對方形拓撲中採用CloudSec的多站點VXLAN進行故障排除
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本檔案介紹以方形拓撲連線的邊界網關之間的VXLAN多站點配置和CloudSec故障排除。
必要條件
需求
思科建議您熟悉以下主題:
- Nexus NXOS軟©版本。
- VXLAN EVPN技術。
- BGP和OSPF路由協定。
採用元件
本檔案中的資訊是根據以下軟體和硬體版本:
- Cisco Nexus 9000。
- NXOS 10.3(4a)版。
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
設定
網路圖表
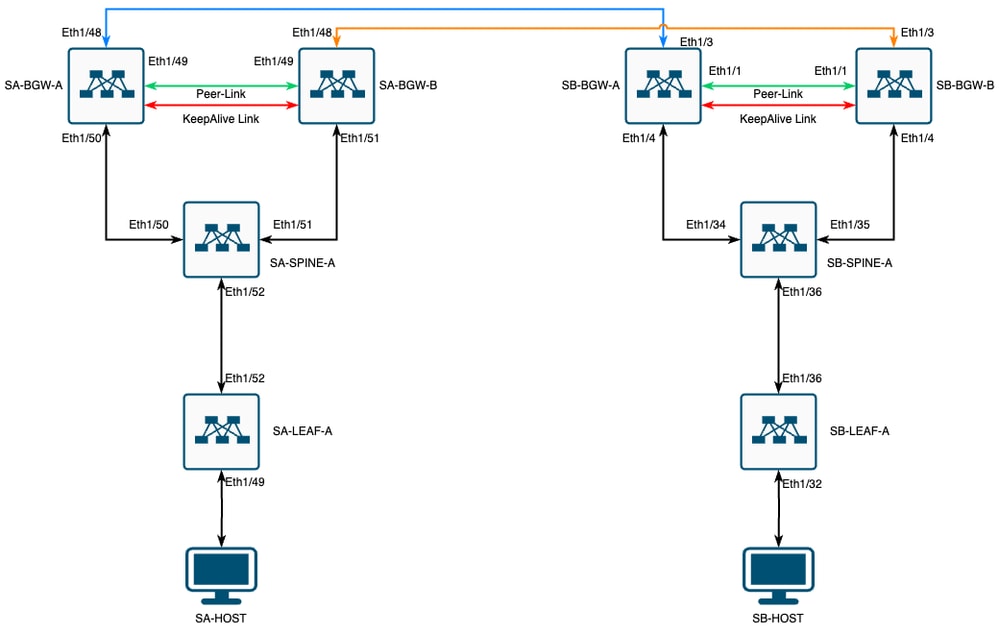 VXLAN MultiSite,採用方形拓撲的CloudSec
VXLAN MultiSite,採用方形拓撲的CloudSec
拓撲詳細資訊
- 兩站點多站點VXLAN EVPN交換矩陣。
- 兩個站點都配置了vPC邊界網關。
- 終端在VLAN 1100中託管。
- 每個站點上的邊界網關通過SVI介面Vlan3600相互之間具有IPv4 iBGP鄰居關係。
- 一個站點上的邊界網關僅與另一個站點上的直接連線的邊界網關具有eBGP IPv4鄰居關係。
- 站點A的邊界網關與站點B的邊界網關具有eBGP L2VPN EVPN鄰居關係。
編址計畫
表中的IP地址在配置期間使用:
| 站點A | 站點B | |||||||||||
| 裝置角色 | 介面ID | 實體整合IP | RID環路IP | NVE回圈IP | MSITE-VIP | 備份SVI IP | 介面ID | 實體整合IP | RID環路IP | NVE回圈IP | MSITE-VIP | 備份SVI IP |
| 葉 | Eth1/52 | 192.168.1.1/30 | 192.168.2.1/32 | 192.168.3.1/32 | 不適用 | 不適用 | Eth1/36 | 192.168.11.1/30 | 192.168.12.1/32 | 192.168.13.1/32 | 不適用 | 不適用 |
| 骨幹 | Eth1/52 | 192.168.1.2/30 | 不適用 | Eth1/36 | 192.168.11.2/30 | 不適用 | ||||||
| Eth1/50 | 192.168.1.5/30 | 192.168.2.2/32 | 不適用 | 不適用 | 不適用 | Eth1/34 | 192.168.11.5/30 | 192.168.12.2/32 | 不適用 | 不適用 | 不適用 | |
| Eth1/51 | 192.168.1.9/30 | 不適用 | Eth1/35 | 192.168.11.9/30 | 不適用 | |||||||
| BGW-A | Eth1/51 | 192.168.1.6/30 | 192.168.2.3/32 | 192.168.3.2/32 | 192.168.100.1/32 | 192.168.4.1/30 | Eth1/4 | 192.168.11.6/30 | 192.168.12.3/32 | 192.168.13.2/32 | 192.168.200.1/32 | 192.168.14.1/30 |
| Eth1/48 | 10.12.10.1/30 | 192.168.3.254/32 | Eth1/3 | 10.12.10.2/30 | 192.168.13.254/32 | |||||||
| BGW-B | Eth1/51 | 192.168.1.10/30 | 192.168.2.4/32 | 192.168.3.3/32 | 192.168.100.1/32 | 192.168.4.2/30 | Eth1/4 | 192.168.11.10/30 | 192.168.12.4/32 | 192.168.13.3/32 | 192.168.200.1/32 | 192.168.14.2/30 |
| Eth1/48 | 10.12.10.5/30 | 192.168.3.254/32 | Eth1/3 | 10.12.10.6/30 | 192.168.13.254/32 |
組態
- 請注意,本指南中僅顯示多站點相關的配置。對於完整配置,您可以使用Cisco VXLAN官方文檔指南Cisco Nexus 9000系列NX-OS VXLAN配置指南10.3(x)版
為了啟用CloudSec,dci-advertise-pip 命令必須在evpn multisite border-gateway下配置:
| SA-BGW-A和SA-BGW-B | SB-BGW-A和SB-BGW-B |
|
|
BGP配置
此配置特定於站點。
| SA-BGW-A和SA-BGW-B | SB-BGW-A和SB-BGW-B |
|
|
- maximum-path 命令允許從鄰居接收多個eBGP L2VPN EVPN路徑。
- additional-path命令指示BGP進程通告裝置能夠傳送/接收其他路徑
對於邊界網關上的所有L3VNI VRF,還必須配置多路徑:
| SA-BGW-A和SA-BGW-B | SB-BGW-A和SB-BGW-B |
|
|
隧道加密配置
所有邊界網關上的此配置必須相同:
key chain CloudSec_Key_Chain1 tunnel-encryption
key 1000
key-octet-string Cl0udSec! cryptographic-algorithm AES_128_CMAC
feature tunnel-encryption
tunnel-encryption must-secure-policy
tunnel-encryption source-interface loopback0
tunnel-encryption policy CloudSec_Policy1此配置特定於站點。tunnel-encryption命令只能應用於具有命令的接evpn multisite dci-tracking口。
| SA-BGW-A和SA-BGW-B | SB-BGW-A和SB-BGW-B |
|
|
啟用通道加密後,向本地環回新增其他屬性,同時向鄰居通告路由,所有eBGP IPv4單播鄰居都必須看到此屬性:
SA-BGW-A# show ip bgp 192.168.2.3
BGP routing table information for VRF default, address family IPv4 Unicast
BGP routing table entry for 192.168.2.3/32, version 1320
Paths: (2 available, best #1)
Flags: (0x000002) (high32 00000000) on xmit-list, is not in urib
Multipath: eBGP iBGP
Advertised path-id 1
Path type: local, path is valid, is best path, no labeled nexthop
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (192.168.2.3)
Origin IGP, MED not set, localpref 100, weight 32768
Tunnel Encapsulation attribute: Length 152 !---This is a new attribute
Path type: redist, path is valid, not best reason: Locally originated, no labeled nexthop
AS-Path: NONE, path locally originated
0.0.0.0 (metric 0) from 0.0.0.0 (192.168.2.3)
Origin incomplete, MED 0, localpref 100, weight 32768
Path-id 1 advertised to peers:
10.12.10.2 192.168.4.2
SA-BGW-A# 對於Route Type-2,還有一個新屬性:
SA-BGW-A# show bgp l2vpn evpn 00ea.bd27.86ef
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 65002:31100
BGP routing table entry for [2]:[0]:[0]:[48]:[00ea.bd27.86ef]:[0]:[0.0.0.0]/216, version 7092
Paths: (2 available, best #2)
Flags: (0x000202) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Multipath: eBGP iBGP
Path type: external, path is valid, not best reason: Router Id, multipath, no labeled nexthop
Imported to 1 destination(s)
Imported paths list: L2-31100
AS-Path: 65002 , path sourced external to AS
192.168.13.3 (metric 0) from 192.168.12.4 (192.168.12.4)
Origin IGP, MED 2000, localpref 100, weight 0
Received label 31100
Received path-id 1
Extcommunity: RT:65001:31100 ENCAP:8
ESI: 0300.0000.00fd.ea00.0309
Advertised path-id 1
Path type: external, path is valid, is best path, no labeled nexthop
Imported to 1 destination(s)
Imported paths list: L2-31100
AS-Path: 65002 , path sourced external to AS
192.168.13.2 (metric 0) from 192.168.12.3 (192.168.12.3)
Origin IGP, MED 2000, localpref 100, weight 0
Received label 31100
Received path-id 1
Extcommunity: RT:65001:31100 ENCAP:8
ESI: 0300.0000.00fd.ea00.0309
Path-id 1 not advertised to any peer
Route Distinguisher: 192.168.2.3:33867 (L2VNI 31100)
BGP routing table entry for [2]:[0]:[0]:[48]:[00ea.bd27.86ef]:[0]:[0.0.0.0]/216, version 7112
Paths: (2 available, best #1)
Flags: (0x000212) (high32 0x000400) on xmit-list, is in l2rib/evpn, is not in HW
Multipath: eBGP iBGP
Advertised path-id 1
Path type: external, path is valid, is best path, no labeled nexthop, in rib
Imported from 65002:31100:[2]:[0]:[0]:[48]:[00ea.bd27.86ef]:[0]:[0.0.0.0]/216
AS-Path: 65002 , path sourced external to AS
192.168.13.2 (metric 0) from 192.168.12.3 (192.168.12.3)
Origin IGP, MED 2000, localpref 100, weight 0
Received label 31100
Received path-id 1
Extcommunity: RT:65001:31100 ENCAP:8
ESI: 0300.0000.00fd.ea00.0309
Path type: external, path is valid, not best reason: Router Id, multipath, no labeled nexthop, in rib
Imported from 65002:31100:[2]:[0]:[0]:[48]:[00ea.bd27.86ef]:[0]:[0.0.0.0]/216
AS-Path: 65002 , path sourced external to AS
192.168.13.3 (metric 0) from 192.168.12.4 (192.168.12.4)
Origin IGP, MED 2000, localpref 100, weight 0
Received label 31100
Received path-id 1
Extcommunity: RT:65001:31100 ENCAP:8
ESI: 0300.0000.00fd.ea00.0309 !---Ethernet Segment Identifier (ESI) is also new attribute
Path-id 1 (dual) advertised to peers:
192.168.2.2
SA-BGW-A# 驗證
啟用cloudsec之前,最好檢查沒有它的設定是否工作正常:
SA-BGW-A(config)# show clock
Warning: No NTP peer/server configured. Time may be out of sync.
