Introduction
This document describes how to find the File Analysis Client ID for Cisco Secure Email Gateway, Cloud Gateway, and Email and Web Manager. The File Analysis Client ID is a unique 65-character registration key used when the Gateway, Cloud Gateway, or Email and Web Manager registers with Cisco Malware Analytics (formerly Threat Grid) for file submission and sandboxing. For example, if you have enabled the File Analysis service, and the reputation service has no information about the file attachment found in a message, and the file attachment meets the criteria for files that can be analyzed (seeSupported Files for File Reputation and Analysis Services), then the message can be quarantined (seeQuarantining Messages with Attachments Sent for Analysis), and the file sent for analysis.
For "Appliance Grouping for File Analysis Reporting," please be sure you know your File Analysis ID(s).
For complete details, please see the "File Reputation Filtering and File Analysis" chapter of the User Guide:
File Analysis Client ID for Gateway, Cloud Gateway, and Email and Web Manager
The File Analysis Client ID is automatically generated for appliances when you enable File Analysis.
Before you begin from the Gateway or Cloud Gateway, please ensure you have the needed feature keys and enabled File Reputation and File Analysis. To see your feature keys, navigate to System Administration > Feature Keys. File Reputation and File Analysis are listed separately and have Active status.
Gateway or Cloud Gateway
- Log in to the user interface.
- Navigate to Security Services > File Reputation and Analysis.
- Click Edit Global Settings…
- Expand Advanced Settings for File Analysis.
The File Analysis Client ID is listed here.
Example:
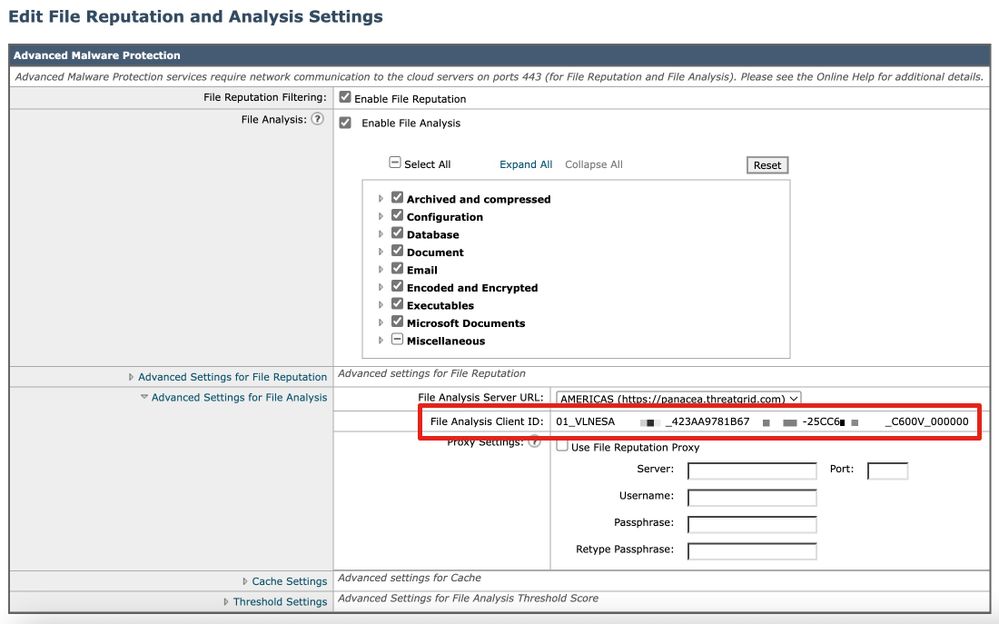
Note: There is a difference in the File Analysis Client ID for virtual appliances vs. hardware appliances.
The File Analysis Client ID for the Gateway or Cloud Gateway is based on a 65-character string format:
| Value |
Explanation |
| 01_ |
"01" is specific to the Gateway or Cloud Gateway. |
| VLNESAXXXYYY_ |
If this is a virtual appliance, it uses the VLN license # (found from the CLI command showlicense). If this is a hardware appliance, there is no field. |
| SERIAL_ |
FULL serial of the appliance. |
| CX00V_ |
Model of the appliance. |
| 00000000 |
Field zeros. Based on the previous fields, these vary to finish out the field of 65 characters. |
Email and Web Manager
- Log in to the user interface.
- Navigate to Centralized Management > Security Appliance.
At the bottom of this page is the File Analysis section. The File Analysis Client ID is listed here.
Example:
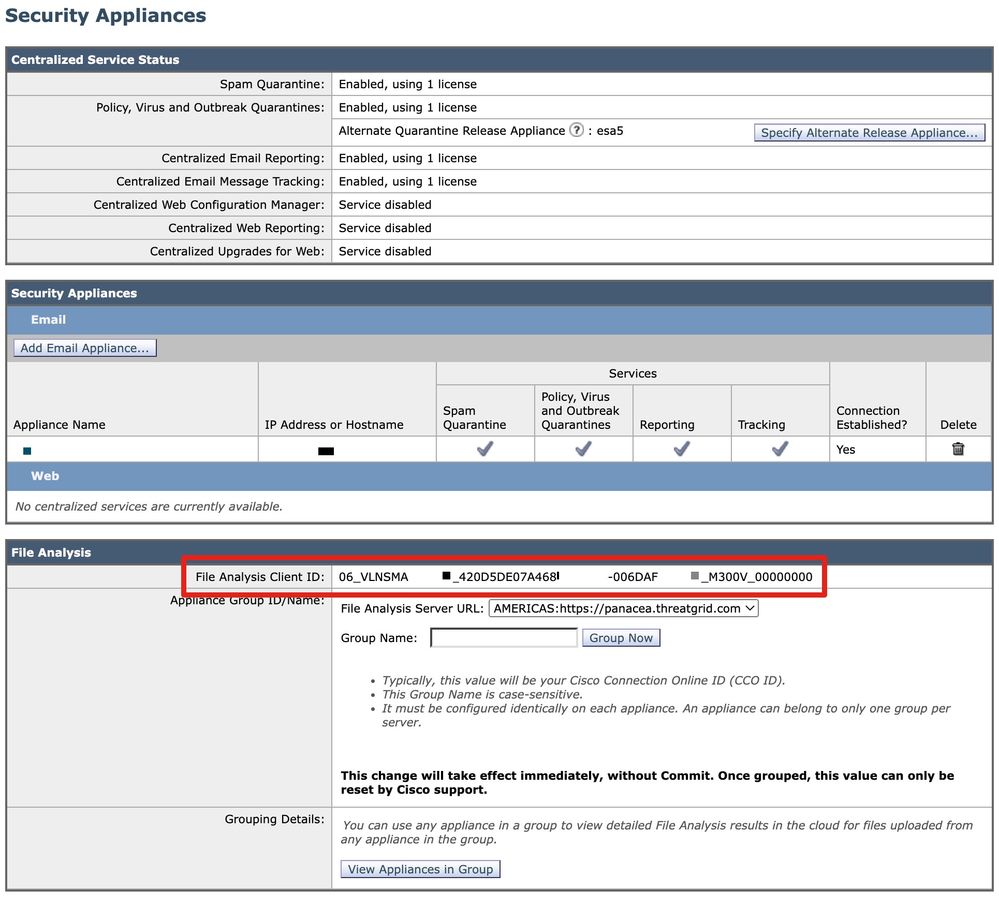
Note: There is a difference in the File Analysis Client ID for virtual appliances vs. hardware appliances.
The File Analysis Client ID for the Email and Web Manager is based on a 65-character string format:
|
Value
|
Explanation
|
|
06_
|
"06" is specific to the Email and Web Manager.
|
|
VLNSMAXXXYYY_
|
If this is a virtual appliance, it uses the VLN license # (found from the CLI command showlicense). If this is a hardware appliance, there is no field.
|
|
SERIAL_
|
FULL serial of the appliance.
|
|
MX00V_
|
Model of the appliance.
|
|
000000
|
Field zeros. Based on the previous fields, these vary to finish out the field of 65 characters.
|
Appliance Grouping for File Analysis Reporting
If your license includes access to Cisco Secure Malware Analytics (https://panacea.threatgrid.com), the best practice for your Gateway or Cloud Gateway is to have them associated with your individual organization account. To allow all content security appliances in your organization to display detailed results in the cloud about files sent for analysis from any Gateway or Cloud Gateway in your organization, you need to join all appliances to the same appliance group. When you log in to Malware Analytics, your submissions and threat samples sent to the cloud for analysis are all displayed in the Malware Analytics dashboard for your organization.
Note: Cloud Gateway customers have this configured during activations and deployment performed by Cisco.
Group Appliances
Note: If you have a Cloud Gateway and this is not completed, please open a support case before you configure an Appliance Group ID/Name.
Gateway or Cloud Gateway
- From the user interface, navigate to Security Services > File Reputation and Analysis.
- Click on Click here to group or view appliances for File Analysis reporting.
- Enter your Appliance Group ID/Name. The default values are:
- It is suggested to use your CCOID for this value.
- An appliance can belong to only one group.
- After you configure the File Analysis feature, you can add a machine to a group.
- Click Group Now.
