- About This Guide
- Index
- Glossary
-
- Configuring IPSec and ISAKMP
- Configuring L2TP over IPSec
- Setting General VPN Parameters
- Configuring Tunnel Groups, Group Policies, and Users
- Configuring IP Addresses for VPN
- Configuring Remote Access VPNs
- Configuring Network Admission Control
- Configuring Easy VPN on the ASA 5505
- Configuring the PPPoE Client
- Configuring LAN-to-LAN VPNs
- Configuring Clientless SSL VPN
- Configuring AnyConnect VPN Client Connections
- Configuring AnyConnect Host Scan
Cisco ASA 5500 Series Configuration Guide using the CLI, 8.4 and 8.6
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- May 6, 2009
Chapter: Configuring the TLS Proxy for Encrypted Voice Inspection
- Information about the TLS Proxy for Encrypted Voice Inspection
- Licensing for the TLS Proxy
- Prerequisites for the TLS Proxy for Encrypted Voice Inspection
- Configuring the TLS Proxy for Encrypted Voice Inspection
- Monitoring the TLS Proxy
- Feature History for the TLS Proxy for Encrypted Voice Inspection
Configuring the TLS Proxy for Encrypted Voice Inspection
This chapter describes how to configure the adaptive security appliance for the TLS Proxy for Encrypted Voice Inspection feature.
This chapter includes the following sections:
- Information about the TLS Proxy for Encrypted Voice Inspection
- Licensing for the TLS Proxy
- Prerequisites for the TLS Proxy for Encrypted Voice Inspection
- Configuring the TLS Proxy for Encrypted Voice Inspection
- Monitoring the TLS Proxy
- Feature History for the TLS Proxy for Encrypted Voice Inspection
Information about the TLS Proxy for Encrypted Voice Inspection
End-to-end encryption often leaves network security appliances “blind” to media and signaling traffic, which can compromise access control and threat prevention security functions. This lack of visibility can result in a lack of interoperability between the firewall functions and the encrypted voice, leaving businesses unable to satisfy both of their key security requirements.
The ASA is able to intercept and decrypt encrypted signaling from Cisco encrypted endpoints to the Cisco Unified Communications Manager (Cisco UCM), and apply the required threat protection and access control. It can also ensure confidentiality by re-encrypting the traffic onto the Cisco UCM servers.
Typically, the ASA TLS Proxy functionality is deployed in campus unified communications network. This solution is ideal for deployments that utilize end to end encryption and firewalls to protect Unified Communications Manager servers.
The security appliance in Figure 49-1 serves as a proxy for both client and server, with Cisco IP Phone and Cisco UCM interaction.
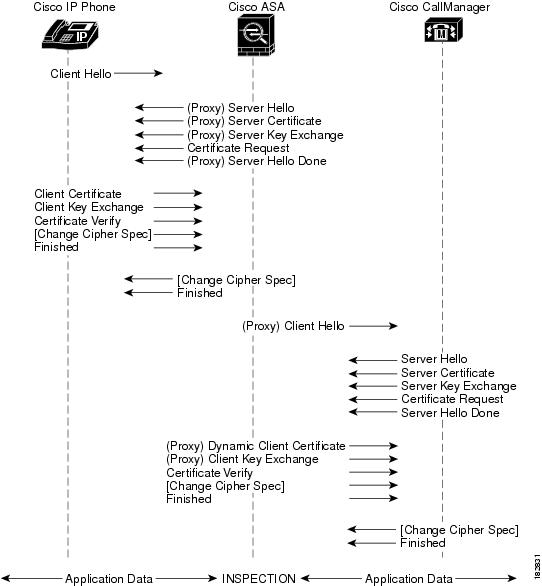
Decryption and Inspection of Unified Communications Encrypted Signaling
With encrypted voice inspection, the security appliance decrypts, inspects and modifies (as needed, for example, performing NAT fixup), and re-encrypts voice signaling traffic while all of the existing VoIP inspection functions for Skinny and SIP protocols are preserved. Once voice signaling is decrypted, the plaintext signaling message is passed to the existing inspection engines.
The security appliance acts as a TLS proxy between the Cisco IP Phone and Cisco UCM. The proxy is transparent for the voice calls between the phone and theCisco UCM. Cisco IP Phones download a Certificate Trust List from the Cisco UCM before registration which contains identities (certificates) of the devices that the phone should trust, such as TFTP servers and Cisco UCM servers. To support server proxy, the CTL file must contain the certificate that the security appliance creates for the Cisco UCMs. To proxy calls on behalf of the Cisco IP Phone, the security appliance presents a certificate that the Cisco UCM can verify, which is a Local Dynamic Certificate for the phone, issued by the certificate authority on the security appliance.
