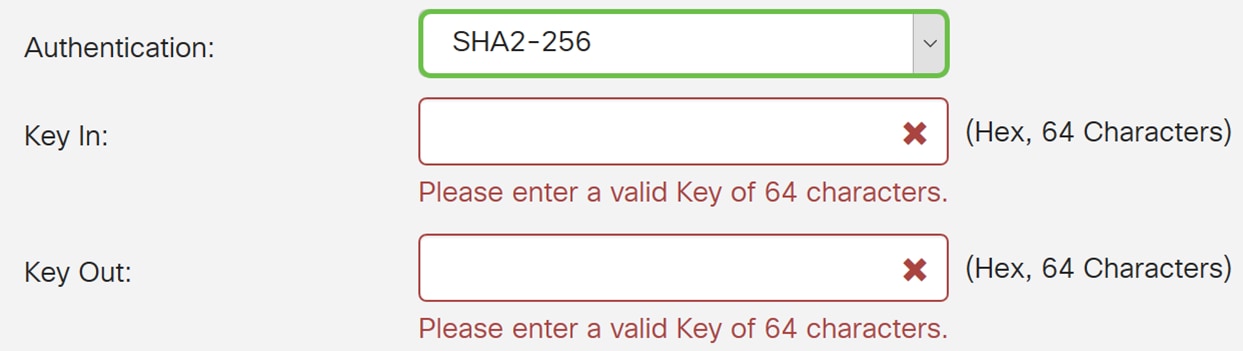
The MD5 is a one-way hashing algorithm that produces a 128-bit digest and is faster than SHA1. The SHA1 is a one-way hashing algorithm that produces a 160-bit digest while SHA2-256 produces a 256-bit digest. SHA2-256 is recommended because it is more secure. Make sure that both ends of the VPN tunnel use the same authentication method. Select an authentication (MD5, SHA1, or SHA2-256).
In this example, we will be selecting SHA2-256.
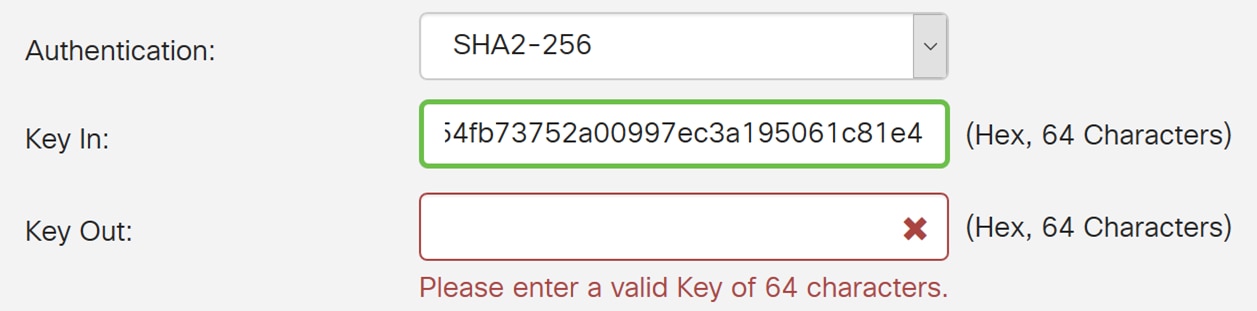
Step 11. Enter in a 64 characters hexadecimal number in the Key In field. This is the key for decrypting ESP packets received in hex format.
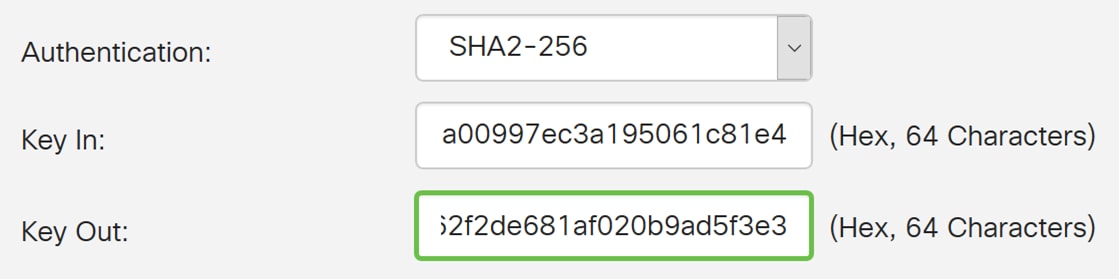
Step 12. Enter in a 64 characters hexadecimal number in the Key Out field. This is the key for encrypting the plain packets in hex format.
