-
Catalyst 4500 Series Software Configuration Guide, 7.5
-
Preface
-
Product Overview
-
Using the Command-Line Interface
-
Configuring the Switch IP Address and Default Gateway
-
Configuring Ethernet and Fast Ethernet Switching
-
Configuring Gigabit Ethernet Switching
-
Configuring Fast EtherChannel and Gigabit EtherChannel
-
Configuring Spanning Tree
-
Configuring Spanning Tree PortFast, BPDU Guard, BPDU Filter, UplinkFast, BackboneFast, and Loop Guard
-
Configuring VTP
-
Configuring VLANs
-
Configuring VLAN Trunks on Fast Ethernet and Gigabit Ethernet Ports
-
Configuring Dynamic VLAN Membership with VMPS
-
Configuring GVRP
-
Configuring QoS
-
Configuring Multicast Services
-
Configuring Port Security
-
Configuring Unicast Flood Blocking
-
Configuring the IP Permit List
-
Configuring Protocol Filtering
-
Checking Port Status and Connectivity
-
Configuring CDP
-
Using Switch TopN Reports
-
Configuring UDLD
-
Configuring SNMP
-
Configuring RMON
-
Configuring SPAN and RSPAN
-
Administering the Switch
-
Configuring Switch Access Using AAA
-
Modifying the Switch Boot Configuration
-
Working with System Software Images
-
Using the Flash File System
-
Working with Configuration Files
-
Configuring Switch Acceleration
-
Configuring System Message Logging
-
Configuring DNS
-
Configuring NTP
-
Glossary
-
Index
-
Table Of Contents
Understanding How PortFast Works
Enabling PortFast on an Access Port
Enabling PortFast on a Trunk Port
Understanding How PortFast BPDU Guard Works
Configuring PortFast BPDU Guard
Understanding How PortFast BPDU Filtering Works
Configuring PortFast BPDU Filtering
Enabling PortFast BPDU Filtering
Disabling PortFast BPDU Filter
Understanding How UplinkFast Works
Understanding How BackboneFast Works
Displaying BackboneFast Statistics
Understanding How Loop Guard Works
Configuring Spanning Tree PortFast, BPDU Guard, BPDU Filter, UplinkFast, BackboneFast, and Loop Guard
This chapter describes how to configure the PortFast, BPDU guard, BPDU filter, UplinkFast, and BackboneFast, and loop guard spanning tree enhancements on the Catalyst enterprise LAN switches.
Note
For information on configuring spanning tree, see "Configuring Spanning Tree."
Note
For complete syntax and usage information for the commands used in this chapter, refer to the Command Reference—Catalyst 4000 Family, Catalyst 2948G, and Catalyst 2980G Switches.
This chapter consists of these major sections:
•
Understanding How PortFast Works
•
Understanding How PortFast BPDU Guard Works
•
Configuring PortFast BPDU Guard
•
Understanding How PortFast BPDU Filtering Works
•
Configuring PortFast BPDU Filtering
•
Understanding How UplinkFast Works
•
Understanding How BackboneFast Works
•
Understanding How Loop Guard Works
Understanding How PortFast Works
PortFast causes a switch or trunk port to enter the spanning tree forwarding state immediately, bypassing the listening and learning states.
You can use PortFast on switch or trunk ports connected to a single workstation, switch, or server to allow those devices to connect to the network immediately, instead of waiting for the port to transition from the listening and learning states to the forwarding state.
CautionYou can use PortFast to connect a single end station or a switch port to a switch port. If you enable PortFast on a port connected to another Layer 2 device, such as a switch, you might create network loops.
When the switch powers up, or when a device is connected to a port, the port normally enters the spanning tree listening state. When the Forward Delay timer expires, the port enters the learning state. When the Forward Delay timer expires a second time, the port is transitioned to the forwarding or blocking state.
When you enable PortFast on a switch or trunk port, the port is immediately transitioned to the spanning tree forwarding state.
Configuring PortFast
These sections describe how to configure PortFast on the switch:
•
Enabling PortFast on an Access Port
•
Enabling PortFast on a Trunk Port
Enabling PortFast on an Access Port
CautionYou can use PortFast to connect a single end station or a switch port to a switch port. If you enable PortFast on a port connected to another Layer 2 device, such as a switch, you might create network loops.
