Introduction
This document describes how to configure Threat-Centric NAC with Advance Malware Protection (AMP) on Identity Services Engine (ISE) 2.1. Threat severity levels and vulnerability assessment results can be used to dynamically control the access level of an endpoint or a user. Posture Services is also be covered as a part of this document.
Note: The purpose of the document is to describe ISE 2.1 Integration with AMP, Posture Services are shown as they are required when we provision AMP from ISE.
Prerequisites
Requirements
Cisco recommends that you have basic knowledge of these topics:
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Identity Service Engine version 2.1
- Wireless LAN Controller (WLC) 8.0.121.0
- AnyConnect VPN Client 4.2.02075
- Windows 7 Service Pack 1
Configure
Network Diagram
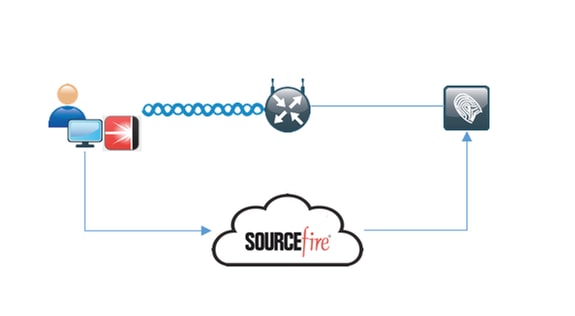
Detailed Flow
1. Client connects to the network, the AMP_Profile is assigned and user is redirected to Anyconnect Provisioning Portal. If Anyconnect is not detected on the machine, all configured modules (VPN, AMP, Posture) are installed. Configuration is pushed for each module along with that profile
2. Once Anyconnect is installed, posture assessment runs
3. AMP Enabler module installs FireAMP connector
4. When client tries to download malicious software, AMP connector throws a warning message and reports it to AMP Cloud
5. AMP Cloud sends this information to ISE
Configure AMP Cloud
Step 1. Download Connector from AMP Cloud
