L2TP Load Balancing and Failover
Available Languages
Contents
Introduction
This document explains the capabilities of a L2TP access concentrator (LAC) that performs load balancing and failover functions to multiple L2TP network servers (LNS).
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
This document is not restricted to specific software and hardware versions.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
LNS Load Balancing
When using RADIUS to deliver virtual private dial-up network (VPDN) tunnel information to a LAC, it is possible to forward users of the same dialed number identification service (DNIS) or domain to multiple LNS. This is a requirement when the incoming tunnels and sessions need to be shared across multiple LNSs to aid in load distribution and offer higher levels of redundancy. In order to enable the load balancing feature, the IP addresses for each LNS that is available as a tunnel endpoint must be delivered in the Cisco vendor-specific attribute (VSA) attribute/value pair.
Cisco:Avpair = "vpdn:ip-addresses=10.51.6.82,10.51.6.59"
The ',' is used as a delimiter to indicate that there are multiple endpoints available to the LAC (you can also use a space as the delimiter to indicate equal priority of tunnel endpoints). The LAC selects which endpoint to use based on the random selection of the first non-active IP address delivered. If this is busy (the LAC cannot connect to the IP address) the next IP address is selected. If there are no non-active IP addresses available, the next selection is based on an IP address that is in 'open tunnel state', and finally an IP address that is 'pending tunnel state'.
LNS Failover
Cisco IOS® software allows a maximum of six priority levels when utilizing multiple LNSs. By using the '/' as the delimiter, you can assign different priority groups to the LNS that are downloaded to the LAC. This allows certain LNSs to operate as the primary LNS and others as a backup. As before, the tunnel endpoints are delivered in the Cisco VSA attribute/value pair.
Cisco:Avpair = "vpdn:ip-addresses=10.51.6.82/10.51.6.59"
The '/' delimiter indicates that 10.51.6.82 is in Priority Group 1 and 10.51.6.59 is in Priority Group 2.
LNS Load Balancing and Failover
It is possible to use both load balancing and failover in the same profile. This is achieved by using the Cisco VSA attribute/value pair "vpdn:ip-addresses", as shown here:
Cisco:Avpair = "vpdn:ip-addresses= 1.1.1.1,2.2.2.2/3.3.3.3,4.4.4.4/5.5.5.5,6.6.6.6"
This is interpreted as:
-
tunnel endpoints 1.1.1.1 and 2.2.2.2 are in Priority Group 1
-
tunnel endpoints 3.3.3.3 and 4.4.4.4 are in Priority Group 2
-
tunnel endpoints 5.5.5.5 and 6.6.6.6 are in Priority Group 3
The load balancing function is performed on Priority Group 1 - non-active/non-busy, open, pending. If none are available at this priority level, go to the next priority level, and continue the selection logic.
Lab Testing
The testing in this section shows three different scenarios for using the load balancing and failover features:
-
LNS load balancing using Cisco vendor-specific attribute/value pairs
-
LNS Failover using Cisco vendor-specific attribute/value pairs
-
LNS load balancing and failover using Cisco vendor-specific attribute/value pairs
LNS Load Balancing using Cisco Vendor-Specific Attribute/Value Pairs
RADIUS Profile
RADIUS user and tunnel profiles on Merit RADIUS Server 3.6B:
2500-1 Password = "cisco" Service-Type = Framed, Framed-Protocol = PPP, Framed-IP-Address = 255.255.255.255 dnis:614629 Password = "cisco" Service-Type = Outbound, Cisco:Avpair = "vpdn:tunnel-type=l2tp", Cisco:Avpair = "vpdn:tunnel-id=hgw", Cisco:Avpair = "vpdn:ip-addresses=10.51.6.82,10.51.6.59", Cisco:Avpair = "vpdn:l2tp-tunnel-password=hello"
LAC - Configuration
aaa new-model !--- Enables Authentication, Authorization and Accounting functionality. aaa group server radius NSA_LAB server 10.51.6.3 auth-port 1645 acct-port 0 non-standard ! aaa authentication login default local aaa authentication ppp default local group NSA_LAB aaa authentication ppp DIAL group NSA_LAB local aaa authorization network default group NSA_LAB local aaa authorization network DIAL group NSA_LAB local !--- Authentication and Authorization will be implemented !--- in sequence by the methods configured. vpdn enable !--- Enables the VPDN feature. no vpdn logging vpdn search-order dnis !--- Once LCP state is open, the dialed number is checked !--- to see if the remote is a VPDN user. interface Serial0:15 no ip address encapsulation ppp no logging event link-status dialer rotary-group 1 dialer-group 1 autodetect encapsulation ppp v120 no snmp trap link-status isdn switch-type primary-net5 isdn incoming-voice modem compress stac ! interface Dialer1 ip unnumbered Loopback0 encapsulation ppp no ip mroute-cache dialer-group 1 autodetect encapsulation ppp v120 !--- Allows the encapsulation type to be dynamically set if the call !--- type is not identified in the ISDN Q.931 Lower Layer Compatibility. peer default ip address pool default compress stac ppp authentication chap pap DIAL ppp authorization DIAL !--- The list-name DIAL is configured, that PPP Authentication and !--- Authorization will use. ppp chap hostname 5300-1 !--- The name 5300-1 is used for all CHAP challenge and response on !--- this interface. ppp multilink ! radius-server host 10.51.6.3 auth-port 1645 acct-port 1646 non-standard !--- 'non-standard' indicates that the RADIUS Server will use !--- non standard RADIUS attributes.
LNS - Configuration
aaa new-model !--- Enables Authentication, Authorization and Accounting functionality. aaa authentication login default local aaa authentication enable default group radius enable aaa authentication ppp default local aaa authentication ppp vpdn group radius none aaa authorization network default local none aaa authorization network vpdn group radius local !--- Authentication and Authorization will be implemented !--- in sequence by the methods configured. vpdn enable !--- Enables the VPDN feature. vpdn-group 1 accept-dialin protocol l2tp virtual-template 1 local name l2tp-gw l2tp tunnel password 7 1211001B1E04 !--- The LNS will accept connections from the LAC using L2TP !--- using All Virtual-Access Interfaces that are created will be cloned from !--- Virtual-Template 1. The name 'l2tp-gw' is used to identify the password, !--- that will authenticate the tunnel, is encrypted. interface Ethernet5/0 ip address 10.51.6.59 255.255.252.0 ! interface Virtual-Template1 ip unnumbered Ethernet5/0 no ip route-cache cef peer default ip address pool default ppp authentication chap vpdn ppp authorization vpdn ! radius-server host 10.51.6.3 auth-port 1645 acct-port 1646 non-standard !--- 'non-standard' identifies the RADIUS Server will be !--- using nonstandard RADIUS attributes.