TLS proxy is supported by the Cisco Unified CallManager Release 5.1 and later. You should be familiar with the security features of the Cisco UCM. For background and detailed description of Cisco UCM security, see the Cisco Unified CallManager document:
http://www.cisco.com/univercd/cc/td/doc/product/voice/c_callmg/5_0/sec_vir/ae/sec504/index.htm
TLS proxy applies to the encryption layer and must be configured with an application layer protocol inspection. You should be familiar with the inspection features on the ASA, especially Skinny and SIP inspection.
Supported Cisco UCM and IP Phones for the TLS Proxy
Cisco Unified Communications Manager
The following releases of the Cisco Unified Communications Manager are supported with the TLS proxy:
- Cisco Unified CallManager Version 4. x
- Cisco Unified CallManager Version 5.0
- Cisco Unified CallManager Version 5.1
- Cisco Unified Communications Manager 6.1
- Cisco Unified Communications Manager 7.0
- Cisco Unified Communications Manager 8.0
The following IP phones in the Cisco Unified IP Phones 7900 Series are supported with the TLS proxy:
- Cisco Unified IP Phone 7985
- Cisco Unified IP Phone 7975
- Cisco Unified IP Phone 7971
- Cisco Unified IP Phone 7970
- Cisco Unified IP Phone 7965
- Cisco Unified IP Phone 7962
- Cisco Unified IP Phone 7961
- Cisco Unified IP Phone 7961G-GE
- Cisco Unified IP Phone 7960
- Cisco Unified IP Phone 7945
- Cisco Unified IP Phone 7942
- Cisco Unified IP Phone 7941
- Cisco Unified IP Phone 7941G-GE
- Cisco Unified IP Phone 7940
- Cisco Unified Wireless IP Phone 7921
- Cisco Unified Wireless IP Phone 7925
- Cisco IP Communicator (CIPC) for softphones
CTL Client Overview
The CTL Client application supplied by Cisco Unified CallManager Release 5.1 and later supports a TLS proxy server (firewall) in the CTL file. Figure 49-2 through Figure 49-5 illustrate the TLS proxy features supported in the CTL Client.
Figure 49-2 CTL Client TLS Proxy Features — Add Firewall
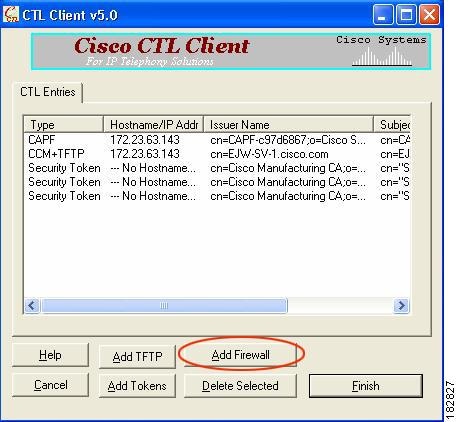
Figure 49-2 shows support for adding a CTL entry consisting of the security appliance as the TLS proxy.
Figure 49-3 CTL Client TLS Proxy Features — ASA IP Address or Domain Name
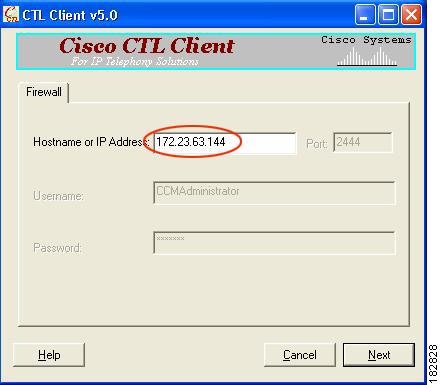
Figure 49-3 shows support for entering the security appliance IP address or domain name in the CTL Client.
Figure 49-4 CTL Client TLS Proxy Features — CTL Entry for ASA
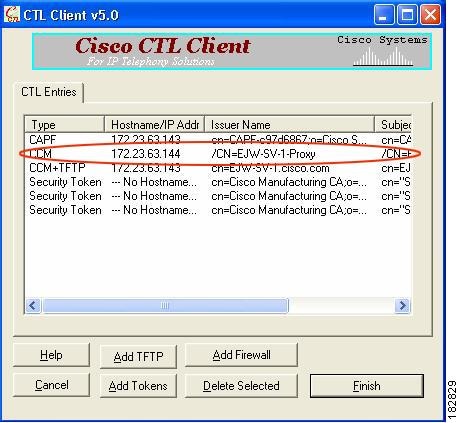
Figure 49-4 shows that the CTL entry for the security appliance as the TLS proxy has been added. The CTL entry is added after the CTL Client connects to the CTL Provider service on the security appliance and retrieves the proxy certificate.
