Contents
- Static Application Mapping Using Performance Routing
- Finding Feature Information
- Prerequisites for Static Application Mapping Using Performance Routing
- Information About Static Application Mapping Using Performance Routing
- Performance Routing Traffic Class Profiling
- Static Application Mapping Using PfR
- Learn List Configuration Mode
- How to Configure Static Application Mapping Using Performance Routing
- Defining a Learn List to Automatically Learn Traffic Classes Using Static Application Mapping
- Manually Selecting Traffic Classes Using Static Application Mapping
- Displaying and Resetting Traffic Class and Learn List Information
- Configuration Examples for Static Application Mapping Using Performance Routing
- Example Defining a Learn List to Automatically Learn Traffic Classes Using Static Application Mapping
- Example Defining a Learn List for Automatically Learned Prefix-Based Traffic Classes
- Example Defining a Learn List for Automatically Learned Application Traffic Classes Using an Access List
- Example Manually Selecting Traffic Classes Using Static Application Mapping
- Example Manually Selecting Prefix-Based Traffic Classes Using a Prefix List
- Example Manually Selecting Application Traffic Classes Using an Access List
- Where To Go Next
- Additional References
- Feature Information for Static Application Mapping Using Performance Routing
Static Application Mapping Using Performance Routing
The OER - Application Aware Routing with Static Application Mapping feature introduces the ability to configure standard applications using just one keyword to simplify the configuration of traffic classes that PfR can automatically learn, or that can be manually configured. This feature also introduces a learn list configuration mode that allows Performance Routing (PfR) policies to be applied to traffic classes profiled in a learn list. Different policies can be applied to each learn list.
- Finding Feature Information
- Prerequisites for Static Application Mapping Using Performance Routing
- Information About Static Application Mapping Using Performance Routing
- How to Configure Static Application Mapping Using Performance Routing
- Configuration Examples for Static Application Mapping Using Performance Routing
- Where To Go Next
- Additional References
- Feature Information for Static Application Mapping Using Performance Routing
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Static Application Mapping Using Performance Routing
Cisco Express Forwarding (CEF) must be enabled on all participating devices. No other switching path is supported, even if otherwise supported by Policy-Based Routing (PBR).
Information About Static Application Mapping Using Performance Routing
- Performance Routing Traffic Class Profiling
- Static Application Mapping Using PfR
- Learn List Configuration Mode
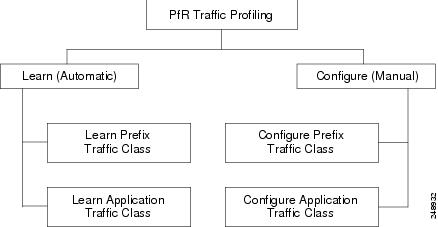
Performance Routing Traffic Class Profiling
Before optimizing traffic, Performance Routing (PfR) has to determine the traffic classes from the traffic flowing through the border routers. To optimize traffic routing, subsets of the total traffic must be identified, and these traffic subsets are named traffic classes. The list of traffic classes entries is named a Monitored Traffic Class (MTC) list. The entries in the MTC list can be profiled either by automatically learning the traffic flowing through the device or by manually configuring the traffic classes. Learned and configured traffic classes can both exist in the MTC list at the same time. Both the learn mechanism and the configure mechanism for traffic classes are implemented during the PfR profile phase. The overall structure of the PfR traffic class profile process and its component parts can be seen in the figure below.
PfR can automatically learn the traffic classes while monitoring the traffic flow through border routers using the embedded NetFlow capability. Although the goal is to optimize a subset of the traffic, you may not know all the exact parameters of this traffic and PfR provides a method to automatically learn the traffic and create traffic classes by populating the MTC list. Within the automatic traffic class learning process there are three components:
- Automatic learning of prefix-based traffic classes
- Automatic learning of application-based traffic classes
- Using learn lists to categorize both prefix-based and application-based traffic classes
PfR can be manually configured to create traffic classes for monitoring and subsequent optimizing. Automatic learning generally uses a default prefix length of /24 but manual configuration allows exact prefixes to be defined. Within the manual traffic class configuration process there are two components:
- Manually configuring prefix-based traffic classes
- Manually configuring application-based traffic classes
The ultimate objective of the profile phase is to select a subset of traffic flowing through the network. This subset of traffic--the traffic classes in the MTC list--represents the classes of traffic that need to be routed based on the best performance path available.
