- Preface
- Introducing the CLI Configuration Guide
- Logging In to the Sensor
- Initializing the Sensor
- Setting Up the Sensor
- Configuring Interfaces
- Configuring Virtual Sensors
- Configuring Event Action Rules
- Defining Signatures
- Configuring Anomaly Detection
- Configuring Global Correlation
- Configuring External Product Interfaces
- Configuring IP Logging
- Displaying and Capturing Live Traffic on an Interface
- Configuring Attack Response Controller for Blocking and Rate Limiting
- Configuring SNMP
- Working With Configuration Files
- Administrative Tasks for the Sensor
- Configuring AIM IPS
- Configuring AIP SSM
- Configuring IDSM2
- Configuring NME IPS
- Obtaining Software
- Upgrading, Downgrading, and Installing System Images
- System Architecture
- Signature Engines
- Troubleshooting
- CLI Error Messages
- Open Source License Files
- Glossary
- Index
Cisco Intrusion Prevention System Sensor CLI Configuration Guide for IPS 7.0
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- April 21, 2009
Chapter: Configuring Global Correlation
- Understanding Global Correlation
- Participating in the SensorBase Network
- Understanding Reputation
- Understanding Network Participation
- Understanding Efficacy
- Reputation and Risk Rating
- Global Correlation and the Produce Alert Event Action
- Global Correlation Features and Goals
- Global Correlation Requirements
- Understanding Global Correlation Sensor Health Metrics
- Configuring Global Correlation Inspection and Reputation Filtering
- Configuring Network Participation
- Disabling Global Correlation
- Displaying Global Correlation Statistics
- Troubleshooting Global Correlation
Configuring Global Correlation
This chapter provides information for configuring global correlation. It contains the following sections:
•![]() Understanding Global Correlation
Understanding Global Correlation
•![]() Participating in the SensorBase Network
Participating in the SensorBase Network
•![]() Understanding Network Participation
Understanding Network Participation
•![]() Global Correlation and the Produce Alert Event Action
Global Correlation and the Produce Alert Event Action
•![]() Global Correlation Features and Goals
Global Correlation Features and Goals
•![]() Global Correlation Requirements
Global Correlation Requirements
•![]() Understanding Global Correlation Sensor Health Metrics
Understanding Global Correlation Sensor Health Metrics
•![]() Configuring Global Correlation Inspection and Reputation Filtering
Configuring Global Correlation Inspection and Reputation Filtering
•![]() Configuring Network Participation
Configuring Network Participation
•![]() Displaying Global Correlation Statistics
Displaying Global Correlation Statistics
•![]() Troubleshooting Global Correlation
Troubleshooting Global Correlation
Understanding Global Correlation
You can configure global correlation so that your sensors are aware of network devices with a reputation for malicious activity, and can take action against them. Participating IPS devices in a centralized Cisco threat database, the SensorBase, receive and absorb global correlation updates. The reputation data contained in the global correlation updates is factored in to the analysis of network traffic, which increases IPS efficacy, because traffic is denied or allowed based on the reputation of the source IP address. The participating IPS devices send data back in to the global correlation database, which results in a feedback loop that keeps the updates current and global.
You can configure the sensor to participate in the global correlation updates and/or in sending telemetry data or you can turn both services off. You can view reputation scores in events and see the reputation score of the attacker.
Participating in the SensorBase Network
Cisco IPS contains a new security capability, Cisco Global Correlation, which uses the immense security intelligence that we have amassed over the years. At regular intervals, Cisco IPS receives threat updates from the Cisco SensorBase Network, which contain detailed information about known threats on the Internet, including serial attackers, Botnet harvesters, Malware outbreaks, and dark nets. The IPS uses this information to filter out the worst attackers before they have a chance to attack critical assets. It then incorporates the global threat data in to its system to detect and prevent malicious activity even earlier.
If you agree to participate in the SensorBase Network, Cisco will collect aggregated statistics about traffic sent to your IPS. This includes summary data on the Cisco IPS network traffic properties and how this traffic was handled by the Cisco appliances. We do not collect the data content of traffic or other confidential business or personal information. All data is aggregated and sent by secure HTTP to the Cisco SensorBase Network servers in periodic intervals. All data shared with Cisco will be anonymous and treated as strictly confidential.
Table 10-1 shows how we use the data.
When you enable Partial or Full Network Participation, the Network Participation Disclaimer appears. You must enter yes to participate. If you do not have a license installed, you receive a warning telling you that global correlation inspection and reputation filtering are disabled until the sensor is licensed. You can obtain a license at http://www.cisco.com/go/license.
For More Information
For information on how to obtain and install a sensor license, see Installing the License Key.
Understanding Reputation
Similar to human social interaction, reputation is an opinion toward a device on the Internet. It enables the installed base of IPS sensors in the field to collaborate using the existing network infrastructure. A network device with reputation is most likely either malicious or infected. You can view reputation information and statistics in IDM.
The IPS sensor collaborates with the global correlation servers (also known as reputation servers) to improve the efficacy of the sensor.
Figure 10-1 shows the role of the sensor and the global correlation servers.
Figure 10-1 IPS Management and Global Correlation Server Interaction
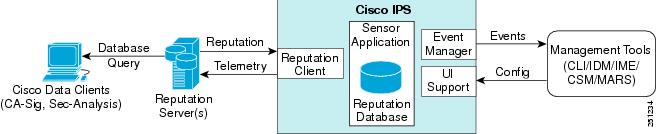
The global correlation servers provide information to the sensor about certain IP addresses that may identify malicious or infected hosts. The sensor uses this information to determine which actions, if any, to perform when potentially harmful traffic is received from a host with known reputation. Because the global correlation database changes rapidly, the sensor must periodically download global correlation updates from the global correlation servers.

For more information about viewing global correlation statistics, see Displaying Statistics.
Understanding Network Participation
Network participation lets us collect nearly real-time data from sensors around the world. Sensors installed at customer sites can send data to the SensorBase. These data feed in to the global correlation database to increase reputation fidelity. Communication between sensors and the SensorBase involves an HTTPS request and response over TCP/IP.
Network participation gathers the following data:
•![]() Signature ID
Signature ID
•![]() Attacker IP address
Attacker IP address
•![]() Attacker port
Attacker port
•![]() Maximum segment size
Maximum segment size
•![]() Victim IP address
Victim IP address
•![]() Victim port
Victim port
•![]() Signature version
Signature version
•![]() TCP options string
TCP options string
•![]() Reputation score
Reputation score
•![]() Risk rating
Risk rating
•![]() Data gathered from the sensor health metrics
Data gathered from the sensor health metrics
The statistics for network participation show the hits and misses for alerts, the reputation actions, and the counters of packets that have been denied.
There are three modes for network participation:
•![]() Off—The network participation server does not collect data, track statistics, or try to contact the Cisco SensorBase Network.
Off—The network participation server does not collect data, track statistics, or try to contact the Cisco SensorBase Network.
•![]() Partial Participation—The network participation server collects data, tracks statistics, and communicates with the SensorBase Network. Data considered to be potentially sensitive is filtered out and never sent.
Partial Participation—The network participation server collects data, tracks statistics, and communicates with the SensorBase Network. Data considered to be potentially sensitive is filtered out and never sent.
•![]() Full Participation—The network participation server collects data, tracks statistics, and communicates with the SensorBase Network. All data collected is sent.
Full Participation—The network participation server collects data, tracks statistics, and communicates with the SensorBase Network. All data collected is sent.
Network participation requires at least 100 MB of available memory, a network connection to the sensor, and a network connection to the Internet.

•![]() For more information on network participation, see Configuring Network Participation.
For more information on network participation, see Configuring Network Participation.
•![]() For more information on bypass mode, see Configuring Inline Bypass Mode.
For more information on bypass mode, see Configuring Inline Bypass Mode.
Understanding Efficacy
Obtaining data from participating IPS clients and using that in conjunction with the existing corpus of threat knowledge improves the efficacy of the IPS. We measure efficacy based on the following:
•![]() False positives as a percentage of actionable events
False positives as a percentage of actionable events
•![]() False negatives as a percentage of threats that do not result in actionable events
False negatives as a percentage of threats that do not result in actionable events
•![]() Actionable events as a percentage of all events
Actionable events as a percentage of all events
For More Information
For more information about reputation and risk rating, see Reputation and Risk Rating.
Reputation and Risk Rating
Risk rating is the concept of the probability that a network event is malicious. You assign a numerical quantification of the risk associated with a particular event on the network. By default, an alert with an extreme risk rating shuts down traffic. Reputation indicates the probability that a particular attacker IP address will initiate malicious behavior based on its known past activity. A certain score is computed for this reputation by the Alarm Channel and added to risk rating, thus improving the efficacy of the IPS. When the attacker has a bad reputation score, an incremental risk is added to the risk rating to make it more aggressive.