Figure 49-5 CTL Client TLS Proxy Features — CTL File Installed on the ASA
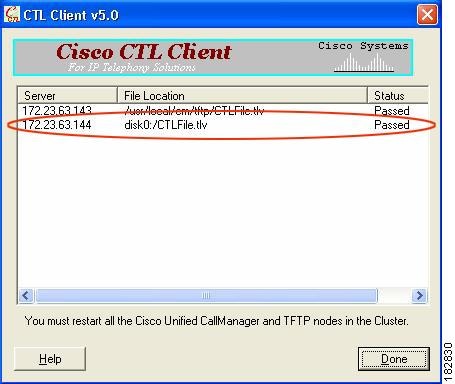
The security appliance does not store the raw CTL file in the flash, rather, it parses the CTL file and installs appropriate trustpoints. Figure 49-5 indicates the installation was successful.
Licensing for the TLS Proxy
The TLS proxy for encrypted voice inspection feature supported by the ASA require a Unified Communications Proxy license.
The following table shows the Unified Communications Proxy license details by platform:

Note![]() This feature is not available on No Payload Encryption models.
This feature is not available on No Payload Encryption models.
|
|
|
|---|---|
| Optional licenses: 24, 50, 100, 250, 500, 750, or 1000 sessions. |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, 1000, or 2000 sessions. |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, 1000, 2000, or 3000 sessions. |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, 1000, 2000, 3000, 5000, or 10,000 sessions.2 |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, or 1000 sessions. |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, 1000, or 2000 sessions. |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, 1000, 2000, or 3000 sessions. |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, 1000, 2000, or 3000 sessions. |
|
| Optional licenses: 24, 50, 100, 250, 500, 750, 1000, 2000, 3000, 5000, or 10,000 sessions. 2 |
Table 49-1 shows the default and maximum TLS session details by platform.
|
|
|
|
|---|---|---|
For more information about licensing, see Chapter4, “Managing Feature Licenses”
Prerequisites for the TLS Proxy for Encrypted Voice Inspection
Before configuring TLS proxy, the following prerequisites are required:
- You must set clock on the security appliance before configuring TLS proxy. To set the clock manually and display clock, use the clock set and show clock commands. We recommend that the security appliance use the same NTP server as the Cisco Unified CallManager cluster. TLS handshake may fail due to certificate validation failure if clock is out of sync between the security appliance and the Cisco Unified CallManager server.
- 3DES-AES license is needed to interoperate with the Cisco Unified CallManager. AES is the default cipher used by the Cisco Unified CallManager and Cisco IP Phone.
- Import the following certificates which are stored on the Cisco UCM. These certificates are required by the ASA for the phone proxy.
If LSC provisioning is required or you have LSC enabled IP phones, you must import the CAPF certificate from the Cisco UCM. If the Cisco UCM has more than one CAPF certificate, you must import all of them to the ASA.
See Chapter48, “Configuring the Cisco Phone Proxy”For example, the CA Manufacturer certificate is required by the phone proxy to validate the IP phone certificate.
Configuring the TLS Proxy for Encrypted Voice Inspection
This section includes the following topics:
- Task flow for Configuring the TLS Proxy for Encrypted Voice Inspection
- Creating Trustpoints and Generating Certificates
- Creating an Internal CA
- Creating a CTL Provider Instance
- Creating the TLS Proxy Instance
- Enabling the TLS Proxy Instance for Skinny or SIP Inspection
Task flow for Configuring the TLS Proxy for Encrypted Voice Inspection
To configure the security appliance for TLS proxy, perform the following steps:
Step 1![]() (Optional) Set the maximum number of TLS proxy sessions to be supported by the security appliance using the following command, for example:
(Optional) Set the maximum number of TLS proxy sessions to be supported by the security appliance using the following command, for example:

Note![]() The tls-proxy maximum-sessions command controls the memory size reserved for cryptographic applications such as TLS proxy. Crypto memory is reserved at the time of system boot. You may need to reboot the security appliance for the configuration to take effect if the configured maximum sessions number is greater than the currently reserved.
The tls-proxy maximum-sessions command controls the memory size reserved for cryptographic applications such as TLS proxy. Crypto memory is reserved at the time of system boot. You may need to reboot the security appliance for the configuration to take effect if the configured maximum sessions number is greater than the currently reserved.
Step 2![]() Create trustpoints and generate certificates for the TLS Proxy for Encrypted Voice Inspection. See Creating Trustpoints and Generating Certificates.
Create trustpoints and generate certificates for the TLS Proxy for Encrypted Voice Inspection. See Creating Trustpoints and Generating Certificates.
Step 3![]() Create the internal CA to sign the LDC for Cisco IP Phones. See Creating an Internal CA.
Create the internal CA to sign the LDC for Cisco IP Phones. See Creating an Internal CA.
Step 4![]() Create the CTL provider instance. See Creating a CTL Provider Instance.
Create the CTL provider instance. See Creating a CTL Provider Instance.
Step 5![]() Create the TLS proxy instance. See Creating the TLS Proxy Instance.
