Contents
- Configuring VLANs
- Finding Feature Information
- Prerequisites for VLANs
- Restrictions for VLANs
- Information About VLANs
- Logical Networks
- Supported VLANs
- VLAN Port Membership Modes
- VLAN Configuration Files
- Normal-Range VLAN Configuration Guidelines
- Extended-Range VLAN Configuration Guidelines
- Information About VLAN Group
- How to Configure VLANs
- How to Configure Normal-Range VLANs
- Creating or Modifying an Ethernet VLAN
- Deleting a VLAN
- Creating VLAN groups (CLI)
- Adding VLAN Group to WLAN (CLI)
- Assigning Static-Access Ports to a VLAN
- How to Configure Extended-Range VLANs
- Creating an Extended-Range VLAN
- Creating an Extended-Range VLAN with an Internal VLAN ID
- Monitoring VLANs
- Troubleshooting VLANs
- Where to Go Next
- Additional References
- Feature Information for VLANs
Configuring VLANs
- Finding Feature Information
- Prerequisites for VLANs
- Restrictions for VLANs
- Information About VLANs
- How to Configure VLANs
- Monitoring VLANs
- Troubleshooting VLANs
- Where to Go Next
- Additional References
- Feature Information for VLANs
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Related References
Prerequisites for VLANs
The following are prerequisites and considerations for configuring VLANs:
- If you plan to configure many VLANs on the switch and to not enable routing, you can set the Switch Database Management (SDM) feature to the VLAN template, which configures system resources to support the maximum number of unicast MAC addresses.
- Switches running the LAN Base feature set support only static routing on SVIs.
- A VLAN should be present in the switch to be able to add it to the VLAN group.
Restrictions for VLANs
The following are restrictions for VLANs:
- The switch supports per-VLAN spanning-tree plus (PVST+) or rapid PVST+ with a maximum of 128 spanning-tree instances. One spanning-tree instance is allowed per VLAN.
- The switch supports both Inter-Switch Link (ISL) and IEEE 802.1Q trunking methods for sending VLAN traffic over Ethernet ports.
- Configuring an interface VLAN router's MAC address is not supported. The interface VLAN already has an MAC address assigned by default.
- The number of VLANs mapped to a VLAN group is not limited by IOS. But if the number of VLANs in a VLAN group exceed the recommended value of 128, the mobility can be unexpected. So it is the responsibility of the administrator to configure feasible number of VLANs in a VLAN group. When a WLAN is mapped to a VLAN group which has more number of VLANs, an error is generated.
- The static IP client behavior is not supported.
- Private VLANs are not supported on the switch.
Information About VLANs
Logical Networks
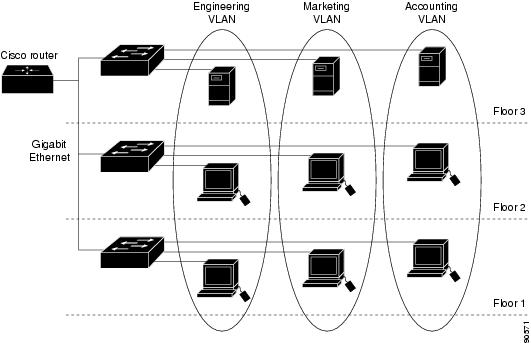
A VLAN is a switched network that is logically segmented by function, project team, or application, without regard to the physical locations of the users. VLANs have the same attributes as physical LANs, but you can group end stations even if they are not physically located on the same LAN segment. Any switch port can belong to a VLAN, and unicast, broadcast, and multicast packets are forwarded and flooded only to end stations in the VLAN. Each VLAN is considered a logical network, and packets destined for stations that do not belong to the VLAN must be forwarded through a router or a switch supporting fallback bridging. In a switch stack, VLANs can be formed with ports across the stack. Because a VLAN is considered a separate logical network, it contains its own bridge Management Information Base (MIB) information and can support its own implementation of spanning tree.
VLANs are often associated with IP subnetworks. For example, all the end stations in a particular IP subnet belong to the same VLAN. Interface VLAN membership on the switch is assigned manually on an interface-by-interface basis. When you assign switch interfaces to VLANs by using this method, it is known as interface-based, or static, VLAN membership.
Traffic between VLANs must be routed .
The switch can route traffic between VLANs by using switch virtual interfaces (SVIs). An SVI must be explicitly configured and assigned an IP address to route traffic between VLANs.
