- Configuring ATM
- AAL1 CES on AIM-ATM
- DHCP Client on WAN Interfaces
- Lossless Compression and ATM Cell Switching and BITS Clocking
- ATM Multilink PPP Support on Multiple VCs
- ATM OAM Support for F5 Continuity Check
- ATM OAM Ping
- ATM Policing by Service Category for SVC SoftPVC
- Configuring ATM SNMP Trap and OAM Enhancements
- ATM SVC Troubleshooting Enhancements
- ATM Software Segmentation and Reassembly
- Unspecified Bit Rate Plus and ATM Enhancements
- Enhanced Voice and QoS for ADSL and G.SHDSL
- End of Life for Multiprotocol over ATM
- Multiprotocol over ATM Overview
- Configuring the Multiprotocol over ATM Client
- Configuring the Multiprotocol over ATM Server
- Configuring Token Ring LAN Emulation MPOA
- MPLS Diff-Serv-aware Traffic Engineering over ATM
- End of Life for LAN Emulation
- LAN Emulation Overview
- Configuring LAN Emulation
- Configuring Token Ring LAN Emulation
- SNMP Trap Support for the Virtual Switch Interface Master MIB
- VLAN 0 Priority Tagging Support
- Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Reuse MAC for ATM Route-Bridge Encapsulation
- Index
Asynchronous Transfer Mode Configuration Guide, Cisco IOS Release 15M&T
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- December 2, 2012
Chapter: Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Finding Feature Information
- Prerequisites for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Restrictions for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Information About Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- How to Configure Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Configuration Examples for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Additional References
- Feature Information for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Glossary
Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
The Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks feature allows 802.1Q tags to be transported over ATM permanent virtual circuits (PVC) used in Asymmetric Digital Subscriber Line 2+ (ADSL2+) uplinks. Additionally, 802.1P marking is allowed and is based on 802.1Q tagging.
 Note |
Although this document uses the generic term ADSL, this feature requires an ADSL2+ uplink. |
- Finding Feature Information
- Prerequisites for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Restrictions for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Information About Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- How to Configure Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Configuration Examples for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Additional References
- Feature Information for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Glossary
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
Restrictions for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
Information About Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Benefits of Preserve 802.1Q Tagging with 802.1P Marking
- VLAN-Based Service Differentiation over ADSL
- Transporting 802.1P Marked 802.1Q Tags
Benefits of Preserve 802.1Q Tagging with 802.1P Marking
- CPE can carry traffic with 802.1P-marked provider-specific 802.1Q tags.
- Voice, video, and data services can be deployed at customer premises. This service combination offers a real-time channel dedicated to VoIP traffic and a second channel that delivers best-effort Internet service.
- All traffic is marked with an 802.1P marking which is implemented using VLAN-based service differentiation.
 Note |
Support for PVCs configured with Route-Bridge Encapsulation (RBE) was introduced with CSCtt22809. |
VLAN-Based Service Differentiation over ADSL
VLAN-based service differentiation allows service providers to offer a range of broadband-enabled services and applications to end users. It supports IP connectivity applications that require real-time network performance and applications that use best-effort, or Internet-grade performance.
The original VLAN tag in an inbound packet is changed to the value configured by the bridge-dot1q encap command before the tag leaves the device. For example, if you enter the command bridge-dot1q encap 10, a VLAN tag of 70 in a packet inbound from the local network is changed to a value of 10 in the egress packet. Any 802.1P value is changed to 0, and frames without VLAN tags are sent out over ATM with an added VLAN header as shown in the figure in the "Transporting 802.1P Marked 802.1Q Tags" section.
From an Ethernet perspective, this service is carried over a dedicated VLAN from the hand-over point to the end-user premises. This VLAN-based service differentiation at the PVC level is shown in the figure below.
| Figure 1 | VLAN-Based Service Differentiation at PVC Level |
The Ethernet VLAN used by the voice, video, and data services must be identified at the customer premises by an 802.1Q VLAN ID configured using the bridge-dot1q encap command. The VLAN is identified at the service provider's end by a service-provider-assigned 802.1ad customer VLAN ID.
The bridge-dot1q encap command changes the local VLAN ID to the VLAN ID required by the service provider. The operation of this command is shown in the figure below.
| Figure 2 | Operation of the bridge-dot1q encap Command |

The figures in the "Transporting 802.1P Marked 802.1Q Tags" section show the PDU data structure in greater detail.
