IPS 5.x and later: NTP on IPS Configuration Example
Available Languages
Contents
Introduction
This document provides a sample configuration for synchronizing the Cisco Secure Intrusion Prevention System (IPS) clock with a network time server using Network Time Protocol (NTP). The Cisco router is configured as an NTP server and the IPS sensor is configured to use the NTP server (Cisco router) as the time source.
Prerequisites
Requirements
Ensure that you meet these requirements before you attempt this configuration:
-
The NTP server must be reachable from the Cisco IPS sensor before you start this NTP configuration.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco 4200 Series IPS Device which runs software version 7.0 and later
-
Cisco IPS Manager Express (IME) version 7.0.1 and later
Note: While IME can be used to monitor sensor devices that run Cisco IPS 5.0 and later, some of the new features and functionality delivered in IME are only supported on sensors that run Cisco IPS 6.1 or later.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Related Products
You can also use this document with these hardware and software versions:
-
Cisco 4200 Series IPS Device which runs software versions 6.0 and earlier
-
Cisco IPS Manager Express (IME) version 6.1.1
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Configuration
Configure a Cisco Router to be an NTP Server
The sensor requires an authenticated connection with an NTP server if it is going to use the NTP server as the time source. The sensor supports only the MD5 hash algorithm for key encryption. Use the following procedure to activate a Cisco router to act as an NTP server and use its internal clock as the time source.
Complete these steps to set up a Cisco router to act as an NTP server:
-
Log in to the router.
-
Enter the configuration mode.
router#configure terminal
-
Create the key ID and key value.
router(config)#ntp authentication-key key_ID md5 key_value
The key ID can be a number between 1 and 65535. The key value is text (numeric or character). It is encrypted later. For example:
router(config)#ntp authentication-key 12345 md5 123
Note: The sensor only supports MD5 keys. Keys might already exist on the router. Use the show running configuration command to check for other keys. You can use those values for the trusted key in step 4.
-
Designate the key you just created in step 3 as the trusted key (or use an existing key).
router(config)#ntp trusted-key key_ID
The trusted key ID is the same number as the key ID in step 3. For example:
router(config)#ntp trusted-key 12345
-
Specify the interface on the router with which the sensor will communicate.
router(config)#ntp source interface_name
For example:
router(config)#ntp source FastEthernet 1/0
-
Specify the NTP master stratum number to be assigned to the sensor as shown here:
router(config)#ntp master stratum_number
For example:
router(config)#ntp master 6
Note: The NTP master stratum number identifies the relative position of the server in the NTP hierarchy. You can choose a number between 1 and 15. It is not important to the sensor which number you choose.
Configure the Sensor to Use an NTP Time Source
Complete the steps in this section in order to configure the sensor to use the NTP time source (Cisco router is the NTP time source in this example).
The sensor requires a consistent time source. It is recommended to use an NTP server. Use the following procedure to configure the sensor to use the NTP server as its time source. You can use Authenticated or Unauthenticated NTP.
Note: For Authenticated NTP, you must obtain the NTP server IP address, NTP server key ID, and the key value from the NTP server.
Complete these steps in order to configure the sensor to use an NTP server as its time source:
-
Log in to the CLI using an account with administrator privileges.
-
Enter the configuration mode as shown here:
sensor#configure terminal
-
Enter the service host mode.
sensor(config)# service host
-
NTP can be configured as Authenticated and Unauthenticated NTP.
Complete these steps in order to configure Unauthenticated NTP:
-
Enter the NTP configuration mode.
sensor(config-hos)#ntp-option enabled-ntp-unauthenticated
-
Specify the NTP server IP address.
sensor(config-hos-ena)#ntp-server ip_address
In this example the NTP server IP address is 10.1.1.1.
sensor(config-hos-ena)#ntp-server 10.1.1.1
This is the procedure to configure Unauthenticated NTP using Cisco IPS Manager Express:
-
Choose Configuration > Corp-IPS > Sensor Setup > Time. Then, click the radio button next to Unauthenticated NTP after you provide the IP address of the NTP server as shown in the screenshot.
-
Click Apply.
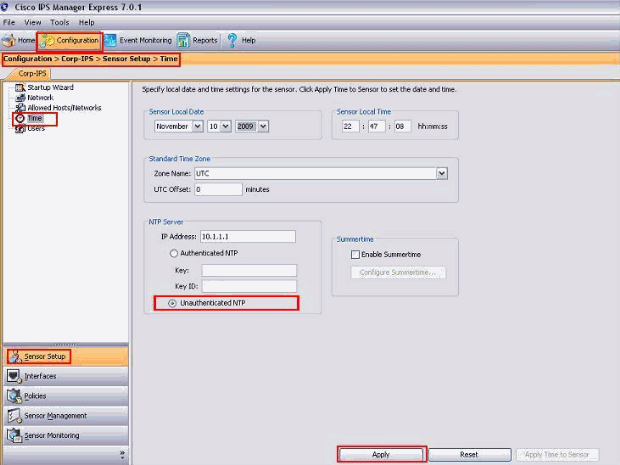
This completes the Unauthenticated NTP configuration.
Complete these steps in order to configure Authenticated NTP:
-
Enter the NTP configuration mode.
sensor(config-hos)#ntp-option enable
-
Specify the NTP server IP address and key ID. The key ID is a number between 1 and 65535. This is the key ID that you already set up on the NTP server.
sensor(config-hos-ena)#ntp-servers ip_address key-id key_ID
In this example the NTP server IP address is 10.1.1.1.
sensor(config-hos-ena)#ntp-server 10.1.1.1 key-id 12345
-
Specify the key value NTP server.
sensor(config-hos-ena)#ntp-keys key_ID md5-key key_value
The key value is text (numeric or character). This is the key value that you already set up on the NTP server. For example:
sensor(config-hos-ena)#ntp-keys 12345 md5-key 123
This is the procedure to configure Authenticated NTP using Cisco IPS Manager Express:
-
Choose Configuration > Corp-IPS > Sensor Setup > Time. Then, click the radio button next to Authenticated NTP after you provide the IP address of the NTP server as shown in the screenshot.
-
Provide the key and the key ID which must be the same as mentioned in the NTP server.
In this example the Key is 123 and the Key ID is 12345.
-
Click Apply.
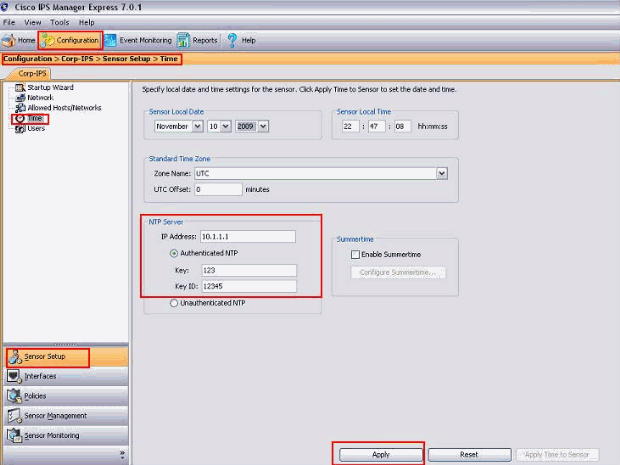
This completes the Authenticated NTP configuration.
-
-
Exit NTP configuration mode.
sensor(config-hos-ena)# exit sensor(config-hos)# exit Apply Changes:?[yes]
-
Press Enter to apply the changes or enter no to discard them.
This completes the configuration task.
Verify
This section provides information you can use to confirm your configuration works properly.
Verify the Authenticated NTP settings. This makes sure that the Authenticated NTP configuration is done correctly.
sensor(config-hos-ena)#show settings
enabled
-----------------------------------------------
ntp-keys (min: 1, max: 1, current: 1)
-----------------------------------------------
key-id: 12345
-----------------------------------------------
md5-key: 123
-----------------------------------------------
-----------------------------------------------
ntp-servers (min: 1, max: 1, current: 1)
-----------------------------------------------
ip-address: 10.1.1.1
key-id: 12345
-----------------------------------------------
-----------------------------------------------
sensor(config-hos-ena)#
In order to display the contents of the configuration contained in the current submode, use the show settings command in any service command mode. This verifies that the Unauthenticated NTP configuration is done correctly.
sensor(config-hos-ena)#show settings
enabled-ntp-unauthenticated
-----------------------------------------------
ntp-server: 10.1.1.1
-----------------------------------------------
sensor(config-hos-ena)#
In order to display the system clock, use the show clock command in EXEC mode as shown. This example shows NTP configured and synchronized:
sensor#show clock detail 11:45:02 CST Tues Jul 20 2011 Time source is NTP sensor#
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
11-Nov-2009 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)


 Feedback
Feedback