Feedback Feedback
|
Table Of Contents
Scenario 1 - PAP and PDP Share a Common Repository
Scenario 2 - PAP and PDP Use Different Repositories
Updating pap_config.xml Parameters
Updating pdp_config.xml parameters:
Obtaining Documentation and Submitting a Service Request
CEPM Policy Cache Guide
Revised: December 3, 2010, Doc Part No: OL-21354-01Contents
•
Obtaining Documentation and Submitting a Service Request
About This Document
Objective
This document is intended to provide the definition and functionalities of the Policy Cache feature, which is introduced in Cisco Enterprise Policy Manager (CEPM) in various deployment scenarios.
Audience
This guide is for administrators who use CEPM and are responsible for resource modelling and entitlement management.
Introduction
Cisco Enterprise Policy Manager (CEPM) is an extremely database intensive application. The policy evaluation operation causes large data reads. In CEPM, the policy data is persisted to and read from the CEPM database. Any change in the policy data impacts the application performance. As the size of the database increases, it may cause variation in performance characteristics of the policy evaluation. To overcome this, CEPM introduces Policy Cache - a framework that allows the policy data to be cached so that policy evaluation can be done quickly in memory rather than relegating all calls to the database. The policy cache infrastructure (PDP application memory) provides better response times to the access requests and leverages application performance.
Table 1 and Table 2 quantify the benefit of utilizing the policy cache in terms of the performance number.
Data details:
No. of Users: 57959
No. of Active Users: 57281
No. of Resources: 20049
No. of Roles: 713
No. of Policies: 81276
No. of Contexts: 329
No. of Applications: 72
The following tables quantify the benefit of utilizing the policy cache in terms of the performance number:
Data details:
No. of Users: 57458
No. of Active Users: 9291
No. of Resources:599880
No. of Roles: 749
No. of Policies: 161666
No. of Contexts: 3
No. of Applications: 61
Deployment Scenarios
There are two deployment scenarios which dictate the use of policy cache as given below:
1.
Scenario 1 - PAP and PDP Share a Common Repository
2.
Scenario 2 - PAP and PDP Use Different Repositories
Note
The JMS provider must be configured and integrated with PAP and PDP in both of these scenarios.
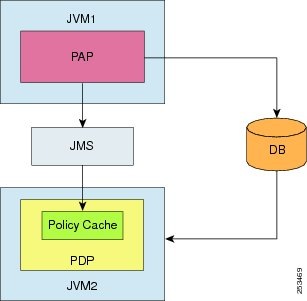
Scenario 1 - PAP and PDP Share a Common Repository
When the PAP and the PDP run in two different JVMs but share a common repository, the policy cache acts as an alternative policy retrieval engine that stores the policy data and retrieves the decision for every authorization request that the PEP sends to the associated PDP.
In this scenario, the policy cache is updated using the publish/subscribe model available within the JMS framework that is integrated with the CEPM application.
During bootstrap, PDP utilizes the database and loads the relevant application data such as entities, entity mappings, mapped policies and attributes, and so on, into the policy cache.
During runtime, whenever a policy change event occurs, the PAP uses the posthook handler to publish the message to the topic associated with the PDP. The PDP, which subscribes to that topic, receives the message and updates the policy cache.
Figure 1
Policy Cache Deployment Scenario 1
In this deployment scenario, you must set the shared_repository tag to false in pap_config.xml and true in pdp_config.xml.
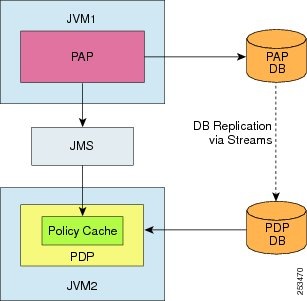
Scenario 2 - PAP and PDP Use Different Repositories
In this scenario, the PAP and the PDP run in two different JVMs, and have two different database instances. The policy cache is updated using the publish/subscribe model within the JMS framework that is integrated with the CEPM application.
During bootstrap, the policy cache is loaded with the relevant policy data from the PDP database.
During runtime, whenever a policy change event occurs within the PAP, the PAP publishes the message to the topic using the posthook handler. The PDP associated with that topic subscribes to the message and updates the policy cache.
Note
The database replication between the PAP and the PDP databases are done using Oracle Streams.
Figure 2
Policy Cache Deployment Scenario 2
In this deployment scenario, you must set the shared_repository tag to false in pap_config.xml and true in pdp_config.xml.
