NAT in Catalyst 6500/6000 Switches Configuration Example
Available Languages
Contents
Introduction
This document explains how to configure Network Address Translation (NAT) on Cisco Catalyst 6500/6000 Series Switches.
Prerequisites
Requirements
Ensure that you meet these requirements before you attempt this configuration:
-
Familiarity with how NAT works.
Refer to How NAT Works for more information.
-
Familiarity with the commands to use in order to configure NAT on a router.
For more information on the commands, refer to Configuring Network Address Translation: Getting Started.
Components Used
The information in this document is based on the Cisco Catalyst 6500 Series Switch with Supervisor Engine 720 that runs Cisco IOS® Software Release 12.2(18)SXD6 and the Cisco Catalyst 6500 Series Switch with Supervisor Engine II that runs CatOS Software Release 8.4(4).
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Related Products
This configuration can also be used with Cisco Catalyst 6000 Series Switches.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Configure
In this section, you are presented with the information to configure the features described in this document.
Note: Use the Command Lookup Tool (registered customers only) to obtain more information on the commands used in this section.
Network Diagram
This document uses this network setup:
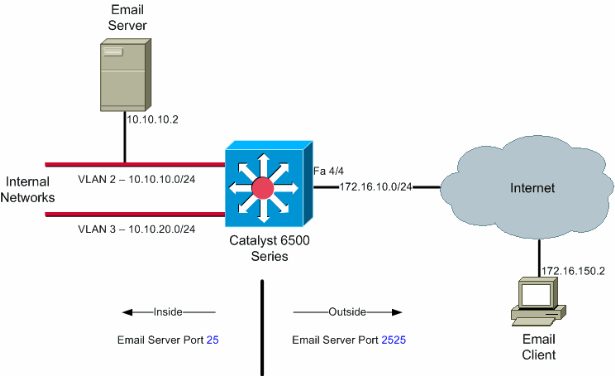
Note: The IP addressing schemes used in this configuration are not legally routable on the Internet. They are RFC 1918 addresses which have been used in a lab environment.
Cisco IOS Configurations
In this configuration example, NAT is configured to overload on the interface FastEthernet 4/4 IP address. This means that more than one inside local address can be dynamically translated to the same global address. In this case, the address assigned to interface FastEthernet 4/4.
In addition, NAT is statically configured so that packets sourced from local address 10.10.10.2 with TCP port 25 (SMTP) are translated to interface FastEthernet 4/4 IP address TCP port 2525. Since this is a static NAT entry, email clients on the outside can originate SMTP packets to the global address of 172.16.10.64. The outside port has been chosen as 2525 to prevent any Denial of Service attacks.
| Catalyst 6500 in Native Mode |
|---|
6509sup720#show running-config Building configuration... Current configuration : 7524 bytes ! version 12.2 service timestamps debug datetime service timestamps log datetime msec localtime service password-encryption service counters max age 10 ! hostname 6509sup720 ! boot system sup-bootflash:s72033-psv-mz.122-18.SXD6.bin !username maui-nas-05 password cisco ! no ip domain-lookup ! no mls flow ip no mls flow ipv6 spanning-tree mode pvst ! redundancy mode sso main-cpu ! ! interface FastEthernet4/4 ip address 172.16.10.64 255.255.255.0 ip nat outside !--- Defines interface FastEthernet 4/4 with an IP address and as a !--- NAT outside interface. ! interface Vlan2 ip address 10.10.10.1 255.255.255.0 ip nat inside !--- Defines interface VLAN 2 with an IP address and as a NAT inside !--- interface. ! interface Vlan3 ip address 10.10.20.1 255.255.255.0 ip nat inside !--- Defines interface VLAN 3 with an IP address and as a NAT inside !--- interface. ! ip nat inside source list 100 interface FastEthernet 4/4 overload !--- Specifies the translation for inside workstations and !--- servers to access the outside world. ip nat inside source static tcp 10.10.10.2 25 interface FastEthernet 4/4 2525 !--- Specifies the static mapping for the outside email clients !--- to access the inside email server. !--- Refer to ip nat inside source for more details !--- on the command. ! ! ip classless no ip http server ! !--- ACL 100 permits only the desired traffic for translation. access-list 100 permit ip 10.10.10.0 0.0.0.255 any access-list 100 permit ip 10.10.20.0 0.0.0.255 any ! line con 0 transport input none line vty 0 4 ! end |
CatOS Configurations
For switches that run in Hybrid mode you need to first configure the VLANs on the Supervisor and then apply the NAT configuration on the MSFC. Instead of having an outside port interface, you need to configure an interface VLAN since, in Hybrid mode, you cannot specify an IP addresses for a particular port.
