Configuring RADIUS Authentication Through the Cisco Cache Engine
Available Languages
Contents
Introduction
This document provides instructions on how to configure RADIUS authentication through the Cache Engine to the Cisco Secure Access Control Server (ACS) for Microsoft Windows NT. You should be running Web Cache Communication Protocol Version 2 (WCCPv2) to correctly follow this procedure. Please refer to Configuring Web Cache Communication Protocol Version 2 on a Cisco Cache Engine and Router for more information on WCCP version 2.
Prerequisites
Requirements
Before attempting this configuration, ensure that you meet these requirements:
-
Familiarity with Cisco Secure ACS for Windows or UNIX.
-
Familiarity with the WCCPv2 configuration on both router and cache Engine.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco Cache Engine 505 in a lab environment with cleared configurations
-
Cisco 2600 Router
-
Cisco Cache Engine Software Release 2.31
-
Cisco IOS® Software Release 12.1(3)T 3
-
Cisco Secure ACS for Microsoft Windows NT/2000 Servers
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
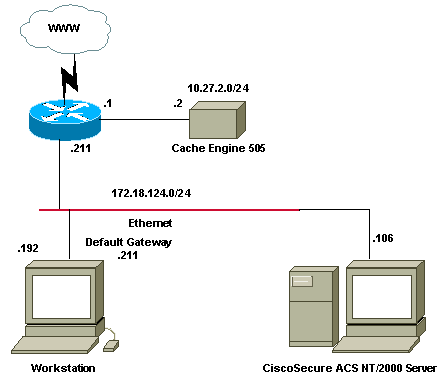
Network Diagram
This document uses this network setup:
Conventions
For more information on document conventions, refer to the Cisco Technical Tips Conventions.
Configure RADIUS Authentication Through Cache Engine Procedure
Use these steps to configure the Cache Engine for RADIUS authentication:
-
Configure the Cache Engine as the network access server (NAS) in Cisco Secure ACS for Windows NT.
-
Configure the user information in Cisco Secure ACS for Windows NT.
-
Configure the Cache Engine for RADIUS, and specify the host and key information.
radius-server host 172.18.124.106 radius-server key cisco123
-
Configure the router for WCCP.
Your command lines for the Cache Engine should appear similar to this:
cepro#configure terminal !--- Enter configuration commands, one per line. !--- End with CNTL/Z. cepro(config)#radius-server host 172.18.124.106 cepro(config)#radius-server key cisco123 cepro#
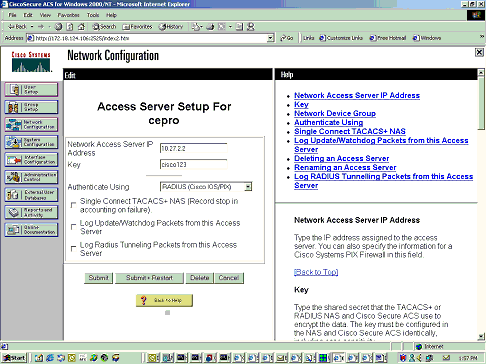
This is the Cache Engine/NAS configuration on Cisco Secure ACS for Windows NT:
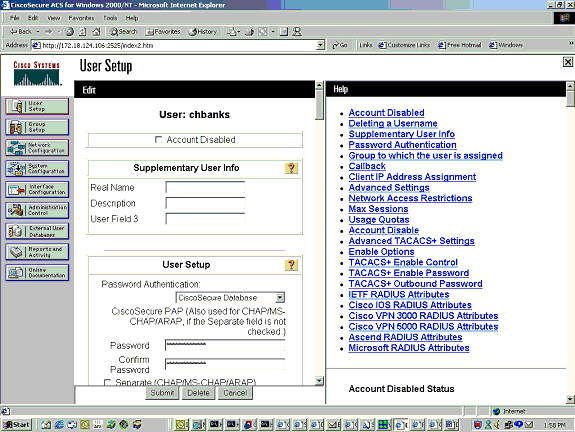
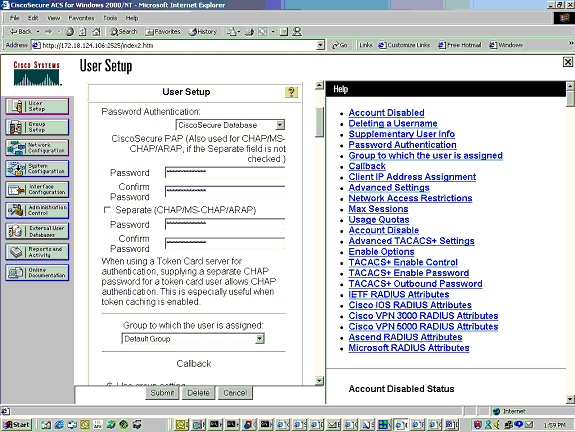
This is the User Setup page on Cisco Secure ACS for Windows NT:
Verify
This section provides information you can use to confirm your configuration is working properly.
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
Cache Engine Commands:
-
show version—Displays the software version running on the Cache Engine.
-
show hardware—Displays both the software version and the hardware type on the Cache Engine.
-
show running-config—Displays the actual running configuration on the Cache Engine.
-
show stat http usage—Displays usage statistics.
-
show radius stat [all | primary | secondary ]—Displays authentication statistics for the primary and secondary RADIUS servers.
This is sample command output of the show version command:
cepro#show version Cisco Cache Engine Copyright (c) 1986-2001 by Cisco Systems, Inc. Software Release: CE ver 2.31 (Build: FCS 02/16/01) Compiled: 11:20:14 Feb 22 2001 by bbalagot Image text-base 0x108000, data_base 0x437534 System restarted by Reload The system has been up for 3 hours, 52 minutes, 33 seconds. System booted from "flash"
This is sample command output of the show hardware command:
cepro#show hardware Cisco Cache Engine Copyright (c) 1986-2001 by Cisco Systems, Inc. Software Release: CE ver 2.31 (Build: FCS 02/16/01) Compiled: 11:20:14 Feb 22 2001 by bbalagot Image text-base 0x108000, data_base 0x437534 System restarted by Reload The system has been up for 3 hours, 52 minutes, 54 seconds. System booted from "flash" Cisco Cache Engine CE505 with CPU AMD-K6 (model 8) (rev. 12) AuthenticAMD 2 Ethernet/IEEE 802.3 interfaces 1 Console interface. 134213632 bytes of Physical Memory 131072 bytes of ROM memory. 8388608 bytes of flash memory. List of disk drives: /c0t0d0 (scsi bus 0, unit 0, lun 0)
This is sample command output of the show running-config command:
cepro#show running-config Building configuration... Current configuration: ! ! logging recycle 64000 logging trap information ! user add admin uid 0 password 1 "eeSdy9dcy" capability admin-access ! ! ! hostname cepro ! interface ethernet 0 ip address 10.27.2.2 255.255.255.0 ip broadcast-address 10.27.2.255 exit ! ! interface ethernet 1 exit ! ip default-gateway 10.27.2.1 ip name-server 161.44.11.21 ip name-server 161.44.11.206 ip domain-name cisco.com ip route 0.0.0.0 0.0.0.0 10.27.2.1 cron file /local/etc/crontab ! bypass timer 1 !--- Specify the router list for use with WCCPv2. wccp router-list 1 10.27.2.1 172.18.124.211 !--- Instruct the router to run web cache service with WCCPv2. wccp web-cache router-list-num 1 !--- WCCPv2 enabled. wccp version 2 ! !--- RADIUS Server host and port is defined. radius-server host 172.18.124.106 auth-port 1645 radius-server host 172.18.124.103 auth-port 1645 !--- RADIUS key defined. radius-server key **** authentication login local enable authentication configuration local enable transaction-logs enable rule no-cache url-regex .*cgi-bin.* rule no-cache url-regex .*aw-cgi.* ! ! end cepro#
Router Commands:
-
show running-config—Displays the actual running configuration on the router.
-
show ip wccp—Displays all registered services.
-
show ip wccp <service-id> detail—Displays the WCCP bucket-distribution for each cache in the cluster. For example, show ip wccp web-cache detail.
This is sample command output of the show running-config command:
33-ns-gateway#show running-config
Building configuration...
Current configuration:
!
version 12.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname 33-Ns-gateway
!
logging buffered 64000 debugging
enable secret 5 $1$IWJr$nI.NcIr/b9DN7jEQQC17R/
!
!
!
!
!
ip subnet-zero
!--- WCCP enabled.
ip wccp web-cache
ip cef
no ip domain-lookup
ip domain-name testdomain.com
ip name-server 161.44.11.21
ip name-server 161.44.11.206
!
!
!
!
interface Ethernet0/0
ip address 10.1.3.50 255.255.255.0
no ip route-cache cef
!
interface Ethernet1/0
description interface to the CE .5
bandwidth 100
ip address 10.27.2.1 255.255.255.0
full-duplex
!
interface Ethernet1/1
description inter to DMZ
ip address 172.18.124.211 255.255.255.0
!--- Configure the interface to enable the router !--- to verify that the appropriate !--- packets are redirected to the cache engine.
ip wccp web-cache redirect out
no ip route-cache cef
no ip route-cache
no ip mroute-cache
!
interface Ethernet1/2
description Preconfigured for recreates 10.27.3.0/24 net
ip address 10.27.3.1 255.255.255.0
no ip route-cache cef
!
interface Ethernet1/3
no ip address
shutdown
!
ip classless
ip route 0.0.0.0 0.0.0.0 172.18.124.1
no ip http server
!
!
line con 0
exec-timeout 0 0
transport input none
line aux 0
exec-timeout 0 0
line vty 0 4
exec-timeout 0 0
password ww
login
!
end
33-Ns-gateway#
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Troubleshooting Commands
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
Note: Before issuing debug commands, please see Important Information on Debug Commands.
Cache Engine Commands:
-
debug authentication all all—Debugs the authentication.
-
debug radius all all—Displays Web interface RADIUS module debug.
-
type var/log/translog/working.log—Verifies that URLs are cached, and that the user accesses the pages. Any other type of messages should be referred to Cisco Technical Support for clarification. The most common type of error messages in this log are authentication failed because of unknown user, or the incorrect server key.
This is sample command output from the debug radius all all and the debug authentication all all commands:
RadiusCheck(): Begin RadiusCheck(): Begin RadiusCheck(): Begin RadiusBuildRequest(): Begin RadiusBuildRequest(): Begin RadiusBuildRequest(): Begin [82] User-Name = "chbanks" [82] User-Name = "chbanks" [82] User-Name = "chbanks" [82] NAS-IP-Address = 10.27.2.2 [82] NAS-IP-Address = 10.27.2.2 [82] NAS-IP-Address = 10.27.2.2 [82] NAS-Port = 80 [82] NAS-Port = 80 [82] NAS-Port = 80 RadiusAuthenticate(): Begin RadiusAuthenticate(): Begin RadiusAuthenticate(): Begin CfgGetRadiusInfo(): Begin CfgGetRadiusInfo(): Begin CfgGetRadiusInfo(): Begin UpdatePassword(): Begin UpdatePassword(): Begin UpdatePassword(): Begin [82] radsend: Request to 172.18.124.106 id=1, length=171 [82] radsend: Request to 172.18.124.106 id=1, length=171 [82] radsend: Request to 172.18.124.106 id=1, length=171 RadiusReplyValidate(): Begin RadiusReplyValidate(): Begin RadiusReplyValidate(): Begin RadiusReplyValidate(): [82] Received 26 byte message back RadiusReplyValidate(): [82] Received 26 byte message back RadiusReplyValidate(): [82] Received 26 byte message back RadiusReplyValidate(): Got a valid response from server 172.18.124.106. RadiusReplyValidate(): Got a valid response from server 172.18.124.106. RadiusReplyValidate(): Got a valid response from server 172.18.124.106. DecodeReply(): Begin DecodeReply(): Begin DecodeReply(): Begin DecodeReply: WEB_YES_BLOCKING default DecodeReply: WEB_YES_BLOCKING default DecodeReply: WEB_YES_BLOCKING default RadiusCheck(): WEB_YES_BLOCKING RadiusCheck(): WEB_YES_BLOCKING RadiusCheck(): WEB_YES_BLOCKING RemoteUserAdd(): Begin RemoteUserAdd(): Begin RemoteUserAdd(): Begin RemoteUserAdd(): Updated remote user chbanks RemoteUserAdd(): Updated remote user chbanks RemoteUserAdd(): Updated remote user chbanks RemoteUserAuthenticate(): Begin RemoteUserAuthenticate(): Begin RemoteUserAuthenticate(): Begin CfgGetRadiusInfo(): Begin CfgGetRadiusInfo(): Begin CfgGetRadiusInfo(): Begin CfgRadiusGetExcludeState(): Begin CfgRadiusGetExcludeState(): Begin CfgRadiusGetExcludeState(): Begin CfgRadiusGetExcludeState(): flag = 0 CfgRadiusGetExcludeState(): flag = 0 CfgRadiusGetExcludeState(): flag = 0 RemoteUserUpdate(): Begin RemoteUserUpdate(): Begin RemoteUserUpdate(): Begin CfgRadiusGetMultipleUserPromptState(): Begin CfgRadiusGetMultipleUserPromptState(): Begin CfgRadiusGetMultipleUserPromptState(): Begin CfgRadiusGetMultipleUserPromptState(): flag = 1 CfgRadiusGetMultipleUserPromptState(): flag = 1 CfgRadiusGetMultipleUserPromptState(): flag = 1 CfgRadiusGetMultipleUserPromptTimeout(): Begin CfgRadiusGetMultipleUserPromptTimeout(): Begin CfgRadiusGetMultipleUserPromptTimeout(): Begin CfgRadiusGetMultipleUserPromptTimeout(): lMultipleUserPromptTimeout = 25 CfgRadiusGetMultipleUserPromptTimeout(): lMultipleUserPromptTimeout = 25 CfgRadiusGetMultipleUserPromptTimeout(): lMultipleUserPromptTimeout = 25 fsgetUsrInfoforIpAddr_radius will be called fsgetUsrInfoforIpAddr_radius will be called fsgetUsrInfoforIpAddr_radius will be called RemoteUserUpdate() returned true RemoteUserUpdate() returned true RemoteUserUpdate() returned true
Router Command:
-
show ip wccp—Displays global WCCP statistics.
 Feedback
Feedback