Transporting 802.1P Marked 802.1Q Tags
An 802.1Q VLAN tag is inserted into the MAC Protocol Data Unit (PDU), and this PDU is sent to the Digital Subscriber Line Access Multiplexer (DSLAM). Incoming and outgoing PDU structures are shown in the two figures below.
The figure below shows the packet structure when the incoming Ethernet frames do not have a VLAN header.
| Figure 3 | Incoming and Outgoing Packet Structures When No Incoming VLAN ID Is Present |
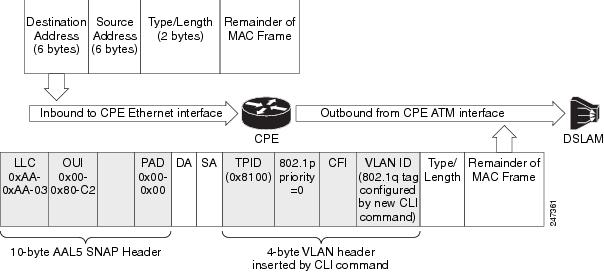
The figure below shows that a 4-byte VLAN header has been inserted in the outgoing packet, with an 802.1P value. The VLAN ID value is configured by the bridge-dot1q encap command.
The figure below shows the incoming packet structure when the incoming Ethernet packets contain a VLAN header.
| Figure 4 | Incoming and Outgoing Packet Structures When an Incoming VLAN ID Is Present |
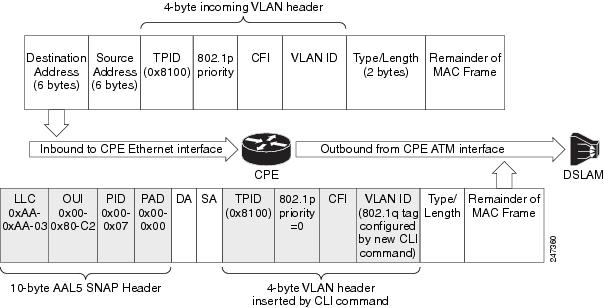
The outgoing packet structure is the same as in figure 1.
 Note |
The 802.1P priority that was configured earlier is changed to 0, and any VLAN ID that is configured is set to the ID configured by the bridge-dot1q encap command. |
The CPE is connected to the DSLAM via an ATM interface that is configured as the bridging interface. The CPE establishes a PPP over Ethernet (PPPoE) session over the bridging ATM interface with the service provider. The VLAN and voice traffic enter customer devices via VLAN ports or a Switched Virtual Interface (SVI).
In the CPE, the packet is classified as data or voice traffic based on the VLAN ID, Differentiated Services Code Point (DSCP), protocol, source MAC address, or port. The packets are marked with the quality of service (QoS) group, and routed from VLAN via the Bridge Virtual Interface (BVI) to the ATM PVC bridging interface.
If the packet requires encapsulation, ATM provides the default VLAN ID. If there is a QoS service policy attached to the PVC, packets are classified against the QoS group. QoS marks the corresponding VLAN ID and 802.1P or class of service (CoS) value into the packet VLAN header. The QoS VLAN ID overwrites the default VLAN ID. If there is no service policy attached in PVC, the packets are sent out with the default VLAN ID and default CoS marking.
Packets returning from the service provider's network and destined to the customer's network carry VLAN tags. The ATM PVC interface removes the VLAN tag before passing it for further processing. These packets do not require classification or QoS marking.
Using PPPoE, the CPE device acts as a PPPoE Dialer client and gets the IP address dynamically from the service provider by using the Point-to-Point Protocol. The Dialer interface has to be configured and associated with the ATM PVC interface. The packets are sent out with the default VLAN ID as PPPoE supports only one VLAN ID per PVC. PPP control packets such as PPPoE Active Discovery Initiation (PADI), PPPoE Active Discovery Request (PADR), PPPoE Active Discovery Terminate (PADT) and keepalive packets are marked with higher priority CoS markings similar to the real-time traffic. The VLAN header has to be removed from the packet at the ingress interface (ATM PVC) when the packet returns.
How to Configure Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
Configuring Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs
Perform this task to configure the Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks feature.
 Note |
Only one bridge-dot1q encap vlan-id command can be configured under a PVC. Only one VLAN ID is allowed per session using PPPoE. The PPPoE session can be disconnected if the configured VLAN ID (set using the set vlan-inner or bridge-dot1q encap vlanid command) differs from the default VLAN ID. |
DETAILED STEPS
Troubleshooting Tips
You need to verify that the bridge-dot1q encap and encapsulation aal5snap commands are configured to carry the tagged VLAN traffic if the 802.1P marked 802.1Q tags are not transported in the MAC PDUs sent to the DSLAM.
