Feedback Feedback
|
Table Of Contents
Cisco Clean Access Installation, Release 3.5
Clean Access Server (CAS) Quick Installation
Clean Access Server Installation Procedure
Clean Access Manager (CAM) Quick Installation
Clean Access Manager Installation Procedure
Install Cisco Clean Access FlexLM License and Access Web Console
Manage the Clean Access Server
Create User Role and Local User (Test)
Configure Traffic Policies for User Roles
Require Use of Clean Access Agent
Make Agent Auto-Upgrade Mandatory
Configure Authentication Servers
Quick Start Guide
Cisco Clean Access Installation, Release 3.5
1 Introduction
This quick start guide is a brief introduction to the major features of the Cisco Clean Access Manager (CAM), Clean Access Server (CAS), web administration console, and Clean Access Agent using local authentication. It is intended to illustrate the minimum steps required to install and configure the CAM and CAS in order to test as Clean Access Agent client on the system. For comprehensive information, including details on configuring network scanning plugins and external authentication servers, refer to the Cisco Clean Access Manager Installation and Administration Guide and Cisco Clean Access Server Installation and Administration Guide, available from http://www.cisco.com/univercd/cc/td/doc/product/vpn/ciscosec/cca/cca35/index.htm
Note that the software installation procedure for the Clean Access Server is the same whether the CAS is in-band (IB) or out-of-band (OOB).
2 In-Band (IB) Deployment
Except where noted, this guide describes basic configuration required for all Cisco Clean Access systems, whether deployment is in-band or out-of-band. Out-of-band deployment requires additional configuration as described below.
3 Out-of-Band (OOB) Deployment
For high-throughput or highly-routed environments, Cisco Clean Access Out-of-Band deployment allows client machines to pass through the Clean Access network only for authentication and certification before being connected directly to the trusted network. Client traffic is considered to be in-band (in the Clean Access network) during authentication and certification, and out-of-band once successfully on the trusted network. With OOB deployment, you can add switches to the Clean Access Manager's domain and control particular switch ports using SNMP. To deploy OOB:
•
Install the latest 3.5.x release of Cisco Clean Access software on your CAM and CAS(es).
•
Obtain an OOB license for your CAM and CAS(es). The Clean Access Server itself is either In-Band (IB) or Out-of-Band (OOB). A Clean Access Manager that is license-enabled for OOB can control both IB and OOB Clean Access Servers.
•
Use supported switch models and IOS/CatOS versions for switches you will control through your CAM.
•
Configure your switches, and configure the Switch Management module (license-enabled) in the Clean Access Manager web admin console.
•
Have clients be physically connected to the ports of controlled switches.
For complete configuration information, see "Switch Management and Cisco Clean Access Out-of-Band (OOB)" in the Cisco Clean Access Manager Installation and Administration Guide.
4 Clean Access Server (CAS) Quick Installation
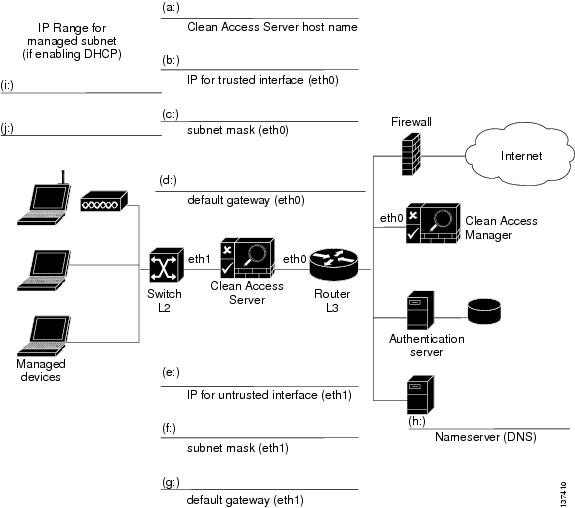
The following worksheet shows the configuration information needed to install the Clean Access Server. Use this worksheet to gather the information specific to your environment. The instructions which follow correlate the information from the worksheet fields with the installation script, clarifying what information is required at each step of the installation.
Figure 1 CAS Installation Worksheet
IP Addressing Considerations
•
eth0 and eth1 generally correlate to the first two network cards—NIC 1 and NIC 2—on most types of server hardware.
•
If using DHCP relay, make sure the DHCP server has a route back to the managed subnets.
•
Real-IP:
–
The trusted (eth0) and untrusted (eth1) interfaces of the CAS must be on different subnets.
–
On the L3 router in your network, you must add a static route to/from the managed subnets to the trusted interface (eth0) of the CAS.
•
NAT Gateway Mode:
–
The trusted (eth0) and untrusted (eth1) interfaces of the CAS must be on different subnets.
Note
NAT Gateway mode is primarily intended for testing purposes and is not recommended for production deployment.
•
Virtual Gateway Mode:
–
The trusted (eth0) and untrusted interfaces (eth1) of the CAS can use the same IP address.
–
The CAM and CAS must be on different subnets.
–
The CAS should be configured for DHCP forwarding.
–
For OOB VGW, the CAS interfaces must be on a separate VLAN from the CAM.
–
For OOB VGW, the untrusted interface of the CAS should not be connected to the switch until VLAN mapping has been configured correctly under Device Management > CCA Servers > IPaddress > Advanced > VLAN Mapping. See the Clean Access Server Installation and Administration Guide for details.
Clean Access Server Installation Procedure
Once you have the worksheet information, use the following steps to install the software for the Clean Access Server.
Connect to the target machine:
Step 1
If you have not done so already, prepare the target installation machine by:
a.
Connecting the target machine to the network, and
b.
Connecting a monitor and keyboard directly to the target machine, or
c.
Connecting a serial cable from your workstation to the target machine, and opening up a serial connection using terminal emulation software such as HyperTerminal.
CautionBe sure to install the Cisco Clean Access software on a dedicated machine, since installing the software reformats and partitions the disk of the target machine. Any existing data or applications on the machine will be lost.
Step 2
Boot the target machine with the installation CD-ROM in the CD drive. When the machine starts up, the installation program starts automatically.
Step 3
At the "boot:" prompt:
a.
Press the Enter key if your monitor and keyboard are directly connected to the machine, or
b.
Type serial in the terminal emulation console and press the Enter key if your workstation is serially connected to the target machine.
The Clean Access Server package installation then executes (this takes a few minutes). When completed, the welcome screen for the Clean Access Server quick configuration utility appears.
Configure the trusted interface (eth0):
Step 4
The first prompt asks you for the IP address of the trusted (wired) interface eth0. This is the interface to the trusted network. Follow the prompts, and enter the value from field (b) from the CAS Installation Worksheet.
Step 5
Next enter the subnet mask of the trusted interface address, or accept the default 255.255.255.0. This is the value from field (c).
Step 6
Enter the address of the default gateway on the trusted network from field (d) of the worksheet. This is typically the IP address of the router between the Clean Access Server subnet and Clean Access Manager subnet.
Step 7
Enter N to accept the default VLAN ID passthrough behavior (in which VLAN IDs are stripped at the interface) or Y (to have VLAN IDs pass through the interface). VLAN ID passthrough is typically not needed for most implementations, unless the ID is used by an external DHCP server for IP pool assignment decisions.
Step 8
Enter N to accept the default management VLAN tagging behavior, in which management VLAN tagging is disabled, or enter Y and specify the VLAN ID to use. In most cases, VLAN ID tagging is not needed.
Configure the untrusted interface (eth1):
Step 9
For the IP address for the untrusted interface eth1, enter the value of field (e). This is the interface to the untrusted (managed) network.
Step 10
Enter the subnet mask for the untrusted interface (eth1) from field (f).
Step 11
For the default gateway address of the untrusted (managed) network, enter the value from field (g).
Step 12
Enter N to accept the default VLAN ID passthrough behavior (in which VLAN IDs are stripped at the interface) or Y (to have IDs pass through the interface). In most cases, the default behavior can be chosen.
Step 13
Enter N to accept the default management VLAN tagging behavior, in which management VLAN tagging is disabled, or enter Y and specify the VLAN ID to use.
Configure nameserver (DNS server):
Step 14
For the hostname, enter and confirm the name of the Clean Access Server from field (a).
Step 15
For the nameserver, enter and confirm the IP address of the DNS server from field (h).
Configure shared secret:
Step 16
The elements of Cisco Clean Access use a shared secret as a password to authenticate each other. The shared secret must be the same for every Clean Access Manager and Clean Access Server in the deployment. The default value is cisco123. Type and confirm the shared secret at the next prompt.
Configure date and time properties:
Step 17
Configure and confirm the time zone, date and time for the server by following the onscreen instructions. For example, California timezone values are: 2-Americas, 45-United States, 15-Pacific.
Generate temporary SSL certificate:
Step 18
For the Clean Access Server SSL certificate, enter Y to generate a temporary certificate. You must generate a temporary SSL certificate at this time. Later, you can replace the temporary certificate with a CA-signed certificate. For the certificate values:
a.
Use the value from field (b) for the fully qualified domain name or IP address.
b.
Enter values as instructed by the configuration script for the remaining certificate settings.
c.
When finished, press the Enter key to generate the certificate with the values you entered or type N to start over.
Note
This generates a temporary security certificate. A temporary certificate requires clients to explicitly accept the certificate when the connection is initiated. You can replace the temporary certificate with a CA-signed certificate for the Clean Access Server later in the Clean Access Manager web admin console.
Configure passwords:
Step 19
Now enter and confirm passwords for the Clean Access Server. Note that cisco123 is the default password for the following accounts:
a.
The root user account on the Linux operating system (SSH users).
b.
The admin user account to directly access the web console of the CAS. Each individual CAS has a web console for limited Clean Access Server-specific settings that is primarily used to configure High Availability.
Step 20
Configuration is now complete. Press the Enter key to reboot the CAS and complete the installation.
Testing the Installation
To test the installation:
•
Ping the eth0 interface address from a command line. If working properly, the interface should respond to the ping.
