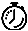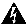-
Real-Time Monitoring Tool Administration Guide for Cisco Unity Connection Release 2.x
-
Index
-
Preface
-
Understanding Real-Time Monitoring Tool
-
Installing and Configuring Real-Time Monitoring Tool
-
Monitoring Predefined Objects
-
Understanding Performance Monitoring
-
Configuring and Displaying Performance Counters
-
Alerts
-
Working with Alerts
-
Using Plug-ins
-
Configuring Trace and Log Central in RTMT
-
Using SysLog Viewer in RTMT
-
Port Monitor
-
Appendix: Performance Objects and Counters for the System
-
Appendix: Performance Objects and Counters for Cisco Unity Connection
-
Table Of Contents
Preface
This preface describes the purpose, audience, organization, and conventions of this guide, and provides information on how to obtain related documentation.
The preface covers these topics:
•
Obtaining Documentation, Obtaining Support, and Security Guidelines
•
Cisco Product Security Overview
PurposeThe Cisco Unified Communications Manager Real-Time Monitoring Tool Administration Guide provides information about the Real-Time Monitoring Tool (RTMT).
Use this book with the Cisco Unity Connection System Administration Guide and the Administration Guide for Cisco Unity Connection Serviceability. All documents provide instructions for administering Cisco Unity Connection and include descriptions of procedural tasks that you complete by using Cisco Unity Connection Administration.
AudienceThe Cisco Unified Communications Manager Real-Time Monitoring Tool Administration Guide provides information for network administrators responsible for managing and supporting Cisco Unity Connection. Network engineers, system administrators, or telecom engineers use this guide to learn about, and administer, remote serviceability features. This guide requires knowledge of telephony and IP networking technology.
OrganizationThe following table shows how this guide is organized:
Provides a brief description of the Real-Time Monitoring Tool (RTMT).
Chapter 2, "Installing and Configuring Real-Time Monitoring Tool"
Provides procedures for installing, upgrading, and uninstalling RTMT. Also provides information on how to navigate within RTMT and how to configure profiles.
Provides an overview of the predefined objects that are monitored by RTMT.
Provides an overview of performance counters.
Chapter 5, "Configuring and Displaying Performance Counters"
Provides procedures for working with performance monitors, including viewing performance counters and counter descriptions.
Provides an overview of alerts, including a description of preconfigured alerts. Describes fields that you use to configure alerts and alert actions.
Provides procedures for working with Alerts.
Provides information on installing and using plugins in the Real-Time Monitoring tool.
Provides information on configuring on-demand trace collection and crash dump files for system services as well as on viewing the trace files in the appropriate viewer.
Provides information on using the SysLog Viewer.
Provides information on the Port Monitor for Cisco Unity Connection.
Chapter A, "Performance Objects and Counters for the System"
Provides a list of performance objects and their associated counters for the system
Appendix B, "Performance Objects and Counters for Cisco Unity Connection"
Provides a list of performance objects and their associated counters for Cisco Unity Connection.
Related DocumentationFor additional Cisco Unity Connection documentation, refer to the Documentation Guide for Cisco Unity Connection at http://www.cisco.com/en/US/products/ps6509/products_documentation_roadmaps_list.html.
ConventionsThis document uses the following conventions:
Notes use the following conventions:
Note
Means reader take note. Notes contain helpful suggestions or references to material not covered in the publication.
Timesavers use the following conventions:
Timesaver
Means the described action saves time. You can save time by performing the action described in the paragraph.
Tips use the following conventions:
Tip
Means the information contains useful tips.
Cautions use the following conventions:
CautionMeans reader be careful. In this situation, you might do something that could result in equipment damage or loss of data.
Warnings use the following conventions:
Warning
This warning symbol means danger. You are in a situation that could cause bodily injury. Before you work on any equipment, you must be aware of the hazards involved with electrical circuitry and familiar with standard practices for preventing accidents.
Obtaining Documentation, Obtaining Support, and Security GuidelinesFor information on obtaining documentation, obtaining support, providing documentation feedback, security guidelines, and also recommended aliases and general Cisco documents, see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Cisco Product Security OverviewThis product contains cryptographic features and is subject to United States and local country laws governing import, export, transfer and use. Delivery of Cisco cryptographic products does not imply third-party authority to import, export, distribute or use encryption. Importers, exporters, distributors and users are responsible for compliance with U.S. and local country laws. By using this product you agree to comply with applicable laws and regulations. If you are unable to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at: http://www.cisco.com/wwl/export/crypto/tool/stqrg.html. If you require further assistance please contact us by sending email to export@cisco.com.

 Feedback
Feedback