Supported VLANs
The switch supports VLANs in VTP client, server, and transparent modes. VLANs are identified by a number from 1 to 4094. VLAN 1 is the default VLAN and is created during system initialization. VLAN IDs 1002 through 1005 are reserved for Token Ring and FDDI VLANs. All of the VLANs except 1002 to 1005 are available for user configuration.
There are 3 VTP versions. VTP version 1 and version 2 support only normal-range VLANs (VLAN IDs 1 to 1005). In these versions, the switch must be in VTP transparent mode when you create VLAN IDs from 1006 to 4094. VTP version 3 supports the entire VLAN range (VLANs 1 to 4094). Extended range VLANs (VLANs 1006 to 4094) are supported only in VTP version 3. You cannot convert from VTP version 3 to VTP version 2 if extended VLANs are configured in the domain.
You can configure up to 4094 VLANs on the switch.
Related Tasks
Related References
VLAN Port Membership Modes
You configure a port to belong to a VLAN by assigning a membership mode that specifies the kind of traffic the port carries and the number of VLANs to which it can belong.
When a port belongs to a VLAN, the switch learns and manages the addresses associated with the port on a per-VLAN basis.
Table 1 Port Membership Modes and Characteristics Membership Mode
VLAN Membership Characteristics
VTP Characteristics
Static-access
A static-access port can belong to one VLAN and is manually assigned to that VLAN.
VTP is not required. If you do not want VTP to globally propagate information, set the VTP mode to transparent. To participate in VTP, there must be at least one trunk port on the switch or the switch stack connected to a trunk port of a second switch or switch stack.
Trunk (IEEE 802.1Q) :
A trunk port is a member of all VLANs by default, including extended-range VLANs, but membership can be limited by configuring the allowed-VLAN list. You can also modify the pruning-eligible list to block flooded traffic to VLANs on trunk ports that are included in the list.
VTP is recommended but not required. VTP maintains VLAN configuration consistency by managing the addition, deletion, and renaming of VLANs on a network-wide basis. VTP exchanges VLAN configuration messages with other switches over trunk links.
Dynamic access
Note Dynamic-access ports and VMPS is not supported on the switch.
A dynamic-access port can belong to one VLAN (VLAN ID 1 to 4094) and is dynamically assigned by a VLAN Member Policy Server (VMPS).
You can have dynamic-access ports and trunk ports on the same switch, but you must connect the dynamic-access port to an end station or hub and not to another switch.
VTP is required.
Configure the VMPS and the client with the same VTP domain name.
To participate in VTP, at least one trunk port on the switch or a switch stack must be connected to a trunk port of a second switch or switch stack.
Voice VLAN
A voice VLAN port is an access port attached to a Cisco IP Phone, configured to use one VLAN for voice traffic and another VLAN for data traffic from a device attached to the phone.
VTP is not required; it has no effect on a voice VLAN.
VLAN Configuration Files
Configurations for VLAN IDs 1 to 1005 are written to the vlan.dat file (VLAN database), and you can display them by entering the show vlan privileged EXEC command. The vlan.dat file is stored in flash memory. If the VTP mode is transparent, they are also saved in the switch running configuration file.
In a switch stack, the whole stack uses the same vlan.dat file and running configuration. On some switches, the vlan.dat file is stored in flash memory on the active switch.
You use the interface configuration mode to define the port membership mode and to add and remove ports from VLANs. The results of these commands are written to the running-configuration file, and you can display the file by entering the show running-config privileged EXEC command.
When you save VLAN and VTP information (including extended-range VLAN configuration information) in the startup configuration file and reboot the switch, the switch configuration is selected as follows:
- If the VTP mode is transparent in the startup configuration, and the VLAN database and the VTP domain name from the VLAN database matches that in the startup configuration file, the VLAN database is ignored (cleared), and the VTP and VLAN configurations in the startup configuration file are used. The VLAN database revision number remains unchanged in the VLAN database.
- If the VTP mode or domain name in the startup configuration does not match the VLAN database, the domain name and VTP mode and configuration for the VLAN IDs 1 to 1005 use the VLAN database information.
- In VTP versions 1 and 2, if VTP mode is server, the domain name and VLAN configuration for VLAN IDs 1 to 1005 use the VLAN database information. VTP version 3 also supports VLANs 1006 to 4094.