•
If the CAS is not responding, try connecting to the CAS using SSH (Secure Shell). Connect with the default username and password combination root/cisco123. Once connected, try pinging the gateway and/or an external website from the CAS to see if the CAS can reach the external network.
If both tests fail, make sure that you have configured the IP address correctly and that the other network settings are correct.
Note
You must generate the SSL certificate or you will not be able to access your CAS as an end user. Before deploying in a live environment, acquire a trusted certificate for the CAS from a Certification Authority to replace the temporary certificate.
If after installation you need to reset the initial configuration settings for the Clean Access Server, connect to the CAS machine directly or through SSH and use the CLI command service perfigo config. See Configuration Script for details.
5 Clean Access Manager (CAM) Quick Installation
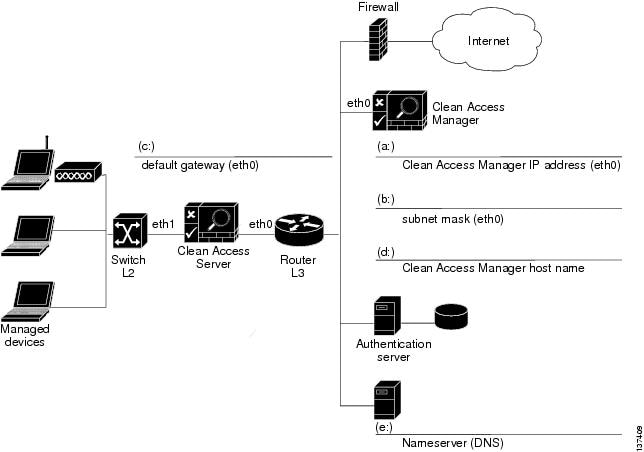
The following worksheet shows the configuration information needed to install the Clean Access Manager. Fill in the fields as appropriate for your environment. The instructions which follow correlate worksheet field information to the installation script.
Figure 2 CAM Installation Worksheet
Clean Access Manager Installation Procedure
Once you have the worksheet information, use the following steps to install the software for the Clean Access Manager.
Connect to the target machine:
Step 1
If you have not done so already, prepare the target machine by:
a.
Connecting the target machine to the network, and
b.
Connecting a monitor and keyboard directly to the target machine, or
c.
Connecting a serial cable from your workstation to the target machine, and opening up a serial connection using terminal emulation software such as HyperTerminal.
CautionBe sure to install the Cisco Clean Access software on a dedicated machine, since installing the software reformats and partitions the disk of the target machine. Any existing data or applications on the machine will be lost.
Step 2
Boot the target machine with the installation CD-ROM in the CD drive. When the machine starts up, the installation program starts automatically.
Step 3
At the "boot:" prompt:
a.
Type serial in the terminal emulation console and press the Enter key if your workstation is serially connected to the target machine.
b.
Press the Enter key if your monitor and keyboard are directly connected to the machine.
Step 4
The Clean Access Manager package installation then executes (this takes a few minutes). When completed, the welcome screen for the Clean Access Manager quick configuration utility appears.
Configure the trusted interface (eth0):
Step 5
Enter the IP address of the eth0 interface from field (a) of the CAM Installation Worksheet.
Note
If deploying a CAS in Virtual Gateway mode, the CAM address must be on a different subnet than the trusted interface (eth0) of the CAS.
Step 6
For the subnet mask of the eth0 interface, enter the value of field (b).
Step 7
For the address of the default gateway, use the value of field (c). This is typically the IP address of the router between the Clean Access Server subnet and Clean Access Manager subnet.
Configure nameserver (DNS server):
Step 8
For the hostname, enter and confirm the value of field (d).
Step 9
Specify your DNS server address from field (e).
Configure shared secret:
Step 10
The Cisco Clean Access elements use a shared secret as a password to authenticate each other. Type the same secret set earlier for the Clean Access Server. The default value is cisco123.
Configure date and time properties:
Step 11
Configure and confirm the time zone, date and time of the CAM as instructed by the configuration utility. These values should be the same as those configured for the Clean Access Server.
Generate temporary SSL certificate:
Step 12
Next generate a temporary SSL certificate. This certificate enables secure access to the web administration console.
a.
Type the Clean Access Manager eth0 IP address from field (a).
b.
For the remaining certificate settings, enter values as instructed by the script.
c.
When finished, press the Enter key to generate the certificate with the values you entered or type N to start over.
Note
This generates a temporary security certificate. For temporary certificates, the client must explicitly accept the certificate when a connection is initiated. You can replace the temporary certificate with a CA-signed certificate later from the Clean Access Manager web admin console.
Configure password:
Step 13
Now configure the password for the root user of the installed Linux operating system for the Clean Access Manager. The default password is cisco123. The root user account is used to access the system over a serial connection or through SSH.
Note
There is already a default username/password of admin/cisco123 for the Clean Access Manager web administration console, so you will not see a prompt for this during installation. The CAM web console is the primary interface for administering and monitoring the Cisco Clean Access deployment. You can change the password for default web console user admin or create additional admin users/passwords through the web console itself once it is accessed.
Step 14
Configuration is now complete. The Clean Access Manager database will initialize.
Step 15
Press the Enter key to reboot the server and complete the Clean Access Manager installation.
Testing the Installation
To test the initial installation, try pinging the Clean Access Manager interface from a command line. If it does not respond, make sure that the CAM machine is properly connected to the network and running.
If necessary, make sure that you have correctly configured network settings at installation by accessing the configuration files directly. For more information, see the Clean Access Manager Installation and Administration Guide.
Configuration Script
If after installation you need to reset the initial configuration settings for either the Clean Access Server or the Clean Access Manager, you can connect to the applicable machine and use the CLI command service perfigo config as described below.
Step 1
While connected to the target machine (either the CAS or CAM) directly, through a serial connection, or through SSH, login as root.
Step 2
Run the following command:
service perfigo configStep 3
Accept the default values or provide new ones for all prompts.
Step 4
When configuration is complete, run the following command:
service perfigo reboot
6 Install Cisco Clean Access FlexLM License and Access Web Console
Use the following steps to obtain and install your FlexLM license files, and access the Clean Access Manager web administration console. For details on evaluation licenses, see Evaluation Licenses. Note that you must use FlexLM licensing to enable Cisco® Clean Access Out-of-Band (see Out-of-Band (OOB) Deployment for further details).
Step 1
With FlexLM licensing, you will receive a Product Authorization Key (PAK) for each software CD package that you purchase.
Step 2
Log in as a registered CCO user and fill out the Customer Registration form found at the PAK Cisco Technical Support site: http://www.cisco.com/go/license. During the customer registration, submit each PAK you received and the MAC addresses of your systems. Please follow the instructions on the license web pages carefully to ensure that the correct MAC addresses are entered.
Step 3
For each PAK that you submit, a license file is generated and sent to you via email.
Step 4
Save each license file you receive to disk.
Step 5
Install the Cisco Clean Access software as described in Clean Access Server (CAS) Quick Installation and Clean Access Manager (CAM) Quick Installation.
Step 6
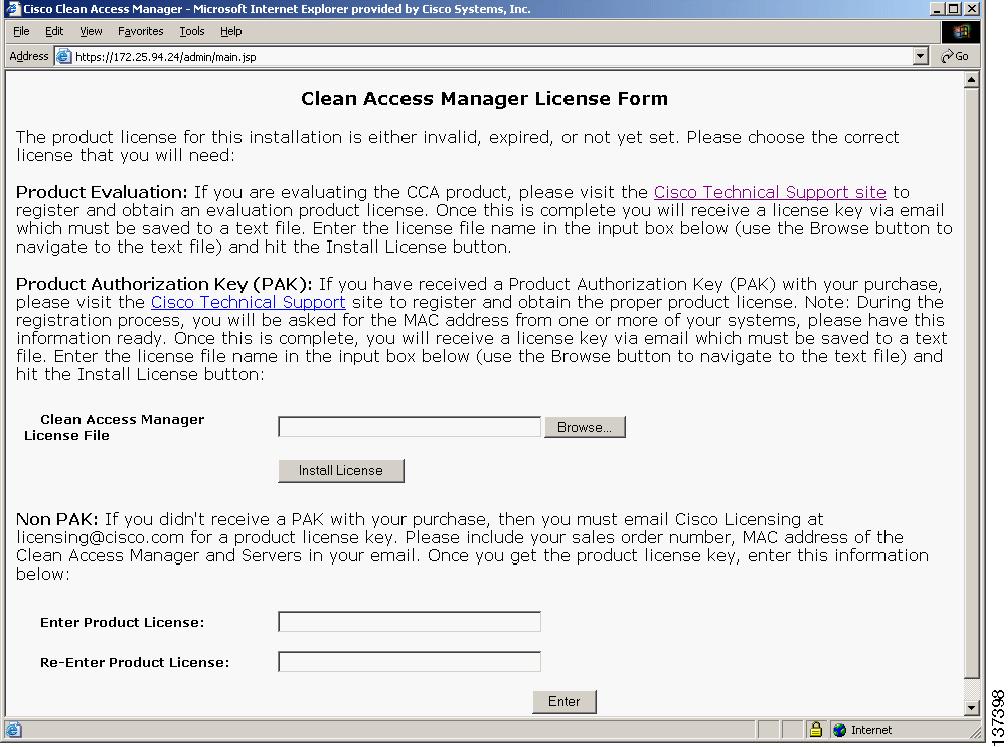
After software installation, access the Clean Access Manager web admin console by opening a web browser and entering the IP address of the CAM as the URL. The Clean Access Manager License form (Figure 3) will appear the first time you do this to prompt you to install your FlexLM license files.
Figure 3 Clean Access Manager License Form
Step 7
In the Clean Access Manager License File field, browse to the starter kit license file for your Clean Access Manager (CAM) and click Install License.