To enable PortFast on a switch port, perform this task in privileged mode:
This example shows how to enable PortFast on port 1 of module 4 and verify the configuration, the PortFast status is shown in the "Fast-Start" column:
Console> (enable) set spantree portfast 4/1 enableWarning:Connecting Layer 2 devices to a fast start port can causetemporary spanning tree loops. Use with caution.Spantree port 4/1 fast start enabled.Console> (enable) show spantree 4/1Port Vlan Port-State Cost Priority Fast-Start Group-method--------- ---- ------------- ----- -------- ---------- ------------4/1 1 blocking 19 20 enabled4/1 100 forwarding 10 20 enabled4/1 521 blocking 19 20 enabled4/1 522 blocking 19 20 enabled4/1 523 blocking 19 20 enabled4/1 524 blocking 19 20 enabled4/1 1003 not-connected 19 20 enabled4/1 1005 not-connected 19 4 enabledConsole> (enable)Enabling PortFast on a Trunk Port
CautionYou can use PortFast to connect a single end station or a switch port to a switch port. If you enable PortFast on a port connected to another Layer 2 device, like a switch, you might create network loops.
To enable PortFast on a trunk port, perform this task in privileged mode:
This example shows how to enable PortFast on port 1 of module 4 of a trunk port, bring the trunk port to a forwarding state, and verify the configuration (the PortFast status is shown in the "Fast-Start" column):
Console> (enable) set spantree portfast 4/1 enable trunkWarning:Connecting Layer 2 devices to a fast start port can causetemporary spanning tree loops. Use with caution.Spantree port 4/1 fast start enabled.Console> (enable) show spantree 4/1Port Vlan Port-State Cost Prio PortfastChannel_id------------------------ ---- ------------- --------- ---- ------------------4/1 1 blocking 4 32 enabled 04/1 100 forwarding 4 32 enabled 04/1 521 blocking 4 32 enabled 04/1 524 blocking 4 32 enabled 04/1 1003 not-connected 4 32 enabled 04/1 1005 not-connected 4 32 enabled 0Console> (enable) show spantree portfast 4/1Portfast:enable trunkPortfast BPDU guard is disabled.Portfast BPDU filter is disabled.Console>
Note
When you enable PortFast between two switches, the system will verify that there are no loops in the network before bringing the blocking trunk to a forwarding state.
Disabling PortFast
To disable PortFast on a switch or trunk port, perform this task in privileged mode:
Step 1
Disable PortFast on a switch port.
set spantree portfast mod_num/port_num disable
Step 2
Verify the PortFast setting.
show spantree mod_num/port_num
This example shows how to disable PortFast on port 1 of module 4:
Console> (enable) set spantree portfast 4/1 disableSpantree port 4/1 fast start disabled.Console> (enable)To reset PortFast on a switch or trunk port to its default settings, perform this task in privileged mode:
Step 1
Reset PortFast to default setting on a switch port.
set spantree portfast mod_num/port_num default
Step 2
Verify the PortFast setting.
show spantree mod_num/port_num
This example shows how to disable PortFast on port 1 of module 4:
Console> (enable) set spantree portfast 4/1 defaultSpantree port 4/1 fast start set to default.Console> (enable) show spantree portfast 4/1Portfast:defaultPortfast BPDU guard is disabled.Portfast BPDU filter is disabled.Console> (enable)Resetting PortFast
To reset PortFast on a switch or trunk port to its default settings, perform this task in privileged mode:
Step 1
Reset PortFast to its default settings on a switch port.
set spantree portfast mod_num/port_num default
Step 2
Verify the PortFast setting.
show spantree mod_num/port_num
This example shows how to reset PortFast to its default settings on port 1 of module 4:
Console> (enable) set spantree portfast 4/1 defaultSpantree port 4/1 fast start set to default.Console> (enable) show spantree portfast 4/1Portfast:defaultPortfast BPDU guard is disabled.Portfast BPDU filter is disabled.Console> (enable)Understanding How PortFast BPDU Guard Works
To prevent loops from occurring in a network, the PortFast mode is supported only on nontrunking access ports because these ports typically do not transmit or receive BPDUs. The most secure implementation of PortFast is to enable it only on ports that connect end stations to switches. Because PortFast can be enabled on nontrunking ports connecting two switches, spanning tree loops can occur because BPDUs are still being transmitted and received on those ports.