Configuration Examples for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
- Example: Traffic from Multiple Incoming VLANs Bridged to a VLAN
- Example: Traffic from Multiple VLANs Arrives at the Router over a Layer 3 Port
Example: Traffic from Multiple Incoming VLANs Bridged to a VLAN
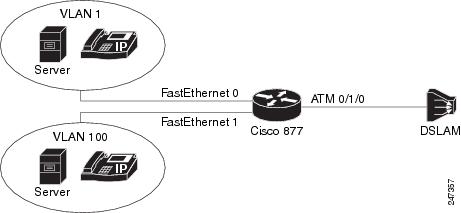
The following example shows how the traffic from multiple incoming VLANs is bridged to a single outgoing VLAN. The traffic arrives on Layer 2 Fast Ethernet ports and a DHCP server assigns IP addresses on the private network. Network Address Translation (NAT) is enabled. A static IP address is used on the outgoing Bridge-Group Virtual Interface (BVI) interface.
This topology is shown in the figure below.
| Figure 5 | Topology: Traffic from Multiple Incoming VLANs Bridged to a Single Outgoing VLAN |

The following configuration is for the Cisco 877 router.
ip dhcp excluded-address 192.168.10.1 ip dhcp excluded-address 192.168.20.1 ! ip dhcp pool test_pool1 network 192.168.10.0 255.255.255.0 default-router 192.168.10.1 ! ip dhcp pool test_pool2 network 192.168.20.0 255.255.255.0 default-router 192.168.20.1 ! ! bridge irb ! ! interface ATM0 no ip address no atm ilmi-keepalive ! interface ATM0.1 point-to-point bridge-group 1 bridge-group 1 spanning-disabled pvc 0/110 bridge-dot1q encap 10 encapsulation aal5snap ! interface FastEthernet0 switchport access vlan 1 ! interface FastEthernet1 switchport access vlan 100 ! interface Vlan1 ip address 192.168.10.1 255.255.255.0 ip nat inside ip virtual-reassembly ! interface Vlan100 ip address 192.168.20.1 255.255.255.0 ip nat inside ip virtual-reassembly ! interface BVI1 ip address 10.0.0.0 255.0.0.0 ip nat outside ip virtual-reassembly ! ip forward-protocol nd ip route 0.0.0.0 0.0.0.0 10.0.0.2 ip nat pool test 10.0.0.0 10.0.0.0 netmask 255.0.0.0 ip nat inside source list 101 pool test overload ip nat inside source list 102 pool test overload ! access-list 101 permit ip 192.168.10.0 0.0.0.255 any log access-list 102 permit ip 192.168.20.0 0.0.0.255 any log ! bridge 1 protocol ieee bridge 1 route ip !
Example: Traffic from Multiple VLANs Arrives at the Router over a Layer 3 Port
The following example shows how traffic from multiple VLANs arrives at the router over a Layer 3 port. All this traffic is bridged over a single ATM virtual circuit to the service provider's DSLAM and tagged with a single VLAN tag. Both WAN and LAN IP addresses are provided by DHCP servers.
This topology is shown in the figure below.
| Figure 6 | Topology: Traffic From Multiple VLANs Arrives at the Router over a Layer 3 Port |

The following configuration is for the Cisco 877 router.
ip dhcp excluded-address 192.168.10.1 ip dhcp excluded-address 192.168.20.1 ! ip dhcp pool test_pool1 network 192.168.10.0 255.255.255.0 default-router 192.168.10.1 ! ip dhcp pool test_pool2 network 192.168.20.0 255.255.255.0 default-router 192.168.20.1 ! bridge irb ! ! interface FastEthernet0/1 no ip address duplex auto speed auto ! interface FastEthernet0/1.1 encapsulation dot1Q 100 ip address 192.168.10.1 255.255.255.0 ip nat inside ip virtual-reassembly ! interface FastEthernet0/1.2 encapsulation dot1Q 1 native ip address 192.168.20.1 255.255.255.0 ip nat inside ip virtual-reassembly ! interface ATM0/1/0 no ip address no atm ilmi-keepalive ! ! interface ATM0/1/0.1 point-to-point bridge-group 1 bridge-group 1 spanning-disabled pvc 9/117 bridge-dot1q encap 10 encapsulation aal5snap ! ! interface BVI1 ip address dhcp ip nat outside ip virtual-reassembly ! ip forward-protocol nd ! ip nat inside source list 101 interface BVI1 overload ip nat inside source list 102 interface BVI1 overload ! access-list 101 permit ip 192.168.10.0 0.0.0.255 any log access-list 102 permit ip 192.168.20.0 0.0.0.255 any log ! bridge 1 protocol ieee bridge 1 route ip
Additional References
Related Documents
| Related Topic |
Document Title |
|---|---|
| Cisco IOS commands |
|
| ATM commands |
Standards and RFCs
| Standard/RFC |
Title |
|---|---|
| IEEE 802.1P |
Traffic Class Expediting and Dynamic Multicast Filtering |
| IEEE 802.1Q |
Virtual LANs |
| IEEE 802.3 |
LAN/MAN CSMA/CD (Ethernet) Access Method |
| ITU-T G.992.1 (G.dmt) |
Asymmetrical Digital Subscriber Line (ADSL) Transceivers |
| ITU-T G.992.5 |
Asymmetrical Digital Subscriber Line (ADSL) Transceivers-Extended Bandwidth ADSL2 (ADSL2+) |
| ITU-T I363.5 |
B-ISDN ATM Adaptation Layer Specification: Type 5 AAL |
Technical Assistance
| Description | Link |
|---|---|
| The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 1 | Feature Information for Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks |
| Feature Name |
Releases |
Feature Information |
|---|---|---|
| Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks |
15.1(2)T |
The Preserve 802.1Q Tagging with 802.1P Marking over ATM PVCs for xDSL Uplinks feature allows 802.1P marking based on 802.1Q tags and transportation of these tags over ATM PVC used in ADSL2+ uplinks. The following commands were introduced: pppoe-client control-packets vlan cos, set vlan-inner. |
| Transporting VLAN Tags over DSL Links |
15.0(1)XA |
The Transporting VLAN Tags over DSL Links feature allows 802.1Q tags to be transported over ATM PVCs used in ADSL2+ uplinks. The following command was introduced: bridge-dot1q encap. |
Glossary
802.1ad--An amendment to IEEE 802.1Q that enables a service provider to offer bridged VLANs over its network.
802.1P--A 3-bit field within an Ethernet frame header added when using IEEE 802.1Q on an IEEE 802.1D network. It specifies a priority value from 0 and 7 that can be used by quality of service (QoS) disciplines to differentiate traffic.
802.1Q--A networking standard written by the IEEE 802.1 workgroup allowing multiple bridged networks to transparently share the same physical network link without leakage of information between networks. 802.1Q is commonly referred to as VLAN tagging.
AAL5SNAP--ATM Adaptation Layer 5 Subnetwork Protocol Access Protocol. A type of network encapsulation that supports multiplexing of two or more protocols over a virtual circuit.
ATM--Asynchronous Transfer Mode. The international standard for cell relay in which multiple service types (such as voice, video, or data) are conveyed in fixed-length (53-byte) cells. Fixed-length cells allow cell processing to occur in hardware, thereby reducing transit delays. ATM is designed to take advantage of high-speed transmission media, such as E3, SONET, and T3.
BVI--Bridge Group Virtual Interface. A logical Layer 3-only interface associated with a bridge group when integrated bridging and routing (IRB) is configured.
CPE--Customer premises equipment. Terminating equipment, such as terminals, telephones, and modems, supplied by the telephone company, installed at customer sites, and connected to the telephone company network. This term can also refer to any telephone equipment residing on the customer site.
CVLAN--Customer Virtual Local Area Network.
DSL--Digital subscriber line. A public network technology that delivers high bandwidth over conventional copper wiring at limited distances. There are four types of DSL: ADSL, HDSL, SDSL, and VDSL.
DSLAM--Digital subscriber line access multiplexer. A device that connects many digital subscriber lines to a network by multiplexing the DSL traffic onto one or more network trunk lines.
IRB--Integrated routing and bridging. Integrated Services Digital Network (ISDN) User Part. An upper-layer application supported by Signalling System 7 for connection setup and tear down.
NAT--Network Address Translation. A mechanism for reducing the need for globally unique IP addresses. NAT allows an organization with addresses that are not globally unique to connect to the Internet by translating those addresses into globally routable address space. Also known as Network Address Translator.
PVC--Permanent virtual circuit (or connection). A virtual circuit that is permanently established. PVCs save bandwidth associated with circuit establishment and tear down in situations where certain virtual circuits must exist all the time. In ATM terminology, this is called a permanent virtual connection.
VoIP--Voice over IP. The capability to carry normal telephony-style voice over an IP-based Internet with plain old telephone service (POTS) like functionality, reliability, and voice quality.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
 Feedback
Feedback