10:02:01.016 UTC Fri Jul 19 2024
Time source is NTP
SA-BGW-A(config)# show tunnel-encryption session
Tunnel-Encryption Peer Policy Keychain RxStatus TxStatus
------------------------ ---------------------------------------- ---------------------------------------- ----------------- -----------------
===============================================
SA-HOST-A# show clock
Warning: No NTP peer/server configured. Time may be out of sync.
10:02:21.592 UTC Fri Jul 19 2024
Time source is NTP
SA-HOST-A# ping 10.100.20.10 count unlimited interval 1
PING 10.100.20.10 (10.100.20.10): 56 data bytes
64 bytes from 10.100.20.10: icmp_seq=0 ttl=254 time=1.583 ms
64 bytes from 10.100.20.10: icmp_seq=1 ttl=254 time=10.407 ms
64 bytes from 10.100.20.10: icmp_seq=2 ttl=254 time=1.37 ms
64 bytes from 10.100.20.10: icmp_seq=3 ttl=254 time=1.489 ms
64 bytes from 10.100.20.10: icmp_seq=4 ttl=254 time=6.685 ms
64 bytes from 10.100.20.10: icmp_seq=5 ttl=254 time=1.547 ms
64 bytes from 10.100.20.10: icmp_seq=6 ttl=254 time=1.859 ms
64 bytes from 10.100.20.10: icmp_seq=7 ttl=254 time=5.219 ms
64 bytes from 10.100.20.10: icmp_seq=8 ttl=254 time=1.337 ms
64 bytes from 10.100.20.10: icmp_seq=9 ttl=254 time=3.528 ms
64 bytes from 10.100.20.10: icmp_seq=10 ttl=254 time=4.057 ms同樣在cloudsec配置之後,SA上的終結點必須成功ping站點B上的終結點。但是,在某些情況下,ping可能會失敗。取決於本地裝置選擇哪個cloudsec對等體傳送cloudsec加密流量。
SA-HOST-A# ping 10.100.20.10
PING 10.100.20.10 (10.100.20.10): 56 data bytes
Request 0 timed out
Request 1 timed out
Request 2 timed out
Request 3 timed out
Request 4 timed out
--- 10.100.20.10 ping statistics ---
5 packets transmitted, 0 packets received, 100.00% packet loss
SA-HOST-A# 疑難排解
檢查源端點上的本地ARP表:
SA-HOST-A# ping 10.100.20.10 count unlimited interval 1
Request 352 timed out
Request 353 timed out
Request 354 timed out
356 packets transmitted, 0 packets received, 100.00% packet loss
SA-HOST-A# clear ip arp delete-force
SA-HOST-A# show ip arp
Flags: * - Adjacencies learnt on non-active FHRP router
+ - Adjacencies synced via CFSoE
# - Adjacencies Throttled for Glean
CP - Added via L2RIB, Control plane Adjacencies
PS - Added via L2RIB, Peer Sync
RO - Re-Originated Peer Sync Entry
D - Static Adjacencies attached to down interface
IP ARP Table for context default
Total number of entries: 1
Address Age MAC Address Interface Flags
10.100.20.10 00:00:02 00ea.bd27.86ef Vlan1100
SA-HOST-A# 此輸出證明BUM流量正在通過,而控制平面正在工作。下一步是檢查通道加密狀態:
SA-BGW-A# show tunnel-encryption session
Tunnel-Encryption Peer Policy Keychain RxStatus TxStatus
------------------------ ---------------------------------------- ---------------------------------------- ----------------- -----------------
192.168.13.2 CloudSec_Policy1 CloudSec_Key_Chain1 Secure (AN: 0) Secure (AN: 0)
192.168.13.3 CloudSec_Policy1 CloudSec_Key_Chain1 Secure (AN: 0) Secure (AN: 0)
SA-BGW-A# 此輸出顯示CloudSec會話已建立。下一步,您可以在SA-HOST-A上運行無限制的ping:
SA-HOST-A# ping 10.100.20.10 count unlimited interval 1從此以後,您必須檢查站點A上的裝置,檢視流量是否到達此裝置。您可以在站點A上路徑沿途的所有裝置上使用ELAM完成此任務。將預設值in-select 從6更改為9可以基於內部報頭進行匹配。您可以在此連結上閱讀有關ELAM的更多資訊:Nexus 9000雲規模ASIC(Tahoe)NX-OS ELAM。
SA-LEAF-A上的ELAM
在生產網路中存在多個SPINE裝置。要瞭解將流量傳送到哪個骨幹,必須首先在LEAF上獲取ELAM。儘管使用in-select 9了此功能,但在連線到源的LEAF上,必須使用外部ipv4標頭,因為到達此LEAF的流量未進行VXLAN加密。在真實網路中,很難捕獲您生成的確切資料包。在這種情況下,您可以運行具有特定長度的ping,並使用Pkt len報頭來識別您的資料包。預設情況下,icmp資料包的長度為64位元組。加上20位元組的IP報頭,總而言之,為您提供了84位元組的PKT Len:
SA-LEAF-A# debug platform internal tah elam
SA-LEAF-A(TAH-elam)# trigger init in-select 9
Slot 1: param values: start asic 0, start slice 0, lu-a2d 1, in-select 9, out-select 0
SA-LEAF-A(TAH-elam-insel9)# set outer ipv4 src_ip 10.100.10.10 dst_ip 10.100.20.10
SA-LEAF-A(TAH-elam-insel9)# start
SA-LEAF-A(TAH-elam-insel9)# report
ELAM not triggered yet on slot - 1, asic - 0, slice - 0
SUGARBOWL ELAM REPORT SUMMARY
slot - 1, asic - 0, slice - 1
============================
Incoming Interface: Eth1/49
Src Idx : 0xc1, Src BD : 1100
Outgoing Interface Info: dmod 1, dpid 64 !---Note dpid value
Dst Idx : 0xcd, Dst BD : 1100
Packet Type: IPv4
Outer Dst IPv4 address: 10.100.20.10
Outer Src IPv4 address: 10.100.10.10
Ver = 4, DSCP = 0, Don't Fragment = 0
Proto = 1, TTL = 255, More Fragments = 0
Hdr len = 20, Pkt len = 84, Checksum = 0xb4ae !---64 byte + 20 byte IP header Pkt len = 84
Inner Payload
Type: CE
L4 Protocol : 1
L4 info not available
Drop Info:
----------
LUA:
LUB:
LUC:
LUD:
Final Drops:
SA-LEAF-A(TAH-elam-insel9)# show system internal ethpm info all | i i "dpid=64" !---Put dpid value here
IF_STATIC_INFO: port_name=Ethernet1/52,if_index:0x1a006600,ltl=5940,slot=0, nxos_port=204,dmod=1,dpid=64,unit=0,queue=65535,xbar_unitbmp=0x0,ns_pid=255,slice_num=1,port_on_slice=24,src_id=48
SA-LEAF-A(TAH-elam-insel9)# show cdp neighbors interface ethernet 1/52
Capability Codes: R - Router, T - Trans-Bridge, B - Source-Route-Bridge
S - Switch, H - Host, I - IGMP, r - Repeater,
V - VoIP-Phone, D - Remotely-Managed-Device,
s - Supports-STP-Dispute
Device-ID Local Intrfce Hldtme Capability Platform Port ID
SA-SPINE-A(FDO242210CS)
Eth1/52 130 R S s N9K-C93240YC-FX2 Eth1/52
Total entries displayed: 1
SA-LEAF-A(TAH-elam-insel9)# 從該輸出中,您可以看到流量到達SA-LEAF-A並從介面Ethernet1/52轉發出去,該介面從拓撲連線到SA-SPINE-A。
SA-SPINE-A上的ELAM
在SPINE上,Pkt Len值將更多,因為50位元組的VXLAN標頭也增加了。預設情況下,SPINE無法匹配沒有或的內部vxlan-parse標feature nv overlay頭。因此,必須在SPINEvxlan-parse enable上使用命令:
SA-SPINE-A(config-if)# debug platform internal tah elam
SA-SPINE-A(TAH-elam)# trigger init in-select 9
Slot 1: param values: start asic 0, start slice 0, lu-a2d 1, in-select 9, out-select 0
SA-SPINE-A(TAH-elam)# vxlan-parse enable
SA-SPINE-A(TAH-elam-insel9)# set inner ipv4 src_ip 10.100.10.10 dst_ip 10.100.20.10
SA-SPINE-A(TAH-elam-insel9)# start
SA-SPINE-A(TAH-elam-insel9)# report
ELAM not triggered yet on slot - 1, asic - 0, slice - 0
HEAVENLY ELAM REPORT SUMMARY
slot - 1, asic - 0, slice - 1
============================
Incoming Interface: Eth1/52
Src Idx : 0xcd, Src BD : 4153
Outgoing Interface Info: dmod 1, dpid 72
Dst Idx : 0xc5, Dst BD : 4151
Packet Type: IPv4
Outer Dst IPv4 address: 192.168.100.1
Outer Src IPv4 address: 192.168.3.1
Ver = 4, DSCP = 0, Don't Fragment = 0
Proto = 17, TTL = 255, More Fragments = 0
Hdr len = 20, Pkt len = 134, Checksum = 0x7d69 !---84 bytes + 50 bytes VXLAN header Pkt len = 134
Inner Payload
Type: IPv4
Inner Dst IPv4 address: 10.100.20.10
Inner Src IPv4 address: 10.100.10.10
L4 Protocol : 17
L4 info not available
Drop Info:
----------
LUA:
LUB:
LUC:
LUD:
Final Drops:
SA-SPINE-A(TAH-elam-insel9)# show system internal ethpm info all | i i "dpid=72"
IF_STATIC_INFO: port_name=Ethernet1/50,if_index:0x1a006200,ltl=5948,slot=0, nxos_port=196,dmod=1,dpid=72,unit=0,queue=65535,xbar_unitbmp=0x0,ns_pid=255,slice_num=1,port_on_slice=0,src_id=0
SA-SPINE-A(TAH-elam-insel9)# show cdp neighbors interface ethernet 1/50
Capability Codes: R - Router, T - Trans-Bridge, B - Source-Route-Bridge
S - Switch, H - Host, I - IGMP, r - Repeater,
V - VoIP-Phone, D - Remotely-Managed-Device,
s - Supports-STP-Dispute
Device-ID Local Intrfce Hldtme Capability Platform Port ID
SA-BGW-A(FDO242210CX)
Eth1/50 169 R S s N9K-C93240YC-FX2 Eth1/50
Total entries displayed: 1
SA-SPINE-A(TAH-elam-insel9)# SA-SPINE-A根據輸出向SA-BGW-A傳送流量。
SA-BGW-A上的ELAM
SA-BGW-A(TAH-elam-insel9)# set inner ipv4 src_ip 10.100.10.10 dst_ip 10.100.20.10
SA-BGW-A(TAH-elam-insel9)# start
SA-BGW-A(TAH-elam-insel9)# report
ELAM not triggered yet on slot - 1, asic - 0, slice - 0
HEAVENLY ELAM REPORT SUMMARY
slot - 1, asic - 0, slice - 1
============================
Incoming Interface: Eth1/50
Src Idx : 0xc5, Src BD : 1100
Outgoing Interface Info: dmod 1, dpid 48
Dst Idx : 0xbd, Dst BD : 1100
Packet Type: IPv4
Outer Dst IPv4 address: 192.168.100.1
Outer Src IPv4 address: 192.168.3.1
Ver = 4, DSCP = 0, Don't Fragment = 0
Proto = 17, TTL = 254, More Fragments = 0
Hdr len = 20, Pkt len = 134, Checksum = 0x7e69
Inner Payload
Type: IPv4
Inner Dst IPv4 address: 10.100.20.10
Inner Src IPv4 address: 10.100.10.10
L4 Protocol : 17
L4 info not available
Drop Info:
----------
LUA:
LUB:
LUC:
LUD:
Final Drops:
SA-BGW-A(TAH-elam-insel9)# show system internal ethpm info all | i i "dpid=48"
IF_STATIC_INFO: port_name=Ethernet1/48,if_index:0x1a005e00,ltl=5956,slot=0, nxos_port=188,dmod=1,dpid=48,unit=0,queue=65535,xbar_unitbmp=0x0,ns_pid=255,slice_num=0,port_on_slice=48,src_id=96
SA-BGW-A(TAH-elam-insel9)# show cdp neighbors interface ethernet 1/48
Capability Codes: R - Router, T - Trans-Bridge, B - Source-Route-Bridge
S - Switch, H - Host, I - IGMP, r - Repeater,
V - VoIP-Phone, D - Remotely-Managed-Device,
s - Supports-STP-Dispute
Device-ID Local Intrfce Hldtme Capability Platform Port ID
SB-BGW-A(FDO2452070B)
Eth1/48 122 R S s N9K-C93216TC-FX2 Eth1/3
Total entries displayed: 1
SA-BGW-A(TAH-elam-insel9)# 根據SA-BGW-A的輸出,流量從Ethernet1/48流向SB-BGW-A。下一步是檢查SB-BGW-A:
SB-BGW-A# debug platform internal tah elam
SB-BGW-A(TAH-elam)# trigger init in-select 9
Slot 1: param values: start asic 0, start slice 0, lu-a2d 1, in-select 9, out-select 0
SB-BGW-A(TAH-elam-insel9)# set inner ipv4 src_ip 10.100.10.10 dst_ip 10.100.20.10
SB-BGW-A(TAH-elam-insel9)# start
SB-BGW-A(TAH-elam-insel9)# report
ELAM not triggered yet on slot - 1, asic - 0, slice - 0
ELAM not triggered yet on slot - 1, asic - 0, slice - 1
!---Reset the previous filter and start again just in case if packet was not captured.
SB-BGW-A(TAH-elam-insel9)# reset
SB-BGW-A(TAH-elam-insel9)# set inner ipv4 src_ip 10.100.10.10 dst_ip 10.100.20.10
SB-BGW-A(TAH-elam-insel9)# start
SB-BGW-A(TAH-elam-insel9)# report
ELAM not triggered yet on slot - 1, asic - 0, slice - 0
ELAM not triggered yet on slot - 1, asic - 0, slice - 1
SB-BGW-A(TAH-elam-insel9)# 根據SB-BGW-A的輸出,ELAM甚至沒有被觸發。這意味著SB-BGW-B正在接收資料包,無法正確解密和解析這些資料包,或者根本無法接收這些資料包。要瞭解cloudsec流量發生了什麼情況,可以再次在SB-BGW-A上運行ELAM,但必須將觸發過濾器設定為用於cloudsec的外部IP地址,因為無法檢視cloudsec加密傳輸資料包的內部報頭。從之前的輸出中,您知道SA-BGW-A處理了流量,這意味著SA-BGW-A使用cloudsec加密流量。因此,您可以使用SA-BGW-A的NVE IP作為ELAM的觸發過濾器。根據前面的輸出,VXLAN加密的ICMP封包長度為134位元組。加上32位元組摘要中的cloudsec標頭,您得到166位元組:
SB-BGW-A(TAH-elam-insel9)# reset SB-BGW-A(TAH-elam-insel9)# set outer ipv4 src_ip 192.168.3.2 SB-BGW-A(TAH-elam-insel9)# start SB-BGW-A(TAH-elam-insel9)# report ELAM not triggered yet on slot - 1, asic - 0, slice - 0 HEAVENLY ELAM REPORT SUMMARY slot - 1, asic - 0, slice - 1 ============================ Incoming Interface: Eth1/3 Src Idx : 0x9, Src BD : 4108 Outgoing Interface Info: dmod 1, dpid 130 Dst Idx : 0xd, Dst BD : 4109 Packet Type: IPv4 Outer Dst IPv4 address: 192.168.13.3 !---NVE IP address of SB-BGW-B Outer Src IPv4 address: 192.168.3.2 Ver = 4, DSCP = 0, Don't Fragment = 0 Proto = 17, TTL = 254, More Fragments = 0 Hdr len = 20, Pkt len = 166, Checksum = 0xd546 !---134 byte VXLAN packet + 32 byte cloudsec header Pkt len = 166 Inner Payload Type: CE L4 Protocol : 17 L4 info not available Drop Info: ---------- LUA: LUB: LUC: LUD: Final Drops: !---To reach SB-BGW-B NVE IP traffic was sent out of Ethernet1/4 which is connected to SB-SPINE-A SB-BGW-A(TAH-elam-insel9)# show system internal ethpm info all | i i "dpid=130" IF_STATIC_INFO: port_name=Ethernet1/4,if_index:0x1a000600,ltl=6132,slot=0, nxos_port=12,dmod=1,dpid=130,unit=0,queue=65535,xbar_unitbmp=0x0,ns_pid=255,slice_num=1,port_on_slice=58,src_id=116SB-BGW-A(TAH-elam-insel9)# show cdp neighbors interface ethernet 1/4 Capability Codes: R - Router, T - Trans-Bridge, B - Source-Route-Bridge S - Switch, H - Host, I - IGMP, r - Repeater, V - VoIP-Phone, D - Remotely-Managed-Device, s - Supports-STP-Dispute Device-ID Local Intrfce Hldtme Capability Platform Port ID SB-SPINE-A(FDO22302CJ0) Eth1/4 131 R S s N9K-C9236C Eth1/34 Total entries displayed: 1 SB-BGW-A(TAH-elam-insel9)# show ip route 192.168.13.3 IP Route Table for VRF "default" '*' denotes best ucast next-hop '**' denotes best mcast next-hop '[x/y]' denotes [preference/metric] '%' in via output denotes VRF 192.168.13.3/32, ubest/mbest: 1/0 *via 192.168.11.5, Eth1/4, [110/6], 00:56:13, ospf-UNDERLAY, intra via 192.168.14.2, [200/0], 01:13:46, bgp-65002, internal, tag 65002 !---The device still have a route for SB-BGW-B NVE IP via SVI
SB-BGW-A(TAH-elam-insel9)# show ip route 192.168.14.2 IP Route Table for VRF "default" '*' denotes best ucast next-hop '**' denotes best mcast next-hop '[x/y]' denotes [preference/metric] '%' in via output denotes VRF 192.168.14.2/32, ubest/mbest: 1/0, attached *via 192.168.14.2, Vlan3600, [250/0], 01:15:05, am SB-BGW-A(TAH-elam-insel9)# show ip arp 192.168.14.2 Flags: * - Adjacencies learnt on non-active FHRP router + - Adjacencies synced via CFSoE # - Adjacencies Throttled for Glean CP - Added via L2RIB, Control plane Adjacencies PS - Added via L2RIB, Peer Sync RO - Re-Originated Peer Sync Entry D - Static Adjacencies attached to down interface IP ARP Table Total number of entries: 1 Address Age MAC Address Interface Flags 192.168.14.2 00:00:13 ecce.1324.c803 Vlan3600 SB-BGW-A(TAH-elam-insel9)# show mac address-table address ecce.1324.c803 Legend: * - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC age - seconds since last seen,+ - primary entry using vPC Peer-Link, (T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan, (NA)- Not Applicable VLAN MAC Address Type age Secure NTFY Ports ---------+-----------------+--------+---------+------+----+------------------ G 3600 ecce.1324.c803 static - F F vPC Peer-Link(R) SB-BGW-A(TAH-elam-insel9)#
從該輸出中,您可以看到cloudsec流量根據路由表通過介面Ethernet1/4轉發到SB-BGW-B。根據Cisco Nexus 9000系列NX-OS VXLAN配置指南,版本10.3(x)指導和限制:
-
目的地為交換器的CloudSec流量必須透過DCI上行鏈路進入交換器。
根據同一指南的vPC Border Gateway Support for Cloudsec部分,如果vPC BGW學習對等vPC BGW的PIP地址並在DCI端通告,則來自兩個vPC BGW的BGP路徑屬性將相同。因此,DCI中間節點最終可以從不擁有PIP地址的vPC BGW中選擇路徑。在此案例中,MCT連結用於來自遠端站點的加密流量。但是在這種情況下,使用的是指向SPINE的介面,儘管如此,BGW也通過BackUp SVI具有OSPF鄰接關係。
SB-BGW-A(TAH-elam-insel9)# show ip ospf neighbors
OSPF Process ID UNDERLAY VRF default
Total number of neighbors: 2
Neighbor ID Pri State Up Time Address Interface
192.168.12.4 1 FULL/ - 01:33:11 192.168.14.2 Vlan3600
192.168.12.2 1 FULL/ - 01:33:12 192.168.11.5 Eth1/4
SB-BGW-A(TAH-elam-insel9)#問題的原因和修復
原因是SVI介面的OSPF開銷。預設情況下,在NXOS上,自動成本參考頻寬為40G。SVI介面的頻寬為1Gbps,而物理介面的頻寬為10Gbps:
SB-BGW-A(TAH-elam-insel9)# show ip ospf interface brief
OSPF Process ID UNDERLAY VRF default
Total number of interface: 5
Interface ID Area Cost State Neighbors Status
Vlan3600 3 0.0.0.0 40 P2P 1 up
Eth1/4 5 0.0.0.0 1 P2P 1 up 在這種情況下,對SVI的成本進行管理更改可以解決此問題。必須在所有邊界網關上完成調整。
SB-BGW-A(config)# int vlan 3600 SB-BGW-A(config-if)# ip ospf cost 1 SB-BGW-A(config-if)# sh ip route 192.168.13.3 IP Route Table for VRF "default" '*' denotes best ucast next-hop '**' denotes best mcast next-hop '[x/y]' denotes [preference/metric] '%' in via output denotes VRF 192.168.13.3/32, ubest/mbest: 1/0 *via 192.168.14.2, Vlan3600, [110/2], 00:00:08, ospf-UNDERLAY, intra via 192.168.14.2, [200/0], 01:34:07, bgp-65002, internal, tag 65002 SB-BGW-A(config-if)#
!---The ping is started to work immediatelyRequest 1204 timed out Request 1205 timed out Request 1206 timed out 64 bytes from 10.100.20.10: icmp_seq=1207 ttl=254 time=1.476 ms 64 bytes from 10.100.20.10: icmp_seq=1208 ttl=254 time=5.371 ms 64 bytes from 10.100.20.10: icmp_seq=1209 ttl=254 time=5.972 ms 64 bytes from 10.100.20.10: icmp_seq=1210 ttl=254 time=1.466 ms 64 bytes from 10.100.20.10: icmp_seq=1211 ttl=254 time=2.972 ms 64 bytes from 10.100.20.10: icmp_seq=1212 ttl=254 time=4.582 ms 64 bytes from 10.100.20.10: icmp_seq=1213 ttl=254 time=1.434 ms 64 bytes from 10.100.20.10: icmp_seq=1214 ttl=254 time=4.486 ms 64 bytes from 10.100.20.10: icmp_seq=1215 ttl=254 time=2.743 ms 64 bytes from 10.100.20.10: icmp_seq=1216 ttl=254 time=1.469 ms 64 bytes from 10.100.20.10: icmp_seq=1217 ttl=254 time=7.322 ms 64 bytes from 10.100.20.10: icmp_seq=1218 ttl=254 time=1.532 ms 64 bytes from 10.100.20.10: icmp_seq=1219 