The PortFast BPDU guard feature prevents loops by moving a nontrunking port into an errdisable state when a BPDU is received on that port. When the BPDU guard feature is enabled on the switch, spanning tree shuts down PortFast-configured interfaces that receive BPDUs, instead of putting them into the spanning tree blocking state. In a valid configuration, PortFast-configured interfaces do not receive BPDUs. If a PortFast-configured interface receives a BPDU, an invalid configuration exists, such as connection of an unauthorized device. The BPDU guard feature provides a secure response to invalid configurations because the administrator must manually put the interface back in service.
Note
When enabled on the switch, spanning tree applies the BPDU guard feature to all PortFast-configured interfaces.
Configuring PortFast BPDU Guard
These sections describe how to configure PortFast BPDU guard on the switch:
•
Disabling PortFast BPDU Guard
Enabling PortFast BPDU Guard
The PortFast feature is configured on an individual port and the PortFast BPDU guard option is configured either globally or on a per-port basis.
When you disable PortFast on a port, PortFast BPDU guard becomes inactive. The port configuration overrides the global configuration unless the port configuration is set to default. If the port configuration is set to default, the global configuration is checked. If the port configuration is enabled, the port configuration is used and the global configuration is not.
To enable and verify PortFast BPDU guard on a nontrunking switch port, perform this task in privileged mode:
Note
For additional PVST+ information, see "Configuring Spanning Tree."
This example shows how to enable PortFast BPDU guard on module 6 port 1, and verify the configuration in the Per VLAN Spanning Tree + (PVST+) mode:
Console> (enable) set spantree portfast bpdu-guard 6/1 enableSpantree port 6/1 bpdu guard enabled.Console> (enable)Console> (enable) show spantree summaryRoot switch for vlans: none.Portfast bpdu-guard enabled for bridge.Uplinkfast disabled for bridge.Backbonefast disabled for bridge.Vlan Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------1 0 0 0 4 42 0 0 0 4 43 0 0 0 4 44 0 0 0 4 45 0 0 0 4 46 0 0 0 4 410 0 0 0 4 420 0 0 0 4 450 0 0 0 4 4100 0 0 0 4 4152 0 0 0 4 4200 0 0 0 5 5300 0 0 0 4 4400 0 0 0 4 4500 0 0 0 4 4521 0 0 0 4 4524 0 0 0 4 4570 0 0 0 4 4801 0 0 0 0 0802 0 0 0 0 0850 0 0 0 4 4917 0 0 0 4 4999 0 0 0 4 41003 0 0 0 0 01005 0 0 0 0 0Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------Total 0 0 0 85 85Console> (enable)Disabling PortFast BPDU Guard
To disable PortFast BPDU guard, perform this task in privileged mode:
This example shows how to disable PortFast BPDU guard on the switch and verify the configuration:
Console> (enable) set spantree portfast bpdu-guard disableSpantree portfast bpdu-guard disabled on this switch.Console> (enable) show spantree summarySummary of connected spanning tree ports by vlanPortfast bpdu-guard disabled for bridge.
Uplinkfast disabled for bridge.Backbonefast disabled for bridge.Vlan Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------1 0 0 0 4 42 0 0 0 4 43 0 0 0 4 44 0 0 0 4 45 0 0 0 4 46 0 0 0 4 410 0 0 0 4 420 0 0 0 4 450 0 0 0 4 4100 0 0 0 4 4152 0 0 0 4 4200 0 0 0 5 5300 0 0 0 4 4400 0 0 0 4 4500 0 0 0 4 4521 0 0 0 4 4524 0 0 0 4 4570 0 0 0 4 4801 0 0 0 0 0802 0 0 0 0 0850 0 0 0 4 4917 0 0 0 4 4999 0 0 0 4 41003 0 0 0 0 01005 0 0 0 0 0Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------Total 0 0 0 85 85Console> (enable)Understanding How PortFast BPDU Filtering Works
BPDU filtering allows you to avoid transmitting BPDUs on PortFast-enabled ports that are connected to an end system. When you enable PortFast on the switch, spanning tree places ports in the forwarding state immediately, instead of going through the listening, learning, and forwarding states.