Email and Web Manager
Note: The option to configure an Appliance Group ID/Name is only available after the Email and Web Manager has an Email Appliance added for centralized management purposes and has the Policy, Virus, Outbreak Quarantines migrated.
- From the user interface, navigate to Centralized Services > Security Appliances.
- Enter your Appliance Group ID/Name. The default values are:
- Typically, this value is your Cisco Connection Online ID (CCO ID).
- This Group Name is case-sensitive.
- It must be configured identically on each appliance. An appliance can belong to only one group per server.
- Click Group Now.
Please note:
- When you add a Group ID, it takes effect immediately, without a commit. If you need to change a Group ID, you must contact Cisco TAC.
- This name is case-sensitive and must be configured identically on each appliance in the Analysis Group.
View Appliances
Gateway or Cloud Gateway
- From the user interface, navigate to Security Services > File Reputation and Analysis.
- Click on Click here to group or view appliances for File Analysis reporting.
- Click on View Appliances.
Email and Web Manager
- From the user interface, navigate to Centralized Services > Security Appliances.
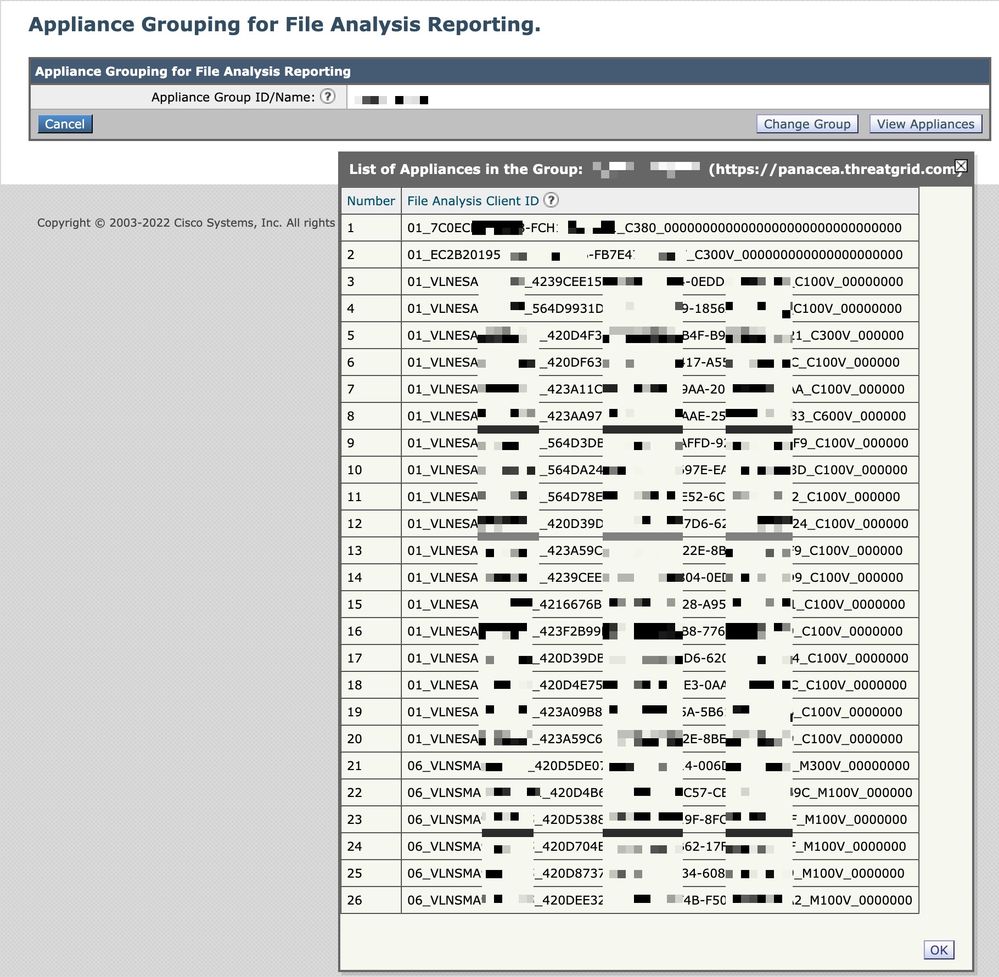
- Click on View Appliances in Group in the File Analysis section.
The File Analysis Client ID of all appliances associated with the Appliance Group ID/Name are listed here.
Example:
Additional Information
Cisco Secure Email Gateway Documentation
Secure Email Cloud Gateway Documentation
Cisco Secure Email and Web Manager Documentation
Cisco Secure Malware Analytics
Cisco Secure Product Documentation




 Feedback
Feedback