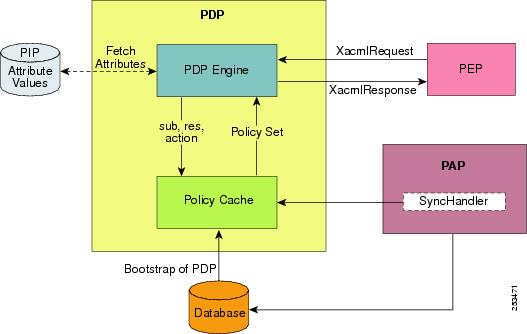
How Policy Cache Works
Figure 3 shows how the policy cache works in a shared deployment where the PAP and the PDP share a common repository:
Figure 3 Policy Cache workflow
When a PEP request hits the PDP, the PDP engine utilizes the policy cache to retrieve the applicable policy sets for the request by using the existing entity information. In case of any rules configured for any policy, the engine utilizes the extracted policy set along with the PIP information retrieved from the PIP repository to evaluate the decision.
In the event the policy cache does not have any data matching the PEP request for evaluation, the PDP returns a `Not Applicable' decision.
Note
With JMS enabled, when you import policies into the PAP either through UI or using APIs, the policy cache is not updated with the imported policies until and unless the PDP server is restarted.
After the caching is done, you can view the log messages in the PDP server to verify how much data has been cached. The following is an extract of the PDP server log which shows the cache warm up confirmation -
2009-10-27 15:18:25,264 INFO [main] net.securent.pdp.PDPEngine- Total memory utilized[18]M.B2009-10-27 15:18:25,264 INFO [main] net.securent.pdp.PDPEngine- Time taken to load below entities into memory[2401]m.s2009-10-27 15:18:25,264 INFO [main] net.securent.pdp.PDPEngine- Number of user's : [3]2009-10-27 15:18:25,264 INFO [main] net.securent.pdp.PDPEngine- Number of group's : [0]2009-10-27 15:18:25,264 INFO [main] net.securent.pdp.PDPEngine- Number of Roles's : [13]2009-10-27 15:18:25,264 INFO [main] net.securent.pdp.PDPEngine- Number of Resources's : [362]2009-10-27 15:18:25,264 INFO [main] net.securent.pdp.PDPEngine- Number of Context's : [1]Configuring Policy Cache
You can enable the policy cache by updating the <sharedRepository> tag and the <pdp> tag in pdp_config.xml and pap_config.xml files.
Updating pap_config.xml Parameters
Following tags and their attributes must be updated in order to utilize the policy cache:
•
<shared_repository> tag—This tag must be set to true, if PAP and PDP share a common repository (as mentioned in Deployment Scenario -1). Set it to false, if the PAP and the PDP have two different repositories.
<shared_repository>true</shared_repository>•
<PDP> tag— The following attributes of the PDP tag must be updated for enabling policy cache and other relevant features:
<pdp policyCacheEnable="true" caseSensitive="true" xacmlAttributes="false" policyCacheRefresh="false" ttl="10">. . .. . .. . .</pdp>–
<policyCacheEnable>— This attribute must be set to true in order to utilize the policy cache for policy decision instead of accessing the database. If this attribute is set to false, the authorization decisions are given from the database and not from the policy cache. By default, this attribute value is set to true.
–
<caseSensitive>— This attribute indicates whether or not to sort input parameters records in a case sensitive manner. If it is set to false, the values of input parameters with different cases are considered the same, for example, username Mary and username MARY are same.
–
<xacmlAttributes>— If this attribute is set to true, the PDP returns the Xacml compliance response, that includes the decision as well as other relevant attributes such as resource names and resource type names along with the authorization decision. If this element is set to false, the PDP returns only the decision.
–
<policyCacheRefresh>— This attribute is set to true to enable policy cache refresh after every fixed time interval specified in ttl attribute. During runtime, this updates the policy cache with the changed events in the PAP application. If you set this attribute to false, the policy cache is not updated during runtime.
–
<ttl>— This indicates the time interval in seconds after every completion of which the Policy cache is automatically updated with the changed events in the PAP application. For example, if you set the value to 5, the policy cache is updated after every 5 seconds only if the policyCacheRefresh attribute is set to true.
•
<jms> tag— The <jms> tag must be updated in both pap_config.xml and pdp_config.xml files to configure the JMS for message synchronization. Refer to CEPM Install and Config Guide for more details on how to configure JMS in CEPM.
Refer to CEPM PAP Configuration Guide for more information on how to update the JMS attributes.