By default, spanning tree sends BPDUs from all ports regardless of whether PortFast is enabled. BDPU filtering is on a per-switch basis; after you enable BPDU filtering, it applies to all PortFast-enabled ports on the switch.
Configuring PortFast BPDU Filtering
These sections describe how to configure PortFast BPDU filter on the switch:
•
Enabling PortFast BPDU Filtering
•
Disabling PortFast BPDU Filter
Enabling PortFast BPDU Filtering
Note
Although you can configure PortFast on an individual port, you configure the PortFast BPDU filter option globally. When you disable PortFast on a port, PortFast BPDU filter becomes inactive for that port.
To enable PortFast BPDU filtering, perform this task in privileged mode:
Note
For additional PVST+ information, see "Configuring Spanning Tree."
By default, BPDU filter is set for each port. This example shows how to enable PortFast BPDU filtering on the port and verify the configuration in PVST+ mode:
Console> (enable) set spantree portfast bpdu-filter 6/1 enableWarning:Ports enabled with bpdu filter will not send BPDUs and drop allreceived BPDUs. You may cause loops in the bridged network if you misusethis feature.Console> (enable) show spantree summaryRoot switch for vlans: none.Portfast bpdu-filter enabled for bridge.Uplinkfast disabled for bridge.Backbonefast disabled for bridge.Vlan Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------1 0 0 0 4 42 0 0 0 4 43 0 0 0 4 44 0 0 0 4 45 0 0 0 4 46 0 0 0 4 4...850 0 0 0 4 4917 0 0 0 4 4999 0 0 0 4 41003 0 0 0 0 01005 0 0 0 0 0Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------Total 0 0 0 85 85Console> (enable)Disabling PortFast BPDU Filter
To disable PortFast BPDU filter on a switch, perform this task in privileged mode:
Step 1
Disable PortFast BPDU filter on the switch.
set spantree portfast bpdu-filter disable
Step 2
Verify the PortFast BPDU filter setting.
show spantree summary
This example shows how to disable PortFast BPDU filter on the switch and verify the configuration:
Console> (enable) set spantree portfast bpdu-filter disableSpantree portfast bpdu-filter disabled on this switch.Console> (enable) show spantree summarySummary of connected spanning tree ports by vlanPortfast bpdu-filter disabled for bridge.Uplinkfast disabled for bridge.Backbonefast disabled for bridge.Vlan Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------1 0 0 0 4 42 0 0 0 4 43 0 0 0 4 44 0 0 0 4 45 0 0 0 4 46 0 0 0 4 410 0 0 0 4 420 0 0 0 4 450 0 0 0 4 4100 0 0 0 4 4152 0 0 0 4 4200 0 0 0 5 5300 0 0 0 4 4400 0 0 0 4 4500 0 0 0 4 4521 0 0 0 4 4524 0 0 0 4 4570 0 0 0 4 4801 0 0 0 0 0802 0 0 0 0 0850 0 0 0 4 4917 0 0 0 4 4999 0 0 0 4 41003 0 0 0 0 01005 0 0 0 0 0Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------Total 0 0 0 85 85Console> (enable)Understanding How UplinkFast Works
UplinkFast provides fast convergence using uplink groups in the network access layer after a spanning tree topology change. An uplink group is a set of ports (per VLAN), only one of which is forwarding at any given time. Specifically, an uplink group consists of the root port (which is forwarding) and a set of blocked ports (not including self-looped ports). The uplink group provides an alternate path in case the currently forwarding link fails.
Note
UplinkFast is most useful in wiring-closet switches with a limited number of active VLANs. This enhancement might not be useful for other types of applications and should not be enabled on backbone or distribution layer switches.
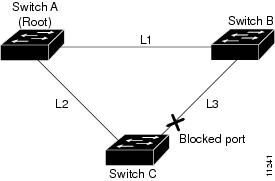
Figure 8-1 shows an example UplinkFast network topology. Switch A, the root switch, is connected directly to Switch B over link L1 and to Switch C over link L2. The port on Switch C that is connected to Switch B over link L3 is in blocking state.
