Learn about the latest trends and best practices in today’s cloud and network security landscape.
See Multicloud Defense in action with an instant demo
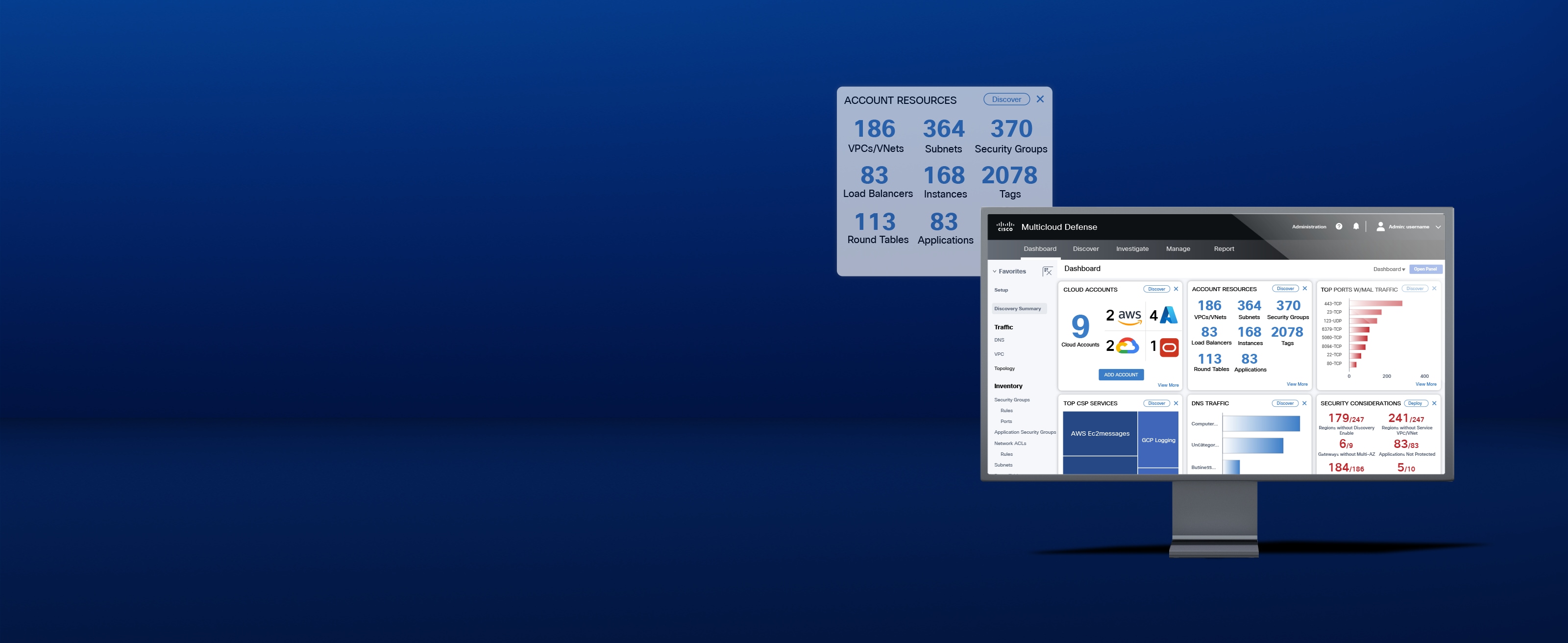
The cloud speaks many languages. Cisco Multicloud Defense translates them all—unifying environments, saving you time, reducing risk, and increasing efficiency. Watch the instant demo to learn how Multicloud Defense simplifies security, helps you maintain control over your cloud data, and reduce risk.
Unify security, protect workloads across environments