Step 13. Press Apply to create the new IPsec Profile.
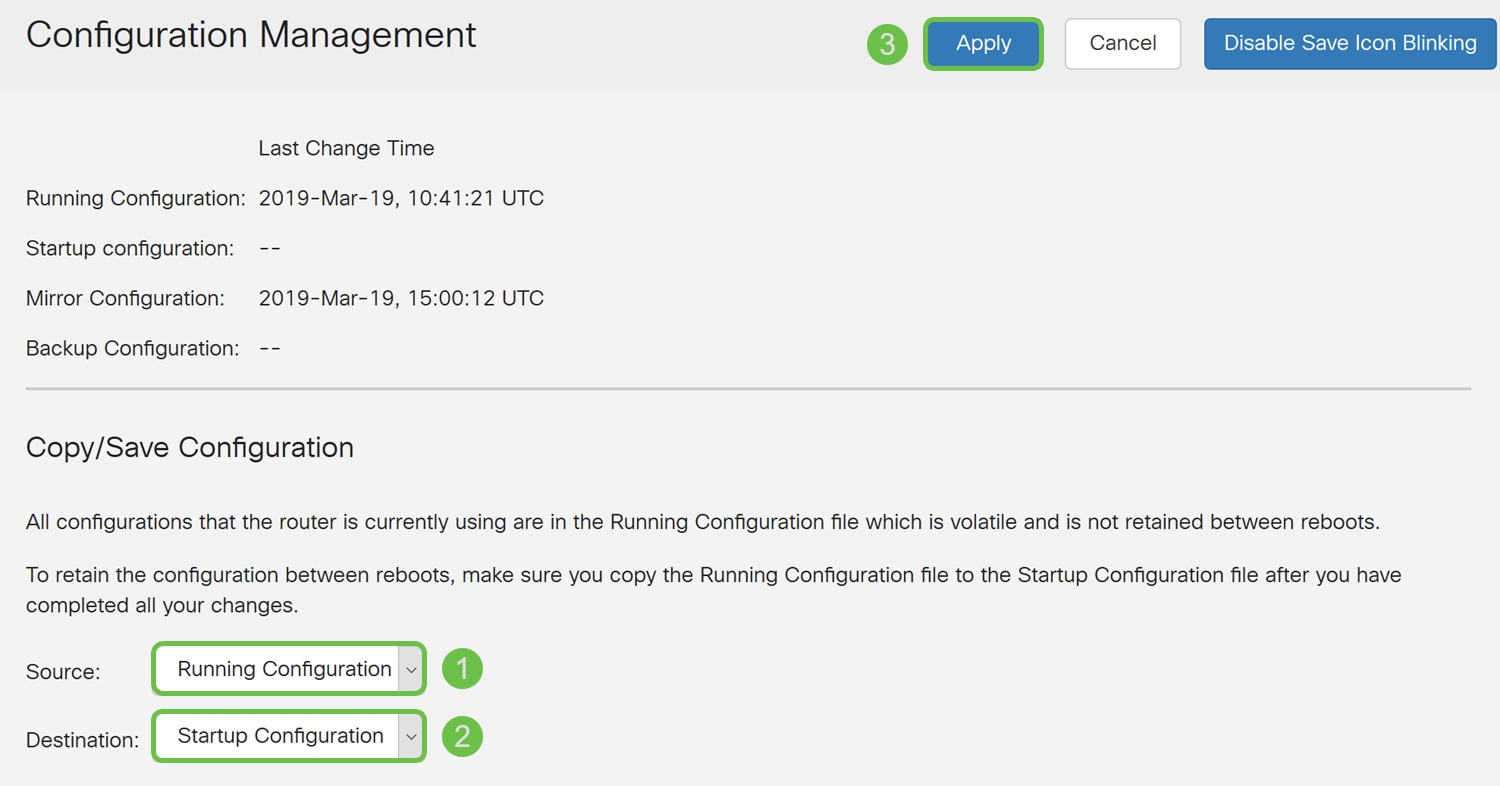
Step 14. At the top of the page, click the Save button. You will be directed to the Configuration Management page.
Step 15. All configurations that the router is currently using are in the Running Configuration file. The configuration will be lost if the device loses power or is rebooted. Copying the Running Configuration file to the Startup Configuration file ensures that the configuration will be saved. Under Configuration Management, make sure the Source is Running Configuration and the Destination is Startup Configuration. Click Apply.
Conclusion
You should now have successfully configured IPsec profile using manual keying mode on your RV160 or RV260.
 Feedback
Feedback