-
Installation and Setup Guide for Cisco Secure ACS Solution Engine Version 3.3
-
Cisco 90-Day Limited Hardware Warranty Terms
-
Preface
-
Cisco Secure ACS Solution Engine Overview
-
Preparing for Installation
-
Installing and Configuring Cisco Secure ACS Solution Engine
-
Administering Cisco Secure ACS Solution Engine
-
Technical Specifications
-
Windows Service Advisement
-
Command Reference
-
Index
-
Table Of Contents
Administering Cisco Secure ACS Solution Engine
Basic Command Line Administration Tasks
Logging In to the Solution Engine via Serial Console
Shutting Down the Solution Engine via Serial Console
Logging Off the Solution Engine via Serial Console
Rebooting the Solution Engine via Serial Console
Determining the Status of Solution Engine System and Services via Serial Console
Stopping Solution Engine Services via Serial Console
Starting Solution Engine Services via Serial Console
Restarting Solution Engine Services via Serial Console
Getting Command Help via Serial Console
Obtaining Support Logs via the Serial Console
Backing Up ACS Data via the Serial Console
Restoring ACS Data via the Serial Console
Compacting the ACS Solution Engine Database
Reconfiguring Solution Engine System Parameters
Resetting the Solution Engine Administrator Password
Resetting the Solution Engine Administrator Name
Reconfiguring the Solution Engine IP Address
Setting the System Time and Date Manually
Setting the System Time and Date with NTP
Setting the Solution Engine System Domain
Setting the Solution Engine System Hostname
Transferring an Upgrade Package to the Solution Engine via Serial Console
Applying a Solution Engine System Upgrade
Understanding the CSAgent Patch
Recovering from Loss of Administrator Credentials
Re-Imaging the Solution Engine Hard Drive
Migrating to Cisco Secure ACS Solution Engine
Administering Cisco Secure ACS Solution Engine
This section describes the major Cisco Secure ACS Solution Engine Version 3.3 system administration tasks that you can perform via the serial console connection command line interface (CLI). For all other Cisco Secure ACS Solution Engine configuration and administration tasks, that is, those performed from the ACS HTML interface, see the User Guide for Cisco Secure ACS Solution Engine Version 3.3.
Serial console service starts automatically when the Cisco Secure ACS Solution Engine boots and prompts the user to log in. Successful login launches a command line application (shell) that operates the CLI.
This section contains the following topics:
•
Basic Command Line Administration Tasks
•
Reconfiguring Solution Engine System Parameters
•
Upgrading the Solution Engine
•
Migrating to Cisco Secure ACS Solution Engine
Basic Command Line Administration Tasks
This section details basic administrative tasks performed using a serial console connected the Cisco Secure ACS Solution Engine. This section contains the following procedures:
•
Logging In to the Solution Engine via Serial Console
•
Shutting Down the Solution Engine via Serial Console
•
Logging Off the Solution Engine via Serial Console
•
Rebooting the Solution Engine via Serial Console
•
Determining the Status of Solution Engine System and Services via Serial Console
•
Stopping Solution Engine Services via Serial Console
•
Starting Solution Engine Services via Serial Console
•
Restarting Solution Engine Services via Serial Console
•
Getting Command Help via Serial Console
Logging In to the Solution Engine via Serial Console
To log in to the Cisco Secure ACS Solution Engine via a serial console, follow these steps:
Step 1
Establish a serial console connection to the Cisco Secure ACS Solution Engine. For details, see Establishing a Serial Console Connection, page 3-15.
Step 2
At the login: prompt, enter the Cisco Secure ACS Solution Engine administrator name.
Step 3
At the password: prompt, enter the Cisco Secure ACS Solution Engine password.
Result: The system prompt appears in the following form:
Cisco Secure ACS Solution Engine name
Note
There is only one set of Cisco Secure ACS Solution Engine login credentials (administrator name and password) that have the serial connection privilege.
Shutting Down the Solution Engine via Serial Console
CautionPowering off the Cisco Secure ACS Solution Engine by using only the power switch may cause the loss or corruption of data. Use this procedure to shut down the Cisco Secure ACS Solution Engine.
To use the serial console to shut down the Cisco Secure ACS Solution Engine, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type shutdown, and then press Enter.
Step 3
At the Are you sure you want to shut down? (Y/N) prompt, type Y for yes and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following message:
It is now safe to turn off the computerStep 4
Press the power switch and hold it for 4 seconds to turn off the Cisco Secure ACS Solution Engine. For the location of the power switch see Figure 1-2 on page 1-4.
The Cisco Secure ACS Solution Engine powers OFF.
Logging Off the Solution Engine via Serial Console
To log off the Cisco Secure ACS Solution Engine via the serial console, follow these steps:
Step 1
At the system prompt, type exit.
Step 2
Press Enter.
Result: The serial console connection closes, and the login: prompt reappears.
Rebooting the Solution Engine via Serial Console
To reboot the Cisco Secure ACS Solution Engine via the serial console, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type reboot, and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following message:
Are you sure you want to reboot? (Y/N)Step 3
Type Y for yes and then press Enter.
Result: The Cisco Secure ACS Solution Engine reboots. When the reboot is finished, the login: prompt reappears.
Determining the Status of Solution Engine System and Services via Serial Console
You can use the serial console connection to obtain system and service status information.
Note
Status determination is typically performed from within the Cisco Secure ACS Solution Engine HTML user interface. For more information, see "Determining the Status of Cisco Secure ACS Services" in the User Guide for Cisco Secure ACS Solution Engine Version 3.3.
To determine the status of the Cisco Secure ACS Solution Engine and the Cisco Secure ACS Services, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type show, and then press Enter.
Result: The system displays the following status information:
Cisco Secure ACS Solution Engine NameCisco Secure ACS Solution Engine Version
Appliance Management Software VersionAppliance Base Image VersionCSA build XXXX: (Patch: x_x_x_xxx)Session Timeout (in minutes)Last Reboot TimeCurrent Date & TimeTime ZoneNTP Server(s)CPU Load (percentage)Free Disk (amount of hard drive space available)Free Physical MemoryAppliance IP ConfigurationDHCP Enabled (Yes/No)IP AddressSubnet MaskDefault GatewayDNS ServersACS Services (running/stopped)CSAdminCSAgentCSAuthCSDbSyncCSLogCSMonCSRadiusCSTacacs
Tracing Routes
If you are unfamiliar with the trace route command or want information on the command's optional arguments, see the Command Reference entry tracert, page C-16.
To trace the network route taken by the Cisco Secure ACS Solution Engine to a given destination, follow these steps:
Step 1
At the system prompt, type tracert, followed by zero or more optional arguments and then the IP address of the target destination.
Step 2
Press Enter.
Result: The system displays the route tracing information followed by the message:
Trace complete
Stopping Solution Engine Services via Serial Console
Note
Stopping solution engine services is a procedure that is typically performed from within the HTML interface.
You can stop any of the Cisco Secure ACS Solution Engine services from the serial console. The Cisco Secure ACS Solution Engine services include the following:
•
CSAdmin
•
CSAgent
•
CSAuth
•
CSDbSync
•
CSLog
•
CSMon
•
CSRadius
•
CSTacacs
Tip
To list the services and their status, you can use the show command. For more information, see Determining the Status of Solution Engine System and Services via Serial Console.
Note
When you stop the CSAgent service, that service remains disabled until you explicitly start it again. That is, if you stop the CSAgent service it does not automatically restart when the system is rebooted.
To stop a service on the Cisco Secure ACS Solution Engine, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type stop followed by a single space and the name of the ACS service you want to stop.
Tip
You can list more than one service to stop; type a single space between each.
Step 3
Press Enter.
Result: The system immediately shows the message:
[service name] is stopping. . .Followed by the message:
[service name] is not running
Starting Solution Engine Services via Serial Console
Note
Starting solution engine services is typically performed from within the HTML user interface.
You can start any of the ACS services from the serial console. The Cisco Secure ACS Solution Engine services include the following:
•
CSAdmin
•
CSAgent
•
CSAuth
•
CSDbSync
•
CSLog
•
CSMon
•
CSRadius
•
CSTacacs
Tip
To list the services and their status, you can use the show command. For more information, see Determining the Status of Solution Engine System and Services via Serial Console.
To start an ACS service, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type start followed by a single space and the name of the ACS service you want to start.
Tip
You can list more than one service to start; type a single space between each.
Step 3
Press Enter.
Result: The system immediately shows the message:
[service name] is starting. . .Followed by the message
[service name] is running
Restarting Solution Engine Services via Serial Console
Note
Restarting solution engine services is a procedure that is typically performed from within the HTML interface.
You can restart any Cisco Secure ACS Solution Engine service from the serial console. Cisco Secure ACS Solution Engine services include the following:
•
CSAdmin
•
CSAgent
•
CSAuth
•
CSDbSync
•
CSLog
•
CSMon
•
CSRadius
•
CSTacacs
Tip
To list the services and their status, you can use the show command. For more information, see Determining the Status of Solution Engine System and Services via Serial Console.
To restart an ACS service, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type restart followed by a single space and the name of the ACS service you want to restart.
Tip
You can list more than one service to restart; type a single space between each.
Step 3
Press Enter.
Result: The system immediately shows the message:
service name is stopping. . .Followed by the messages
service name is not runningservice name is startingservice name is running
Getting Command Help via Serial Console
To obtain a list and description of commands on the Cisco Secure ACS Solution Engine via the serial console, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type help, and then press Enter.
Tip
Press Enter again to scroll through the list of commands, as necessary.
Result: The Cisco Secure ACS Solution Engine displays the following list of commands and their descriptions:
For more information on Cisco Secure ACS Solution Engine commands, see Appendix C, "Command Reference."
Working with System Data
This section details basic data manipulation tasks performed from a serial console connected to the Cisco Secure ACS Solution Engine. This section contains the following procedures:
•
Obtaining Support Logs via the Serial Console
•
Backing Up ACS Data via the Serial Console
•
Restoring ACS Data via the Serial Console
•
Compacting the ACS Solution Engine Database
Obtaining Support Logs via the Serial Console
This section details the procedure for running the support tool. The support tool first collects logs, system Registry information, and other ancillary data, and then compresses the collected information into a single file with the extension .cab. This file can then be sent to support personnel for analysis.
CautionPerforming this procedure stops and restarts all services and will interrupt use of the Cisco Secure ACS Solution Engine.
Note
This procedure is typically performed from within the Cisco Secure ACS Solution Engine HTML interface.
This procedure uses the support command. For more information on this command, see support, page C-16, of Appendix C, "Command Reference." The arguments for the support command include the following:.
To generate a .cab file of log and system Registry information, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type support and the arguments necessary to your purpose.
Step 3
Press Enter.
Step 4
To collect user database information, at the Collect User Data? prompt, type Y and then press Enter.
Step 5
At the Enter FTP Server directory prompt, enter the filepath to the location on your FTP server that you want to send the file to and then press Enter.
Step 6
At the Collect Previous days logs? prompt, type the number of days for which you want to collect information (from 1 to 9999) and press Enter.
Step 7
At the Enter FTP Server Hostname or IP address prompt, enter your FTP server hostname or IP address and press Enter.
Step 8
At the Enter FTP Server Username prompt, enter your FTP server user account name and press Enter.
CautionPerforming this next step begins the procedure that stops and restarts all services and will, therefore, interrupt use of the Cisco Secure ACS Solution Engine.
Step 9
At the Enter FTP Server Password prompt, enter your FTP server password and press Enter.
Result: The Cisco Secure ACS Solution Engine displays a series of messages detailing the writing and dumping of the files and the stopping and starting of services. At file transfer conclusion the system displays the following messages:
Transferring `Package.cab' completedPress any key to finish.This indicates the Cisco Secure ACS Solution Engine has packaged and transferred the .cab file as specified and restarts services.
Step 10
Press Enter.
Result: The system returns to the system prompt.
Exporting Logs
This section details the procedure for exporting Cisco Secure ACS Solution Engine log files to an FTP server for further examination and processing. Using the exportlogs command, you can either enter the name of the log or logs to exported or select log names from a list.
Before you begin
You must have the FTP server address and filepath, as well as the proper credentials for writing to the FTP server (username and password).