The Alarm Channel handles signature events from the data path. The alert processing units have multiple aggregation techniques, action overrides, action filters, attacker reputation, and per-action custom handling methods. We use the large reputation data from the reputation participation client to score attackers in the Alarm Channel and then use this score to influence the risk rating and actions of the alert.
For More Information
•![]() For a detailed description of risk rating, see Calculating the Risk Rating.
For a detailed description of risk rating, see Calculating the Risk Rating.
•![]() For a detailed description of threat rating, see Understanding Threat Rating.
For a detailed description of threat rating, see Understanding Threat Rating.
•![]() For a detailed description of event action filters, see Configuring Event Action Filters.
For a detailed description of event action filters, see Configuring Event Action Filters.
•![]() For a detailed description of Alarm Channel, see Understanding SensorApp.
For a detailed description of Alarm Channel, see Understanding SensorApp.
•![]() For a detailed description of event action aggregation, see Understanding Event Action Aggregation.
For a detailed description of event action aggregation, see Understanding Event Action Aggregation.
Global Correlation and the Produce Alert Event Action
A produce-alert event action is added for an event under the following conditions:
•![]() Global correlation has increased the risk rating of an event.
Global correlation has increased the risk rating of an event.
•![]() Global correlation has added either the deny-packet-inline or deny-attacker-inline event action.
Global correlation has added either the deny-packet-inline or deny-attacker-inline event action.
Adding the produce-alert event action ensures that all events being denied by global correlation result in alerts that you can view through your monitoring tool. This prevents global correlation from denying events that you do not know about.

Note ![]() This feature only applies to global correlation inspection where the traffic is allowed if no specific signature is matched. It does not apply to reputation filtering where the packet is denied before signature analysis, and no alerts are generated when packets are denied by reputation filtering.
This feature only applies to global correlation inspection where the traffic is allowed if no specific signature is matched. It does not apply to reputation filtering where the packet is denied before signature analysis, and no alerts are generated when packets are denied by reputation filtering.
For More Information
For detailed information about event actions, see Event Actions.
Global Correlation Features and Goals
There are three main features of global correlation:
•![]() Global correlation inspection—We use the global correlation reputation knowledge of attackers to influence alert handling and deny actions when attackers with a bad score are seen on the sensor.
Global correlation inspection—We use the global correlation reputation knowledge of attackers to influence alert handling and deny actions when attackers with a bad score are seen on the sensor.
•![]() Reputation filtering—Applies automatic deny actions to packets from known malicious sites.
Reputation filtering—Applies automatic deny actions to packets from known malicious sites.
•![]() Network reputation—Sensor sends alert and TCP fingerprint data to the SensorBase.
Network reputation—Sensor sends alert and TCP fingerprint data to the SensorBase.
Global correlation has the following goals:
•![]() Dealing intelligently with alerts thus improving efficacy.
Dealing intelligently with alerts thus improving efficacy.
•![]() Improving protection against known malicious sites.
Improving protection against known malicious sites.
•![]() Sharing telemetry data with the SensorBase to improve visibility of alerts and sensor actions on a global scale.
Sharing telemetry data with the SensorBase to improve visibility of alerts and sensor actions on a global scale.
•![]() Simplifying configuration settings.
Simplifying configuration settings.
•![]() Automatic handling of the uploads and downloads of the information.
Automatic handling of the uploads and downloads of the information.
Global Correlation Requirements
Global correlation has the following requirements:
•![]() Valid license
Valid license
You must have a valid sensor license for global correlation features to function. You can still configure and display statistics for the global correlation features, but the global correlation databases are cleared and no updates are attempted. Once you install a valid license, the global correlation features are reactivated.
•![]() Agree to Network Participation disclaimer
Agree to Network Participation disclaimer
•![]() External connectivity for sensor and a DNS server
External connectivity for sensor and a DNS server
The global correlation features require the sensor to connect to the Cisco SensorBase network. Domain name resolution is also required for these features to function. You can either configure the sensor to connect through an HTTP proxy server that has a DNS client running on it, or you can assign an Internet routeable address to the management interface of the sensor and configure the sensor to use a DNS server. In Cisco IPS the HTTP proxy and DNS servers are used only by the global correlation features.
If you are connecting through an HTTP proxy, make sure you have the following configuration:
–![]() The proxy must allow HTTP requests from the IPS systems to http://updates.ironport.com/ibrs/ on port 80.
The proxy must allow HTTP requests from the IPS systems to http://updates.ironport.com/ibrs/ on port 80.
–![]() The proxy must allow HTTPS requests from the IPS systems to update-manifests.ironport.com on port 443.
The proxy must allow HTTPS requests from the IPS systems to update-manifests.ironport.com on port 443.
–![]() The firewall must allow access from the proxy to the internet (any destination address) on ports 80 and 443.
The firewall must allow access from the proxy to the internet (any destination address) on ports 80 and 443.
If you are NOT connecting through the HTTP proxy:
–![]() The firewall must allow access from each IPS to the Internet (any destination address) on ports 80 and 443.
The firewall must allow access from each IPS to the Internet (any destination address) on ports 80 and 443.

Note ![]() The IPS does not support the use of authenticated proxies.
The IPS does not support the use of authenticated proxies.

•![]() No IPv6 address support
No IPv6 address support
The global correlation inspection and the reputation filtering deny features do not support IPv6 addresses. For global correlation inspection, the sensor does not receive or process reputation data for IPv6 addresses. The risk rating for IPv6 addresses is not modified for global correlation inspection. Similarly, network participation does not include event data for attacks from IPv6 addresses. And finally, IPv6 addresses do not appear in the deny list.
•![]() Sensor in inline mode
Sensor in inline mode
The sensor must operate in inline mode so that the global correlation features can increase efficacy by being able to use the inline deny actions.
•![]() IPS version that supports global correlation
IPS version that supports global correlation
•![]() Sensor that supports the global correlation features
Sensor that supports the global correlation features
For More Information
•![]() For information on how to obtain and install a sensor license, see Installing the License Key.
For information on how to obtain and install a sensor license, see Installing the License Key.
•![]() For information about the Network Participation disclaimer, see Participating in the SensorBase Network.
For information about the Network Participation disclaimer, see Participating in the SensorBase Network.
•![]() For information about configuring an HTTP proxy or DNS server to support global correlation, see Configuring the DNS and Proxy Servers for Global Correlation.
For information about configuring an HTTP proxy or DNS server to support global correlation, see Configuring the DNS and Proxy Servers for Global Correlation.
Understanding Global Correlation Sensor Health Metrics
For global correlation, the following metrics are added to sensor health monitoring:
•![]() Green indicates that the last update was successful.
Green indicates that the last update was successful.
•![]() Yellow indicates that there has not been a successful update within the past day (86,400 seconds).
Yellow indicates that there has not been a successful update within the past day (86,400 seconds).
•![]() Red indicates that there has not been a successful update within the last three days (259,200 seconds).
Red indicates that there has not been a successful update within the last three days (259,200 seconds).
For network participation, the following metrics are added to sensor health monitoring:
•![]() Green indicates that the last connection was successful.
Green indicates that the last connection was successful.
•![]() Yellow indicates that less than 6 connections failed in a row.
Yellow indicates that less than 6 connections failed in a row.
•![]() Red indicates that more than 6 connections failed in a row.
Red indicates that more than 6 connections failed in a row.
Use the health-monitor command in service submode to configure the health statistics for the sensor. Use the show health command to see the results of the health-monitor command.
Global correlation health status defaults to red and changes to green after a successful global correlation update. Successful global correlation updates require a DNS server or an HTTP proxy server. Because DNS and HTTP proxy server configuration features are new to IPS 7.0, they are unconfigured after an upgrade to 7.0. As a result, global correlation health and overall sensor health status are red until you configure a DNS or HTTP proxy server on the sensor. If the sensor is deployed in an environment where a DNS or HTTP proxy server is not available, you can address the red global correlation health and overall sensor health status by disabling global correlation and configuring sensor health status to exclude global correlation health status.
For More Information
•![]() For the procedure for viewing sensor health metrics, see Showing Sensor Overall Health Status.
For the procedure for viewing sensor health metrics, see Showing Sensor Overall Health Status.
•![]() For the procedure for adding a DNS or HTTP proxy server, see Configuring the DNS and Proxy Servers for Global Correlation.
For the procedure for adding a DNS or HTTP proxy server, see Configuring the DNS and Proxy Servers for Global Correlation.
•![]() For the procedure for disabling global correlation, see Disabling Global Correlation.
For the procedure for disabling global correlation, see Disabling Global Correlation.
•![]() For the procedure for excluding global correlation health from overall sensor health, see Configuring Health Status Information.
For the procedure for excluding global correlation health from overall sensor health, see Configuring Health Status Information.
Configuring Global Correlation Inspection and Reputation Filtering
This section describes global correlation inspection and reputation filtering, and how to configure them. It contains the following topics:
•![]() Understanding Global Correlation Inspection and Reputation Filtering
Understanding Global Correlation Inspection and Reputation Filtering
•![]() Configuring Global Correlation Inspection and Reputation Filtering
Configuring Global Correlation Inspection and Reputation Filtering
Understanding Global Correlation Inspection and Reputation Filtering
You can configure the sensor to use updates from the SensorBase Network to adjust the risk rating. The client determines which updates are available and applicable to the sensor by communicating with the global correlation update server and a file server, which is a two-phase process. In the first phase the sensor sends a client manifest to the global correlation update sever via an HTTPS POST request. The server then returns the server manifest document in the HTTPS response. In the next phase the sensor identifies the updates that are available and how to obtain them from a file server. The sensor downloads the encrypted update files via HTTP from the file server using the information in the server manifest. The integrity of these update files has been verified by comparing its MD5 hash with the hash value specified in the server manifest.
Figure 10-2 demonstrates how the global correlation update client obtains the files.
Figure 10-2 Global Correlation Update Client
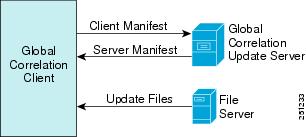

Once you configure global correlation, updates are automatic and happen at regular intervals, approximately every five minutes by default, but this interval may be modified by the global correlation server. The sensor gets a full update and then applies an incremental update periodically.
You configure an HTTP proxy or a DNS server in the service network-setting submode. If you turn on global correlation, you can choose how aggressively you want the deny actions to be enforced against malicious hosts. You can then enable reputation filtering to deny access to known malicious hosts. If you only want a report of what could have happened, you can enable test-global-correlation. This puts the sensor in Audit mode, and actions the sensor would have performed are generated in the events.
Use the show health command in privileged EXEC mode to display the overall health status information of the sensor. The health status categories are rated by red and green with red being critical.

For More Information
•![]() For the procedure for configuring global correlation features, see Configuring Global Correlation Inspection and Reputation Filtering.
For the procedure for configuring global correlation features, see Configuring Global Correlation Inspection and Reputation Filtering.
•![]() For the procedure to view sensor health metrics, see Showing Sensor Overall Health Status.
For the procedure to view sensor health metrics, see Showing Sensor Overall Health Status.
•![]() For information on CollaborationApp, see CollaborationApp.
For information on CollaborationApp, see CollaborationApp.
•![]() For more information on bypass mode, see Configuring Inline Bypass Mode.
For more information on bypass mode, see Configuring Inline Bypass Mode.
Configuring Global Correlation Inspection and Reputation Filtering

The following options apply:
•![]() global-correlation-inspection {on | off}—Turns global correlation inspection on or off. When turned on, the sensor uses updates from the SensorBase network to adjust the risk rating. The default is on.
global-correlation-inspection {on | off}—Turns global correlation inspection on or off. When turned on, the sensor uses updates from the SensorBase network to adjust the risk rating. The default is on.
•![]() global-correlation-inspection-influence {permissive | standard | aggressive}—Lets you choose the level of global correlation inspection. The default is standard.
global-correlation-inspection-influence {permissive | standard | aggressive}—Lets you choose the level of global correlation inspection. The default is standard.
–![]() permissive—global correlation data has little influence in the decision to deny traffic.
permissive—global correlation data has little influence in the decision to deny traffic.
–![]() standard—global correlation moderately influences the decision to deny traffic.
standard—global correlation moderately influences the decision to deny traffic.
–![]() aggressive—global correlation data heavily influences the decision to deny traffic.
aggressive—global correlation data heavily influences the decision to deny traffic.
•![]() reputation-filtering {on | off}—Turns reputation filtering on or off. When turned on, the sensor denies access to malicious hosts that are listed in the global correlation database. The default is on.
reputation-filtering {on | off}—Turns reputation filtering on or off. When turned on, the sensor denies access to malicious hosts that are listed in the global correlation database. The default is on.
•![]() test-global-correlation {on | off}—Enables reporting of deny actions that are affected by global correlation. Allows you to test the global correlation features without actually denying any hosts. The default is off.
test-global-correlation {on | off}—Enables reporting of deny actions that are affected by global correlation. Allows you to test the global correlation features without actually denying any hosts. The default is off.
To configure global correlation features, follow these steps:
Step 1 ![]() Log in to the CLI using an account with administrator privileges.
Log in to the CLI using an account with administrator privileges.
Step 2 ![]() Enter global correlation submode.
Enter global correlation submode.
sensor# configure terminal
sensor(config)# service global-correlation
sensor(config-glo)#
Step 3 ![]() Turn on global correlation inspection.
Turn on global correlation inspection.
sensor(config-glo)# global-correlation-inspection on
sensor(config-glo)#
Step 4 ![]() Specify the level of global correlation inspection.
Specify the level of global correlation inspection.
sensor(config-glo)# global-correlation-inspection-influence aggressive
sensor(config-glo)#
Step 5 ![]() Turn on reputation filtering.
Turn on reputation filtering.
sensor(config-glo)# reputation-filtering on
sensor(config-glo)#
Step 6 ![]() Test global correlation data, but not actually deny traffic.
Test global correlation data, but not actually deny traffic.
sensor(config-glo)# test-global-correlation on
sensor(config-glo)#
Step 7 ![]() Verify the settings.
Verify the settings.
sensor(config-glo)# show settings
global-correlation-inspection: on default: on
global-correlation-inspection-influence: aggressive default: standard
reputation-filtering: on default: on
test-global-correlation: on default: off
sensor(config-glo)#
Step 8 ![]() Exit global correlation submode.
Exit global correlation submode.
sensor(config-glo)# exit
Apply Changes:?[yes]:
Step 9 ![]() Press Enter to apply your changes or enter no to discard them.
Press Enter to apply your changes or enter no to discard them.
For More Information
•![]() For information about configuring an HTTP proxy or DNS server to support global correlation, see Configuring the DNS and Proxy Servers for Global Correlation.
For information about configuring an HTTP proxy or DNS server to support global correlation, see Configuring the DNS and Proxy Servers for Global Correlation.
•![]() For information on how to obtain and install a sensor license, see Installing the License Key.
For information on how to obtain and install a sensor license, see Installing the License Key.
•![]() For more information about the sensor health metrics, see Showing Sensor Overall Health Status.
For more information about the sensor health metrics, see Showing Sensor Overall Health Status.
Configuring Network Participation

Note ![]() Configuring the sensor for partial network participation limits a third party from extracting reconnaissance information about your internal network from the global correlation database.
Configuring the sensor for partial network participation limits a third party from extracting reconnaissance information about your internal network from the global correlation database.
You can configure the sensor to send data to the SensorBase. You can configure the sensor to fully participate and send all data to the SensorBase. Or you can configure the sensor to collect the data but to omit potentially sensitive data, such as the destination IP address of trigger packets.
The following option applies:
•![]() network-participation—Sets the level of network participation. The default is off.
network-participation—Sets the level of network participation. The default is off.
–![]() off—No data is contributed to the SensorBase network.
off—No data is contributed to the SensorBase network.
–![]() partial—Data is contributed to the SensorBase network but potentially sensitive information is withheld.
partial—Data is contributed to the SensorBase network but potentially sensitive information is withheld.
–![]() full—All data is contributed to the SensorBase network.
full—All data is contributed to the SensorBase network.

Note ![]() You must accept the Network Participation disclaimer to turn on network participation.
You must accept the Network Participation disclaimer to turn on network participation.
To turn on network participation, follow these steps:
Step 1 ![]() Log in to the CLI using an account with administrator privileges.
Log in to the CLI using an account with administrator privileges.
Step 2 ![]() Enter global correlation submode.
Enter global correlation submode.
sensor# configure terminal
sensor(config)# service global-correlation
sensor(config-glo)#
Step 3 ![]() Turn on network participation.
Turn on network participation.
sensor(config-glo)# network-participation {full | partial]
sensor(config-glo)# exit
Step 4 ![]() Enter yes to agree to participate in the SensorBase Network.
Enter yes to agree to participate in the SensorBase Network.
If you agree to participate in the SensorBase Network, Cisco will collect aggregated statistics about traffic sent to your IPS. This includes summary data on the Cisco IPS network traffic properties and how this traffic was handled by the Cisco appliances. We do not collect the data content of traffic or other sensitive business or personal information. All data is aggregated and sent via secure HTTP to the Cisco SensorBase Network servers in periodic intervals. All data shared with Cisco will be anonymous and treated as strictly confidential.
The table below describes how the data will be used by Cisco.
Participation Level = "Partial":
* Type of Data: Protocol Attributes (e.g. TCP max segment size and
options string)
Purpose: Track potential threats and understand threat exposure
* Type of Data: Attack Type (e.g. Signature Fired and Risk Rating)
Purpose: Used to understand current attacks and attack severity
* Type of Data: Connecting IP Address and port
Purpose: Identifies attack source
* Type of Data: Summary IPS performance (CPU utilization memory usage,
inline vs. promiscuous, etc)
Purpose: Tracks product efficacy
Participation Level = "Full" additionally includes:
* Type of Data: Victim IP Address and port
Purpose: Detect threat behavioral patterns
Do you agree to participate in the SensorBase Network?[no]:
Step 5 ![]() Verify the settings.
Verify the settings.
sensor(config-glo)# show settings
network-participation: full default: off
global-correlation-inspection: on default: on
global-correlation-inspection-influence: aggressive default: standard
reputation-filtering: on default: on
test-global-correlation: on default: off
sensor(config-glo)#
Step 6 ![]() Exit global correlation submode.
Exit global correlation submode.
sensor(config-glo)# exit
Apply Changes:?[yes]:
Step 7 ![]() Press Enter to apply your changes or enter no to discard them.
Press Enter to apply your changes or enter no to discard them.
For More Information
For more information about participating in the SensorBase Network, see Participating in the SensorBase Network.
Disabling Global Correlation
If your sensor is deployed in an environment where a DNS server or HTTP proxy server is not available, you may want to disable global correlation so that global correlation health does not appear as red in the overall sensor health, thus indicating a problem. You can also configure sensor health to exclude global correlation.
The following options apply:
•![]() global-correlation-inspection {on | off}—Turns global correlation inspection on or off. When turned on, the sensor uses updates from the SensorBase network to adjust the risk rating. The default is on.
global-correlation-inspection {on | off}—Turns global correlation inspection on or off. When turned on, the sensor uses updates from the SensorBase network to adjust the risk rating. The default is on.
•![]() reputation-filtering {on | off}—Turns reputation filtering on or off. When turned on, the sensor denies access to malicious hosts that are listed in the global correlation database. The default is on.
reputation-filtering {on | off}—Turns reputation filtering on or off. When turned on, the sensor denies access to malicious hosts that are listed in the global correlation database. The default is on.
•![]() network-participation—Sets the level of network participation. The default is off.
network-participation—Sets the level of network participation. The default is off.
–![]() off—No data is contributed to the SensorBase Network.
off—No data is contributed to the SensorBase Network.
–![]() partial—Data is contributed to the SensorBase Network but potentially sensitive information is withheld.
partial—Data is contributed to the SensorBase Network but potentially sensitive information is withheld.
–![]() full—All data is contributed to the SensorBase Network.
full—All data is contributed to the SensorBase Network.
To disable global correlation features, follow these steps:
Step 1 ![]() Log in to the CLI using an account with administrator privileges.
Log in to the CLI using an account with administrator privileges.
Step 2 ![]() Enter global correlation submode.
Enter global correlation submode.
sensor# configure terminal
sensor(config)# service global-correlation
sensor(config-glo)#
Step 3 ![]() Turn off global correlation inspection.
Turn off global correlation inspection.
sensor(config-glo)# global-correlation-inspection off
sensor(config-glo)#
Step 4 ![]() Turn off reputation filtering.
Turn off reputation filtering.
sensor(config-glo)# reputation-filtering off
sensor(config-glo)#
Step 5 ![]() Turn off network participation.
Turn off network participation.
sensor(config-glo)# network-participation off
sensor(config-glo)# exit
Step 6 ![]() Verify the settings.
Verify the settings.
sensor(config-glo)# show settings
network-participation: full default: off
global-correlation-inspection: on default: off
reputation-filtering: on default: off
sensor(config-glo)#
Step 7 ![]() Exit global correlation submode.
Exit global correlation submode.
sensor(config-glo)# exit
Apply Changes:?[yes]:
Step 8 ![]() Press Enter to apply your changes or enter no to discard them.
Press Enter to apply your changes or enter no to discard them.
For More Information
For the procedure for excluding global correlation from overall sensor health, see Configuring Health Status Information.
Displaying Global Correlation Statistics
Use the show statistics global-correlation command to display global correlation statistics. Use the show statistics global-correlation [name | clear] command to display statistics for these components for all virtual sensors. If you provide the virtual sensor name, the statistics for that virtual sensor only are displayed.

Note ![]() For IPS 7.0(7)E4 and later and IPS 7.1(5)E4 and later, the output includes any failures that have been detected.
For IPS 7.0(7)E4 and later and IPS 7.1(5)E4 and later, the output includes any failures that have been detected.
To display and clear global correlation statistics for the sensor, follow these steps:
Step 1 ![]() Log in to the CLI.
Log in to the CLI.
Step 2 ![]() Display the statistics for global correlation.
Display the statistics for global correlation.
sensor# show statistics global-correlation
Network Participation:
Counters:
Total Connection Attempts = 4347
Total Connection Failures = 155
Connection Failures Since Last Success = 0
Connection History:
Connection Attempt on June 17 2012, at 21:57:19 UTC = Successful
Connection Attempt on June 17 2012, at 21:54:18 UTC = Successful
Connection Attempt on June 17 2012, at 21:51:17 UTC = Successful
Connection Attempt on June 17 2012, at 21:48:17 UTC = Successful
Connection Attempt on June 17 2012, at 21:45:16 UTC = Successful
Updates:
Status Of Last Update Attempt = Disabled
Time Since Last Successful Update = never
Counters:
Update Failures Since Last Success = 0
Total Update Attempts = 0
Total Update Failures = 0
Update Interval In Seconds = 300
Update Server = update-manifests.ironport.com
Update Server Address = Unknown
Current Versions:
Warnings:
Details:
Last fail log =
sensor#
Step 3 ![]() Clear the statistics for global correlation:
Clear the statistics for global correlation:
sensor# show statistics global-correlation clear
Network Participation:
Counters:
Total Connection Attempts = 0
Total Connection Failures = 0
Connection Failures Since Last Success = 0
Connection History:
Connection Attempt on June 17 2012, at 22:03:20 UTC = Successful
Connection Attempt on June 17 2012, at 22:00:19 UTC = Successful
Connection Attempt on June 17 2012, at 21:57:19 UTC = Successful
Connection Attempt on June 17 2012, at 21:54:18 UTC = Successful
Connection Attempt on June 17 2012, at 21:51:17 UTC = Successful
Updates:
Status Of Last Update Attempt = Disabled
Time Since Last Successful Update = never
Counters:
Update Failures Since Last Success = 0
Total Update Attempts = 0
Total Update Failures = 0
Update Interval In Seconds = 300
Update Server = update-manifests.ironport.com
Update Server Address = Unknown
Current Versions:
Warnings:
Details:
Last fail log =
sensor#
Troubleshooting Global Correlation
Make sure you observe the following when configuring global correlation:
•![]() Because global correlation updates occur through the sensor management interface, firewalls must allow port 443/80 traffic.
Because global correlation updates occur through the sensor management interface, firewalls must allow port 443/80 traffic.
•![]() You must have an HTTP proxy server or a DNS server configured to allow global correlation features to function.
You must have an HTTP proxy server or a DNS server configured to allow global correlation features to function.
•![]() If you have an HTTP proxy server configured, the proxy must allow port 443/80 traffic from IPS systems.
If you have an HTTP proxy server configured, the proxy must allow port 443/80 traffic from IPS systems.
•![]() You must have a valid IPS license to allow global correlation features to function.
You must have a valid IPS license to allow global correlation features to function.
•![]() Global correlation features only contain external IP addresses, so if you position a sensor in an internal lab, you may never receive global correlation information.
Global correlation features only contain external IP addresses, so if you position a sensor in an internal lab, you may never receive global correlation information.
•![]() Make sure your sensor supports the global correlation features
Make sure your sensor supports the global correlation features
•![]() Make sure your IPS version supports the network participation features.
Make sure your IPS version supports the network participation features.
For More Information
•![]() For the procedure for configuring a DNS or HTTP proxy server, see Configuring the DNS and Proxy Servers for Global Correlation.
For the procedure for configuring a DNS or HTTP proxy server, see Configuring the DNS and Proxy Servers for Global Correlation.
•![]() For the procedure for obtaining an IPS license, see Installing the License Key.
For the procedure for obtaining an IPS license, see Installing the License Key.
•![]() For detailed information about HTTP proxy server configuration, see Global Correlation Requirements.
For detailed information about HTTP proxy server configuration, see Global Correlation Requirements.
 Feedback
Feedback