Debugs Taken from LAC
Jan 1 00:32:54.847: %LINK-3-UPDOWN: Interface Serial0:0, changed state to up Jan 1 00:32:55.027: Se0:0 PPP: Treating connection as a callin Jan 1 00:32:55.027: Se0:0 PPP: Phase is ESTABLISHING, Passive Open Jan 1 00:32:55.027: Se0:0 CHAP: Using alternate hostname 5300-1 Jan 1 00:32:55.027: Se0:0 LCP: State is Listen Jan 1 00:32:55.027: Se0:0 LCP: I CONFREQ [Listen] id 112 len 10 - snip - Jan 1 00:32:55.063: Se0:0 LCP: State is Open Jan 1 00:32:55.063: Se0:0 PPP: Phase is AUTHENTICATING, by this end Jan 1 00:32:55.063: Se0:0 CHAP: Using alternate hostname 5300-1 Jan 1 00:32:55.063: Se0:0 CHAP: O CHALLENGE id 14 len 27 from "5300-1" Jan 1 00:32:55.083: Se0:0 CHAP: I RESPONSE id 14 len 27 from "2500-1" Jan 1 00:32:55.083: Se0:0 PPP: Phase is FORWARDING Jan 1 00:32:55.083: Se0:0 VPDN: Got DNIS string 614629 Jan 1 00:32:55.083: Se0:0 VPDN: Looking for tunnel -- dnis:614629 -- Jan 1 00:32:55.083: Serial0:0 AAA/AUTHOR/VPDN (480033158): Port='Serial0:0' list='default' service=NET Jan 1 00:32:55.083: AAA/AUTHOR/VPDN: Serial0:0 (480033158) user='dnis:614629' Jan 1 00:32:55.087: Serial0:0 AAA/AUTHOR/VPDN (480033158): send AV service=ppp Jan 1 00:32:55.087: Serial0:0 AAA/AUTHOR/VPDN (480033158): send AV protocol=vpdn Jan 1 00:32:55.087: Serial0:0 AAA/AUTHOR/VPDN (480033158): found list "default" Jan 1 00:32:55.087: Serial0:0 AAA/AUTHOR/VPDN (480033158): Method=NSA_LAB (radius) Jan 1 00:32:55.087: RADIUS: Initial Transmit Serial0:0 id 50 10.51.6.3:1645, Access-Request, len 100 Jan 1 00:32:55.087: Attribute 4 6 0A330644 Jan 1 00:32:55.087: Attribute 5 6 00000000 Jan 1 00:32:55.087: Attribute 26 17 00000009020B5365 Jan 1 00:32:55.087: Attribute 61 6 00000002 Jan 1 00:32:55.087: Attribute 1 13 646E6973 Jan 1 00:32:55.087: Attribute 30 8 36313436 Jan 1 00:32:55.087: Attribute 2 18 F0AF3BC4 Jan 1 00:32:55.087: Attribute 6 6 00000005 Jan 1 00:32:55.091: RADIUS: Received from id 50 10.51.6.3:1645, Access-Accept, len 167 Jan 1 00:32:55.091: Attribute 6 6 00000005 Jan 1 00:32:55.091: Attribute 26 29 0000000901177670 Jan 1 00:32:55.091: Attribute 26 26 0000000901147670 Jan 1 00:32:55.091: Attribute 26 47 0000000901297670 Jan 1 00:32:55.091: Attribute 26 39 0000000901217670 !--- LAC receives a call, negotiates PPP, LCP is declared Open, !--- the dialed number is queried to ascertain if this is a VPDN customer. !--- VPDN attempts to find an existing tunnel for the user, queries RADIUS for !--- the tunnel information. Jan 1 00:32:55.091: RADIUS: saved authorization data for user 61F40024 at 61F9813C Jan 1 00:32:55.091: RADIUS: cisco AVPair "vpdn:tunnel-type=l2tp" Jan 1 00:32:55.091: RADIUS: cisco AVPair "vpdn:tunnel-id=hgw" Jan 1 00:32:55.091: RADIUS: cisco AVPair "vpdn:ip-addresses=10.51.6.82,10.51.6.59" Jan 1 00:32:55.095: RADIUS: cisco AVPair "vpdn:l2tp-tunnel-password=hello" Jan 1 00:32:55.095: AAA/AUTHOR (480033158): Post authorization status = PASS_ADD Jan 1 00:32:55.095: AAA/AUTHOR/VPDN: Processing AV service=ppp Jan 1 00:32:55.095: AAA/AUTHOR/VPDN: Processing AV protocol=vpdn Jan 1 00:32:55.095: AAA/AUTHOR/VPDN: Processing AV tunnel-type=l2tp Jan 1 00:32:55.095: AAA/AUTHOR/VPDN: Processing AV tunnel-id=hgw Jan 1 00:32:55.095: AAA/AUTHOR/VPDN: Processing AV ip-addresses= 10.51.6.82,10.51.6.59 Jan 1 00:32:55.095: AAA/AUTHOR/VPDN: Processing AV l2tp-tunnel-password=hello Jan 1 00:32:55.095: Se0:0 VPDN/RPMS/: Got tunnel info for dnis:614629 Jan 1 00:32:55.095: Se0:0 VPDN/RPMS/: LAC hgw Jan 1 00:32:55.095: Se0:0 VPDN/RPMS/: l2tp-busy-disconnect yes Jan 1 00:32:55.095: Se0:0 VPDN/RPMS/: l2tp-tunnel-password xxxxxx Jan 1 00:32:55.095: Se0:0 VPDN/RPMS/: 2 IP addresses Jan 1 00:32:55.095: Se0:0 VPDN/RPMS/: IP 10.51.6.82 Priority 1 Jan 1 00:32:55.095: Se0:0 VPDN/RPMS/: IP 10.51.6.59 Priority 1 Jan 1 00:32:55.095: Se0:0 VPDN/: curlvl 1 Address 0: 10.51.6.82, priority 1 Jan 1 00:32:55.095: Se0:0 VPDN/: Select non-active address 10.51.6.82, priority 1 !--- The tunnel information is downloaded, using Cisco VSA. Two LNS IP !--- Addresses are used with a ',' as the delimiter, indicating that both !--- have equal priority. In this case 10.51.6.82 is selected as the tunnel !--- endpoint. Jan 1 00:32:55.095: Se0:0 VPDN: Find LNS process created Jan 1 00:32:55.095: Tnl 49467 L2TP: SM State idle Jan 1 00:32:55.095: Tnl 49467 L2TP: O SCCRQ Jan 1 00:32:55.099: Tnl 49467 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 00:32:55.099: Tnl 49467 L2TP: SM State wait-ctl-reply Jan 1 00:32:55.099: Se0:0 VPDN: Forward to address 10.51.6.82 Jan 1 00:32:55.099: Se0:0 VPDN: Pending Jan 1 00:32:55.099: Se0:0 VPDN: Process created Jan 1 00:32:55.191: Tnl 49467 L2TP: I SCCRP from l2tp-gw Jan 1 00:32:55.191: Tnl 49467 L2TP: Got a challenge from remote peer, l2tp-gw Jan 1 00:32:55.191: Tnl 49467 L2TP: Got a response from remote peer, l2tp-gw Jan 1 00:32:55.191: Tnl 49467 L2TP: Tunnel Authentication success Jan 1 00:32:55.191: Tnl 49467 L2TP: Tunnel state change from wait-ctl-reply to established Jan 1 00:32:55.191: Tnl 49467 L2TP: O SCCCN to l2tp-gw tnlid 62193 Jan 1 00:32:55.195: Tnl 49467 L2TP: SM State established Jan 1 00:32:55.195: Tnl/Cl 49467/16 L2TP: Session FS enabled Jan 1 00:32:55.195: Tnl/Cl 49467/16 L2TP: Session state change from idle to wait-for-tunnel Jan 1 00:32:55.195: Se0:0 Tnl/Cl 49467/16 L2TP: Create session Jan 1 00:32:55.195: Tnl 49467 L2TP: SM State established Jan 1 00:32:55.195: Se0:0 Tnl/Cl 49467/16 L2TP: O ICRQ to l2tp-gw 62193/0 Jan 1 00:32:55.195: Se0:0 Tnl/Cl 49467/16 L2TP: Session state change from wait-for-tunnel to wait-reply Jan 1 00:32:55.195: Se0:0 VPDN: 2500-1 is forwarded Jan 1 00:32:55.327: Se0:0 Tnl/Cl 49467/16 L2TP: O ICCN to l2tp-gw 62193/17 Jan 1 00:32:55.327: Se0:0 Tnl/Cl 49467/16 L2TP: Session state change from wait-reply to established Jan 1 00:32:56.195: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0:0, changed state to up Jan 1 00:33:00.851: %ISDN-6-CONNECT:Interface Serial0:0 is now connected to 2500-1 Jan 1 00:33:06.111: %ISDN-6-CONNECT: Interface Serial0:1 is now connected to N/A N/A !--- Second call is received by the LAC, !--- the dialed number is a VPDN customer. Jan 1 00:33:35.027: As1 LCP: I CONFREQ [Closed] id 1 len 23 - snip - Jan 1 00:33:39.275: As1 LCP: State is Open Jan 1 00:33:39.275: As1 PPP: Phase is AUTHENTICATING, by this end Jan 1 00:33:39.275: As1 CHAP: Using alternate hostname 5300-1 Jan 1 00:33:39.275: As1 CHAP: O CHALLENGE id 2 len 27 from "5300-1" Jan 1 00:33:39.383: As1 CHAP: I RESPONSE id 2 len 25 from "paul" Jan 1 00:33:39.383: As1 PPP: Phase is FORWARDING Jan 1 00:33:39.383: As1 VPDN: Got DNIS string 614629 Jan 1 00:33:39.383: As1 VPDN: Looking for tunnel -- dnis:614629 -- Jan 1 00:33:39.387: Async1 AAA/AUTHOR/VPDN (3019717950): Port='Async1' list='default' service=NET Jan 1 00:33:39.387: AAA/AUTHOR/VPDN: Async1 (3019717950) user='dnis:614629' Jan 1 00:33:39.387: Async1 AAA/AUTHOR/VPDN (3019717950): send AV service=ppp Jan 1 00:33:39.387: Async1 AAA/AUTHOR/VPDN (3019717950): send AV protocol=vpdn Jan 1 00:33:39.387: Async1 AAA/AUTHOR/VPDN (3019717950): found list "default" Jan 1 00:33:39.387: Async1 AAA/AUTHOR/VPDN (3019717950): Method=NSA_LAB (radius) Jan 1 00:33:39.387: RADIUS: Initial Transmit Async1 id 52 10.51.6.3:1645, Access-Request, len 97 Jan 1 00:33:39.387: Attribute 4 6 0A330644 Jan 1 00:33:39.387: Attribute 5 6 00000001 Jan 1 00:33:39.387: Attribute 26 14 0000000902084173 Jan 1 00:33:39.387: Attribute 61 6 00000000 Jan 1 00:33:39.387: Attribute 1 13 646E6973 Jan 1 00:33:39.387: Attribute 30 8 36313436 Jan 1 00:33:39.387: Attribute 2 18 E9164E4C Jan 1 00:33:39.387: Attribute 6 6 00000005 Jan 1 00:33:39.391: RADIUS: Received from id 52 10.51.6.3:1645, Access-Accept, len 167 Jan 1 00:33:39.391: Attribute 6 6 00000005 Jan 1 00:33:39.391: Attribute 26 29 0000000901177670 Jan 1 00:33:39.391: Attribute 26 26 0000000901147670 Jan 1 00:33:39.391: Attribute 26 47 0000000901297670 Jan 1 00:33:39.391: Attribute 26 39 0000000901217670 Jan 1 00:33:39.391: RADIUS: saved authorization data for user 621904CC at 61FAB9EC Jan 1 00:33:39.391: RADIUS: cisco AVPair "vpdn:tunnel-type=l2tp" Jan 1 00:33:39.391: RADIUS: cisco AVPair "vpdn:tunnel-id=hgw" Jan 1 00:33:39.391: RADIUS: cisco AVPair "vpdn:ip-addresses=10.51.6.82,10.51.6.59" Jan 1 00:33:39.391: RADIUS: cisco AVPair "vpdn:l2tp-tunnel-password=hello" Jan 1 00:33:39.395: AAA/AUTHOR (3019717950): Post authorization status = PASS_ADD Jan 1 00:33:39.395: AAA/AUTHOR/VPDN: Processing AV service=ppp Jan 1 00:33:39.395: AAA/AUTHOR/VPDN: Processing AV protocol=vpdn Jan 1 00:33:39.395: AAA/AUTHOR/VPDN: Processing AV tunnel-type=l2tp Jan 1 00:33:39.395: AAA/AUTHOR/VPDN: Processing AV tunnel-id=hgw Jan 1 00:33:39.395: AAA/AUTHOR/VPDN: Processing AV ip-addresses=10.51.6.82,10.51.6.59 Jan 1 00:33:39.395: AAA/AUTHOR/VPDN: Processing AV l2tp-tunnel-password=hello Jan 1 00:33:39.395: As1 VPDN/RPMS/: Got tunnel info for dnis:614629 Jan 1 00:33:39.395: As1 VPDN/RPMS/: LAC hgw Jan 1 00:33:39.395: As1 VPDN/RPMS/: l2tp-busy-disconnect yes Jan 1 00:33:39.395: As1 VPDN/RPMS/: l2tp-tunnel-password xxxxxx Jan 1 00:33:39.395: As1 VPDN/RPMS/: 2 IP addresses Jan 1 00:33:39.395: As1 VPDN/RPMS/: IP 10.51.6.82 Priority 1 Jan 1 00:33:39.395: As1 VPDN/RPMS/: IP 10.51.6.59 Priority 1 Jan 1 00:33:39.395: As1 VPDN/: curlvl 1 Address 1: 10.51.6.59, priority 1 Jan 1 00:33:39.395: As1 VPDN/: Select non-active address 10.51.6.59, priority 1 !--- The second non-active endpoint is selected 10.51.6.59 !--- and the control connection is established. Jan 1 00:33:39.395: As1 VPDN: Find LNS process created Jan 1 00:33:39.395: Tnl 20770 L2TP: SM State idle Jan 1 00:33:39.395: Tnl 20770 L2TP: O SCCRQ Jan 1 00:33:39.399: Tnl 20770 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 00:33:39.399: Tnl 20770 L2TP: SM State wait-ctl-reply Jan 1 00:33:39.399: As1 VPDN: Forward to address 10.51.6.59 Jan 1 00:33:39.399: As1 VPDN: Pending Jan 1 00:33:39.399: As1 VPDN: Process created Jan 1 00:33:39.399: Tnl 20770 L2TP: I SCCRP from l2tp-gw Jan 1 00:33:39.399: Tnl 20770 L2TP: Got a challenge from remote peer, l2tp-gw Jan 1 00:33:39.399: Tnl 20770 L2TP: Got a response from remote peer, l2tp-gw Jan 1 00:33:39.399: Tnl 20770 L2TP: Tunnel Authentication success Jan 1 00:33:39.399: Tnl 20770 L2TP: Tunnel state change from wait-ctl-reply to established Jan 1 00:33:39.403: Tnl 20770 L2TP: O SCCCN to l2tp-gw tnlid 42921 Jan 1 00:33:39.403: Tnl 20770 L2TP: SM State established Jan 1 00:33:39.403: As1 VPDN: Forwarding... Jan 1 00:33:39.403: Tnl/Cl 20770/17 L2TP: Session FS enabled Jan 1 00:33:39.403: Tnl/Cl 20770/17 L2TP: Session state change from idle to wait-for-tunnel Jan 1 00:33:39.403: As1 Tnl/Cl 20770/17 L2TP: Create session Jan 1 00:33:39.403: Tnl 20770 L2TP: SM State established Jan 1 00:33:39.403: As1 Tnl/Cl 20770/17 L2TP: O ICRQ to l2tp-gw 42921/0 Jan 1 00:33:39.403: As1 Tnl/Cl 20770/17 L2TP: Session state change from wait-for-tunnel to wait-reply Jan 1 00:33:39.403: As1 VPDN: paul is forwarded Jan 1 00:33:39.407: As1 Tnl/Cl 20770/17 L2TP: O ICCN to l2tp-gw 42921/16 Jan 1 00:33:39.407: As1 Tnl/Cl 20770/17 L2TP: Session state change from wait-reply to established

LNS Failover Using Cisco Vendor-Specific Attribute/Value Pairs
RADIUS Profile
RADIUS user and tunnel profiles on Merit RADIUS Server 3.6B:
2500-1 Password = "cisco" Service-Type = Framed, Framed-Protocol = PPP, Framed-IP-Address = 255.255.255.255 dnis:614629 Password = "cisco" Service-Type = Outbound, Cisco:Avpair = "vpdn:tunnel-type=l2tp", Cisco:Avpair = "vpdn:tunnel-id=hgw", Cisco:Avpair = "vpdn:ip-addresses=10.51.6.82/10.51.6.59", Cisco:Avpair = "vpdn:l2tp-tunnel-password=hello"
LAC and LNS Configuration
Same as previous.
Debugs Taken from LAC
Jan 1 02:00:35.767: As2 LCP: State is Open Jan 1 02:00:35.767: As2 PPP: Phase is AUTHENTICATING, by this end [0 sess, 0 load] Jan 1 02:00:35.767: As2 CHAP: Using alternate hostname 5300-1 Jan 1 02:00:35.767: As2 CHAP: O CHALLENGE id 1 len 27 from "5300-1" Jan 1 02:00:35.959: As2 CHAP: I RESPONSE id 1 len 25 from "paul" Jan 1 02:00:35.959: As2 PPP: Phase is FORWARDING [0 sess, 0 load] Jan 1 02:00:35.959: As2 VPDN: Got DNIS string 614629 Jan 1 02:00:35.959: As2 VPDN: Looking for tunnel -- dnis:614629 -- Jan 1 02:00:35.959: AAA/AUTHOR/VPDN: Async2 (3581154520) user='dnis:614629' Jan 1 02:00:35.963: Async2 AAA/AUTHOR/VPDN (3581154520): send AV service=ppp Jan 1 02:00:35.963: Async2 AAA/AUTHOR/VPDN (3581154520): send AV protocol=vpdn Jan 1 02:00:35.963: Async2 AAA/AUTHOR/VPDN (3581154520): found list "default" Jan 1 02:00:35.963: Async2 AAA/AUTHOR/VPDN (3581154520): Method=NSA_LAB (radius) Jan 1 02:00:35.963: RADIUS: Initial Transmit Async2 id 56 10.51.6.3:1645, Access-Request, len 109 Jan 1 02:00:35.963: Attribute 4 6 0A330644 Jan 1 02:00:35.963: Attribute 5 6 00000000 Jan 1 02:00:35.963: Attribute 26 14 0000000902084173 Jan 1 02:00:35.963: Attribute 61 6 00000000 Jan 1 02:00:35.963: Attribute 1 13 646E6973 Jan 1 02:00:35.963: Attribute 30 8 36313436 Jan 1 02:00:35.963: Attribute 31 12 31363139 Jan 1 02:00:35.963: Attribute 2 18 2A5AF04C Jan 1 02:00:35.963: Attribute 6 6 00000005 Jan 1 02:00:35.967: RADIUS: Received from id 56 10.51.6.3:1645, Access-Accept, len 167 Jan 1 02:00:35.967: Attribute 6 6 00000005 Jan 1 02:00:35.967: Attribute 26 29 0000000901177670 Jan 1 02:00:35.967: Attribute 26 26 0000000901147670 Jan 1 02:00:35.967: Attribute 26 47 0000000901297670 Jan 1 02:00:35.967: Attribute 26 39 0000000901217670 Jan 1 02:00:35.967: RADIUS: cisco AVPair "vpdn:tunnel-type=l2tp" Jan 1 02:00:35.967: RADIUS: cisco AVPair "vpdn:tunnel-id=hgw" Jan 1 02:00:35.967: RADIUS: cisco AVPair "vpdn:ip-addresses=10.51.6.82/10.51.6.59" Jan 1 02:00:35.967: RADIUS: cisco AVPair "vpdn:l2tp-tunnel-password=hello" Jan 1 02:00:35.967: AAA/AUTHOR (3581154520): Post authorization status = PASS_ADD Jan 1 02:00:35.967: AAA/AUTHOR/VPDN: Processing AV service=ppp Jan 1 02:00:35.967: AAA/AUTHOR/VPDN: Processing AV protocol=vpdn Jan 1 02:00:35.967: AAA/AUTHOR/VPDN: Processing AV tunnel-type=l2tp Jan 1 02:00:35.967: AAA/AUTHOR/VPDN: Processing AV tunnel-id=hgw Jan 1 02:00:35.967: AAA/AUTHOR/VPDN: Processing AV ip-addresses= 10.51.6.82/10.51.6.59 Jan 1 02:00:35.967: AAA/AUTHOR/VPDN: Processing AV l2tp-tunnel-password=hello !--- LAC receives a call, negotiates PPP, LCP is declared Open, !--- the dialed number is queried to ascertain if this is a VPDN customer. !--- VPDN attempts to find an existing tunnel for the user, queries RADIUS for !--- the tunnel information. Jan 1 02:00:35.967: As2 VPDN/RPMS/: Got tunnel info for dnis:614629 Jan 1 02:00:35.971: As2 VPDN/RPMS/: LAC hgw Jan 1 02:00:35.971: As2 VPDN/RPMS/: l2tp-busy-disconnect yes Jan 1 02:00:35.971: As2 VPDN/RPMS/: l2tp-tunnel-password xxxxxx Jan 1 02:00:35.971: As2 VPDN/RPMS/: 2 IP addresses Jan 1 02:00:35.971: As2 VPDN/RPMS/: IP 10.51.6.82 Priority 1 Jan 1 02:00:35.971: As2 VPDN/RPMS/: IP 10.51.6.59 Priority 2 Jan 1 02:00:35.971: As2 VPDN/: curlvl 1 Address 0: 10.51.6.82, priority 1 Jan 1 02:00:35.971: As2 VPDN/: Select non-active address 10.51.6.82, priority 1 !--- The tunnel information is downloaded, using Cisco VSA. !--- Two RADIUS server IP Address's are used with a '/' as the delimiter, !--- indicating that there are two priority groups. In this case 10.51.6.82, !--- as Priority level 1, is selected as the tunnel endpoint. Jan 1 02:00:35.971: Tnl 17044 L2TP: SM State idle Jan 1 02:00:35.971: Tnl 17044 L2TP: O SCCRQ Jan 1 02:00:35.971: Tnl 17044 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 02:00:35.971: Tnl 17044 L2TP: SM State wait-ctl-reply Jan 1 02:00:35.971: As2 VPDN: Find LNS process created Jan 1 02:00:35.971: As2 VPDN: Forward to address 10.51.6.82 Jan 1 02:00:35.971: As2 VPDN: Pending Jan 1 02:00:35.971: As2 VPDN: Process created Jan 1 02:00:35.983: Tnl 17044 L2TP: I SCCRP from l2tp-gw Jan 1 02:00:35.983: Tnl 17044 L2TP: Got a challenge from remote peer, l2tp-gw Jan 1 02:00:35.983: Tnl 17044 L2TP: Got a response from remote peer, l2tp-gw Jan 1 02:00:35.983: Tnl 17044 L2TP: Tunnel Authentication success Jan 1 02:00:35.983: Tnl 17044 L2TP: Tunnel state change from wait-ctl-reply to established Jan 1 02:00:35.983: Tnl 17044 L2TP: O SCCCN to l2tp-gw tnlid 9017 Jan 1 02:00:35.983: Tnl 17044 L2TP: SM State established Jan 1 02:00:35.983: As2 VPDN: Forwarding... Jan 1 02:00:35.987: Tnl/Cl 17044/2 L2TP: Session FS enabled Jan 1 02:00:35.987: Tnl/Cl 17044/2 L2TP: Session state change from idle to wait-for-tunnel Jan 1 02:00:35.987: As2 Tnl/Cl 17044/2 L2TP: Create session Jan 1 02:00:35.987: Tnl 17044 L2TP: SM State established Jan 1 02:00:35.987: As2 Tnl/Cl 17044/2 L2TP: O ICRQ to l2tp-gw 9017/0 Jan 1 02:00:35.987: As2 Tnl/Cl 17044/2 L2TP: Session state change from wait-for-tunnel to wait-reply Jan 1 02:00:35.987: As2 VPDN: paul is forwarded Jan 1 02:00:35.995: As2 Tnl/Cl 17044/2 L2TP: O ICCN to l2tp-gw 9017/2 Jan 1 02:00:35.995: As2 Tnl/Cl 17044/2 L2TP: Session state change from wait-reply to established !--- The Tunnel and Session are now established. !--- A second call is received by the LAC. Jan 1 02:03:21.775: Se0:1 LCP: State is Open Jan 1 02:03:21.775: Se0:1 PPP: Phase is AUTHENTICATING, by this end [0 sess, 0 load] Jan 1 02:03:21.775: Se0:1 CHAP: Using alternate hostname 5300-1 Jan 1 02:03:21.775: Se0:1 CHAP: O CHALLENGE id 1 len 27 from "5300-1" Jan 1 02:03:21.799: Se0:1 CHAP: I RESPONSE id 1 len 27 from "2500-1" Jan 1 02:03:21.799: Se0:1 PPP: Phase is FORWARDING [0 sess, 0 load] Jan 1 02:03:21.799: Se0:1 VPDN: Got DNIS string 614629 Jan 1 02:03:21.799: Se0:1 VPDN: Looking for tunnel -- dnis:614629 -- Jan 1 02:03:21.799: Serial0:1 AAA/AUTHOR/VPDN (2106866192): Port='Serial0:1' list='default' service=NET Jan 1 02:03:21.799: AAA/AUTHOR/VPDN: Serial0:1 (2106866192) user='dnis:614629' Jan 1 02:03:21.799: Serial0:1 AAA/AUTHOR/VPDN (2106866192): send AV service=ppp Jan 1 02:03:21.799: Serial0:1 AAA/AUTHOR/VPDN (2106866192): send AV protocol=vpdn Jan 1 02:03:21.799: Serial0:1 AAA/AUTHOR/VPDN (2106866192): found list "default" Jan 1 02:03:21.799: Serial0:1 AAA/AUTHOR/VPDN (2106866192): Method=NSA_LAB (radius) Jan 1 02:03:21.803: RADIUS: Initial Transmit Serial0:1 id 60 10.51.6.3:1645, Access-Request, len 112 Jan 1 02:03:21.803: Attribute 4 6 0A330644 Jan 1 02:03:21.803: Attribute 5 6 00000001 Jan 1 02:03:21.803: Attribute 26 17 00000009020B5365 Jan 1 02:03:21.803: Attribute 61 6 00000002 Jan 1 02:03:21.803: Attribute 1 13 646E6973 Jan 1 02:03:21.803: Attribute 30 8 36313436 Jan 1 02:03:21.803: Attribute 31 12 32303835 Jan 1 02:03:21.803: Attribute 2 18 1A511187 Jan 1 02:03:21.803: Attribute 6 6 00000005 Jan 1 02:03:21.803: RADIUS: Received from id 60 10.51.6.3:1645, Access-Accept, len 167 Jan 1 02:03:21.803: Attribute 6 6 00000005 Jan 1 02:03:21.803: Attribute 26 29 0000000901177670 Jan 1 02:03:21.803: Attribute 26 26 0000000901147670 Jan 1 02:03:21.803: Attribute 26 47 0000000901297670 Jan 1 02:03:21.803: Attribute 26 39 0000000901217670 Jan 1 02:03:21.807: RADIUS: cisco AVPair "vpdn:tunnel-type=l2tp" Jan 1 02:03:21.807: RADIUS: cisco AVPair "vpdn:tunnel-id=hgw" Jan 1 02:03:21.807: RADIUS: cisco AVPair "vpdn:ip-addresses=10.51.6.82/10.51.6.59" Jan 1 02:03:21.807: RADIUS: cisco AVPair "vpdn:l2tp-tunnel-password=hello" Jan 1 02:03:21.807: AAA/AUTHOR (2106866192): Post authorization status = PASS_ADD Jan 1 02:03:21.807: AAA/AUTHOR/VPDN: Processing AV service=ppp Jan 1 02:03:21.807: AAA/AUTHOR/VPDN: Processing AV protocol=vpdn Jan 1 02:03:21.807: AAA/AUTHOR/VPDN: Processing AV tunnel-type=l2tp Jan 1 02:03:21.807: AAA/AUTHOR/VPDN: Processing AV tunnel-id=hgw Jan 1 02:03:21.807: AAA/AUTHOR/VPDN: Processing AV ip-addresses= 10.51.6.82/10.51.6.59 Jan 1 02:03:21.807: AAA/AUTHOR/VPDN: Processing AV l2tp-tunnel-password=hello Jan 1 02:03:21.807: Se0:1 VPDN/RPMS/: Got tunnel info for dnis:614629 Jan 1 02:03:21.807: Se0:1 VPDN/RPMS/: LAC hgw Jan 1 02:03:21.807: Se0:1 VPDN/RPMS/: l2tp-busy-disconnect yes Jan 1 02:03:21.807: Se0:1 VPDN/RPMS/: l2tp-tunnel-password xxxxxx Jan 1 02:03:21.807: Se0:1 VPDN/RPMS/: 2 IP addresses Jan 1 02:03:21.807: Se0:1 VPDN/RPMS/: IP 10.51.6.82 Priority 1 Jan 1 02:03:21.807: Se0:1 VPDN/RPMS/: IP 10.51.6.59 Priority 2 Jan 1 02:03:21.807: Se0:1 VPDN/: curlvl 1 Address 0: 10.51.6.82, priority 1 Jan 1 02:03:21.811: Se0:1 VPDN/: Select open address 10.51.6.82, priority 1 Jan 1 02:03:21.811: Se0:1 VPDN: Forward to address 10.51.6.82 !--- The tunnel information is downloaded, LNS - 10.51.6.82 is !--- selected again as the tunnel endpoint as this is in Priority level 1. Jan 1 02:03:21.811: Se0:1 VPDN: Forwarding... Jan 1 02:03:21.811: Tnl/Cl 17044/3 L2TP: Session state change from idle to wait-for-tunnel Jan 1 02:03:21.811: Se0:1 Tnl/Cl 17044/3 L2TP: Create session Jan 1 02:03:21.811: Tnl 17044 L2TP: SM State established Jan 1 02:03:21.811: Se0:1 Tnl/Cl 17044/3 L2TP: O ICRQ to l2tp-gw 9017/0 Jan 1 02:03:21.811: Se0:1 Tnl/Cl 17044/3 L2TP: Session state change from wait-for-tunnel to wait-reply Jan 1 02:03:21.811: Se0:1 VPDN: 2500-1 is forwarded Jan 1 02:03:21.819: Se0:1 Tnl/Cl 17044/3 L2TP: O ICCN to l2tp-gw 9017/3 Jan 1 02:03:21.819: Se0:1 Tnl/Cl 17044/3 L2TP: Session state change from wait-reply to established
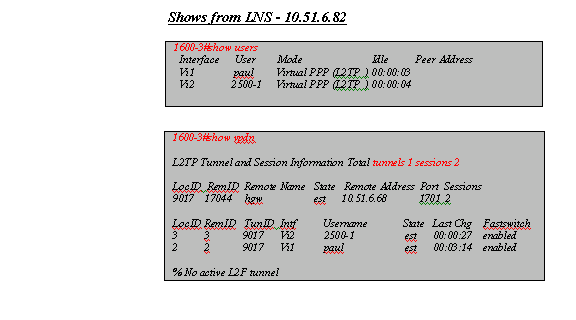
LNS Load Balancing and Failover using Cisco Vendor-Specific Attribute/Value Pairs
RADIUS Profile
RADIUS user and tunnel profile on Merit RADIUS Server 3.6B:
2500-1 Password = "cisco" Service-Type = Framed, Framed-Protocol = PPP, Framed-IP-Address = 255.255.255.255 dnis:614629 Password = "cisco" Service-Type = Outbound, Cisco:Avpair = "vpdn:tunnel-type=l2tp", Cisco:Avpair = "vpdn:tunnel-id=hgw", Cisco:Avpair = "vpdn:ip-addresses= 10.51.6.80,10.51.6.59/10.51.6.2,10.51.6.3/10.51.6.82,10.51.6.5", Cisco:Avpair = "vpdn:l2tp-tunnel-password=hello"
LAC and LNS Configuration
Same as previous.
Debugs taken from LAC
Jan 1 00:43:11.539: %LINK-3-UPDOWN: Interface Serial0:0, changed state to up Jan 1 00:43:11.755: Se0:0 LCP: State is Open Jan 1 00:43:11.755: Se0:0 PPP: Phase is AUTHENTICATING, by this end Jan 1 00:43:11.755: Se0:0 CHAP: Using alternate hostname 5300-1 Jan 1 00:43:11.755: Se0:0 CHAP: O CHALLENGE id 18 len 27 from "5300-1" Jan 1 00:43:11.775: Se0:0 CHAP: I RESPONSE id 18 len 27 from "2500-1" Jan 1 00:43:11.775: Se0:0 PPP: Phase is FORWARDING Jan 1 00:43:11.775: Se0:0 VPDN: Got DNIS string 614629 Jan 1 00:43:11.775: Se0:0 VPDN: Looking for tunnel -- dnis:614629 -- Jan 1 00:43:11.775: Serial0:0 AAA/AUTHOR/VPDN (2215378044): Port='Serial0:0' list='default' service=NET Jan 1 00:43:11.775: AAA/AUTHOR/VPDN: Serial0:0 (2215378044) user='dnis:614629' Jan 1 00:43:11.775: Serial0:0 AAA/AUTHOR/VPDN (2215378044): send AV service=ppp Jan 1 00:43:11.775: Serial0:0 AAA/AUTHOR/VPDN (2215378044): send AV protocol=vpdn Jan 1 00:43:11.775: Serial0:0 AAA/AUTHOR/VPDN (2215378044): found list "default" Jan 1 00:43:11.775: Serial0:0 AAA/AUTHOR/VPDN (2215378044): Method=NSA_LAB (radius) Jan 1 00:43:11.779: RADIUS: Initial Transmit Serial0:0 id 57 10.51.6.3:1645, Access-Request, len 112 Jan 1 00:43:11.779: Attribute 4 6 0A330644 Jan 1 00:43:11.779: Attribute 5 6 00000000 Jan 1 00:43:11.779: Attribute 26 17 00000009020B5365 Jan 1 00:43:11.779: Attribute 61 6 00000002 Jan 1 00:43:11.779: Attribute 1 13 646E6973 Jan 1 00:43:11.779: Attribute 30 8 36313436 Jan 1 00:43:11.779: Attribute 31 12 32303835 Jan 1 00:43:11.779: Attribute 2 18 BA50FCD1 Jan 1 00:43:11.779: Attribute 6 6 00000005 Jan 1 00:43:11.783: RADIUS: Received from id 57 10.51.6.3:1645, Access-Accept, len 208 Jan 1 00:43:11.783: Attribute 6 6 00000005 Jan 1 00:43:11.783: Attribute 26 29 0000000901177670 Jan 1 00:43:11.783: Attribute 26 26 0000000901147670 Jan 1 00:43:11.783: Attribute 26 88 0000000901527670 Jan 1 00:43:11.783: Attribute 26 39 0000000901217670 Jan 1 00:43:11.783: RADIUS: cisco AVPair "vpdn:tunnel-type=l2tp" Jan 1 00:43:11.783: RADIUS: cisco AVPair "vpdn:tunnel-id=hgw" Jan 1 00:43:11.783: RADIUS: cisco AVPair "vpdn:ip-addresses= 10.51.6.80,10.51.6.59/10.51.6.2,10.51.6.3/10.51.6.82,10.51.6.5" Jan 1 00:43:11.783: RADIUS: cisco AVPair "vpdn:l2tp-tunnel-password=hello" Jan 1 00:43:11.783: AAA/AUTHOR (2215378044): Post authorization status = PASS_ADD Jan 1 00:43:11.783: AAA/AUTHOR/VPDN: Processing AV service=ppp Jan 1 00:43:11.783: AAA/AUTHOR/VPDN: Processing AV protocol=vpdn Jan 1 00:43:11.783: AAA/AUTHOR/VPDN: Processing AV tunnel-type=l2tp Jan 1 00:43:11.783: AAA/AUTHOR/VPDN: Processing AV tunnel-id=hgw Jan 1 00:43:11.783: AAA/AUTHOR/VPDN: Processing AV ip-addresses= 10.51.6.80,10.51.6.59/10.51.6.2,10.51.6.3/10.51.6.82,10.51.6.5 Jan 1 00:43:11.783: AAA/AUTHOR/VPDN: Processing AV l2tp-tunnel-password=hello Jan 1 00:43:11.783: Se0:0 VPDN/RPMS/: Got tunnel info for dnis:614629 Jan 1 00:43:11.783: Se0:0 VPDN/RPMS/: LAC hgw Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: l2tp-busy-disconnect yes Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: l2tp-tunnel-password xxxxxx Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: 6 IP addresses Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: IP 10.51.6.80 Priority 1 Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: IP 10.51.6.59 Priority 1 Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: IP 10.51.6.2 Priority 2 Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: IP 10.51.6.3 Priority 2 Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: IP 10.51.6.82 Priority 3 Jan 1 00:43:11.787: Se0:0 VPDN/RPMS/: IP 10.51.6.5 Priority 3 !--- The tunnel information is downloaded, using Cisco VSA. Two RADIUS !--- server IP Addresses are used with a '/' as the delimiter for each !--- of the three priority groups. In this case, 10.51.6.82 in Priority !--- Group 3, is the tunnel endpoint that is valid. Jan 1 00:43:11.787: Se0:0 VPDN/: curlvl 1 Address 1: 10.51.6.59, priority 1 Jan 1 00:43:11.787: VPDN: Free busy address 10.51.6.59 Jan 1 00:43:11.787: Se0:0 VPDN/: Select non-active address 10.51.6.59, priority 1 Jan 1 00:43:11.787: Se0:0 VPDN: Find LNS process created Jan 1 00:43:11.787: Tnl 8262 L2TP: SM State idle Jan 1 00:43:11.787: Tnl 8262 L2TP: O SCCRQ Jan 1 00:43:11.787: Tnl 8262 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 00:43:11.787: Tnl 8262 L2TP: SM State wait-ctl-reply Jan 1 00:43:11.787: Se0:0 VPDN: Forward to address 10.51.6.59 Jan 1 00:43:11.791: Se0:0 VPDN: Pending Jan 1 00:43:11.791: Se0:0 VPDN: Process created Jan 1 00:43:12.787: Tnl 8262 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:12.787: Tnl 8262 L2TP: Control channel retransmit delay set to 1 seconds Jan 1 00:43:13.787: Tnl 8262 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:13.787: Tnl 8262 L2TP: Control channel retransmit delay set to 2 seconds Jan 1 00:43:15.787: Tnl 8262 L2TP: Timeout opening tunnel to 10.51.6.59 Jan 1 00:43:15.787: Tnl 63291 L2TP: Control channel retransmit delay set to 4 seconds Jan 1 00:43:15.787: Se0:0 VPDN/: curlvl 1 Address 1: 10.51.6.59, priority 1 busy !--- 10.51.6.59 is selected as the first non-active IP Address in Priority !--- Group 1. As we cannot establish the Control Connection after the !--- 4 second SCCRQ timeout, we select the next non-active IP !