Melhore a produtividade no Catalyst 8000V com Multi-TxQs no AWS
Opções de download
Linguagem imparcial
O conjunto de documentação deste produto faz o possível para usar uma linguagem imparcial. Para os fins deste conjunto de documentação, a imparcialidade é definida como uma linguagem que não implica em discriminação baseada em idade, deficiência, gênero, identidade racial, identidade étnica, orientação sexual, status socioeconômico e interseccionalidade. Pode haver exceções na documentação devido à linguagem codificada nas interfaces de usuário do software do produto, linguagem usada com base na documentação de RFP ou linguagem usada por um produto de terceiros referenciado. Saiba mais sobre como a Cisco está usando a linguagem inclusiva.
Sobre esta tradução
A Cisco traduziu este documento com a ajuda de tecnologias de tradução automática e humana para oferecer conteúdo de suporte aos seus usuários no seu próprio idioma, independentemente da localização. Observe que mesmo a melhor tradução automática não será tão precisa quanto as realizadas por um tradutor profissional. A Cisco Systems, Inc. não se responsabiliza pela precisão destas traduções e recomenda que o documento original em inglês (link fornecido) seja sempre consultado.
Contents
Introdução
Este documento descreve como habilitar e utilizar Multi-TXQs no Catalyst 8000V implantado em ambientes AWS para melhorar o desempenho de throughput.
Informações de Apoio
A presença de várias filas simplifica e acelera o processo de mapeamento de pacotes de entrada e saída para um vCPU específico. Utilizar Multi-TXQs no Catalyst 8000V permite a utilização eficiente do núcleo através dos núcleos de dataplane disponíveis alocados, resultando em maior desempenho de throughput. Este artigo fornece uma visão geral simples de como os Multi-TXQs funcionam, como são configurados, mostra configurações de CLI de exemplo para implantações do Catalyst 8000V Autônomas e de SD-WAN e revisa comandos de solução de problemas para ajudar a encontrar gargalos de desempenho.
Comportamento do Catalyst 8000V quando não estiver usando Multi-TxQs
Até a versão de software 17.18, os pacotes que entram no Catalyst 8000V são distribuídos para todos os vCPU (núcleos de processamento de pacotes), independentemente dos fluxos. Quando o PP conclui o processamento do pacote, a ordem do fluxo é restaurada para ser enviada em uma interface.
Antes de colocar o pacote em uma fila de transmissão (TxQ), o Catalyst 8000V cria um TxQ por interface. Portanto, se houver apenas uma interface de saída disponível, vários fluxos irão para um TxQ.
O Catalyst 8000V não pode aproveitar esse processo Multi-TxQ se houver apenas uma interface disponível. Isso resulta em gargalos de desempenho de throughput e distribuição desigual de carga entre os núcleos de dataplane disponíveis. Se houver apenas uma interface de saída sendo usada para transmitir dados da instância do C8000V, haverá apenas um TxQ disponível para transmitir o tráfego de rede e possivelmente fazer com que os pacotes sejam descartados devido ao preenchimento mais rápido da fila única.
Como referência, você pode encontrar o modelo de arquitetura TxQ único para o Catalyst 8000V implantado no AWS aqui na Figura 1.
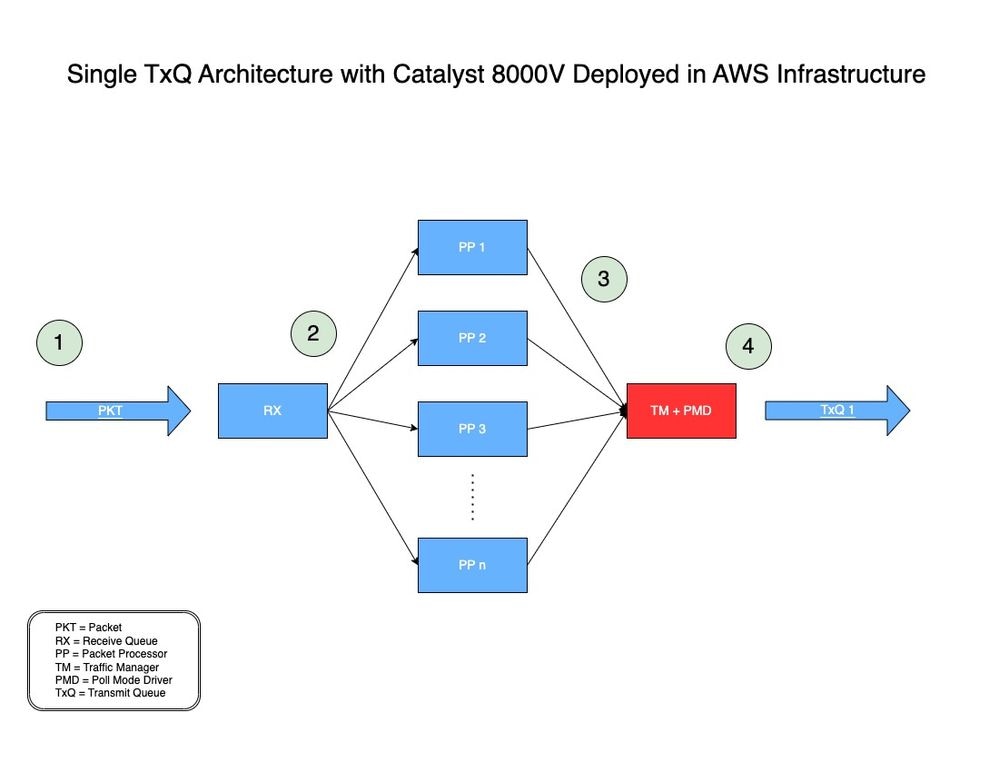
Figura 1: Modelo de arquitetura TxQ única para Catalyst 8000V implantado no AWS.
-
- Um pacote de rede (PKT) atravessa um VPC e é recebido na interface de entrada de um C8000V.
- O PKT é colocado em uma fila de recepção (RX) e, em seguida, é encaminhado para um mecanismo de processador de pacotes (PP) decidido por um algoritmo.
- Depois que o Packet Processor (PP) processa o pacote, ele o envia para o Traffic Manager (TM).
- No final do processamento da TM, um núcleo é responsável por colocar o pacote em um TxQ disponível, que é então encaminhado à interface de saída do Catalyst 8000V.
O que são Multi-TXQs na infraestrutura AWS
O AWS ENA fornece várias filas de transmissão (Multi-TxQ's) para reduzir a sobrecarga interna e aumentar a escalabilidade. A presença de várias filas simplifica e acelera o processo de mapeamento de pacotes de entrada e saída para um vCPU específico. O modelo de referência de rede AWS e DPDK é baseado em fluxo, onde cada vCPU processa um fluxo e transmite pacotes desse fluxo para uma fila de transmissão atribuída (TxQ). O par de filas RX/TX para cada vCPU é válido com base no modelo baseado em fluxo.
Como o Catalyst 8000V NÃO é baseado em fluxo, a instrução "par de filas RX/TX para cada vCPU" não se aplica ao Catalyst 8000V.
Nesse caso, as filas RX/TX não são por vCPU, mas por interface. As filas RX/TX atuam como interfaces entre o aplicativo (Catalyst 8000V) e a infraestrutura/hardware AWS para enviar tráfego de dados/rede. O AWS controla a velocidade e o número de filas RX/TX disponíveis por interface com base em cada instância.
O Catalyst 8000V deve ter várias interfaces para criar vários TxQs. Para manter a ordem de fluxo com vários fluxos saindo de uma interface (quando o Catalyst 8000V permite vários TxQs seguindo esse processo), o Catalyst 8000V mistura fluxos com base nas 5 tuplas para selecionar o TxQ apropriado. Um usuário pode criar várias interfaces no Catalyst 8000V usando a mesma NIC física conectada à instância usando interfaces de loopback ou endereços IP secundários.
Na Figura 2, você pode descobrir como um pacote é processado usando a arquitetura Multi-TxQ com o Catalyst 8000V no AWS.
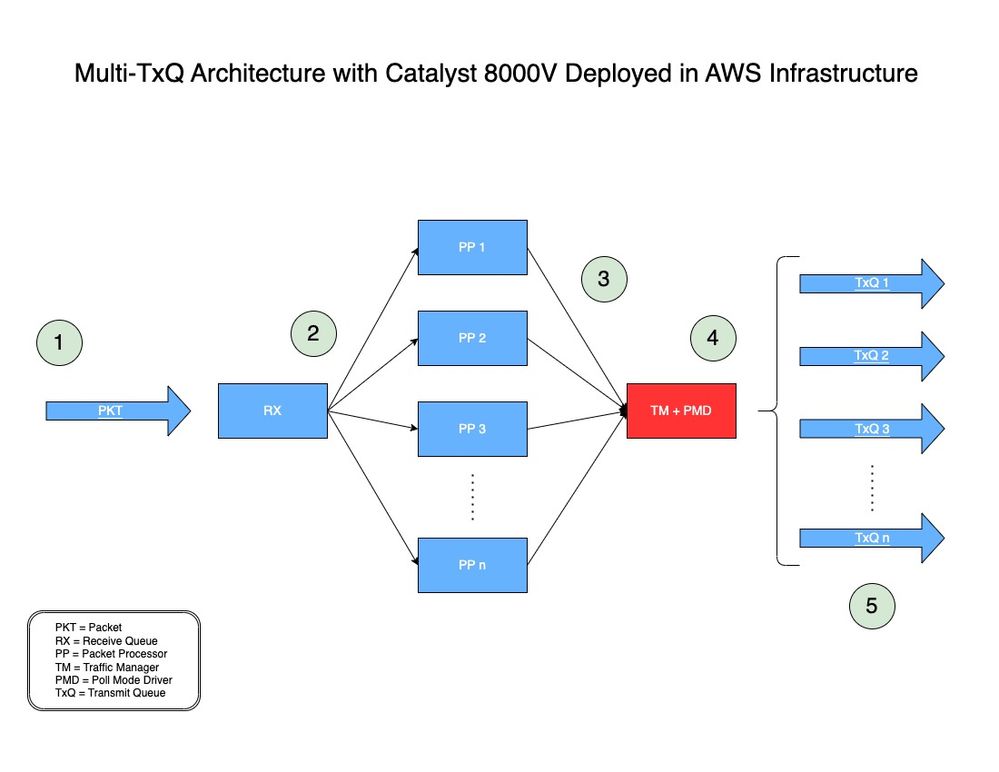
Figura 2: Modelo de arquitetura Multi-TxQ para Catalyst 8000V implantado no AWS.
-
- Um pacote de rede (PKT) atravessa um VPC e é recebido na interface de entrada de um C8000V.
- O PKT é colocado em uma fila de recepção (RX) e, em seguida, é encaminhado para um mecanismo de processador de pacotes (PP) decidido por um algoritmo.
- Depois que o Packet Processor (PP) processa o pacote, ele o envia para o Traffic Manager (TM).
- No final do processamento da TM, antes de colocar o pacote em uma fila de transmissão (TxQ), a TM examina o cabeçalho do pacote e mistura o pacote (explicado na próxima seção). Outro componente, o PMD (Poll Mode Driver), é usado para configurar o número de TXQs suportados pela instância. Um núcleo é dedicado à função TM + PMD que faz o hash e o envio do pacote para o TxQ atribuído.
- O TxQ é escolhido com base nas cinco tuplas hash e módulo com o número de TxQ suportado pela instância. Os pacotes são colocados no TxQ selecionado e encaminhados para a interface de saída do Catalyst 8000V.
Como o tráfego é dividido em vários TxQs
No final do processamento da TM conforme mostrado na Etapa 4 da Figura 2, antes de colocar o pacote em um TxQ, a TM examina o cabeçalho do pacote e extrai as 5 tuplas (endereço de destino, endereço de origem, protocolo, porta de destino e porta de origem) e mistura o pacote em um TxQ.
O TxQ é escolhido com base nas cinco tuplas hash e módulo com o número de TxQ suportado pela instância.
Versões do software Catalyst 8000V que suportam Multi-TxQs
As instâncias AWS EC2 do mesmo tipo de família de instâncias suportam um número diferente de TXQs, dependendo do tamanho da instância. O C8000V começou a suportar vários TxQs a partir do IOS® XE 17.7.
Iniciando no IOS® XE 17.7, o C8000V suporta vários TxQs no C5n.9xlarge que pode ter até 8 TXQs.
Iniciando no IOS® XE 17.9, o C8000V suporta o tamanho de instância C5n.18xlarge, que pode ter até 12 TXQs (50% mais que C5n.9xlarge).
Embora o Multi-TxQ seja suportado pelo IOS® XE 17.7, é ALTAMENTE recomendado usar o IOS® XE 17.9 para o ciclo de vida do software e para recursos de desempenho de throughput mais alto com suporte a 12 TxQ.
Como projetar o esquema de endereçamento IP para computar o hashing
Para criar um hash uniforme do tráfego entre todos os TxQs disponíveis, é necessário usar endereços IP especiais quando o Catalyst 8000V estiver encerrando túneis IPsec/GRE.
Há scripts públicos disponíveis para gerar esses endereços IP especiais a serem usados para configurar as interfaces do Catalyst 8000V que são responsáveis pela terminação desses túneis. Esta seção fornece instruções sobre como fazer o download e usar os scripts para criar os endereços IP necessários para até mesmo o hashing de Multi-TxQ.
Se o Catalyst 8000V estiver lidando com tráfego de texto claro como o TCP/UDP, nenhum esquema especial de endereçamento IP será necessário.
As instruções originais podem ser encontradas aqui: https://github.com/CiscoDevNet/python-c8000v-aws-multitx-queues/
Note: Para o Catalyst 8000V executando a versão 17.18 ou posterior, os pacotes estão sendo distribuídos de forma diferente. Portanto, um algoritmo de hash diferente precisa ser usado.
Pré-requisitos
- Deve possuir Linux/MacOS ou uma máquina Windows capaz de executar scripts Python.
- Verificar se a versão do Python é 3.8.9 ou superior; verifique a versão Python com 'python3 —version'
- Instale o PIP caso ainda não esteja instalado. Caso contrário, execute:
- curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
- python3 get-pip.py
Você pode verificar qual versão do Python sua máquina está usando com o comando 'python3 —version'.
user@computer ~ % python3 --version
Python 3.9.6
Depois que a versão do Python tiver sido verificada e estiver em execução, uma versão igual ou superior à 3.8.9, instale a versão mais recente do PIP.
user@computer ~ % curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2570k 100 2570k 0 0 6082k 0 --:--:-- --:--:-- --:--:-- 6135k
user@computer ~ % python3 get-pip.py
Defaulting to user installation because normal site-packages is not writeable
Collecting pip
Downloading pip-23.3.1-py3-none-any.whl.metadata (3.5 kB)
Downloading pip-23.3.1-py3-none-any.whl (2.1 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 2.1/2.1 MB 7.4 MB/s eta 0:00:00
Installing collected packages: pip
WARNING: The scripts pip, pip3 and pip3.9 are installed in '/Users/name/Library/Python/3.9/bin' which is not on PATH.
Consider adding this directory to PATH or, if you prefer to suppress this warning, use --no-warn-script-location.
Successfully installed pip-23.3.1
[notice] A new release of pip is available: 21.2.4 -> 23.3.1
[notice] To update, run: /Applications/Xcode.app/Contents/Developer/usr/bin/python3 -m pip install --upgrade pip
Criar Ambiente Virtual
Depois que os pré-requisitos tiverem sido instalados, crie o ambiente virtual e baixe o script de hash de endereço IP usado para gerar o esquema de endereço IP exclusivo para Multi-TxQ.
Resumo dos comandos:
- python3 -m venv c8kv-hash
- cd c8kv-hash
- bin/ativate de origem
- git clone https://github.com/CiscoDevNet/python-c8000v-aws-multitx-queues/
- cd c8kv-aws-pmd-hash
- python3 -m pip install — upgrade pip
- pip install -r requirements.txt
Ambientes virtuais em Python são usados para criar espaços de trabalho isolados que não afetam outros projetos ou dependências. Crie o ambiente virtual 'c8kv-hash' usando este comando:
user@computer Desktop % python3 -m venv c8kv-hashNavegue dentro do ambiente virtual para a pasta 'c8kv-hash' (criada anteriormente).
user@computer Desktop % cd c8kv-hashAtive o ambiente virtual.
user@computer c8kv-hash % source bin/activateClonar o repositório que tem o script Python de hash Multi-TxQ.
(c8kv-hash) user@computer c8kv-hash % git clone https://github.com/CiscoDevNet/python-c8000v-aws-multitx-queues.git
Cloning into 'c8kv-aws-pmd-hash'...
remote: Enumerating objects: 82, done.
remote: Counting objects: 100% (82/82), done.
remote: Compressing objects: 100% (59/59), done.
remote: Total 82 (delta 34), reused 57 (delta 19), pack-reused 0
Receiving objects: 100% (82/82), 13.01 KiB | 2.60 MiB/s, done.
Resolving deltas: 100% (34/34), done.
Quando o repositório tiver sido clonado, navegue até a pasta 'c8kv-aws-pmd-hash'. Como ele está localizado no ambiente virtual criado, instale a versão mais recente do PIP.
(c8kv-hash) user@computer c8kv-hash % cd c8kv-aws-pmd-hash
(c8kv-hash) user@computer c8kv-aws-pmd-hash % python3 -m pip install --upgrade pip
Requirement already satisfied: pip in /Users/name/Desktop/c8kv-hash/lib/python3.9/site-packages (21.2.4)
Collecting pip
Downloading pip-23.3.1-py3-none-any.whl (2.1 MB)
|████████████████████████████████| 2.1 MB 2.7 MB/s
Installing collected packages: pip
Attempting uninstall: pip
Found existing installation: pip 21.2.4
Uninstalling pip-21.2.4:
Successfully uninstalled pip-21.2.4
Successfully installed pip-23.3.1
Depois que o PIP tiver sido atualizado, instale as dependências encontradas no arquivo requirements.txt na pasta.
(c8kv-hash) user@computer c8kv-aws-pmd-hash % pip install -r requirements.txt
Collecting crc32c==2.3 (from -r requirements.txt (line 1))
Downloading crc32c-2.3-cp39-cp39-macosx_11_0_arm64.whl (27 kB)
Installing collected packages: crc32c
Successfully installed crc32c-2.3O ambiente virtual agora está atualizado e pode ser usado para gerar o esquema de endereços IP para Multi-TxQ.
Calcular o esquema de endereços IP usando o script de índice de hash Python para as versões 17.7 e 17.8 (reprovação)

Note: OS SCRIPTS DE HASH 7.7 E 17.8 SERÃO SUBSTITUÍDOS EM BREVE. É ALTAMENTE RECOMENDÁVEL USAR O SCRIPT DE HASH 17.9
Resumo dos comandos:
- python3 c8kv_multitxq_hash.py —old_crc 1 —dest_network 192.168.1.0/24 —src_network 192.168.2.0/24 --unique_hash 1
'—old_crc 1' gera um índice de hash baseado nas versões 17.7 e 17.8 com módulo 8 para corresponder ao PMD TXQ suportado (NÃO modifique)
'—dest_network' define a sub-rede do endereço da rede de destino (modifique com base no esquema de endereços IP da rede)
'—src_network' define a sub-rede do endereço de rede de origem (modifique com base no esquema de endereços IP da rede)
'—unique_hash 1' gera um conjunto (8 pares para 8 TXQs) de endereços IP com hash exclusivos. Isso pode ser modificado.
(c8kv-hash) user@computer c8kv-aws-pmd-hash % python3 c8kv_multitxq_hash.py --old_crc 1 --dest_network 192.168.1.0/24 --src_network 192.168.2.0/24 --unique_hash 1
Dest: Src: Prot dstport srcport Hash: Rev-hash:
192.168.1.0 192.168.2.0 2 5
192.168.1.0 192.168.2.1 2 7
192.168.1.0 192.168.2.2 2 1
192.168.1.0 192.168.2.3 2 3
192.168.1.0 192.168.2.4 2 5
192.168.1.0 192.168.2.5 2 7
192.168.1.0 192.168.2.6 2 1
192.168.1.0 192.168.2.7 2 3
192.168.1.0 192.168.2.8 2 5
192.168.1.0 192.168.2.9 2 7
192.168.1.0 192.168.2.10 2 1
.
. ### trimmed output ###
.
192.168.1.255 192.168.2.247 5 2
192.168.1.255 192.168.2.248 5 4
192.168.1.255 192.168.2.249 5 6
192.168.1.255 192.168.2.250 5 0
192.168.1.255 192.168.2.251 5 2
192.168.1.255 192.168.2.252 5 4
192.168.1.255 192.168.2.253 5 6
192.168.1.255 192.168.2.254 5 0
192.168.1.255 192.168.2.255 5 2
Unique hash:
------ Tunnels set 0 ---------
192.168.1.37<===>192.168.2.37<===>0
192.168.1.129<===>192.168.2.129<===>1
192.168.1.36<===>192.168.2.36<===>2
192.168.1.128<===>192.168.2.128<===>3
192.168.1.39<===>192.168.2.39<===>4
192.168.1.131<===>192.168.2.131<===>5
192.168.1.38<===>192.168.2.38<===>6
192.168.1.130<===>192.168.2.130<===>7
Calcular o esquema de endereços IP usando o script de índice de hash Python para as versões 17.9 e posteriores
Resumo dos comandos:
- python3 c8kv_multitxq_hash.py —dest_network 192.168.1.0/24 —src_network 192.168.2.0/24 —prot udp —src_port 12346 —dst_port 12346 —unique_hash 1
Observe que no IOS® XE versão 17.9 e posterior, o script usa o módulo 12 sem a opção —old_crc, correspondendo ao PMD TXQ suportado.
'—dest_network' define a sub-rede do endereço da rede de destino (modifique com base no esquema de endereços IP da rede)
'—src_network' define a sub-rede do endereço de rede de origem (modifique com base no esquema de endereços IP da rede)
'—prot udp' define o protocolo usado. O usuário pode especificar o parâmetro do protocolo como "gre" ou "tcp" ou "udp" ou qualquer valor decimal (OPCIONAL)
'—src_port' define a porta de origem usada (OPCIONAL)
'—dst_port' define a porta de destino usada (OPCIONAL)
'—unique_hash 1' gera um conjunto (12 pares para 12 TXQs) de endereços IP com hash exclusivos. Isso pode ser modificado.
(c8kv-hash) user@computer c8kv-aws-pmd-hash % python3 c8kv_multitxq_hash.py --dest_network 192.168.1.0/24 --src_network 192.168.2.0/24 --prot udp --src_port 12346 --dst_port 12346 --unique_hash 1
Dest: Src: Prot dstport srcport Hash: Rev-hash:
192.168.1.0 192.168.2.0 17 12346 12346 ==> 4 4 <-- Unique Hash Value
192.168.1.0 192.168.2.1 17 12346 12346 ==> 4 4
192.168.1.0 192.168.2.2 17 12346 12346 ==> 8 8 <-- Unique Hash Value
192.168.1.0 192.168.2.3 17 12346 12346 ==> 0 0 <-- Unique Hash Value
192.168.1.0 192.168.2.4 17 12346 12346 ==> 0 0
192.168.1.0 192.168.2.5 17 12346 12346 ==> 0 0
192.168.1.0 192.168.2.6 17 12346 12346 ==> 4 4
192.168.1.0 192.168.2.7 17 12346 12346 ==> 0 0
192.168.1.0 192.168.2.8 17 12346 12346 ==> 9 9 <-- Unique Hash Value
192.168.1.0 192.168.2.9 17 12346 12346 ==> 9 9
192.168.1.0 192.168.2.10 17 12346 12346 ==> 9 9
192.168.1.0 192.168.2.11 17 12346 12346 ==> 1 1 <-- Unique Hash Value
192.168.1.0 192.168.2.12 17 12346 12346 ==> 1 1
.
. ### trimmed output ###
.
192.168.1.255 192.168.2.250 17 12346 12346 ==> 1 1
192.168.1.255 192.168.2.251 17 12346 12346 ==> 1 1
192.168.1.255 192.168.2.252 17 12346 12346 ==> 9 9
192.168.1.255 192.168.2.253 17 12346 12346 ==> 1 1
192.168.1.255 192.168.2.254 17 12346 12346 ==> 5 5 <-- Unique Hash Value
192.168.1.255 192.168.2.255 17 12346 12346 ==> 9 9
Unique hash:
------ Tunnels set 0 ---------
192.168.1.38 <===> 192.168.2.38<===>0
192.168.1.37 <===> 192.168.2.37<===>1
192.168.1.53 <===> 192.168.2.53<===>2
192.168.1.39 <===> 192.168.2.39<===>3
192.168.1.48 <===> 192.168.2.48<===>4
192.168.1.58 <===> 192.168.2.58<===>5
192.168.1.42 <===> 192.168.2.42<===>6
192.168.1.46 <===> 192.168.2.46<===>7
192.168.1.40 <===> 192.168.2.40<===>8
192.168.1.43 <===> 192.168.2.43<===>9
192.168.1.36 <===> 192.168.2.36<===>10
192.168.1.56 <===> 192.168.2.56<===>11
Exemplo de configuração de topologia e CLI usando 8 TXQs com interfaces de loopback

Figura 3: Exemplo de topologia que usa oito TxQs usando interfaces de loopback.
Este é um exemplo de configuração CLI para 'c8kv-out' (Figura 3) que cria oito túneis IPsec com interfaces de loopback usando os endereços IP com hash calculados (192.168.1.X) da seção anterior.
Uma configuração semelhante se aplicaria ao outro ponto final do roteador (c8kv-peer) com os oito endereços IP com hash calculados restantes (192.168.2.X).
ip cef load-sharing algorithm include-ports source destination 00ABC123
crypto keyring tunnel0
local-address Loopback0
pre-shared-key address 192.168.2.37 key cisco
crypto keyring tunnel1
local-address Loopback1
pre-shared-key address 192.168.2.129 key cisco
crypto keyring tunnel2
local-address Loopback2
pre-shared-key address 192.168.2.36 key cisco
crypto keyring tunnel3
local-address Loopback3
pre-shared-key address 192.168.2.128 key cisco
crypto keyring tunnel4
local-address Loopback4
pre-shared-key address 192.168.2.39 key cisco
crypto keyring tunnel5
local-address Loopback5
pre-shared-key address 192.168.2.131 key cisco
crypto keyring tunnel6
local-address Loopback6
pre-shared-key address 192.168.2.38 key cisco
crypto keyring tunnel7
local-address Loopback7
pre-shared-key address 192.168.2.130 key cisco
crypto isakmp policy 200
encryption aes
hash sha
authentication pre-share
group 16
lifetime 28800
crypto isakmp profile isakmp-tunnel0
keyring tunnel0
match identity address 0.0.0.0
local-address Loopback0
crypto isakmp profile isakmp-tunnel1
keyring tunnel1
match identity address 0.0.0.0
local-address Loopback1
crypto isakmp profile isakmp-tunnel2
keyring tunnel2
match identity address 0.0.0.0
local-address Loopback2
crypto isakmp profile isakmp-tunnel3
keyring tunnel3
match identity address 0.0.0.0
local-address Loopback3
crypto isakmp profile isakmp-tunnel4
keyring tunnel4
match identity address 0.0.0.0
local-address Loopback4
crypto isakmp profile isakmp-tunnel5
keyring tunnel5
match identity address 0.0.0.0
local-address Loopback5
crypto isakmp profile isakmp-tunnel6
keyring tunnel6
match identity address 0.0.0.0
local-address Loopback6
crypto isakmp profile isakmp-tunnel7
keyring tunnel7
match identity address 0.0.0.0
local-address Loopback7
crypto ipsec transform-set ipsec-prop-vpn-tunnel esp-gcm 256
mode tunnel
crypto ipsec df-bit clear
crypto ipsec profile ipsec-vpn-tunnel
set transform-set ipsec-prop-vpn-tunnel
set pfs group16
interface Loopback0
ip address 192.168.1.37 255.255.255.255
!
interface Loopback1
ip address 192.168.1.129 255.255.255.255
!
interface Loopback2
ip address 192.168.1.36 255.255.255.255
!