In order to download the connector, navigate to Management > Download Connector. Then select type and Download FireAMP (Windows, Android, Mac, Linux). In this case Audit was selected and the installation file of FireAMP for Windows.
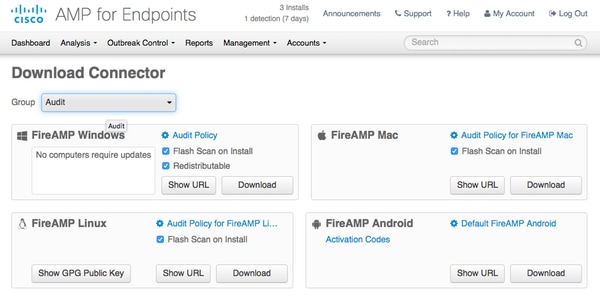
Note: Downloading this file generates an .exe file called Audit_FireAMPSetup.exe in the example. This file was sent to the web server to be available once the user asks for the configuration of AMP.
Configure ISE
Step 1. Configure Posture Policies and Conditions
Navigate to Policy > Policy Elements > Conditions > Posture > File Condition.You can see that a simple condition for file existence has been created. File has to exist if endpoint is to be compliant with the policy verified by the Posture module:
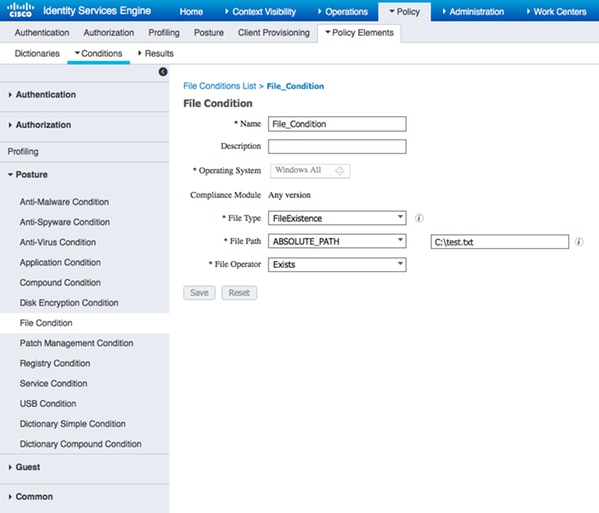
This condition is used for a requirement:
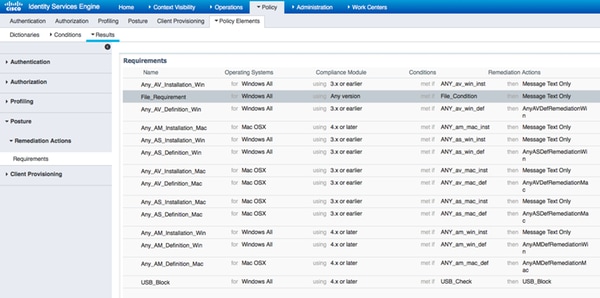
The requirement is used in the Posture policy for Microsoft Windows systems:
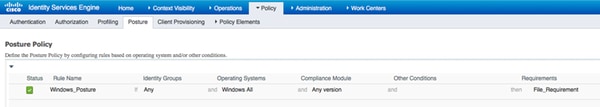
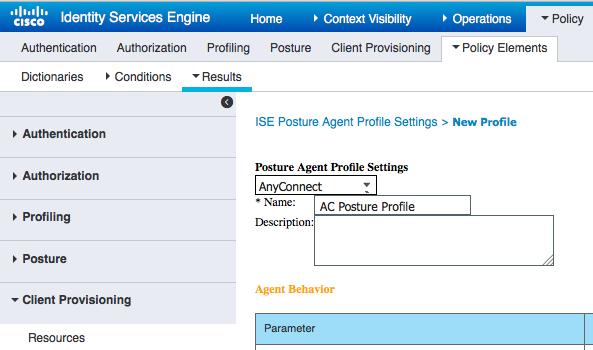
Step 2. Configure Posture Profile
- Navigate to Policy > Policy Elements > Results > Client Provisioning > Resources and add Network Admission Control (NAC) Agent or AnyConnect Agent Posture Profile
- Select Anyconnect
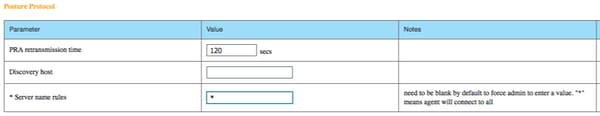
- From the Posture Protocol section add * in order to allow the Agent to connect to all servers
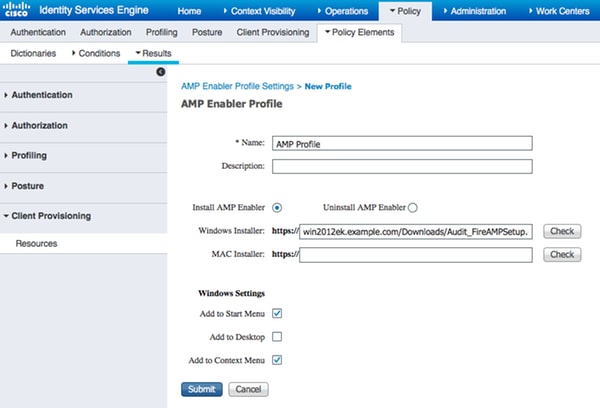
Step 3. Configure AMP Profile