Create the TLS proxy instance. See Creating the TLS Proxy Instance.
Step 6![]() Enable the TLS proxy y with SIP and Skinny inspection. See Enabling the TLS Proxy Instance for Skinny or SIP Inspection.
Enable the TLS proxy y with SIP and Skinny inspection. See Enabling the TLS Proxy Instance for Skinny or SIP Inspection.
Step 7![]() Export the local CA certificate (ldc_server) and install it as a trusted certificate on the Cisco UCM server.
Export the local CA certificate (ldc_server) and install it as a trusted certificate on the Cisco UCM server.
a.![]() Use the following command to export the certificate if a trust-point with proxy-ldc-issuer is used as the signer of the dynamic certificates, for example:
Use the following command to export the certificate if a trust-point with proxy-ldc-issuer is used as the signer of the dynamic certificates, for example:
b.![]() For the embedded local CA server LOCAL-CA-SERVER, use the following command to export its certificate, for example:
For the embedded local CA server LOCAL-CA-SERVER, use the following command to export its certificate, for example:
Save the output to a file and import the certificate on the Cisco UCM. For more information, see the Cisco Unified CallManager document: http://www.cisco.com/univercd/cc/td/doc/product/voice/c_callmg/5_0/iptp_adm/504/iptpch6.htm#wp1040848
After this step, you may use the Display Certificates function on the Cisco Unified CallManager GUI to verify the installed certificate:
http://www.cisco.com/univercd/cc/td/doc/product/voice/c_callmg/5_0/iptp_adm/504/iptpch6.htm#wp1040354
Step 8![]() Run the CTL Client application to add the server proxy certificate (ccm_proxy) to the CTL file and install the CTL file on the security appliance. See the Cisco Unified CallManager document for information on how to configure and use CTL Client:
Run the CTL Client application to add the server proxy certificate (ccm_proxy) to the CTL file and install the CTL file on the security appliance. See the Cisco Unified CallManager document for information on how to configure and use CTL Client:
http://www.cisco.com/univercd/cc/td/doc/product/voice/c_callmg/5_1/nci/p08/secuauth.htm

Note![]() You will need the CTL Client that is released with Cisco Unified CallManager Release 5.1 to interoperate with the security appliance. See the “CTL Client Overview” section for more information regarding TLS proxy support.
You will need the CTL Client that is released with Cisco Unified CallManager Release 5.1 to interoperate with the security appliance. See the “CTL Client Overview” section for more information regarding TLS proxy support.
Creating Trustpoints and Generating Certificates
The Cisco UCM proxy certificate could be self-signed or issued by a third-party CA. The certificate is exported to the CTL client.
Import the required certificates, which are stored on the Cisco UCM. See the “Certificates from the Cisco UCM” section and the “Importing Certificates from the Cisco UCM” section.
Once you have created the trustpoints and generated the certificates, create the internal CA to sign the LDC for Cisco IP Phones. See Creating an Internal CA.
Creating an Internal CA
Create an internal local CA to sign the LDC for Cisco IP Phones.
This local CA is created as a regular self-signed trustpoint with proxy-ldc-issuer enabled. You can use the embedded local CA LOCAL-CA-SERVER on the ASA to issue the LDC.
Once you have created the internal CA, create the CTL provider instance. See Creating a CTL Provider Instance.
Creating a CTL Provider Instance
Create a CTL Provider instance in preparation for a connection from the CTL Client.
The default port number listened by the CTL Provider is TCP 2444, which is the default CTL port on the Cisco UCM. Use the service port command to change the port number if a different port is used by the Cisco UCM cluster.
Once you have created the CTL provider instance, create the TLS proxy instance. See Creating the TLS Proxy Instance.
Creating the TLS Proxy Instance
Create the TLS proxy instance to handle the encrypted signaling.
Once you have created TLS proxy instance, enable the TLS proxy instance for Skinny and SIP inspection. See Enabling the TLS Proxy Instance for Skinny or SIP Inspection.
Enabling the TLS Proxy Instance for Skinny or SIP Inspection
Enable TLS proxy for the Cisco IP Phones and Cisco UCMs in Skinny or SIP inspection. The following procedure shows how to enable the TLS proxy instance for Skinny inspection.
Monitoring the TLS Proxy
You can enable TLS proxy debug flags along with SSL syslogs to debug TLS proxy connection problems. For example, using the following commands to enable TLS proxy-related debug and syslog output only:
The following is sample output reflecting a successful TLS proxy session setup for a SIP phone:
Use the show tls-proxy commands with different options to check the active TLS proxy sessions. The following are some sample outputs:
Feature History for the TLS Proxy for Encrypted Voice Inspection
Table 49-2 lists the release history for this feature.
|
|
|
|
|---|---|---|
 Feedback
Feedback