CautionPerforming this procedure stops and restarts all services and will interrupt use of the Cisco Secure ACS Solution Engine.
To export log files to an FTP server, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type exportlogs logname.
Tip
You can enter more than one log name separating each with a space. If you enter no log name, after you press Enter, the system displays the names of the log files available for export.
CautionPerforming this procedure stops and restarts all services and will interrupt use of the Cisco Secure ACS Solution Engine.
Step 3
Press Enter.
Step 4
At the prompt, enter the IP address or hostname of the FTP server and press Enter.
Step 5
At the prompt, enter your FTP server username and press Enter.
Step 6
At the prompt, enter your FTP server password and press Enter.
Step 7
At the prompt, enter the FTP server directory filepath and press Enter.
Result: The Cisco Secure ACS Solution Engine exports the specified files to the specified location.
Exporting a List of Groups
This section details the procedure for exporting a list of Cisco Secure ACS Solution Engine user groups to an FTP server for further examination and processing.
Before you begin
You must have the FTP server address and filepath, as well as the proper credentials for writing to the FTP server (username and password).
CautionPerforming this procedure stops and restarts the csauth service and will interrupt use of the Cisco Secure ACS Solution Engine.
To export a user group list to an FTP server, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type exportgroups.
Tip
You can enter the following parameters following the command or in response to subsequent prompts: [server] [username] [filepath]
Step 3
Press Enter.
Result: The system displays the following message:
Command with restart CSAuth. Are you sure you want to continue?
CautionPerforming this procedure stops and restarts the csauth service and will interrupt use of the Cisco Secure ACS Solution Engine.
Step 4
To proceed, type Y and press Enter.
Step 5
At the Enter FTP Server Hostname or IP Address prompt, enter the FTP server IP address or hostname and press Enter.
Step 6
At the Directory: prompt, enter the FTP server filepath and press Enter.
Step 7
At the Usnername: prompt, enter your FTP server username and press Enter.
Step 8
At the Password: prompt, enter your FTP server password and press Enter.
Result: The Cisco Secure ACS Solution Engine exports the group list file to the specified location. When done the system displays following message:
Transferring `groups.txt' completedThe system prompt returns.
Exporting a List of Users
This section details the procedure for exporting a list of Cisco Secure ACS Solution Engine users to an FTP server for further examination and processing.
Before you begin
You must have the FTP server address and filepath, as well as the proper credentials for writing to the FTP server (username and password).
CautionPerforming this procedure stops and restarts the csauth service and will interrupt use of the Cisco Secure ACS Solution Engine.
To export a list of users to an FTP server, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type exportusers.
Tip
You can enter the following parameters following the command or in response to subsequent prompts: [server] [username] [filepath]
Step 3
Press Enter.
Result: The system displays the following message:
Command with restart CSAuth. Are you sure you want to continue?
CautionPerforming this procedure stops and restarts the csauth service and will interrupt use of the Cisco Secure ACS Solution Engine.
Step 4
To proceed, type Y and press Enter.
Step 5
At the Enter FTP Server Hostname or IP Address prompt, enter the FTP server IP address or hostname and press Enter.
Step 6
At the Directory: prompt, enter the FTP server filepath and press Enter.
Step 7
At the Username: prompt, enter your FTP server username and press Enter.
Step 8
At the Password: prompt, enter your FTP server password and press Enter.
Result: The Cisco Secure ACS Solution Engine exports the list of users file to the specified location. When done the system displays following message:
Transferring `users.txt' completedThe system prompt returns.
Backing Up ACS Data via the Serial Console
This section details how to use the serial console to backup Cisco Secure ACS Solution Engine data to an FTP server.
Note
This procedure is typically performed from within the HTML interface.
During backup, AAA services are interrupted and Cisco Secure ACS Solution Engine data is packaged and sent in a file to an FTP server. You may choose to encrypt this file package. For information on how to restore the backup data to the system, see Restoring ACS Data via the Serial Console.
Before you begin
You must have the FTP server address and filepath, as well as the proper credentials for writing to the FTP server (username and password).
CautionThis procedure interrupts the use of the Cisco Secure ACS Solution Engine for AAA services.
To export Cisco Secure ACS Solution Engine data to an FTP server, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type backup.
Tip
You can enter the following parameters following the command or in response to subsequent prompts: [server] [username] [filepath]
Step 3
Press Enter.
Step 4
At the Enter FTP Server Hostname or IP Address: prompt, enter the FTP server IP address or hostname and press Enter.
Step 5
At the Enter FTP Server Directory: prompt, enter the FTP server filepath and press Enter.
Step 6
At the Enter FTP Server Username: prompt, enter your FTP server username and press Enter.
Step 7
At the Enter FTP Server Password: prompt, enter your FTP server password and press Enter.
Step 8
At the File: prompt, enter the name you want to give the backup file and then press Enter.
Step 9
At the Encrypt Backup File? (Y or N) prompt, type Y to encrypt the backup file or N not to encrypt it, and then press Enter.
CautionThis procedure interrupts the use of the Cisco Secure ACS Solution Engine for AAA services.
Step 10
If you previously chose to encrypt the backup file, at the Encryption Enter FTP Server Password: prompt, type a password and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following messages:
Backing up now . . .All running services will be stopped and restarted automatically.Are you sure you want to proceed? (y/Y = proceed)Step 11
To proceed, type Y and press Enter.
Result: The Cisco Secure ACS Solution Engine exports the backup file to the specified location and displays messages regarding the progress of the backup. Before returning to the system prompt, the following message signifies the completion of the backup process:
Transferring xxx completed.
Restoring ACS Data via the Serial Console
This section details how use the serial console to restore Cisco Secure ACS Solution Engine data from an FTP server after having performed a backup. For more information on backing up Cisco Secure ACS Solution Engine data, see Backing Up ACS Data via the Serial Console.
Note
This procedure is typically performed from within the HTML interface.
Before you begin
You must have the FTP server address and filepath, as well as the proper credentials for writing to the FTP server (username and password). You also need the name of the backup file and, if the backup was encrypted, the decryption password.
CautionThis procedure interrupts the use of the Cisco Secure ACS Solution Engine for AAA services.
CautionThis procedure overwrites current system data and replaces it with the backup data.
To restore Cisco Secure ACS Solution Engine data from an FTP server, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type restore.
Tip
You can enter the following parameters following the command or in response to subsequent prompts: [server] [username] [filepath]
Step 3
Press Enter.
Step 4
At the Enter FTP Server Hostname or IP Address: prompt, enter the FTP server IP address or hostname and press Enter.
Step 5
At the Enter FTP Server Directory: prompt, enter the FTP server filepath and press Enter.
Step 6
At the Enter FTP Server Username: prompt, enter your FTP server username and press Enter.
Step 7
At the Enter FTP Server Password: prompt, enter your FTP server password and press Enter.
Step 8
At the File: prompt, enter the name of the backup file and then press Enter.
Step 9
At the Select Components to Restore: User and Group Database: prompt, to restore the user and group database type Y and then press Enter.
Step 10
At the CiscoSecure ACS System Configuration: (Y or N) prompt, to restore the system configuration data type Y and then press Enter.
Step 11
At the Decrypt Backup file? (Y or N) prompt, if you previously encrypted the backup file, type Y and then press Enter.
Step 12
If you previously chose to decrypt the backup file, at the Encryption Password: prompt, type the FTP password, and then press Enter.
Note
The system displays a warning message:
Reloading a system backup will overwrite ALL current configuration information. All services will be stopped and started automaticallyStep 13
At the Are you sure you want to proceed? (Y or N) prompt, type Y and then press Enter.
Result: The Cisco Secure ACS Solution Engine receives the backup file from the specified location and displays messages regarding the restoration. You may see warnings about components not included in the backup file. For example, if Cisco Secure ACS Solution Engine has no shared profile components configured, you see a message about DCS (device command sets) not on the backup. This is normal.
When completed the system displays the message:
Done
Compacting the ACS Solution Engine Database
This section details the procedure you perform to compact the Cisco Secure ACS Solution Engine user database. Like many relational databases, the Cisco Secure ACS Solution Engine user database handles the deletion of records by marking deleted records as deleted but not removing the record from the database. Over time, your Cisco Secure ACS Solution Engine user database may be substantially larger than is required by the number of users it contains. To reduce the CiscoSecure user database size, you can compact it periodically.
Database compaction includes three basic operations that take place automatically when you issue the dbcompact command:
•
A database dump occurs.
•
The database is initialized, thus removing deleted records.
•
The dumped data is loaded back to the database.
Performing this procedure can reduce the amount of space that the database takes up and improve the database response time.
CautionCompacting the CiscoSecure user database requires that you stop the CSAuth service. While CSAuth is stopped, no users are authenticated.
Note
This procedure is typically performed from within the Cisco Secure ACS Solution Engine HTML user interface.
To compact the Cisco Secure ACS Solution Engine use database, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type dbcompact.
Result: The system displays the following message:
Command will restart CSAuth. Are you sure you want to continue? (Y/N):
CautionCompacting the CiscoSecure user database requires that you stop the CSAuth service. While CSAuth is stopped, no users are authenticated.
Step 3
Type Y, and then press Enter.
Result: The system displays a series of messages similar to the following:
Stopping service: CSAuthDoneInitializing database . . .Loading database from dump.txt . . .DoneStarting service: CSAuthFinally, the system returns to displaying the system prompt.
Reconfiguring Solution Engine System Parameters
This section details basic reconfiguration tasks performed from a serial console connected the Cisco Secure ACS Solution Engine. This section contains the following procedures:
•
Resetting the Solution Engine Administrator Password
•
Resetting the Solution Engine Administrator Name
•
Reconfiguring the Solution Engine IP Address
•
Setting the System Time and Date Manually
•
Setting the System Time and Date with NTP
•
Setting the Solution Engine System Domain
•
Setting the Solution Engine System Hostname
Resetting the Solution Engine Administrator Password
There is always a single set of Cisco Secure ACS Solution Engine administrator credentials consisting of administrator name and password. Unlike other ACS administrative accounts, this unique administrative account is granted all privileges, cannot be deleted, and is not listed in the Administrators table of the Administrative Control page in the Cisco Secure ACS HTML user interface.
You can reset the Cisco Secure ACS Solution Engine administrator name, the administrator password, or both. This procedure details how to reset the password after having logged on with the existing credentials. To reset the administrator name see Resetting the Solution Engine Administrator Name.
If you do not have the existing Cisco Secure ACS Solution Engine administrator login credentials to log in with, you must have the recovery CD ROM to reset these credentials. For information on resetting the administrator login and password without first logging in, see Recovering from Loss of Administrator Credentials.
To reset the Cisco Secure ACS Solution Engine administrator login credentials, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type set password and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following prompt:
Enter old password:Step 3
Type the password, and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following prompt:
Enter new account name:Step 4
Type the new account name, and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following prompt:
Enter new passwordStep 5
Type the new password, and then press Enter.
Note
The new password must not contain the administrator account name, must contain a minimum of 6 characters, and it must include a mix of at least 3 character types (numerals, special characters, upper case letters, and lowercase letters). Each of the following examples is acceptable: 1PaSsWoRd, *password44, Pass*word.
Result: The Cisco Secure ACS Solution Engine displays the following prompt:
Reenter new passwordStep 6
Type the new password again, and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following prompt:
Password is set successfully. Administrator account name is set to _____
Resetting the Solution Engine Administrator Name
There is always a single set of Cisco Secure ACS Solution Engine administrator credentials consisting of administrator name and password. Unlike other ACS administrative accounts, this unique administrative account is granted all privileges, cannot be deleted, and is not listed in the Administrators table of the Administrative Control page in the Cisco Secure ACS HTML user interface.
You can reset the Cisco Secure ACS Solution Engine administrator name, the administrator password, or both. This procedure details how to reset the administrator name after having logged on with the existing credentials. To reset the password, see Resetting the Solution Engine Administrator Password.
If you do not have the existing Cisco Secure ACS Solution Engine administrator login credentials with which to log in, you must have the recovery CD ROM to reset these credentials. For information on resetting the administrator login and password without first logging on, see Recovering from Loss of Administrator Credentials.
To reset the Cisco Secure ACS Solution Engine administrator name, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type set admin, and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the Set administrator's name prompt.
Step 3
Type the new administrator name, and then press Enter.
Step 4
At the Set administrator name again prompt, type the administrator name again and then press Enter.
Result: The system displays the following message on the console:
Administrator name is set successfully.
Reconfiguring the Solution Engine IP Address
Typically, you configure the IP address only once, during initial configuration. See Configuring the Cisco Secure ACS Solution Engine, page 3-16.
CautionReconfiguring the IP address may cause other network devices to fail to recognize the Cisco Secure ACS Solution Engine.
CautionReconfiguring the IP address causes services to restart. AAA services to users will be interrupted.
Note
To set or change the IP address of your Cisco Secure ACS Solution Engine, it must be connected to a working Ethernet connection.
To reconfigure the IP address, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
Type set ip, and then press Enter.
Step 3
At the Use Static IP Address [Y]: prompt, type Y for yes or N for No, and then press Enter.
Step 4
If you answered No to using a static IP address, the system displays a confirmation of DHCP and the message IP Address is reconfigured. Continue the procedure with Step 5.
If you responded Yes in the previous step to use a static IP address, do the following:
a.
To specify the Cisco Secure ACS Solution Engine IP address, at the IP Address [xx.xx.xx.xx]: prompt, type the IP address, and then press Enter.
b.
At the Subnet Mask [xx.xx.xx.xx]: prompt, type the subnet mask, and then press Enter.
c.
At the Default Gateway [xx.xx.xx.xx]: prompt, type the default gateway, and then press Enter.
d.
At the DNS Servers [xx.xx.xx.xx]: prompt, type the address of any DNS servers you intend to use (separate each by a single space), and then press Enter.
Result: The system displays the new configuration information and the following message:
IP Address is reconfigured.Step 5
Review the information presented and, at the Confirm the changes? [Y]: prompt, press Enter.
Result: The Cisco Secure ACS Solution Engine restarts. The system displays the following message:
New ip address is set.Step 6
At the prompt, Test network connectivity [Yes]:, type Y, and then press Enter.
Tip
This step executes a ping command to ensure the connectivity of the Cisco Secure ACS Solution Engine.
Step 7
At the prompt, Enter hostname or IP address:, type the IP address or hostname of a device connected to the Cisco Secure ACS Solution Engine and then press Enter.
Result: If successful, the system displays the ping statistics. Once again the system displays the prompt: Test network connectivity [Yes]:.
Step 8
If network connectivity is proven okay in the previous two steps, at the prompt, Test network connectivity [Yes]:, type N, and then press Enter.
Tip
The system will continue to provide you with the opportunity to test network connectivity until you answer no. This gives you an opportunity, if required, to correct network connections or retype the IP address.
Result: The Cisco Secure ACS Solution Engine restarts services, after which, it displays the system prompt.
Setting the System Time and Date Manually
You can set and maintain the system date and time using either of two methods:
•
Set the time and date manually.
•
Assign a network time protocol (NTP) server with which the system synchronizes its date and time.
To set the Cisco Secure ACS Solution Engine system time and date using an NTP, see Setting the System Time and Date with NTP.
To set the Cisco Secure ACS Solution Engine system time and date manually, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type set time, and then press Enter.
Result: The system displays the following message on the console:
Current Date Time Setting:Time Zone: (GMT -xx:xx) XXX TimeDate and Time: mm/dd/yyyy hh/mm/ssNTP Servers: ("Ntp Synchronization Disabled" - or -a list of NTP servers)Change Date & Time Setting? [N]Step 3
To set the time zone, time, or date type Y, and then press Enter.
Result: The system displays a list of indexed time zones and the following message:
[xx] (GMT -xx:xx) XXX Time.Enter desired time zone index (0 for more choices) [x]:Step 4
Enter the desired time zone index number from the time zone setting list, and then press Enter.
Tip
You can also type 0 (zero) and press Enter to see more time zone index numbers.
Result: The system displays the new time zone.
Step 5
At the Synchronize with NTP Server? prompt, type N, and then press Enter.
Step 6
At the Enter date [mm/dd/yyyy]: prompt, type the date, and then press Enter.
Step 7
At the Enter time [hh:mm:ss]: prompt, type the current time, and then press Enter.
Result: The system time is reset.
Setting the System Time and Date with NTP
You can set and maintain the system date and time using either of two methods:
•
Set the time and date manually.
•
Assign a network time protocol (NTP) server with which the system synchronizes its date and time. (You can configure backup NTP servers if you desire.)
To set the Cisco Secure ACS Solution Engine system time and date manually, see Setting the System Time and Date Manually.
To set the Cisco Secure ACS Solution Engine system time and date with NTP, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type set time, and then press Enter.
Result: The system displays the following message on the console:
Current Date Time Setting:Time Zone: (GMT -xx:xx) XXX Time Date and Time: mm/dd/yyyy hh/mm/ss NTP Servers: ("Ntp Synchronization Disabled" - or - List of NTP servers)Change Date & Time Setting? [N]Step 3
To set the time zone, time, or date type Y, and then press Enter.
Result: The system lists indexed time zones and the following message:
[xx] (GMT -xx:xx) XXX Time.Enter desired time zone index (0 for more choices) [x]:Step 4
Enter the desired time zone index number from the time zone setting list, and then press Enter.
Tip
You can also type 0 (zero) and press Enter to see more time zone index numbers; or simply press Enter to accept the existing time zone.
Result: The system displays the time zone setting.
Step 5
At the Synchronize with NTP Server? prompt, type Y, and then press Enter.
Step 6
At the Enter NTP Server IP Address(es): prompt, enter the IP address of the NTP server you want to use, and then press Enter.
Tip
If you want to configure multiple NTP servers, at the Enter NTP Server IP Address: prompt, enter multiple IP addresses each separated by a space.
Result: The system displays the following message on the console:
Successfully synchronized with NTP serverCurrent Date/Time Setting:Time Zone: XXXDate & Time:NTP servers:
Setting the System Timeout
You can set a system timeout. This is the number of minutes with no activity on the serial console that can pass before the console login times out. To set the Cisco Secure ACS Solution Engine system timeout, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type set timeout followed by a single space and the timeout period in minutes.
Step 3
Press Enter.
Result: The system sets the new timeout period.
Setting the Solution Engine System Domain
You can set the system DNS domain from the serial console. To set the Cisco Secure ACS Solution Engine system domain, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type set domain followed by a single space and the domain name.
Step 3
Press Enter.
Result: The system displays the following confirmation message:
You should reboot appliance for the change to take effect.
Setting the Solution Engine System Hostname
CautionPerforming this procedure stops and restarts all services and will interrupt use of the Cisco Secure ACS Solution Engine.
You can set the system hostname. To set the Cisco Secure ACS Solution Engine system hostname, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 2
At the system prompt, type set hostname followed by a single space and the hostname.
Tip
You can use up to 15 letters and numbers but no spaces.
Step 3
Press Enter.
Result: The system restarts all services and the hostname is reset. The system then displays the following confirmation message:
You should reboot appliance for the change to take effect.(The hostname is then reset after system reboot.)
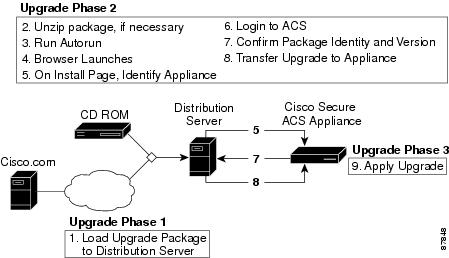
Upgrading the Solution Engine
This section describes how to load and install a Cisco Secure ACS Solution Engine upgrade image from the command line interface of the serial console.
Upgrading the Cisco Secure ACS Solution Engine typically involves the following three steps:
1.
Obtain the upgrade package from Cisco Systems and load it onto a distribution server in your network. This can be done either by employing an upgrade CD or downloading the upgrade package from Cisco.com.
2.
Load the upgrade image onto the Cisco Secure ACS Solution Engine from the distribution server on your network. You can do this either from within the HTML interface, or from the serial console. The Cisco Secure ACS Solution Engine verifies the files transferred to ensure that they have not been corrupted. For more information on performing this step from the HTML interface, see the User Guide for Cisco Secure ACS Appliance. To load the upgrade image using the command line interface, use the following procedure: Upgrading the Solution Engine.
3.
Finally, apply the Cisco Secure ACS Solution Engine system upgrade. You can do this either from within the HTML interface, or from the serial console. For more information, see Applying a Solution Engine System Upgrade.
This process is shown in Figure 4-1.
Figure 4-1 Solution Engine Upgrade Process
Transferring an Upgrade Package to the Solution Engine via Serial Console
Use this procedure to transfer an upgrade package from a distribution server to a Cisco Secure ACS Solution Engine.
Before you begin
You must have acquired the upgrade package and selected a distribution server. For more information, see Upgrading the Solution Engine.
Note
This procedure is typically performed from within the HTML interface. For more information, see the User Guide for Cisco Secure ACS Solution Engine Version 3.3.
To transfer an upgrade to your Cisco Secure ACS Solution Engine, follow these steps:
Step 1
If the distribution server uses Microsoft Windows, follow these steps:
a.
If you have acquired the upgrade package on CD, insert the CD in a CD ROM drive on the distribution server.
Tip
You can also use a shared CD drive on a different computer. If you do so and autorun is enabled on the shared CD drive, the HTTP server included in the upgrade package runs on the other computer, not the distribution server.
b.
If either of the following conditions are true:
•
You have acquired the upgrade package as a compressed file.
•
Autorun is not enabled on the CD ROM drive.
locate the autorun.bat file on the CD or in the directory that you extracted the compressed upgrade package in and run it.
Result: The HTTP server starts.
Step 2
If the distribution server uses Sun Solaris, follow these steps:
a.
If you have acquired the upgrade package on CD, insert the CD in a CD ROM drive on the distribution server.
b.
Locate the autorun.sh file on the CD or in the directory that you extracted the compressed upgrade package in.
c.
Run autorun.sh.
Result: The HTTP server starts. Messages from autorun.sh appear in a console window. Two web browser windows appear. The browser window titled Appliance Upgrade contains the Enter solution engine hostname or IP address box. The browser window titled New Desktop contains buttons labeled Install Next and Stop Distribution Server. You can use the New Desktop window to start transfers to other solution engines.
Step 3
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
Step 4
At the system prompt, type download followed by the IP address of the distribution server.
Step 5
Press Enter.
Result: The system displays a number of messages including, finally, the following confirmation message:
Successfully downloaded the package. Run upgrade command to install the package.
Applying a Solution Engine System Upgrade
You use this procedure to install upgrades on the Cisco Secure ACS Solution Engine. Upgrades may include the installation of a full software revision or simply the installation of a software patch.
Before you begin
You must have an upgrade to install. For information on checking the availability of and obtaining an upgrade, see the User Guide for Cisco Secure ACS Solution Engine Version 3.3. For information on how to load the upgrade package onto the Cisco Secure ACS Solution Engine see, Transferring an Upgrade Package to the Solution Engine via Serial Console.
Also, if CSAgent is running, you must disable it before you issue the upgrade command. For information on stopping services see Stopping Solution Engine Services via Serial Console.
Finally, because the Cisco Secure ACS Solution Engine is non-operational during the upgrade process, you may want to schedule the upgrade for a time when its absence online will have the least impact.
To apply a Cisco Secure ACS Solution Engine system upgrade, follow these steps:
Step 1
Log in to the Cisco Secure ACS Solution Engine. For more information, see Logging In to the Solution Engine via Serial Console.
CautionThe Cisco Secure ACS Solution Engine will be non-operational during the upgrade process.
Note
If CSAgent is running, you must disable it before you issue the upgrade command.
Step 2
At the system prompt, type upgrade.
Step 3
Press Enter.
Result: The system displays the following confirmation message:
Installing the patch could adversely affect the system. Do you still want to continue?---y(yes), n(no)Step 4
Type Y to continue.
Result: The system displays a series of messages that include:
---Extracting------Verifying . . .---
Tip
If there is no upgrade package loaded on the Cisco Secure ACS Solution Engine, you will see a message that requests that you download an upgrade package.
Step 5
Depending on your certification authority settings, you may see a warning message similar to the following:
Upgrade package was not verifiedApplying this upgrade package may corrupt the applianceContinue at your own risk!Continue ---y(yes), n(no)If you do see this prompt, type y to continue.
Result: The system displays a series of messages that may include:
Installing Cisco Secure ACS Version: x.x.xUpgrading . . .ACS Installation was successfulSuccessfully upgraded Cisco Secure ACS Version x.x.xCompleted upgrade and system will be rebooted.
Note
During this installation of the upgrade, the system reboots twice. Therefore, when the system displays the following message:
Reboot will occur in a few minutes.
Login:
Continue to wait until you see the final message:
Status: Appliance is functioning normally.
This message indicates that the upgrade is complete.
Tip
To obtain system information, including the current version, see Determining the Status of Solution Engine System and Services via Serial Console.
Patch Rollback
Removing Installed Patches
Use this procedure to uninstall one or more patches and to roll back the Cisco Secure ACS Solution Engine to the version that existed before the patch installation.
To roll back a Cisco Secure ACS Solution Engine system patch, follow these steps:
Step 1
Connect a console to the Cisco Secure ACS Solution Engine console port. For the location of the console port, see Figure 1-3 on page 1-5.
Step 2
Type rollback and the name of the patch application that you want rolled back. Then press Enter.
Tip
If you do not include the specific patch application name as a parameter following the rollback command, the system displays the list of patches that can be rolled back. Use this list to identify the patch application name, type rollback followed by the patch application name, and then press Enter.
Result: The system displays the following confirmation message:
Are you sure you want to rollback [patch name]?)(Y/N):Step 3
Type Y to continue.
Result: The system displays a series of messages that include:
Rolling patch backRollback process initiated successfullySuccessfully rolled back `[patch name]' to 0.
Tip
To obtain system information, including the current version, see Determining the Status of Solution Engine System and Services via Serial Console.
Understanding the CSAgent Patch
In Cisco Secure ACS Solution Engine Version 3.3 the CSAgent service is implemented as a pre-installed patch. You must stop CSAgent before you can install any patch or upgrade. Although, as a patch, the CSAgent can be rolled back, the preferred method for disabling this service is simply to stop it. Once stopped, the CSAgent service does not restart when the system is restarted; you must explicitly restart the service for it to operate. For more information, see User Guide for Cisco Secure ACS Solution Engine Version 3.3.
Recovery Management
Cisco Secure ACS Solution Engine functionality includes two procedures that the administrator can perform using the Cisco Secure ACS Solution Engine Recovery CD ROM. These procedures, detailed in this section, include the following:
•
Recovering from Loss of Administrator Credentials
•
Re-Imaging the Solution Engine Hard Drive
Recovering from Loss of Administrator Credentials
If you cannot log in to the system because you have lost the account name or password for the Cisco Secure ACS Solution Engine administrator account, perform this procedure. In this procedure you use the Cisco Secure ACS Solution Engine Recovery CD ROM to access the system via the serial console and reset the administrator login credentials.
You should understand the following regarding the Cisco Secure ACS Solution Engine administrator login credentials:
•
There is only one set of administrator login credentials at one time.
•
Administrator login credentials are set (that is, changed from the default) during initial configuration.
•
Administrator login credentials may be reset. For more information, see Resetting the Solution Engine Administrator Password.
•
This recovery procedure entails replacing the administrator login credentials with a new account name and password.
To reset the administrator login credentials, follow these steps:
Step 1
Connect a console to the Cisco Secure ACS Solution Engine console port. For the location of the console port, see Figure 1-3 on page 1-5.
Step 2
Power on the console.
Step 3
Place the Cisco Secure ACS Solution Engine Recovery CD ROM into the solution engine CD ROM drive.
Step 4
Power on the Cisco Secure ACS Solution Engine. (Or if already running, reboot the solution engine. For more information, see Rebooting the Solution Engine via Serial Console.)
Result: The system displays the following message on the console:
ACS Appliance Recovery Options[1] Reset administrator account[2] Restore hard disk image from CD[3] Exit and rebootEnter menu item number: [ ]Step 5
Type 1.
Result: The system displays the following prompt:
Hit the Return key to log in.Step 6
Type Y.
Result: The system displays the following prompt:
Please remove this recovery CD from the drive,then hit RETURN to restart the system:Step 7
Remove the recovery CD from the drive, and then press Enter.
Result: The system reboots, and then displays the system version information followed by:
Status: The appliance is functioning properlyLogin:Step 8
Type Administrator, and then press Enter.
Note
The password is case sensitive.
Step 9
At the password prompt, type setup, and then press Enter.
Result: The system displays the system prompt.
Step 10
At the Enter new account name: prompt, type the name of the Cisco Secure ACS Solution Engine administrator, and then press Enter.
Step 11
At the Enter new password: prompt, type the new Cisco Secure ACS Solution Engine password, and then press Enter.
Note
The new password must contain a minimum of 6 characters, and it must include a mix of at least 3 character types (numerals, special characters, upper case letters, and lower case letters). Each of the following examples is acceptable: 1PaSsWoRd, *password44, Pass*word.
Step 12
At the Enter new password again: prompt, type the new Cisco Secure ACS Solution Engine password, and then press Enter.
Result: The system displays the following message on the console:
Password is set successfully.
Re-Imaging the Solution Engine Hard Drive
Use the Cisco Secure ACS Solution Engine Recovery CD ROM to re-image the Cisco Secure ACS Solution Engine if necessary. This will destroy all data and install a new image.
To re-image your Cisco Secure ACS Solution Engine, follow these steps:
CautionPerforming this procedure destroys all data stored on the Cisco Secure ACS Solution Engine.
Step 1
Connect a console to the Cisco Secure ACS Solution Engine console port. For the location of the console port, see Figure 1-3 on page 1-5.
Step 2
Put the Recovery CD in the Cisco Secure ACS Solution Engine CD-ROM drive. For the location of the CD-ROM drive, see Figure 1-2 on page 1-4.
Step 3
Power on the Cisco Secure ACS Solution Engine. (Or if the solution engine is already running, reboot it. For more information, see Rebooting the Solution Engine via Serial Console.
Result: The Cisco Secure ACS Solution Engine displays the following message on the console:
ACS Appliance Recovery Options[1] Reset administrator account[2] Restore hard disk image from CD[3] Exit and rebootEnter menu item number: [ ]Step 4
Type 2, and then press Enter.
Result: The Cisco Secure ACS Solution Engine displays the following message on the console:
This operation will completely erase the hard drive. Press `Y' to confirm, any other key to cancel: __
CautionThe next step erases the Cisco Secure ACS Solution Engine hard drive. You will permanently lose all system data that you have not backed up.
Step 5
Type Y.
Result: The Cisco Secure ACS Solution Engine processes the new image (this may take more than 2 minutes) while displaying odd characters and then displays the following message on the console:
The system has been reimaged successfully. Please remove this recovery CD from the drive, then hit RETURN to restart the system:Step 6
Remove the Recovery CD from the Cisco Secure ACS Solution Engine.
Step 7
Press Enter to restart the Cisco Secure ACS Solution Engine.
Result: The Cisco Secure ACS Solution Engine reboots, performs some configurations, and reboots again. The configurations that occur after the first reboot take a significant amount of time, during which there is no feedback; this is normal system behavior.
Note
After re-imaging the solution engine hard drive, you must once again perform initial configuration of the Cisco Secure ACS Solution Engine. For detailed instructions, see Configuring the Cisco Secure ACS Solution Engine, page 3-16.
Migrating to Cisco Secure ACS Solution Engine
Migrating from Cisco Secure ACS for Windows Server to Cisco Secure ACS Solution Engine uses the backup and restore features of Cisco Secure ACS. Backup files produced by Cisco Secure ACS for Windows Server are compatible with Cisco Secure ACS Solution Engine, provided that both are using the same version of Cisco Secure ACS software.
Depending upon what version of Cisco Secure ACS for Windows Server is used and the operating system that it runs on, the migration process varies. For example, if Cisco Secure ACS runs on Windows NT 4.0, the procedure below will advise you when it is necessary to upgrade to Windows 2000 Server. Because the use of the backup and restore features is only supported between Cisco Secure ACSes of the same version, you must use Cisco Secure ACS for Windows Server, version 3.3, to transfer data from Cisco Secure ACS for Windows Server to Cisco Secure ACS Solution Engine. Cisco Secure ACS for Windows Server, version 3.3, supports Windows 2000 Server and Windows Server 2003, not Windows NT 4.0. See the following procedure for more details.
Before You Begin
Before upgrading or transferring data, back up your original Cisco Secure ACS and save the backup file in a location on a drive that is not local to the computer running Cisco Secure ACS.
To migrate from a Windows version of Cisco Secure ACS to Cisco Secure ACS Solution Engine, follow these steps:
Step 1
Set up the appliance, following the steps in Chapter 3, "Installing and Configuring Cisco Secure ACS Solution Engine."
Step 2
Upgrade Cisco Secure ACS for Windows Server to version 3.3. If you do not have a license for version 3.3, you can use the trial version, available at http://www.cisco.com/pcgi-bin/tablebuild.pl/acs-win-3des.
If you run Cisco Secure ACS on Windows NT 4.0, upgrade to Cisco Secure ACS version 3.0, and then migrate to Windows 2000 Server before upgrading to Cisco Secure ACS version 3.3. Cisco Secure ACS version 3.3 does not support Windows NT 4.0 and Cisco Secure ACS version 3.0 is the most recent version of Cisco Secure ACS that supports Windows NT 4.0. For information about upgrading to Cisco Secure ACS version 3.0 or about migrating to Windows 2000 Server, see Installing Cisco Secure ACS 3.0 for Windows 2000/NT Servers. You can acquire the trial version of Cisco Secure ACS version 3.0 at http://www.cisco.com/pcgi-bin/tablebuild.pl/acs-win-3des.
Note
For information about the versions of Cisco Secure ACS that we used to test the upgrade process, see the Release Notes. The most recent version of the Release Notes are on Cisco.com, accessible from the following URL:
http://www.cisco.com/univercd/cc/td/doc/product/access/acs_soft/
csacs4nt/index.htmStep 3
In the HTML interface of Cisco Secure ACS for Windows Server, version 3.3, use the Cisco Secure ACS Backup feature to back up the database. For more information about the Cisco Secure ACS Backup feature, see the User Guide for Cisco Secure ACS for Windows Server, version 3.3.
Step 4
Copy the backup file from the computer running Cisco Secure ACS for Windows Server, version 3.3, to a directory on an FTP server. The directory must be accessible from the FTP root directory. Cisco Secure ACS Solution Engine must be able to contact the FTP server. Any gateway devices must permit FTP communication between the appliance and the FTP server.
Step 5
In the HTML interface of Cisco Secure ACS Solution Engine, use the Cisco Secure ACS Restore feature to restore the database. For more information about restoring databases, see the User Guide for Cisco Secure ACS Solution Engine, version 3.3.
The Cisco Secure ACS Solution Engine contains the original configuration of the Windows version Cisco Secure ACS that you migrated from.
Step 6
Continuing in the HTML interface of the Cisco Secure ACS Solution Engine, verify the settings for the "(Default)" entry in the Proxy Distribution Table are correct. To do so, select Network Configuration > (Default) and ensure that the Forward To list contains the entry for the appliance.
Step 7
If you want to replace the computer running Cisco Secure ACS for Windows Server with Cisco Secure ACS Solution Engine, you must change the IP address of the appliance to that of the computer running Cisco Secure ACS for Windows Server.
Note
If you do not change the IP address of the Cisco Secure ACS Solution Engine to the address of the computer running Cisco Secure ACS for Windows Server, you must reconfigure all AAA clients to use the IP address of the Cisco Secure ACS Solution Engine.
To change the IP address of the Cisco Secure ACS Solution Engine, follow these steps:
a.
Record the IP address of the computer running Cisco Secure ACS for Windows Server.
b.
Change the IP address of the computer running Cisco Secure ACS with Windows Server to a different IP address.
c.
Change the IP address of the Cisco Secure ACS Solution Engine to the IP address previously used by the computer running Cisco Secure ACS for Windows Server. This is the IP address you recorded in step a. For detailed steps, see Reconfiguring the Solution Engine IP Address.

 Feedback
Feedback