interface Loopback3
ip address 192.168.1.128 255.255.255.255
!
interface Loopback4
ip address 192.168.1.39 255.255.255.255
!
interface Loopback5
ip address 192.168.1.131 255.255.255.255
!
interface Loopback6
ip address 192.168.1.38 255.255.255.255
!
interface Loopback7
ip address 192.168.1.130 255.255.255.255
!
interface Tunnel0
ip address 10.101.100.101 255.255.255.0
load-interval 30
tunnel source Loopback0
tunnel mode ipsec ipv4
tunnel destination 192.168.2.37
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel1
ip address 10.101.101.101 255.255.255.0
load-interval 30
tunnel source Loopback1
tunnel mode ipsec ipv4
tunnel destination 192.168.2.129
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel2
ip address 10.101.102.101 255.255.255.0
load-interval 30
tunnel source Loopback2
tunnel mode ipsec ipv4
tunnel destination 192.168.2.36
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel3
ip address 10.101.103.101 255.255.255.0
load-interval 30
tunnel source Loopback3
tunnel mode ipsec ipv4
tunnel destination 192.168.2.128
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel4
ip address 10.101.104.101 255.255.255.0
load-interval 30
tunnel source Loopback4
tunnel mode ipsec ipv4
tunnel destination 192.168.2.39
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel5
ip address 10.101.105.101 255.255.255.0
load-interval 30
tunnel source Loopback5
tunnel mode ipsec ipv4
tunnel destination 192.168.2.131
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel6
ip address 10.101.106.101 255.255.255.0
load-interval 30
tunnel source Loopback6
tunnel mode ipsec ipv4
tunnel destination 192.168.2.38
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel7
ip address 10.101.107.101 255.255.255.0
load-interval 30
tunnel source Loopback7
tunnel mode ipsec ipv4
tunnel destination 192.168.2.130
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface GigabitEthernet2
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
! ### IP route from servers to c8kv-uut
ip route 10.1.0.0 255.255.0.0 GigabitEthernet2 10.0.1.10
! ### IP routes from c8kv-uut to clients on c8kv-peer side, routes are evenly distributed to all 8 TXQ’s
ip route 10.10.0.0 255.255.0.0 Tunnel0
ip route 10.10.0.0 255.255.0.0 Tunnel1
ip route 10.10.0.0 255.255.0.0 Tunnel2
ip route 10.10.0.0 255.255.0.0 Tunnel3
ip route 10.10.0.0 255.255.0.0 Tunnel4
ip route 10.10.0.0 255.255.0.0 Tunnel5
ip route 10.10.0.0 255.255.0.0 Tunnel6
ip route 10.10.0.0 255.255.0.0 Tunnel7
! ### IP route from c8kv-uut Loopback int tunnel endpoint to c8kv-peer Loopback int tunnel endpoints
ip route 192.168.2.0 255.255.255.0 GigabitEthernet3 10.0.2.30 Exemplo de configuração de topologia e CLI usando 12 TXQs com interfaces de loopback

Figura 4. Exemplo de topologia que usa doze TxQs usando interfaces de loopback.
Este é um exemplo de configuração CLI para 'c8kv-out' (Figura 4) que cria doze túneis IPsec com interfaces de loopback usando os endereços IP com hash calculados (192.168.1.X) da seção anterior.
Uma configuração semelhante se aplicaria ao outro ponto final do roteador (c8kv-peer) com os oito endereços IP com hash calculados restantes (192.168.2.X).
ip cef load-sharing algorithm include-ports source destination 00ABC123
crypto keyring tunnel0
local-address Loopback0
pre-shared-key address 192.168.2.38 key cisco
crypto keyring tunnel1
local-address Loopback1
pre-shared-key address 192.168.2.37 key cisco
crypto keyring tunnel2
local-address Loopback2
pre-shared-key address 192.168.2.53 key cisco
crypto keyring tunnel3
local-address Loopback3
pre-shared-key address 192.168.2.39 key cisco
crypto keyring tunnel4
local-address Loopback4
pre-shared-key address 192.168.2.48 key cisco
crypto keyring tunnel5
local-address Loopback5
pre-shared-key address 192.168.2.58 key cisco
crypto keyring tunnel6
local-address Loopback6
pre-shared-key address 192.168.2.42 key cisco
crypto keyring tunnel7
local-address Loopback7
pre-shared-key address 192.168.2.46 key cisco
crypto keyring tunnel8
local-address Loopback8
pre-shared-key address 192.168.2.40 key cisco
crypto keyring tunnel9
local-address Loopback9
pre-shared-key address 192.168.2.43 key cisco
crypto keyring tunnel10
local-address Loopback10
pre-shared-key address 192.168.2.36 key cisco
crypto keyring tunnel11
local-address Loopback11
pre-shared-key address 192.168.2.56 key cisco
crypto isakmp policy 200
encryption aes
hash sha
authentication pre-share
group 16
lifetime 28800
crypto isakmp profile isakmp-tunnel0
keyring tunnel0
match identity address 0.0.0.0
local-address Loopback0
crypto isakmp profile isakmp-tunnel1
keyring tunnel1
match identity address 0.0.0.0
local-address Loopback1
crypto isakmp profile isakmp-tunnel2
keyring tunnel2
match identity address 0.0.0.0
local-address Loopback2
crypto isakmp profile isakmp-tunnel3
keyring tunnel3
match identity address 0.0.0.0
local-address Loopback3
crypto isakmp profile isakmp-tunnel4
keyring tunnel4
match identity address 0.0.0.0
local-address Loopback4
crypto isakmp profile isakmp-tunnel5
keyring tunnel5
match identity address 0.0.0.0
local-address Loopback5
crypto isakmp profile isakmp-tunnel6
keyring tunnel6
match identity address 0.0.0.0
local-address Loopback6
crypto isakmp profile isakmp-tunnel7
keyring tunnel7
match identity address 0.0.0.0
local-address Loopback7
crypto isakmp profile isakmp-tunnel8
keyring tunnel8
match identity address 0.0.0.0
local-address Loopback8
crypto isakmp profile isakmp-tunnel9
keyring tunnel9
match identity address 0.0.0.0
local-address Loopback9
crypto isakmp profile isakmp-tunnel10
keyring tunnel10
match identity address 0.0.0.0
local-address Loopback10
crypto isakmp profile isakmp-tunnel11
keyring tunnel11
match identity address 0.0.0.0
local-address Loopback11
crypto ipsec transform-set ipsec-prop-vpn-tunnel esp-gcm 256
mode tunnel
crypto ipsec df-bit clear
crypto ipsec profile ipsec-vpn-tunnel
set transform-set ipsec-prop-vpn-tunnel
set pfs group16
interface Loopback0
ip address 192.168.1.38 255.255.255.255
!
interface Loopback1
ip address 192.168.1.37 255.255.255.255
!
interface Loopback2
ip address 192.168.1.53 255.255.255.255
!
interface Loopback3
ip address 192.168.1.39 255.255.255.255
!
interface Loopback4
ip address 192.168.1.48 255.255.255.255
!
interface Loopback5
ip address 192.168.1.58 255.255.255.255
!
interface Loopback6
ip address 192.168.1.42 255.255.255.255
!
interface Loopback7
ip address 192.168.1.46 255.255.255.255
!
interface Loopback8
ip address 192.168.1.40 255.255.255.255
!
interface Loopback9
ip address 192.168.1.43 255.255.255.255
!
interface Loopback10
ip address 192.168.1.36 255.255.255.255
!
interface Loopback11
ip address 192.168.1.56 255.255.255.255
interface Tunnel0
ip address 10.101.100.101 255.255.255.0
load-interval 30
tunnel source Loopback0
tunnel mode ipsec ipv4
tunnel destination 192.168.2.38
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel1
ip address 10.101.101.101 255.255.255.0
load-interval 30
tunnel source Loopback1
tunnel mode ipsec ipv4
tunnel destination 192.168.2.37
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel2
ip address 10.101.102.101 255.255.255.0
load-interval 30
tunnel source Loopback2
tunnel mode ipsec ipv4
tunnel destination 192.168.2.53
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel3
ip address 10.101.103.101 255.255.255.0
load-interval 30
tunnel source Loopback3
tunnel mode ipsec ipv4
tunnel destination 192.168.2.39
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel4
ip address 10.101.104.101 255.255.255.0
load-interval 30
tunnel source Loopback4
tunnel mode ipsec ipv4
tunnel destination 192.168.2.48
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel5
ip address 10.101.105.101 255.255.255.0
load-interval 30
tunnel source Loopback5
tunnel mode ipsec ipv4
tunnel destination 192.168.2.58
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel6
ip address 10.101.106.101 255.255.255.0
load-interval 30
tunnel source Loopback6
tunnel mode ipsec ipv4
tunnel destination 192.168.2.42
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel7
ip address 10.101.107.101 255.255.255.0
load-interval 30
tunnel source Loopback7
tunnel mode ipsec ipv4
tunnel destination 192.168.2.46
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel8
ip address 10.101.108.101 255.255.255.0
load-interval 30
tunnel source Loopback8
tunnel mode ipsec ipv4
tunnel destination 192.168.2.40
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel9
ip address 10.101.109.101 255.255.255.0
load-interval 30
tunnel source Loopback9
tunnel mode ipsec ipv4
tunnel destination 192.168.2.43
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel10
ip address 10.101.110.101 255.255.255.0
load-interval 30
tunnel source Loopback10
tunnel mode ipsec ipv4
tunnel destination 192.168.2.36
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel11
ip address 10.101.111.101 255.255.255.0
load-interval 30
tunnel source Loopback11
tunnel mode ipsec ipv4
tunnel destination 192.168.2.56
tunnel protection ipsec profile ipsec-vpn-tunnel
interface GigabitEthernet2
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
! ### IP route from c8kv-uut to local servers
ip route 10.1.0.0 255.255.0.0 GigabitEthernet2 10.0.1.10
! ### IP routes from c8kv-uut to clients on c8kv-peer side, routes are evenly distributed to all 12 TXQ’s
ip route 10.10.0.0 255.255.0.0 Tunnel0
ip route 10.10.0.0 255.255.0.0 Tunnel1
ip route 10.10.0.0 255.255.0.0 Tunnel2
ip route 10.10.0.0 255.255.0.0 Tunnel3
ip route 10.10.0.0 255.255.0.0 Tunnel4
ip route 10.10.0.0 255.255.0.0 Tunnel5
ip route 10.10.0.0 255.255.0.0 Tunnel6
ip route 10.10.0.0 255.255.0.0 Tunnel7
ip route 10.10.0.0 255.255.0.0 Tunnel8
ip route 10.10.0.0 255.255.0.0 Tunnel9
ip route 10.10.0.0 255.255.0.0 Tunnel10
ip route 10.10.0.0 255.255.0.0 Tunnel11
! ### IP route from c8kv-uut Loopback int tunnel endpoint to c8kv-peer Loopback int tunnel endpoints
ip route 192.168.2.0 255.255.255.0 GigabitEthernet3 10.0.2.30 Exemplo de configuração de topologia e CLI usando 12 TXQs com endereços IP secundários

Figura 5. Exemplo de topologia que usa doze TxQs usando endereços IP secundários.
Se os endereços de loopback não puderem ser usados no ambiente AWS, os endereços IP secundários anexados ao ENI poderão ser usados.
Este é um exemplo de configuração CLI para 'c8kv-out' (Figura 5) que cria doze túneis IPsec com a origem sendo 1 endereço IP primário + 11 endereços IP secundários conectados à interface GigabitEthernet3 usando endereços IP com hash calculados (10.0.2.X). Uma configuração semelhante se aplicaria ao outro ponto final do roteador (c8kv-peer) com os doze endereços IP com hash calculados restantes (20.0.2.X).

Note: Neste exemplo, estamos usando um segundo C8000V como o endpoint de túnel, mas outros endpoints de rede em nuvem, como TGW ou DX, também podem ser usados.
ip cef load-sharing algorithm include-ports source destination 00ABC123
crypto keyring tunnel0
local-address 10.0.2.20
pre-shared-key address 20.0.2.30 key cisco
crypto keyring tunnel1
local-address 10.0.2.21
pre-shared-key address 20.0.2.31 key cisco
crypto keyring tunnel2
local-address 10.0.2.22
pre-shared-key address 20.0.2.32 key cisco
crypto keyring tunnel3
local-address 10.0.2.23
pre-shared-key address 20.0.2.33 key cisco
crypto keyring tunnel4
local-address 10.0.2.24
pre-shared-key address 20.0.2.36 key cisco
crypto keyring tunnel5
local-address 10.0.2.25
pre-shared-key address 20.0.2.35 key cisco
crypto keyring tunnel6
local-address 10.0.2.26
pre-shared-key address 20.0.2.37 key cisco
crypto keyring tunnel7
local-address 10.0.2.27
pre-shared-key address 20.0.2.38 key cisco
crypto keyring tunnel8
local-address 10.0.2.28
pre-shared-key address 20.0.2.40 key cisco
crypto keyring tunnel9
local-address 10.0.2.29
pre-shared-key address 20.0.2.41 key cisco
crypto keyring tunnel10
local-address 10.0.2.30
pre-shared-key address 20.0.2.44 key cisco
crypto keyring tunnel11
local-address 10.0.2.31
pre-shared-key address 20.0.2.46 key cisco
crypto isakmp policy 200
encryption aes
hash sha
authentication pre-share
group 16
lifetime 28800
crypto isakmp profile isakmp-tunnel0
keyring tunnel0
match identity address 20.0.2.30 255.255.255.255
local-address 10.0.2.20
crypto isakmp profile isakmp-tunnel1
keyring tunnel1
match identity address 20.0.2.31 255.255.255.255
local-address 10.0.2.21
crypto isakmp profile isakmp-tunnel2
keyring tunnel2
match identity address 20.0.2.32 255.255.255.255
local-address 10.0.2.22
crypto isakmp profile isakmp-tunnel3
keyring tunnel3
match identity address 20.0.2.33 255.255.255.255
local-address 10.0.2.23
crypto isakmp profile isakmp-tunnel4
keyring tunnel4
match identity address 20.0.2.36 255.255.255.255
local-address 10.0.2.24
crypto isakmp profile isakmp-tunnel5
keyring tunnel5
match identity address 20.0.2.35 255.255.255.255
local-address 10.0.2.25
crypto isakmp profile isakmp-tunnel6
keyring tunnel6
match identity address 20.0.2.37 255.255.255.255
local-address 10.0.2.26
crypto isakmp profile isakmp-tunnel7
keyring tunnel7
match identity address 20.0.2.38 255.255.255.255
local-address 10.0.2.27
crypto isakmp profile isakmp-tunnel8
keyring tunnel8
match identity address 20.0.2.40 255.255.255.255
local-address 10.0.2.28
crypto isakmp profile isakmp-tunnel9
keyring tunnel9
match identity address 20.0.2.41 255.255.255.255
local-address 10.0.2.29
crypto isakmp profile isakmp-tunnel10
keyring tunnel10
match identity address 20.0.2.44 255.255.255.255
local-address 10.0.2.30
crypto isakmp profile isakmp-tunnel11
keyring tunnel11
match identity address 20.0.2.46 255.255.255.255
local-address 10.0.2.31
crypto ipsec transform-set ipsec-prop-vpn-tunnel esp-gcm 256
mode tunnel
crypto ipsec df-bit clear
crypto ipsec profile ipsec-vpn-tunnel
set transform-set ipsec-prop-vpn-tunnel
set pfs group16
interface Tunnel0
ip address 10.101.100.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.20
tunnel mode ipsec ipv4
tunnel destination 20.0.2.30
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel1
ip address 10.101.101.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.21
tunnel mode ipsec ipv4
tunnel destination 20.0.2.31
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel2
ip address 10.101.102.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.22
tunnel mode ipsec ipv4
tunnel destination 20.0.2.32
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel3
ip address 10.101.103.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.23
tunnel mode ipsec ipv4
tunnel destination 20.0.2.33
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel4
ip address 10.101.104.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.24
tunnel mode ipsec ipv4
tunnel destination 20.0.2.36
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel5
ip address 10.101.105.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.25
tunnel mode ipsec ipv4
tunnel destination 20.0.2.35
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel6
ip address 10.101.106.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.26
tunnel mode ipsec ipv4
tunnel destination 20.0.2.37
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel7
ip address 10.101.107.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.27
tunnel mode ipsec ipv4
tunnel destination 20.0.2.38
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel8
ip address 10.101.108.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.28
tunnel mode ipsec ipv4
tunnel destination 20.0.2.40
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel9
ip address 10.101.109.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.29
tunnel mode ipsec ipv4
tunnel destination 20.0.2.41
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel10
ip address 10.101.110.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.30
tunnel mode ipsec ipv4
tunnel destination 20.0.2.44
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface Tunnel11
ip address 10.101.111.101 255.255.255.0
load-interval 30
tunnel source 10.0.2.31
tunnel mode ipsec ipv4
tunnel destination 20.0.2.46
tunnel protection ipsec profile ipsec-vpn-tunnel
!
interface GigabitEthernet2
mtu 9216
ip address dhcp
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
mtu 9216
ip address 10.0.2.20 255.255.255.0
ip address 10.0.2.21 255.255.255.0 secondary
ip address 10.0.2.22 255.255.255.0 secondary
ip address 10.0.2.23 255.255.255.0 secondary
ip address 10.0.2.24 255.255.255.0 secondary
ip address 10.0.2.25 255.255.255.0 secondary
ip address 10.0.2.26 255.255.255.0 secondary
ip address 10.0.2.27 255.255.255.0 secondary
ip address 10.0.2.28 255.255.255.0 secondary
ip address 10.0.2.29 255.255.255.0 secondary
ip address 10.0.2.30 255.255.255.0 secondary
ip address 10.0.2.31 255.255.255.0 secondary
load-interval 30
speed 25000
no negotiation auto
no mop enabled
no mop sysid
!
! ### IP route from c8kv-uut to local servers
ip route 10.1.0.0 255.255.255.0 GigabitEthernet2 10.0.1.10
! ### IP routes from c8kv-uut to clients on c8kv-peer side, routes are evenly distributed to all 12 TXQ’s
ip route 10.10.0.0 255.255.0.0 Tunnel0
ip route 10.10.0.0 255.255.0.0 Tunnel1
ip route 10.10.0.0 255.255.0.0 Tunnel2
ip route 10.10.0.0 255.255.0.0 Tunnel3
ip route 10.10.0.0 255.255.0.0 Tunnel4
ip route 10.10.0.0 255.255.0.0 Tunnel5
ip route 10.10.0.0 255.255.0.0 Tunnel6
ip route 10.10.0.0 255.255.0.0 Tunnel7
ip route 10.10.0.0 255.255.0.0 Tunnel8
ip route 10.10.0.0 255.255.0.0 Tunnel9
ip route 10.10.0.0 255.255.0.0 Tunnel10
ip route 10.10.0.0 255.255.0.0 Tunnel11
! ### IP route from c8kv-uut Gi3 int tunnel endpoint to c8kv-peer Gi3
int tunnel endpoints (secondary IP addresses on c8kv-peer side)
ip route 20.0.2.30 255.255.255.255 10.0.2.1
ip route 20.0.2.31 255.255.255.255 10.0.2.1
ip route 20.0.2.32 255.255.255.255 10.0.2.1
ip route 20.0.2.33 255.255.255.255 10.0.2.1
ip route 20.0.2.36 255.255.255.255 10.0.2.1
ip route 20.0.2.35 255.255.255.255 10.0.2.1
ip route 20.0.2.37 255.255.255.255 10.0.2.1
ip route 20.0.2.38 255.255.255.255 10.0.2.1
ip route 20.0.2.40 255.255.255.255 10.0.2.1
ip route 20.0.2.41 255.255.255.255 10.0.2.1
ip route 20.0.2.44 255.255.255.255 10.0.2.1
ip route 20.0.2.46 255.255.255.255 10.0.2.1 Implantação típica do Catalyst 8000V no AWS
Modo Autônomo
Consulte os exemplos anteriores de configurações e topologias CLI. A configuração da CLI pode ser copiada e modificada com base no esquema de endereçamento de rede e nos endereços IP com hash gerados.
Para uma criação de túnel bem-sucedida, certifique-se de criar rotas IP no C8000V e nas tabelas de roteamento no AWS VPC.
Modo SD-WAN
Este é um exemplo de topologia e configuração de SD-WAN que cria TLOCs usando interfaces de loopback em C8000Vs localizados em um AWS VPC.
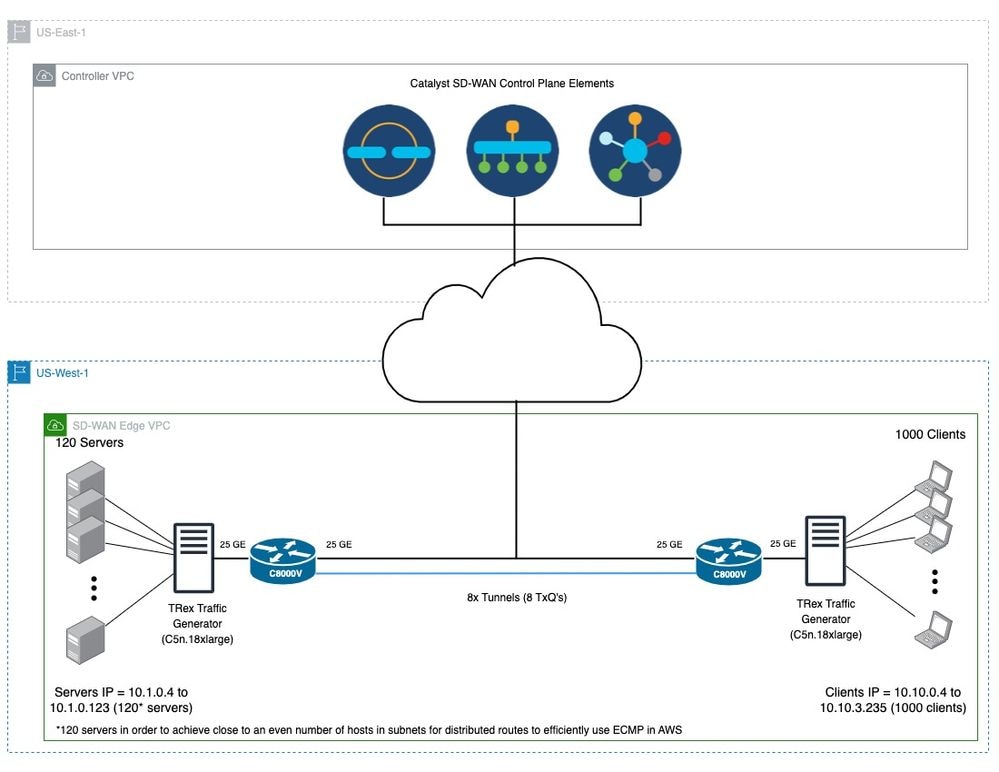
Figura 6. Exemplo de topologia SD-WAN que usa TLOCs com interfaces de loopback em C8000Vs localizados em um AWS VPC.

Note: Na figura 6, a conexão em preto representa a conexão de controle (VPN0) entre os elementos do plano de controle da SD-WAN e os dispositivos de borda da SD-WAN. As conexões de cor azul representam os túneis entre os dois dispositivos de borda da SD-WAN que usam TLOCs.
Você pode encontrar um exemplo de configuração de SD-WAN CLI para a Figura 6 (aqui).
csr_uut#show sdwan run
system
system-ip 29.173.249.161
site-id 5172
admin-tech-on-failure
sp-organization-name SP_ORG_NAME
organization-name ORG_NAME
upgrade-confirm 15
vbond X.X.X.X
!
memory free low-watermark processor 68484
service timestamps debug datetime msec
service timestamps log datetime msec
no service tcp-small-servers
no service udp-small-servers
platform console virtual
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
hostname csr_uut
username ec2-user privilege 15 secret 5 $1$4P16$..ag88eFsOMLIemjNcWSt0
vrf definition 11
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
!
vrf definition Mgmt-intf
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
!
no ip finger
no ip rcmd rcp-enable
no ip rcmd rsh-enable
no ip dhcp use class
ip route 0.0.0.0 0.0.0.0 X.X.X.X
ip route 0.0.0.0 0.0.0.0 X.X.X.X
ip route 0.0.0.0 0.0.0.0 X.X.X.X
ip route vrf 11 10.1.0.0 255.255.0.0 X.X.X.X
ip route vrf Mgmt-intf 0.0.0.0 0.0.0.0 X.X.X.X
no ip source-route
ip ssh pubkey-chain
username ec2-user
key-hash ssh-rsa 353158c28c7649710b3c933da02e384b ec2-user
!
!
!
no ip http server
ip http secure-server
ip nat settings central-policy
ip nat settings gatekeeper-size 1024
ipv6 unicast-routing
class-map match-any class0
match dscp 1
!
class-map match-any class1
match dscp 2
!
class-map match-any class2
match dscp 3
!
class-map match-any class3
match dscp 4
!
class-map match-any class4
match dscp 5
!
class-map match-any class5
match dscp 6
!
class-map match-any class6
match dscp 7
!
class-map match-any class7
match dscp 8
!
policy-map qos_map1
class class0
priority percent 20
!
class class1
bandwidth percent 18
random-detect
!
class class2
bandwidth percent 15
random-detect
!
class class3
bandwidth percent 12
random-detect
!
class class4
bandwidth percent 10
random-detect
!
class class5
bandwidth percent 10
random-detect
!
class class6
bandwidth percent 10
random-detect
!
class class7
bandwidth percent 5
random-detect
!
!
interface GigabitEthernet1
no shutdown
ip address dhcp
no mop enabled
no mop sysid
negotiation auto
exit
interface GigabitEthernet2
no shutdown
ip address dhcp
load-interval 30
speed 10000
no negotiation auto
service-policy output qos_map1
exit
interface GigabitEthernet3
shutdown
ip address dhcp
load-interval 30
speed 10000
no negotiation auto
exit
interface GigabitEthernet4
no shutdown
vrf forwarding 11
ip address X.X.X.X 255.255.255.0
load-interval 30
speed 10000
no negotiation auto
exit
interface Loopback1
no shutdown
ip address 192.168.1.21 255.255.255.255
exit
interface Loopback2
no shutdown
ip address 192.168.1.129 255.255.255.255
exit
interface Loopback3
no shutdown
ip address 192.168.1.20 255.255.255.255
exit
interface Loopback4
no shutdown
ip address 192.168.1.128 255.255.255.255
exit
interface Loopback5
no shutdown
ip address 192.168.1.23 255.255.255.255
exit
interface Loopback6
no shutdown
ip address 192.168.1.131 255.255.255.255
exit
interface Loopback7
no shutdown
ip address 192.168.1.22 255.255.255.255
exit
interface Loopback8
no shutdown
ip address 192.168.1.130 255.255.255.255
exit
interface Tunnel1
no shutdown
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode sdwan
exit
interface Tunnel14095001
no shutdown
ip unnumbered Loopback1
no ip redirects
ipv6 unnumbered Loopback1
no ipv6 redirects
tunnel source Loopback1
tunnel mode sdwan
exit
interface Tunnel14095002
no shutdown
ip unnumbered Loopback2
no ip redirects
ipv6 unnumbered Loopback2
no ipv6 redirects
tunnel source Loopback2
tunnel mode sdwan
exit
interface Tunnel14095003
no shutdown
ip unnumbered Loopback3
no ip redirects
ipv6 unnumbered Loopback3
no ipv6 redirects
tunnel source Loopback3
tunnel mode sdwan
exit
interface Tunnel14095004
no shutdown
ip unnumbered Loopback4
no ip redirects
ipv6 unnumbered Loopback4
no ipv6 redirects
tunnel source Loopback4
tunnel mode sdwan
exit
interface Tunnel14095005
no shutdown
ip unnumbered Loopback5
no ip redirects
ipv6 unnumbered Loopback5
no ipv6 redirects
tunnel source Loopback5
tunnel mode sdwan
exit
interface Tunnel14095006
no shutdown
ip unnumbered Loopback6
no ip redirects
ipv6 unnumbered Loopback6
no ipv6 redirects
tunnel source Loopback6
tunnel mode sdwan
exit
interface Tunnel14095007
no shutdown
ip unnumbered Loopback7
no ip redirects
ipv6 unnumbered Loopback7
no ipv6 redirects
tunnel source Loopback7
tunnel mode sdwan
exit
interface Tunnel14095008
no shutdown
ip unnumbered Loopback8
no ip redirects
ipv6 unnumbered Loopback8
no ipv6 redirects
tunnel source Loopback8
tunnel mode sdwan
exit
no logging console
aaa authentication enable default enable
aaa authentication login default local
aaa authorization console
aaa authorization exec default local none
login on-success log
license smart transport smart
license smart url https://smartreceiver.cisco.com/licservice/license
line aux 0
!
line con 0
stopbits 1
!
line vty 0 4
transport input ssh
!
line vty 5 80
transport input ssh
!
sdwan
interface GigabitEthernet1
tunnel-interface
encapsulation ipsec
color private1 restrict
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface GigabitEthernet2
exit
interface GigabitEthernet3
exit
interface Loopback1
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private2 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback2
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private3 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback3
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private4 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback4
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private5 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback5
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color private6 restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback6
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color red restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback7
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color blue restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
interface Loopback8
tunnel-interface
encapsulation ipsec preference 150 weight 1
no border
color green restrict
no last-resort-circuit
no low-bandwidth-link
max-control-connections 0
no vbond-as-stun-server
vmanage-connection-preference 0
port-hop
carrier default
nat-refresh-interval 5
hello-interval 1000
hello-tolerance 12
bind GigabitEthernet2
no allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
appqoe
no tcpopt enable
no dreopt enable
no httpopt enable
!
omp
no shutdown
send-path-limit 16
ecmp-limit 16
graceful-restart
no as-dot-notation
timers
graceful-restart-timer 43200
exit
address-family ipv4
advertise connected
advertise static
!
address-family ipv6
advertise connected
advertise static
!
!
!
security
ipsec
replay-window 8192
integrity-type ip-udp-esp esp
!
!
sslproxy
no enable
rsa-key-modulus 2048
certificate-lifetime 730
eckey-type P256
ca-tp-label PROXY-SIGNING-CA
settings expired-certificate drop
settings untrusted-certificate drop
settings unknown-status drop
settings certificate-revocation-check none
settings unsupported-protocol-versions drop
settings unsupported-cipher-suites drop
settings failure-mode close
settings minimum-tls-ver TLSv1
dual-side optimization enable
!
policy
app-visibility
flow-visibility
!Solução de problemas de desempenho de throughput no AWS

Note: A realização de testes de desempenho em ambientes de nuvem pública introduz novas variáveis que podem afetar o desempenho do throughput. Estes são alguns pontos a serem considerados durante a execução desses tipos de testes:
- Uso de recursos subjacentes pelos pares no momento da execução dos testes
- Não usar hosts dedicados (o uso de hosts dedicados aumenta o custo da nuvem em 16x)
- A nuvem é executada em regiões diferentes, o desempenho pode variar
- Em alguns casos, os números são semelhantes independentemente do perfil de recurso; isso possivelmente se deve à limitação de AWS na interface por tamanho de instância
- O AWS acelera a taxa de pacotes por segundo em instâncias EC2 que também podem causar a queda de pacotes
- O AWS não divulga a taxa de limitação, mas as quedas devido à limitação de pps podem ser observadas por meio do contador 'pps_permit_beyond'
Comandos úteis de solução de problemas do CLI
Ao conduzir testes de desempenho de throughput, esses comandos de identificação e solução de problemas podem ser usados para identificar gargalos ou motivos para degradação do desempenho.
"show platform hardware qfp ative statistics drop" - nos permite entender se há qualquer queda no c8kv. Precisamos garantir que não haja descartes traseiros significativos ou incrementos de contadores relevantes.
"show platform hardware qfp ative statistics drop clear" - Este comando limpa os contadores.
"show platform hardware qfp ative datapath infrastructure sw-cio" - Este comando fornece informações detalhadas sobre a porcentagem de Packet Processor (PP), Traffic Manager (TM) sendo utilizada durante as execuções de desempenho. Isso nos permite determinar se há capacidade de processamento suficiente ou não do c8kv.
"show platform hardware qfp ative datapath util summary" - Este comando fornece as informações completas de entrada/saída que o c8kv está transmitindo/recebendo de todas as portas.
Verifique a taxa de entrada/saída e veja se há queda. Verifique também a porcentagem de carga de processamento. Se atingir 100%; significa que o c8kv atingiu sua capacidade.
"show plat hardware qfp ative infrastructure bqs interface GigabitEthernetX" - Esse comando permite verificar as estatísticas do nível de interface em termos de número de fila, largura de banda, descartes.
"show controller" - Este comando nos fornece muitas informações granulares sobre os pacotes bons rx/tx, pacotes perdidos.
Esse comando pode ser usado em um cenário em que não vemos nenhum descarte traseiro, mas o gerador de Tráfego ainda nos mostra o descarte.
Isso pode acontecer em um cenário em que a utilização de dados já está atingindo 100% e da mesma forma o PP em 100%.
Se os contadores rx_miss_errors continuam aumentando, isso indica que o CSR está pressionando a infraestrutura de nuvem porque não consegue processar mais nenhum tráfego.
"show platform hardware qfp ative datapath infrastructure sw-hqf" - pode ser usado para verificar se há congestionamento devido à pressão de retorno do AWS.
"show plat hardware qfp ative datapath infrastructure sw-nic" - Determina como a carga do tráfego é balanceada em várias filas. Após 17.7, temos 8 Multi-TXQs.
Além disso, ele pode determinar se há alguma fila específica que esteja pegando todo o tráfego ou sendo balanceada corretamente.
"show controllers | em erros|excedido|Giga" - Mostra as quedas de pacotes devido à limitação de pps feita do lado AWS, que pode ser observada através do contador pps_allowbeyond_counter.
Exemplo de saída CLI
Exemplo de saída em que o contador de descartes de cauda continua incrementando - Emita o comando várias vezes para ver se os contadores estão incrementando, permitindo assim que confirmemos que são realmente descartes de cauda.
csr_uut#show platform hardware qfp active statistics drop
Last clearing of QFP drops statistics : never
-------------------------------------------------------------------------
Global Drop Stats Packets Octets
-------------------------------------------------------------------------
Disabled 30 3693
IpFragErr 192 290976
Ipv4NoRoute 43 3626
Ipv6NoRoute 4 224
SdwanImplicitAclDrop 31 3899
TailDrop 19099700 22213834441
UnconfiguredIpv6Fia 3816 419760
Exemplo de saída mostrado aqui - Emita o comando a cada 30 segundos para obter os dados em tempo real
csr_uut#show platform hardware qfp active datapath infrastructure sw-cio
Credits Usage:
ID Port Wght Global WRKR0 WRKR1 WRKR2 WRKR3 WRKR4 WRKR5 WRKR6 WRKR7 WRKR8 WRKR9 WRKR10 WRKR11 WRKR12 WRKR13 Total
1 rcl0 16: 455 0 4 1 2 3 2 2 4 4 4 4 0 4 23 512
1 rcl0 32: 496 0 0 0 0 0 0 0 0 0 0 0 0 0 16 512
2 ipc 1: 468 4 2 4 3 0 1 1 4 0 2 0 4 0 18 511
3 vxe_punti 4: 481 0 0 0 0 0 0 0 0 0 0 0 0 0 31 512
4 Gi1 4: 446 0 0 1 1 0 2 3 0 3 2 0 1 1 52 512
5 Gi2 4: 440 4 4 4 3 2 1 1 3 2 4 4 3 2 59 504
6 Gi3 4: 428 1 1 1 0 4 4 1 0 4 4 0 0 2 43 494
7 Gi4 4: 427 1 1 0 1 4 2 0 4 3 4 1 1 7 56 512
Core Utilization over preceding 12819.5863 seconds
--------------------------------------------------
ID: 0 1 2 3 4 5 6 7 8 9 10 11 12 13
% PP: 6.11 6.23 6.09 6.09 6.04 6.05 6.06 6.07 6.05 6.03 6.04 6.06 0.00 0.00
% RX: 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 2.23
% TM:0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 4.79 0.00
% IDLE: 93.89 93.77 93.91 93.91 93.96 93.95 93.94 93.93 93.95 93.97 93.96 93.94 95.21 97.77
Exemplo de saída mostrado aqui - Verifique a taxa de entrada/saída e veja se há queda. Verifique também a porcentagem de carga de processamento. Se atingir 100%; significa que o nó atingiu sua capacidade.
csr_uut#show platform hardware qfp active datapath util summary
CPP 0: 5 secs 1 min 5 min 60 min
Input: Total (pps)900215 980887 903176 75623
(bps) 10276623992 11197595912 10310265440 863067008
Output: Total (pps)900216 937459 865930 72522
(bps) 10276642720 10712432752 9894215928 828417104
Processing: Load (pct)56 58 54 4
Exemplo de saída mostrado aqui para estatísticas de nível de interface:
csr_uut#sh plat hardware qfp active infrastructure bqs interface GigabitEthernet2
Interface: GigabitEthernet2, QFP interface: 7
Queue: QID: 111 (0x6f)
bandwidth (cfg) : 0 , bandwidth (hw) : 1050000000
shape (cfg) : 0 , shape (hw) : 0
prio level (cfg) : 0 , prio level (hw) : n/a
limit (pkts ) : 1043
Statistics:
depth (pkts ) : 0
tail drops (bytes): 0 , (packets) : 0
total enqs (bytes): 459322360227 , (packets) : 374613901
licensed throughput oversubscription drops:
(bytes): 0 , (packets) : 0
Schedule: (SID:0x8a)
Schedule FCID : n/a
bandwidth (cfg) : 10500000000 , bandwidth (hw) : 10500000000
shape (cfg) : 10500000000 , shape (hw) : 10500000000
Schedule: (SID:0x87)
Schedule FCID : n/a
bandwidth (cfg) : 200000000000 , bandwidth (hw) : 200000000000
shape (cfg) : 200000000000 , shape (hw) : 200000000000
Schedule: (SID:0x86)
Schedule FCID : n/a
bandwidth (cfg) : 500000000000 , bandwidth (hw) : 500000000000
shape (cfg) : 500000000000 , shape (hw) : 500000000000
csr_uut#sh plat hardware qfp active infrastructure bqs interface GigabitEthernet3 | inc tail
tail drops (bytes): 55815791988 , (packets) : 43177643
Exemplo de saída para os pacotes bons de RX/TX, estatísticas de pacotes perdidos
c8kv-aws-1#show controller
GigabitEthernet1 - Gi1 is mapped to UIO on VXE
rx_good_packets 346
tx_good_packets 243
rx_good_bytes 26440
tx_good_bytes 31813
rx_missed_errors 0
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
GigabitEthernet2 - Gi2 is mapped to UIO on VXE
rx_good_packets 96019317
tx_good_packets 85808651
rx_good_bytes 12483293931
tx_good_bytes 11174853219
rx_missed_errors 522036
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
GigabitEthernet3 - Gi3 is mapped to UIO on VXE
rx_good_packets 171596935
tx_good_packets 191911304
rx_good_bytes 11668588022
tx_good_bytes 13049984257
rx_missed_errors 21356065
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
GigabitEthernet4 - Gi4 is mapped to UIO on VXE
rx_good_packets 95922932
tx_good_packets 85831238
rx_good_bytes 12470124252
tx_good_bytes 11158486786
rx_missed_errors 520328
rx_errors 46
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0packets 0
rx_q0bytes 0
rx_q0errors 0
tx_q0packets 0
tx_q0bytes 0
Exemplo de saída para verificar se há congestionamento devido à pressão contrária de AWS:
csr_uut#show platform hardware qfp active datapath infrastructure sw-hqf
Name : Pri1 Pri2 None / Inflight pkts
GigabitEthernet4 : XON XON XOFF / 43732
HQF[0] IPC: send 514809 fc 0 congested_cnt 0
HQF[0] recycle: send hi 0 send lo 228030112
fc hi 0 fc lo 0
cong hi 0 cong lo 0
HQF[0] pkt: send hi 433634 send lo 2996661158
fc/full hi 0 fc/full lo 34567275
cong hi 0 cong lo 4572971630**************Congestion counters keep incrementing
HQF[0] aggr send stats 3225639713 aggr send lo state 3225206079
aggr send hi stats 433634
max_tx_burst_sz_hi 0 max_tx_burst_sz_lo 0
HQF[0] gather: failed_to_alloc_b4q 0
HQF[0] ticks 662109543, max ticks accumulated 348
HQF[0] mpsc stats: count: 0
enq 3225683472 enq_spin 0 enq_post 0 enq_flush 0
sig_cnt:0 enq_cancel 0
deq 3225683472 deq_wait 0 deq_fail 0 deq_cancel 0
deq_wait_timeout
Exemplo de saída de como o tráfego tem a carga balanceada em várias filas:
um-csr-uut#sh plat hardware qfp active datapath infrastructure sw-nic
pmd b1c5a400 device Gi1
RX: pkts 50258 bytes 4477620 return 0 badlen 0
pkts/burst 1 cycl/pkt 579 ext_cycl/pkt 996
Total ring read 786244055, empty 786197491
TX: pkts 57860 bytes 6546349
pri-0: pkts 7139 bytes 709042
pkts/send 1
pri-1: pkts 3868 bytes 451352
pkts/send 1
pri-2: pkts 1875 bytes 219403
pkts/send 1
pri-3: pkts 2417 bytes 242527
pkts/send 1
pri-4: pkts 8301 bytes 984022
pkts/send 1
pri-5: pkts 10268 bytes 1114859
pkts/send 1
pri-6: pkts 1740 bytes 175353
pkts/send 1
pri-7: pkts 22252 bytes 2649791
pkts/send 1
Total: pkts/send 1 cycl/pkt 1091
send 56756 sendnow 0
forced 56756 poll 0 thd_poll 0
blocked 0 retries 0 mbuf alloc err 0
TX Queue 0: full 0 current index 0 hiwater 0
TX Queue 1: full 0 current index 0 hiwater 0
TX Queue 2: full 0 current index 0 hiwater 0
TX Queue 3: full 0 current index 0 hiwater 0
TX Queue 4: full 0 current index 0 hiwater 0
TX Queue 5: full 0 current index 0 hiwater 0
TX Queue 6: full 0 current index 0 hiwater 0
TX Queue 7: full 0 current index 0 hiwater 0
pmd b1990b00 device Gi2
RX: pkts 1254741010 bytes 511773562848 return 0 badlen 0
pkts/burst 16 cycl/pkt 792 ext_cycl/pkt 1342
Total ring read 1012256968, empty 937570790
TX: pkts 1385120320 bytes 564465308380
pri-0: pkts 168172786 bytes 68650796972
pkts/send 1
pri-1: pkts 177653235 bytes 72542203822
pkts/send 1
pri-2: pkts 225414300 bytes 91947701824
pkts/send 1
pri-3: pkts 136817435 bytes 55908224442
pkts/send 1
pri-4: pkts 256461818 bytes 104687120554
pkts/send 1
pri-5: pkts 176043289 bytes 71879529606
pkts/send 1
pri-6: pkts 83920827 bytes 34264110122
pkts/send 1
pri-7: pkts 160636635 bytes 64585622696
pkts/send 1
Total: pkts/send 1 cycl/pkt 442
send 1033104466 sendnow 41250092
forced 1776500651 poll 244223290 thd_poll 0
blocked 1060879040 retries 3499069 mbuf alloc err 0
TX Queue 0: full 0 current index 0 hiwater 31
TX Queue 1: full 718680 current index 0 hiwater 255
TX Queue 2: full 0 current index 0 hiwater 31
TX Queue 3: full 0 current index 0 hiwater 31
TX Queue 4: full 15232240 current index 0 hiwater 255
TX Queue 5: full 0 current index 0 hiwater 31
TX Queue 6: full 0 current index 0 hiwater 31
TX Queue 7: full 230668 current index 0 hiwater 224
pmd b1712d00 device Gi3
RX: pkts 1410702537 bytes 498597093510 return 0 badlen 0
pkts/burst 18 cycl/pkt 269 ext_cycl/pkt 321
Total ring read 1011915032, empty 934750846
TX: pkts 754803798 bytes 266331910366
pri-0: pkts 46992577 bytes 16616415156
pkts/send 1
pri-1: pkts 49194201 bytes 17379760716
pkts/send 1
pri-2: pkts 46991555 bytes 16616509252
pkts/send 1
pri-3: pkts 49195026 bytes 17381741474
pkts/send 1
pri-4: pkts 48875656 bytes 17283423414
pkts/send 1
pri-5: pkts 417370776 bytes 147056906106
pkts/send 6
pri-6: pkts 46992860 bytes 16617923068
pkts/send 1
pri-7: pkts 49191147 bytes 17379231180
pkts/send 1
Total: pkts/send 2 cycl/pkt 0
send 339705775 sendnow 366141927
forced 3138709511 poll 2888466204 thd_poll 0
blocked 1758644571 retries 27927046 mbuf alloc err 0
TX Queue 0: full 0 current index 0 hiwater 0
TX Queue 1: full 0 current index 0 hiwater 0
TX Queue 2: full 0 current index 0 hiwater 0
TX Queue 3: full 0 current index 0 hiwater 0
TX Queue 4: full 0 current index 1 hiwater 0
TX Queue 5: full 27077270 current index 0 hiwater 224
TX Queue 6: full 0 current index 0 hiwater 0
TX Queue 7: full 0 current index 0 hiwater 0
Exemplo de saída que mostra as quedas de pacotes devido à limitação de pps realizada do lado AWS, que pode ser observado através do contador pps_allowamount_excluded:
C8k-AWS-2#show controllers | in errors|exceeded|Giga
GigabitEthernet1 - Gi1 is mapped to UIO on VXE
rx_missed_errors 1750262
rx_errors 0
tx_errors 0
rx_mbuf_allocation_errors 0
rx_q0_errors 0
rx_q1_errors 0
rx_q2_errors 0
rx_q3_errors 0
bw_in_allowance_exceeded 0
bw_out_allowance_exceeded 0
pps_allowance_exceeded 11750
conntrack_allowance_exceeded 0
linklocal_allowance_exceeded 0
Histórico de revisões
| Revisão | Data de publicação | Comentários |
|---|---|---|
1.0 |
07-Aug-2025
|
Versão inicial |
Colaborado por engenheiros da Cisco
- Alexis Flores
- Michalina SlomianskaEngenheiro técnico de marketing
- Josh LeathamArquiteto sênior de soluções de parceiros
Contate a Cisco
- Abrir um caso de suporte

- (É necessário um Contrato de Serviço da Cisco)
 Feedback
Feedback