Step 8
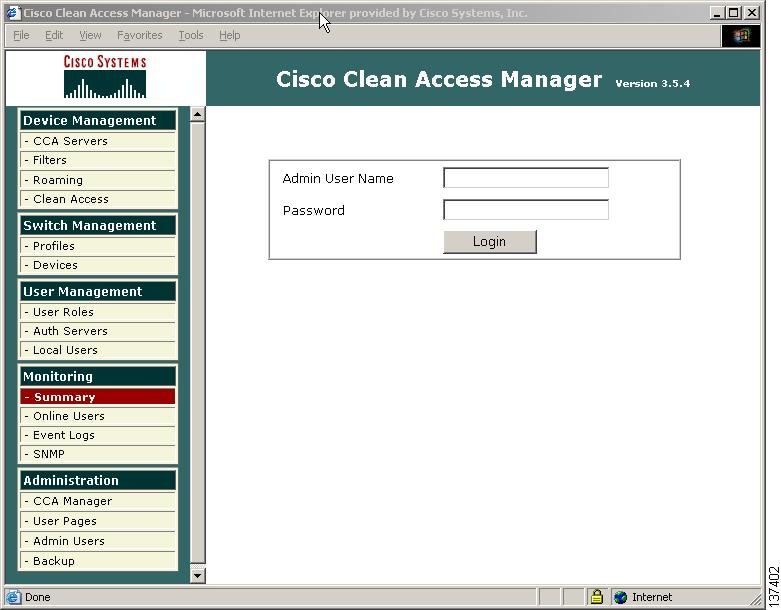
When you submit a valid license for the CAM (either evaluation, starter kit, or individual license), you should be redirected to the admin user login page of the Clean Access Manager web admin console. Enter the default username/password admin/cisco123 and click Login.
Figure 4 Admin Console Login
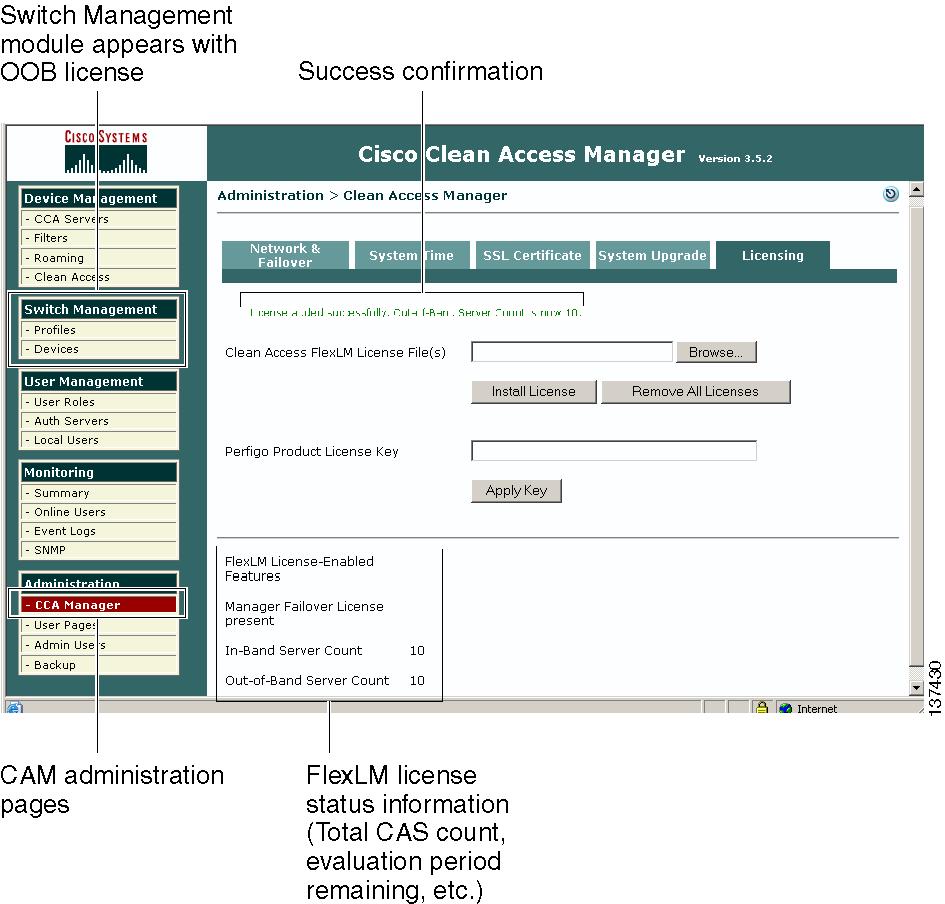
Step 9
By default, the first page that appears in the web console is the Monitoring > Summary page. Starting from the module menus in the left-hand pane, navigate to Administration > CCA Manager > Licensing (shown in Figure 5). Use this Licensing form to install additional license files for your Clean Access Server(s).
Figure 5 Cisco Clean Access Licensing Administration Page
Step 10
In the Clean Access FlexLM License File(s) field, browse to the license file for your Clean Access Server or Server bundle, and click Install License. You should see a green confirmation text string at the top of the page if the license was installed successfully, as well as the Server increment count (for example, "License added successfully. Out-of-Band Server Count is now 10").
Step 11
Repeat this step for each Clean Access Server license file you need to install (you should have received one license file per PAK submitted during customer registration). The status information at the bottom of the page will display the total number of Clean Access Servers enabled per successful license file installation.
Note
Clicking the Remove All Licenses button removes ALL FlexLM license files from the system. You cannot remove individual license files. You must enter the CAM license to be able to access the web admin console. Once the CAM license is installed, you can add additional CAS licenses as desired.
A permanent FlexLM license takes precedence and replaces an evaluation FlexLM license. FlexLM licenses (either permanent or evaluation) take precedence and replace legacy (Perfigo) license keys (even though the legacy key is still installed).When an evaluation FlexLM expires, or is removed, an existing legacy license key will again take effect.
Evaluation Licenses
To evaluate the Cisco Clean Access product, an official PAK is not required. An evaluation license enables:
•
1 Clean Access Manager (CAM)
•
1 In-Band (IB) Clean Access Server (CAS)
•
1 Out-of-Band (OOB) Clean Access Server (CAS)
•
1 IB failover CAS
•
1 OOB failover CAM
You do not need to submit MAC addresses for your machines to obtain an evaluation license. Use the following steps to obtain and install an evaluation license file.
CautionIt is recommended to obtain a permanent license file before continuing with full-scale deployment. Evaluation licenses are intended for trial purposes and expire after 30 days. Once a license expires, the elements of Cisco Clean Access will not be able to start. Contact a Cisco representative to purchase a permanent license.
Step 1
Register to obtain a 30-day evaluation license from the Product Evaluation License Cisco Technical Support site: http://www.cisco.com/go/license/public.
Step 2
After registering, the evaluation license file is generated and sent to you via email. Save the evaluation license file you receive to disk.
Step 3
Install the Cisco Clean Access software as described in Clean Access Server (CAS) Quick Installation and Clean Access Manager (CAM) Quick Installation
Step 4
After software installation, access the Clean Access Manager web admin console by opening a web browser and entering the IP address of the CAM as the URL. The Clean Access Manager License form (Figure 3) will appear the first time you do this to prompt you to install your FlexLM license file.
Step 5
Browse to your saved evaluation license file and install it in the Clean Access Manager License File field.
Step 6
Go to Administration > CCA Manager > Licensing (Figure 5) to view the days remaining for your evaluation period.
Note
Once installed, a permanent FlexLM license takes precedence and replaces an evaluation FlexLM license.
7 Add a Clean Access Server
Once you have installed valid licenses and accessed the web admin console, configure the installation using information from the CAS Installation Worksheet and CAM Installation Worksheet.
Step 1
First, add the Clean Access Server to the Clean Access Manager's managed domain.
Step 2
Go the Device Management module and click the CCA Servers link.
Step 3
Click the New Server tab.
Step 4
In the Server IP Address field, enter the trusted interface (eth0) IP address of the Clean Access Server from field (b) of the CAS Installation Worksheet.
Step 5
Server Location is an optional description of the server. Type a location or any other information that identifies the CAS.
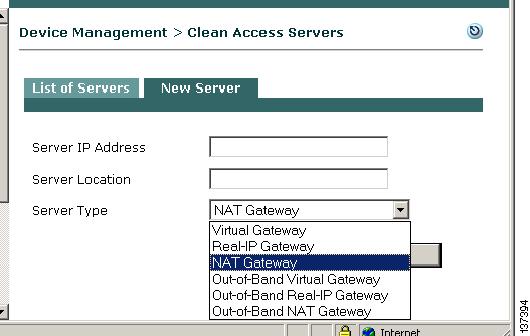
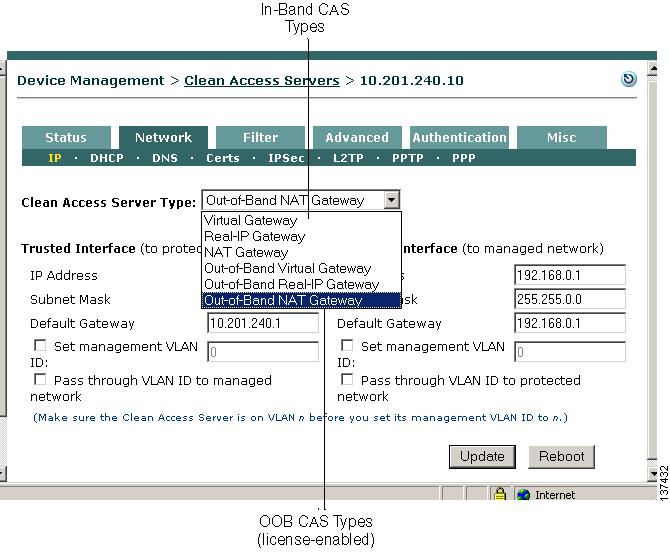
Step 6
The Server Type dropdown menu determines whether the Clean Access Server operates as a bridge or a gateway.