AMP Profile contains information where the Windows Installer is located. Windows Installer was downloaded earlier from the AMP Cloud. It should be accessible from the client machine. Certificate of the HTTPS Server, where Installer is located should be trusted by client machine as well.
Step 2. Upload Applications and XML Profile to ISE
- Download the application manually from official Cisco site: anyconnect-win-4.2.02075-k9.pkg
- On ISE, navigate to Policy > Policy Elements > Results > Client Provisioning > Resources, and add Agent Resources From Local Disk
- Choose Cisco Provided Packages and select anyconnect-win-4.2.02075-k9.pkg
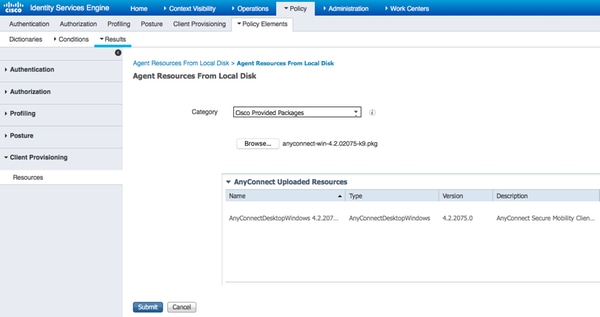
- Navigate to Policy > Policy Elements > Results > Client Provisioning > Resources and add Agent Resources From Local Disk
- Choose Customer Created Packages and type AnyConnect Profile. Select VPNDisable_ServiceProfile.xml
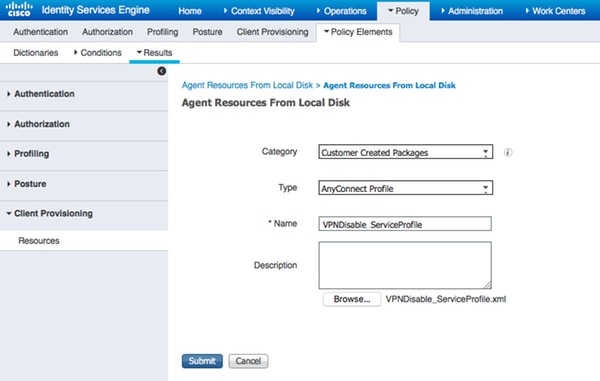
Note: VPNDisable_ServiceProfile.xml is used to hide VPN title, since this example does not use VPN module. This is the content of VPNDisable_ServiceProfile.xml:
<AnyConnectProfile xmlns="http://schemas.xmlsoap.org/encoding/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.xmlsoap.org/encoding/ AnyConnectProfile.xsd">
<ClientInitialization>
<ServiceDisable>true</ServiceDisable>
</ClientInitialization>
</AnyConnectProfile>
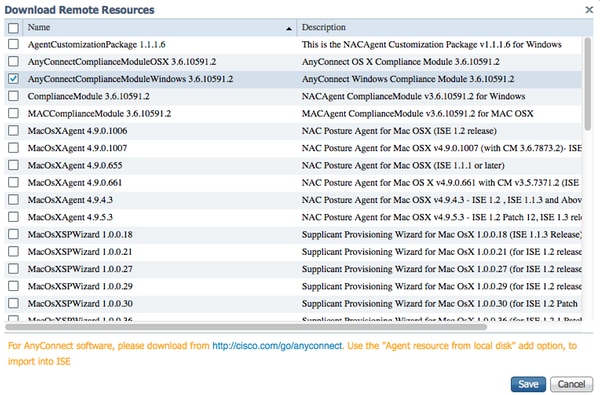
Step 3. Download AnyConnect Compliance module
- Navigate to Policy > Policy Elements > Results > Client Provisioning > Resources and add Agent Resources from Cisco site