| Catalyst 6500 in Hybrid Mode Configurations on the Supervisor (Switch Processor) |
|---|
!--- Configure VLAN 2, VLAN 3 and VLAN 4 on the Supervisor. !--- Add VLAN 2. Catalyst6500> (enable) set vlan 2 VLAN 2 configuration successful !--- Add VLAN 3. Catalyst6500> (enable) set vlan 3 VLAN 3 configuration successful !--- Add VLAN 4. Catalyst6500> (enable) set vlan 4 VLAN 4 configuration successful !--- Assign port fa4/4 to VLAN 4. Catalyst6500> (enable) set vlan 4 4/4 VLAN 4 modified. VLAN 1 modified. VLAN Mod/Ports ---- ----------------------- 4 4/4 Catalyst6500> (enable) |
| Catalyst 6500 in Hybrid Mode Configurations on the MSFC (Route Processor) |
|---|
MSFC#show running-config Building configuration... Current configuration : 1024 bytes ! version 12.1 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname Router ! boot system flash bootflash:c6msfc2-jk2o3sv-mz.121-26.E1.bin ! ip subnet-zero ! ! ! ip ssh time-out 120 ip ssh authentication-retries 3 redundancy high-availability single-router-mode ! ! ! ! ! interface Vlan2 ip address 10.10.10.1 255.255.255.0 ip nat inside !--- Defines interface VLAN 2 with an IP address and as a NAT inside !--- interface. ! interface Vlan3 ip address 10.10.20.1 255.255.255.0 ip nat inside !--- Defines interface VLAN 3 with an IP address and as a NAT inside !--- interface. ! interface Vlan4 ip address 172.16.10.64 255.255.255.0 ip nat outside !--- Defines interface VLAN 4 with an IP address and as a NAT outside !--- interface. ! ip nat inside source list 100 interface Vlan4 overload !--- Specifies the translation for inside workstations and !--- servers to access the outside world. ip nat inside source static tcp 10.10.10.2 25 interface Vlan4 2525 !--- Specifies the static mapping for the outside email clients !--- to access the inside email server. ip classless no ip http server ! access-list 100 permit ip 10.10.10.0 0.0.0.255 any access-list 100 permit ip 10.10.20.0 0.0.0.255 any !--- ACL 100 permits only the desired traffic for translation. ! ! line con 0 line vty 0 4 no login ! ! end |
Verify
Use this section to confirm that your configuration works properly.
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output
-
show ip nat translations—Displays active NAT translations.
Cat6k#show ip nat translations Pro Inside global Inside local Outside local Outside global tcp 172.16.10.64:2525 10.10.10.2:25 --- ---
-
show ip access-list—Displays the contents of all current IP access lists.
Cat6k#show ip access-lists Extended IP access list 100 permit ip 10.10.10.0 0.0.0.255 any (32 matches) permit ip 10.10.20.0 0.0.0.255 any (22 matches) deny ip any any -
show ip nat statistics—Displays NAT statistics.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Troubleshooting Commands
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output.
Note: Refer to Important Information on Debug Commands before you use debug commands.
-
debug ip nat—Displays information about IP packets translated by the IP NAT feature.
Cat6k#debug ip nat IP NAT debugging is on Cat6k# *Mar 1 01:40:47.692 CET: NAT: s=10.10.10.2->172.16.10.4, d=172.16.150.2 [80] *Mar 1 01:40:47.720 CET: NAT*: s=172.16.150.2, d=172.16.10.4->10.10.10.2 [80] *Mar 1 01:40:47.720 CET: NAT*: s=10.10.20.2->172.16.10.4, d=172.16.150.2 [81] *Mar 1 01:40:47.748 CET: NAT*: s=172.16.150.2, d=172.16.10.4->10.10.20.2 [81] *Mar 1 01:40:47.748 CET: NAT*: s=10.10.10.2->172.16.10.4, d=172.16.150.2 [82] *Mar 1 01:40:47.784 CET: NAT*: s=172.16.150.2, d=172.16.10.4->10.10.10.2 [82] *Mar 1 01:40:47.784 CET: NAT*: s=10.10.20.2->172.16.10.4, d=172.16.150.2 [83] *Mar 1 01:40:47.836 CET: NAT*: s=172.16.150.2, d=172.16.10.4->10.10.20.2 [83] *Mar 1 01:40:47.836 CET: NAT*: s=10.10.10.2->172.16.10.4, d=172.16.150.2 [84] *Mar 1 01:40:47.884 CET: NAT*: s=172.16.150.2, d=172.16.10.4->10.10.10.2 [84]
-
clear ip nat translation *—Clears dynamic Network Address Translation (NAT) translations from the translation table.
Related Commands
-
ip nat—Designates that traffic which originates from or destined for the interface is subject to NAT.
-
ip nat inside destination—Enables NAT of the inside destination address.
-
ip nat inside source—Enables NAT of the inside source address.
-
ip nat outside source—Enables NAT of the outside source address.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
01-Aug-2007 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback