Introduction
This document answers the most Frequently Asked Questions (FAQs) related to Secure Shell (SSH). Cisco IOS® SSH code is Cisco original code.
How do I configure SSH terminal-line access (also known as reverse-telnet)?
This was first introduced in some platforms of Cisco IOS Software Release 12.2.2.T.
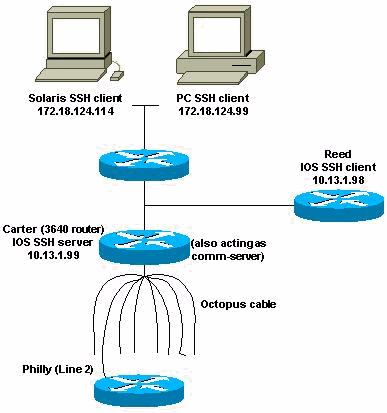
Router(config)#line line-number [ending-line-number]
Router(config-line)#no exec
Router(config-line)#login {local | authentication listname
Router(config-line)#rotary group
Router(config-line)#transport input {all | ssh}
Router(config-line)#exit
Router(config)#ip ssh port portnum rotary group
!--- Line 1 SSH Port Number 2001
line 1
no exec
login authentication default
rotary 1
transport input ssh
!--- Line 2 SSH Port Number 2002
line 2
no exec
login authentication default
rotary 2
transport input ssh
!--- Line 3 SSH Port Number 2003
line 3
no exec
login authentication default
rotary 3
transport input ssh
ip ssh port 2001 rotary 1 3
Command Reference
ip ssh port
ip ssh port portnum rotary group
no ip ssh port portnum rotary group
-
portnum - Specifies the port to which SSH needs to connect, such as 2001.
-
rotary group - Specifies the defined rotary that needs to search for a valid name.
Is SSH supported on the Catalyst 2900?
No, it is not.
How can I determine which platforms and versions of code support SSH?
See the Feature Navigator ( registered customers only) and specify the SSH feature.
When I try to remove certain SSH commands from my router, it continues to ask me to create RSA keys in order to enable SSH. Why is this?
An example of this problem is shown here:
804#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
804(config)#no ip ssh time-out 120
Please create RSA keys to enable SSH.
804(config)#no ip ssh authen
Please create RSA keys to enable SSH.
804(config)
You have encountered Cisco bug ID CSCdv70159 ( registered customers only) .
Does Cisco IOS SSH version 2 support Digital Signature Standard (DSS)?
Cisco IOS SSH version 2 does not support DSS.
Does the Cisco IOS SSH server support agent forwarding?
Cisco IOS SSH does not support agent forwarding. It interoperates with all the commercial SSH implementations.
What client authentication mechanisms are supported on the Cisco IOS SSH server?
Cisco IOS SSH version 2 (SSHv2) supports keyboard-interactive and password-based authentication methods. In addition to these authentication methods, the SSHv2 Enhancements for RSA Keys feature (available in Cisco IOS Software Release 15.0(1)M and later) supports RSA-based public key authentication for the client and server. For additional information on the authentication mechanisms supported by the Cisco IOS SSH server, refer to Secure Shell Version 2 Support.
What does the error Local: Corrupted check bytes on input mean?
Corrupted checkbytes means the SSH packet received failed its integrity check. This is usually because of incorrect decryption. This is also because of an incorrect key used. The incorrect key is caused by the dropping of an encrypted SSH packet. You have either dropped an encrypted packet which should have been sent or dropped a received encrypted packet which should have been decrypted.
Does Cisco IOS support SSH with Blowfish cipher?
Cisco IOS does not support SSH with Blowfish cipher. When an SSH client sends such unsupported cipher, the router displays debug messages mentioned in SSH Client Sends Unsupported (Blowfish) Cipher.
When I try to generate RSA keys for SSH access on a router using the crypto key generate rsa command in config mode, I receive this error: % Invalid input detected at '^' marker.. It does not let the router generate the RSA keys to enable SSH access for the router. How is this error resolved?
This error appears when the image used on the router does not support the crypto key generate rsa command. This command is supported only in security images. In order to resolve this error use the security image of the appropriate series of the Cisco IOS router used.
Do Crypto images support Strong cipher to use SSH with ciphers such as 3DES or AES?
Yes. Only Crypto images support Strong cipher. In order to use SSH with ciphers such as 3DES or AES you must have Crypto images on your Cisco device.
These messages are seen in the logs when I try to configure SSH on a router: SSH2 13: RSA_sign: private key not found and SSH2 13: signature creation failed, status -1. How is this resolved?
These log messages are seen due to Cisco bug IDs CSCsa83601 ( registered customers only) and CSCtc41114 ( registered customers only). Refer to these bugs for more information.
Related Information