More details about each of the traffic class profiling components in the figure above are contained in the "Understanding Performance Routing" module.
Static Application Mapping Using PfR
The OER - Application Aware Routing with Static Application Mapping feature introduced the ability to define an application using a keyword to simplify the configuration of application-based traffic classes. PfR uses well-known applications with fixed ports, and more than one application may be configured at the same time. The list of static applications available for profiling Performance Routing traffic classes is constantly evolving. Use the traffic-class application ? command to determine if a static application is available for use with Performance Routing.
The table below displays a partial list of static applications that can be configured with Performance Routing. The applications are considered static because they are defined with fixed port and protocols as shown in the table. Configuration is performed on a master controller under learn list configuration mode.
| Table 1 | Static Application List |
|
Application |
Keyword |
Protocol |
Port |
|---|---|---|---|
|
CU-SeeMe-Server --CU-SeeMe desktop video conference |
cuseeme |
TCP UDP |
7648 7649 7648 7649 24032 |
|
DHCP-Client --Dynamic Host Configuration Protocol client |
dhcp (Client) |
UDP/TCP |
68 |
|
DHCP-Server --Dynamic Host Configuration Protocol server |
dhcp (Server) |
UDP/TCP |
67 |
|
DNS --Domain Name Server lookup |
dns |
UDP/TCP |
53 |
|
FINGER-Server --Finger server |
finger |
TCP |
79 |
|
FTP --File Transfer Protocol |
ftp |
TCP |
20, 21 |
|
GOPHER-Server --Gopher server |
gopher |
TCP/UDP |
70 |
|
HTTP-- Hypertext Transfer Protocol, World Wide Web traffic |
http |
TCP/UDP |
80 |
|
HTTPSSL-Server-- Hypertext Transfer Protocol over TLS/SSL, Secure World Wide Web traffic server |
secure-http |
TCP |
443 |
|
IMAP-Server --Internet Message Access Protocol server |
imap |
TCP/UDP |
143 220 |
|
SIMAP-Server --Secure Internet Message Access Protocol server |
secure-imap |
TCP/UDP |
585 993 (Preferred) |
|
IRC-Server --Internet Relay Chat server |
irc |
TCP/UDP |
194 |
|
SIRC-Server --Secure Internet Relay Chat server |
secure-irc |
TCP/UDP |
994 |
|
Kerberos-Server --Kerberos server |
kerberos |
TCP/UDP |
88 749 |
|
L2TP-Server --L2F/L2TP tunnel Layer 2 Tunnel Protocol server |
l2tp |
UDP |
1701 |
|
LDAP-Server --Lightweight Directory Access Protocol server |
ldap |
TCP/UDP |
389 |
|
SLDAP-Server --Secure Lightweight Directory Access Protocol server |
secure-ldap |
TCP/UDP |
636 |
|
MSSQL-Server --MS SQL server |
mssql |
TCP |
1443 |
|
NETBIOS-Server --NETBIOS server |
netbios |
UDP TCP |
137 138 137 139 |
|
NFS-Server --Network File System server |
nfs |
TCP/UDP |
2049 |
|
NNTP-Server --Network News Transfer Protocol |
nntp |
TCP/UDP |
119 |
|
SNNTP-Server --Network News Transfer Protocol over TLS/SSL |
secure-nntp |
TCP/UDP |
563 |
|
NOTES-Server --Lotus Notes server |
notes |
TCP/UDP |
1352 |
|
NTP-Server --Network Time Protocol server |
ntp |
TCP/UDP |
123 |
|
PCanywhere-Server --Symantec pcANYWHERE |
pcany |
UDP TCP |
22 5632 65301 5631 |
|
POP3-Server --Post Office Protocol server |
pop3 |
TCP/UDP |
110 |
|
SPOP3-Server --Post Office Protocol over TLS/SSL server |
secure-pop3 |
TCP/UDP |
123 |
|
PPTP-Server --Point-to-Point Tunneling Protocol server |
pptp |
TCP |
17233 |
|
SSH --Secured Shell |
ssh |
TCP |
22 |
|
SMTP-Server --Simple Mail Transfer Protocol server |
smtp |
TCP |
25 |
|
Telnet --Telnet |
telnet |
TCP |
23 |
The master controller is configured to learn the top prefixes based on highest outbound throughput or delay for the filtered traffic, and the resulting traffic classes are added to the PfR application database to be passively and actively monitored.