Figure 8-1 UplinkFast Example Before Direct Link Failure
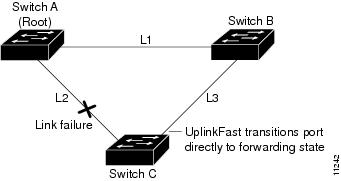
If Switch C detects a link failure on the currently active link L2 (a direct link failure), UplinkFast unblocks the blocked port on Switch C and transitions it to the forwarding state immediately, without transitioning the port through the listening and learning states (as shown in Figure 8-2). This switchover takes approximately one to five seconds.
Figure 8-2 Example of UplinkFast after Direct Link Failure
As soon as the switch transitions the alternate port to the forwarding state, the switch begins transmitting dummy multicast frames on that port, one for each entry in the local EARL table (except those entries associated with the failed root port). By default, approximately 15 dummy multicast frames are transmitted per 100 ms.
Each dummy multicast frame uses the station address in the EARL table entry as its source MAC address and a dummy multicast address (01-00-0C-CD-CD-CD) as the destination MAC address.
Switches receiving these dummy multicast frames immediately update their EARL table entries for each source MAC address to use the new port, allowing the switches to begin using the new path almost immediately.
If connectivity on the original root port is restored, the switch waits for a period equal to twice the forward delay time plus five seconds before transitioning the port to the forwarding state in order to allow the neighbor port enough time to transition through the listening and learning states to the forwarding state.
Configuring UplinkFast
These sections describe how to configure the UplinkFast feature on the switch:
Enabling UplinkFast
When you enable UplinkFast on the switch, UplinkFast processing is enabled and the spanning tree bridge priority for all VLANs is set to 49,152, making it unlikely that the switch will become the root switch. In addition, the spanning tree port cost and port-VLAN cost of all ports on the switch is increased by 3000.
The station_update_rate value in the UplinkFast command represents the number of dummy multicast packets transmitted per 100 ms (the default is 15 packets per 100 ms) in the event of a direct link failure.
Use the all-protocols on keywords on switches that have UplinkFast enabled but do not have protocol filtering enabled, and that are connected to upstream switches in the network that have protocol filtering enabled. The all-protocols on keywords cause the switch to generate multicasts for each protocol-filtering group.
On switches with both UplinkFast and protocol filtering enabled, or if no other switches have protocol filtering enabled, you do not need to use the all-protocols on keywords.
Note
When you enable UplinkFast, it affects all VLANs on the switch. You cannot configure UplinkFast on a per-VLAN basis.
To enable UplinkFast, perform this task in privileged mode:
This example shows how to enable UplinkFast with a station-update rate of 40 packets per 100 ms and how to verify that UplinkFast is enabled:
Console> (enable) set spantree uplinkfast enable rate 40VLANs 1-1005 bridge priority set to 49152.The port cost and portvlancost of all ports set to above 3000.Station update rate set to 40 packets/100ms.uplinkfast all-protocols field set to off.uplinkfast enabled for bridge.Console> (enable) show spantree uplinkfastStation update rate set to 40 packets/100ms.uplinkfast all-protocols field set to off.VLAN port list-----------------------------------------------1 1/1(fwd),1/2100 1/2(fwd)521 1/1(fwd),1/2522 1/1(fwd),1/2523 1/1(fwd),1/2524 1/1(fwd),1/2Console> (enable)This example shows how to display the UplinkFast feature settings for all VLANs:
Console> show spantree uplinkfastStation update rate set to 15 packets/100ms.uplinkfast all-protocols field set to off.VLAN port list------------------------------------------------1-20 1/1(fwd),1/2-1/521-50 1/9(fwd), 1/6-1/8, 1/10-1/1251-100 2/1(fwd), 2/12Console>Disabling UplinkFast
To disable UplinkFast and restore the default spanning tree bridge priority, port cost, and port-VLAN cost values to their default values, enter the clear spantree uplinkfast command.
CautionUse caution when entering the clear spantree uplinkfast command. This command restores the port-VLAN costs on all ports to the default minus one (18) and the port cost to the default value (19). If you have configured per-VLAN load sharing on redundant trunk links, the load-sharing configuration can be affected by this command.
You can disable only spanning tree UplinkFast processing on the switch using the set spantree uplinkfast disable command. This command does not affect the bridge priority, port cost, and port-VLAN cost values on the switch.
Note
When you disable UplinkFast, it affects all VLANs on the switch. You cannot disable UplinkFast on a per-VLAN basis.
To disable UplinkFast on a switch, perform this task in privileged mode:
This example shows how to disable UplinkFast on the switch and restore the default bridge priority, port cost, and port-VLAN cost values:
Console> (enable) clear spantree uplinkfastThis command will cause all portcosts, portvlancosts, and thebridge priority on all vlans to be set to default.Do you want to continue (y/n) [n]? yVLANs 1-1005 bridge priority set to 32768.The port cost of all bridge ports set to default value.The portvlancost of all bridge ports set to default value.uplinkfast all-protocols field set to off.uplinkfast disabled for bridge.Console> (enable) show spantree uplinkfastuplinkfast disabled for bridge.Console> (enable)Understanding How BackboneFast Works
BackboneFast provides fast convergence in the network backbone after a spanning tree topology change occurs. A switch detects an indirect link failure (the failure of a link to which the switch is not directly connected) when the switch receives inferior BPDUs from its designated bridge on its root port or blocked ports. These inferior BPDUs indicate that the designated bridge has lost its connection to the root bridge. An inferior BPDU identifies a single switch as both the root bridge and the designated bridge. Under normal spanning tree rules, the switch ignores inferior BPDUs for the configured maximum aging time (specified by the set spantree maxage command).
The switch tries to determine if it has an alternate path to the root bridge. If the inferior BPDU arrives on a blocked port, the root port and other blocked ports on the switch become alternate paths to the root bridge. If the inferior BPDU arrives on the root port, all blocked ports become alternate paths to the root bridge. If the inferior BPDU arrives on the root port and there are no blocked ports, the switch assumes that it has lost connectivity to the root bridge, causes the maximum aging time on the root to expire, and becomes the root switch according to normal spanning tree rules.
If the switch has alternate paths to the root bridge, it uses these alternate paths to transmit a new kind of protocol data unit (PDU) called the Root Link Query PDU out all alternate paths to the root bridge. If the switch determines that it still has an alternate path to the root, it causes the maximum aging time on the ports on which it received the inferior BPDU to expire. If all the alternate paths to the root bridge indicate that the switch has lost connectivity to the root bridge, the switch causes the maximum aging times on the ports on which it received an inferior BPDU to expire. If one or more alternate paths can still connect to the root bridge, the switch makes all ports on which it received an inferior BPDU its designated ports and moves them out of the blocking state (if they were in the blocking state), through the listening and learning states, and into the forwarding state.
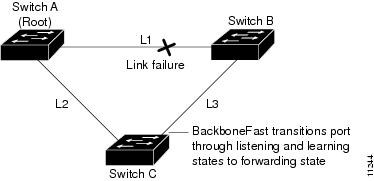
Figure 8-3 shows an example of a BackboneFast network topology. Switch A, the root switch, connects directly to Switch B over link L1 and to Switch C over link L2. The port on Switch C that connects directly to Switch B over link L3 is in the blocking state.
Figure 8-3 Example of BackboneFast before Indirect Link Failure
If link L1 fails, Switch C detects this failure as an indirect failure, since it is not connected directly to link L1. Switch B no longer has a path to the root switch. BackboneFast allows the blocked port on Switch C to move immediately to the listening state without waiting for the maximum aging time for the port to expire. BackboneFast then transitions the port on Switch C to the forwarding state, providing a path from Switch B to Switch A. This switchover takes approximately 30 seconds. Figure 8-4 shows how BackboneFast reconfigures the topology to account for the failure of link L1.
Figure 8-4 Example of BackboneFast after Indirect Link Failure
If a new switch is introduced into a shared-medium topology, BackboneFast is not activated. Figure 8-5 shows a shared-medium topology in which a new switch is added. The new switch begins sending inferior BPDUs, which indicate that it is the root switch. However, the other switches ignore these inferior BPDUs and the new switch learns that Switch B is the designated bridge to Switch A, the root switch.