Normal-Range VLAN Configuration Guidelines
Normal-range VLANs are VLANs with IDs from 1 to 1005. VTP 1 and 2 only support normal-range VLANs.
Follow these guidelines when creating and modifying normal-range VLANs in your network:
- Normal-range VLANs are identified with a number between 1 and 1001. VLAN numbers 1002 through 1005 are reserved for Token Ring and FDDI VLANs.
- VLAN configuration for VLANs 1 to 1005 are always saved in the VLAN database. If the VTP mode is transparent, VTP and VLAN configuration are also saved in the switch running configuration file.
- If the switch is in VTP server or VTP transparent mode, you can add, modify or remove configurations for VLANs 2 to 1001 in the VLAN database. (VLAN IDs 1 and 1002 to 1005 are automatically created and cannot be removed.)
- With VTP versions 1 and 2, the switch supports VLAN IDs 1006 through 4094 only in VTP transparent mode (VTP disabled). These are extended-range VLANs and configuration options are limited. Extended-range VLANs created in VTP transparent mode are not saved in the VLAN database and are not propagated. VTP version 3 supports extended range VLAN (VLANs 1006 to 4094) database propagation in VTP server and transparent mode. If extended VLANs are configured, you cannot convert from VTP version 3 to version 1 or 2.
- Before you can create a VLAN, the switch must be in VTP server mode or VTP transparent mode. If the switch is a VTP server, you must define a VTP domain or VTP will not function.
- The switch does not support Token Ring or FDDI media. The switch does not forward FDDI, FDDI-Net, TrCRF, or TrBRF traffic, but it does propagate the VLAN configuration through VTP.
- The switch supports 128 spanning tree instances. If a switch has more active VLANs than supported spanning-tree instances, spanning tree can be enabled on 128 VLANs and is disabled on the remaining VLANs. If you have already used all available spanning-tree instances on a switch, adding another VLAN anywhere in the VTP domain creates a VLAN on that switch that is not running spanning-tree. If you have the default allowed list on the trunk ports of that switch (which is to allow all VLANs), the new VLAN is carried on all trunk ports. Depending on the topology of the network, this could create a loop in the new VLAN that would not be broken, particularly if there are several adjacent switches that all have run out of spanning-tree instances. You can prevent this possibility by setting allowed lists on the trunk ports of switches that have used up their allocation of spanning-tree instances. If the number of VLANs on the switch exceeds the number of supported spanning-tree instances, we recommend that you configure the IEEE 802.1s Multiple STP (MSTP) on your switch to map multiple VLANs to a single spanning-tree instance.
- When a switch in a stack learns a new VLAN or deletes or modifies an existing VLAN (either through VTP over network ports or through the CLI), the VLAN information is communicated to all stack members.
- When a switch joins a stack or when stacks merge, VTP information (the vlan.dat file) on the new switches will be consistent with the active switch.
Related Tasks
Related References
Extended-Range VLAN Configuration Guidelines
VTP 3 only supports extended-range VLANs. Extended-range VLANs are VLANs with IDs from 1006 to 4094.
Follow these guidelines when creating extended-range VLANs:
- VLAN IDs in the extended range are not saved in the VLAN database and are not recognized by VTP unless the switch is running VTP version 3.
- You cannot include extended-range VLANs in the pruning eligible range.
- In VTP version 1 and 2, a switch must be in VTP transparent mode when you create extended-range VLANs. If VTP mode is server or client, an error message is generated, and the extended-range VLAN is rejected. VTP version 3 supports extended VLANs in server and transparent modes.
- For VTP version 1 or 2, you can set the VTP mode to transparent in global configuration mode. You should save this configuration to the startup configuration so that the switch boots up in VTP transparent mode. Otherwise, you lose the extended-range VLAN configuration if the switch resets. If you create extended-range VLANs in VTP version 3, you cannot convert to VTP version 1 or 2.
- STP is enabled by default on extended-range VLANs, but you can disable it by using the no spanning-tree vlan vlan-id global configuration command. When the maximum number of spanning-tree instances are on the switch, spanning tree is disabled on any newly created VLANs. If the number of VLANs on the switch exceeds the maximum number of spanning-tree instances, we recommend that you configure the IEEE 802.1s Multiple STP (MSTP) on your switch to map multiple VLANs to a single spanning-tree instance.
- The number of routed ports, SVIs, and other configured features affects the use of the switch hardware. If you try to create an extended-range VLAN and there are not enough hardware resources available, an error message is generated, and the extended-range VLAN is rejected.
- In a switch stack, the whole stack uses the same running configuration and saved configuration, and extended-range VLAN information is shared across the stack.
Related Tasks
Related References
Information About VLAN Group
Whenever a wireless client connects to a wireless network (WLAN), the client is placed in a VLAN that is associated with the WLAN. In a large venue such as an auditorium, a stadium, or a conference where there are numerous wireless clients, having only a single WLAN to accommodate many clients might be a challenge.
The VLAN group feature enables in using a single WLAN that can support multiple VLANs. The clients can get assigned to one of the configured VLANs. This feature enables to map a WLAN to a single VLAN or multiple VLANs using the VLAN groups. When a wireless client associates to the WLAN, the VLAN is derived by an algorithm based on the MAC address of the wireless client. A VLAN is assigned to the client and the client gets the IP address from the assigned VLAN. This feature also extends the current AP group architecture and AAA override architecture, where the AP groups and AAA override can override a VLAN or a VLAN group to which the WLAN is mapped.
Related Concepts
How to Configure VLANs
How to Configure Normal-Range VLANs
You can set these parameters when you create a new normal-range VLAN or modify an existing VLAN in the VLAN database:
- VLAN ID
- VLAN name
- VLAN type
- VLAN state (active or suspended)
- Maximum transmission unit (MTU) for the VLAN
- Security Association Identifier (SAID)
- Bridge identification number for TrBRF VLANs
- Ring number for FDDI and TrCRF VLANs
- Parent VLAN number for TrCRF VLANs
- Spanning Tree Protocol (STP) type for TrCRF VLANs
- VLAN number to use when translating from one VLAN type to another
You can cause inconsistency in the VLAN database if you attempt to manually delete the vlan.dat file. If you want to modify the VLAN configuration, follow the procedures in this section.
- Creating or Modifying an Ethernet VLAN
- Deleting a VLAN
- Creating VLAN groups (CLI)
- Adding VLAN Group to WLAN (CLI)
- Assigning Static-Access Ports to a VLAN
Creating or Modifying an Ethernet VLAN
Before You BeginSUMMARY STEPSWith VTP version 1 and 2, if the switch is in VTP transparent mode, you can assign VLAN IDs greater than 1006, but they are not added to the VLAN database.
The switch supports only Ethernet interfaces. Because FDDI and Token Ring VLANs are not locally supported, you only configure FDDI and Token Ring media-specific characteristics for VTP global advertisements to other switches.
Although the switch does not support Token Ring connections, a remote device with Token Ring connections could be managed from one of the supported switches. Switches running VTP Version 2 advertise information about these Token Ring VLANs:
2. vlan vlan-id
3. name vlan-name
4. mtu mtu-size
5. media { ethernet | fd-net | fddi | tokenring | trn-net }
6. remote-span
8. show vlan {name vlan-name | id vlan-id}
DETAILED STEPSRelated References
Deleting a VLAN
SUMMARY STEPSWhen you delete a VLAN from a switch that is in VTP server mode, the VLAN is removed from the VLAN database for all switches in the VTP domain. When you delete a VLAN from a switch that is in VTP transparent mode, the VLAN is deleted only on that specific switch or a switch stack.
You cannot delete the default VLANs for the different media types: Ethernet VLAN 1 and FDDI or Token Ring VLANs 1002 to 1005.
Caution
When you delete a VLAN, any ports assigned to that VLAN become inactive. They remain associated with the VLAN (and thus inactive) until you assign them to a new VLAN.
DETAILED STEPS
Command or Action Purpose Related References
Creating VLAN groups (CLI)
SUMMARY STEPS
1. configure terminal
2. vlan group groupname vlan-list 1-256
3. end
DETAILED STEPS
Command or Action Purpose
Step 1 configure terminal
Example:Switch# configure terminalEnters global command mode.
Step 2 vlan group groupname vlan-list 1-256
Example:Switch#vlan group vlangrp1 vlan-list 91-95Creates a VLAN group with the given group name and adds all the VLANs listed in the command. The recommended number of VLANs in a group is 32.
Step 3 end
Example:Switch(vlan)#endExits the global configuration mode. Alternatively, press CTRL +Z to exit the global configuration mode.