For in-band operation, choose one of the following CAS operating modes as appropriate for your environment:
a.
Virtual Gateway —CAS acts as a bridge between the untrusted network and an existing gateway.
b.
Real-IP Gateway — CAS acts as a gateway for the untrusted network.
c.
NAT Gateway — CAS acts as a gateway and performs NAT services for the untrusted network.
Note
For Real-IP and NAT Gateways, the trusted (eth0) and untrusted (eth1) interfaces of the CAS must be on different subnets. For Virtual Gateway, the CAS must be on a different subnet than the CAM, the eth0 and eth1 interfaces of the CAS can use the same IP address, and the CAS should be configured for DHCP forwarding.
For out-of-band operation, the Out-of-Band Server Types appear in the dropdown menu when you apply an OOB (Switch Management) enabled license to a Clean Access deployment. For OOB, the CAS operates as a Virtual, Real-IP, or NAT Gateway while client traffic is in-band (in the Clean Access network) during authentication and certification. Once clients are authenticated and certified, they are considered "out-of-band" (no longer passing through the Clean Access network) and allowed directly onto the trusted network. Choose one of the following operating modes for the CAS:
d.
Out-of-Band Virtual Gateway — CAS is a Virtual Gateway while traffic is in-band for authentication and certification.
e.
Out-of-Band Real-IP Gateway — CAS is a Real-IP Gateway while traffic is in-band for authentication and certification.
f.
Out-of-Band NAT Gateway — CAS is a NAT Gateway while traffic is in-band for authentication and certification.
Step 7
Click Add Clean Access Server.
Note that the Clean Access Manager can control both IB and OOB Clean Access Servers in its domain, but the CAS itself is either an IB or OOB server.
Note
If the Clean Access Manager cannot add the Clean Access Server to its managed list of servers:
Make sure the CAS is pingable. If not, the network settings may be incorrect. Reset them using service perfigo config.
The CAM and CAS must have the same shared secret. If this is the problem, reset the shared secret with service perfigo config.
In Virtual Gateway mode, ensure that the CAM and CAS are on different subnets.
8 Manage the Clean Access Server
Step 1
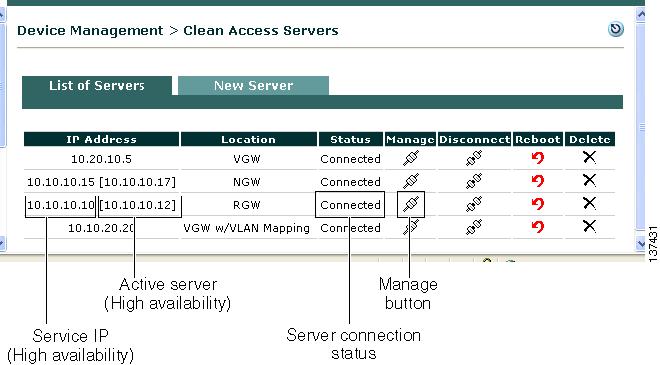
Once added to the Clean Access Manager, the new Clean Access Server should appear with a Status of Connected in the list under Device Management > CCA Servers > List of Servers.
Step 2
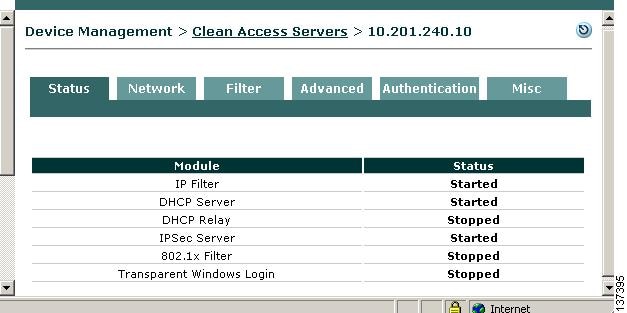
Click the Manage button for the corresponding Clean Access Server in the List of Servers to bring up the Clean Access Server (CAS) management pages (Figure 6).
Step 3
By default, the Status tab for the Clean Access Server appears first. The Status page shows whether the components of the server are running.
Figure 6 CAS Management Pages (Status Tab)
Note
In this document, Device Management > CCA Servers > IPaddress denotes the CAS management pages accessed from Device Management > List of Servers> Manage.
Step 4
Click the Network tab and double-check the settings on the IP page for the Trusted and Untrusted interfaces against your CAS Installation Worksheet.
Step 5
If you need to modify settings on this form, make sure to click Update, then Reboot. The CAS will show a status of "Not connected" while it reboots. Wait for it to show "Connected" status before continuing.
9 Set Up DHCP
If using a Real-IP or NAT Gateway configuration for the server, configure DHCP settings as described below. If a DHCP server already exists in your environment, it may be easiest to relay to that server for initial testing purposes. See the Clean Access Server Installation and Administration Guide for further details on DHCP configuration in the CAS.
Step 1
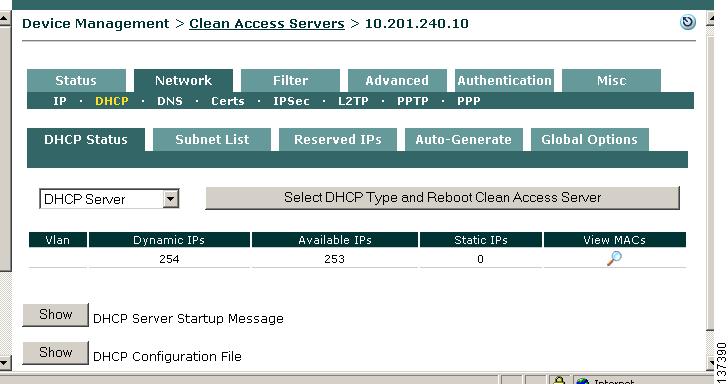
In the CAS management pages, click the Network tab, then the DHCP submenu link. The DHCP Status tab displays by default.
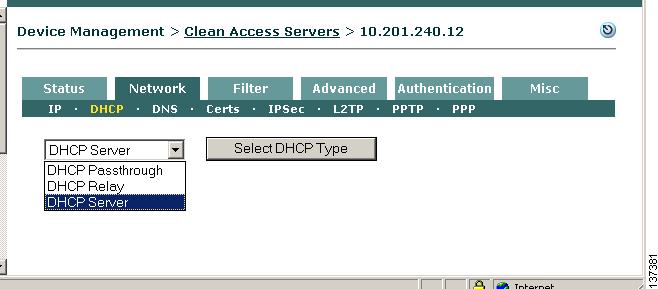
Step 2
The DHCP type dropdown menu indicates the DHCP operation mode for the Clean Access Server. The options are:
a.
DHCP Server - The CAS allocates client IP addresses for the untrusted (managed) network.
b.
DHCP Passthrough (default)- The CAS propagates the DHCP broadcast messages across its interfaces without modification. This mode should be selected if there is an existing DHCP server on the network segment.
c.
DHCP Relay - The CAS forwards messages from clients to another DHCP server. If selecting this type, wait for the page to refresh after clicking the Select DHCP Type button, then specify the external DHCP server by IP address in the Relay to DHCP Server field and click Update.
Step 3
For this example, choose DHCP Server as the operation type and click the Select DHCP Type button (note that this button toggles to Select DHCP Type and Reboot Clean Access Server after the CAS is configured as a DHCP Server).
The next step is to configure the IP pool from which client addresses are assigned using fields (i) and (j) from the CAS Installation Worksheet.
Step 4
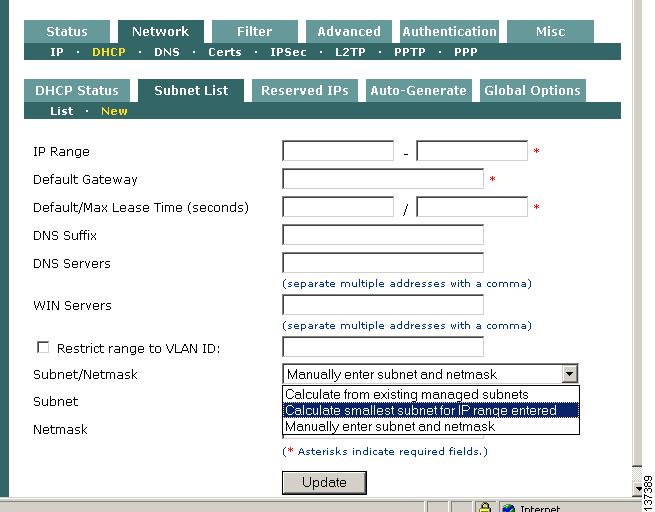
From Device Management > CCA Servers > IPaddress > Network > DHCP, Click the Subnet List tab, then the New sublink.
Step 5
In the New range form, fill out the following fields:
•
IP Range - The IP address pool to be assigned to clients. Use field (i) and field (j) of the CAS Installation Worksheet to provide a range of addresses in the untrusted network not currently used in your environment.
•
Default Gateway - The IP address of the default gateway IP address passed to clients (this should be the untrusted (eth1) IP address of the CAS, field (e) of the CAS Installation Worksheet).
•
Default/Max Lease Time (seconds)- The default and maximum amount of time that the IP address is given to the client, in seconds (such as 3600). The default lease time is used if the client does not request a particular lease time.
•
DNS Suffix - The DNS suffix to be passed to clients along with the address (e.g. yourorganization.com).
•
DNS Servers - The address of one or more DNS servers in the client's environment. Multiple addresses should be comma-separated.
•
WIN Servers - The address of one or more WIN servers in the client's environment. Multiple addresses should be comma-separated.
•
Restrict range to VLAN ID — This option is used when more than one managed subnet is added and more than one VLAN is configured. You can leave this blank for this example.
•
Subnet/Netmask - Choose how the subnet and netmask values are calculated for the IP pool. Options are:
–
Calculate from existing managed subnets.
–
Calculate smallest subnet for IP range entered.
–
Manually enter subnet and mask — the Subnet and Netmask fields appear below if this option is selected.
For this example, select Calculate smallest subnet for IP range entered.
Step 6
When finished, click Update. If any error messages appear, correct the configuration as instructed and try creating the pool again.
Step 7
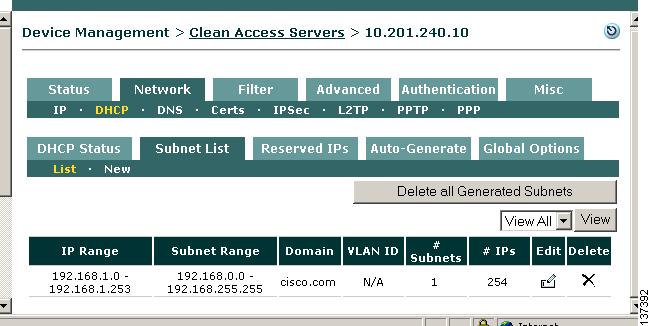
The new subnet list now appears under Device Management > CCA Servers > IPaddress > Network > DHCP > Subnet List > List.
Step 8
You can click the DHCP Status tab to display the total number of Dynamic IPs configured for the new subnet list and Available IPs remaining in the subnet list that can be assigned to clients (in the example below, only one address is assigned).
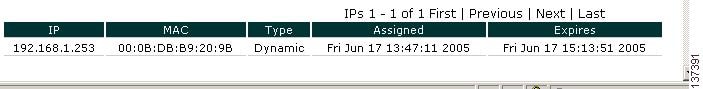
Step 9
When IP addresses are assigned to clients, clicking the View MACs button (magnifying glass icon) on the DHCP Status page displays the client information.
Step 10
You can verify that the DHCP module is running for a CAS by clicking the Status tab for the Clean Access Server. Make sure the DHCP Server module displays a status of Started.
10 Add Default Login Page
A default login page must exist to allow all managed users (web login or Clean Access Agent) to authenticate. The login page appears to web login users whenever they open a web browser to access the network. Before full deployment, you can customize the page to reflect your organization.
Step 1
In the console, click Administration > User Pages.
Step 2
Click the Login Page tab. The List submenu page appears by default.
Step 3
Click the Add submenu link.
Step 4
Leaving the default settings (*), click the Add button to add a default login page for all users.
Step 5
The new page appears under Login Page > List.
Edit Login Page
To modify a login page configuration later, click the Edit button next to the page under Administration > User Pages > Login Page > List. This brings up the following configuration options:
•
The General sublink allows you to make the page frame-based (allowing organizational logos to be added) or frame-less, and target the page to users by VLAN, subnet, or Operating System.
•
The Content sublink lets you customize login page elements such as default authentication servers, instructional text, button labels, and add logo files you uploaded to the CAM using Administration > User Pages > File Upload. The Content page also provides a Preview button to enable you to see what the page will look like to end users.
•
The Style sublink lets you alter background and foreground colors and styles of the page.
For complete details, see the Cisco Clean Access Manager Installation and Administration Guide.
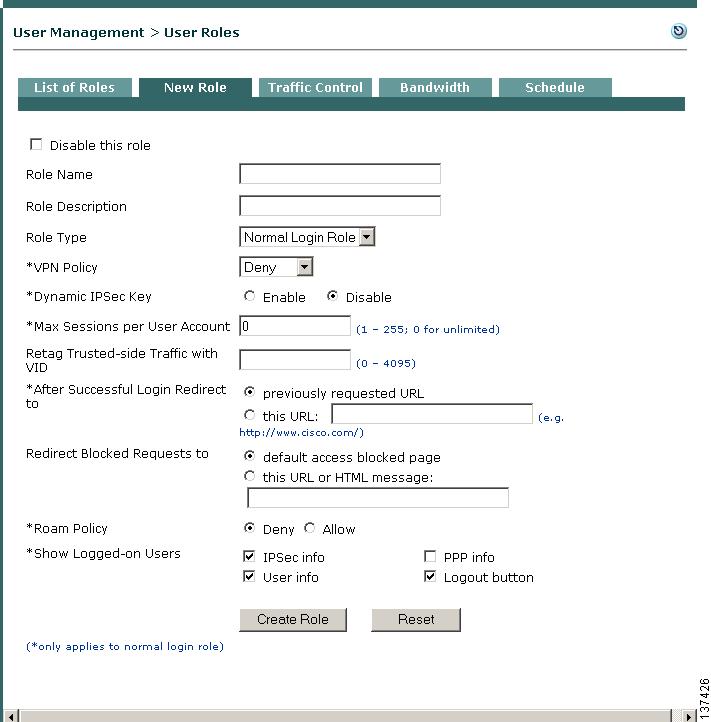
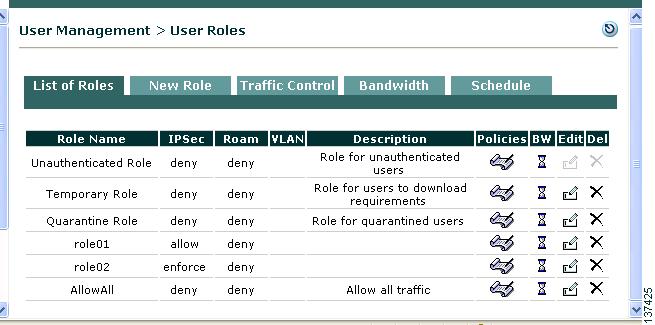
11 Create User Role and Local User (Test)
Cisco Clean Access puts users in roles when users log into the Clean Access network (out-of-band users are put into roles during the time that they are in-band). User roles aggregate a variety of user policies in the system, including traffic, bandwidth, application of network scanning plugins, and Clean Access Agent host requirements. The steps below show how to create a normal login role, then create a test local user to authenticate into that role. (Local users are validated by the Clean Access Manager and are used primarily for testing.) Once the role is created, you can configure the associated policies for the users in the role.
Step 1
Go to User Management > User Roles.
Step 2
Click the New Role tab to bring up the New Role form.
Step 3
Type a name for Role Name, such as AllowAll, and an optional Role Description. For this example, use the default values for the other form fields.
Step 4
Click Create Role. The new role appears under User Management > User Roles > List of Roles.
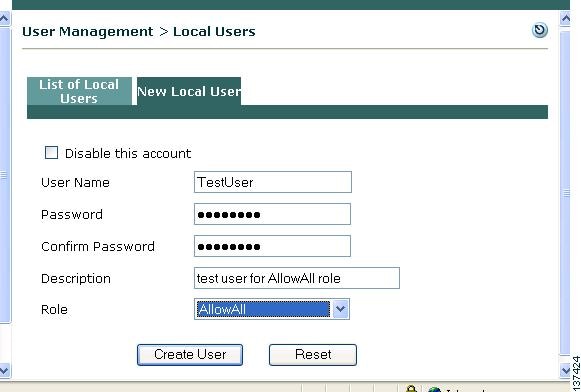
Step 5
Next, go to User Management > Local Users.
Step 6
Click the New Local User tab and fill in form fields as follows:
a.
Type a User Name, such as TestUser.
b.
Enter a password for the Password and Confirm Password fields (such as TestUser).
c.
Type an optional Description for the user.
d.
Choose the role you previously created, AllowAll, from the Role dropdown menu.
e.
Click Create User.
Step 7
The new user now appears under User Management > Local Users > List of Local Users.
12 Configure Traffic Policies for User Roles
By default, when a new normal login role is created, all client-side traffic originating from the untrusted network is blocked and all CAM/CAS-side traffic originating from the trusted network is allowed. After a normal login user role is created, Untrusted -> Trusted traffic control policies need to be configured to allow users to send and receive traffic while logged into that role. When users log into the network using the Clean Access Agent, the system first puts them in the system Temporary role while determining whether they meet host requirements. If they do, users are allowed on the network in the normal login role to which their user credentials are associated. If clients fail requirements, users stay in the Temporary role until they meet requirements or reach session timeout. (If using network scanning, clients that fail scan plugins can be put in a quarantine role or blocked from the network. See the Cisco Clean Access Manager Installation and Administration Guide for details on network scanning.)
Step 1
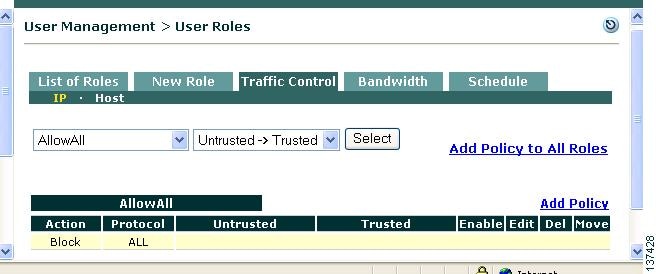
Go to User Management > User Roles > List of Roles and click the Policies button for the new AllowAll role you created.
Step 2
This will take you to the User Management > User Roles > Traffic Control tab (filtered for the specified role). The Traffic Control tab has two sublinks, IP and Host, that navigate to the list of IP-based traffic policies and Host-based traffic policies, respectively. For each list, traffic policies can be displayed for all user roles in the system or just the one you pick from the dropdown menu. The IP policy list appears initially by default, with the traffic direction set to Untrusted -> Trusted (for traffic moving from managed clients to the protected backend network).
Step 3
From User Management > User Roles > Traffic Control > IP, and with your "AllowAll" user role selected from the dropdown menu, click the Add Policy link for the role (on the right-hand side of the page).