Figure 8-5 Adding a Switch in a Shared-Medium Topology
Configuring BackboneFast
These sections describe how to configure the BackboneFast feature:
•
Displaying BackboneFast Statistics
Enabling BackboneFast
Note
You must enable BackboneFast on all switches in the network. BackboneFast is not supported on Token Ring VLANs. This feature is supported for use with third-party switches.
To enable BackboneFast on the switch, perform this task in privileged mode:
Step 1
Enable BackboneFast on the switch.
set spantree backbonefast enable
Step 2
Verify that BackboneFast is enabled.
show spantree backbonefast
This example shows how to enable BackboneFast on the switch and how to verify the configuration:
Console> (enable) set spantree backbonefast enableBackbonefast enabled for all VLANsConsole> (enable) show spantree backbonefastBackbonefast is enabled.Console> (enable)Displaying BackboneFast Statistics
To display BackboneFast statistics, perform this task in privileged mode:
This example shows how to display BackboneFast statistics:
Console> (enable) show spantree summarySummary of connected spanning tree ports by vlanUplinkfast disabled for bridge.Backbonefast enabled for bridge.Vlan Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------1 0 0 0 1 1Blocking Listening Learning Forwarding STP Active----- -------- --------- -------- ---------- ----------Total 0 0 0 1 1BackboneFast statistics-----------------------Number of inferior BPDUs received (all VLANs) : 0Number of RLQ req PDUs received (all VLANs) : 0Number of RLQ res PDUs received (all VLANs) : 0Number of RLQ req PDUs transmitted (all VLANs) : 0Number of RLQ res PDUs transmitted (all VLANs) : 0Console> (enable)Disabling BackboneFast
To disable BackboneFast on the switch, perform this task in privileged mode:
Step 1
Disable BackboneFast on the switch.
set spantree backbonefast disable
Step 2
Verify that BackboneFast is disabled.
show spantree backbonefast
This example shows how to disable BackboneFast on the switch and how to verify the configuration:
Console> (enable) set spantree backbonefast disableBackbonefast enabled for all VLANsConsole> (enable) show spantree backbonefastBackbonefast is disabled.Console> (enable)Understanding How Loop Guard Works
Unidirectional link failures may cause a root port or alternate port to become designated as root if BPDUs are absent. Some software failures may introduce temporary loops in the network. The loop guard feature checks if a root port or an alternate root port receives BPDUs. If the port is receiving BPDUs, the loop guard feature puts the port into an inconsistent state until it starts receiving BPDUs again. Loop guard isolates the failure and lets spanning tree converge to a stable topology without the failed link or bridge.
You can enable loop guard on a per-port basis with the set spantree guard loop command.
Note
Provided that you are in MST mode, you can set all the ports on a switch with the set spantree global-defaults loop-guard command.
When you enable loop guard, it is automatically applied to all of the active instances or VLANs to which that port belongs. When you disable loop guard, it is disabled for the specified ports. Disabling loop guard moves all loop-inconsistent ports to the listening state.
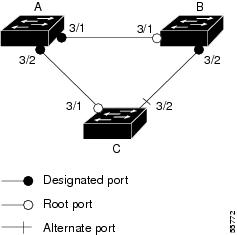
If you enable loop guard on a channel and the first link becomes unidirectional, loop guard blocks the entire channel until the affected port is removed from the channel. Figure 8-6 shows loop guard in a triangle switch configuration.
Figure 8-6 Triangle Switch Configuration with Loop Guard
Figure 8-6 illustrates the following configuration:
•
Switches A and B are distribution switches.
•
Switch C is an access switch.
•
Loop guard is enabled on ports 3/1 and 3/2 on Switches A, B, and C.
Use loop guard only in topologies where there are blocked ports. Topologies that have no blocked ports, which are loop free, do not need to enable this feature. Enabling loop guard on a root switch has no effect but provides protection when a root switch becomes a nonroot switch.
Follow these guidelines when using loop guard:
•
Do not enable loop guard on PortFast-enabled or dynamic VLAN ports.
