-
User Guide for Cisco Security MARS Local Controller, Release 5.3.x
-
Preface
-
STM Task Flow Overview
-
Reporting and Mitigation Devices Overview
-
Authenticating with External AAA Servers
-
Configuring Router and Switch Devices
-
Configuring Firewall Devices
-
Configuring VPN Devices
-
Configuring Network-based IDS and IPS Devices
-
Configuring Host-Based IDS and IPS Devices
-
Configuring Antivirus Devices
-
Configuring Vulnerability Assessment Devices
-
Configuring Generic, Solaris, Linux, and Windows Application Hosts
-
Configuring Database Applications
-
Configuring Web Server Devices
-
Configuring Web Proxy Devices
-
Configuring AAA Devices
-
Configuring Wireless LAN Devices
-
Configuring Custom Devices
-
Policy Table Lookup on Cisco Security Manager
-
Network Summary
-
Case Management
-
Incident Investigation and Mitigation
-
Queries and Reports
-
Rules
-
Sending Alerts
-
Management Tab Overview
-
System Maintenance
-
Cisco Security MARS XML API Reference
-
Regular Expression Reference
-
Date/Time Format Specfication
-
System Rules and Reports Reference
-
Glossary
-
Index
-
Table Of Contents
Supporting Cisco Secure ACS Server
Supporting Cisco Secure ACS Solution Engine
Configure Cisco Secure ACS to Generate Logs
Configure TACACS+ Command Authorization for Cisco Routers and Switches
Install and Configure the PN Log Agent
Upgrade PN Log Agent to a Newer Version
Application Log Messages for the PN Log Agent
Add and Configure the Cisco ACS Device in MARS
Configuring AAA Devices
Revised: February 23, 2007Authentication, authorization, and accounting (AAA) devices provide accountability throughout your network, ensuring that valid users are authorized to use the network services they request and providing detailed event logs regarding failures and successes in such requests.
The AAA server is a key component in the Network Access Control (NAC) initiative (see Configuring Network Admission Control Features, page 2-53 and Enable NAC-specific Messages, page 4-4). Cisco Secure Access Control Server (ACS), which is the AAA server for NAC, returns access control decisions to the network access device on the basis of the antivirus credentials of the hosts that are requesting network services.
MARS supports the Cisco Secure ACS software and the Cisco Secure ACS Solution Engine, version 3.3 and later. In the case of Cisco Secure ACS software, support is provided by an agent that resides on the Cisco Secure ACS server. For the Cisco Secure ACS Solution Engine, this agent must reside on a remote logging host. This agent provides MARS with three event logs in syslog format. The logs are as follows:
•
Passed authentication log (requires Cisco Secure ACS, 3.3 or later)
•
Failed attempts log
•
RADIUS accounting log
To support NAC and the 802.1x features, Cisco Secure ACS uses the RADIUS authentication protocol and the cisco-av-pair attributes. For more information on configuring Cisco Secure ACS as a posture validation server for NAC, see the following URLs:
•
"Network Admission Control" chapter in User Guide for Cisco Secure ACS for Windows Server, Version 3.3
•
"Posture Validation" chapter in User Guide for Cisco Secure ACS for Windows, Version 4.0
•
"Using Profile Templates" section in the "Network Access Profiles" chapter in User Guide for Cisco Secure ACS for Windows, Version 4.0
For more information on the cisco-av-pair attributes, see the following URL:
This chapter explains how to prepare the Cisco Secure ACS server or the Cisco Secure ACS Solution Engine to allow MARS to collect the event logs. It also describes how to configure MARS to receive and process these logs correctly. Using the web interface, you must define a host to represent the Cisco Secure ACS server (or the remote logging agent collecting logs for the Cisco Secure ACS Solution Engine) and then add the software application to that host.
Supporting Cisco Secure ACS Server
To configure a Cisco Secure ACS server to act as a reporting device, you must perform three tasks:
1.