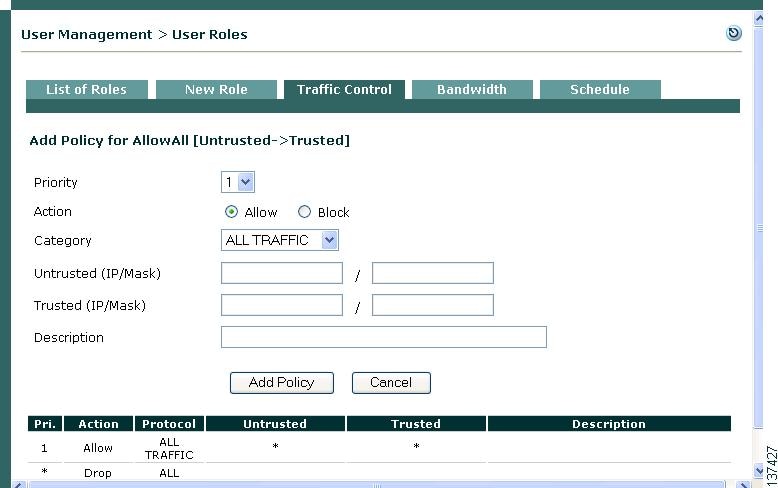
Step 4
In the IP-based Add Policy form that appears for the AllowAll role, configure options as follows:
a.
Leave Priority as 1.
b.
Leave Action as Allow.
c.
To enable all access, choose ALL TRAFFIC from the Category dropdown menu.
d.
Click Add Policy. The policy will display for the AllowAll role under User Management > User Roles > Traffic Control > IP.
Note
The Priority field determines which IP traffic policy is applied first. You can change this any time using the up/down arrows of the Move column in the policies list.
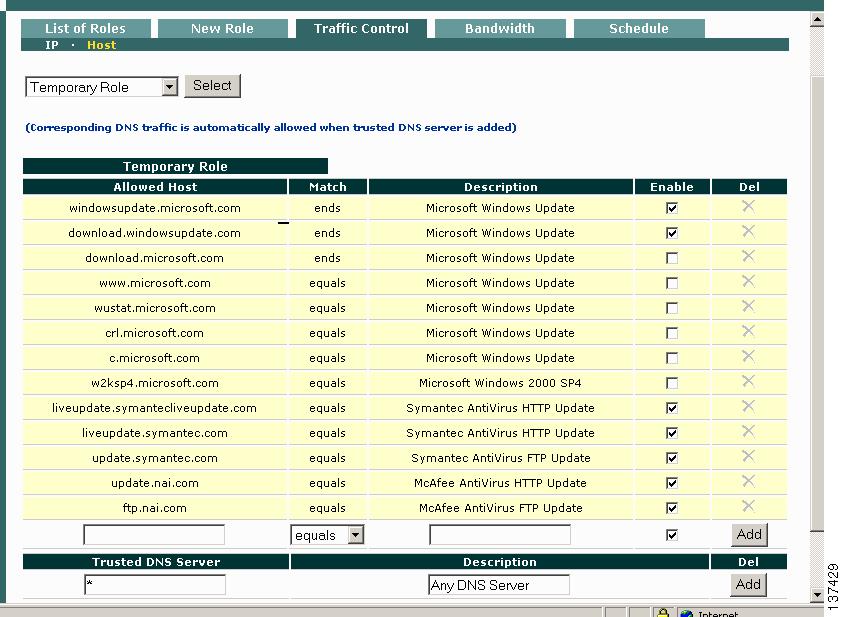
Step 5
Go to User Management > User Roles > Traffic Control > Host and scroll down to the policies for the Temporary Role.
Step 6
At the bottom of the form, make sure the default asterisk (*) is in the Trusted DNS Server text box and click the Add button next to the entry. This allows traffic for any DNS server and automatically adds an IP-based traffic policy allowing UDP traffic to/from the trusted network for clients in the Temporary role.
Step 7
Next, click the Enable checkboxes for any of the preconfigured Allowed Hosts to allow clients who fail Clean Access Agent requirements to go to these sites to fix their systems while they are in the Temporary role. You can also add your own hosts by entering the information in the Allowed Host and Description text box fields, selecting an operator (e.g. contains) and clicking the Add button.
13 Require Use of Clean Access Agent
New users are presented with a webpage from which they can download the setup executable to install the Clean Access Agent the first time they open a web browser and perform a web login (see Figure 8). Once the Clean Access Agent (version 3.5.1 or above) is downloaded to clients, you can configure the Agent to be automatically updated on clients via the web administration console (see Make Agent Auto-Upgrade Mandatory).
Step 1
Go to Device Management > Clean Access.
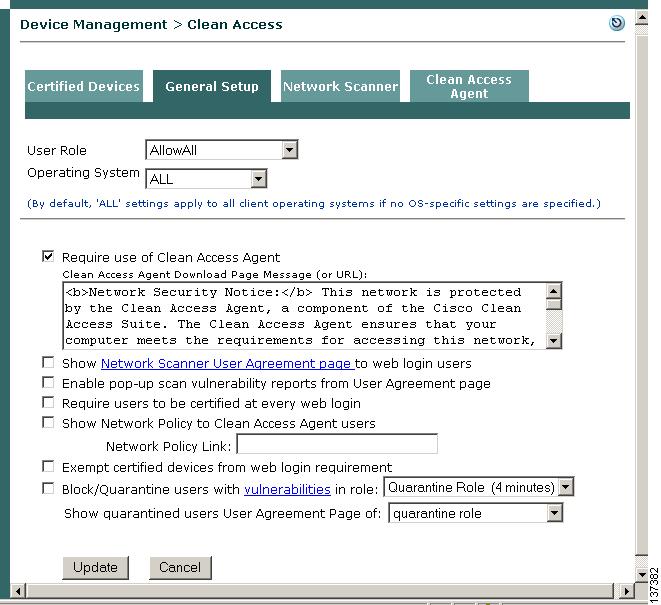
Step 2
Click the General Setup tab.
Step 3
Select the AllowAll role from the User Role dropdown menu.
Step 4
Leave the default setting of ALL for the client Operating System dropdown.
Step 5
Click the checkbox for Require use of Clean Access Agent.
Step 6
Click Update. This will present the Clean Access Agent download page to any user that opens a web browser and logs in with credentials that associate the user to the AllowAll role.
14 Make Agent Auto-Upgrade Mandatory
With Cisco Clean Access 3.5.1 or above installed on the CAM and CAS, and Clean Access Agent 3.5.1 or above installed on clients, you can enable mandatory or optional Agent auto-upgrade for all Clean Access Agent users. To make Agent auto-upgrade mandatory, use the following steps.
Step 1
Go to Device Management > Clean Access > Clean Access Agent > Distribution.
Step 2
Click the checkbox for "Current Clean Access Agent Patch is a mandatory upgrade."
Step 3
Click the Update button.
Step 4
Go to Device Management > Clean Access > Clean Access Agent > Update.
Step 5
Click the checkbox for "Check for CCA Agent upgrade patches along with Checks, Rules and AV List."
Step 6
Click the Update button.
When users reboot or exit/restart their Clean Access Agent, they will see a prompt to upgrade to a newer Agent when an update patch is downloaded to the CAM and made available to the CAS. The user must click OK (mandatory upgrade) and the client automatically installs the newer Agent. If auto-upgrade is left as optional, users will still see a prompt when they reboot or exit/restart their Agent, but they have the option of clicking Yes to install it immediately or No to postpone the upgrade.
15 Configure an AV Requirement
Once you have enforced use of the Clean Access Agent on a role, you can configure a variety of requirements to make sure users trying to log into the role have required packages on their systems (e.g. hotfixes, antivirus software or virus definition files) or alternatively, block users who have undesirable software installed. The following example shows how to configure a Clean Access Agent AV Definition Update requirement that checks if Symantec antivirus definition files are up-to-date on a Windows XP or 2000 client. For complete details on how to configure Clean Access Agent AV and custom requirements in the web admin console, see the Cisco Clean Access Manager Installation and Administration Guide. In this example, the general configuration steps are as follows:
3.
Create New AV Definition Update Requirement
4.
Map AV Definition Update Requirement to AV Definition Rule
5.
Map AV Definition Update Requirement to User Role
Update your CAM
Step 1
First, make sure to update your CAM to the latest version of the Supported Antivirus Product List, Cisco Checks & Rules, and CCA Agent Upgrade Patch by going to Device Management > Clean Access > Clean Access Agent > Updates.
Step 2
Make sure the "Check for CCA Agent upgrade patches along with Checks, Rules and AV List" option is chosen before updating to ensure that any 3.5.1 or above Agents installed on clients are updated with the latest patches.
Step 3
To configure Automatic Update, click the checkbox for "Check for updates every [] hours." (1 hour is recommended).
Step 4
Click Update. Status messages appear at the bottom of the page when update is complete.
Create New AV Rule
Step 5
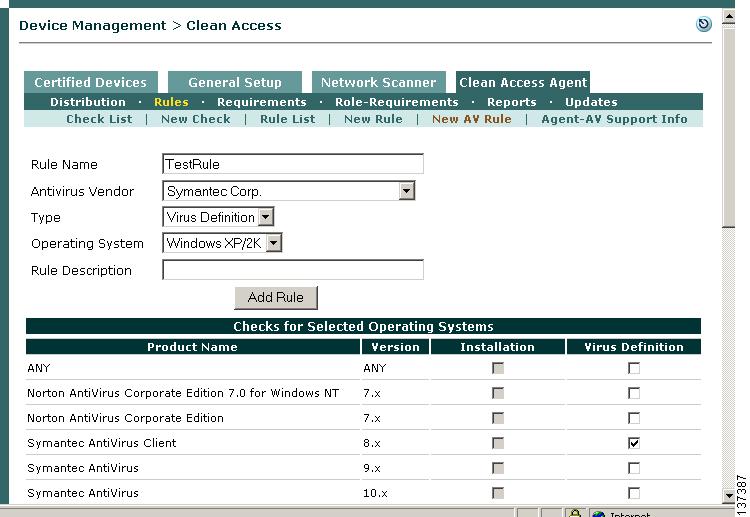
Next, go to Device Management > Clean Access > Clean Access Agent > Rules > New AV Rule.
Step 6
Type a name in the Rule Name field, such as TestRule (make sure there are no spaces in the name).
