IOS NAT Load-Balancing with Optimized Edge Routing for Two Internet Connections
Available Languages
Contents
Introduction
This document describes a configuration for a Cisco IOS® router to connect a network to the Internet with Network Address Translation through two ISP connections. The Cisco IOS Software Network Address Translation (NAT) can distribute subsequent TCP connections and UDP sessions over multiple network connections if equal-cost routes to a given destination are available. In the event that one of the connections becomes unusable, object-tracking, a component of Optimized Edge Routing (OER), can be used to deactivate the route until the connection becomes available again, which assures network availability in spite of instability or unreliability of an Internet connection.
Prerequisites
Requirements
This document assumes that you have functional LAN and WAN connections; it does not provide configuration or troubleshooting background to establish initial connectivity.
-
This document does not describe a way to differentiate between the routes, so there is no way to prefer a more-desirable connection over a less-desirable connection.
-
This document describes the configuration of OER to enable or disable either Internet route based on the reachability of the DNS servers of the ISP. You need to identify specific hosts that can be reachable through only one of the ISP connections and cannot be available if that ISP connection is not available.
Components Used
This configuration was developed with a Cisco 1811 router with 12.4(15)T Advanced IP Services software. If a different software version is used, some features are potentially not available, or the configuration commands can differ from those shown in this document. Similar configuration are available on all Cisco IOS router platforms although the interface configuration likely varies between different platforms.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Configure
You potentially need to add policy-based routing for specific traffic to ensure that it always uses one ISP connection. Examples of traffic that require this behavior include IPSec VPN clients, VoIP handsets, and any other traffic that use only one of the ISP-connection options to prefer the same IP address, higher speed, or lower latency on the connection.
Note: Use the Command Lookup Tool (registered customers only) to find more information on the commands used in this document.
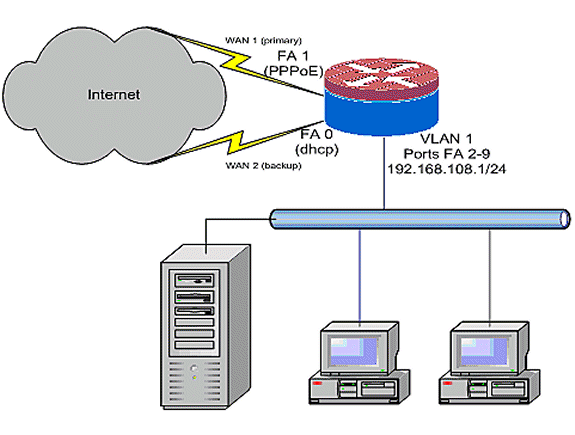
Network Diagram
This document uses this network setup:
Configurations
This configuration example, as illustrated in the network diagram, describes an access router that uses a DHCP-configured IP connection to one ISP (as shown by FastEthernet 0), and a PPPoE connection over the other ISP connection. The connection types have no particular impact on the configuration unless object-tracking and OER and/or policy-based routing is to be used with a DHCP-assigned Internet connection. In these cases, it can be very difficult to define a next-hop router for policy routing or OER.
| Router Configuration Example |
|---|
track timer interface 5 ! ! Configure timers on route tracking ! track 123 rtr 1 reachability delay down 15 up 10 ! track 345 rtr 2 reachability delay down 15 up 10 ! ! Use “ip dhcp client route track [number]” ! to monitor route on DHCP interfaces ! Define ISP-facing interfaces with “ip nat outside” ! interface FastEthernet0 ip address dhcp ip dhcp client route track 345 ip nat outside ip virtual-reassembly ! interface FastEthernet1 no ip address pppoe enable no cdp enable ! interface FastEthernet2 no cdp enable ! interface FastEthernet3 no cdp enable ! interface FastEthernet4 no cdp enable ! interface FastEthernet5 no cdp enable ! interface FastEthernet6 no cdp enable ! interface FastEthernet7 no cdp enable ! interface FastEthernet8 no cdp enable ! interface FastEthernet9 no cdp enable ! ! Define LAN-facing interfaces with “ip nat inside” ! interface Vlan1 description LAN Interface ip address 192.168.108.1 255.255.255.0 ip nat inside ip virtual-reassembly ip tcp adjust-mss 1452 ! ! Define ISP-facing interfaces with “ip nat outside” ! Interface Dialer 0 description PPPoX dialer ip address negotiated ip nat outside ip virtual-reassembly ip tcp adjust-mss ! ip route 0.0.0.0 0.0.0.0 dialer 0 track 123 ! ! Configure NAT overload (PAT) to use route-maps ! ip nat inside source route-map fixed-nat interface Dialer0 overload ip nat inside source route-map dhcp-nat interface FastEthernet0 overload ! ! Configure an OER tracking entry ! to monitor the first ISP connection ! ip sla 1 icmp-echo 172.16.108.1 source-interface Dialer0 timeout 1000 threshold 40 frequency 3 ! ! Configure a second OER tracking entry ! to monitor the second ISP connection ! ip sla 2 icmp-echo 172.16.106.1 source-interface FastEthernet0 timeout 1000 threshold 40 frequency 3 ! ! Set the SLA schedule and duration ! ip sla schedule 1 life forever start-time now ip sla schedule 2 life forever start-time now ! ! Define ACLs for traffic that ! will be NATed to the ISP connections ! access-list 110 permit ip 192.168.108.0 0.0.0.255 any ! ! Route-maps associate NAT ACLs with NAT ! outside on the ISP-facing interfaces ! route-map fixed-nat permit 10 match ip address 110 match interface Dialer0 ! route-map dhcp-nat permit 10 match ip address 110 match interface FastEthernet0 |
With DHCP-assigned route tracking:
| DHCP-Assigned Route Tracking Configuration Example (Optional) |
|---|
interface FastEthernet0 description Internet Intf ip dhcp client route track 123 ip address dhcp ip nat outside ip virtual-reassembly speed 100 full-duplex no cdp enable |
Verify
Use this section to confirm that your configuration works properly.
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output.
-
show ip nat translation — Displays NAT activity between NAT inside hosts and NAT outside hosts. This command provides verification that inside hosts are translated to both NAT outside addresses.
Router# sh ip nat tra Pro Inside global Inside local Outside local Outside global tcp 172.16.108.44:54486 192.168.108.3:54486 172.16.104.10:22 172.16.104.10:22 tcp 172.16.106.42:49620 192.168.108.3:49620 172.16.102.11:80 172.16.102.11:80 tcp 172.16.108.44:1623 192.168.108.4:1623 172.16.102.11:445 172.16.102.11:445 Router#
-
show ip route — Verifies that multiple routes to the Internet are available.
Router# sh ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is 172.16.108.1 to network 0.0.0.0 C 192.168.108.0/24 is directly connected, Vlan1 172.16.0.0/24 is subnetted, 2 subnets C 172.16.108.0 is directly connected, FastEthernet4 C 172.16.106.0 is directly connected, Vlan106 S* 0.0.0.0/0 [1/0] via 172.16.108.1 [1/0] via 172.16.106.1 Router#
Troubleshoot
After you configure the Cisco IOS router with NAT, if the connections do not work, be sure of these:
-
NAT is applied appropriately on outside and inside interfaces.
-
NAT configuration is complete, and ACLs reflect the traffic that must be NATed.
-
Multiple routes to the Internet/WAN are available.
-
If you use route tracking to be sure that the Internet connections are available, check the state of the route tracking.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
15-Nov-2007 |
Initial Release |
 Feedback
Feedback