- Select AnyConnect Windows Compliance Module 3.6.10591.2 and click on Save
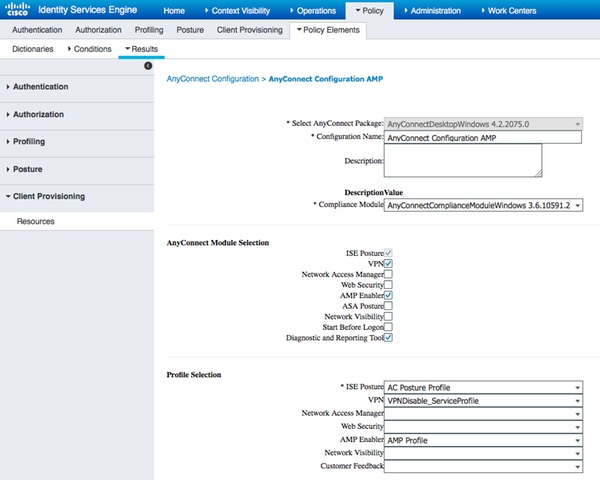
Step 4. Add AnyConnect Configuration
- Navigate to Policy > Policy Elements > Results > Client Provisioning > Resources, and add AnyConnect Configuration
- Configure the name and select the compliance module and all required AnyConnect modules (VPN, AMP, and Posture)
- In Profile Selection, choose the profile configured earlier for each module
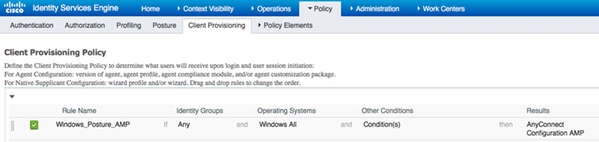
Step 5. Configure Client Provisioning Rules
The AnyConnect configuration created earlier is referenced in the Client Provisioning rules
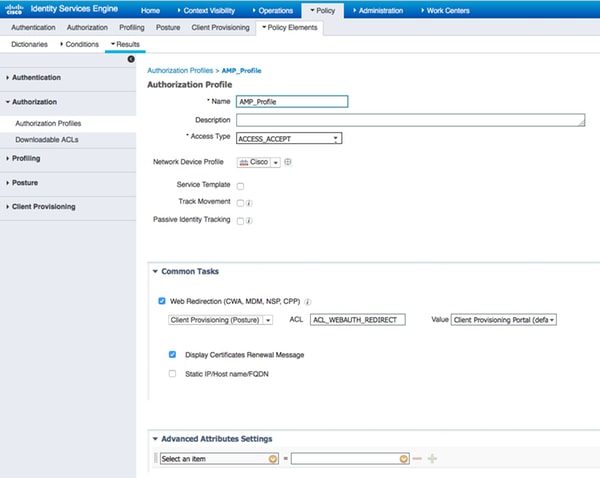
Step 6. Configure Authorization Policies
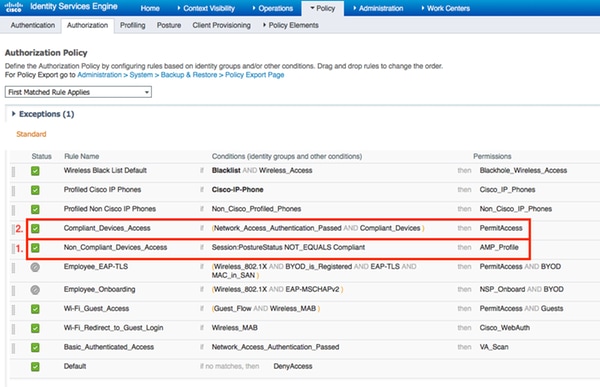
First the redirection to Client Provisioning Portal takes place. Standard authorization policies for posture are used.
Afterwards, once Compliant, full access is assigned
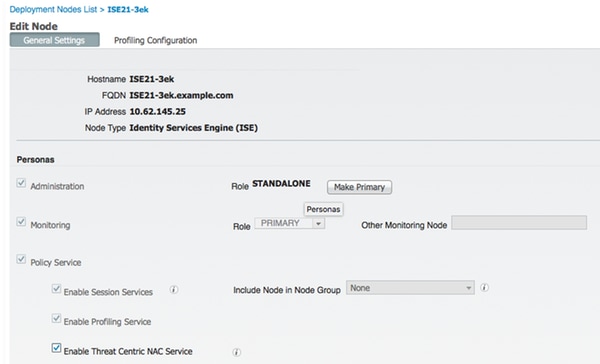
Step 7. Enable TC-NAC Services
Enable TC-NAC Services under Administration > Deployment > Edit Node. Check Enable Threat Centric NAC Service checkbox.
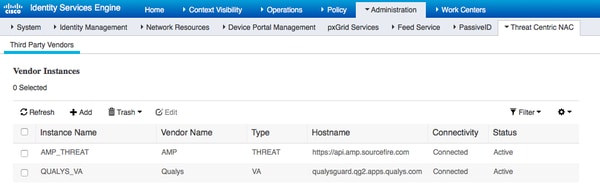
Step 8. Configure AMP Adapter
Navigate to Administration > Threat Centric NAC > Third Party Vendors > Add. Click on Save
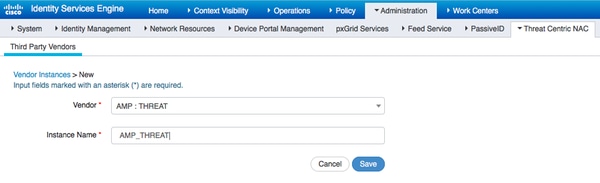
It should transition to Ready to Configure state. Click on Ready to Configure
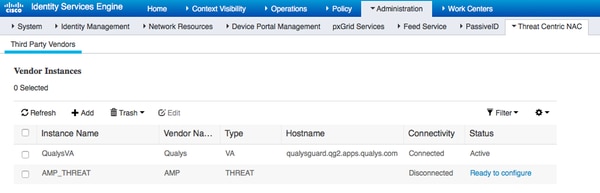
Select Cloud and click on Next
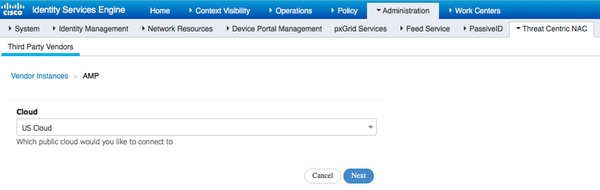
Click the FireAMP link and login as admin in FireAMP.
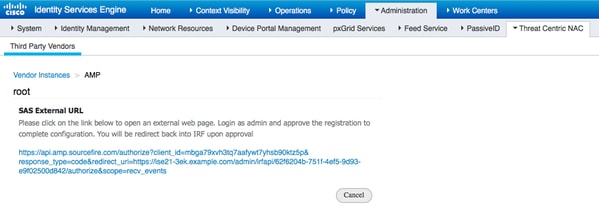
Click Allow in the Applications panel to authorize the Streaming Event Export request. After that action, you are redirected back to Cisco ISE
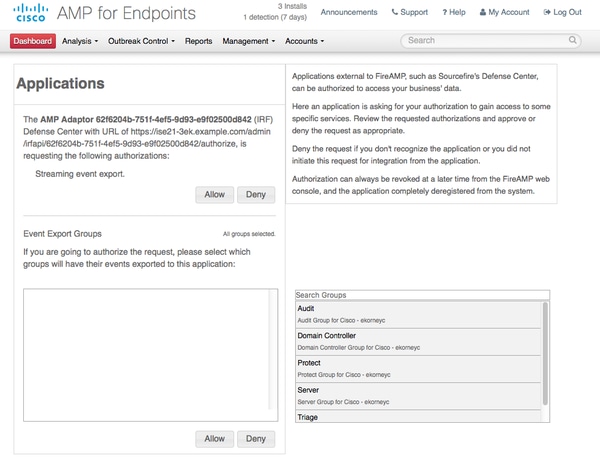
Select the events (for example, suspicious download, connection to suspicious domain, executed malware, java compromise) that you would like to monitor. The summary of the adapter instance configuration is displayed in the configuration summary page. Adapter Instance transitions to Connected/Active State.
Verify
Endpoint
Connect to wireless network via PEAP (MSCHAPv2).
Once connected redirection to Client Provisioning Portal takes place.
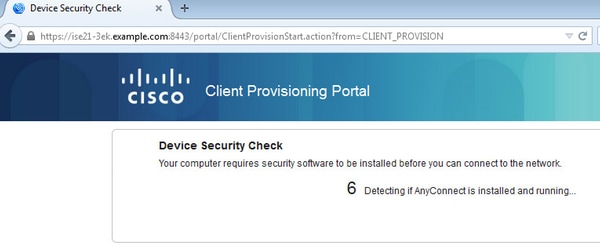
Since there is nothing installed on the client machine, ISE prompts for AnyConnect client installation.
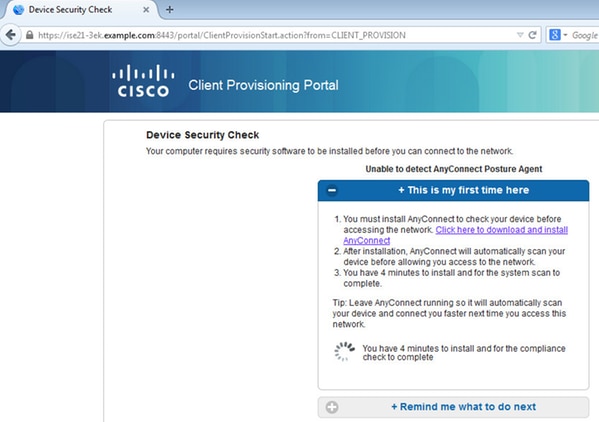
Network Setup Assistant (NSA) application should be downloaded and run from client machine.
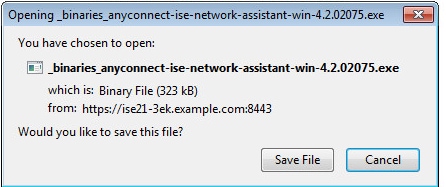
NSA takes care of installing required components and profiles.
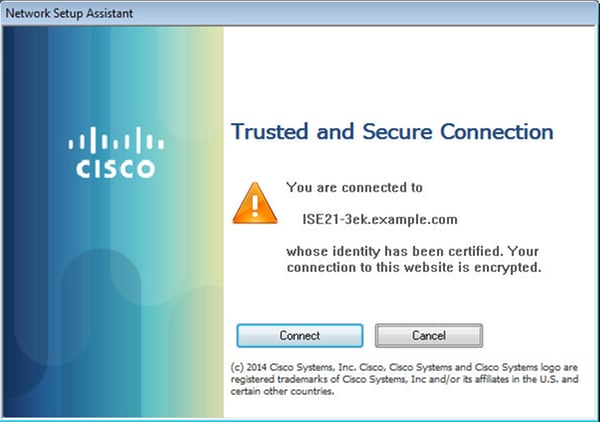
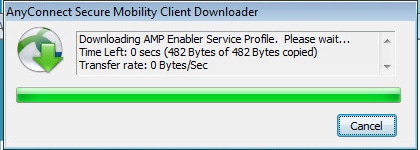
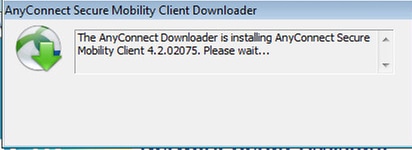
Once installation is finished, AnyConnect Posture module performs compliance check.
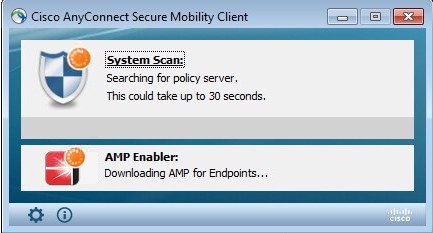
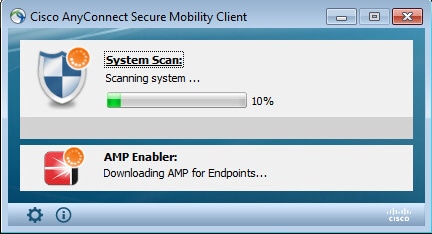
As full access is given, if endpoint is compliant, AMP is downloaded and installed from the webserver specified earlier in the AMP Profile.
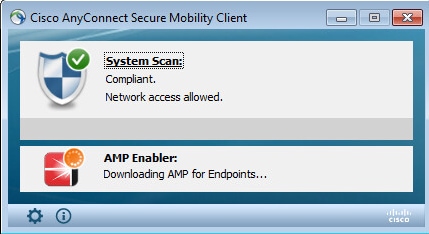
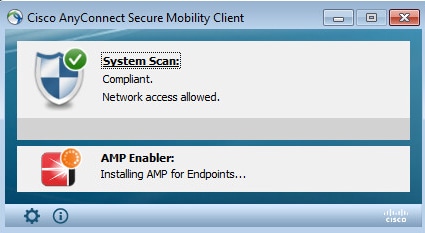
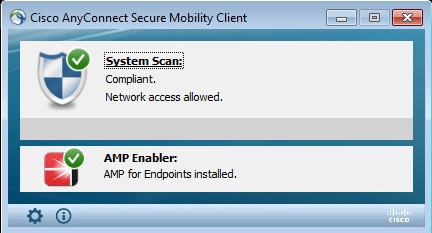
AMP Connector shows up.
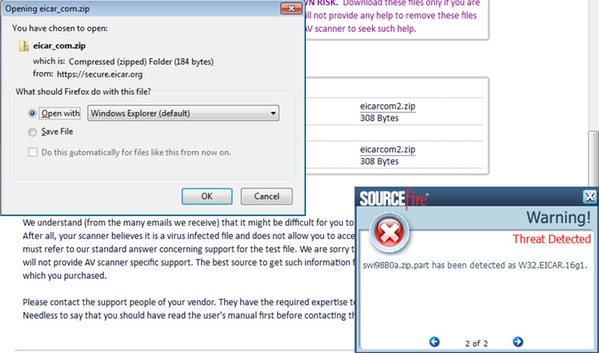
To test AMP in action the Eicar string contained in a zip file is downloaded. The Threat is detected, and reported to AMP Cloud.
AMP Cloud
To verify the details of the threat Dashboard of AMP cloud can be used.
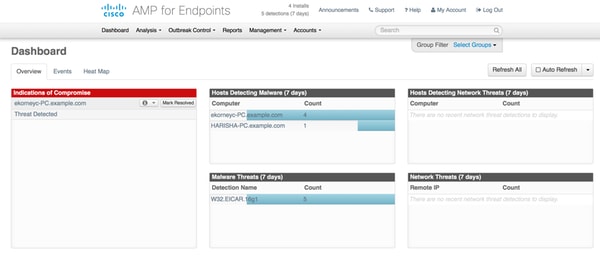
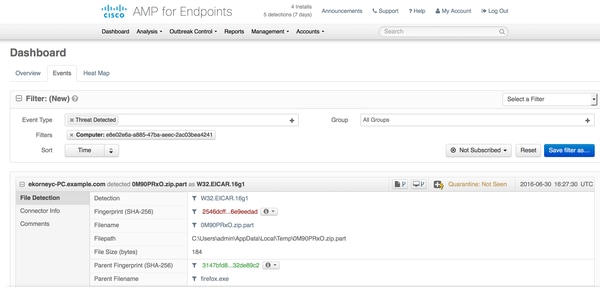
In order to get more details about the threat, filepath and fingerpints, you can click on the Host, where malware was detected.