Step 7
Select Symantec Corp. from the Antivirus Vendor dropdown menu. This populates the form below, Checks for Selected Operating Systems, with the vendor's products (for the default Type and OS, which is Installation/Windows XP/2K)
Note
Choosing ANY from the Antivirus Vendor dropdown configures the AV rule to check the client for any supported AV product from any of the vendors (for the OS specified). If using this option, make sure your CAM is running release 3.5.2.1 or above.
Step 8
Select Virus Definition from the Type dropdown menu. Note that this disables (greys out) the Installation checkboxes on the form below.
Step 9
Select Windows XP/2K from the Operating System dropdown menu. This displays the vendor's product versions for this client OS.
Step 10
Type an optional Rule Description if desired.
Step 11
In the form for Checks for Selected Operating Systems, click the checkbox for a specific product(s), for example Symantec AntiVirus Client 8.x, or click the ANY checkbox to configure the AV rule to check client virus definition files for any product supported for Symantec Corp.
Note
Choosing ANY from the Checks for Selected Operating Systems table configures the AV rule to check the client for any product supported for that particular vendor and OS. If using this option, make sure your CAM is running release 3.5.2.1 or above.
Step 12
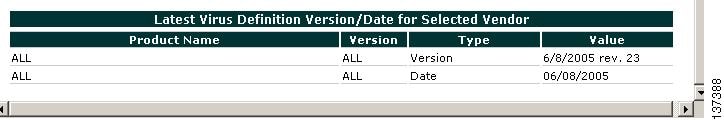
Scroll down all the way to the bottom of the form and verify the Latest Virus Definition Version/Date for Selected Vendor table. This will show the latest version or date value for the chosen product from the AV vendor. When testing on your client, compare these values with the version shown on the client AV software to verify that virus definition files have been updated.
Note
You can also view this information from Device Management > Clean Access > Clean Access Agent > Rules > Agent-AV Support Info.
Step 13
Click Add Rule. This adds the new AV definition rule at the bottom of Device Management > Clean Access > Clean Access Agent > Rules > Rule List.
Note
If your test client has a different AV package installed, choose a different Antivirus Vendor. The New AV Rule form displays the supported AV products available as of the latest Update for the vendor, OS, and check type (Installation or Virus Definition) chosen. For this example, make sure that Virus Definition is selected for Type.
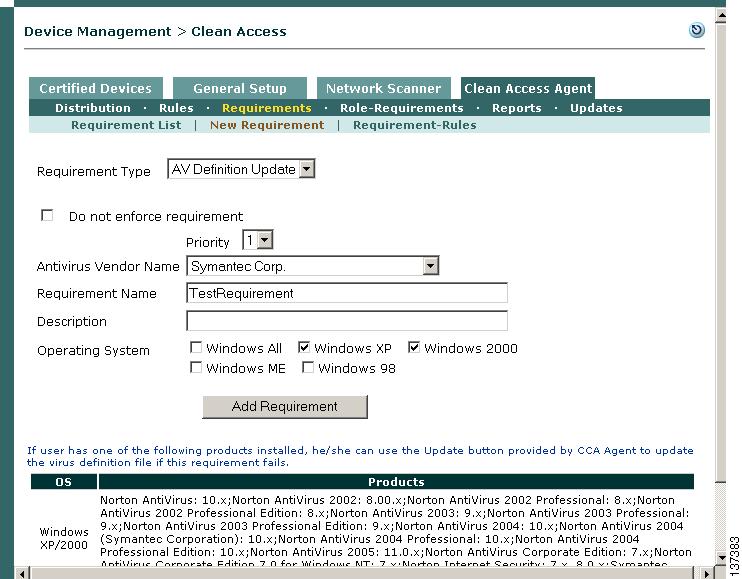
Create New AV Definition Update Requirement
Step 14
Next, create an AV Definition Update requirement by going to Device Management > Clean Access > Clean Access Agent > Requirements > New Requirement.
Step 15
Select AV Definition Update from the Requirement Type dropdown menu.
Step 16
Select Symantec Corp. from the Antivirus Vendor Name dropdown menu.
Step 17
Type TestRequirement in the Requirement Name text box (make sure there are no spaces).
Step 18
In the Description textbox, type instructions for the user such as: Please click the Update button to update the virus definition files for your installed Antivirus software. Please allow a few minutes for the update to complete. (Make sure there are no quotations or special characters in the text box.)
Step 19
Click the Windows XP and Windows 2000 checkboxes for Operating System.
Step 20
Click Add Requirement. The new TestRequirement will be listed under Device Management > Clean Access > Clean Access Agent > Requirements > Requirement List.
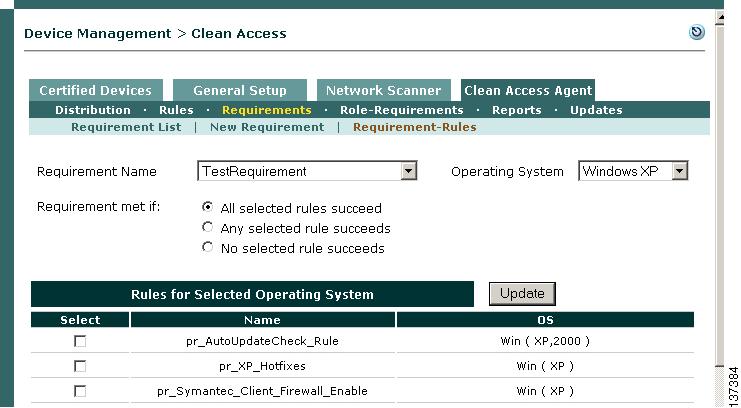
Map AV Definition Update Requirement to AV Definition Rule
Step 21
Next, go to Device Management > Clean Access > Clean Access Agent > Requirements > Requirement-Rules.
Step 22
Select TestRequirement from the Requirement Name dropdown menu.
Step 23
Select WindowsXP from the Operating System dropdown menu. All AV rules and preconfigured Cisco rules ("pr_") applicable to the requirement and OS will display.
Step 24
Leave the default setting for Requirement met if: (All selected rules succeed).
Step 25
Under Rules for Selected Operating System, scroll down to the bottom of the page and click the checkbox for TestRule.
Step 26
Click Update.
Step 27
Select Windows2000 from the Operating System dropdown menu and click Update again. The AV rule is now mapped to the requirement for Windows XP and 2000 client systems.
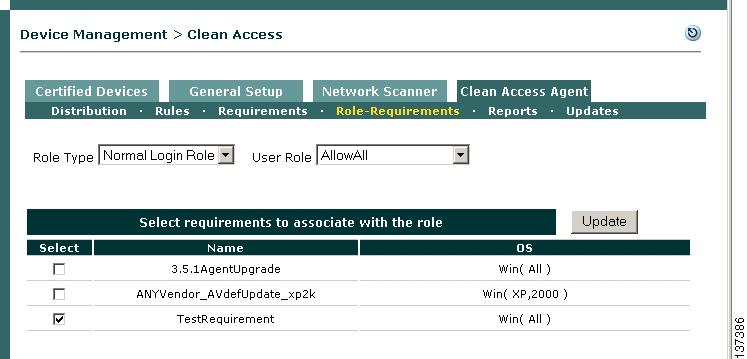
Map AV Definition Update Requirement to User Role
Step 28
Finally, go to Device Management > Clean Access > Clean Access Agent > Requirements > Role-Requirements.
Step 29
Leave Normal Login Role selected for the Role Type dropdown menu.
Step 30
Select AllowAll from the User Role dropdown menu.
Step 31
The form under Select requirements to associate with the role displays all requirements you have configured. Click the checkbox for TestRequirement.
Step 32
Click Update. Clean Agent requirement configuration is now complete. For this example configuration, any Windows XP/2000 user that logs in with user credentials associated to the AllowAll role will be required to have up-to-date AV definition files for the Symantec product chosen. If not, the Clean Access Agent will prompt the user to update their client files.
16 Test as a Managed Client
The easiest way to test Clean Access as an actual user is to connect a client computer to a switch connected to the untrusted (eth1) interface of the Clean Access Server and perform the following tests.
Step 1
Check whether the DHCP module correctly assigns a dynamic IP address:
a.
After attaching the client computer, restart it and open a command line window.
b.
From a command tool, type ipconfig /all and check the IP address and DHCP information you have been assigned. Your IP address should fall within the range of addresses you configured for the DHCP module.
Note
If you don't immediately get a client IP address in the correct range, try typing ipconfig /release then ipconfig /renew in the command tool.
Step 2
Check your web access:
a.
From a browser on your computer, attempt to navigate to any web page, such as www.google.com.
b.
In the Security Alert warning dialog, click Yes to accept the temporary certificate.
c.
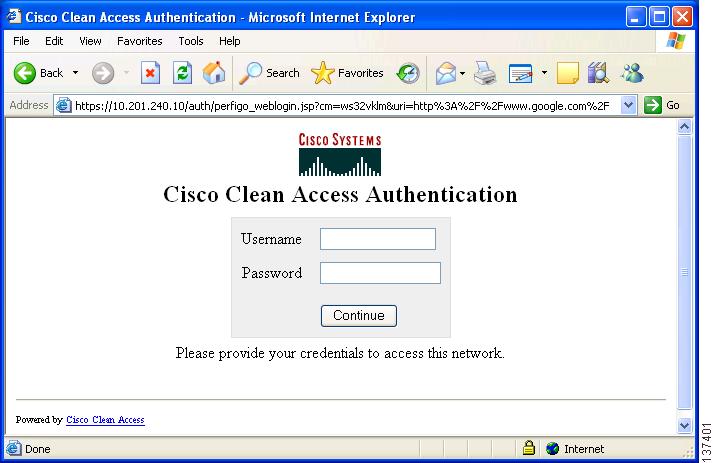
You should be redirected to the default web login page (Figure 7).
Note
Login page elements should be customized for your own organization before live deployment. See Edit Login Page for details.
