Contents
- RSVP-VRF Lite Admission Control
- Finding Feature Information
- Prerequisites for RSVP-VRF Lite Admission Control
- Restrictions for RSVP-VRF Lite Admission Control
- Information About RSVP-VRF Lite Admission Control
- Overview of RSVP-VRF Lite Admission Control
- Benefits of RSVP-VRF Lite Admission Control
- How to Configure RSVP-VRF Lite Admission Control
- Enabling RSVP on an Interface
- Configuring a Receiver Proxy on a Tailend Router
- Configuring a Static Sender on a Headend Router
- Configuring an RSVP Application Identity That Is VRF Aware
- Configuring an RSVP Local Policy That Is VRF Aware
- Verifying the RSVP-VRF Lite Admission Control Configuration
- Configuration Examples for RSVP-VRF Lite Admission Control
- Examples Configuring RSVP-VRF Lite Admission Control
- Examples Verifying RSVP-VRF Lite Admission Control
- Additional References
- Feature Information for RSVP-VRF Lite Admission Control
- Glossary
RSVP-VRF Lite Admission Control
The RSVP--VRF Lite Admission Control feature introduces support for Resource Reservation Protocol (RSVP) call admission control (CAC) in an IP session within the context of a virtual routing and forwarding (VRF) instance.
- Finding Feature Information
- Prerequisites for RSVP-VRF Lite Admission Control
- Restrictions for RSVP-VRF Lite Admission Control
- Information About RSVP-VRF Lite Admission Control
- How to Configure RSVP-VRF Lite Admission Control
- Configuration Examples for RSVP-VRF Lite Admission Control
- Additional References
- Feature Information for RSVP-VRF Lite Admission Control
- Glossary
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for RSVP-VRF Lite Admission Control
You must configure RSVP on one or more interfaces on at least two neighboring routers that share a link within the network.
Restrictions for RSVP-VRF Lite Admission Control
- Multi-topology routing (MTR) is not supported.
- Multiprotocol Label Switching (MPLS) virtual private network (VPN) VRFs are not supported.
- RSVP authentication is not supported.
Information About RSVP-VRF Lite Admission Control
Overview of RSVP-VRF Lite Admission Control
An RSVP flow is identified by its tuple, which includes its destination IP address, its destination port, and its protocol. This tuple should be unique on all the nodes along the path from the sender to the receiver. In the context of the global routing domain, each flow can be uniquely identified through its tuple.
However, with the implementation of virtual routing and forwarding (VRF), a separate instance of the routing and forwarding table for each VRF routing domain can exist. Each of the VRF instances has its own address pool range, which could overlap between VRF routing domains. This poses a problem to the existing implementation of RSVP, where sessions are identified by the tuple. Sessions with the same tuple can exist in the context of different VRF domains. To solve the problem, the tuple has to be extended to take into account the VRF instance. The new tuple has a VRF ID, a destination IP address , a destination port, and a protocol . The VRF ID is derived based on the interface on which an RSVP packet has been received and is not signaled using RSVP. Therefore, each node needs to infer the VRF ID based on the RSVP control packet's incoming interface.
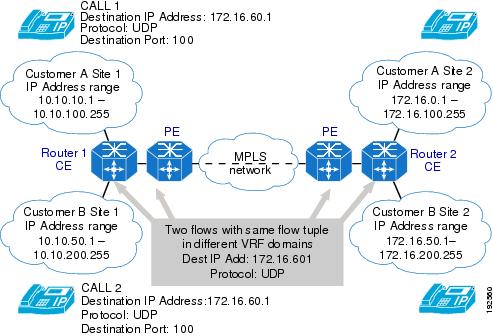
The figure below shows a VRF-lite deployment scenario.
The figure above shows VRF lite configured on Router 1 customer edge (CE) and Router 2 CE, and MPLS-VPN configured between the provider edge (PE) routers. In such a deployment scenario, the RSVP implementation needs to be VRF aware in the CE routers; that is, the flows must be recognized in the context of the VRF domain in which the sender and receiver of the flow reside. However, RSVP QoS is not enabled on the PE routers.
On the CE routers, with VRF lite functionality, VRF is identified based on the VRF configured on the incoming interface; that is, on the interface facing the customer site and the interface facing the PE.
Benefits of RSVP-VRF Lite Admission Control
The RSVP--VRF Lite Admission Control feature provides the benefits of RSVP in a VRF-lite environment to include the following:
- Guaranteed QoS through explicit admission control
- Virtualization
- Security
- Separation of routing contexts
- Overlapping of IP addresses
How to Configure RSVP-VRF Lite Admission Control
- Enabling RSVP on an Interface
- Configuring a Receiver Proxy on a Tailend Router
- Configuring a Static Sender on a Headend Router
- Configuring an RSVP Application Identity That Is VRF Aware
- Configuring an RSVP Local Policy That Is VRF Aware
- Verifying the RSVP-VRF Lite Admission Control Configuration
Enabling RSVP on an Interface
Perform this task to enable RSVP on all the interfaces along the path from the sender to the receiver.
DETAILED STEPS
Configuring a Receiver Proxy on a Tailend Router
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode.
|
Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. |
Step 3 |
ip
rsvp
listener
[vrf vrf-name] dst {udp | tcp | any | number} {any | dst-port} {announce | reply | reject} Example: Router(config)# ip rsvp listener vrf myvrf 192.168.2.1 any any reply |
Configures an RSVP router to listen for PATH messages.
|
Step 4 |
end
Example: Router(config)# end |
(Optional) Returns to privileged EXEC mode. |
Configuring a Static Sender on a Headend Router
Perform this task to configure a static sender with a VRF on a headend router to make the router proxy an RSVP PATH message.
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode.
|
Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. |
Step 3 |
ip
rsvp
sender-host
session-ip-address
sender-ip-address
{tcp | udp | ip-protocol} session-d-port sender-s-port bandwidth burst-size [identity alias] [vrf vrf-name] Example: Router(config)# ip rsvp sender-host 10.0.0.7 10.0.0.1 udp 1 1 10 10 vrf myvrf |
Enables a router to simulate a host generating RSVP PATH messages.
|
Step 4 |
end
Example: Router(config)# end |
Exits global configuration mode and returns to privileged EXEC mode. |
Configuring an RSVP Application Identity That Is VRF Aware
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode.
|
Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. |
Step 3 |
ip
rsvp
policy
vrf
vrf-name
{identity{alias policy-locator regular-expression| local}}{acl acl1[acl2...acl8] | default | identity alias1[alias2...alias4]| origin-as as1 [as2...as8]} Example: Router(config)# ip rsvp policy vrf myvrf identity voice policy-locator voiceStream |
Creates a local policy for a VRF and enters local policy configuration mode.
|
Step 4 |
end
Example: Router(config-rsvp-policy-local)# end |
(Optional) Exits local policy configuration mode and returns to privileged EXEC mode. |
Configuring an RSVP Local Policy That Is VRF Aware
DETAILED STEPS
| Command or Action | Purpose | |||||
|---|---|---|---|---|---|---|
Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode.
| ||||
Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. | ||||
Step 3 |
ip
rsvp
policy
vrf
vrf-name
{identity{alias policy-locator regular-expression| local}}{acl acl1[acl2...acl8] | default | identity alias1[alias2...alias4]| origin-as as1 [as2...as8]} Example: Router(config)# ip rsvp policy vrf myvrf local default |
Creates a local policy for a VRF and enters local policy configuration mode.
| ||||
Step 4 |
{accept | forward[all | path| path-error | resv| resv-error] | default | exit | fast-reroute | local-override | maximum [bandwidth [group x] [single y] | senders n]| preempt-priority [traffic-eng x] setup-priority [hold-priority]} Example: Router(config-rsvp-policy-local)# forward all |
(Optional) Defines the properties of the local policy that you are creating. (These are the submode commands.)
| ||||
Step 5 |
end
Example: Router(config-rsvp-policy-local)# end |
(Optional) Exits local policy configuration mode and returns to privileged EXEC mode. |
Verifying the RSVP-VRF Lite Admission Control Configuration
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
Step 1 |
enable
Example: Router> enable |
(Optional) Enables privileged EXEC mode. |
Step 2 |
show
ip
rsvp
counters
[authentication][interface type number|
neighbor[vrf{*| vrf-name}] | state teardown| summary]
Example: Router# show ip rsvp counters neighbor vrf myvrf |
(Optional) Displays the number of RSVP messages that were sent and received on each interface. |
Step 3 |
show
ip
rsvp
host
vrf
{* | vrf-name}
{receivers |
senders}
[group-name |
group-address]
Example: Router(config)# show ip rsvp vrf * senders |
(Optional) Displays specific information for an RSVP host configured with a VRF instance. |
Step 4 |
show
ip
rsvp
installed
[vrf{* | vrf-name}]
[interface-type interface-number]
[detail]
Example: Router# show ip rsvp installed vrf myvrf detail |
(Optional) Displays RSVP-related installed filters and corresponding bandwidth information. |
Step 5 |
show
ip
rsvp
interface
[vrf{* | vrf-name}]
[detail] [interface-type interface-number]
Example: Router# show ip rsvp interface vrf myvrf detail |
(Optional) Displays information related to RSVP. |
Step 6 |
show
ip
rsvp
listeners
[ip-address | any | vrf{* | vrf-name}]
[udp | tcp | any | protocol]
[dst-port | any]
Example: Router# show ip rsvp listeners vrf myvrf1 |
(Optional) Displays the RSVP listeners for a specified port or protocol. |
Step 7 |
show
ip
rsvp
neighbor
[detail | inactive[detail]] | vrf{* | vrf-name}]
Example: Router# show ip rsvp neighbor vrf myvrf1 |
(Optional) Displays current RSVP neighbors. |
Step 8 |
show
ip
rsvp
policy
vrf
{* | vrf-name}
[identity[alias]] |
local[acl acl | default | detail[acl acl | default | identity alias | interface interface-type | origin-as as-number]]
Example: Router# show ip rsvp policy vrf myvrf1 |
(Optional) Displays information for an RSVP policy configured with a VRF instance. |
Step 9 |
show
ip
rsvp
request
[vrf{* | vrf-name}]
[detail] [filter
[destination ip-address|
hostname]
[dst-port port-number]
[source ip-address|
hostname]
[src-port port-number]]
Example: Router# show ip rsvp request vrf myvrf1 |
(Optional) Displays RSVP-related request information currently in the database. |
Step 10 |
show
ip
rsvp
reservation
[detail |
filter
[destination ip-address|
hostname]
[dst-port port-number]
[source ip-address|
hostname]
[src-port port-number]] [vrf{* |
vrf-name}]
Example: Router# show ip rsvp reservation vrf myvrf1 |
(Optional) Displays RSVP-related receiver information currently in the database. |
Step 11 |
show
ip
rsvp
sender
[detail |
filter
[destination ip-address|
hostname]
[dst-port port-number]
[source ip-address|
hostname]
[src-port port-number]] [vrf{* |
vrf-name}]
Example: Router# show ip rsvp sender vrf myvrf1 |
(Optional) Displays RSVP PATH-related sender information currently in the database. |
Step 12 |
show
ip
rsvp
signalling
fast-local-repair
[statistics[detail]]
Example: Router# show ip rsvp signalling fast-local repair statistics detail |
(Optional) Displays fast-local-repair (FLR)-specific information, including VRF, maintained by RSVP. |
Configuration Examples for RSVP-VRF Lite Admission Control
- Examples Configuring RSVP-VRF Lite Admission Control
- Examples Verifying RSVP-VRF Lite Admission Control
Examples Configuring RSVP-VRF Lite Admission Control
The following example enables RSVP on a router interface along the path from the sender to the receiver.
 Note | If the interface lies in a VRF domain, use the ip rsvp bandwidth command to enable RSVP for that VRF. |
Router# configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)# interface Ethernet0/0 Router(config-if)# ip rsvp bandwidth 1158 100 Router(config-if)# end
The following example configures a receiver proxy with a specified VRF on a tailend router:
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)# ip rsvp listener vrf myvrf 192.168.2.1 any any reply
Router(config)# end
The following example configures a static sender with a specified VRF on a headend router:
Router# configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)# ip rsvp sender-host 10.0.0.7 10.0.0.1 udp 1 1 10 10 vrf myvrf Router(config)# end
Examples Verifying RSVP-VRF Lite Admission Control
In the following example, all the interfaces associated with the VRF named myvrf display in detail: Router# show ip rsvp interface vrf myvrf detail Se1/0: RSVP: Enabled Interface State: Up Bandwidth: Curr allocated: 300K bits/sec Max. allowed (total): 400K bits/sec Max. allowed (per flow): 400K bits/sec Max. allowed for LSP tunnels using sub-pools (pool 1): 0 bits/sec Set aside by policy (total): 0 bits/sec Traffic Control: RSVP Data Packet Classification is OFF RSVP resource provider is: none Signalling: DSCP value used in RSVP msgs: 0x3F Number of refresh intervals to enforce blockade state: 4 Authentication: disabled Key chain: <none> Type: md5 Window size: 1 Challenge: disabled FRR Extension: Backup Path: Not Configured BFD Extension: State: Disabled Interval: Not Configured RSVP Hello Extension: State: Disabled RFC 3175 Aggregation: Enabled Role: interior VRF: myvrf The following example displays details of the RSVP reservations installed for RSVP session that belong to the VRF named myvrf: Router# show ip rsvp installed vrf myvrf detail RSVP: FastEthernet2/0 has the following installed reservations RSVP Reservation. Destination is 10.10.10.10. Source is 10.10.10.12, Protocol is UDP, Destination port is 10, Source port is 10 Traffic Control ID handle: C8000407 Created: 22:51:26 UTC Sun Feb 17 2008 Admitted flowspec: Reserved bandwidth: 10K bits/sec, Maximum burst: 10K bytes, Peak rate: 10K bits/sec Min Policed Unit: 0 bytes, Max Pkt Size: 0 bytes Resource provider for this flow: None Conversation supports 1 reservations [0xBF000406] Data given reserved service: 0 packets (0 bytes) Data given best-effort service: 0 packets (0 bytes) Reserved traffic classified for 12783 seconds Long-term average bitrate (bits/sec): 0 reserved, 0 best-effort Policy: INSTALL. Policy source(s): Default VRF : myvrf
The following example shows the listeners configured for the VRF named myvrf:
Router# show ip rsvp listeners vrf myvrf
VRF : myvrf1
To Protocol DPort Description Action OutIf
10.0.2.1 any any RSVP Proxy reply
The following example shows the neighbors created for the VRF named myvrf:
Router# show ip rsvp neighbor vrf myvrf
VRF: myvrf
Neighbor Encapsulation Time since msg rcvd/sent
10.10.15.3 Raw IP 00:00:14 00:00:06
10.10.16.2 Raw IP 00:00:29 00:00:15
The following example displays all the locally created RSVP senders for the configured VRFs:
Router# show ip rsvp host vrf * senders
VRF: vrf2
To From Pro DPort Sport Prev Hop I/F BPS
192.168.104.4 198.168.104.12 UDP 10 10 none none 10K
Mode(s): Host CLI
VRF: vrf1
To From Pro DPort Sport Prev Hop I/F BPS
192.168.105.4 198.168.105.12 UDP 10 10 none none 10K
Mode(s): Host CLI
Additional References
Related Documents
|
Related Topic |
Document Title |
|---|---|
|
QoS commands: complete command syntax, command modes, command history, defaults, usage guidelines, and examples |
Cisco IOS Quality of Service Solutions Command Reference |
|
VRF-related internet draft |
Support for RSVP in Layer 3 VPNs, Internet draft, November 19, 2007 [draft-davie-tsvwg-rsvp-l3vpn-01.txt] |
|
Cisco IOS commands |
MIBs
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for RSVP-VRF Lite Admission Control
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 1 | Feature Information for RSVP--VRF Lite Admission Control |
|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
RSVP--VRF Lite Admission Control |
15.0(1)SY |
The RSVP--VRF Lite Admission Control feature introduces support for RSVP CAC in an IP session within the context of a VRF instance. The following commands were introduced or modified by this feature: debug ip rsvp , ip rsvp listener, ip rsvp policy vrf, ip rsvp reservation-host, ip rsvp sender-host, show ip rsvp counters, show ip rsvp host vrf, show ip rsvp installed, show ip rsvp interface, show ip rsvp listeners, show ip rsvp neighbor, show ip rsvp policy vrf, show ip rsvp request, show ip rsvp reservation, show ip rsvp sender, show ip rsvp signalling fast-local-repair. |
Glossary
admission control --The process by which an RSVP reservation is accepted or rejected on the basis of end-to-end available network resources.
QoS --quality of service. A measure of performance for a transmission system that reflects its transmission quality and service availability. Quality of service focuses on achieving appropriate network performance for networked applications; it is superior to best effort performance.
RSVP --Resource Reservation Protocol. A protocol that supports the reservation of resources across an IP network. Applications that run on IP end systems can use RSVP to indicate to other nodes the nature (bandwidth, jitter, maximum burst, and so on) of the packet streams that they want to receive.
VRF --virtual routing and forwarding. An extension of IP routing that provides multiple routing instances. A VRF consists of an IP routing table, a derived forwarding table, a set of interfaces that use the forwarding table, and a set of rules and routing protocols that determine what goes into the forwarding table. In general, a VRF includes the routing information that defines a customer VPN site that is attached to a provider edge (PE) router.
Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1005R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.

 Feedback
Feedback