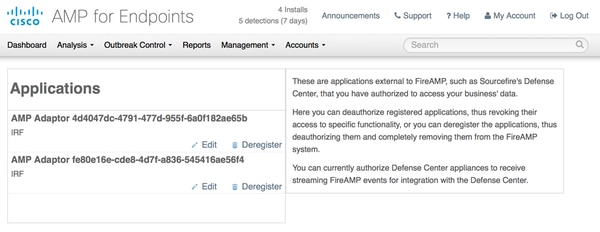
To View or Deregister Instance of ISE you can navigate to Accounts > Applications
ISE
On ISE itself regular posture flow is seen, redirection takes place first to check network compliance. As soon as the endpoint is compliant, CoA Reauth is sent and new profile with PermitAccess is assigned.
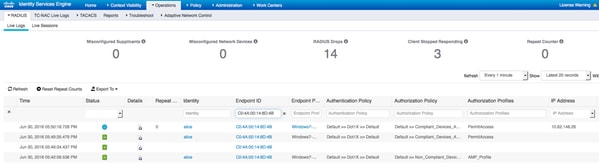
To view the detected Threats you can navigate to Context Visibility > Endpoints > Compromised Endpoints
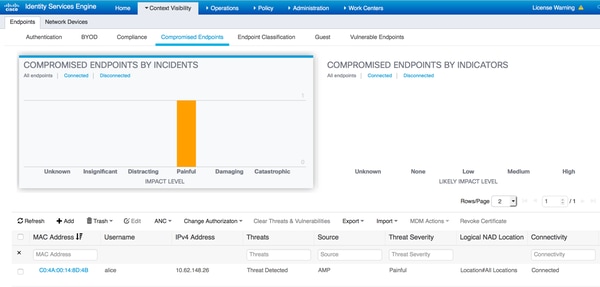
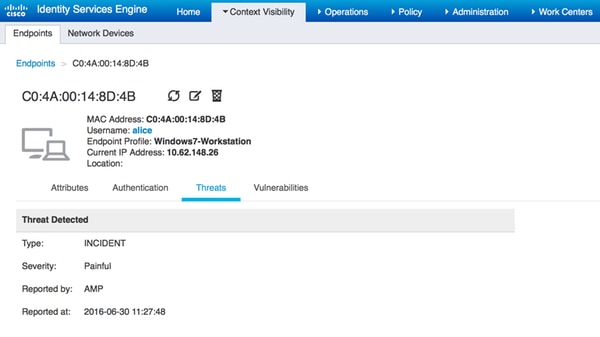
If you select the endpoint and navigate to Threat tab, more details are displayed.
When a threat event is detected for an endpoint, you can select the MAC address of the endpoint on the Compromised Endpoints page and apply an ANC policy (if configured, for example Quarantine). Alternatively you can issue Change of Authorization to terminate the session.
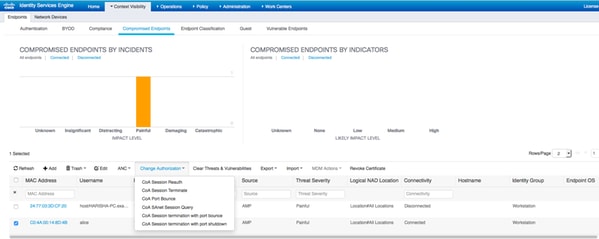
If CoA Session Terminate is selected, ISE sends CoA Disconnect and client loses access to the network.
Troubleshoot
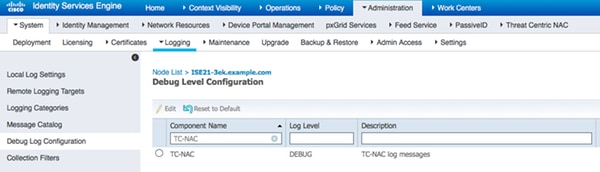
In order to enable debugs on ISE navigate to Administration > System > Logging > Debug Log Configuration, select TC-NAC Node and change the Log Level of TC-NAC component to DEBUG
Logs to be checked - irf.log. You can tail it directly from ISE CLI:
ISE21-3ek/admin# show logging application irf.log tail
Threat Even is received from the AMP Cloud
2016-06-30 18:27:48,617 DEBUG [IRF-AMQP-Dispatcher-Notification-0][] cisco.cpm.irf.amqp.NotificationDispatcher:processDelivery:53 -:::::- calling notification handler com.cisco.cpm.irf.service.IrfNotificationHandler$MyNotificationHandler@3fac8043 Message{messageType=NOTIFICATION, messageId=THREAT_EVENT, content='{"c0:4a:00:14:8d:4b": [{"incident": {"Impact_Qualification": "Painful"}, "time-stamp": 1467304068599, "vendor": "AMP", "title": "Threat Detected"}]}', priority=0, timestamp=Thu Jun 30 18:27:48 CEST 2016, amqpEnvelope=Envelope(deliveryTag=79, redeliver=false, exchange=irf.topic.events, routingKey=irf.events.threat), amqpProperties=#contentHeader<basic>(content-type=application/json, content-encoding=null, headers=null, delivery-mode=null, priority=0, correlation-id=null, reply-to=null, expiration=null, message-id=THREAT_EVENT, timestamp=null, type=NOTIFICATION, user-id=null, app-id=fe80e16e-cde8-4d7f-a836-545416ae56f4, cluster-id=null)}
2016-06-30 18:27:48,617 DEBUG [IRF-AMQP-Dispatcher-Notification-0][] cisco.cpm.irf.service.IrfNotificationHandler:handle:140 -:::::- Added to the pending queue: Message{messageType=NOTIFICATION, messageId=THREAT_EVENT, content='{"c0:4a:00:14:8d:4b": [{"incident": {"Impact_Qualification": "Painful"}, "time-stamp": 1467304068599, "vendor": "AMP", "title": "Threat Detected"}]}', priority=0, timestamp=Thu Jun 30 18:27:48 CEST 2016, amqpEnvelope=Envelope(deliveryTag=79, redeliver=false, exchange=irf.topic.events, routingKey=irf.events.threat), amqpProperties=#contentHeader<basic>(content-type=application/json, content-encoding=null, headers=null, delivery-mode=null, priority=0, correlation-id=null, reply-to=null, expiration=null, message-id=THREAT_EVENT, timestamp=null, type=NOTIFICATION, user-id=null, app-id=fe80e16e-cde8-4d7f-a836-545416ae56f4, cluster-id=null)}
2016-06-30 18:27:48,617 DEBUG [IRF-AMQP-Dispatcher-Notification-0][] cisco.cpm.irf.amqp.NotificationDispatcher:processDelivery:59 -:::::- DONE processing notification: Envelope(deliveryTag=79, redeliver=false, exchange=irf.topic.events, routingKey=irf.events.threat) #contentHeader<basic>(content-type=application/json, content-encoding=null, headers=null, delivery-mode=null, priority=0, correlation-id=null, reply-to=null, expiration=null, message-id=THREAT_EVENT, timestamp=null, type=NOTIFICATION, user-id=null, app-id=fe80e16e-cde8-4d7f-a836-545416ae56f4, cluster-id=null)
2016-06-30 18:27:48,706 DEBUG [IRF-EventProcessor-0][] cisco.cpm.irf.service.IrfEventProcessor:parseNotification:221 -:::::- parsing notification: Message{messageType=NOTIFICATION, messageId=THREAT_EVENT, content='{"c0:4a:00:14:8d:4b": [{"incident": {"Impact_Qualification": "Painful"}, "time-stamp": 1467304068599, "vendor": "AMP", "title": "Threat Detected"}]}', priority=0, timestamp=Thu Jun 30 18:27:48 CEST 2016, amqpEnvelope=Envelope(deliveryTag=79, redeliver=false, exchange=irf.topic.events, routingKey=irf.events.threat), amqpProperties=#contentHeader<basic>(content-type=application/json, content-encoding=null, headers=null, delivery-mode=null, priority=0, correlation-id=null, reply-to=null, expiration=null, message-id=THREAT_EVENT, timestamp=null, type=NOTIFICATION, user-id=null, app-id=fe80e16e-cde8-4d7f-a836-545416ae56f4, cluster-id=null)}
Information about the threat is sent to PAN
2016-06-30 18:27:48,724 DEBUG [IRF-EventProcessor-0][] cisco.cpm.irf.service.IrfEventProcessor:storeEventsInES:366 -:::::- Adding threat event info to send to PAN - c0:4a:00:14:8d:4b {incident={Impact_Qualification=Painful}, time-stamp=1467304068599, vendor=AMP, title=Threat Detected}














































 Feedback
Feedback