ttl=254 time=1.438 ms 64 bytes from 10.100.20.10: icmp_seq=1220 ttl=254 time=7.122 ms 64 bytes from 10.100.20.10: icmp_seq=1221 ttl=254 time=1.344 ms 64 bytes from 10.100.20.10: icmp_seq=1222 ttl=254 time=1.63 ms 64 bytes from 10.100.20.10: icmp_seq=1223 ttl=254 time=6.133 ms 64 bytes from 10.100.20.10: icmp_seq=1224 ttl=254 time=1.455 ms 64 bytes from 10.100.20.10: icmp_seq=1225 ttl=254 time=3.221 ms 64 bytes from 10.100.20.10: icmp_seq=1226 ttl=254 time=4.435 ms 64 bytes from 10.100.20.10: icmp_seq=1227 ttl=254 time=1.463 ms 64 bytes from 10.100.20.10: icmp_seq=1228 ttl=254 time=5.14 ms 64 bytes from 10.100.20.10: icmp_seq=1229 ttl=254 time=2.796 ms 64 bytes from 10.100.20.10: icmp_seq=1230 ttl=254 time=1.49 ms 64 bytes from 10.100.20.10: icmp_seq=1231 ttl=254 time=6.707 ms 64 bytes from 10.100.20.10: icmp_seq=1232 ttl=254 time=1.447 ms 64 bytes from 10.100.20.10: icmp_seq=1233 ttl=254 time=1.285 ms 64 bytes from 10.100.20.10: icmp_seq=1234 ttl=254 time=7.097 ms 64 bytes from 10.100.20.10: icmp_seq=1235 ttl=254 time=1.295 ms 64 bytes from 10.100.20.10: icmp_seq=1236 ttl=254 time=0.916 ms 64 bytes from 10.100.20.10: icmp_seq=1237 ttl=254 time=6.24 ms 64 bytes from 10.100.20.10: icmp_seq=1238 ttl=254 time=1.439 ms 64 bytes from 10.100.20.10: icmp_seq=1239 ttl=254 time=2.739 ms 64 bytes from 10.100.20.10: icmp_seq=1240 ttl=254 time=4.477 ms 64 bytes from 10.100.20.10: icmp_seq=1241 ttl=254 time=1.431 ms 64 bytes from 10.100.20.10: icmp_seq=1242 ttl=254 time=5.372 ms 64 bytes from 10.100.20.10: icmp_seq=1243 ttl=254 time=3.119 ms 64 bytes from 10.100.20.10: icmp_seq=1244 ttl=254 time=1.504 ms 64 bytes from 10.100.20.10: icmp_seq=1245 ttl=254 time=6.909 ms 64 bytes from 10.100.20.10: icmp_seq=1246 ttl=254 time=1.498 ms 64 bytes from 10.100.20.10: icmp_seq=1247 ttl=254 time=1.454 ms 64 bytes from 10.100.20.10: icmp_seq=1248 ttl=254 time=6.701 ms 64 bytes from 10.100.20.10: icmp_seq=1249 ttl=254 time=1.441 ms 64 bytes from 10.100.20.10: icmp_seq=1250 ttl=254 time=1.888 ms 64 bytes from 10.100.20.10: icmp_seq=1251 ttl=254 time=6.052 ms 64 bytes from 10.100.20.10: icmp_seq=1252 ttl=254 time=1.469 ms 64 bytes from 10.100.20.10: icmp_seq=1253 ttl=254 time=3.61 ms 64 bytes from 10.100.20.10: icmp_seq=1254 ttl=254 time=4.213 ms 64 bytes from 10.100.20.10: icmp_seq=1255 ttl=254 time=1.276 ms 64 bytes from 10.100.20.10: icmp_seq=1256 ttl=254 time=5.712 ms 64 bytes from 10.100.20.10: icmp_seq=1257 ttl=254 time=2.299 ms 64 bytes from 10.100.20.10: icmp_seq=1258 ttl=254 time=1.417 ms 64 bytes from 10.100.20.10: icmp_seq=1259 ttl=254 time=7.159 ms 64 bytes from 10.100.20.10: icmp_seq=1260 ttl=254 time=1.538 ms 64 bytes from 10.100.20.10: icmp_seq=1261 ttl=254 time=1.629 ms 64 bytes from 10.100.20.10: icmp_seq=1262 ttl=254 time=7.892 ms 64 bytes from 10.100.20.10: icmp_seq=1263 ttl=254 time=1.495 ms 64 bytes from 10.100.20.10: icmp_seq=1264 ttl=254 time=2.792 ms ^C --- 10.100.20.10 ping statistics --- 1265 packets transmitted, 58 packets received, 95.42% packet loss round-trip min/avg/max = 0.916/3.31/7.892 ms SA-HOST-A#
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
29-Jul-2024
|
初始版本 |
由思科工程師貢獻
- Chingiz KhalafovTechnical Consulting Engineer
 意見
意見