•
Do not enable PortFast on loop guard-enabled ports.
•
Do not enable loop guard if root guard is enabled.
•
Do not enable loop guard on ports that are connected to a shared link.
Note
We recommend that you enable loop guard on root ports and alternate root ports on access switches.
Loop guard interacts with other features as follows:
•
Loop guard does not affect the functionality of UplinkFast or BackboneFast.
•
Root guard forces a port to always be designated as the root port. Loop guard is effective only if the port is a root port or an alternate port. Do not enable loop guard and root guard on a port at the same time.
•
PortFast transitions a port into a forwarding state immediately when a link is established. Because a PortFast-enabled port will not be a root port or alternate port, loop guard and PortFast cannot be configured on the same port. Assigning dynamic VLAN membership for the port requires that the port is PortFast enabled. Do not configure a loop guard-enabled port with dynamic VLAN membership.
•
If your network has a type-inconsistent port or a PVID-inconsistent port, all BPDUs are dropped until the misconfiguration is corrected. The port transitions out of the inconsistent state after the message age expires. Loop guard ignores the message age expiration on type-inconsistent ports and PVID-inconsistent ports. If the port is already blocked by loop guard, misconfigured BPDUs received on the port make loop guard recover, but the port is moved into the type-inconsistent state or PVID-inconsistent state.
•
In high-availability switch configurations, if a port is put into the blocked state by loop guard, it remains blocked even after switchover to the redundant supervisor engine. The newly activated supervisor engine recovers the port only after receiving a BPDU on that port.
•
Loop guard uses the ports known to spanning tree. Loop guard can take advantage of logical ports provided by the Port Aggregation Protocol (PAgP). However, to form a channel, all the physical ports grouped in the channel must have compatible configurations. PAgP enforces uniform configurations of root guard or loop guard on all the physical ports to form a channel.
These caveats apply to loop guard:
–
Spanning tree always chooses the first operational port in the channel to send the BPDUs. If that link becomes unidirectional, loop guard blocks the channel, even if other links in the channel are functioning properly.
–
If a set of ports that are already blocked by loop guard are grouped together to form a channel, spanning tree loses all the state information for those ports and the new channel port may obtain the forwarding state with a designated role.
–
If a channel is blocked by loop guard and the channel breaks, spanning tree loses all the state information. The individual physical ports may obtain the forwarding state with the designated role, even if one or more of the links that formed the channel are unidirectional.
•
You can enable UniDirectional Link Detection (UDLD) to help isolate the link failure. A loop may occur until UDLD detects the failure, but loop guard will not be able to detect it.
•
Loop guard has no effect on a disabled spanning tree instance or a VLAN.
Configuring Loop Guard
The next two sections describe how to configure loop guard.
Enabling Loop Guard
Use the set spantree guard command to enable the spanning tree loop guard feature on a per-port basis. To set all the ports on the switch, use the set spantree mst global-defaults loop-guard command.
To enable loop guard on an individual port, perform this task in privileged mode:
This example shows how to enable loop guard on port 5/1:
Console> (enable) set spantree guard loop 5/1Rootguard is enabled on port 5/1, enabling loopguard will disable rootguard onthis port.Do you want to continue (y/n) [n]? yLoopguard on port 5/1 is enabled.Console> (enable)This example shows how to enable loop guard on all the ports on a switch:
Console> (enable) set spantree mst global-defaults loop-guard enableSpantree global loop-guard state enabled on this switch.Disabling Loop Guard
Use the set spantree guard command to disable the spanning tree loop guard feature on a per-port basis. To disable loop guard on all the ports on a switch, use the set spantree mst global-defaults loop-guard command.
To disable loop guard on the switch, perform this task in privileged mode:
This example shows how to disable loop guard on port 5/1:
Console> (enable) set spantree guard none 5/1Rootguard is disabled on port 5/1, disabling loopguard will disable rootguard onthis port.Do you want to continue (y/n) [n]? yLoopguard on port 5/1 is disabled.Console> (enable)This example shows how to disable loop guard on all the ports on a switch:
Console> (enable) set spantree mst global-defaults loop-guard disableSpantree global loop-guard state disabled on this switch.

 Feedback
Feedback