Figure 7 Web Login Page
.
Note
If entering a domain name as a URL does not bring up the login page, your DNS settings may not be properly configured. In this case, try entering 1.1.1.1 as the URL to redirect you to the web login page.
Step 3
Login with the Username and Password you created for your local user (TestUser/TestUser).
Step 4
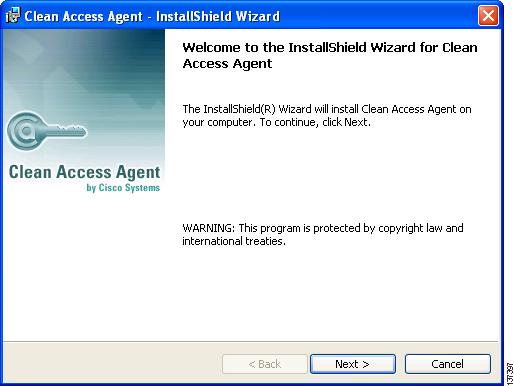
Click Continue. The Clean Access Agent download page should appear (Figure 8).
Figure 8 Clean Access Agent Download Page
Step 5
Click the Download button and Save the setup executable to an accessible folder. Then Run the file.
Step 6
The Clean Access Agent Install Shield Wizard appears. Follow the installation instructions and install the Clean Access Agent to your client machine. The Clean Access Agent will install to C:\Program Files\Cisco Systems\Clean Access Agent\ on the client
.
Step 7
When the installation is complete, you will see Clean Access Agent system tray icon, desktop shortcut, and login dialog.
Step 8
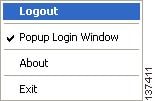
Right-clicking the Clean Access Agent system tray icon brings up the taskbar menu
.
There are four options:
•
Login/Logout— This option toggles depending on the login status of the user. Users can log themselves out by right-clicking the menu and selecting Logout.
•
Popup Login Window—This is enabled by default and causes the CCA Agent login dialog to pop up whenever the client is behind the CAS and is not logged in.
•
About—This displays the version of the CCA Agent.
•
Exit—This quits the Clean Access Agent. The user will not be logged out. To restart the application and display it on the system tray, double-click the Clean Access Agent desktop shortcut.
Note
Exit does not log off users from the network, nor does rebooting the client computer. Users can only log themselves off the network by right-clicking the taskbar menu and selecting Logout.
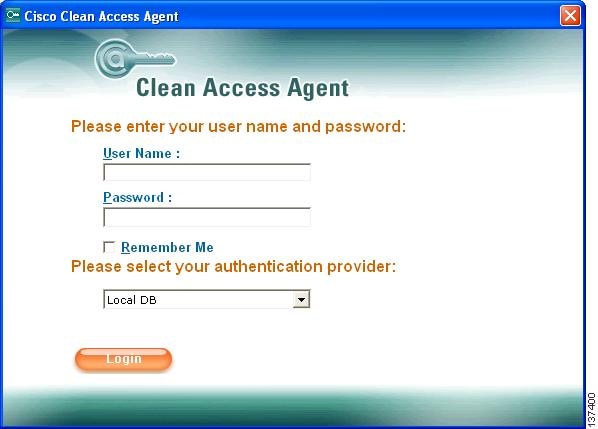
Step 9
In the Clean Access Agent login dialog that pops up, login with the Username and Password you created for the local user (TestUser/TestUser).
Step 10
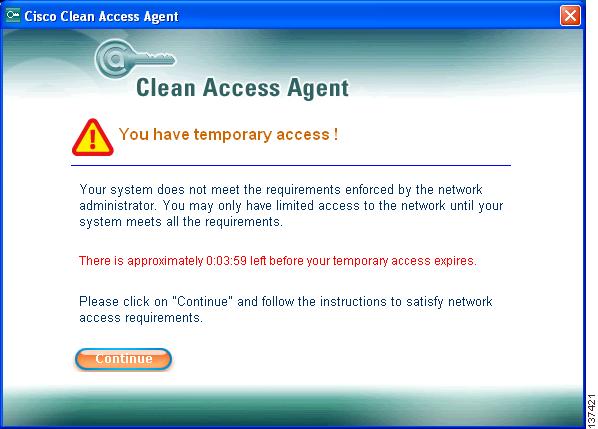
Because you configured an AV Definition Requirement for this user role, a temporary access dialog should display if your client AV definition files are not up-to-date.
Step 11
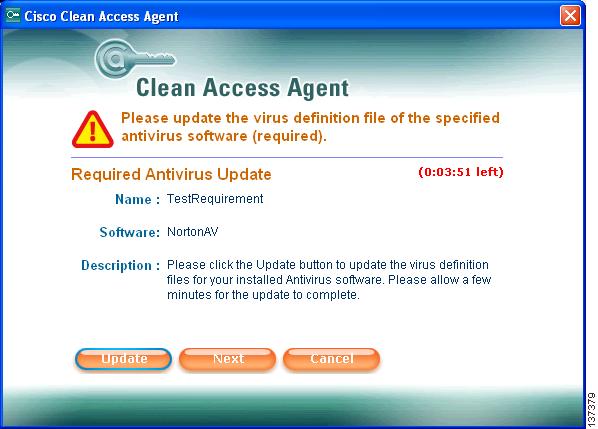
Click Continue. The AV requirement you configured displays in the Required Antivirus Update dialog. You will have a default session time of 4 minutes in the Temporary role to perform whatever action is necessary to meet the requirement type (in this case, update your AV definition files).
Step 12
Click the Update button in the Required Antivirus Update dialog. The Clean Access Agent will update the virus definition files for the AV software directly.
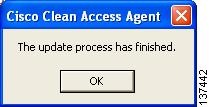
Step 13
A confirmation dialog pops up when update is complete. Click OK.
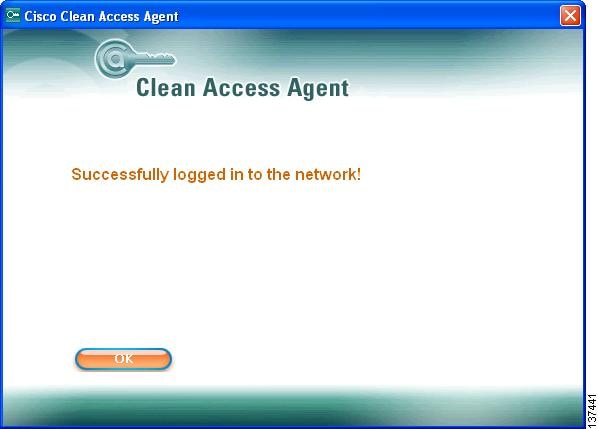
Step 14
Click the Next button in the Required Antivirus Update dialog. A login success confirmation should appear.
Step 15
Click OK. You should now have access to the network in the AllowAll role (with corresponding traffic policies).
Note
If you time out of your Temporary session, you will instead see a "Temporary access to the network has expired" dialog. In this case, click OK, wait for the login dialog to pop up, and login again.
Step 16
Open the AV software on the client and verify that the version/date information has updated for the virus definition file.
Tip
When using Automatic Update from the CAM, you can verify the latest system virus definition versions/dates for various AV products by selecting the applicable vendor/product from the Agent-AV Support Info or New AV Rule page.
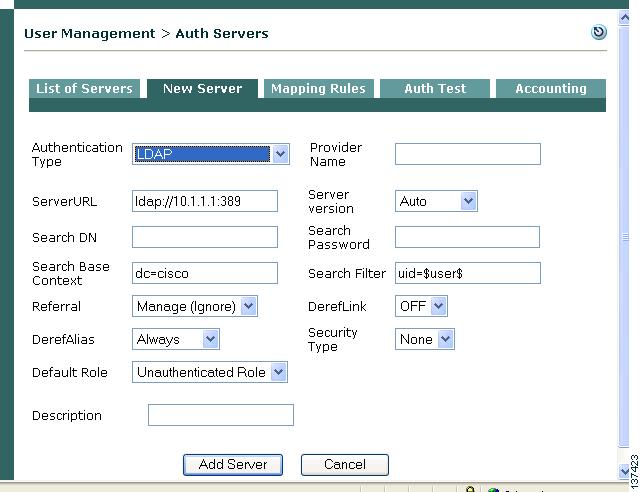
17 Configure Authentication Servers
To integrate Cisco Clean Access with an existing authentication server, you will need to know the configuration parameters for the type of authentication server you want to use. These can include the location of the authentication server, connect strings, and so on. Use the following steps once you have the information applicable for your authentication source.
Step 1
Go to User Management > Auth Servers.
Step 2
Click the New Server tab.
Step 3
Choose the type of authentication source you are using from the Authentication Type scroll list. Options are as follows:
Step 4
The parameters specific for the authentication type appear in the form.
Step 5
Type a name for the source in the Provider Name field. This name will appear in the Provider list in the login page.
Step 6
Enter other parameters appropriate for your authentication source and click Add Server.
Step 7
The new external authentication server appears under User Management > Auth Servers > List of Servers.
See the Cisco Clean Access Manager Installation and Administration Guide for details on configuring mapping rules to map users into user roles based on VLAN ID or LDAP/RADIUS authentication server attributes.
18 User Authentication Test
Before testing an external authentication server as an actual user, there is a simple user authentication test that can validate your authentication server parameters immediately in the web admin console.
Step 1
Go to User Management > Auth Servers > Auth Test.
Step 2
Select a Provider. The Clean Access Manager is the default Local provider.
Step 3
Enter User Name and Password values and click the Test button. The results appear at the bottom of page. If the username and password are valid, the console displays the role assigned to the user.
Note
Under Administration > User Pages >Login Page > Edit > Content > Default Provider, make sure to change your Default Provider from Local DB to the new auth server you configured to allow clients to be authenticated externally instead of locally in the Clean Access Manager.
Step 4
Users should now be able to access the managed network using the login credentials stored in the authentication source you configured. Perform client testing as described in Test as a Managed Client.