Related References
Adding VLAN Group to WLAN (CLI)
SUMMARY STEPS
1. configure terminal
2. wlan wlanname 1 wlanname
3. client vlan vlangrp1
4. end
DETAILED STEPS
Command or Action Purpose
Step 1 configure terminal
Example:Switch# configure terminalEnters global command mode.
Step 2 wlan wlanname 1 wlanname
Example:Switch(config)#wlan wlanA 1 wlanAEnables the WLAN to map a VLAN group.
Step 3 client vlan vlangrp1
Example:Switch(config-wlan)#client vlan vlangrp1Maps the VLAN group to the WLAN.
Step 4 end
Example:Switch(config-wlan)#endExits the global configuration mode. Alternatively, press CTRL +Z to exit the global configuration mode.
Assigning Static-Access Ports to a VLAN
SUMMARY STEPSYou can assign a static-access port to a VLAN without having VTP globally propagate VLAN configuration information by disabling VTP (VTP transparent mode). For more information on static-access ports, see VLAN Port Membership Modes.
If you assign an interface to a VLAN that does not exist, the new VLAN is created.
1. configure terminal
2. interface interface-id
3. switchport mode access
4. switchport access vlan vlan-id
5. end
6. show running-config interface interface-id
7. show interfaces interface-id switchport
DETAILED STEPS
Command or Action Purpose
Step 1 configure terminal
Example:Switch# configure terminalEnters global configuration mode
Step 2 interface interface-id
Example:Switch(config)# interface gigabitethernet2/0/1Enters the interface to be added to the VLAN.
Step 3 switchport mode access
Example:Switch(config-if)# switchport mode accessDefines the VLAN membership mode for the port (Layer 2 access port).
Step 4 switchport access vlan vlan-id
Example:Switch(config-if)# switchport access vlan 2Assigns the port to a VLAN. Valid VLAN IDs are 1 to 4094.
Step 5 end
Example:Switch(config-if)# endReturns to privileged EXEC mode.
Step 6 show running-config interface interface-id
Example:Switch# copy running-config startup-configVerifies the VLAN membership mode of the interface.
Step 7 show interfaces interface-id switchport
Example:Switch# show interfaces gigabitethernet2/0/1Verifies your entries in the Administrative Mode and the Access Mode VLAN fields of the display.
Related References
How to Configure Extended-Range VLANs
With VTP version 1 and version 2, when the switch is in VTP transparent mode (VTP disabled), you can create extended-range VLANs (in the range 1006 to 4094). VTP 3 version supports extended-range VLANs in server or transparent move.
Extended-range VLANs enable service providers to extend their infrastructure to a greater number of customers. The extended-range VLAN IDs are allowed for any switchport commands that allow VLAN IDs.
With VTP version 1 or 2, extended-range VLAN configurations are not stored in the VLAN database, but because VTP mode is transparent, they are stored in the switch running configuration file, and you can save the configuration in the startup configuration file. Extended-range VLANs created in VTP version 3 are stored in the VLAN database.
You can change only the MTU size , private VLAN, and the remote SPAN configuration state on extended-range VLANs; all other characteristics must remain at the default state.
Creating an Extended-Range VLAN
SUMMARY STEPSIn VTP version 1 or 2, if you enter an extended-range VLAN ID when the switch is not in VTP transparent mode, an error message is generated when you exit VLAN configuration mode, and the extended-range VLAN is not created.
Before you create an extended-range VLAN, you can verify that the VLAN ID is not used internally by entering the show vlan internal usage privileged EXEC command.
2. vtp mode transparent
3. vlan vlan-id
4. remote-span
5. mtu mtu size
6. exit
7. interface vlan
8. ip mtu mtu-size
10. show vlan id vlan-id
11. copy running-config startup config
DETAILED STEPS
Command or Action Purpose
Step 1 configure terminal
Example:Switch# configure terminalStep 2 vtp mode transparent
Example:Switch(config)# vtp mode transparentConfigures the switch for VTP transparent mode, disabling VTP.
Note This step is not required for VTP version 3.
Step 3 vlan vlan-id
Example:Switch(config)# vlan 2000 Switch(config-vlan)#Enters an extended-range VLAN ID and enters VLAN configuration mode. The range is 1006 to 4094.
Step 4 remote-span
Example:Switch(config-vlan)# remote-span(Optional) Configures the VLAN as the RSPAN VLAN.
Step 5 mtu mtu size
Example:Switch(config-vlan)# mtu 1024Modifies the VLAN by changing the MTU size.
Step 6 exit
Example:Switch(config-vlan)# exit Switch(config)#Returns to configuration mode.
Step 7 interface vlan
Example:Switch(config)# interface vlan 200 Switch(config-if)#Enters the interface configuration mode for the selected VLAN.
Step 8 ip mtu mtu-size
Example:Switch(config-if)# ip mtu 1024 Switch(config-if)#(Optional) Modifies the VLAN by changing the MTU size. You can configure the MTU size between 68 to 1500 bytes.
Note Although all VLAN commands appear in the CLI help, only the ip mtu mtu-size, private-vlan, and remote-span commands are supported for extended-range VLANs.
Step 9 end
Example:Switch(config)# endStep 10 show vlan id vlan-id
Example:Switch# show vlan id 2000Verifies that the VLAN has been created.
Step 11 copy running-config startup config
Example:Switch# copy running-config startup-configSaves your entries in the switch startup configuration file. To save an extended-range VLAN configuration, you need to save the VTP transparent mode configuration and the extended-range VLAN configuration in the switch startup configuration file. Otherwise, if the switch resets, it will default to VTP server mode, and the extended-range VLAN IDs will not be saved.
Note This step is not required for VTP version 3 because VLANs are saved in the VLAN database.
Related References
Creating an Extended-Range VLAN with an Internal VLAN ID
SUMMARY STEPSIf you enter an extended-range VLAN ID that is already assigned to an internal VLAN, an error message is generated, and the extended-range VLAN is rejected. To manually free an internal VLAN ID, you must temporarily shut down the routed port that is using the internal VLAN ID.
1. show vlan internal usage
2. configure terminal
3. interface interface-id
4. shutdown
5. exit
6. vtp mode transparent
7. vlan vlan-id
8. exit
9. interface interface-id
10. no shutdown
11. end
12. copy running-config startup config
DETAILED STEPS
Command or Action Purpose
Step 1 show vlan internal usage
Example:Switch# show vlan internal usageDisplays the VLAN IDs being used internally by the switch. If the VLAN ID that you want to use is an internal VLAN, the display shows the routed port that is using the VLAN ID. Enter that port number in Step 3.
Step 2 configure terminal
Example:Switch# configure terminalEnters global configuration mode.
Step 3 interface interface-id
Example:Switch(config)# interface gigabitethernet1/0/3Specifies the interface ID for the routed port that is using the VLAN ID, and enter interface configuration mode.
Step 4 shutdown
Example:Switch(config-if)# shutdownShuts down the port to free the internal VLAN ID.
Step 5 exit
Example:Switch(config-if)# exitReturns to global configuration mode.
Step 6 vtp mode transparent
Example:Switch(config)# vtp mode transparentSets the VTP mode to transparent for creating extended-range VLANs.
Note This step is not required for VTP version 3.
Step 7 vlan vlan-id
Example:Switch(config-vlan)# vlan 2000Enters the new extended-range VLAN ID, and enter VLAN configuration mode.
Step 8 exit
Example:Switch(config-vlan)# exitExits from VLAN configuration mode, and return to global configuration mode.
Step 9 interface interface-id
Example:Switch(config)# interface gigabitethernet1/0/3Specifies the interface ID for the routed port that you shut down in Step 4, and enter interface configuration mode.
Step 10 no shutdown
Example:Switch(config)# no shutdownRe-enables the routed port. It will be assigned a new internal VLAN ID.
Step 11 end
Example:Switch(config)# endReturns to privileged EXEC mode.
Step 12 copy running-config startup config
Example:Switch# copy running-config startup-configSaves your entries in the switch startup configuration file. To save an extended-range VLAN configuration, you need to save the VTP transparent mode configuration and the extended-range VLAN configuration in the switch startup configuration file. Otherwise, if the switch resets, it will default to VTP server mode, and the extended-range VLAN IDs will not be saved.
Note This step is not required for VTP version 3 because VLANs are saved in the VLAN database.
Related References
Monitoring VLANs
Table 2 Privileged EXEC show Commands Command
Purpose
show interfaces [vlan vlan-id]
Displays characteristics for all interfaces or for the specified VLAN configured on the switch
show platform vlan [switch number | vlan-id ]
Displays VLAN information by switch or VLAN number.
show vlan [ access-map name | brief | dot1q { tag native } | filter [ access-map | vlan ] | group [ group-name name ] | id vlan-id | ifindex | mtu | name name | remote-span | summary ]
Displays parameters for all VLANs or the specified VLAN on the switch . The following command options are available:
- access-map—Displays the VLAN access-maps.
- brief—Displays VTP VLAN status in brief.
- dot1q—Displays the dot1q parameters.
- filter—Displays VLAN filter information.
- group—Displays the VLAN group with its name and the connected VLANs that are available.
- id—Displays VTP VLAN status by identification number.
- ifindex—Displays SNMP ifIndex.
- mtu—Displays VLAN MTU information.
- name—Display the VTP VLAN information by specified name.
- remote-span–Displays the remote SPAN VLANs.
- summary—Displays a summary of VLAN information.
Related Concepts
Troubleshooting VLANs
This section describes commands used to troubleshoot VLANs.
The following commands can be used to troubleshoot VLANs on the switch .
Table 3 VLAN Troubleshooting CommandsCommand
Description
debug platform vlan [ error [ switch number ] | event [switch number ] | switch number ]
Debugs platform related VLAN issues
debug switchport {backup { all | errors | events | vlan-load-balancing } }
Debugs the switchport configuration. The following debug switchport options are available:
debug sw-vlan { badpmcookies | cfg-vlan | events | ifs | management | mapping | notification | packets | redundancy | registries | vtp }
Debugs the VLAN manager. The following command options are available:
- badpmcookies—Debugs VLAN manager incidents of bad Port Manager (pm) cookies.
- cfg-vlan—Debugs the VLAN configuration.
- events—Debugs VLAN manager events.
- ifs—Debugs VLAN manager ifs error tests.
- management—Debugs VLAN manager management of internal vlans.
- mapping—Debugs VLAN mapping.
- notification—Debugs VLAN manager notifications.
- packets—Debugs VLAN manager packets.
- redundancy—Debugs VTP VLAN redundancy.
- registries—Debugs VLAN manager registries.
- vtp—VTP protocol debugging.
debug vlan { configuration vlan }
Debugs the VLAN. Specify the VLAN or VLAN range for debugging.
Additional References
Related Documents
Related Topic Document Title CLI commands
Layer 2/3 Command Reference, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
VLAN Command Reference (Catalyst 3850 Switches)
VLANs and IEEE 802.1Q Tunneling
Security Configuration Guide, Cisco IOS Release 3SE (Catalyst 3850 Switches)
Security Command Reference, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
VLAN access-maps
Security Configuration Guide, Cisco IOS Release 3SE (Catalyst 3850 Switches)
Security Command Reference, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
Cisco Flexible NetFlow
Cisco Flexible NetFlow Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
Flexible Netflow Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
IGMP Snooping
IP Multicast Command Reference, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
IP Multicast Routing Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
IPv6
Catalyst 3850 IPv6 Configuration Guide, Release 3.2SE
IPv6 Command Reference, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
SPAN
Network Management Command Reference, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
Network Management Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
MIBs
MIB MIBs Link All supported MIBs for this release.
- BRIDGE-MIB (RFC1493)
- CISCO-BRIDGE-EXT-MIB
- CISCO-CDP-MIB
- CISCO-PAGP-MIB
- CISCO-PRIVATE-VLAN-MIB
- CISCO-LAG-MIB
- CISCO-L2L3-INTERFACE-CONFIG-MIB
- CISCO-MAC-NOTIFICATION-MIB
- CISCO-STP-EXTENSIONS-MIB
- CISCO-VLAN-IFTABLE-RELATIONSHIP-MIB
- CISCO-VLAN-MEMBERSHIP-MIB
- CISCO-VTP-MIB
- IEEE8023-LAG-MIB
- IF-MIB (RFC 1573)
- RMON-MIB (RFC 1757)
- RMON2-MIB (RFC 2021)
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL:
Technical Assistance
Description Link The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies.
To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds.
Access to most tools on the Cisco Support website requires a Cisco.com user ID and password.
Feature Information for VLANs
Table 4 Feature Information for VLANs Feature Name
Releases
Feature Information
VLAN functionality
Cisco IOS XE 3.2SE
The switch supports VLANs in VTP client, server, and transparent modes. VLANs are identified by a number from 1 to 4094. VLAN 1 is the default VLAN and is created during system initialization. VLAN IDs 1002 through 1005 are reserved for Token Ring and FDDI VLANs. All of the VLANs except 1002 to 1005 are available for user configuration.

 Feedback
Feedback