Updating pdp_config.xml parameters:
Following tags and their attributes must be updated in order to utilize the policy cache:
•
<shared_repository> tag—This tag must be set to true, if PAP and PDP share a common repository (as mentioned in Deployment Scenario -1). Set it to false, if the PAP and the PDP have two different repositories.
<shared_repository>true</shared_repository>•
<PDP> tag— The following attributes of the PDP tag must be updated for enabling policy cache and other relevant features:
<pdp attributeEnable="false" cloningCheckEnable="false" retry="1000" policyCacheEnable="true" caseSensitive="true" xacmlAttributes="false">. . .. . .. . .</pdp>–
attributeEnable attribute—Set its value to True if you want the PDP to send attributes related to various entities for a policy, such as user attributes, role attributes, and resource attributes. Otherwise, set its value to False.
–
cloningCheckEnable attribute—Set its value to True if, you want the PDP to send the policy details of the main user for which this user is cloned. Otherwise, set its value to False.
–
retry attribute—When the databases (entitlement repository or external PIP) of a PDP become unresponsive (due to connection failure during query execution time), the PEP retries to send the request to PDP after a specified time interval. This `retry' time interval is set in the <retry> tag in the pdp_config.xml file. For example, assume the retry value given in pdp_config.xml is X seconds and the timeout value given in pep_config.xml is Y seconds (where X < Y). When the PEP sends a request to the PDP and the PDP finds the database is down, it sends a retry message to the PEP conveying that it should resend the request after X seconds. The PEP will resend the request to the PDP after X seconds. This process will continue till the PEP gets a proper response. If it does not get any response within the specified timeout interval (Y seconds), it will throw an exception. Set this value in seconds.
–
<policyCacheEnable>— This attribute must be set to true in order to utilize the policy cache for policy decision instead of accessing the database. If this attribute is set to false, the authorization decisions are given from the database and not the policy cache. By default, this attribute value is set to true.
–
<caseSensitive>— This attribute indicates whether or not to sort input parameters records in a case sensitive manner. If it is set to false, the values of input parameters with different cases are considered the same, for example, username Mary and username MARY are same.
–
<xacmlAttributes>— If this attribute is set to true, the PDP returns the Xacml compliance response, that includes the decision as well as other relevant attributes such as resource names and resource type names along with the authorization decision. If this element is set to false, the PDP returns only the decision.
•
<jms> tag— The <jms> tag must be updated in both pap_config.xml and pdp_config.xml files to configure the JMS for message synchronization.
Refer to CEPM PDP Configuration Guide for more information on how to update the JMS attributes.
Documentation Updates
Table 3 Updates to CEPM Policy Cache Guide
June 10, 2010
Cisco Enterprise Policy Manager (EPM) Release 3.3.1.0
December 4, 2010
Scenario 2 - PAP and PDP Use Different Repositories is updated.
Related Documentation
Following are the related documents that are available in CEPM-V3.3.0.0 documentation:
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information, see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What's New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free service and Cisco currently supports RSS Version 2.0.
CCDE, CCENT, CCSI, Cisco Eos, Cisco Explorer, Cisco HealthPresence, Cisco IronPort, the Cisco logo, Cisco Nurse Connect, Cisco Pulse, Cisco SensorBase, Cisco StackPower, Cisco StadiumVision, Cisco TelePresence, Cisco TrustSec, Cisco Unified Computing System, Cisco WebEx, DCE, Flip Channels, Flip for Good, Flip Mino, Flipshare (Design), Flip Ultra, Flip Video, Flip Video (Design), Instant Broadband, and Welcome to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn, Cisco Capital, Cisco Capital (Design), Cisco:Financed (Stylized), Cisco Store, Flip Gift Card, and One Million Acts of Green are service marks; and Access Registrar, Aironet, AllTouch, AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Lumin, Cisco Nexus, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation, Continuum, EtherFast, EtherSwitch, Event Center, Explorer, Follow Me Browsing, GainMaker, iLYNX, IOS, iPhone, IronPort, the IronPort logo, Laser Link, LightStream, Linksys, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, PCNow, PIX, PowerKEY, PowerPanels, PowerTV, PowerTV (Design), PowerVu, Prisma, ProConnect, ROSA, SenderBase, SMARTnet, Spectrum Expert, StackWise, WebEx, and the WebEx logo are registered trademarks of Cisco and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1002R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
© 2009 Cisco Systems, Inc. All rights reserved.