Configure Cisco Secure ACS server to generate the correct log files and details and define the AAA clients.
2.
Install the PN Log Agent on the Cisco Secure ACS server and configure it to forward the correct log files.
3.
Add the Cisco Secure ACS server to the MARS web interface
You can also configure Cisco Secure ACS to provide command authorization for the MARS Appliance. In this role, Cisco Secure ACS verifies that the MARS Appliance is authorized to execute specific commands on reporting devices and mitigation devices.
The following sections detail supporting a Cisco Secure ACS server:
•
Install and Configure the PN Log Agent
•
Add and Configure the Cisco ACS Device in MARS
Supporting Cisco Secure ACS Solution Engine
MARS supports the Cisco Secure ACS Solution Engine via a remote logging host. Cisco Secure ACS Remote Agent for Windows is a Windows-based application that supports Cisco Secure ACS Solution Engine for remote logging.
Even though the Cisco Secure ACS Solution Engine supports up to five appliance via a remote logging host, MARS currently supports only one Cisco Secure ACS Solution Engines per remote logging host. Otherwise, MARS cannot identify the IP address of the originating Cisco Secure ACS Solution Engine.
To enable this support, follow these steps:
1.
Configure the Cisco Secure ACS Solution Engine to publish logs to the remote logging host. See Bootstrap Cisco Secure ACS.
2.
Install and configure the Cisco Secure ACS Remote Agent for Windows on the target remote logging host. This host must be running a supported version of Microsoft Windows.
For instructions on installing and configuring the remote agent, see see Installation and Configuration Guide for Cisco Secure ACS Remote Agents.
3.
Install the pnLog Agent on the remote logging host.
For information on installing and configuring the pnLog Agent, see Install and Configure the PN Log Agent.
4.
Add the remote logging host to MARS as a Cisco ACS 3.x reporting device. To perform this task see Add and Configure the Cisco ACS Device in MARS, and substitute the ACS server references with the remote logging host.
Bootstrap Cisco Secure ACS
Bootstrapping the Cisco Secure ACS includes the following task:
•
Configure Cisco Secure ACS to Generate Logs
•
(Optional) Configure TACACS+ Command Authorization for Cisco Routers and Switches
Configure Cisco Secure ACS to Generate Logs
To configure Cisco Secure ACS to generate the audit logs required by MARS, follow these steps:
Step 1
Log in to the Cisco Secure ACS server or Solution Engine.
Step 2
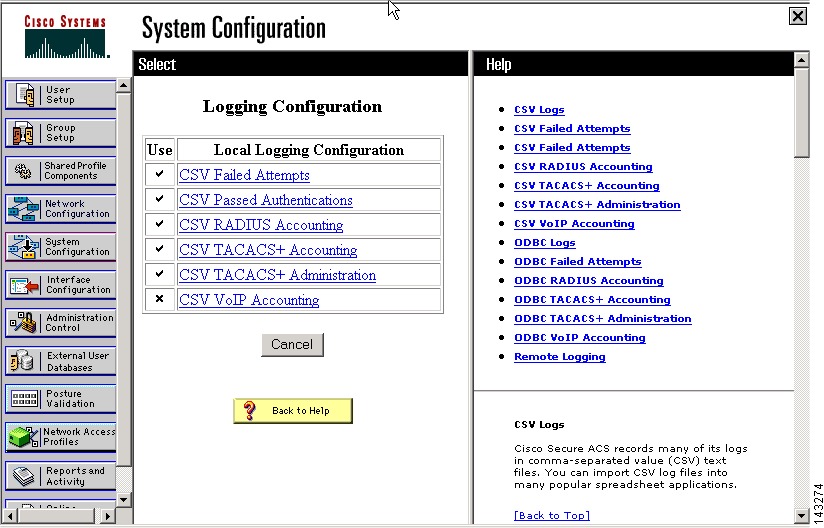
Select System Configuration > Logging.
Step 3
Verify that CVS Failed Attempts, CVS Passed Authentications and CVS RADIUS Accounting Logging are enabled.
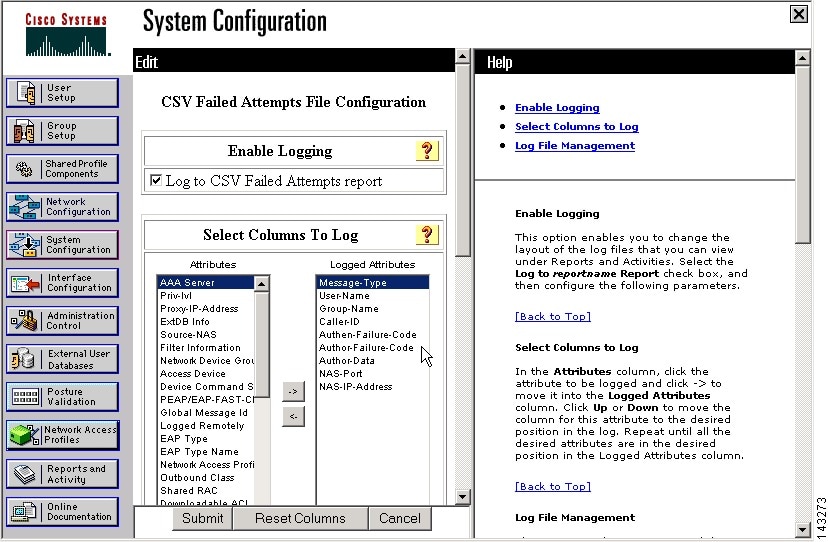
Step 4
Click CSV Failed Attempts, and verify that the following attributes appear in the Logged Attributes list:
•
User-Name
•
Caller-ID
•
NAS-Port
•
NAS-IP-Address
•
AAA-Server
•
Authen-Failure-Code
•
Message-Type
Step 5
Click Submit
Step 6
Click CVS Passed Authentications, and verify that the following attributes appear in the Logged Attributes list:
•
AAA Server'
•
User-Name
•
Caller-ID
•
NAS-Port
•
NAS-IP-Address
•
System-Posture-Token
•
EAP Type Name
Step 7
Click Submit.
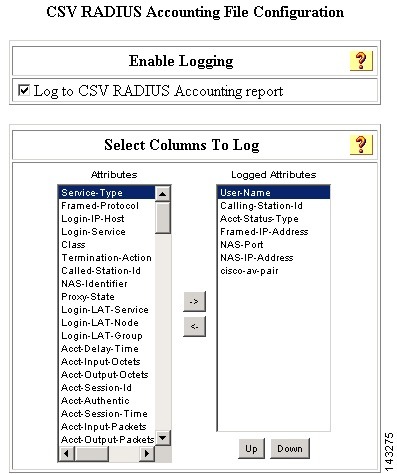
Step 8
Click CVS RADIUS Accounting, and verify that the following attributes appear in the Logged Attributes list:
•
User-Name
•
Calling-Station-Id
•
Acct-Status-Type
•
NAS-Port
•
NAS-IP-Address
•
AAA Server
•
Framed-IP-Address
Step 9
To support the 802.1x features of NAC, select the following RADIUS accounting attributes:
•
Framed-IP address
•
cisco-av-pair
Step 10
Click Submit.
For additional details on the RADIUS attributes supported by Cisco Secure ACS, see to the following URL:
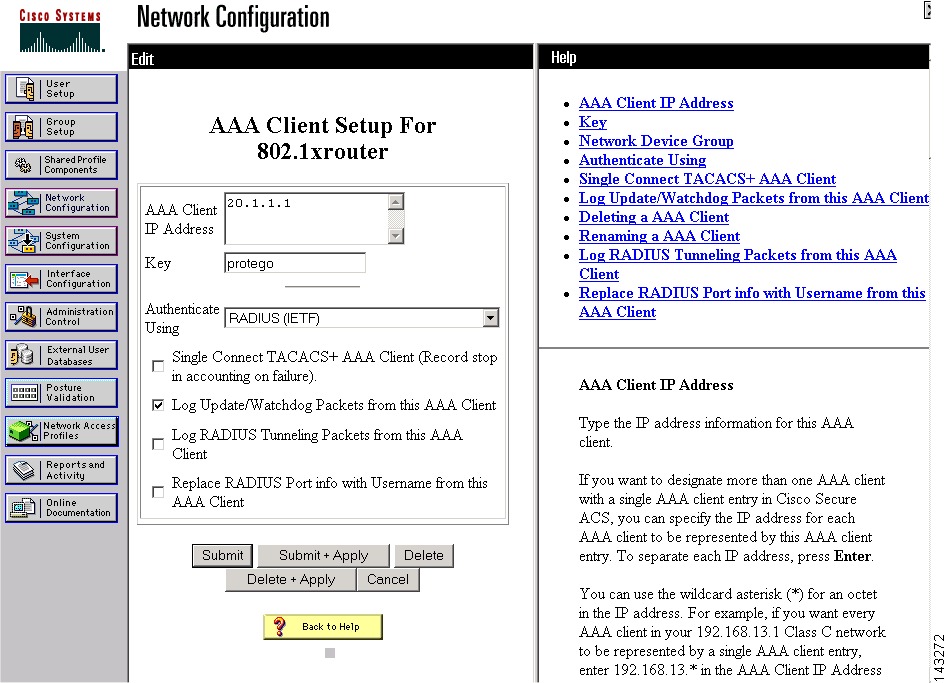
Define AAA Clients
To support the 802.1x features of NAC, you must also define the Cisco switches as AAA clients within Cisco Secure ACS. When defining a AAA client, verify the following settings:
•
Enable the authentication method that best supports the 802.1x functionality that you want to enable. This option is selected in the Using Authentication box.
•
Enable logging of watchdog packets, interim updates. Select the Log Update/Watchdog Packets from this AAA Client check box. This option ensures that interim updates are sent from the Cisco Secure ACS to MARS.
To enable 802.1x logging support, the following configuration must also be completed.
•
Ensure DHCP snooping is enabled on each network access device that you plan to define as an 802.1x client in MARS
Note
The attack path can not be calculated for a NAC 802.1x security incident when the events triggering the incident are reported to the MARS Appliance by Cisco Secure ACS. However, the MARS Appliance knows the switch port to block so you can mitigate without the attack path.
Figure 15-1 displays example settings for such a client.
Figure 15-1 Configure a AAA Client to Support 802.1x
For more information on defining AAA clients, see the following URL:
Configure TACACS+ Command Authorization for Cisco Routers and Switches
You can use the TACACS+ feature of Cisco Secure ACS to authorize the command sets that MARS is allowed to execute on a reporting device. The use of this feature is not required by MARS. However, if you are using this feature on your routers and switches, you must ensure that MARS is allowed to execute specific commands. Required commands are grouped under two operations: configuration retrieval and mitigation.
The following commands support configuration retrieval:
•
all show commands
•
changeto system
•
changeto context <context_name>
•
enable
•
page
•
no page
•
terminal length 0
•
terminal pager lines 0
•
write terminal
The following commands support mitigation:
•
conf terminal
•
interface <interface_name>
•
shutdown
•
set port disable <port_name>
For more information on configuring command authorization sets in Cisco Secure ACS, see the following URL:
Install and Configure the PN Log Agent
MARS includes the PN Log Agent to monitor Cisco Secure ACS active log files (failed attempts, passed authentications, and RADIUS accounting). This agent pushes these log files via syslog to MARS. You can download the PN Log Agent from the software download center at the following URL:
http://www.cisco.com/pcgi-bin/tablebuild.pl/cs-mars-misc
Note
If you are upgrading to a new version of the PN Log Agent, see Upgrade PN Log Agent to a Newer Version.
As part of its operation, the PNLog Agent service writes error and informational message to the Application Log, which can be viewed using the Event Viewer. To learn more about these messages, see Application Log Messages for the PN Log Agent.
To install and configure the PNLog Agent, follow these steps:
Step 1
Download the PN Log Agent and install it on the server running Cisco Secure ACS or on the remote logging host to which the Cisco Secure ACS Solution Engine is publishing its logs.
Note
If installing on a remote logging host, you must have configured the Cisco Secure ACS Remote Agent for Windows on the target remote logging host.
For instructions on installing and configuring the remote agent, see Installation and Configuration Guide for Cisco Secure ACS Remote Agents.
Step 2
Select Start > All Programs > Protego Networks > PNLogAgent > Pn Log Agent
Step 3
Click Edit > PN-MARS Config.
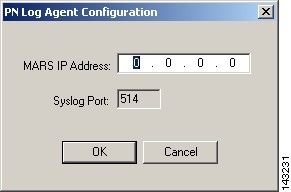
Result: The PN Log Agent Configuration dialog box appears.
Step 4
In the MARS IP Address field, enter the address of the MARS Appliance, and click OK.
Step 5
Select Edit > Log File Config > Add.
Step 6
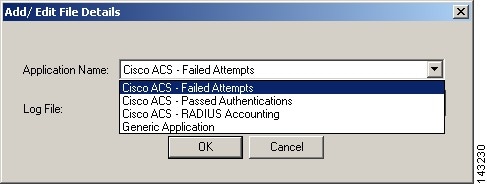
From the Edit pull down menu select Add.
Result: The Add/Edit File Details dialog box appears.
Step 7
From the Application Name list, select the Cisco ACS-Failed Attempts.
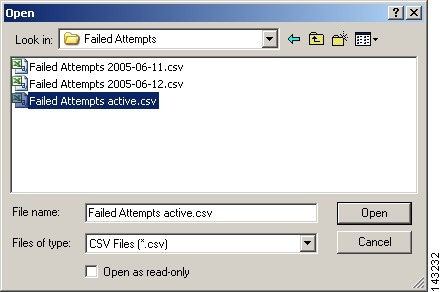
Step 8
Click on the ... button to select the appropriate log where all Cisco Secure ACS logs are stored. In this example after selecting Failed Attempts application, be sure to select the matching log file, Failed Attempts active log.
Result: The Open dialog box appears.
Step 9
Add all 3 applications and their active log files:
•
Failed Attempts active
•
Passed Authentications active
•
RADIUS Accounting active
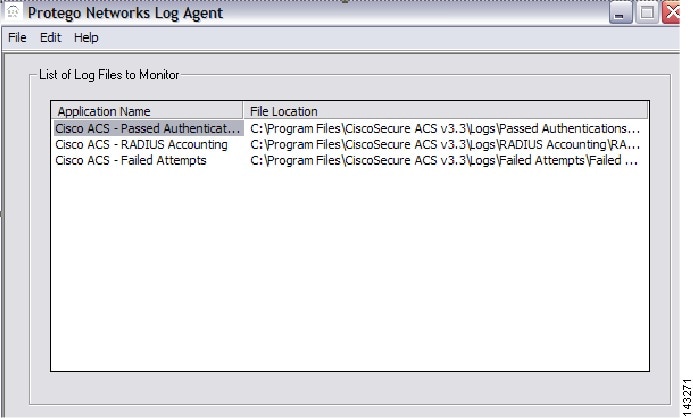
Result: The configured files appear in the List of Log Files to Monitor list.
Step 10
Select File > Activate.
Upgrade PN Log Agent to a Newer Version
You can determine which version of the PN Log Agent is running on your server by selecting Help > About in the PN Log Agent Configuration dialog box. This program is updated independently of the MARS Appliance software updates. Therefore, the version number does not correspond to any release of the MARS Appliance software.
Note
Beginning with the 4.1.3 release of the pnLog agent, the agent requires a minimum of Cisco Security Monitoring, Analysis, and Response System, release 4.1.3 running on the appliances to which it is reporting in order to operate correctly.
To upgrade to the new PN Log Agent from an existing installation, you must perform the following steps:
Step 1
On the Cisco Secure ACS or syslog server where PN Log Agent is running, uninstall the old agent.
a.
To uninstall the old agent, click Start > Control Panel > Add/Remove Programs.
b.
Select PnLogAgent in the list of currently installed programs, and click Remove.
c.
Select Yes to confirm the removal.
Step 2
Reboot the server.
Step 3
Install the new agent. You can download this tool from the following URL:
http://www.cisco.com/pcgi-bin/tablebuild.pl/cs-mars-misc
Step 4
Re-configure the new agent, specifying the list of files and IP address of the MARS Appliance, etc.
For information on configuring the pnLog Agent, see Install and Configure the PN Log Agent.
Application Log Messages for the PN Log Agent
The PN Log Agent service writes events to the Application Log of Event Viewer on the Cisco Secure ACS server. The agent, identified in the log messages as PNLogAgentService, writes status messages, such as successful service start and stop. It also writes error messages for incomplete configuration and error conditions, such as when the service is out of memory.
Table 15-1 categories the types of messages that can occur and explains their affects on the PNLog Agent service.
Add and Configure the Cisco ACS Device in MARS
To add the host and Cisco Secure ACS software application to MARS, follow these steps:
Step 1
Click Admin > Security and Monitor Devices > Add.
Step 2
From the Device Type list, select Add SW Security apps on a new host.
You can also select Add SW Security apps on an existing host if you have already defined the host within MARS, perhaps as part of the Management >IP Management settings or if you are running another application on the host, such as Microsoft Internet Information Services.
Step 3
In the Device Name field, enter the hostname of the server or the remote logging host.
Step 4
In the Reporting IP field, enter the IP address of the interface in Cisco Secure ACS server or the remote logging host from which the syslog messages will originate.
Step 5
Under Enter interface information, enter the interface name, IP address, and netmask value of the interface in Cisco Secure ACS server or remote logging host from which the syslog messages will originate.
This address is the same value as the Reporting IP address.
Step 6
Click Apply.
Step 7
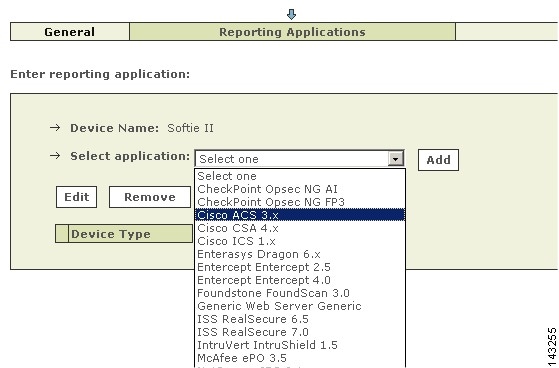
Click Next to move the Reporting Applications tab.
Step 8
In the Select Application box, select Cisco ACS 3.x, and then click Add.
Result: The Cisco ACS 3.x Windows Requirements page appears, explaining that you must have installed an agent on the server as described in Install and Configure the PN Log Agent.
Note
The Cisco ACS 3.x option supports both Cisco Secure ACS 3.x and Cisco Secure ACS 4.0. No explicit 4.0 option exists for Cisco Secure ACS.
Step 9
Click Submit to add this application to the host.
Result: Cisco ACS 3.x appears in the Device Type list.
Step 10
Click the Vulnerability Assessment Info link to define the host information that MARS uses to determine false positive attacks against this host. Continue with Define Vulnerability Assessment Information, page 11-12.
Step 11
Click Done to save the changes.
Result: The new host appears in the Security and Monitoring Information list.
Step 12
To activate the device, click Activate.

 Feedback
Feedback