--- Address in the same Priority Group. Jan 1 00:43:15.787: Se0:0 VPDN/: curlvl 1 Address 0: 10.51.6.80, priority 1 Jan 1 00:43:15.787: VPDN: Free busy address 10.51.6.80 Jan 1 00:43:15.787: Se0:0 VPDN/: Select non-active address 10.51.6.80, priority 1 Jan 1 00:43:15.787: Tnl 63291 L2TP: Tunnel state change from wait-ctl-reply to idle Jan 1 00:43:15.787: Tnl 63291 L2TP: SM State idle Jan 1 00:43:15.787: Tnl 63291 L2TP: O SCCRQ Jan 1 00:43:15.787: Tnl 63291 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 00:43:15.787: Tnl 63291 L2TP: SM State wait-ctl-reply Jan 1 00:43:16.787: Tnl 63291 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:16.787: Tnl 63291 L2TP: Control channel retransmit delay set to 1 seconds Jan 1 00:43:17.543: %ISDN-6-CONNECT: Interface Serial0:0 is now connected to 2085730592 Jan 1 00:43:17.787: Tnl 63291 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:17.787: Tnl 63291 L2TP: Control channel retransmit delay set to 2 seconds Jan 1 00:43:19.787: Tnl 63291 L2TP: Timeout opening tunnel to 10.51.6.80 Jan 1 00:43:19.787: Tnl 52784 L2TP: Control channel retransmit delay set to 4 seconds Jan 1 00:43:19.787: Se0:0 VPDN/: curlvl 1 Address 0: 10.51.6.80, priority 1 busy Jan 1 00:43:19.787: Se0:0 VPDN/: curlvl 1 Address 1: 10.51.6.59, priority 1 busy Jan 1 00:43:19.787: Se0:0 VPDN/: curlvl 2 Address 2: 10.51.6.2, priority 2 Jan 1 00:43:19.787: VPDN: Free busy address 10.51.6.2 Jan 1 00:43:19.787: Se0:0 VPDN/: Select non-active address 10.51.6.2, priority 2 Jan 1 00:43:19.787: Tnl 52784 L2TP: Tunnel state change from wait-ctl-reply to idle Jan 1 00:43:19.787: Tnl 52784 L2TP: SM State idle Jan 1 00:43:19.787: Tnl 52784 L2TP: O SCCRQ Jan 1 00:43:19.787: Tnl 52784 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 00:43:19.787: Tnl 52784 L2TP: SM State wait-ctl-reply Jan 1 00:43:20.787: Tnl 52784 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:20.787: Tnl 52784 L2TP: Control channel retransmit delay set to 1 seconds Jan 1 00:43:21.671: Se0:0 CHAP: I RESPONSE id 18 len 27 from "2500-1" Jan 1 00:43:21.671: Se0:0 VPDN: LCP state already FORWARDING/FORWARDED, silent discard Jan 1 00:43:21.787: Tnl 52784 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:21.787: Tnl 52784 L2TP: Control channel retransmit delay set to 2 seconds Jan 1 00:43:23.787: Tnl 52784 L2TP: Timeout opening tunnel to 10.51.6.2 Jan 1 00:43:23.787: Tnl 42277 L2TP: Control channel retransmit delay set to 4 seconds Jan 1 00:43:23.787: Se0:0 VPDN/: curlvl 2 Address 2: 10.51.6.2, priority 2 busy Jan 1 00:43:23.787: Se0:0 VPDN/: curlvl 2 Address 3: 10.51.6.3, priority 2 Jan 1 00:43:23.787: VPDN: Free busy address 10.51.6.3 Jan 1 00:43:23.787: Se0:0 VPDN/: Select non-active address 10.51.6.3, priority 2 Jan 1 00:43:23.787: Tnl 42277 L2TP: Tunnel state change from wait-ctl-reply to idle Jan 1 00:43:23.787: Tnl 42277 L2TP: SM State idle Jan 1 00:43:23.787: Tnl 42277 L2TP: O SCCRQ Jan 1 00:43:23.787: Tnl 42277 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 00:43:23.787: Tnl 42277 L2TP: SM State wait-ctl-reply Jan 1 00:43:24.787: Tnl 42277 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:24.787: Tnl 42277 L2TP: Control channel retransmit delay set to 1 seconds Jan 1 00:43:25.787: Tnl 42277 L2TP: O Resend SCCRQ, flg TLS, ver 2, len 128, tnl 0, cl 0, ns 0, nr 0 Jan 1 00:43:25.787: Tnl 42277 L2TP: Control channel retransmit delay set to 2 seconds Jan 1 00:43:27.787: Tnl 42277 L2TP: Timeout opening tunnel to 10.51.6.3 Jan 1 00:43:27.787: Tnl 31770 L2TP: Control channel retransmit delay set to 4 seconds Jan 1 00:43:27.787: Se0:0 VPDN/: curlvl 2 Address 3: 10.51.6.3, priority 2 busy Jan 1 00:43:27.787: Se0:0 VPDN/: curlvl 2 Address 2: 10.51.6.2, priority 2 busy Jan 1 00:43:27.787: Se0:0 VPDN/: curlvl 3 Address 4: 10.51.6.82, priority 3 Jan 1 00:43:27.787: Se0:0 VPDN/: Select non-active address 10.51.6.82, priority 3 !--- Eventually arrive at the IP Address 10.51.6.82 in Priority Group 3. !--- As this is valid, the Control Connection and session are established. Jan 1 00:43:27.787: Tnl 31770 L2TP: Tunnel state change from wait-ctl-reply to idle Jan 1 00:43:27.787: Tnl 31770 L2TP: SM State idle Jan 1 00:43:27.787: Tnl 31770 L2TP: O SCCRQ Jan 1 00:43:27.787: Tnl 31770 L2TP: Tunnel state change from idle to wait-ctl-reply Jan 1 00:43:27.787: Tnl 31770 L2TP: SM State wait-ctl-reply Jan 1 00:43:27.799: Tnl 31770 L2TP: I SCCRP from l2tp-gw Jan 1 00:43:27.799: Tnl 31770 L2TP: Got a challenge from remote peer, l2tp-gw Jan 1 00:43:27.799: Tnl 31770 L2TP: Got a response from remote peer, l2tp-gw Jan 1 00:43:27.799: Tnl 31770 L2TP: Tunnel Authentication success Jan 1 00:43:27.799: Tnl 31770 L2TP: Tunnel state change from wait-ctl-reply to established Jan 1 00:43:27.799: Tnl 31770 L2TP: O SCCCN to l2tp-gw tnlid 3843 Jan 1 00:43:27.799: Tnl 31770 L2TP: SM State established Jan 1 00:43:27.799: Se0:0 VPDN: Forwarding... Jan 1 00:43:27.799: Tnl/Cl 31770/7 L2TP: Session FS enabled Jan 1 00:43:27.799: Tnl/Cl 31770/7 L2TP: Session state change from idle to wait-for-tunnel Jan 1 00:43:27.803: Se0:0 Tnl/Cl 31770/7 L2TP: Create session Jan 1 00:43:27.803: Tnl 31770 L2TP: SM State established Jan 1 00:43:27.803: Se0:0 Tnl/Cl 31770/7 L2TP: O ICRQ to l2tp-gw 3843/0 Jan 1 00:43:27.803: Se0:0 Tnl/Cl 31770/7 L2TP: Session state change from wait-for-tunnel to wait-reply Jan 1 00:43:27.803: Se0:0 VPDN: 2500-1 is forwarded Jan 1 00:43:27.811: Se0:0 Tnl/Cl 31770/7 L2TP: O ICCN to l2tp-gw 3843/9 Jan 1 00:43:27.811: Se0:0 Tnl/Cl 31770/7 L2TP: Session state change from wait-reply to established Jan 1 00:43:28.803: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0:0, changed state to up
Related Information
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback