瞭解安全Web裝置中的資料包流
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本檔案介紹代理配置網路中的網路流量,特別側重安全網路裝置(SWA)。
必要條件
需求
思科建議您瞭解以下主題:
- 基本TCP/IP概念。
- 代理設定的基本知識。
- 有關使用Proxy的環境中使用的驗證機制的基本知識。
本文的縮寫為:
TCP:傳輸控制協定
UDP:用戶數據包協定
IP:Internet協定
GRE:通用路由封裝
HTTP:超文本傳輸協定。
HTTPS:超文本傳輸協定安全。
URL:統一資源定位器
TLS:傳輸層安全
採用元件
本文件所述內容不限於特定軟體和硬體版本。
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
代理部署的不同型別
TLS握手
HTTPS中的TLS握手發生在客戶端和伺服器通過Internet通訊時,從而提供安全連線。該過程維護兩個正在通訊的應用程式之間的隱私性和資料完整性。它通過一系列步驟運行,其中客戶端和伺服器就所有後續傳輸的加密標準和代碼達成一致。握手的目的是阻止任何未經授權的訪問或第三方操縱。它還對通訊方的身份進行身份驗證以消除模擬。此程式對於HTTPS至關重要,因為它可確保資料在傳輸過程中保持安全。
以下是TLS握手的步驟:
-
客戶端Hello:客戶端使用hello消息啟動握手過程。此消息包含客戶端TLS版本、支援的密碼套件以及稱為「客戶端隨機」的隨機位元組字串。
-
伺服器Hello:伺服器以hello消息進行響應。此消息包括伺服器選擇的TLS版本、選擇的密碼套件、稱為「伺服器隨機」的隨機位元組字串以及伺服器數位證書。如有必要,伺服器還會請求客戶端數位證書進行相互身份驗證。
-
客戶端驗證伺服器證書:客戶端向頒發證書的證書頒發機構檢查伺服器數位證書。這可以確保客戶端正在與合法伺服器進行通訊。
-
預置金鑰:客戶端傳送隨機位元組字串,稱為「前主金鑰」,用於建立會話金鑰。客戶端使用伺服器公鑰加密此預先主金鑰,因此只有伺服器可以使用其私鑰對其進行解密。
-
主金鑰:客戶端和伺服器都使用前主金鑰和來自hello消息的隨機位元組字串來獨立計算相同的「主金鑰」。 此共用金鑰是生成會話金鑰的基礎。
-
客戶端完成:客戶端傳送「完成」消息,該消息使用會話金鑰加密,以發出握手客戶端部分的完成訊號。
-
伺服器已完成:伺服器傳送「已完成」消息(也使用會話金鑰加密),以發出握手伺服器部分的完成訊號。
HTTP響應代碼
1xx :資訊
| 代碼 | 詳細資料 |
|
100繼續 |
通常在ICAP協定中看到。這是一個資訊性響應,使客戶端知道它可以繼續傳送資料。關於ICAP服務(如病毒掃描),伺服器只希望看到前x個位元組。當掃描完第一組位元組並且沒有檢測到病毒時,它會傳送100 Continue以讓客戶端知道傳送對象的其餘部分。 |
2xx:成功
| 代碼 | 詳細資料 |
|
200正常 |
最常見的響應代碼。這表示請求成功而沒有任何問題。 |
3xx:重定向
| 代碼 | 詳細資料 |
|
301永久重新導向 |
這是永久重新導向,當您重新導向到www子域時,可以看到此代碼。 |
|
302臨時重新導向 |
這是臨時重新導向。指示客戶端對Location:標題。 |
|
304未修改 |
這是對GIMS(GET If-modified-since)的響應。 這實際上是一個標準的HTTP GET,包括報頭If-modified-since:<日期>。此標頭告知伺服器,客戶端在其本地快取中有一個請求對象的副本,其中包括提取該對象的日期。如果自該日期以來修改了對象,則伺服器將以200 OK和對象的新副本進行響應。如果自獲取日期以來對象未更改,伺服器將傳送回304 Not Modified響應。 |
|
307驗證重新導向 |
這在透明代理部署中最為常見,當代理伺服器配置為驗證請求並將請求重定向到另一個URL以驗證使用者時, |
4xx代碼:客戶端錯誤
| 代碼 | 詳細資料 |
|
400錯誤請求 |
這說明HTTP請求有問題,因為它不符合正確的語法。可能的原因可能包括單個行上的多個報頭、報頭中的空格或URI中缺少HTTP/1.1等。有關正確語法,請參閱RFC 2616。 |
|
401未授權 需要Web伺服器驗證 |
訪問請求的對象需要身份驗證。401代碼用於與目標Web伺服器進行身份驗證。當SWA以透明模式運行並在代理上啟用身份驗證時,它會將一個401返回給客戶端,因為裝置將自己顯示為OCS(源內容伺服器)。 「www-authenticate:」HTTP響應報頭中詳細介紹了可以使用的身份驗證方法。這將通知客戶端伺服器是否請求NTLM、基本或其他形式的身份驗證。 |
|
403被拒絕 |
客戶端無法訪問請求的對象。多種原因可能導致伺服器拒絕對象訪問。伺服器通常在HTTP資料或HTML響應中提供原因說明。 |
|
404未找到 |
伺服器上不存在請求的對象。 |
|
需要407代理驗證 |
這與401相同,不同之處在於,它專門用於對Proxy(而不是OCS)的身份驗證。只有當請求被明確傳送到Proxy時,才會傳送。 當SWA配置為透明代理時,無法將407傳送到客戶端,因為客戶端不知道該代理存在。如果是這種情況,則客戶端很可能使用FIN或RST作為TCP套接字。 |
5xx:伺服器錯誤
| 代碼 | 詳細資料 |
|
501內部伺服器錯誤 |
一般Web伺服器故障。 |
|
502錯誤的網關 |
當充當網關或代理的伺服器收到來自入站伺服器的無效響應時發生。它發出訊號,表明網關從上游或源伺服器收到了不適當的響應。 |
|
503服務不可用 |
表示由於臨時過載或計畫的維護,伺服器當前無法處理請求。這表示伺服器暫時停止服務,但過一段時間後可以再次使用。 |
|
504網關超時 |
表示客戶端或代理未從它嘗試訪問以載入網頁或完成瀏覽器另一請求的Web伺服器收到及時響應。這通常意味著上游伺服器發生故障。 |
顯式部署
在這裡…….
無身份驗證的顯式部署中的HTTP流量
客戶端和SWA
網路流量在客戶端的IP地址和SWA代理介面的IP地址之間傳輸(通常是P1介面,但可能是P2或管理介面,具體取決於代理配置)。
從客戶端發往TCP埠80或3128的流量發往SWA(預設SWA代理埠為TCP 80和3128,在本例中使用埠3128)
- TCP握手。
- 從客戶端獲取HTTP(目標IP = SWA IP,目標埠= 3128)
- 來自代理的HTTP響應(源IP = SWA)
- 資料傳輸
- TCP連線終止(4次握手)
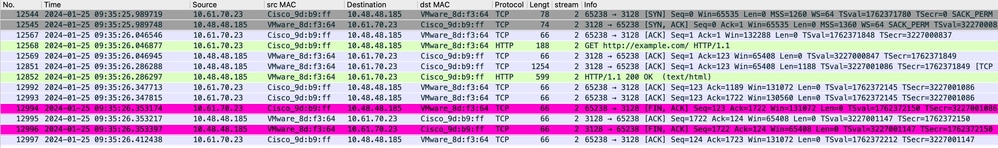 Image-Client到SWA,HTTP顯式模式
Image-Client到SWA,HTTP顯式模式
SWA和Web伺服器
網路流量發生在代理的IP地址和Web伺服器的IP地址之間。
來自SWA的流量將發往TCP埠80,且來源為隨機埠(不是代理埠)
- TCP握手。
- HTTP從代理獲取(目標IP = Web伺服器,目標埠= 80)
- 來自Web伺服器的HTTP響應(源IP =代理伺服器)
- 資料傳輸
- TCP連線終止(4次握手)
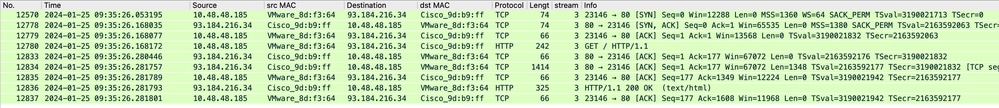 影象 — HTTP-SWA到Web伺服器 — 顯式 — 無快取
影象 — HTTP-SWA到Web伺服器 — 顯式 — 無快取
以下是來自使用者端的HTTP Get範例
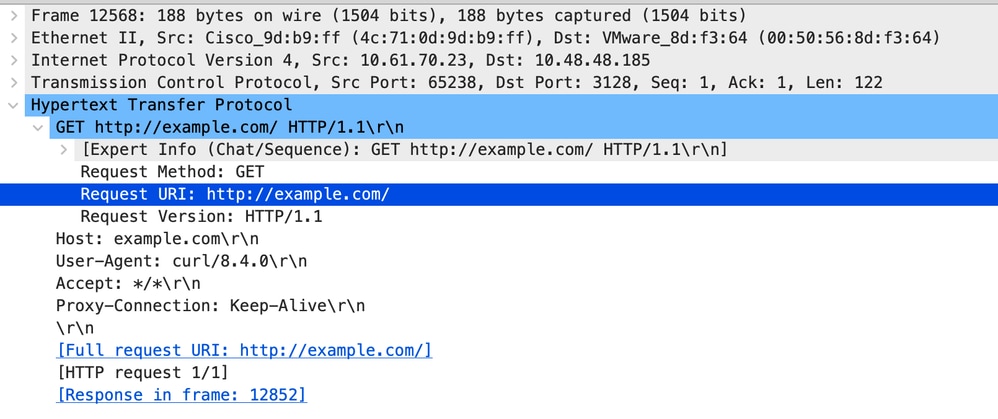 影象 — SWA HTTP GET的客戶端 — Explicit
影象 — SWA HTTP GET的客戶端 — Explicit
這表示從客戶端到SWA,然後到Web伺服器,最後再返回到客戶端的整個流量流。
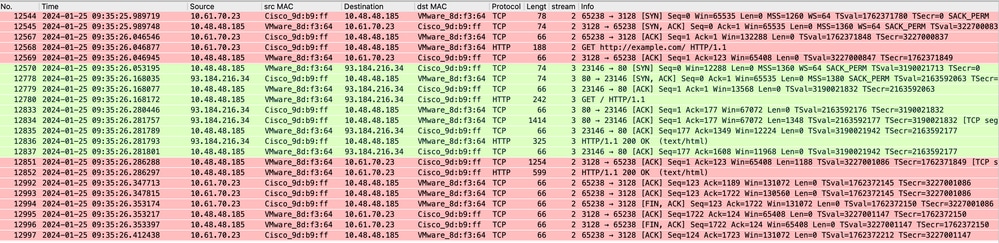 影象 — 所有流量HTTP顯式 — 無快取
影象 — 所有流量HTTP顯式 — 無快取

附註:每個流量流都以不同的顏色區分;從客戶端到SWA的流是一種顏色,而從SWA到Web伺服器的流是另一種顏色。
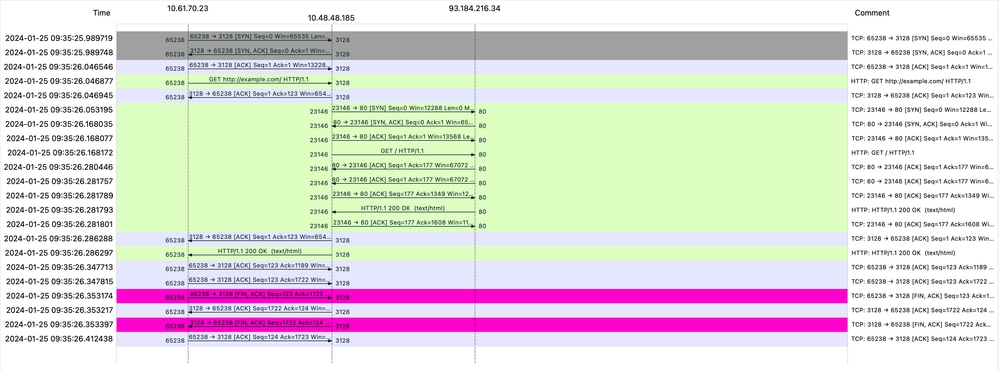 影象 — 通訊流HTTP顯式 — 無快取
影象 — 通訊流HTTP顯式 — 無快取
以下是存取日誌的範例:
1706172876.686 224 10.61.70.23 TCP_MISS/200 1721 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,1,"-",0,0,0,1,"-",-,-,-,"-",1,-,"-","-",-,-,"IW_ref",-,"Unknown","Reference","-","Unknown","Unknown","-","-",61.46,0,-,"Unknown","-",1,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 10, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 108, Request Header = 0, Request to Server = 0, 1st byte to client = 3, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 106, Response header = 0, Server response = 1, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 2, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 1, AMP response = 0, AMP total = 0; Latency = 4; "25/Jan/2024:09:54:36 +0100" ][Client Port = 65238, Server IP = 10.184.216.34, Server Port = 80]包含快取資料的流量
這表示當資料在SWA快取中時,從客戶端到SWA的整個流量流。
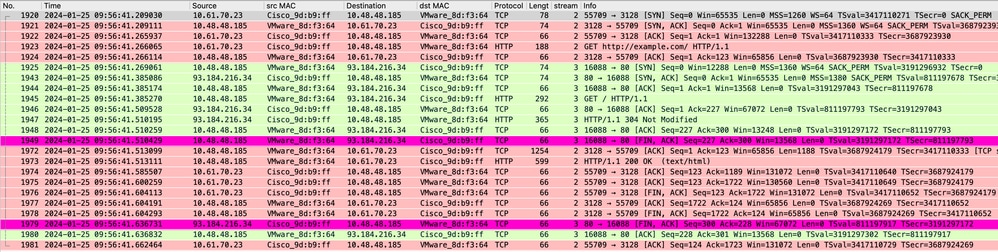 影象 — HTTP顯式快取資料
影象 — HTTP顯式快取資料

附註:您可以看到,Web伺服器返回HTTP響應304:未修改快取。(在本例中,封包編號1947)
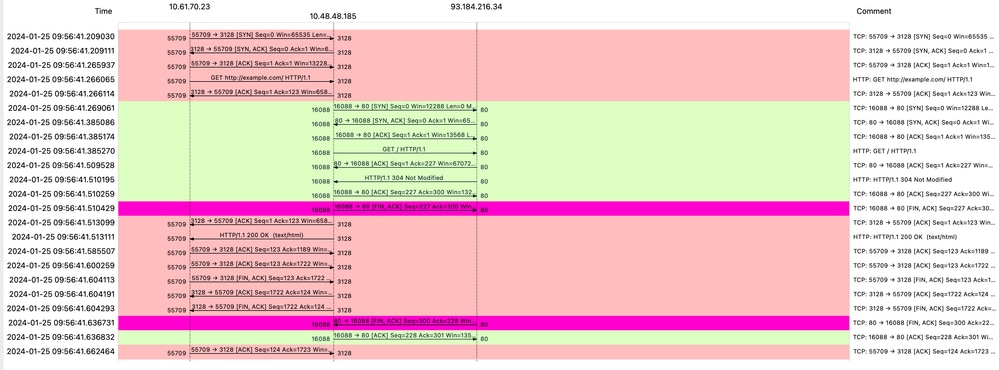 影象 — 帶快取的顯式流HTTP
影象 — 帶快取的顯式流HTTP
以下是HTTP響應304的示例
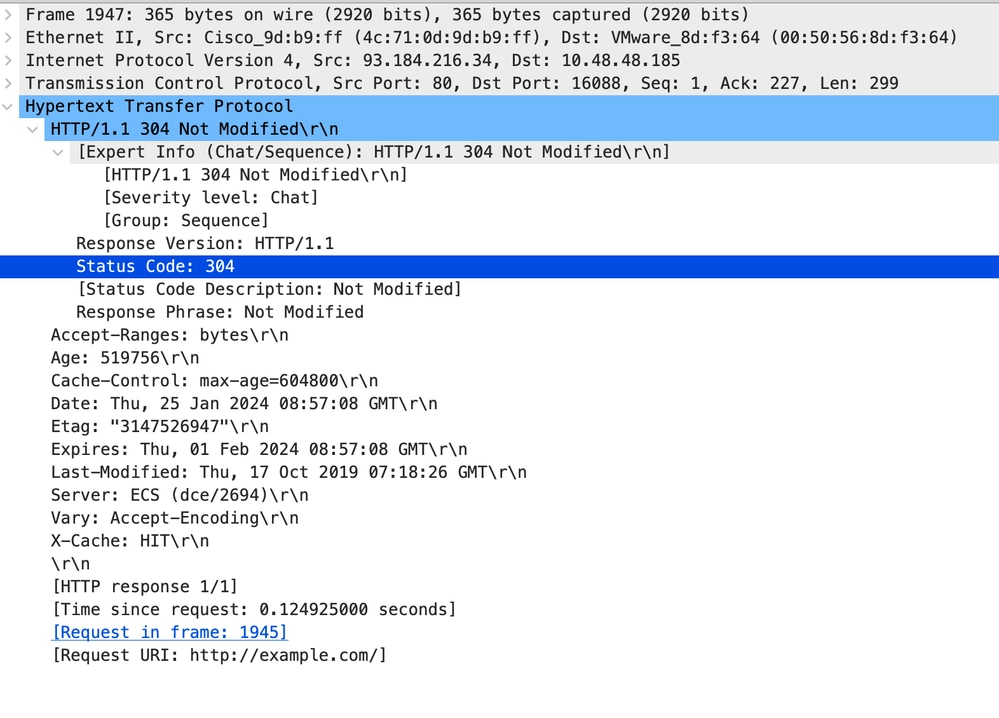 影象 — HTTP顯式304響應
影象 — HTTP顯式304響應
以下是存取日誌的範例:
1706173001.489 235 10.61.70.23 TCP_REFRESH_HIT/200 1721 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,1,"-",0,0,0,1,"-",-,-,-,"-",1,-,"-","-",-,-,"IW_ref",-,"Unknown","Reference","-","Unknown","Unknown","-","-",58.59,0,-,"Unknown","-",1,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 150, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 110, Request Header = 0, Request to Server = 0, 1st byte to client = 2, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 119, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 1, AMP response = 0, AMP total = 0; Latency = 1; "25/Jan/2024:09:56:41 +0100" ][Client Port = 55709, Server IP = 10.184.216.34, Server Port = 80]無身份驗證的顯式部署中的HTTPs流量
客戶端和SWA
網路流量在客戶端的IP地址和SWA代理介面的IP地址之間傳輸(通常是P1介面,但可能是P2或管理介面,具體取決於代理配置)。
從客戶端發往TCP埠80或3128的流量發往SWA(預設SWA代理埠為TCP 80和3128,在本例中使用埠3128)
- TCP握手。
- 來自客戶端的HTTP CONNECT(目標IP = SWA,目標埠= 3128)
- 來自代理的HTTP響應(源IP = SWA)
- 使用URL的SNI的客戶端Hello(源IP =客戶端)
- 伺服器Hello(源IP = SWA)
- 伺服器金鑰交換(源IP = SWA)
- 客戶端金鑰交換(源IP =客戶端)
- 資料傳輸
- TCP連線終止(4次握手)
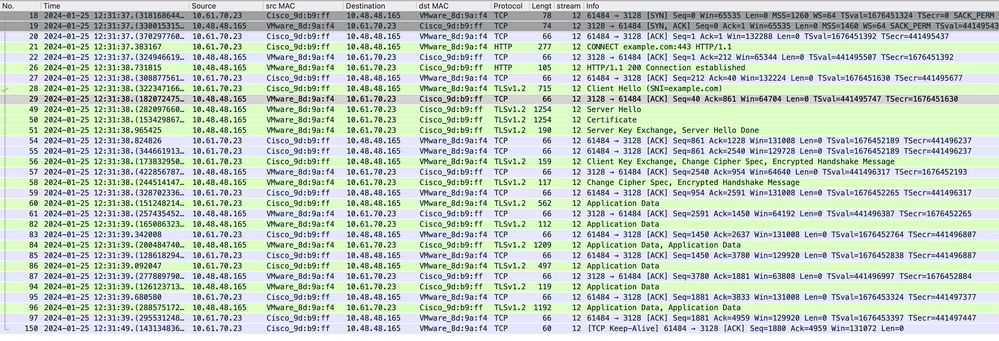 映像 — SWA的HTTPS客戶端 — 顯式 — 無快取
映像 — SWA的HTTPS客戶端 — 顯式 — 無快取
以下是從客戶端到SWA的客戶端Hello的詳細資訊,如您在伺服器名稱指示(SNI)中看到的Web伺服器的URL,在本示例中,URL為www.example.com,客戶端通告了17個密碼套件:
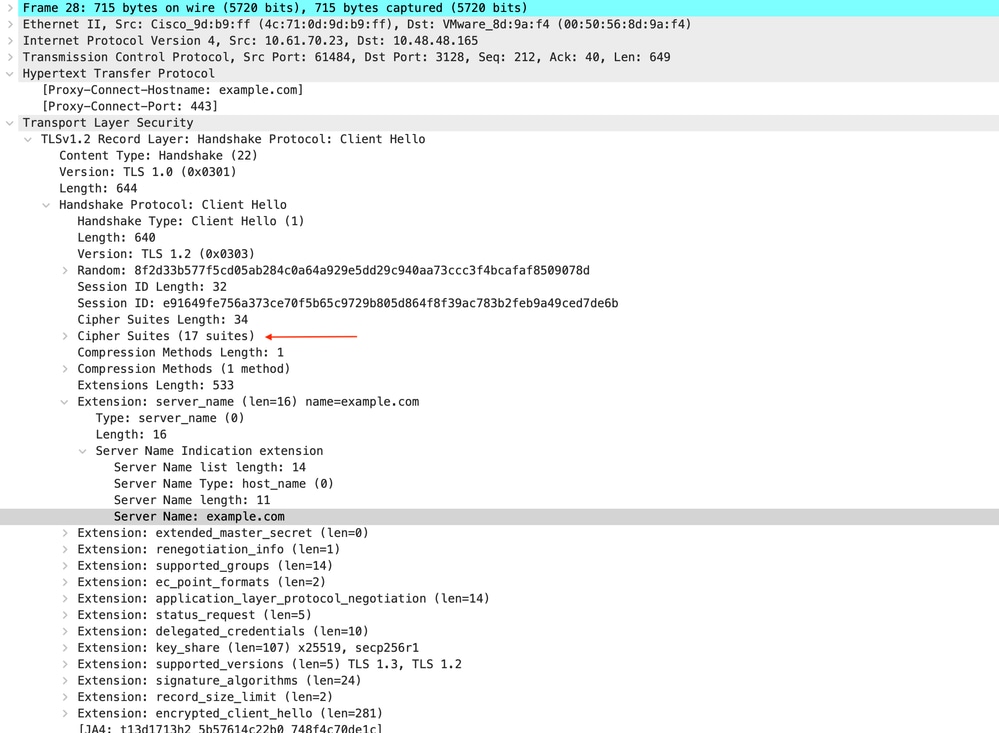 映像 — HTTPS客戶端hello — 顯式 — SWA客戶端
映像 — HTTPS客戶端hello — 顯式 — SWA客戶端

提示:您可以在Wireshark中使用此過濾器搜尋URL/SNI :tls.handshake.extensions_server_name == "www.example.com"
以下是SWA傳送到客戶端的證書示例
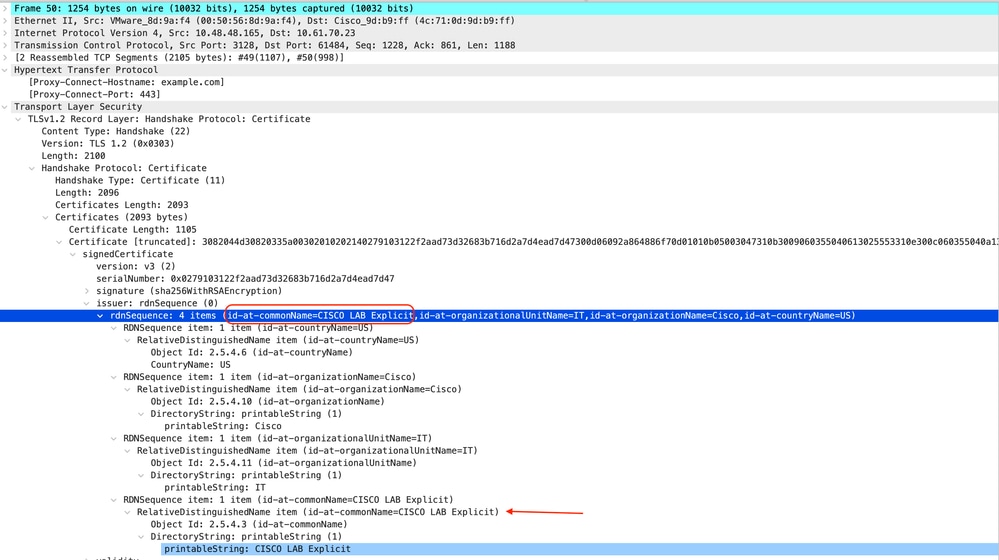 映像 — HTTPS證書 — 顯式 — SWA到客戶端
映像 — HTTPS證書 — 顯式 — SWA到客戶端
SWA和Web伺服器
網路流量發生在代理的IP地址和Web伺服器的IP地址之間。
來自SWA的流量將發往TCP埠443(不是代理埠)
- TCP握手。
- 客戶端Hello(目標IP = Web伺服器,目標埠= 443)
- 伺服器Hello(源IP = Web伺服器)
- 資料傳輸
- TCP連線終止(4次握手)
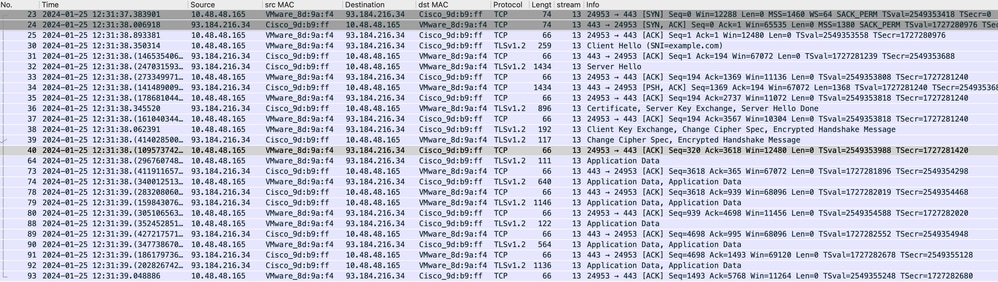 影象 — HTTPS — 顯式 — SWA到Web伺服器
影象 — HTTPS — 顯式 — SWA到Web伺服器
以下是從SWA到Web伺服器的客戶端Hello的詳細資訊,因為您可以看到SWA通告了12個密碼套件:
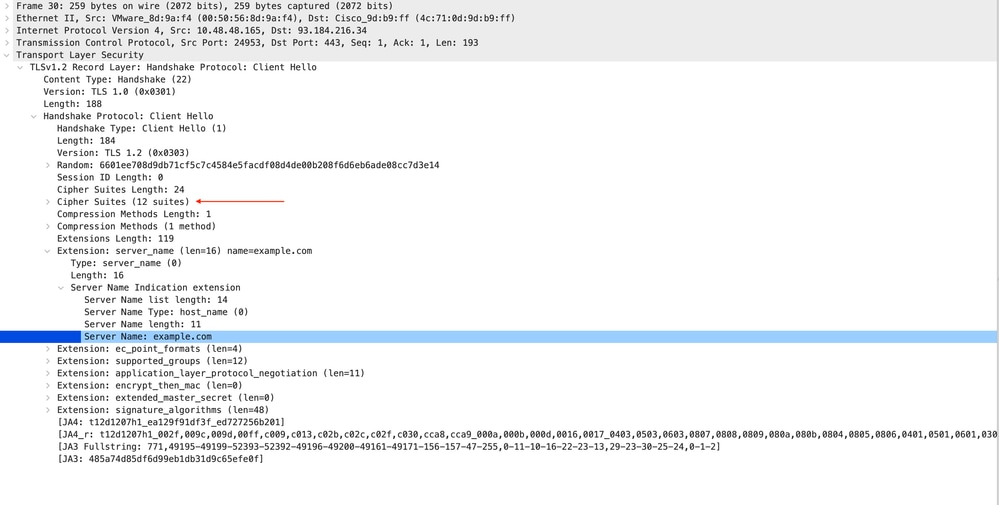 影象 — HTTPS客戶端Hello - SWA到Web伺服器 — 無聊天
影象 — HTTPS客戶端Hello - SWA到Web伺服器 — 無聊天

附註:此處觀察的密碼套件與從使用者端到SWA的使用者端Hello中的密碼套件不同,因為設定為解密此流量的SWA使用自己的密碼。

提示:在Server Key Exchange from SWA to Web Server中,顯示Web Server證書。但是,如果上游代理找到您的SWA的配置,則會顯示其證書而不是Web伺服器證書。
以下是來自使用者端的HTTP CONNECT範例
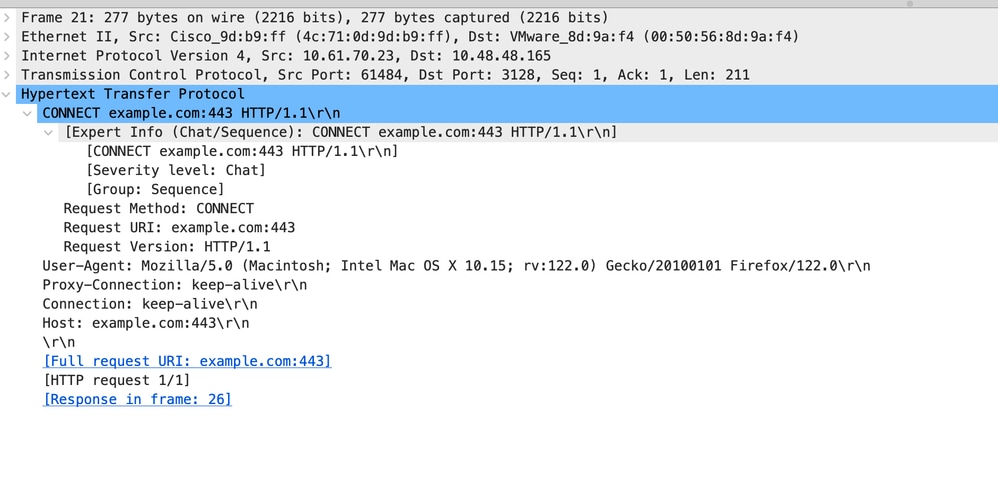 影象 — 客戶端HTTP連線
影象 — 客戶端HTTP連線
這表示從客戶端到SWA,然後到Web伺服器,最後再返回到客戶端的整個流量流。
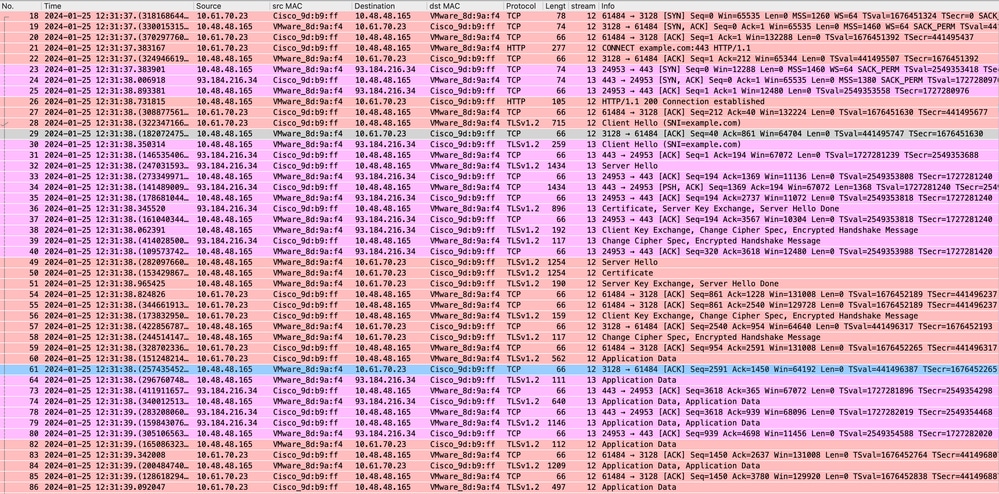 映像 — 完整HTTPS顯式 — 無快取
映像 — 完整HTTPS顯式 — 無快取

附註:每個流量流都以不同的顏色區分;從客戶端到SWA的流是一種顏色,而從SWA到Web伺服器的流是另一種顏色。
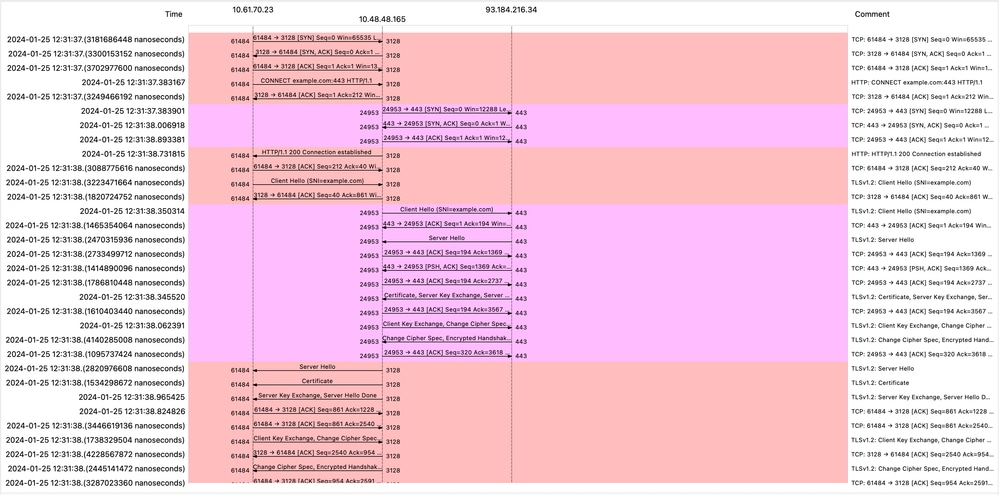 影象 — HTTPS流 — 顯式 — 無快取
影象 — HTTPS流 — 顯式 — 無快取
以下是存取日誌的範例:
1706174571.215 582 10.61.70.23 TCP_MISS_SSL/200 39 CONNECT tunnel://www.example.com:443/ - DIRECT/www.example.com - DECRYPT_WEBCAT_7-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"IW_ref",-,"-","Reference","-","Unknown","Unknown","-","-",0.54,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 1600, User Agent = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 113, Request Header = 0, Request to Server = 0, 1st byte to client = 113, Response Header = 0, Client Body = 79 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 0, Response header = 0, Server response = 344, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 0, AMP total = 0; Latency = 0; "25/Jan/2024:10:22:51 +0100" ][Client Port = 24953, Server IP = 10.184.216.34, Server Port = 443]
1706174571.486 270 10.61.70.23 TCP_MISS_SSL/200 1106 GET https://www.example.com:443/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,1,"-",0,0,0,1,"-",-,-,-,"-",1,-,"-","-",-,-,"IW_ref",-,"Unknown","Reference","-","Unknown","Unknown","-","-",32.77,0,-,"Unknown","-",1,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 1630, User Agent = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 3, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 264, Response header = 0, Server response = 2, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 1, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 1, AMP response = 0, AMP total = 0; Latency = 2; "25/Jan/2024:10:22:51 +0100" ][Client Port = 24953, Server IP = 10.184.216.34, Server Port = 443]
附註:您可以看到,在HTTPS流量的透明部署中,Accesslogs中有兩行,第一行是流量被加密時,您可以看到CONNECT,並且Web伺服器的URL以tunnel://開頭。如果在SWA中啟用解密,則第二行包含GET,並且整個URL以HTTPS開頭,這意味著流量已解密。
直通HTTPS流量
如果您將SWA配置為通過流量,則以下為總流量:
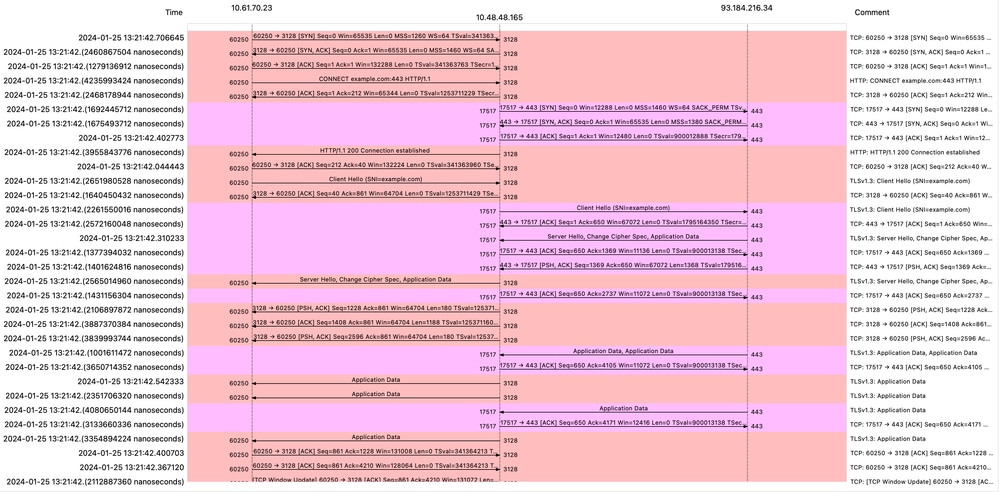 影象 — HTTPS傳輸 — 顯式 — 流
影象 — HTTPS傳輸 — 顯式 — 流
以下是從SWA到Web伺服器的客戶端Hello示例:
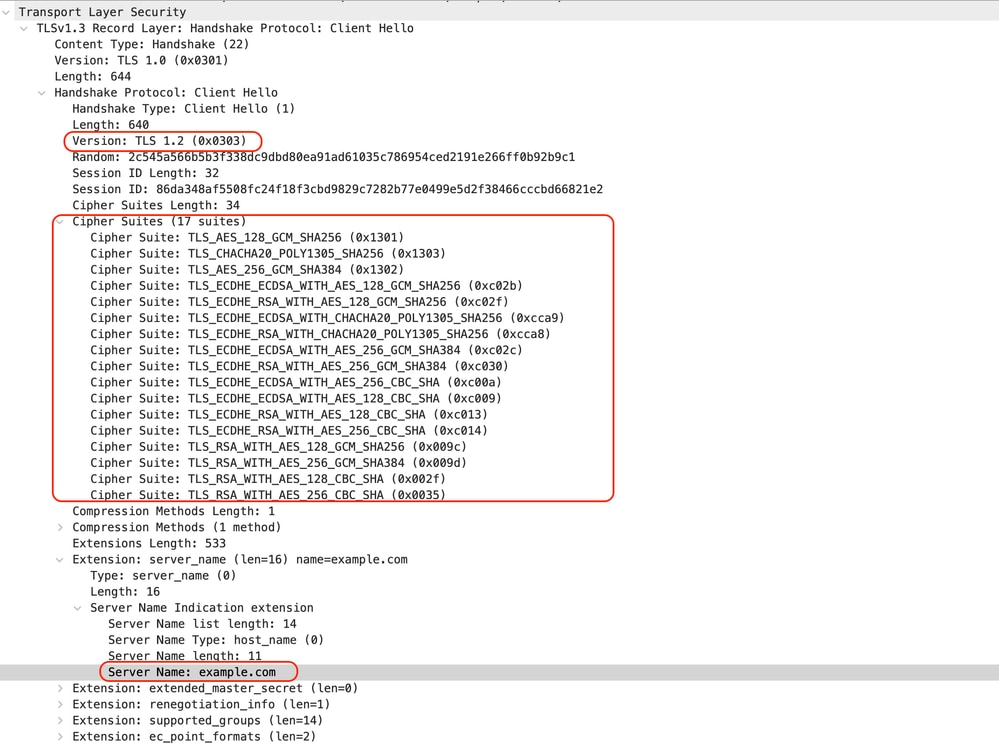 影象 — HTTPS直通 — 顯式 — SWA到Web伺服器 — 客戶端hello
影象 — HTTPS直通 — 顯式 — SWA到Web伺服器 — 客戶端hello
與從客戶端到SWA的客戶端Hello相同:
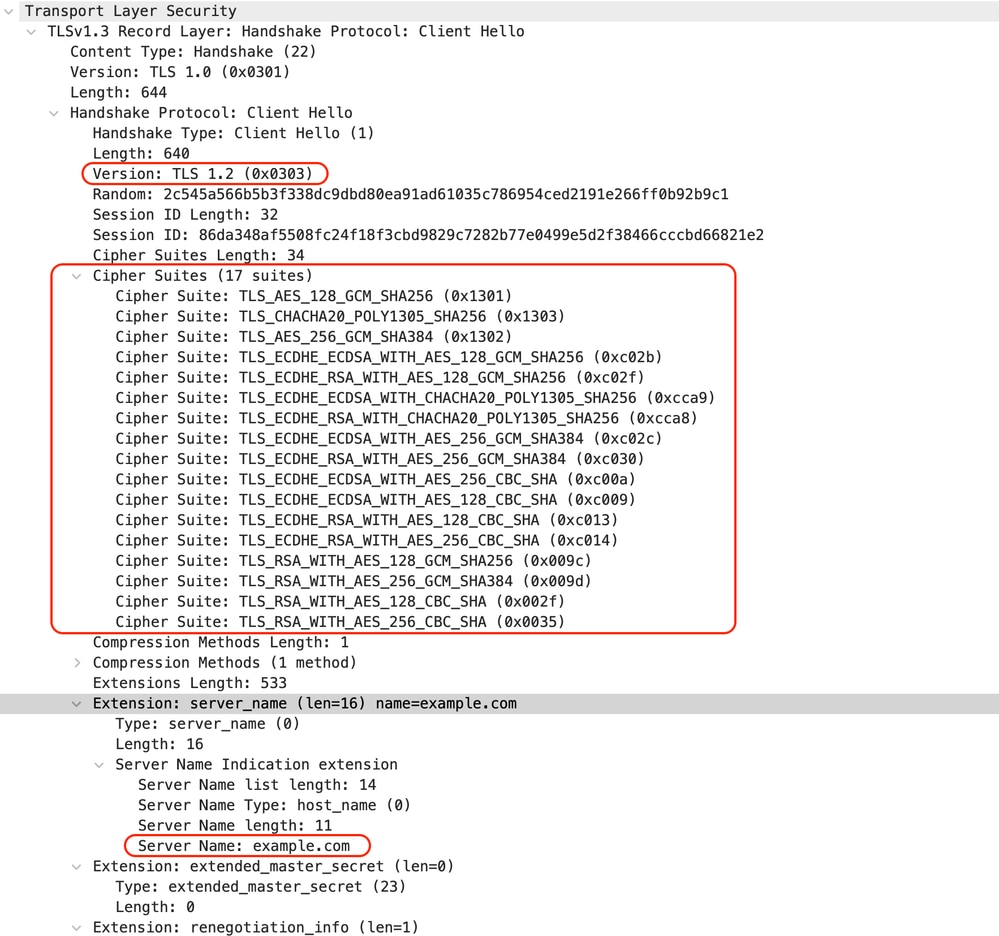 映像 — HTTPS直通 — 顯式 — 客戶端到SWA — 客戶端hello
映像 — HTTPS直通 — 顯式 — 客戶端到SWA — 客戶端hello
以下是存取日誌範例:
1706185288.920 53395 10.61.70.23 TCP_MISS/200 6549 CONNECT tunnel://www.example.com:443/ - DIRECT/www.example.com - PASSTHRU_WEBCAT_7-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"IW_ref",-,"-","Reference","-","Unknown","Unknown","-","-",0.98,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 210, User Agent = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 233, Request Header = 0, Request to Server = 0, 1st byte to client = 119, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 0, Response header = 0, Server response = 436, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 22, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 0, AMP total = 0; Latency = 22; "25/Jan/2024:13:21:28 +0100" ][Client Port = 59939, Server IP = 10.184.216.34, Server Port = 443]
附註:您可以看到,它只是一條線路,操作是PASSTHRU。
透明部署
無身份驗證的透明部署中的HTTP流量
客戶端和SWA
網路流量在客戶端的IP地址和Web伺服器的IP地址之間傳輸。
來自使用者端的流量目的地為TCP連線埠80(不是代理連線埠)
- TCP握手。
- 從客戶端獲取HTTP(目標IP = Web伺服器,目標埠= 80)
- 來自代理的HTTP響應(源IP = Web伺服器)
- 資料傳輸
- TCP連線終止(4次握手)
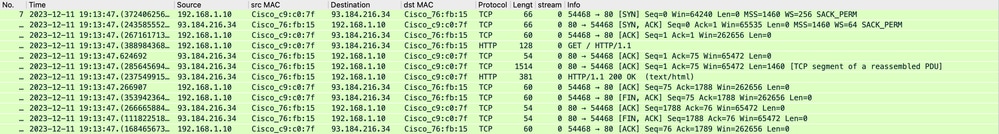 映像 — 客戶端到Proxy - HTTP — 透明 — 無身份驗證
映像 — 客戶端到Proxy - HTTP — 透明 — 無身份驗證
以下是來自使用者端的HTTP Get範例
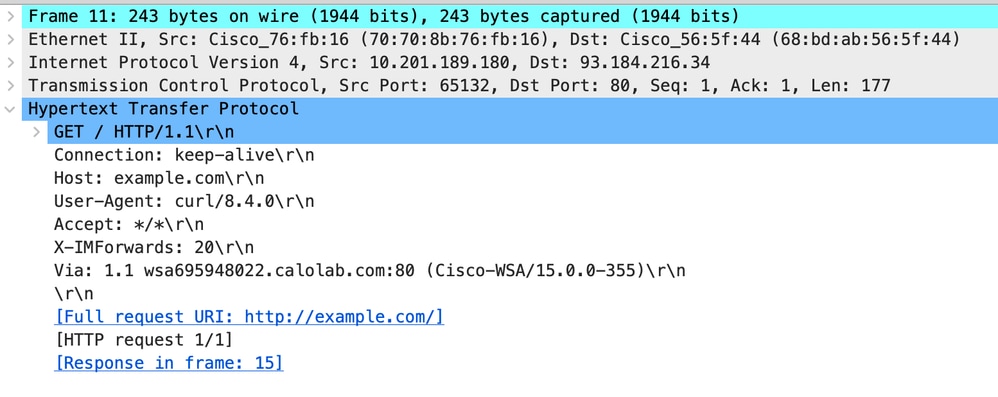 影象 — 客戶端到Proxy - HTTP — 透明 — 無身份驗證 — 客戶端HTTP Get
影象 — 客戶端到Proxy - HTTP — 透明 — 無身份驗證 — 客戶端HTTP Get
SWA和Web伺服器
網路流量發生在代理的IP地址和Web伺服器的IP地址之間。
來自SWA的流量將發往TCP埠80(不是代理埠)
- TCP握手。
- HTTP從代理獲取(目標IP = Web伺服器,目標埠= 80)
- 來自Web伺服器的HTTP響應(源IP =代理伺服器)
- 資料傳輸
- TCP連線終止(4次握手)
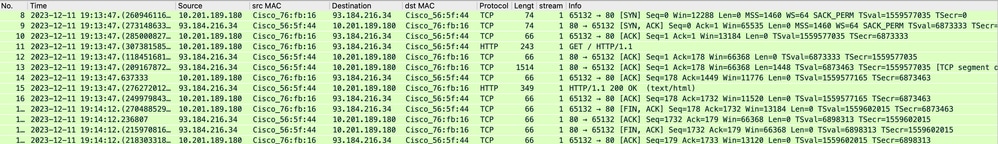 映像 — Proxy和Web伺服器 — HTTP — 透明 — 無身份驗證
映像 — Proxy和Web伺服器 — HTTP — 透明 — 無身份驗證
以下是來自Proxy的HTTP Get範例
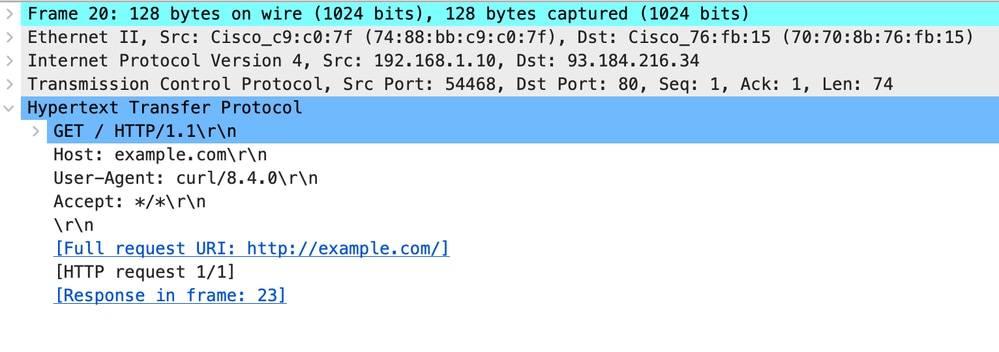 影象 — Proxy to Web Server - HTTP — 透明 — 無身份驗證 — Proxy HTTP Get
影象 — Proxy to Web Server - HTTP — 透明 — 無身份驗證 — Proxy HTTP Get
這表示從客戶端到SWA,然後到Web伺服器,最後再返回到客戶端的整個流量流。
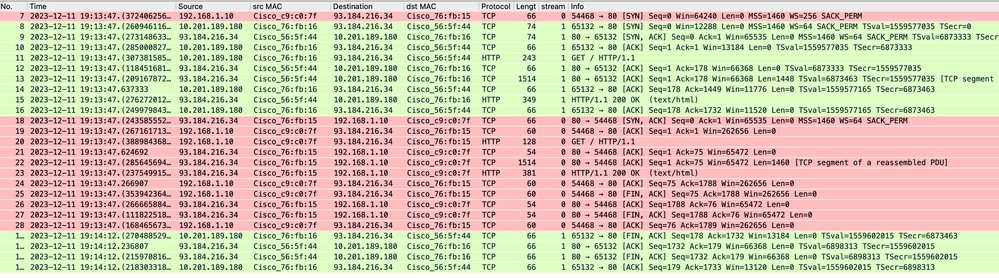 映像 — 總流量 — HTTP — 透明 — 無身份驗證
映像 — 總流量 — HTTP — 透明 — 無身份驗證

附註:每個流量流都以不同的顏色區分;從客戶端到SWA的流是一種顏色,而從SWA到Web伺服器的流是另一種顏色。
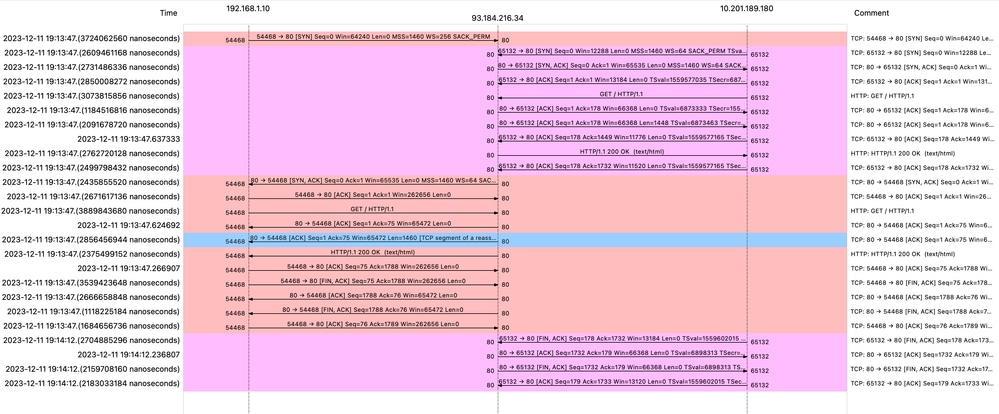 影象 — WCCP HTTP流
影象 — WCCP HTTP流
以下是存取日誌的範例:
1702318427.181 124 192.168.1.10 TCP_MISS/200 1787 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",115.29,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 50, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 0, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 1, Request Header = 0, Client Body = 0, 1st response byte = 124, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 124>, AMP total = 124<; Latency = 1; "11/Dec/2023:19:13:47 +0100" ][Client Port = 54468, Server IP = 10.184.216.34, Server Port = 80]包含快取資料的流量
這表示當資料在SWA快取中時,從客戶端到SWA的整個流量流。
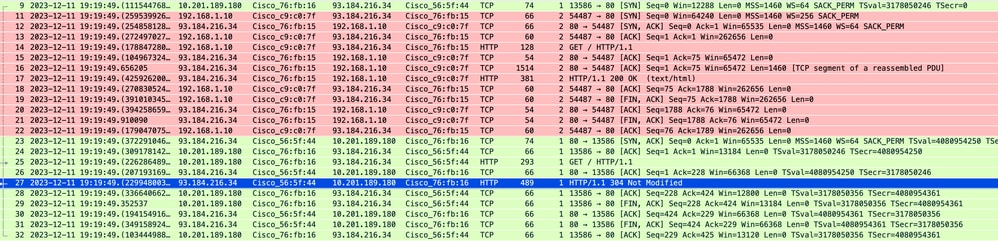 影象 — 快取 — 總流量 — HTTP — 透明 — 無身份驗證
影象 — 快取 — 總流量 — HTTP — 透明 — 無身份驗證

附註:您可以看到,Web伺服器返回HTTP響應304:未修改快取。(在本例中,封包編號27)
以下是HTTP響應304的示例
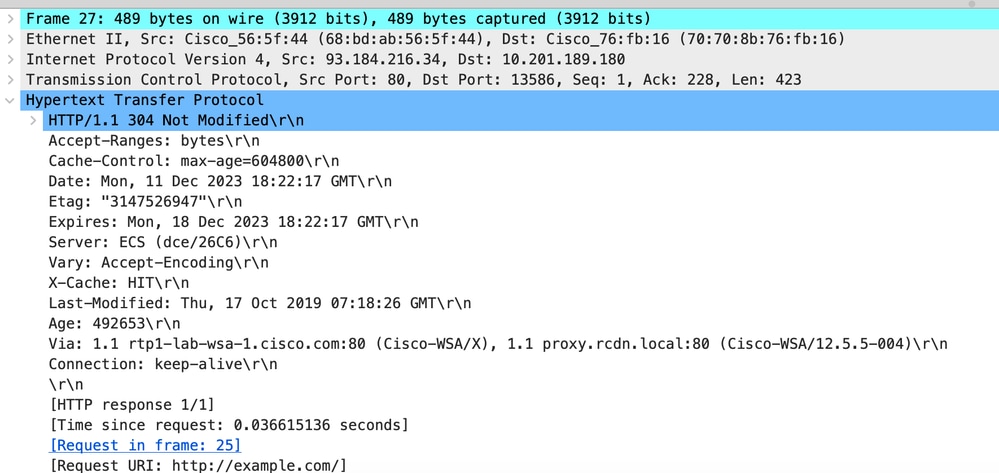 影象 — 快取 — HTTP響應304 - HTTP — 透明 — 無身份驗證
影象 — 快取 — HTTP響應304 - HTTP — 透明 — 無身份驗證
以下是存取日誌的範例:
1702318789.560 105 192.168.1.10 TCP_REFRESH_HIT/200 1787 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",136.15,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 360, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 0, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 2, Request Header = 0, Client Body = 0, 1st response byte = 104, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 105>, AMP total = 105<; Latency = 2; "11/Dec/2023:19:19:49 +0100" ][Client Port = 54487, Server IP = 10.184.216.34, Server Port = 80]無身份驗證的透明部署中的HTTP流量
客戶端和SWA
網路流量在客戶端的IP地址和Web伺服器的IP地址之間傳輸。
來自使用者端的流量目的地為TCP連線埠443(不是代理連線埠)
- TCP握手。
- TLS握手客戶端問候 — 伺服器問候 — 伺服器金鑰交換 — 客戶端金鑰交換
- 資料傳輸
- TCP連線終止(4次握手)
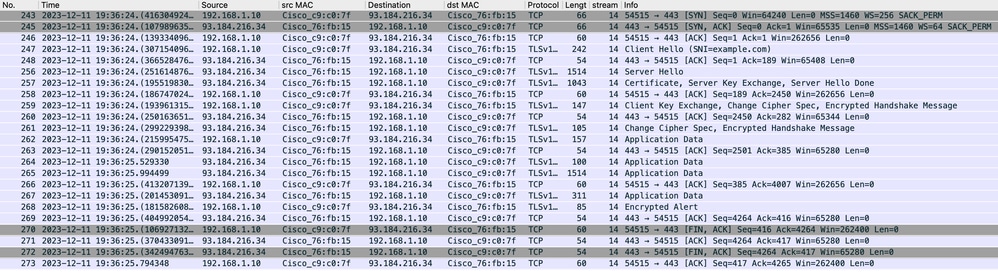 映像 — 客戶端到Proxy - HTTP — 透明 — 無身份驗證
映像 — 客戶端到Proxy - HTTP — 透明 — 無身份驗證
以下是從客戶端到SWA的客戶端Hello的詳細資訊,如您在伺服器名稱指示(SNI)中看到的Web伺服器的URL,在本例中為www.example.com。
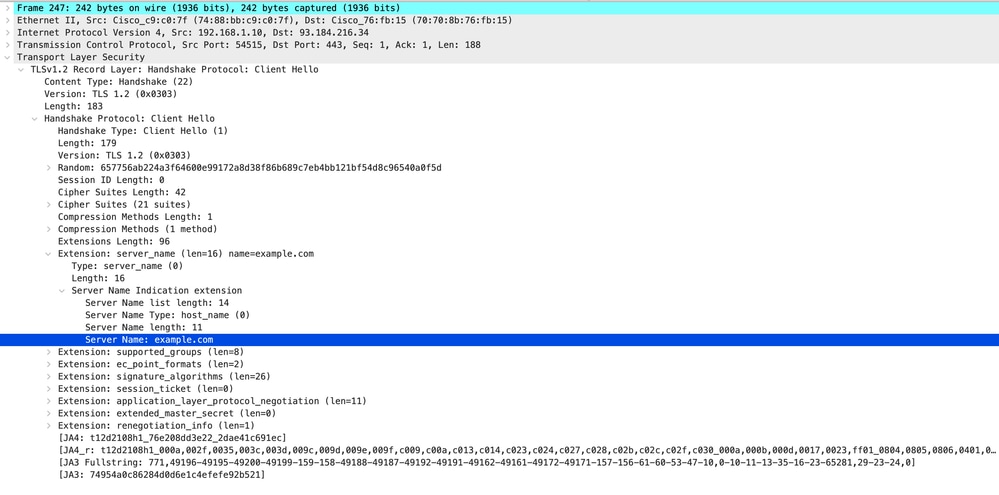 影象 — 客戶端Hello — 客戶端到代理 — 透明 — 無身份驗證
影象 — 客戶端Hello — 客戶端到代理 — 透明 — 無身份驗證

提示:您可以在Wireshark中使用此過濾器搜尋URL/SNI :tls.handshake.extensions_server_name == "www.example.com"
以下是伺服器金鑰交換範例
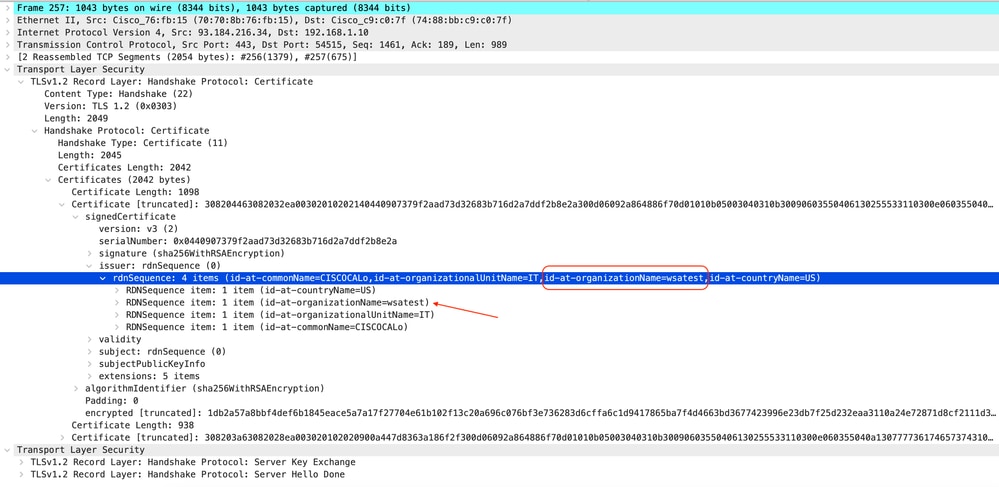 影象 — 伺服器金鑰交換 — 客戶端到代理 — 透明 — 無身份驗證
影象 — 伺服器金鑰交換 — 客戶端到代理 — 透明 — 無身份驗證

附註:您可以看到,憑證是在SWA中設定為解密憑證的憑證。
SWA和Web伺服器
網路流量發生在代理的IP地址和Web伺服器的IP地址之間。
來自SWA的流量將發往TCP埠443(不是代理埠)
- TCP握手。
- TLS握手客戶端問候 — 伺服器問候 — 伺服器金鑰交換 — 客戶端金鑰交換
- 資料傳輸
- TCP連線終止(4次握手)
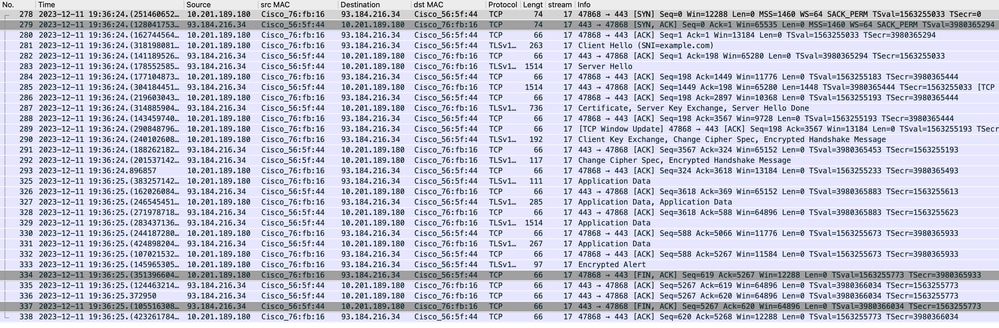 影象 — Web伺服器的代理 — HTTPs — 透明 — 無身份驗證
影象 — Web伺服器的代理 — HTTPs — 透明 — 無身份驗證
以下是從SWA到Web伺服器的客戶端Hello示例
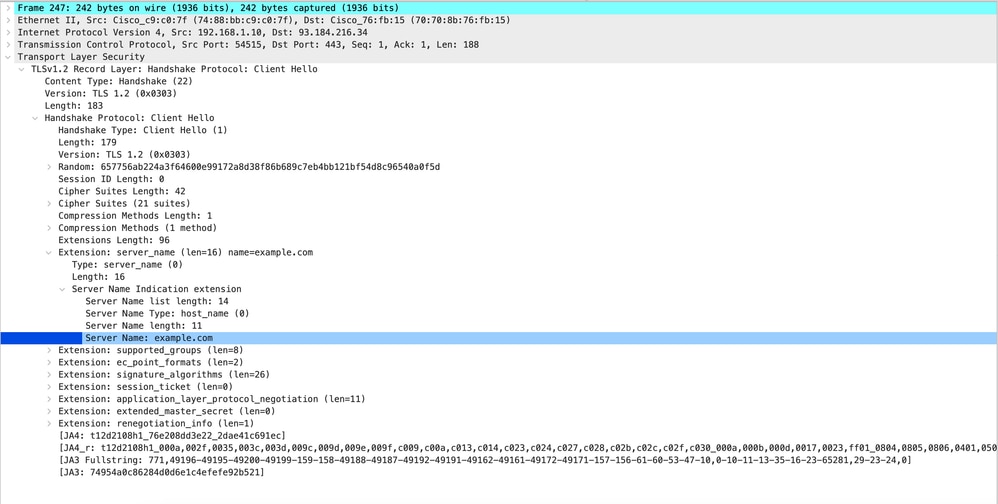 影象 — 客戶端Hello - Web伺服器的代理 — 透明 — 無身份驗證
影象 — 客戶端Hello - Web伺服器的代理 — 透明 — 無身份驗證

附註:此處觀察的密碼套件與從使用者端到SWA的使用者端Hello中的密碼套件不同,因為設定為解密此流量的SWA使用自己的密碼。

提示:在Server Key Exchange from SWA to Web Server中,顯示Web Server證書。但是,如果上游代理找到您的SWA的配置,則會顯示其證書而不是Web伺服器證書。
以下是存取日誌的範例:
1702319784.943 558 192.168.1.10 TCP_MISS_SSL/200 0 TCP_CONNECT 10.184.216.34:443 - DIRECT/www.example.com - DECRYPT_ADMIN_DEFAULT_ACTION_7-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",0.00,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 940, User Agent = -, AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 0, Response Header = 0, Client Body = 50 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 45, Client Body = 0, 1st response byte = 0, Response header = 0, Server response = 249, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 5, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 558>, AMP total = 558<; Latency = 50; "11/Dec/2023:19:36:24 +0100" ][Client Port = 54515, Server IP = 10.184.216.34, Server Port = 443]
1702319785.190 247 192.168.1.10 TCP_MISS_SSL/200 1676 GET https://www.example.com:443/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",54.28,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 960, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 50, Response Header = 50, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 97, Client Body = 0, 1st response byte = 48, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 247>, AMP total = 247<; Latency = 97; "11/Dec/2023:19:36:25 +0100" ][Client Port = 54515, Server IP = 10.184.216.34, Server Port = 443]
附註:正如您在HTTPS流量的透明部署中所看到的,Accesslogs中有兩行,第一行是流量被加密時,您可以看到TCP_CONNECT和Web伺服器的IP地址。如果在SWA中啟用解密,則第二行包含GET,並且整個URL以HTTPS開頭,這表示流量已解密,SWA知道該URL。
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
13-May-2024
|
初始版本 |
由思科工程師貢獻
- Amirhossein MojarradTechnical Consulting Engineer
 意見
意見