在FTD上使用IKEv2設定VRF感知站台對站台通道
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本文檔介紹如何在由Firepower管理中心(FMC)管理的Firepower威脅防禦(FTD)上配置虛擬路由和轉發(VRF)感知IKEv2站點到站點VPN隧道。
必要條件
需求
思科建議您瞭解以下主題:
- 對VPN的基本瞭解
- 體驗FMC
- 瞭解VRF實施
採用元件
本檔案中的資訊是根據以下軟體版本:
- Cisco FMC版本7.x
- Cisco FTD版本7.x

注意:本文檔中的資訊是根據特定實驗室環境中的裝置建立的。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
虛擬路由和轉送
在虛擬路由中,您可以建立多個虛擬路由器,為介面組維護單獨的路由表,從而實現網路分離。這樣無需使用多個裝置即可分段網路路徑,從而增強了功能。
由於路由例項是獨立的,因此可以使用重疊的IP地址而不會彼此衝突。每個VRF都有自己的路由協定會話以及IPv4和IPv6路由表。
限制
- 位於任何VRF例項中的介面不能用作隧道終端/VPN介面。
- 用於終止VPN隧道的介面只能位於全局VRF中。
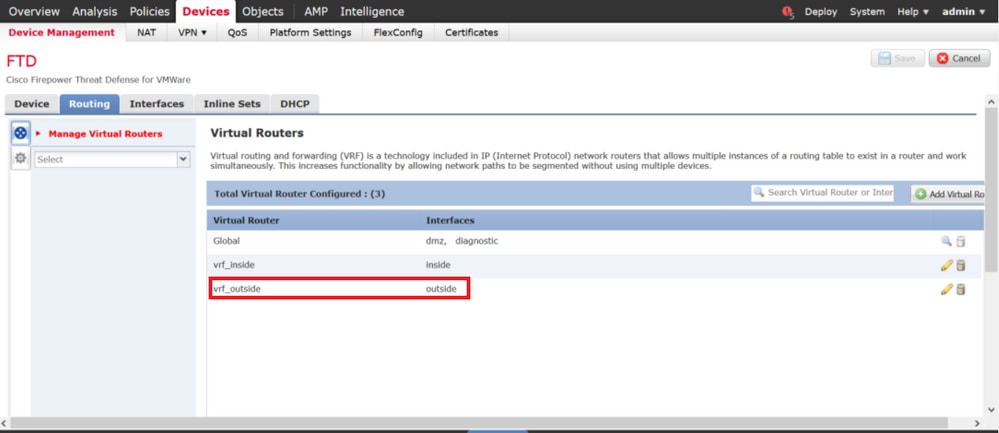
限制1
如果將 outside 介面增加到虛擬路由器 vrf_outside 中,則在建立站點到站點VPN拓撲時,該介面不會顯示在用於選擇終端介面的下拉選單中。
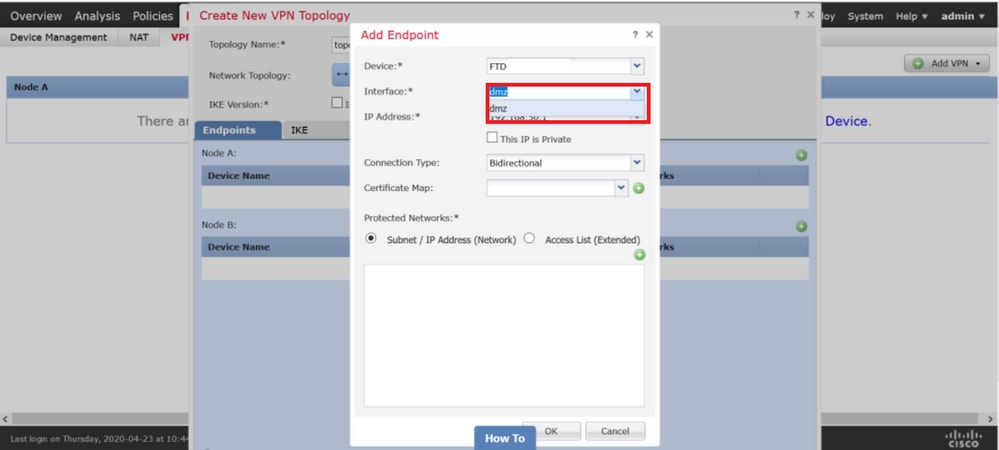
限制2
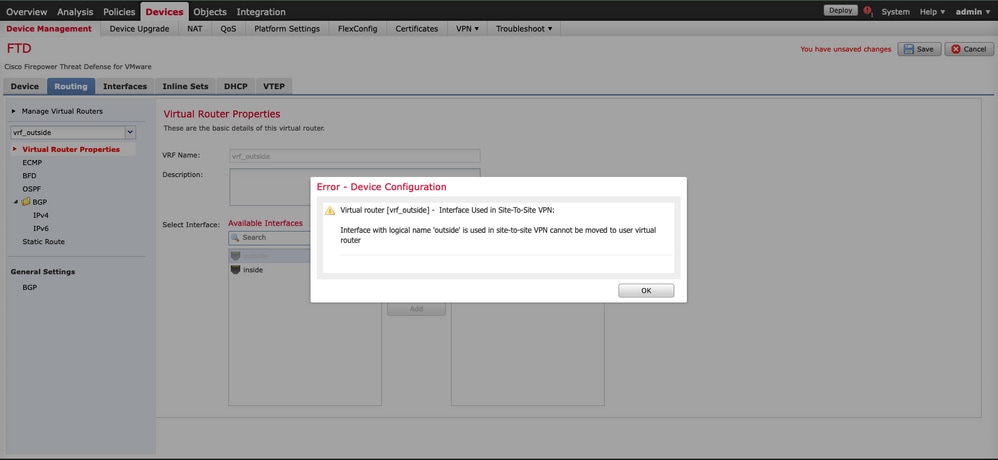
限制2如果outside 介面上存在站點到站點VPN拓撲,則無法將介面增加到VRF例項。FMC提供的錯誤表明,充當VPN隧道的 outside (WAN)介面將終端終止為全局VRF的一部分,而不是自定義VRF。
網路圖表
網路圖表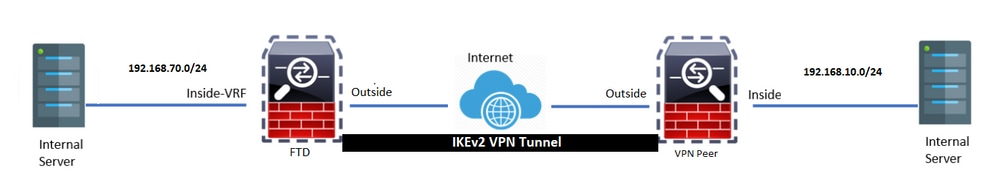
設定
設定在FTD 7.x和任何其他裝置(ASA/FTD/路由器或第三方供應商)之間配置IKEv2站點到站點VPN隧道。

注意:本文檔假定已配置站點到站點VPN隧道。有關更多詳細資訊,請參閱如何在由FMC管理的FTD上配置站點到站點VPN。
導航到 Devices > Device Management。點選 Edit ,然後選擇Routing。
步驟 1.按一下 Manage Virtual Routers如圖所示。
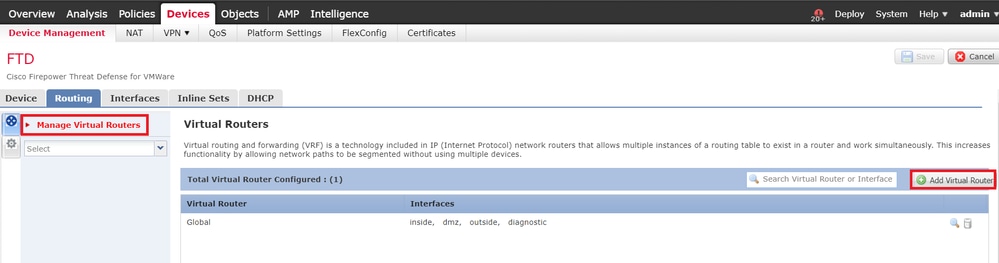
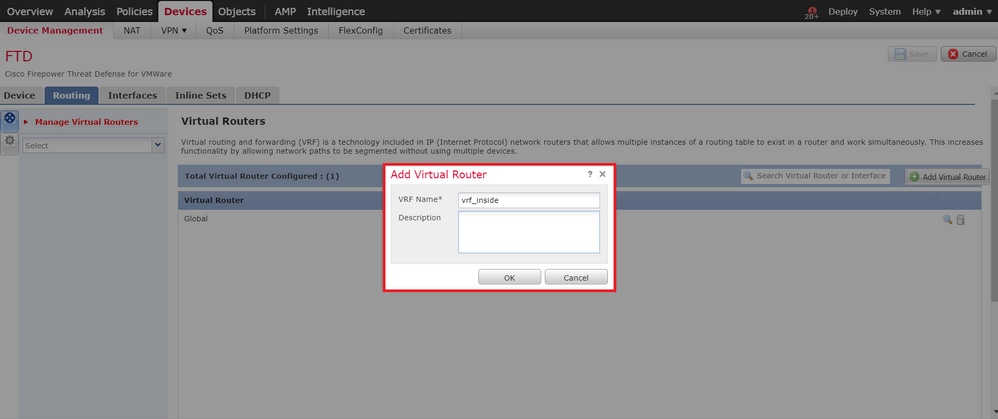
步驟 2.點選 Add Virtual Router 並將所需的VRF例項增加到其中。對於此部署,vrf_inside使用。
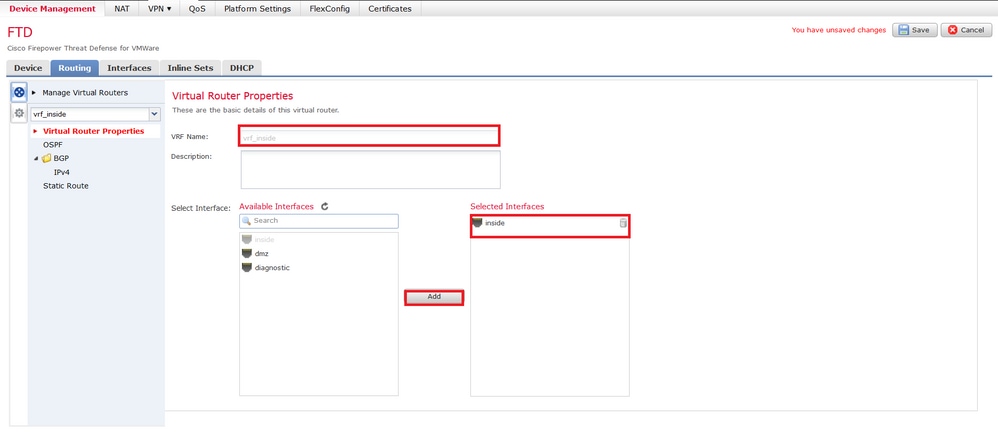
步驟 3.建立VRF例項後,將顯示增加所需介面的選項。對於此部署,inside將介面增加到vrf_inside,如下圖所示。
步驟 4.對於此部署,這些是站點到站點VPN隧道的流量選擇器。
Source: 192.168.70.0/24 [This network is on inside interface which is in "vrf_inside"] 192.168.80.0/24 [This network is on dmz interface which is not in any vrf instance] Destination : 192.168.10.0/24路由洩漏
路由洩漏VRF允許路由器為不同的虛擬網路維護單獨的路由表。需要例外時,VRF路由洩漏允許在VRF之間路由某些流量。全局路由表(GRT)和虛擬路由和轉發(VRF)表之間的路由洩漏是使用靜態路由完成的。這兩種方法都提供下一跳IP地址(用於多接入網段)或將路由引出介面(點對點介面)。
從VRF到全局的路由洩漏
從VRF到全局的路由洩漏- 選擇
Devices > Device Management,然後按一下Edit以訪問FTD。 - 按一下
Routing。依照預設,會顯示「全域路由特性」頁面。 - 按一下
Static Route。 - 按一下
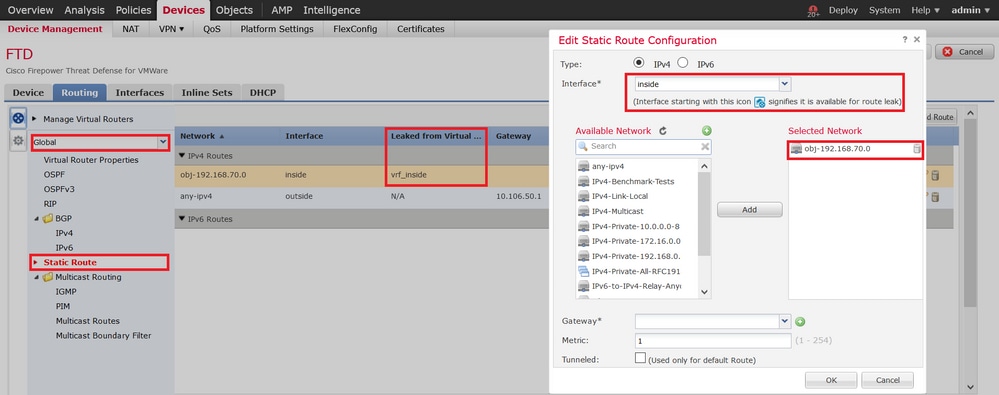
Add Route, configure:
· Interface — 選擇內部介面。
· Network— 選擇vrf_inside虛擬路由器網路對象(192.168.70.0/24)。
· Gateway— 保留為空。將路由洩漏到另一個虛擬路由器時,請勿選擇網關。
路由洩漏允許受站點到站點VPN的外部(遠端)終端保護的終端訪問vrf_inside虛擬路由器中的192.168.70.0/24網路。
5. 按一下OK 如下圖所示。
在CLI上,路由顯示為:
route inside 192.168.70.0 255.255.255.0 1 請注意,網路192.168.70.0/24直接連線到inside介面,但此網路在GRT中不可見,因為該網路位於VRF例項中。為了使該路由在GRT中可用,該路由已從vrf_inside洩露到Global。
從全局到VRF的路由洩漏
從全局到VRF的路由洩漏- 選擇
Devices > Device Management,然後按一下Edit。 - 按一下
Routing,然後從下拉選單中選擇vrf_inside。 - 按一下
Static Route。 - 按一下
Add Route , configure:
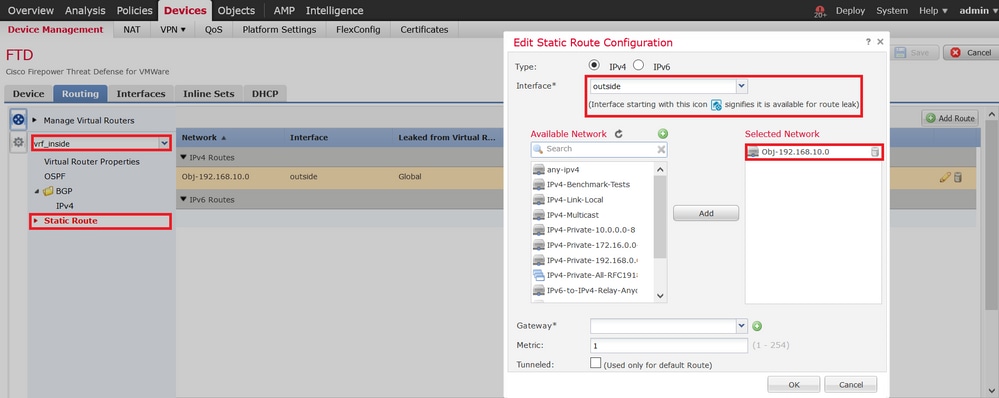
· Interface - 選擇全局路由器的外部介面
· Network— 選擇全局虛擬路由器網路對象(192.168.10.0/24)
· Gateway— 保留為空。將路由洩漏到另一個虛擬路由器時,請勿選擇網關
此靜態路由允許192.168.70.0/24網路上的終端發起透過站點到站點VPN隧道與192.168.10.0/24的連線。
5. 按一下OK如下圖所示。
在CLI上,路由顯示為:
route vrf vrf_inside outside 192.168.10.0 255.255.255.0 1驗證
驗證使用本節內容,確認您的組態是否正常運作。所有輸出都是從網路圖中所示的FTD收集而來。
FTD# show vrf Name VRF ID Description Interfaces vrf_inside 1 inside FTD# show run route route outside 10.0.0.0 255.0.0.0 10.106.50.1 1 route inside 192.168.70.0 255.255.255.0 1 FTD# show run route vrf vrf_inside route vrf vrf_inside outside 192.168.10.0 255.255.255.0 1FTD# show route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, + - replicated route Gateway of last resort is not set S 10.0.0.0 255.0.0.0 [1/0] via 10.106.50.1, outside C 10.106.50.0 255.255.255.0 is directly connected, outside L 10.106.50.212 255.255.255.255 is directly connected, outside V 192.168.10.0 255.255.255.0 connected by VPN (advertised), outside S 192.168.70.0 255.255.255.0 [1/0] is directly connected, inside C 192.168.80.0 255.255.255.0 is directly connected, dmz L 192.168.80.1 255.255.255.255 is directly connected, dmz FTD# show crypto ikev2 sa IKEv2 SAs: Session-id:8, Status:UP-ACTIVE, IKE count:1, CHILD count:1 Tunnel-id Local Remote Status Role 444445753 10.106.50.212/500 10.197.224.175/500 READY RESPONDER Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:19, Auth sign: PSK, Auth verify: PSK Life/Active Time: 86400/11 sec Child sa: local selector 192.168.70.0/0 - 192.168.70.255/65535 remote selector 192.168.10.0/0 - 192.168.10.255/65535 ESP spi in/out: 0x5e950adb/0x47acd2dc FTD# show crypto ipsec sa peer 10.197.224.175 peer address: 10.197.224.175 Crypto map tag: CSM_outside_map, seq num: 2, local addr: 10.106.50.212 access-list vrf-crypto-acl extended permit ip 192.168.70.0 255.255.255.0 192.168.10.0 255.255.255.0 local ident (addr/mask/prot/port): (192.168.70.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0) current_peer: 10.197.224.175 #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 4, #pkts comp failed: 0, #pkts decomp failed: 0 #pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0 #PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0 #TFC rcvd: 0, #TFC sent: 0 #Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0 #send errors: 0, #recv errors: 0 local crypto endpt.: 10.106.50.212/500, remote crypto endpt.: 10.197.224.175/500 path mtu 1500, ipsec overhead 74(44), media mtu 1500 PMTU time remaining (sec): 0, DF policy: copy-df ICMP error validation: disabled, TFC packets: disabled current outbound spi: 47ACD2DC current inbound spi : 5E950ADB inbound esp sas: spi: 0x5E950ADB (1586825947) SA State: active transform: esp-aes-256 esp-sha-hmac no compression in use settings ={L2L, Tunnel, IKEv2, } slot: 0, conn_id: 10, crypto-map: CSM_outside_map sa timing: remaining key lifetime (kB/sec): (4193279/28774) IV size: 16 bytes replay detection support: Y Anti replay bitmap: 0x00000000 0x0000001F outbound esp sas: spi: 0x47ACD2DC (1202508508) SA State: active transform: esp-aes-256 esp-sha-hmac no compression in use settings ={L2L, Tunnel, IKEv2, } slot: 0, conn_id: 10, crypto-map: CSM_outside_map sa timing: remaining key lifetime (kB/sec): (4147199/28774) IV size: 16 bytes replay detection support: Y Anti replay bitmap: 0x00000000 0x00000001 疑難排解
疑難排解本節提供的資訊可用於對組態進行疑難排解。
FTD# show crypto ipsec sa peer 10.197.224.175 peer address: 10.197.224.175 Crypto map tag: CSM_outside_map, seq num: 2, local addr: 10.106.50.212 access-list vrf-crypto-acl extended permit ip 192.168.70.0 255.255.255.0 192.168.10.0 255.255.255.0 local ident (addr/mask/prot/port): (192.168.70.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0) current_peer: 10.197.224.175 #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 >>>> Packets received from remote end gets decapsulated but there are not encaps for the responses #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0 #pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0 #PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0 #TFC rcvd: 0, #TFC sent: 0 #Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0 #send errors: 0, #recv errors: 0 local crypto endpt.: 10.106.50.212/500, remote crypto endpt.: 10.197.224.175/500 path mtu 1500, ipsec overhead 74(44), media mtu 1500 PMTU time remaining (sec): 0, DF policy: copy-df ICMP error validation: disabled, TFC packets: disabled current outbound spi: 490F4CD1 current inbound spi : DB5608EB inbound esp sas: spi: 0xDB5608EB (3679848683) SA State: active transform: esp-aes-256 esp-sha-hmac no compression in use settings ={L2L, Tunnel, IKEv2, } slot: 0, conn_id: 11, crypto-map: CSM_outside_map sa timing: remaining key lifetime (kB/sec): (4008959/28761) IV size: 16 bytes replay detection support: Y Anti replay bitmap: 0x00000000 0x0000001F outbound esp sas: spi: 0x490F4CD1 (1225739473) SA State: active transform: esp-aes-256 esp-sha-hmac no compression in use settings ={L2L, Tunnel, IKEv2, } slot: 0, conn_id: 11, crypto-map: CSM_outside_map sa timing: remaining key lifetime (kB/sec): (4239360/28761) IV size: 16 bytes replay detection support: Y Anti replay bitmap: 0x00000000 0x00000001 capture capin type raw-data interface inside [Capturing - 0 bytes] >>>> Captures applied on LAN(inside) interface shows decapsulated packets are not routed into LAN network match ip host 192.168.10.2 host 192.168.70.2 FTD# show cap capin 0 packet captured 0 packet shown capture asp type asp-drop all [Capturing - 0 bytes] >>>> ASP Captures shows decapsulated packets are being dropped on FTD FTD# show capture asp | i 192.168.70.2 145: 15:28:47.670894 192.168.10.2 > 192.168.70.2 icmp: echo request 154: 15:28:49.666545 192.168.10.2 > 192.168.70.2 icmp: echo request 171: 15:28:51.672740 192.168.10.2 > 192.168.70.2 icmp: echo request 172: 15:28:53.664928 192.168.10.2 > 192.168.70.2 icmp: echo request FTD# packet-tracer input outside icmp 192.168.10.2 8 0 192.168.70.2 detailed >>>> Packet tracer from outside shows "no route" for 192.168.70.0/24 network Phase: 1 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: Forward Flow based lookup yields rule: in id=0x2ba3bce77330, priority=1, domain=permit, deny=false hits=171480, user_data=0x0, cs_id=0x0, l3_type=0x8 src mac=0000.0000.0000, mask=0000.0000.0000 dst mac=0000.0000.0000, mask=0100.0000.0000 input_ifc=outside, output_ifc=any Result: input-interface: outside(vrfid:0) input-status: up input-line-status: up Action: drop Drop-reason: (no-route) No route to host, Drop-location: frame 0x000055d9b7e8c7ce flow (NA)/NA FTD# show run route route outside 10.0.0.0 255.0.0.0 10.106.50.1 1 >>>> As the network 192.168.70.0/24 is in "vrf_inside" instance, there is no route leaked from Global to vrf_inside FTD# show run route route outside 10.0.0.0 255.0.0.0 10.106.50.1 1 route inside 192.168.70.0 255.255.255.0 1 >>>> After leaking the route from Global to vrf_inside FTD# show cap capin >>>> Now capture shows bi-directional traffic on LAN(inside) interface 10 packets captured 1: 15:44:32.972743 192.168.10.2 > 192.168.70.2 icmp: echo request 2: 15:44:32.974543 192.168.70.2 > 192.168.10.2 icmp: echo reply 3: 15:44:33.032209 192.168.10.2 > 192.168.70.2 icmp: echo request 4: 15:44:33.033353 192.168.70.2 > 192.168.10.2 icmp: echo reply 5: 15:44:33.089656 192.168.10.2 > 192.168.70.2 icmp: echo request 6: 15:44:33.092814 192.168.70.2 > 192.168.10.2 icmp: echo reply 7: 15:44:33.149024 192.168.10.2 > 192.168.70.2 icmp: echo request 8: 15:44:33.151878 192.168.70.2 > 192.168.10.2 icmp: echo reply 9: 15:44:33.158774 192.168.10.2 > 192.168.70.2 icmp: echo request 10: 15:44:33.161048 192.168.70.2 > 192.168.10.2 icmp: echo reply 10 packets shown FTD# packet-tracer input outside icmp 192.168.10.2 8 0 192.168.70.2 detailed >>>> Verified packet flow using Packet tracer Phase: 1 Type: INPUT-ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: Found next-hop 0.0.0.0 using egress ifc inside(vrfid:1) -------------------Output Omitted------------------------
Phase: 8 Type: VPN Subtype: ipsec-tunnel-flow Result: ALLOW Config: Additional Information: Forward Flow based lookup yields rule: in id=0x2ba3bdc75cc0, priority=70, domain=ipsec-tunnel-flow, deny=false hits=7, user_data=0xea71cdc, cs_id=0x2ba3bce93e70, reverse, flags=0x0, protocol=0 src ip/id=192.168.10.0, mask=255.255.255.0, port=0, tag=any dst ip/id=192.168.70.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0 input_ifc=outside(vrfid:0), output_ifc=any -------------------Output Omitted------------------------ Phase: 13 Type: VPN Subtype: encrypt Result: ALLOW Config: Additional Information: Reverse Flow based lookup yields rule: out id=0x2ba3bd44ed40, priority=70, domain=encrypt, deny=false hits=7, user_data=0xea6e344, cs_id=0x2ba3bce93e70, reverse, flags=0x0, protocol=0 src ip/id=192.168.70.0, mask=255.255.255.0, port=0, tag=any dst ip/id=192.168.10.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0 input_ifc=any(vrfid:65535), output_ifc=outside Result: input-interface: outside(vrfid:0) input-status: up input-line-status: up output-interface: inside(vrfid:1) output-status: up output-line-status: up Action: drop Drop-reason: (ipsec-spoof) IPSEC Spoof detected, Drop-location: frame 0x000055d9b7e8b4d1 flow (NA)/NA 修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
23-Mar-2023
|
初始版本 |
由思科工程師貢獻
- Rishabh AggarwalCisco TAC Engineer
- Sadhana K SCisco TAC Engineer
- Nidhi KejriwalCisco TAC Engineer
 意見
意見