Learn List Configuration Mode
The Learn List feature introduced a new configuration mode named learn list. Learn lists are a way to categorize learned traffic classes. In each learn list, different criteria including prefixes, application definitions, filters, and aggregation parameters for learning traffic classes can be configured. A traffic class is automatically learned by PfR based on each learn list criteria, and each learn list is configured with a sequence number. The sequence number determines the order in which learn list criteria are applied. Learn lists allow different PfR policies to be applied to each learn list; in previous releases, the traffic classes could not be divided, and an PfR policy was applied to all the learned traffic classes.
Four types of traffic classes--to be automatically learned or manually configured--can be profiled:
- Traffic classes based on destination prefixes
- Traffic classes representing custom application definitions using access lists
- Traffic classes based on a static application mapping name with optional prefix lists to define destination prefixes
The traffic-class commands are used under learn list mode to simplify the automatic learning of traffic classes. Only one type of traffic-class command can be specified per learn list, and the throughput (PfR) and delay (PfR) commands are also mutually exclusive within a learn list.
The match traffic-class commands are used under PfR map configuration mode to simplify the manual configuration of traffic classes. Only one type of match traffic-class command can be specified per PfR map.
How to Configure Static Application Mapping Using Performance Routing
- Defining a Learn List to Automatically Learn Traffic Classes Using Static Application Mapping
- Manually Selecting Traffic Classes Using Static Application Mapping
- Displaying and Resetting Traffic Class and Learn List Information
Defining a Learn List to Automatically Learn Traffic Classes Using Static Application Mapping
Perform this task at the master controller to define a learn list using static application mapping. Within a learn list, a keyword that represents an application can be used to identify specific application traffic classes. The defined learn list will contain traffic classes to be automatically learned by PfR using the static application mapping. The resulting traffic classes can be filtered by a prefix list, if required.
In this task, a learn list is configured to create a traffic class using static application mapping keywords. Learn lists allow different PfR policies to be applied to each learn list. The resulting prefixes are aggregated to a prefix length of 24. A prefix list is applied to the traffic class to permit traffic from the 10.0.0.0/8 prefix. The master controller is configured to learn the top prefixes based on highest outbound throughput for the filtered traffic, and the resulting traffic class is added to the PfR application database.
The learn list is referenced in a PfR policy using a PfR map and activated using the policy-rules (PfR) command.
To display information about the configured learn lists and the traffic classes learned by PfR, use the "Displaying and Resetting Traffic Class and Learn List Information" section.
DETAILED STEPS
Example
In this example, two learn lists are configured to identify remote login traffic and file transfer traffic. The remote login traffic class is configured using keywords representing Telnet and Secure Shell (SSH) traffic, and the resulting prefixes are aggregated to a prefix length of 24. The file transfer traffic class is configured using a keyword that represents FTP and is also aggregated to a prefix length of 24. A prefix list is applied to the file transfer traffic class to permit traffic from the 10.0.0.0/8 prefix. The master controller is configured to learn the top prefixes based on highest outbound throughput for the filtered traffic, and the resulting traffic classes are added to the PfR application database. PfR maps are configured to match the learn lists and the File Transfer traffic class is activated using the policy-rules (PfR) command.
ip prefix-list INCLUDE_10_NET 10.0.0.0/8 pfr master policy-rules LL_FILE_MAP learn list seq 10 refname LEARN_REMOTE_LOGIN_TC traffic-class application telnet ssh aggregation-type prefix-length 24 throughput exit list seq 20 refname LEARN_FILE_TRANSFER_TC traffic-class application ftp filter INCLUDE_10_NET aggregation-type prefix-length 24 throughput exit exit exit pfr-map LL_REMOTE_MAP 10 match pfr learn list LEARN_REMOTE_LOGIN_TC exit pfr-map LL_FILE_MAP 20 match pfr learn list LEARN_FILE_TRANSFER_TC end
Manually Selecting Traffic Classes Using Static Application Mapping
Perform this task to manually select traffic classes using static application mapping. Use this task when you know the destination prefixes and the applications that you want to select for the traffic classes. In this task, an IP prefix list is created to define the destination prefixes, and static applications are defined using the match traffic-class application (PfR) command. Using a PfR map, each prefix is matched with each application to create the traffic classes.
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode. |
Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. |
Step 3 |
ip
prefix-list
list-name
[seq
seq-value] {deny
network/length |
permit
network/length}
Example: Router(config)# ip prefix-list LIST1 permit 10.1.1.0/24 |
Creates a prefix list to specify destination prefix-based traffic classes. |
Step 4 | Repeat Step 3 for more prefix list entries, as required.
|
-- |
Step 5 |
pfr-map
map-name
sequence-number
Example: Router(config)# pfr-map APPLICATION_MAP 10 |
Enters PfR map configuration mode to configure a PfR map. |
Step 6 |
match
traffic-class
application
application-name
prefix-list
prefix-list-name
Example: Router(config-pfr-map)# traffic-class application telnet ssh prefix-list LIST1 |
Manually configures one or more static applications as match criteria against a prefix list to create traffic classes using a PfR map.
|
Step 7 |
end
Example: Router(config-pfr-map)# end |
(Optional) Exits PfR map configuration mode and returns to privileged EXEC mode. |
Displaying and Resetting Traffic Class and Learn List Information
Perform this task to display traffic class and learn list information and optionally, to reset some traffic class information. These commands can be entered on a master controller after learn lists are configured and traffic classes are automatically learned, or when traffic classes are manually configured using a PfR map. The commands can be entered in any order and all the commands are optional.
DETAILED STEPS
| Step 1 |
enable
Enables privileged EXEC mode. Enter your password if prompted. Example:
Router> enable
|
| Step 2 |
show
pfr
master
traffic-class
[access-list
access-list-name|
application
application-name[prefix] |
inside |
learned[delay |
inside |
list
list-name|
throughput] |
prefix
prefix|
prefix-list
prefix-list-name] [active|
passive|
status] [detail]
This command is used to display information about traffic classes learned or manually configured under PfR learn list configuration mode. Example:
Router# show pfr master traffic-class
OER Prefix Statistics:
Pas - Passive, Act - Active, S - Short term, L - Long term, Dly - Delay (ms),
P - Percentage below threshold, Jit - Jitter (ms),
MOS - Mean Opinion Score
Los - Packet Loss (packets-per-million), Un - Unreachable (flows-per-million),
E - Egress, I - Ingress, Bw - Bandwidth (kbps), N - Not applicable
U - unknown, * - uncontrolled, + - control more specific, @ - active probe all
# - Prefix monitor mode is Special, & - Blackholed Prefix
% - Force Next-Hop, ^ - Prefix is denied
DstPrefix Appl_ID Dscp Prot SrcPort DstPort SrcPrefix
Flags State Time CurrBR CurrI/F Protocol
PasSDly PasLDly PasSUn PasLUn PasSLos PasLLos EBw IBw
ActSDly ActLDly ActSUn ActLUn ActSJit ActPMOS
--------------------------------------------------------------------------------
10.1.1.0/24 N defa N N N N
# OOPOLICY 32 10.11.1.3 Gi0/0/1 BGP
N N N N N N N IBwN
130 134 0 0 N N
|
| Step 3 |
show
pfr
master
learn
list
[list-name]
This command is used to display one or all of the configured PfR learn lists. In this example, the information about two learn lists is displayed. Example:
Router# show pfr master learn list
Learn-List LIST1 10
Configuration:
Application: ftp
Aggregation-type: bgp
Learn type: thruput
Policies assigned: 8 10
Stats:
Application Count: 0
Application Learned:
Learn-List LIST2 20
Configuration:
Application: telnet
Aggregation-type: prefix-length 24
Learn type: thruput
Policies assigned: 5 20
Stats:
Application Count: 2
Application Learned:
Appl Prefix 10.1.5.0/24 telnet
Appl Prefix 10.1.5.16/28 telnet
|
| Step 4 |
clear
pfr
master
traffic-class
[access-list
access-list-name|
application
application-name[prefix]|
inside |
learned[delay |
inside |
list
list-name|
throughput]|
prefix
prefix|
prefix-list
prefix-list-name]
This command is used to clear PfR controlled traffic classes from the master controller database. The following example clears traffic classes defined by the Telnet application and the 10.1.1.0/24 prefix: Example:
Router# clear pfr master traffic-class application telnet 10.1.1.0/24
|
Configuration Examples for Static Application Mapping Using Performance Routing
- Example Defining a Learn List to Automatically Learn Traffic Classes Using Static Application Mapping
- Example Defining a Learn List for Automatically Learned Prefix-Based Traffic Classes
- Example Defining a Learn List for Automatically Learned Application Traffic Classes Using an Access List
- Example Manually Selecting Traffic Classes Using Static Application Mapping
- Example Manually Selecting Prefix-Based Traffic Classes Using a Prefix List
- Example Manually Selecting Application Traffic Classes Using an Access List
Example Defining a Learn List to Automatically Learn Traffic Classes Using Static Application Mapping
The following example defines application traffic classes using static application mapping. In this example, the following two PfR learn lists are defined:
- LEARN_REMOTE_LOGIN_TC--Remote login traffic represented by Telnet and SSH.
- LEARN_FILE_TRANSFER_TC--File transfer traffic represented by FTP and filtered by the 10.0.0.0/8 prefix.
The goal is to optimize the remote login traffic using one policy (POLICY_REMOTE), and to optimize the file transfer traffic using a different policy (POLICY_FILE). This task configures traffic class learning based on the highest delay. The policy-rules (PfR) command activates the remote traffic class learn list. To activate the file transfer traffic class, replace the POLICY_REMOTE map name with the POLICY_FILE map name using the policy-rules (PfR) command.
ip prefix-list INCLUDE_10_NET 10.0.0.0/8 pfr master policy-rules POLICY_REMOTE 10 learn list seq 10 refname LEARN_REMOTE_LOGIN_TC traffic-class application telnet ssh aggregation-type prefix-length 24 delay exit list seq 20 refname LEARN_FILE_TRANSFER_TC traffic-class application ftp filter INCLUDE_10_NET aggregation-type prefix-length 24 delay exit exit pfr-map POLICY_REMOTE 10 match pfr learn list LEARN_REMOTE_LOGIN_TC exit pfr-map POLICY_FILE 20 match pfr learn list LEARN_FILE_TRANSFER_TC end
Example Defining a Learn List for Automatically Learned Prefix-Based Traffic Classes
The following example configured on the master controller, defines a learn list that will contain traffic classes that are automatically learned based only on a prefix list. In this example, there are three branch offices and the goal is to optimize all the traffic going to branch offices A and B using one policy (Policy1), and to optimize traffic going to branch office C using a different policy (Policy2).
Branch A is defined as any prefix that matches 10.1.0.0./16, Branch B is defined as any prefix that matches 10.2.0.0./16, and Branch C is defined as any prefix that matches 10.3.0.0./16.
This task configures prefix learning based on the highest outbound throughput. The policy-rules (PfR) command activates the traffic class learn list configured for branch offices A and B.
ip prefix-list BRANCH_A_B permit seq 10 10.1.0.0/16 ip prefix-list BRANCH_A_B permit seq 20 10.2.0.0/16 ip prefix-list BRANCH_C permit seq 30 10.3.0.0/16 pfr master policy-rules POLICY1 learn list seq 10 refname LEARN_BRANCH_A_B traffic-class prefix-list BRANCH_A_B throughput exit list seq 20 refname LEARN_BRANCH_C traffic-class prefix-list BRANCH_C throughput exit exit exit pfr-map POLICY1 10 match pfr learn list LEARN_BRANCH_A_B exit pfr-map POLICY2 10 match pfr learn list LEARN_BRANCH_C end
Example Defining a Learn List for Automatically Learned Application Traffic Classes Using an Access List
The following example creates an access list that defines custom application traffic classes. In this example, the custom application consists of four criteria:
- Any TCP traffic on destination port 500
- Any TCP traffic on ports in the range from 700 to 750
- Any UDP traffic on source port 400
- Any IP packet marked with a DSCP bit of ef
The goal is to optimize the custom application traffic using a learn list that is referenced in a PfR policy named POLICY_CUSTOM_APP. This task configures traffic class learning based on the highest outbound throughput. The policy-rules (PfR) command activates the custom application traffic class learn list.
ip access-list extended USER_DEFINED_TC permit tcp any any 500 permit tcp any any range 700 750 permit udp any eq 400 any permit ip any any dscp ef exit pfr master policy-rules POLICY_CUSTOM_APP learn list seq 10 refname CUSTOM_APPLICATION_TC traffic-class access-list USER_DEFINED_TC aggregation-type prefix-length 24 throughput exit exit exit pfr-map POLICY_CUSTOM_APP 10 match pfr learn list CUSTOM_APPLICATION_TC end
Example Manually Selecting Traffic Classes Using Static Application Mapping
The following example starting in global configuration mode, configures a PfR map to include application traffic predefined as telnet or Secure Shell and destined to prefixes in the 10.1.1.0/24 network, 10.1.2.0/24 network, and 172.16.1.0/24 network.
ip prefix-list LIST1 permit 10.1.1.0/24 ip prefix-list LIST1 permit 10.1.2.0/24 ip prefix-list LIST1 permit 172.16.1.0/24 pfr-map PREFIXES 10 match traffic-class application telnet ssh prefix-list LIST1 end
Example Manually Selecting Prefix-Based Traffic Classes Using a Prefix List
The following example configured on the master controller, manually selects traffic classes based only on destination prefixes. Use this task when you know the destination prefixes that you want to select for the traffic classes. An IP prefix list is created to define the destination prefixes and using a PfR map, the traffic classes are profiled.
ip prefix-list PREFIX_TC permit 10.1.1.0/24 ip prefix-list PREFIX_TC permit 10.1.2.0/24 ip prefix-list PREFIX_TC permit 172.16.1.0/24 pfr-map PREFIX_MAP 10 match traffic-class prefix-list PREFIX_TC end
Example Manually Selecting Application Traffic Classes Using an Access List
The following example configured on the master controller, manually selects traffic classes using an access list. Each access list entry is a traffic class that must include a destination prefix and may include other optional parameters.
ip access-list extended ACCESS_TC permit tcp any 10.1.1.0 0.0.0.255 eq 500 permit tcp any 172.17.1.0 0.0.255.255 eq 500 permit tcp any 172.17.1.0 0.0.255.255 range 700 750 permit tcp 192.168.1.1 0.0.0.0 10.1.2.0 0.0.0.255 eq 800any any dscp ef exit pfr-map ACCESS_MAP 10 match traffic-class access-list ACCESS_TC
Where To Go Next
For information about other Performance Routing features or general conceptual material, see the documents in the "Related Documents" section.
Additional References
Related Documents
|
Related Topic |
Document Title |
|---|---|
|
Cisco IOS commands |
|
|
Cisco PfR commands: complete command syntax, command mode, command history, defaults, usage guidelines and examples |
|
|
Basic PfR configuration |
"Configuring Basic Performance Routing" module |
|
Concepts required to understand the Performance Routing operational phases |
"Understanding Performance Routing" module |
|
Advanced PfR configuration |
"Configuring Advanced Performance Routing" module |
|
IP SLAs overview |
IP SLAs Configuration Guide |
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for Static Application Mapping Using Performance Routing
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 2 | Feature Information for Static Application Mapping Using Performance Routing |
|
Feature Name |
Releases |
Feature Configuration Information |
|---|---|---|
|
OER - Application Aware Routing with Static Application Mapping |
12.4(15)T |
The OER - Application Aware Routing with Static Application Mapping feature introduces the ability to configure standard applications using just one keyword. This feature also introduces a learn list configuration mode that allows Performance Routing (PfR) policies to be applied to traffic classes profiled in a learn list. Different policies can be applied to each learn list. New traffic-class and match traffic-class commands are introduced to simplify the configuration of traffic classes that PfR can automatically learn, or that can be manually configured. The following commands were introduced or modified by this feature: clear pfr master traffic-class, count (PfR), delay (PfR),list (PfR), match traffic-class access-list (PfR), match traffic-class application (PfR), match traffic-class prefix-list (PfR), show pfr border defined application, show pfr master defined application, show pfr master learn list, show pfr master traffic-class, throughput (PfR), traffic-class access-list (PfR), traffic-class application (PfR), traffic-class prefix-list (PfR). |
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.

 Feedback
Feedback