Asymmetric Routing and Firewalls
By Arvind Durai
Overview of Asymmetric Routing
What is Asymmetric Routing?
In Asymmetric routing, a packet traverses from a source to a destination in one path and takes a different path when it returns to the source. This is commonly seen in Layer-3 routed networks.
Issues to Consider with Asymmetric Routing
Asymmetric routing is not a problem by itself, but will cause problems when Network Address Translation (NAT) or firewalls are used in the routed path. For example, in firewalls, state information is built when the packets flow from a higher security domain to a lower security domain. The firewall will be an exit point from one security domain to the other. If the return path passes through another firewall, the packet will not be allowed to traverse the firewall from the lower to higher security domain because the firewall in the return path will not have any state information. The state information exists in the first firewall.
Designs Options for Support of Asymmetric Routing in Firewalls
1. Symmetric routing flow through the firewall
Keep the traffic flow symmetric through the firewall infrastructure. Here, the packet flow from one security domain to another will be through a single firewall. Redundancy for the flow is achieved via firewall redundancy (failover configuration).
2. Support of the Asymmetric routing feature
The Asymmetric routing (ASR) feature is supported in both the FWSM 3.x and ASA 7.x code releases, and can be leveraged in the firewalls in active/standby and active/active modes. This feature aligns the firewalls with the Layer-3 network to avoid asymmetric routing issues.
The designs in the data center using firewalls can leverage the asymmetric routing feature and active/active context in multiple context transparent firewalls to have dual routing paths for the same security rules. Figure 1 elaborates this design option:
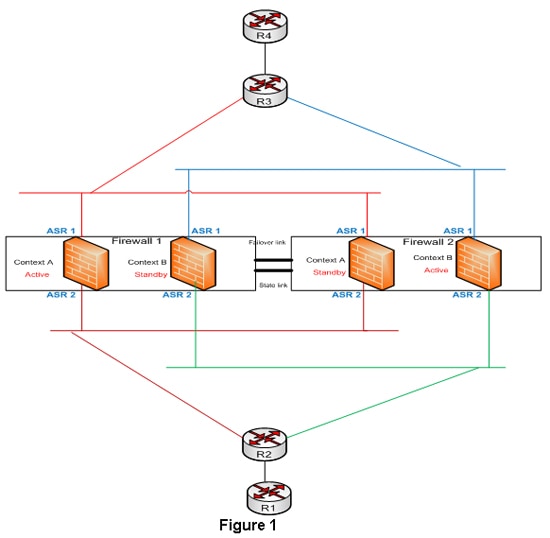
Firewalls 1 and 2 are in multiple context transparent mode and the security rules are the same for both the contexts. Routers R2 and R1 are in the inside security domain and routers R3 and R4 are in the outside security domain. The outside interfaces of both the firewalls are represented as ASR group 1 and the inside interfaces of the firewalls are represented as ASR group 2. The firewalls will be configured with respective access lists to pass the interesting traffic and the routing protocol information. Keep in mind that the firewall should be in transparent mode for the routing protocol to flow between the inside and the outside security domains and for a neighbor relationship to be formed. Routers R2 and R3 will have separate VLANs connecting each context of the firewall in each security domain. The inside and outside VLANs connecting the firewall will be in the same subnet but in different VLANs, since the firewall is in transparent mode. IGP neighbor relationship will be formed between routers R2 and R3 through these VLANs. This provides two routing paths in the design across two firewall contexts with the same security rule set and the packets can flow through either firewall contexts. The state information synchronization is maintained by ASR feature.
Summary
ASR issues have long been associated with routing designs that involved packets passing through firewalls. The support for asymmetric routing in firewalls changes this previous design philosophy. The asymmetric routing support with other new features can be leveraged for having greater scalability and redundancy for traffic passing through the firewall infrastructure.
This article provides only a snapshot of ASR feature and a design associated with this feature.


