Cisco TelePresence Content Server Release 6.x Public SSL Certificate Installation Guide
Available Languages
Table of Contents
Cisco TelePresence Content Server Release 6.x Public SSL Certificate Installation Guide
Create Certificate Signing Request
Submit Certificate for Signing
Self-Signed Certificate Installation
Obtaining Documentation and Submitting a Service Request
Cisco TelePresence Content Server Release 6.x Public SSL Certificate Installation Guide
This document provides instructions for installing a single-use domain name or subdomain SSL certificate, or a self-signed certificate, on a Cisco TelePresence Content Server Release 6.x.
SSL Certificate Installation
Complete these steps to install a single-use SSL certificate on the Content Server:
1.
Create Certificate Signing Request
2.
Submit Certificate for Signing
3.
Complete Certificate Request
Contact a certificate authority (CA) to request an SSL certificate for use with Window Server 2008 R2 Internet Information Services Version 7 (IIS7). You can use any CA, these four are among the best known:
- VeriSign—www.verisign.com
- GoDaddy—www.godaddy.com
- Comodo—www.comodo.com
- Network Solutions—www.networksolutions.com
Create Certificate Signing Request
Follow these steps to create a certificate signing request (CSR or certification request) to apply for a digital identity certificate.
Step 1
Open a Remote Desktop Connection to the Content Server. Log in as an administrator.
Step 2
Go to Start > Administrative Tools > Internet Information Services (IIS) Manager .
Step 3
In the Features view, double-click Server Certificates .
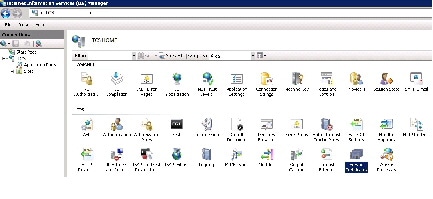
Step 4
In the Actions pane, click Create Certificate Request .

Step 5
In the Distinguished Name Properties window:
a.
Enter the Common name for the Content Server. The Common name is the FQDN used to access the Content Server from within your organization.

Note Do not use the Content Server IP address for the Common name. For the certificate to function properly, enter the Content Server FQDN.
Some certificate authorities provide Unified Communications certificates that allow the listing of multiple Subject Alternative Names (SAN) to secure multiple distinct hostnames in one certificate. The SAN option is not available when using the IIS certificate utility. The IIS utility supports only single-use certificates.
b.
Enter the Organization , Organizational unit , City , State , and Country . Click Next .
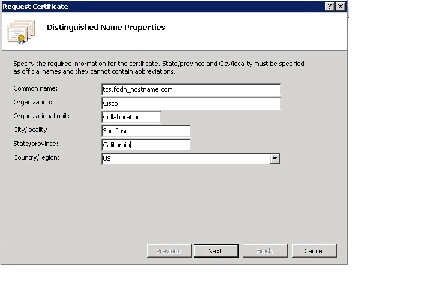
Step 6
In the Cryptographic Service Provider Properties window, enter the following:
a.
In the Cryptographic service provider drop-down menu, choose Microsoft RSA SChannel Cryptographic Provider .
b.
In the Bit length field, enter a key-length value that can be used by the provider. A longer bit length is more secure, but it can affect performance.
Step 7
In the File Name window, enter a filename for the certificate request < C:\Users\Administrator\Desktop\cert_request.txt >. The Certificate Authority that you choose will accept the request and “sign” it for you.
Step 8
Open the file that you created in Step 7. Store the complete request including the “Begin” and “End” sections and all dashes in a text file. Do not include any additional carriage returns after the final dash. The file will look like the following example. Click Finish .

Submit Certificate for Signing
Step 1
Request an SSL certificate from a certificate authority (CA). See Before You Begin for a list of recommended CA vendors.
Follow the CA instructions to create an account and order an SSL certificate.
Step 2
When you reach the CA screen that requests the certificate signing, paste (or upload) the text file that you created in Step 8.

Step 3
When the CA completes the signing process (and optionally, verifies the domain ownership), download the certificate in the IIS7 server format.
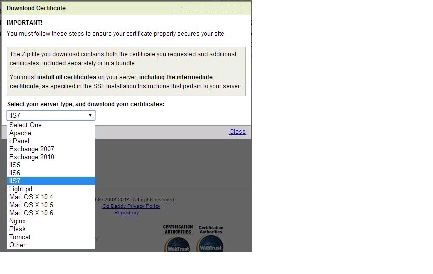
Step 4
The CA will provide two files: the intermediate certificate (PKCS #7 Certificates) and the server certificate (Security Certificate). Each certificate must be installed separately to complete the signing process. Copy both files to the Content Server IIS.

Note Make certain that you properly identify and copy the two certificate files. The intermediate certificate PKCS #7 Certificates includes all of the necessary intermediate certificates. The Security Certificate is the server certificate.
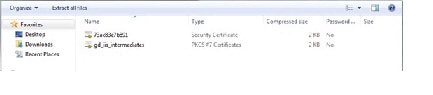
Step 5
Go to Start > Run > MMC (Microsoft Management Console). Choose File > Add/Remove Snap-in .
Step 6
Choose Certificates > Add to add the Console Root folder to the Selected snap-ins window. Click OK .
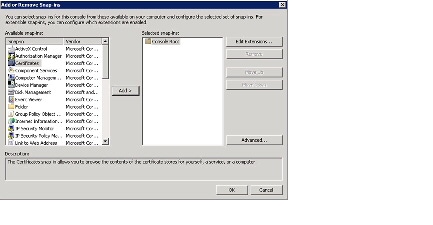
Step 7
In the Certificates snap-in window, click the Computer account radio button. Click Next .
Step 8
In the Select Computer window, click the Local computer (the computer this console is running on) radio button. Click Finish . Click OK to return to the MMC.
Step 9
In the MMC, click + Certificates to expand the menu.
Step 10
Right-click the Intermediate Certification Authorities folder. Choose All Tasks > Import to open the certificate import wizard. Click Next .
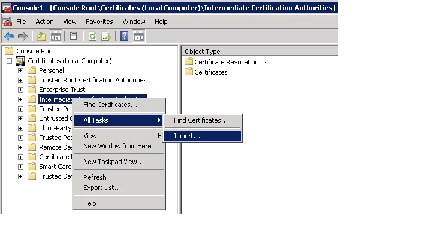
Step 11
Choose Browse . Choose the PKCS#7 Certificates format and choose the intermediates certificate from the CA. Click Open .

Note If you incorrectly choose the Server certificate at this step, you will need to start over at Step 7. You will need to create a new cert_request.txt file, and request a certificate re-key from the CA (the CA will revoke the original key and reissue a new key).

Step 12
In the Certificate Store window, click the Place all certificates in the following store radio button. Confirm that Intermediate Certification Authorities is displayed in the Certificate store field. Click Next .
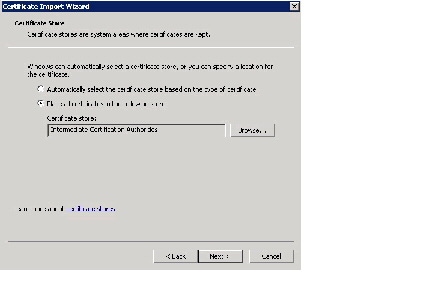
Step 13
Click Finish to close the certificate import wizard.
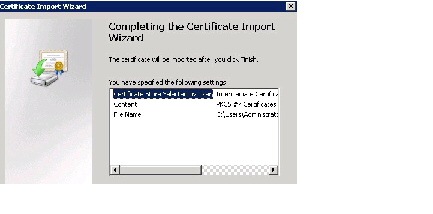
Step 14
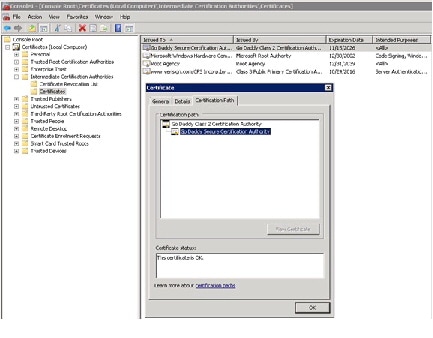
In the MMC, verify the certificate installation.
a.
Go to Certificates (Local Computer > Intermediate Certification Authorities > Certificates .
b.
Choose the certificate that you imported.
c.
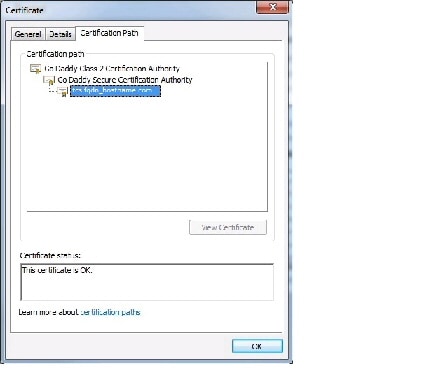
In the Certificate window, choose the Certification Path tab. Choose the certificate. The Certificate status will read OK . Click OK .
Complete Certificate Request
Step 1
Go to Start > Administrative Tools > Internet Information Services (IIS) Manager .
Step 2
Double-click Server Certificates .
Step 3
In the Actions pane, click Complete Certificate Request .

Step 4
In the Specify Certificate Authority Response window
a.
Browse to the file that contains the CA response.
b.
In the Friendly name field, type a friendly name for the certificate that is easy to remember and identify.
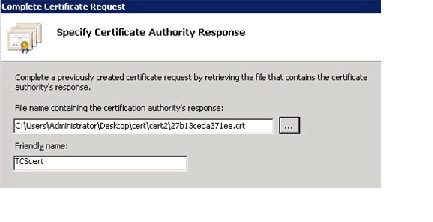
Step 5
Click OK . The certificate is loaded into the Microsoft certificate store.
Next, you will bind and enable the certificate within IIS for the Content Server website.
Step 6
In IIS, go to Start Page > TCS > Sites > Default Web Site . Click Bindings to open the Site Bindings window.
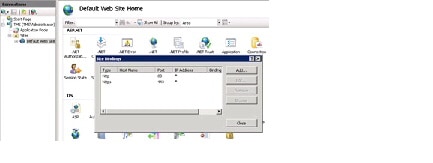
Step 7
In the Site Bindings window, choose https/443 and click Edit . If https/443 is not present, click Add to add the binding and then click Edit .
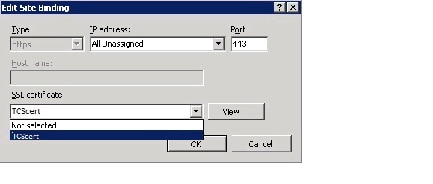
Step 8
In the Edit Site Binding window SSL certificate drop down menu, choose the friendly name certificate that you entered in Step 4.

Note If you do not see the friendly name certificate that you created in Step 4, confirm that you have correctly completed all previous steps in this procedure.
Step 9
Click OK to complete the HTTPS binding for your default website certificate. It will take a few moments to complete.
Verify Certificate
Step 1
Verify that the certificate is functioning by browsing to the Content Server FQDN.
Step 2
In the browser address field, click on the green lock icon in the Content Server URL.
Step 3
In the Certificate window, click the Certification Path tab. Choose the certificate and verify the status in the Certificate status pane. Click OK .
Self-Signed Certificate Installation
If you use a self-signed certificate for the Content Server, client browsers will generate an error stating that the signing certificate authority is unknown and not trusted. Because of the certificate-error message, you should develop an appropriate work around that is consistent with your security policies for all users that access the Content Server.
Follow these steps to install a self-signed certificate:
Step 1
Open a Remote Desktop Connection to the Content Server. Log in as an administrator.
Step 2
Go to Start > Administrative Tools > Internet Information Services (IIS) Manager .
Step 3
In the Features view, double-click Server Certificates .
Step 4
In the Actions pane, click Create Self-signed Certificate .
Step 5
On the Create Self-Signed Certificate page, type a “Friendly name” for the certificate in the Specify a friendly name for the certificate box. Click OK .
Related Documentation
http://www.cisco.com/en/US/products/ps11347/tsd_products_support_series_home.html
http://www.cisco.com/en/US/products/ps12130/products_installation_and_configuration_guides_list.html
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, using the Cisco Bug Search Tool (BST), submitting a service request, and gathering additional information, see What’s New in Cisco Product Documentation at: http://www.cisco.com/c/en/us/td/docs/general/whatsnew/whatsnew.html .
Subscribe to What’s New in Cisco Product Documentation , which lists all new and revised Cisco technical documentation, as an RSS feed and deliver content directly to your desktop using a reader application. The RSS feeds are a free service.
This document is to be used in conjunction with the documents listed in the “Related Documentation” section.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback